MN624 Digital Forensic Report: Data Acquisition, Tools and Methods
VerifiedAdded on 2022/09/13
|10
|1015
|18
Report
AI Summary
This report delves into the realm of digital forensics, exploring the critical processes involved in investigating cybercrimes and digital attacks. It begins by defining digital forensics, also known as computer forensics, as a scientific investigatory process focused on identifying, recovering, and validating digital evidence. The report outlines the four primary steps of digital forensics: data collection, examination, analysis, and reporting. It then discusses the ProDiscover forensic tool, highlighting its features and its role in analyzing digital files without compromising data integrity. The report also emphasizes the importance of data acquisition, detailing various methods used to gather digital evidence, including static and live acquisition techniques. Furthermore, it covers data preservation methods like hash values, drive imaging, and chain of custody, ensuring the admissibility of evidence in legal proceedings. The report concludes by explaining two data acquisition methods: creating a disk image file and creating a sparse copy of a targeted folder.

Running head: MN624
MN624
Name of the Student
Name of the University
Author Note
MN624
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN624 1
Table of Contents
Digital Forensic:.........................................................................................................................2
ProDiscover forensics tool:........................................................................................................2
Data acquisition in digital forensic:...........................................................................................3
Data preservation methods in digital forensic:...........................................................................3
Explain two data acquisition method for digital forensic:.........................................................4
References:.................................................................................................................................5
Table of Contents
Digital Forensic:.........................................................................................................................2
ProDiscover forensics tool:........................................................................................................2
Data acquisition in digital forensic:...........................................................................................3
Data preservation methods in digital forensic:...........................................................................3
Explain two data acquisition method for digital forensic:.........................................................4
References:.................................................................................................................................5

2MN624
Digital Clues:
Digital forensic is popularly known as computer forensic, which is one of the
effective scientific investigatory process that helps to investigate the cyber-crime or a digital
attack. Focusing on the application area of digital forensic it is noticed that the nominated
branch consists of crime investigation, identification, recovery process identification,
validation of the identified strategies as well as determination of digital evidence that has
been identified from the investigation [1].
While elaborating the processes identified in the digital forensic technique it is
noticed that it consists of four primary steps which includes the collection of data,
examination of the collected data, analysis of those data as well as from the analysis reporting
the results gathered from those data.
Followed by a thorough investigation on the effectiveness of digital forensic it is
noticed that this technique helps to determine the criminal as well as the intention of the
criminal.
Prodiscover forensics tool:
Prodiscover forensic tool is one of the effective computer forensic tool that helps the
law enforcement digital forensic professional to investigate the criminal incidence with the
purpose to protect the digital evidence and to develop a report which will help in legal
actions.
While analyzing the feature of the nominated tool it is noticed that the tool helps to
effectively analyze the alleged digital files with the purpose to detect the threat present in the
suspected area. It generally investigates the crimes by analyzing the alleged disks however,
during the investigation it does not harms of impacts the data preset in that disk [2].
Digital Clues:
Digital forensic is popularly known as computer forensic, which is one of the
effective scientific investigatory process that helps to investigate the cyber-crime or a digital
attack. Focusing on the application area of digital forensic it is noticed that the nominated
branch consists of crime investigation, identification, recovery process identification,
validation of the identified strategies as well as determination of digital evidence that has
been identified from the investigation [1].
While elaborating the processes identified in the digital forensic technique it is
noticed that it consists of four primary steps which includes the collection of data,
examination of the collected data, analysis of those data as well as from the analysis reporting
the results gathered from those data.
Followed by a thorough investigation on the effectiveness of digital forensic it is
noticed that this technique helps to determine the criminal as well as the intention of the
criminal.
Prodiscover forensics tool:
Prodiscover forensic tool is one of the effective computer forensic tool that helps the
law enforcement digital forensic professional to investigate the criminal incidence with the
purpose to protect the digital evidence and to develop a report which will help in legal
actions.
While analyzing the feature of the nominated tool it is noticed that the tool helps to
effectively analyze the alleged digital files with the purpose to detect the threat present in the
suspected area. It generally investigates the crimes by analyzing the alleged disks however,
during the investigation it does not harms of impacts the data preset in that disk [2].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3MN624
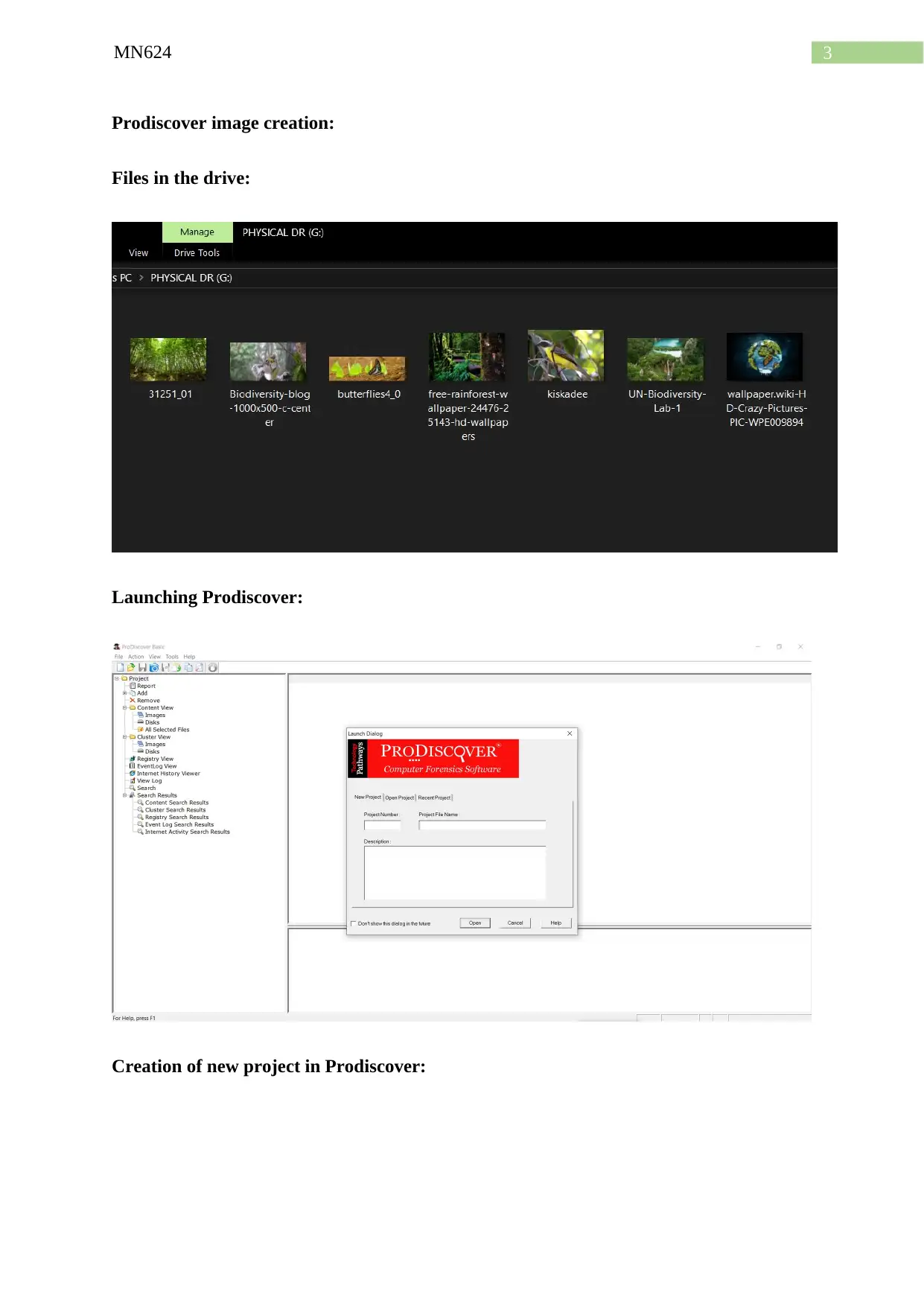
Prodiscover image creation:
Files in the drive:
Launching Prodiscover:
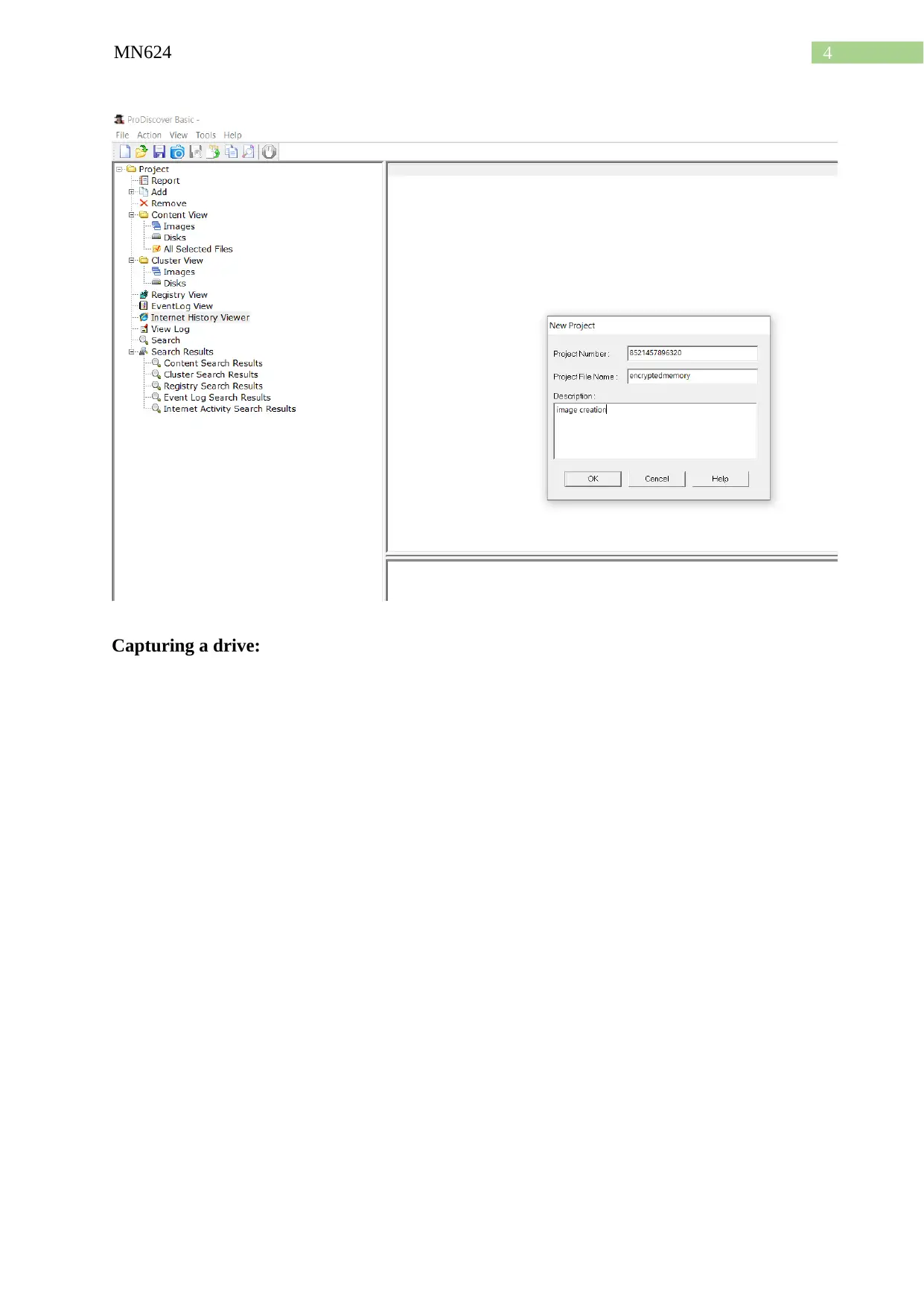
Creation of new project in Prodiscover:
Prodiscover image creation:
Files in the drive:
Launching Prodiscover:
Creation of new project in Prodiscover:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4MN624
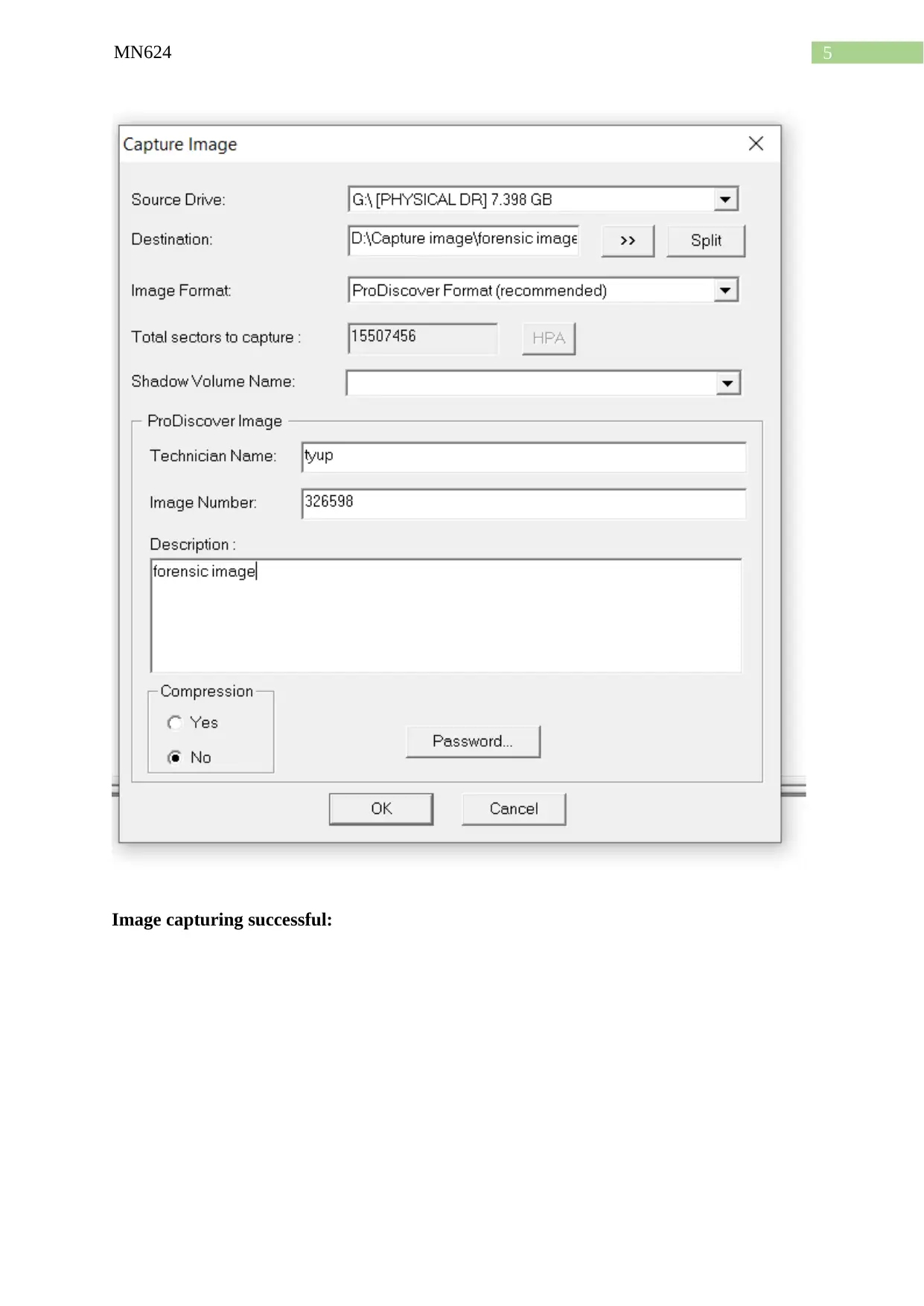
Capturing a drive:
Capturing a drive:
5MN624
Image capturing successful:
Image capturing successful:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6MN624
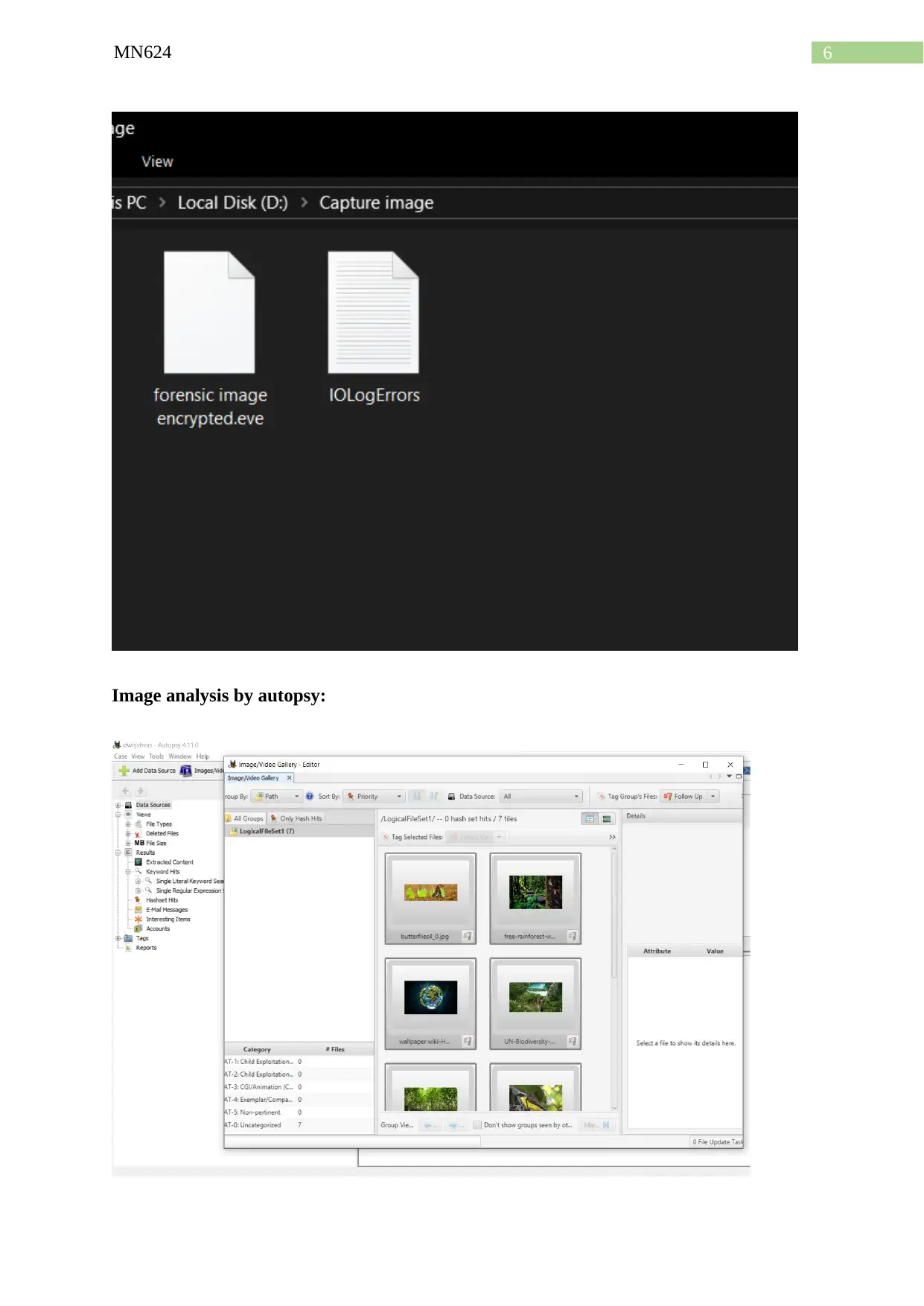
Image analysis by autopsy:
Image analysis by autopsy:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MN624
Data acquisition in digital forensic:
Data acquisition is such technique by which data will be collected from the targeted
area and then those collected data will be analyzed with the purpose to extract some
information about the targeted area. Considering the processes of digital forensic it is noticed
that data acquisition is one of the essential parts of digital forensic as by using this the law
enforcement professionals gathers digital evidence following the departmental guidelines.
Followed by the collection of those data it will analyze those data and then it will proceed for
further procedure.
Now focusing on the importance of data acquisition for the examiner it is noticed that
by using the data acquisition the examiner will be able to gather the digital evidence and from
that collected evidence the investigator will be able to extract the information from the digital
evidence. Along with this the decision of court is also gets influenced by the collected
evidence. Thus, it can be stated that this is one of the most essential part of digital forensic
[3].
Data preservation methods in digital forensic:
Followed by the above discussion it is noticed that in the field of digital forensic there
is a huge significance of effective data preservation method as these process helps to ensure
the legal admissibility during any forensic investigation. Among numerous data preservation
methods hash value, drive imaging and chain of custody are the most effective methods that
will enhance the digital investigation.
Hash Value- this is one of the effective data preservation method by which the investigator
verifies the integrity and the authenticity of the collected image. During the investigation
process the machine generates a cryptographic hash values such as MD5, SHA-1. These
values are very effective while submitting the evidence into court.
Data acquisition in digital forensic:
Data acquisition is such technique by which data will be collected from the targeted
area and then those collected data will be analyzed with the purpose to extract some
information about the targeted area. Considering the processes of digital forensic it is noticed
that data acquisition is one of the essential parts of digital forensic as by using this the law
enforcement professionals gathers digital evidence following the departmental guidelines.
Followed by the collection of those data it will analyze those data and then it will proceed for
further procedure.
Now focusing on the importance of data acquisition for the examiner it is noticed that
by using the data acquisition the examiner will be able to gather the digital evidence and from
that collected evidence the investigator will be able to extract the information from the digital
evidence. Along with this the decision of court is also gets influenced by the collected
evidence. Thus, it can be stated that this is one of the most essential part of digital forensic
[3].
Data preservation methods in digital forensic:
Followed by the above discussion it is noticed that in the field of digital forensic there
is a huge significance of effective data preservation method as these process helps to ensure
the legal admissibility during any forensic investigation. Among numerous data preservation
methods hash value, drive imaging and chain of custody are the most effective methods that
will enhance the digital investigation.
Hash Value- this is one of the effective data preservation method by which the investigator
verifies the integrity and the authenticity of the collected image. During the investigation
process the machine generates a cryptographic hash values such as MD5, SHA-1. These
values are very effective while submitting the evidence into court.

8MN624
Drive Imaging- is also an effective method of data preservation by which the investigator
stores the collected images by creating the duplicates of those digital evidences.
Chain of Custody- is such paper work in which the investigator collects the evidence from
the client and share it when required by documenting all of the transfer detail in the form of
chain of custody [4].
Data acquisition methods:
Considering the fact that in digital forensic there are two categories of data acquisition
present in digital forensic which includes the static acquisition and live acquisition.
Creating a disk to image file data acquisition is one of the most effective data collection
method the enables an investigator to bit to bit copy the digital evidence. The example of this
type of acquisition is Prodiscover which helps to gather the digital evidence.
Creation of sparse copy of a targeted folder is also very effective data acquisition method
in which the investigator targets the digital evidence as well as it enable the investigator to
analyze the deleted data as well.
Drive Imaging- is also an effective method of data preservation by which the investigator
stores the collected images by creating the duplicates of those digital evidences.
Chain of Custody- is such paper work in which the investigator collects the evidence from
the client and share it when required by documenting all of the transfer detail in the form of
chain of custody [4].
Data acquisition methods:
Considering the fact that in digital forensic there are two categories of data acquisition
present in digital forensic which includes the static acquisition and live acquisition.
Creating a disk to image file data acquisition is one of the most effective data collection
method the enables an investigator to bit to bit copy the digital evidence. The example of this
type of acquisition is Prodiscover which helps to gather the digital evidence.
Creation of sparse copy of a targeted folder is also very effective data acquisition method
in which the investigator targets the digital evidence as well as it enable the investigator to
analyze the deleted data as well.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MN624
References:
[1] L. Cameron 2018. Future of digital forensics faces six security challenges in fighting
borderless cybercrime and dark web tools.
[2] S. Watson and A. Dehghantanha 2016. Digital forensics: the missing piece of the Internet
of Things promise. Computer Fraud & Security, 2016(6), pp.5-8.
[3] X. Du, N.A. Le-Khac and M. Scanlon 2017. Evaluation of digital forensic process models
with respect to digital forensics as a service. arXiv preprint arXiv:1708.01730.
[4] T. Wu, F. Breitinger and I. Baggili 2019, August. IoT Ignorance is Digital Forensics
Research Bliss: A Survey to Understand IoT Forensics Definitions, Challenges and Future
Research Directions. In Proceedings of the 14th International Conference on Availability,
Reliability and Security (pp. 1-15).
References:
[1] L. Cameron 2018. Future of digital forensics faces six security challenges in fighting
borderless cybercrime and dark web tools.
[2] S. Watson and A. Dehghantanha 2016. Digital forensics: the missing piece of the Internet
of Things promise. Computer Fraud & Security, 2016(6), pp.5-8.
[3] X. Du, N.A. Le-Khac and M. Scanlon 2017. Evaluation of digital forensic process models
with respect to digital forensics as a service. arXiv preprint arXiv:1708.01730.
[4] T. Wu, F. Breitinger and I. Baggili 2019, August. IoT Ignorance is Digital Forensics
Research Bliss: A Survey to Understand IoT Forensics Definitions, Challenges and Future
Research Directions. In Proceedings of the 14th International Conference on Availability,
Reliability and Security (pp. 1-15).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





