Digital Forensics Report: Analyzing Clown Content - Western Australia
VerifiedAdded on 2023/06/03
|47
|6608
|329
Case Study
AI Summary
This document presents a computer forensics case study involving the alleged access of illegal clown-related content in Western Australia. The investigation focuses on a suspect named Clark, whose computer was seized and forensically imaged. The report details the analysis of the forensic image using tools like Autopsy, highlighting the identification of numerous clown-related images, videos, and documents. Metadata from these files, including creation and access times, are scrutinized to establish a timeline of events and potentially link Clark to the content. The investigation also explores web bookmarks, cookies, and download history to further assess the suspect's online activity related to clowns. The report aims to determine the extent of Clark's involvement in accessing or possessing the prohibited content.

Computer Forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.......................................................................................................................................2
2. Resources............................................................................................................................................2
3. Progress..............................................................................................................................................2
3.1 Issue-1 Presentation of contents.........................................................................................................2
3.2 Identification of ownership.........................................................................................................28
3.3 Intention of Crime.......................................................................................................................30
3.4 File Quantity................................................................................................................................30
3.5 Software installed........................................................................................................................31
4. Conclusion........................................................................................................................................33
5. References........................................................................................................................................34
Appendix I –Running Sheet....................................................................................................................38
Appendix II –Timeline of Events............................................................................................................42
Page 1 of 47
1. Introduction.......................................................................................................................................2
2. Resources............................................................................................................................................2
3. Progress..............................................................................................................................................2
3.1 Issue-1 Presentation of contents.........................................................................................................2
3.2 Identification of ownership.........................................................................................................28
3.3 Intention of Crime.......................................................................................................................30
3.4 File Quantity................................................................................................................................30
3.5 Software installed........................................................................................................................31
4. Conclusion........................................................................................................................................33
5. References........................................................................................................................................34
Appendix I –Running Sheet....................................................................................................................38
Appendix II –Timeline of Events............................................................................................................42
Page 1 of 47

1. Introduction
The offence is take place in a work place at Western Australia. The Clark who works at
there is involved in that offence. The other Clark may be involved in that offence. The Clark’s
statement is that he did not always take the computer home or locked it when he is away from his
desk ("Operating System Forensics | National Initiative for Cybersecurity Careers and Studies",
2018). The liability of the suspects or victims may cause delay in the investigation. The offence
of accessing or owning clown content will be investigated. In the investigation, Clark is a main
suspect. The computer related to the investigation is seized and that belongs to Clark. The hard
drive of the computer is wiped away ("Hacking & Digital Forensics & Autopsy - Stay lunix",
2018). But the forensic image is obtained. In the forensic image, the clown related contents will
be searched ("FTK Imager: Lesson 4: Mount Image File, Recover Deleted File", 2018). The
investigation will be completed by October 2018 (Zhao, Zong & Wu, 2014). The investigation
will start in first week of October 2018. The factors which may affect the completion time of
analysis are installation of appropriate tools, technical issues etc. ("FTK Imager and Custom
Content Images", 2018).
2. Resources
The forensic tools and a computer is the resources needed for this entire investigation.
And also the investigators, suspects are also included. The forensic tools are the important thing
in the investigation ("FTK Imager: Lesson 1: Install FTK Imager", 2018) (Pattnaik & Jana,
2005).
FTK Imager ("FTK Imager 3.2.0", 2018)
Autopsy
OS Forensics
Page 2 of 47
The offence is take place in a work place at Western Australia. The Clark who works at
there is involved in that offence. The other Clark may be involved in that offence. The Clark’s
statement is that he did not always take the computer home or locked it when he is away from his
desk ("Operating System Forensics | National Initiative for Cybersecurity Careers and Studies",
2018). The liability of the suspects or victims may cause delay in the investigation. The offence
of accessing or owning clown content will be investigated. In the investigation, Clark is a main
suspect. The computer related to the investigation is seized and that belongs to Clark. The hard
drive of the computer is wiped away ("Hacking & Digital Forensics & Autopsy - Stay lunix",
2018). But the forensic image is obtained. In the forensic image, the clown related contents will
be searched ("FTK Imager: Lesson 4: Mount Image File, Recover Deleted File", 2018). The
investigation will be completed by October 2018 (Zhao, Zong & Wu, 2014). The investigation
will start in first week of October 2018. The factors which may affect the completion time of
analysis are installation of appropriate tools, technical issues etc. ("FTK Imager and Custom
Content Images", 2018).
2. Resources
The forensic tools and a computer is the resources needed for this entire investigation.
And also the investigators, suspects are also included. The forensic tools are the important thing
in the investigation ("FTK Imager: Lesson 1: Install FTK Imager", 2018) (Pattnaik & Jana,
2005).
FTK Imager ("FTK Imager 3.2.0", 2018)
Autopsy
OS Forensics
Page 2 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
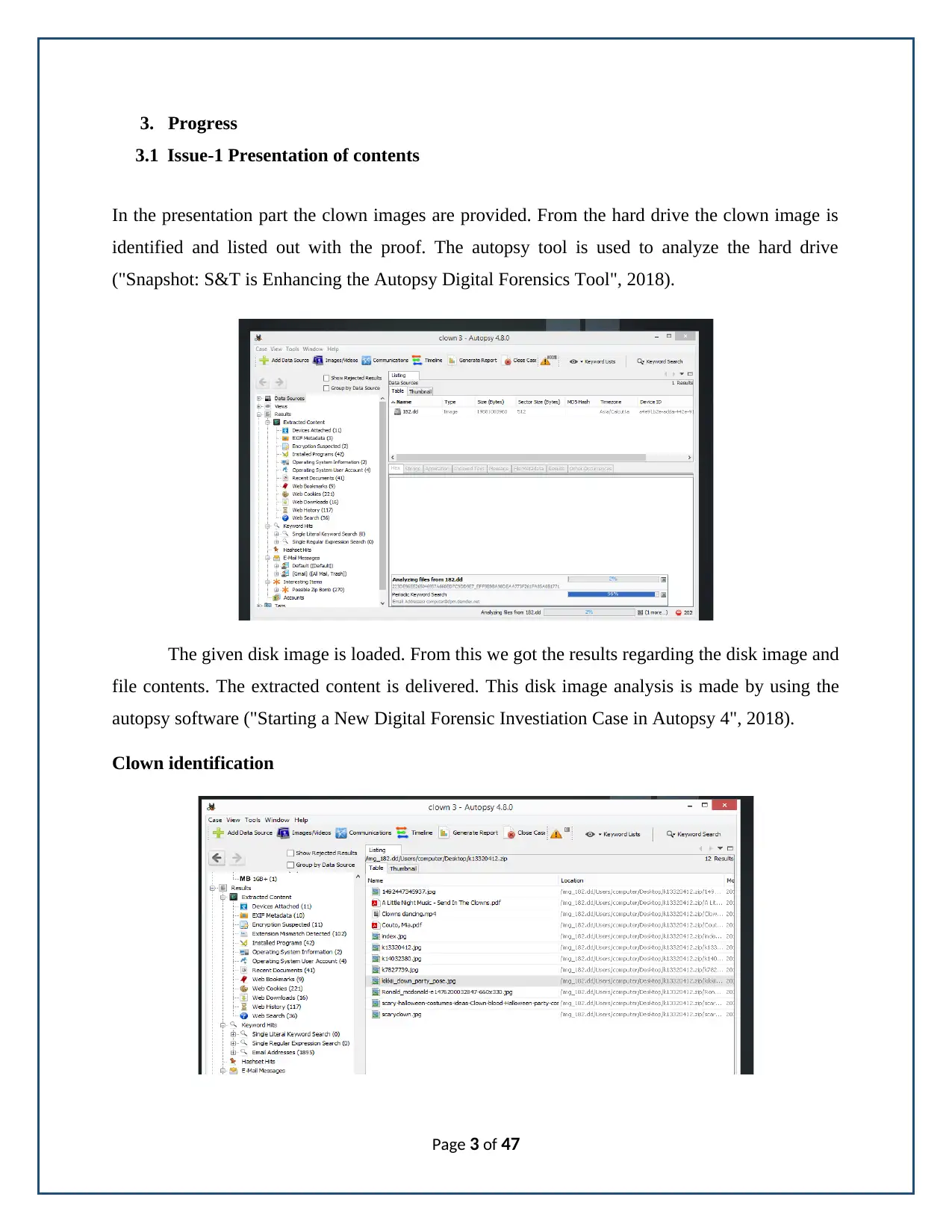
3. Progress
3.1 Issue-1 Presentation of contents
In the presentation part the clown images are provided. From the hard drive the clown image is
identified and listed out with the proof. The autopsy tool is used to analyze the hard drive
("Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool", 2018).
The given disk image is loaded. From this we got the results regarding the disk image and
file contents. The extracted content is delivered. This disk image analysis is made by using the
autopsy software ("Starting a New Digital Forensic Investiation Case in Autopsy 4", 2018).
Clown identification
Page 3 of 47
3.1 Issue-1 Presentation of contents
In the presentation part the clown images are provided. From the hard drive the clown image is
identified and listed out with the proof. The autopsy tool is used to analyze the hard drive
("Snapshot: S&T is Enhancing the Autopsy Digital Forensics Tool", 2018).
The given disk image is loaded. From this we got the results regarding the disk image and
file contents. The extracted content is delivered. This disk image analysis is made by using the
autopsy software ("Starting a New Digital Forensic Investiation Case in Autopsy 4", 2018).
Clown identification
Page 3 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The desktop contents are analyzed. From the analysis we have found the clown images,
and the videos regarding the clown. The clown pdf such as a little night music is retrieved. Also
there are many images retrieved from the analysis regarding clown. The Clark downloaded the
clown images and stored in the computer desktop (Bell, 2018).
Clown image 1
Name /img_182.dd/Users/computer/Pictures/kikkii_clown_party_pose.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:05 AEST
Modified 2018-06-19 05:20:06 AEST
Size 50304
Accessed 2018-06-19 05:20:06 AEST
MD5 76e4975e5efc2a1268584fef7ade5f59
Internal ID 51651
Page 4 of 47
and the videos regarding the clown. The clown pdf such as a little night music is retrieved. Also
there are many images retrieved from the analysis regarding clown. The Clark downloaded the
clown images and stored in the computer desktop (Bell, 2018).
Clown image 1
Name /img_182.dd/Users/computer/Pictures/kikkii_clown_party_pose.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:05 AEST
Modified 2018-06-19 05:20:06 AEST
Size 50304
Accessed 2018-06-19 05:20:06 AEST
MD5 76e4975e5efc2a1268584fef7ade5f59
Internal ID 51651
Page 4 of 47

The clown image is identified. The name is ‘kikkii_clown_party_pose’. This clown
image is downloaded and stored in the pictures folder by the suspect. At the same time he made
the email to someone regarding the clown content. The device model is Canon EOS IOD. This
picture is taken by the device Canon. It is presented in the EXIF Meta data. From the file Meta
data we can able to find the creation time of the file. Based on this time the investigator required
to identify any suspicious activity during the same time (Galvao, 2006) (Imager & AccessData
Group, 2018).
Clown image 2
Name /img_182.dd/Users/computer/Desktop/k7827739.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:52:14 AEST
Modified 2018-07-02 06:52:15 AEST
Size 41284
Accessed 2018-07-02 06:52:14 AEST
MD5 39db918c4014d3a64fabbc17a2fe49a7
Internal ID 51461
From the Clark’s Laptop hard disk image file there are number of pictures and some
other files are founded (mannaza, 2018). Among the various pictures and videos some of them
Page 5 of 47
image is downloaded and stored in the pictures folder by the suspect. At the same time he made
the email to someone regarding the clown content. The device model is Canon EOS IOD. This
picture is taken by the device Canon. It is presented in the EXIF Meta data. From the file Meta
data we can able to find the creation time of the file. Based on this time the investigator required
to identify any suspicious activity during the same time (Galvao, 2006) (Imager & AccessData
Group, 2018).
Clown image 2
Name /img_182.dd/Users/computer/Desktop/k7827739.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:52:14 AEST
Modified 2018-07-02 06:52:15 AEST
Size 41284
Accessed 2018-07-02 06:52:14 AEST
MD5 39db918c4014d3a64fabbc17a2fe49a7
Internal ID 51461
From the Clark’s Laptop hard disk image file there are number of pictures and some
other files are founded (mannaza, 2018). Among the various pictures and videos some of them
Page 5 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

are related to the clown. The above illustrated picture is one of the clown picture retrieved from
the Clark’s laptop image file. The name of the file is “K7827739” and the file is founded on the
desktop. This picture file is a .jpeg format. And the files internal ID is 51461. In the above shown
table contains the various information about the file. The table contains the file meta details like
file type, MIME type, and file created time and modified time etc. these details are highly
helpful for find the person who download those files (Morrison & Petrisor, 2004). It also
provides the access log details. Here the access log is a set of information. The picture is
downloaded on (2018-07-02 06:52:14 AEST). So the investigator required to check whether
there is any noticeable actions are done by the suspect on the particular time period. From that
we may know about the person who created this file on Clark’s system.
Clown image 3
Name /img_182.dd/Users/computer/Desktop/k14032380.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:51:52 AEST
Modified 2018-07-02 06:51:52 AEST
Size 31837
Accessed 2018-07-02 06:51:52 AEST
MD5 913cb94539abfe8de858ce16c0a40e99
Page 6 of 47
the Clark’s laptop image file. The name of the file is “K7827739” and the file is founded on the
desktop. This picture file is a .jpeg format. And the files internal ID is 51461. In the above shown
table contains the various information about the file. The table contains the file meta details like
file type, MIME type, and file created time and modified time etc. these details are highly
helpful for find the person who download those files (Morrison & Petrisor, 2004). It also
provides the access log details. Here the access log is a set of information. The picture is
downloaded on (2018-07-02 06:52:14 AEST). So the investigator required to check whether
there is any noticeable actions are done by the suspect on the particular time period. From that
we may know about the person who created this file on Clark’s system.
Clown image 3
Name /img_182.dd/Users/computer/Desktop/k14032380.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:51:52 AEST
Modified 2018-07-02 06:51:52 AEST
Size 31837
Accessed 2018-07-02 06:51:52 AEST
MD5 913cb94539abfe8de858ce16c0a40e99
Page 6 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internal ID 51458
Also another clown’s picture founded from the Clark’s Laptop image hard disk image
file. And the file name is k14032380. Similar to the previous picture it is also related to the
clown (Mudge, 2007). So this picture is also considered as the evidence for containing the
suspicious data in the Laptop. This picture clearly shows that suspect’s laptop contains the data
about the clown. Here also the created time, modified time as well as accessed time for the files
are founded form the file meta data. This particular picture file is created on 2018-07-02
06:51:52 AEST. Here also the investigator required to check any evidences regarding to the
suspects access during this time on other processes like sending mails, opening mails etc. From
the file Meta data also the various information like MIME type, size of the file etc are founded
and those information are tabulated.
Clown image 4
Name /img_182.dd/Users/computer/Desktop/k13320412.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:45:08 AEST
Modified 2018-07-02 06:45:08 AEST
Page 7 of 47
Also another clown’s picture founded from the Clark’s Laptop image hard disk image
file. And the file name is k14032380. Similar to the previous picture it is also related to the
clown (Mudge, 2007). So this picture is also considered as the evidence for containing the
suspicious data in the Laptop. This picture clearly shows that suspect’s laptop contains the data
about the clown. Here also the created time, modified time as well as accessed time for the files
are founded form the file meta data. This particular picture file is created on 2018-07-02
06:51:52 AEST. Here also the investigator required to check any evidences regarding to the
suspects access during this time on other processes like sending mails, opening mails etc. From
the file Meta data also the various information like MIME type, size of the file etc are founded
and those information are tabulated.
Clown image 4
Name /img_182.dd/Users/computer/Desktop/k13320412.jpg
Type File System
MIME Type image/jpeg
Created 2018-07-02 06:45:08 AEST
Modified 2018-07-02 06:45:08 AEST
Page 7 of 47

Size 35546
Accessed 2018-07-02 06:45:08 AEST
MD5 e5ab36f6264d22714a88d53338469f95
Internal ID 51453
The clown image of “k13320412.jpg” is obtained from the analysis. It is retrieved from
the user desktop files. As similar to the above three images it is also related to clown. So this file
also considered as an evidence against suspect. As similar to other three pictures this file
also .jpeg format image file. It is created on 2018-07-02 06:45:08 AEST in suspect’s laptop. Also
the time of creation as well as time of modification are founded from the file Meta data. So the
investigator required to search about any noticeable actions on the above mentioned time. If any
actions are carried out by the suspect on the above mentioned time helps to prove that the suspect
having the system when the suspicious files creation.
Clown image 5
Name /img_182.dd/Users/computer/Pictures/scary-halloween-costumes-
ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:51:54 AEST
Modified 2018-06-18 05:51:55 AEST
Size 59178
Accessed 2018-06-18 05:51:54 AEST
Page 8 of 47
Accessed 2018-07-02 06:45:08 AEST
MD5 e5ab36f6264d22714a88d53338469f95
Internal ID 51453
The clown image of “k13320412.jpg” is obtained from the analysis. It is retrieved from
the user desktop files. As similar to the above three images it is also related to clown. So this file
also considered as an evidence against suspect. As similar to other three pictures this file
also .jpeg format image file. It is created on 2018-07-02 06:45:08 AEST in suspect’s laptop. Also
the time of creation as well as time of modification are founded from the file Meta data. So the
investigator required to search about any noticeable actions on the above mentioned time. If any
actions are carried out by the suspect on the above mentioned time helps to prove that the suspect
having the system when the suspicious files creation.
Clown image 5
Name /img_182.dd/Users/computer/Pictures/scary-halloween-costumes-
ideas-Clown-blood-Halloween-party-costumes-e1410943909179.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:51:54 AEST
Modified 2018-06-18 05:51:55 AEST
Size 59178
Accessed 2018-06-18 05:51:54 AEST
Page 8 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MD5 51632444d9845cc6686adcf24e536f77
Internal ID 51664
The clown image is identified from the disk analysis. This image is presented in the
computer desktop. The suspect clerk only downloaded this image. History is presented in the
web bookmarks. This picture also related to clown. So it is also considered as the evidence for
the suspicious activity. Form the conducted DF analysis the Meta data of the file retrieved. From
the file Meta data we can able to identify the information like creation time etc. (Ochiai,
Yamakawa, Fukushima, Yamada & Hayashi, 2000).
Clown image 6
Name /img_182.dd/Users/computer/Pictures/s-l640.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:17 AEST
Modified 2018-06-19 05:20:17 AEST
Size 57620
Accessed 2018-06-19 05:20:17 AEST
MD5 dd42fe966af825567338e4f873cc2f6a
Page 9 of 47
Internal ID 51664
The clown image is identified from the disk analysis. This image is presented in the
computer desktop. The suspect clerk only downloaded this image. History is presented in the
web bookmarks. This picture also related to clown. So it is also considered as the evidence for
the suspicious activity. Form the conducted DF analysis the Meta data of the file retrieved. From
the file Meta data we can able to identify the information like creation time etc. (Ochiai,
Yamakawa, Fukushima, Yamada & Hayashi, 2000).
Clown image 6
Name /img_182.dd/Users/computer/Pictures/s-l640.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-19 05:20:17 AEST
Modified 2018-06-19 05:20:17 AEST
Size 57620
Accessed 2018-06-19 05:20:17 AEST
MD5 dd42fe966af825567338e4f873cc2f6a
Page 9 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internal ID 51657
It is presented in the pictures folder. The modified time, change time and access time are
obtained regarding the clown image. The application sector is used to display the clown image.
As similar to the other founded pictures this picture also related to clown. So this picture also
considered as the evidence for the suspicious activity. File Meta data are retrieved from the
image file. From the retrieved file Meta data we can able to identify the information like
creation time etc. These details may helpful for prove the crime is done by the Clark. In the
given table the various Meta details about the file are given.
Clown image 7
Name /img_182.dd/Users/computer/Pictures/1492447345937.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:52:15 AEST
Modified 2018-06-18 05:52:15 AEST
Size 17134
Accessed 2018-06-18 05:52:15 AEST
MD5 3e58af33ebb789d5d81cb4ac613a76c9
Page 10 of 47
It is presented in the pictures folder. The modified time, change time and access time are
obtained regarding the clown image. The application sector is used to display the clown image.
As similar to the other founded pictures this picture also related to clown. So this picture also
considered as the evidence for the suspicious activity. File Meta data are retrieved from the
image file. From the retrieved file Meta data we can able to identify the information like
creation time etc. These details may helpful for prove the crime is done by the Clark. In the
given table the various Meta details about the file are given.
Clown image 7
Name /img_182.dd/Users/computer/Pictures/1492447345937.jpg
Type File System
MIME Type image/jpeg
Created 2018-06-18 05:52:15 AEST
Modified 2018-06-18 05:52:15 AEST
Size 17134
Accessed 2018-06-18 05:52:15 AEST
MD5 3e58af33ebb789d5d81cb4ac613a76c9
Page 10 of 47
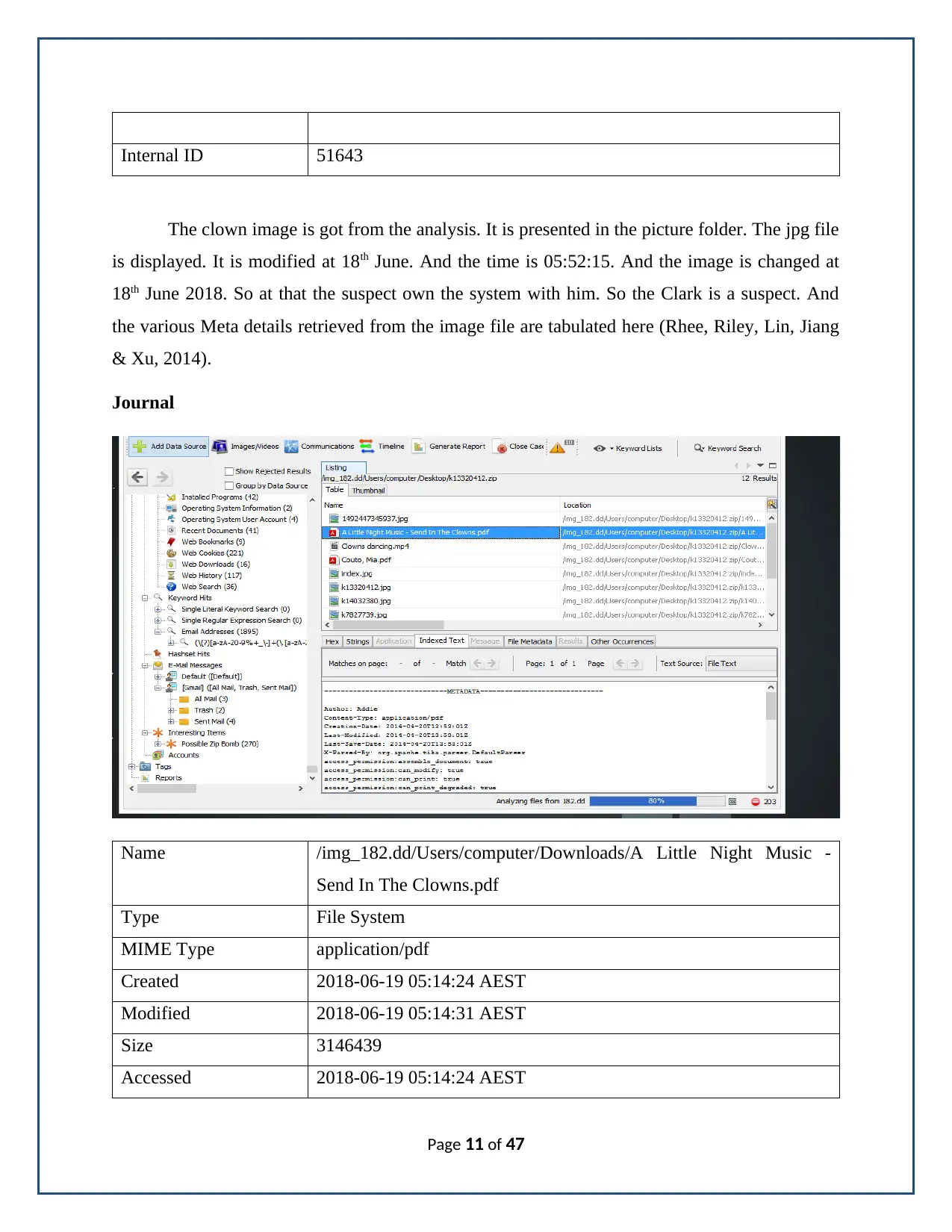
Internal ID 51643
The clown image is got from the analysis. It is presented in the picture folder. The jpg file
is displayed. It is modified at 18th June. And the time is 05:52:15. And the image is changed at
18th June 2018. So at that the suspect own the system with him. So the Clark is a suspect. And
the various Meta details retrieved from the image file are tabulated here (Rhee, Riley, Lin, Jiang
& Xu, 2014).
Journal
Name /img_182.dd/Users/computer/Downloads/A Little Night Music -
Send In The Clowns.pdf
Type File System
MIME Type application/pdf
Created 2018-06-19 05:14:24 AEST
Modified 2018-06-19 05:14:31 AEST
Size 3146439
Accessed 2018-06-19 05:14:24 AEST
Page 11 of 47
The clown image is got from the analysis. It is presented in the picture folder. The jpg file
is displayed. It is modified at 18th June. And the time is 05:52:15. And the image is changed at
18th June 2018. So at that the suspect own the system with him. So the Clark is a suspect. And
the various Meta details retrieved from the image file are tabulated here (Rhee, Riley, Lin, Jiang
& Xu, 2014).
Journal
Name /img_182.dd/Users/computer/Downloads/A Little Night Music -
Send In The Clowns.pdf
Type File System
MIME Type application/pdf
Created 2018-06-19 05:14:24 AEST
Modified 2018-06-19 05:14:31 AEST
Size 3146439
Accessed 2018-06-19 05:14:24 AEST
Page 11 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 47
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





