MN624: Digital Forensics Assignment 1A - Data Acquisition & Analysis
VerifiedAdded on 2022/08/30
|11
|1309
|17
Homework Assignment
AI Summary
This document is a student's solution to MN624 Assignment 1A, focusing on digital forensics. The assignment covers key aspects such as the objectives of digital forensics, which includes data recovery, evidence preservation, and identifying culprits. It details the process of creating forensic images from various storage media, including USB drives, and explains different data acquisition methods like disk-to-image and sparse acquisition, emphasizing the importance of volatility and proper tools. The assignment also addresses evidence handling, specifically data preservation through imaging and the use of hash values for integrity validation. Furthermore, it differentiates between live and dead data acquisition methodologies, outlining the procedures and tools involved in each approach. The document provides a comprehensive overview of the digital forensics process, from data acquisition to evidence handling and analysis, making it a valuable resource for students studying digital forensics.

Running head: MN624 ASSIGNMENT 1A
MN624 ASSIGNMENT 1A
Name of the Student
Name of the University
Author Note
MN624 ASSIGNMENT 1A
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN624 ASSIGNMENT 1A 1
Table of Contents
Question 1:.................................................................................................................................2
Question 2:.................................................................................................................................2
Question 3:.................................................................................................................................3
Question 4:.................................................................................................................................4
References:.................................................................................................................................5
Table of Contents
Question 1:.................................................................................................................................2
Question 2:.................................................................................................................................2
Question 3:.................................................................................................................................3
Question 4:.................................................................................................................................4
References:.................................................................................................................................5

2MN624 ASSIGNMENT 1A
Question 1:
Digital forensics is the procedure of uncovering and then interpreting electronic data. The
main aim of the procedure is to preserve any kind of evidence in its original form while
executing an investigation that is structured by collection, identification, and validation of
digital information for the objective of reconstruction of the past events [1]. The important
objectives of using digital forensics are as follows:
It assists in order to recover, evaluate and then preserve the computer and associated
materials in a manner such that it assists the agency of investigation in order to present
them as evidence in the court of law [2].
It assists in order to postulate the motive that is behind the crime and then recognise the
main culprit.
Helps to recognise the evidences quickly and permits the investigator to estimate the
potential effect of the activity that is malicious and then validate them.
Developing a report of computer forensic, that provides a whole report on the procedure
of investigation.
Evidence image creation:
USB drive:
Question 1:
Digital forensics is the procedure of uncovering and then interpreting electronic data. The
main aim of the procedure is to preserve any kind of evidence in its original form while
executing an investigation that is structured by collection, identification, and validation of
digital information for the objective of reconstruction of the past events [1]. The important
objectives of using digital forensics are as follows:
It assists in order to recover, evaluate and then preserve the computer and associated
materials in a manner such that it assists the agency of investigation in order to present
them as evidence in the court of law [2].
It assists in order to postulate the motive that is behind the crime and then recognise the
main culprit.
Helps to recognise the evidences quickly and permits the investigator to estimate the
potential effect of the activity that is malicious and then validate them.
Developing a report of computer forensic, that provides a whole report on the procedure
of investigation.
Evidence image creation:
USB drive:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3MN624 ASSIGNMENT 1A
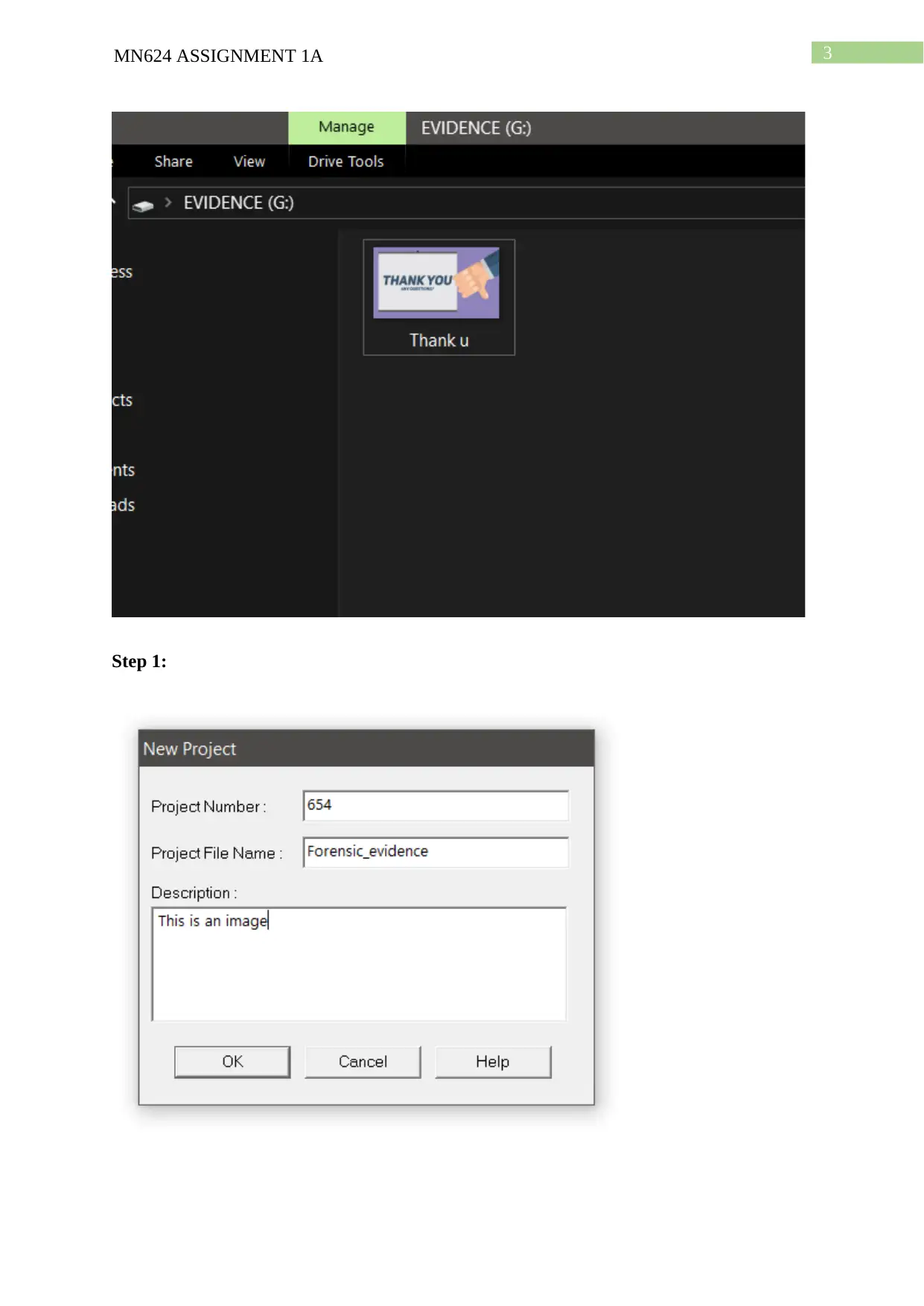
Step 1:
Step 1:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4MN624 ASSIGNMENT 1A
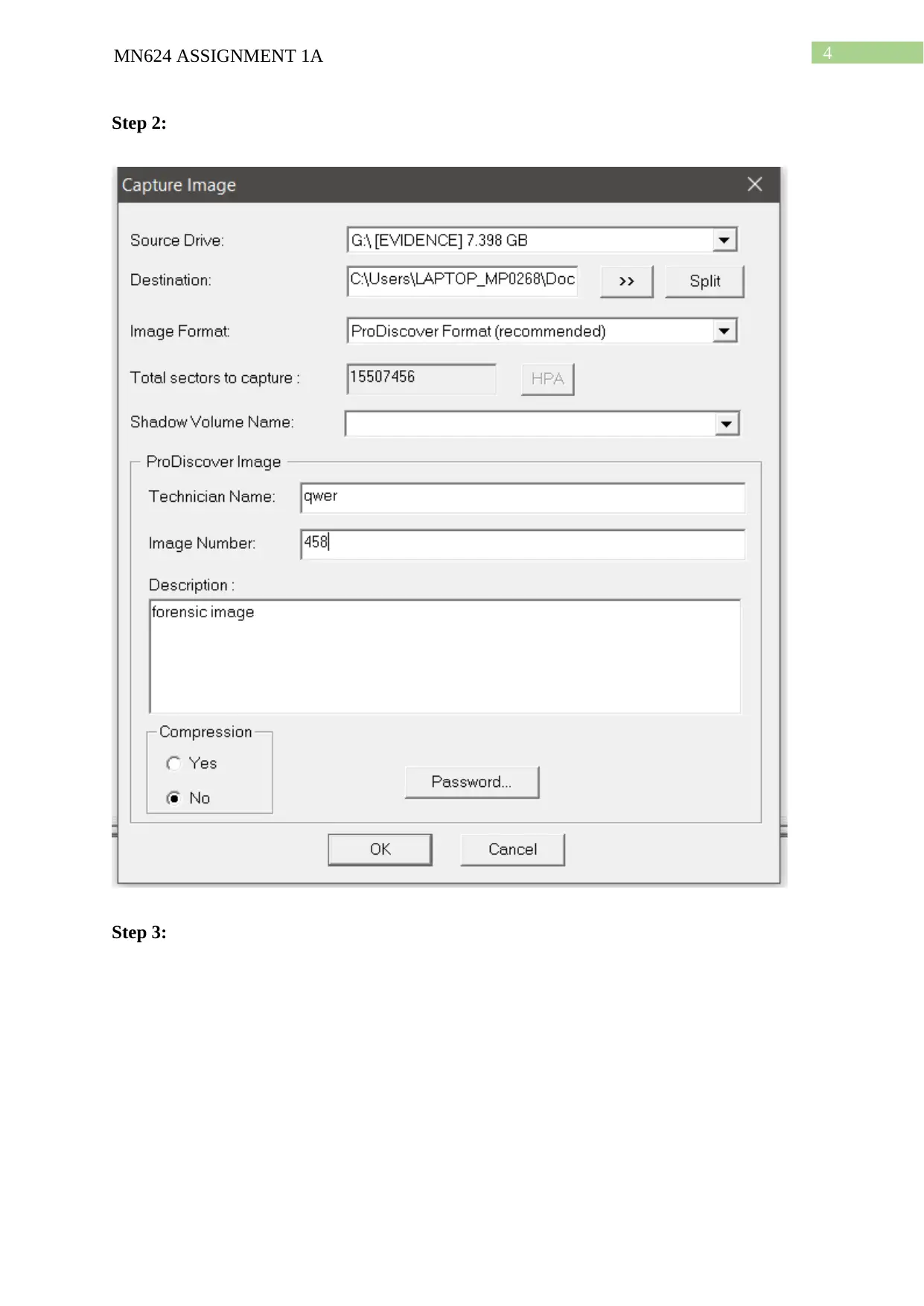
Step 2:
Step 3:
Step 2:
Step 3:
5MN624 ASSIGNMENT 1A
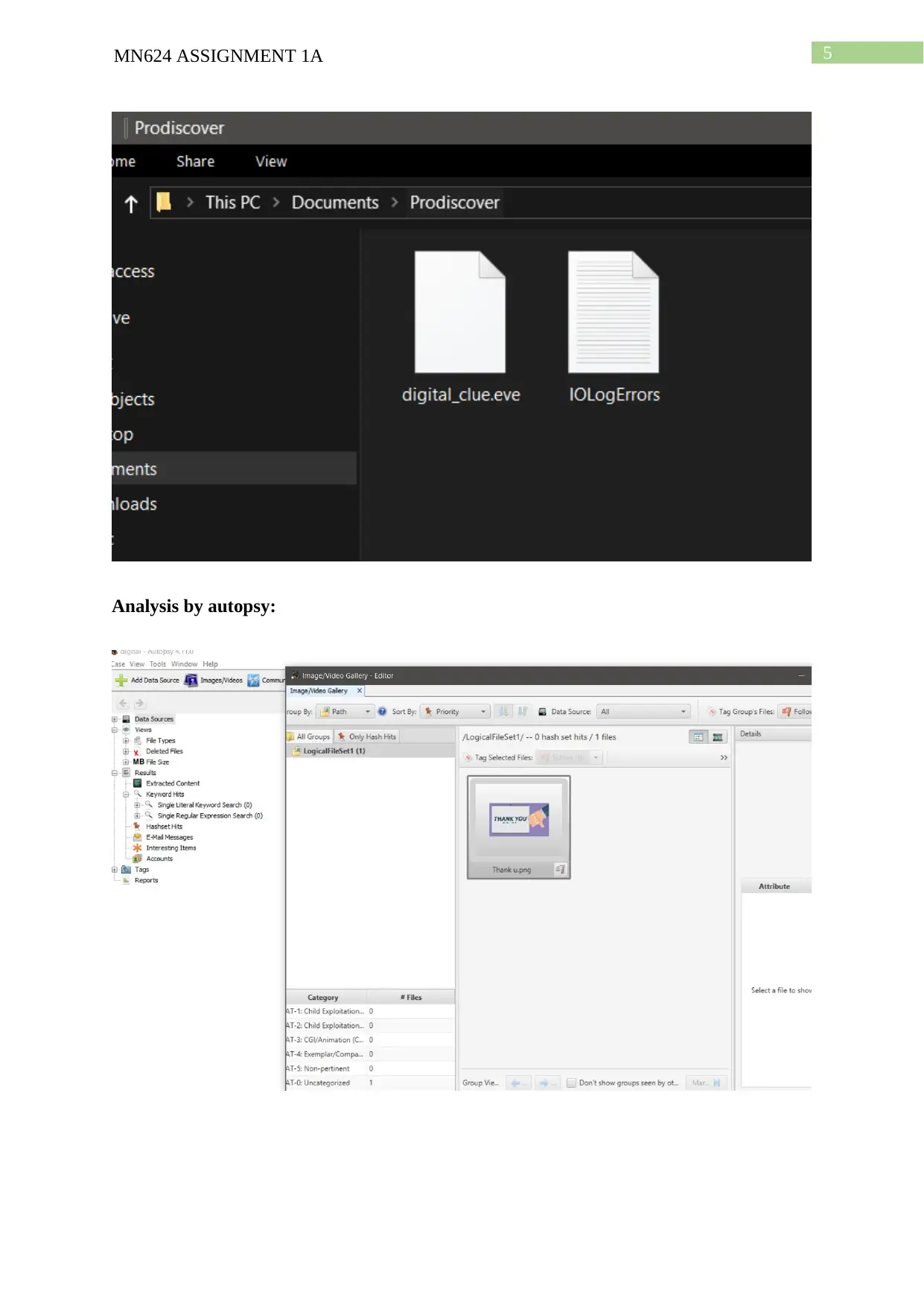
Analysis by autopsy:
Analysis by autopsy:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MN624 ASSIGNMENT 1A
Question 2:
The acquisition of data is the procedure of making an image of forensic from the
computer media such as thumb drive, hard drive, servers and many more that stores the
digital data consisting of consoles of gaming and various devices. The image of forensics is
made utilising the hardware those are specialized that prevents any type of data from being
written to the media of source so that it remains perfect [3]. The image of forensic and not the
original media is utilised by the examiner of forensic in order to carry out the evaluation.
There are four methods of acquiring data: disk too image file, disk to disk copy, sparse copy
of data of folder or file and logical disk to disk file. The acquisition that is sparse is useful in
conditions where there are large amount of data to be acquired from large drives. While
collecting the evidence those are digital, the investigators must comply with the role of
volatility that refers to the sequence in which the evidence that is digital is collected. The
order should be maintained from data of high volatile to low volatile [4]. Proper tools must be
utilised for the purposes of acquisition of data and always execute acquisition test on the test
drive rather than on the drives those are suspected. The acquisition of data should be
validated with tools those are built in such as the hexadecimal editor with MD5 and SHA-1
functions of hashing.
Question 3:
Handling the evidence is one of the essential parts of digital forensics. Nothing should
be done that can modify the evidences those are digital. This is called preservation of data
that is the protection and the isolation of the evidences those are digital as found without any
modification so that it can be examined later [5].
Imaging of drive: before the investigators start to examine the evidence from source, they
need to image the evidences first. Imaging a drive the procedure of forensic in which an
Question 2:
The acquisition of data is the procedure of making an image of forensic from the
computer media such as thumb drive, hard drive, servers and many more that stores the
digital data consisting of consoles of gaming and various devices. The image of forensics is
made utilising the hardware those are specialized that prevents any type of data from being
written to the media of source so that it remains perfect [3]. The image of forensic and not the
original media is utilised by the examiner of forensic in order to carry out the evaluation.
There are four methods of acquiring data: disk too image file, disk to disk copy, sparse copy
of data of folder or file and logical disk to disk file. The acquisition that is sparse is useful in
conditions where there are large amount of data to be acquired from large drives. While
collecting the evidence those are digital, the investigators must comply with the role of
volatility that refers to the sequence in which the evidence that is digital is collected. The
order should be maintained from data of high volatile to low volatile [4]. Proper tools must be
utilised for the purposes of acquisition of data and always execute acquisition test on the test
drive rather than on the drives those are suspected. The acquisition of data should be
validated with tools those are built in such as the hexadecimal editor with MD5 and SHA-1
functions of hashing.
Question 3:
Handling the evidence is one of the essential parts of digital forensics. Nothing should
be done that can modify the evidences those are digital. This is called preservation of data
that is the protection and the isolation of the evidences those are digital as found without any
modification so that it can be examined later [5].
Imaging of drive: before the investigators start to examine the evidence from source, they
need to image the evidences first. Imaging a drive the procedure of forensic in which an
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MN624 ASSIGNMENT 1A
examiner develops a duplicate of the drive. This image of forensic of all the digital media
assists retains evidence for the forensic investigation [6]. When examining the image,
examiners should keep in mind that even the damaged drives could retain essential data those
are recoverable in order to recognise and then catalogue. In the best cases, the examiners can
recover the files those are deleted utilising techniques of forensics.
Hash values: When an examiner images a machine for analysis, the procedure generates hash
values of cryptography. The main aim of the hash value is to validate the integrity and
authenticity of the image as a correct duplicate of the media that is original. The hash values
are important when the providing the evidence to the court as modifying even the smallest
data bit will produce a new value of hash
Question 4:
In digital forensics, the important and the first step are to make a precise copy of the data on
the hard drive. The acquisition of data is developing a copy of the evidence of media that are
digital, either on site where the device is present or if the devices of forensics can be taken to
a location that is secured
There are two types of methodology of acquisition of data that includes:
Live acquisition
Dead acquisition
Live acquisition: there are two ways by which live acquisition of data can be carried out:
utilising bootable CD and DD command. For better investigation and research, the creators
have developed many tools of digital forensics. In live acquisition of data, data is retrieved
from a device that is digital directly through its interface [7]. For example, switching on the
computer and then executing the programs from the operating systems of the computer
examiner develops a duplicate of the drive. This image of forensic of all the digital media
assists retains evidence for the forensic investigation [6]. When examining the image,
examiners should keep in mind that even the damaged drives could retain essential data those
are recoverable in order to recognise and then catalogue. In the best cases, the examiners can
recover the files those are deleted utilising techniques of forensics.
Hash values: When an examiner images a machine for analysis, the procedure generates hash
values of cryptography. The main aim of the hash value is to validate the integrity and
authenticity of the image as a correct duplicate of the media that is original. The hash values
are important when the providing the evidence to the court as modifying even the smallest
data bit will produce a new value of hash
Question 4:
In digital forensics, the important and the first step are to make a precise copy of the data on
the hard drive. The acquisition of data is developing a copy of the evidence of media that are
digital, either on site where the device is present or if the devices of forensics can be taken to
a location that is secured
There are two types of methodology of acquisition of data that includes:
Live acquisition
Dead acquisition
Live acquisition: there are two ways by which live acquisition of data can be carried out:
utilising bootable CD and DD command. For better investigation and research, the creators
have developed many tools of digital forensics. In live acquisition of data, data is retrieved
from a device that is digital directly through its interface [7]. For example, switching on the
computer and then executing the programs from the operating systems of the computer

8MN624 ASSIGNMENT 1A
Dead acquisition: the acquisition that is offline or dead can generate some information and
the examiners cannot recover any information [8]. To develop an image of forensic of a
whole disk, the procedure of imaging should not modify any data on the disk and that all the
including unallocated and the metadata should be included in them.
Dead acquisition: the acquisition that is offline or dead can generate some information and
the examiners cannot recover any information [8]. To develop an image of forensic of a
whole disk, the procedure of imaging should not modify any data on the disk and that all the
including unallocated and the metadata should be included in them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MN624 ASSIGNMENT 1A
References:
[1]E. Casey, "Maturation of digital forensics", Digital Investigation, vol. 29, pp. A1-A2,
2019. Available: 10.1016/j.diin.2019.05.002.
[2]N. Hildayanti, "Forensics Analysis of Router On Computer Networks Using Live
Forensics Method", International Journal of Cyber-Security and Digital Forensics, vol. 8,
no. 1, pp. 74-81, 2019. Available: 10.17781/p002559.
[3]J. Stüttgen, S. Vömel and M. Denzel, "Acquisition and analysis of compromised firmware
using memory forensics", Digital Investigation, vol. 12, pp. S50-S60, 2015. Available:
10.1016/j.diin.2015.01.010.
[4]E. Akbal and S. Dogan, "Forensics Image Acquisition Process of Digital
Evidence", International Journal of Computer Network and Information Security, vol. 10, no.
5, pp. 1-8, 2018. Available: 10.5815/ijcnis.2018.05.01.
[5]J. Kong, "Data Extraction on MTK-based Android Mobile Phone Forensics", Journal of
Digital Forensics, Security and Law, 2015. Available: 10.15394/jdfsl.2015.1209.
[6]P. Lokhande and B. Meshram, "Digital Forensics Analysis for Data Theft", The
International Journal of Forensic Computer Science, vol. 10, no. 1, pp. 29-51, 2015.
Available: 10.5769/j201501004.
[7]I. Homem and S. Dosis, "On the Network Performance of Digital Evidence Acquisition of
Small Scale Devices over Public Networks", Journal of Digital Forensics, Security and Law,
2015. Available: 10.15394/jdfsl.2015.1205.
[8]E. Casey, "Maturation of digital forensics", Digital Investigation, vol. 29, pp. A1-A2,
2019. Available: 10.1016/j.diin.2019.05.002.
References:
[1]E. Casey, "Maturation of digital forensics", Digital Investigation, vol. 29, pp. A1-A2,
2019. Available: 10.1016/j.diin.2019.05.002.
[2]N. Hildayanti, "Forensics Analysis of Router On Computer Networks Using Live
Forensics Method", International Journal of Cyber-Security and Digital Forensics, vol. 8,
no. 1, pp. 74-81, 2019. Available: 10.17781/p002559.
[3]J. Stüttgen, S. Vömel and M. Denzel, "Acquisition and analysis of compromised firmware
using memory forensics", Digital Investigation, vol. 12, pp. S50-S60, 2015. Available:
10.1016/j.diin.2015.01.010.
[4]E. Akbal and S. Dogan, "Forensics Image Acquisition Process of Digital
Evidence", International Journal of Computer Network and Information Security, vol. 10, no.
5, pp. 1-8, 2018. Available: 10.5815/ijcnis.2018.05.01.
[5]J. Kong, "Data Extraction on MTK-based Android Mobile Phone Forensics", Journal of
Digital Forensics, Security and Law, 2015. Available: 10.15394/jdfsl.2015.1209.
[6]P. Lokhande and B. Meshram, "Digital Forensics Analysis for Data Theft", The
International Journal of Forensic Computer Science, vol. 10, no. 1, pp. 29-51, 2015.
Available: 10.5769/j201501004.
[7]I. Homem and S. Dosis, "On the Network Performance of Digital Evidence Acquisition of
Small Scale Devices over Public Networks", Journal of Digital Forensics, Security and Law,
2015. Available: 10.15394/jdfsl.2015.1205.
[8]E. Casey, "Maturation of digital forensics", Digital Investigation, vol. 29, pp. A1-A2,
2019. Available: 10.1016/j.diin.2019.05.002.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10MN624 ASSIGNMENT 1A
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





