MITS5004 IT Security Assignment 1: Digital Forensic Evaluation Report
VerifiedAdded on 2022/11/28
|10
|557
|325
Presentation
AI Summary
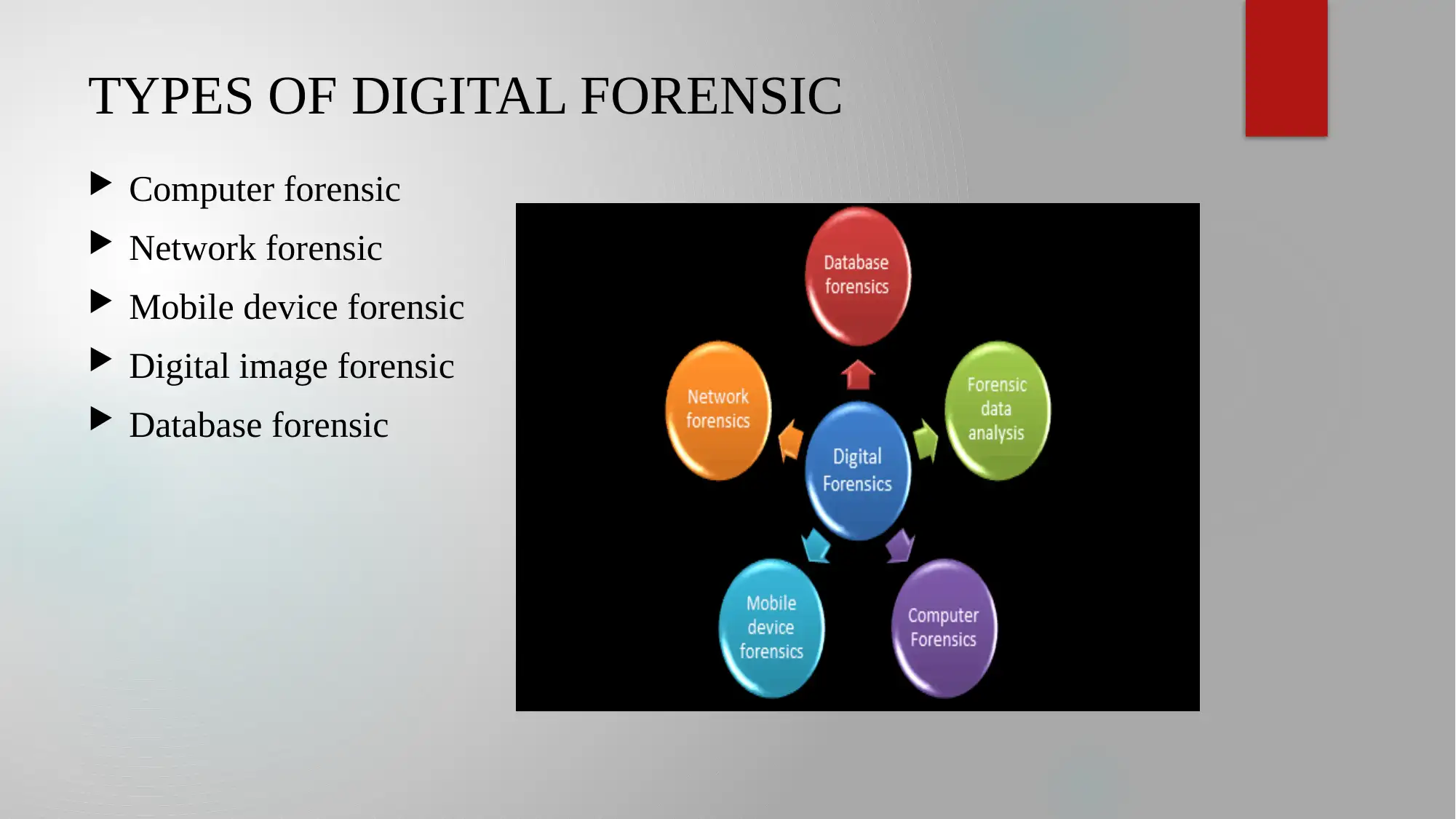
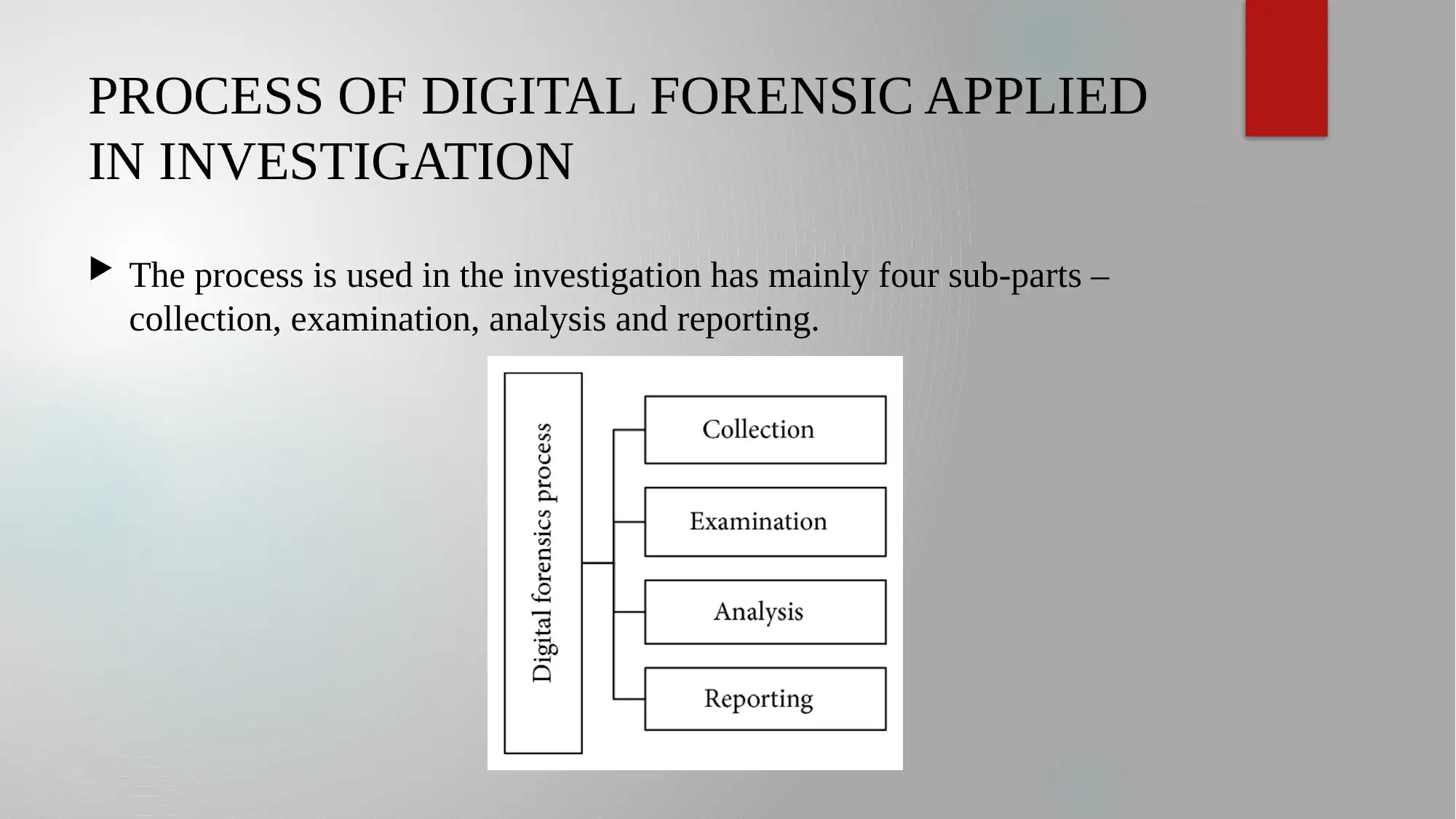
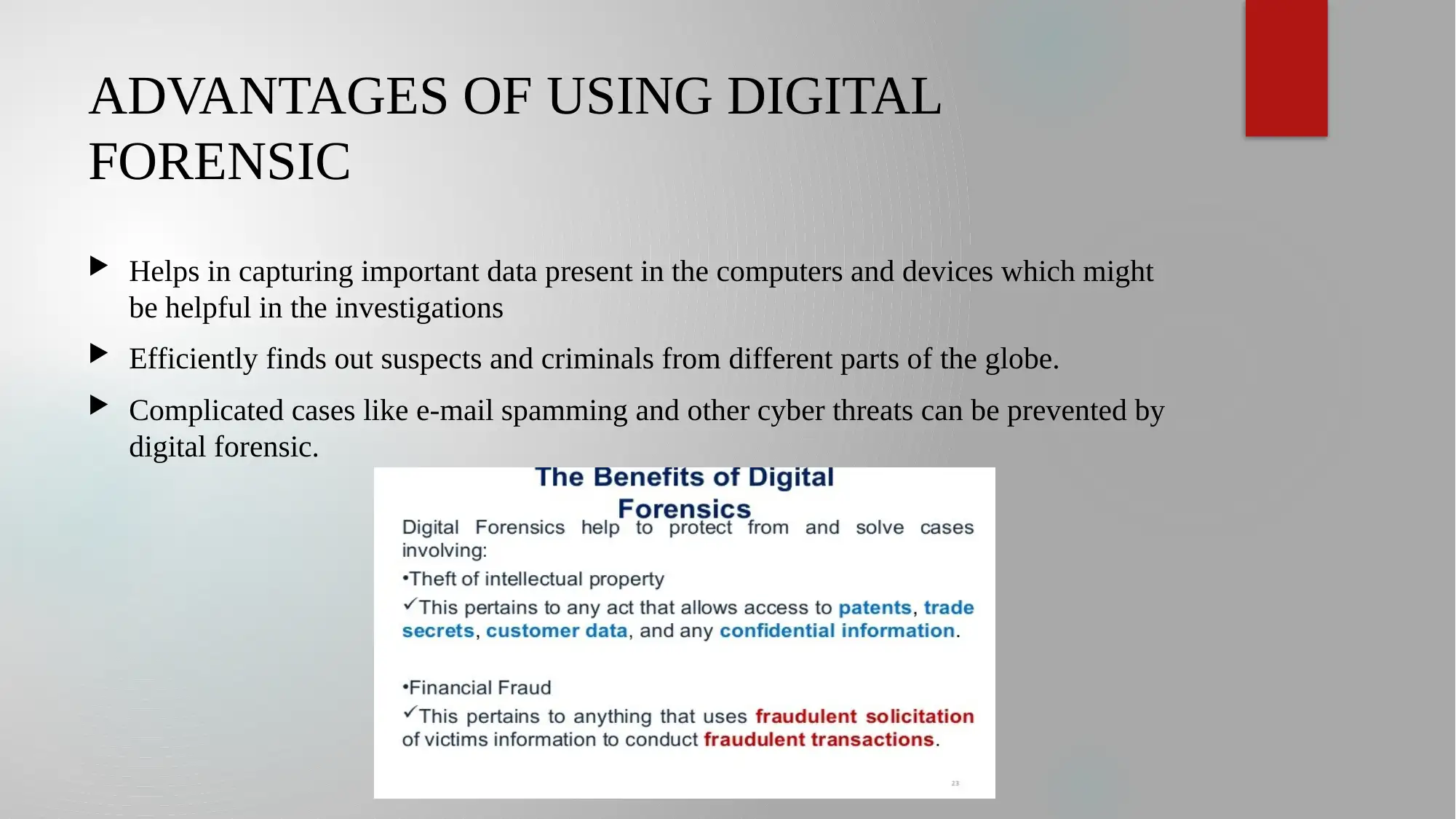
This presentation provides an overview of digital forensic evaluation in modern criminal investigations. It discusses the increasing importance of digital forensics due to technological advancements and its application in legal proceedings. The presentation outlines various types of digital forensics, including computer, network, and mobile device forensics, along with different process models such as the extended model for cybercrime investigation and the systematic digital forensic model. It highlights the four key steps in the investigation process: collection, examination, analysis, and reporting. The advantages of using digital forensics are also explored, such as capturing important data, identifying suspects, and preventing cyber threats. The presentation concludes by emphasizing the need to adapt digital investigation processes to the emergence of new technologies.
1 out of 10














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)