Digital Forensics Case Study: IT Fraud Investigation NCI 2018
VerifiedAdded on 2023/06/15
|16
|4333
|263
Case Study
AI Summary
This case study presents a digital forensics investigation into a potential IT fraud incident at Needful Things Ltd., involving a departing employee, Mortimer Smith, and allegations of data theft and sabotage. The solution outlines the initial steps for the CEO, Ricardo Sanchez, including preserving evidence and securing the premises. It details interview questions for key personnel (CEO, HR, IT) to gather information and identifies potential challenges like lack of cooperation or the possibility of a setup. Furthermore, the solution describes the forensic analysis of digital devices (phone, workstation, USB drive, CDs), emphasizing the importance of fingerprint analysis, data extraction, and file property examination. A chain of custody form is included to track evidence handling. The investigation aims to determine if Smith engaged in malicious activity or if the evidence is circumstantial.

Running Head: DIGITAL FORENSICS
Digital Forensics
Name of the Student
Name of the University
Digital Forensics
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DIGITAL FORENSICS
Question 1
Answer to A
In the phone call from the CEO, the initial details of the problem have been learnt.
However, without viewing the evidences, suitable actions cannot be taken. Hence, the initial
advices for the CEO should be as follows.
Keep the Workstation On – The first advice to be given to the CEO will be to keep the
workstation on unless someone from the forensics department visits the office and seizes the
machine (Gilani, Kozak and Innes 2016). This is mainly because the workstation may have a
password set and if it is switched off, it will require additional effort to reopen the workstation by
breaking the pass code.
Seal the Office Room – The next advice will be to keep the office room sealed with
nobody inside. This is a precautionary measure considering the fact that there may be an insider
who is actually working for Mortimer Smith. This person may try to access the workstation and
delete all the relevant evidences that the present in the computer.
Keep All Evidences As They Are – The CEO also should ensure the evidences including
the flash drive, CDs and others are kept as they are before handing over to the forensic personnel
(Prayudi and Sn 2015). The CEO should also ensure nobody takes away the evidences or even
come near the workstation for that matter.
No Leave for Employees before Experts Arrive – Another major step that the CEO needs
to take is to not allow any of the employees to leave the office premises or even use
communication devices to contact anyone except family before the forensic experts arrive at the
Question 1
Answer to A
In the phone call from the CEO, the initial details of the problem have been learnt.
However, without viewing the evidences, suitable actions cannot be taken. Hence, the initial
advices for the CEO should be as follows.
Keep the Workstation On – The first advice to be given to the CEO will be to keep the
workstation on unless someone from the forensics department visits the office and seizes the
machine (Gilani, Kozak and Innes 2016). This is mainly because the workstation may have a
password set and if it is switched off, it will require additional effort to reopen the workstation by
breaking the pass code.
Seal the Office Room – The next advice will be to keep the office room sealed with
nobody inside. This is a precautionary measure considering the fact that there may be an insider
who is actually working for Mortimer Smith. This person may try to access the workstation and
delete all the relevant evidences that the present in the computer.
Keep All Evidences As They Are – The CEO also should ensure the evidences including
the flash drive, CDs and others are kept as they are before handing over to the forensic personnel
(Prayudi and Sn 2015). The CEO should also ensure nobody takes away the evidences or even
come near the workstation for that matter.
No Leave for Employees before Experts Arrive – Another major step that the CEO needs
to take is to not allow any of the employees to leave the office premises or even use
communication devices to contact anyone except family before the forensic experts arrive at the

2DIGITAL FORENSICS
scene. This is required in order to ensure the employees are not able to communicate with
Mortimer Smith before official investigation starts and leak out important information (Lillis et
al. 2016). With the slightest of hints of information, Mortimer Smith may escape and travel to
another country or place before the investigation is officially opened.
All these advices will be given to Mr. Sanchez so that all the evidences of the case can be
taken and a suitable chain of custody can be prepared before the actual investigation starts.
Furthermore, as a part of the investigation, all the employees of the company will be interviewed
so that suitable information may be extracted that will help the case and prepare a suitable charge
against Mortimer Smith.
Answer to B
In the meeting, a detailed interview will be taken of the CEO, HR and a member of the IT
department. The following questions will be asked to each of them.
CEO
When did Mortimer Smith join the company?
How was he as an employee?
What were his duties as an employee?
Have you ever noticed any suspicious activity from him?
When did you come to know that he wants to resign?
What did he say when he submitted his resignation letter?
Anything you want to say that may be valuable in this investigation?
HR
scene. This is required in order to ensure the employees are not able to communicate with
Mortimer Smith before official investigation starts and leak out important information (Lillis et
al. 2016). With the slightest of hints of information, Mortimer Smith may escape and travel to
another country or place before the investigation is officially opened.
All these advices will be given to Mr. Sanchez so that all the evidences of the case can be
taken and a suitable chain of custody can be prepared before the actual investigation starts.
Furthermore, as a part of the investigation, all the employees of the company will be interviewed
so that suitable information may be extracted that will help the case and prepare a suitable charge
against Mortimer Smith.
Answer to B
In the meeting, a detailed interview will be taken of the CEO, HR and a member of the IT
department. The following questions will be asked to each of them.
CEO
When did Mortimer Smith join the company?
How was he as an employee?
What were his duties as an employee?
Have you ever noticed any suspicious activity from him?
When did you come to know that he wants to resign?
What did he say when he submitted his resignation letter?
Anything you want to say that may be valuable in this investigation?
HR
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DIGITAL FORENSICS
How often do you recruit your employees?
What method do you follow during the recruitment process?
How to you test the skills of the job applicant?
How did Mortimer Smith perform during the interview?
Did he say anything about future planning during the interview or anytime later?
How to do you monitor the employees during work?
Do you penalize the employees who fail to abide by the company’s policies?
Anything else you want to say that may help the investigation?
IT Department Member
What is your network configuration that you use in the company?
How many systems are connected to the server during working hours?
Are there any restrictions of visiting websites while working?
Do you have any firewalls to block access to some specific websites from the office
workstation?
Do you have any online monitoring system to check the websites accessed by the
employees from their workstations?
Did you ever monitor Mortimer Smith’s activities in his workstation?
Anything else you want to say that may help the investigation?
These are the main questions that will be asked to the three persons but some other
questions will also be asked in order to ensure each and every bit of information is gathered
regarding the case. All these data and information will add up to development of a suitable case
with evidences and eye witnesses (Van Baar, Van Beek and van Eijk 2014). In addition to these
How often do you recruit your employees?
What method do you follow during the recruitment process?
How to you test the skills of the job applicant?
How did Mortimer Smith perform during the interview?
Did he say anything about future planning during the interview or anytime later?
How to do you monitor the employees during work?
Do you penalize the employees who fail to abide by the company’s policies?
Anything else you want to say that may help the investigation?
IT Department Member
What is your network configuration that you use in the company?
How many systems are connected to the server during working hours?
Are there any restrictions of visiting websites while working?
Do you have any firewalls to block access to some specific websites from the office
workstation?
Do you have any online monitoring system to check the websites accessed by the
employees from their workstations?
Did you ever monitor Mortimer Smith’s activities in his workstation?
Anything else you want to say that may help the investigation?
These are the main questions that will be asked to the three persons but some other
questions will also be asked in order to ensure each and every bit of information is gathered
regarding the case. All these data and information will add up to development of a suitable case
with evidences and eye witnesses (Van Baar, Van Beek and van Eijk 2014). In addition to these
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DIGITAL FORENSICS
three personnel, other employees and stakeholders of the company will also be interviewed for
any piece of information that might be useful in the case. Without sufficient evidence, motive
and eye witnesses (if possible), the case against Mortimer Smith cannot be arranged that can be
presented in the court for continuing the charge of Needful Things Ltd. However, there may be
several issues arising during this interview meeting. These are as follows.
No Cooperation – Although Ricardo Sanchez is willing to build up a case against
Mortimer Smith for trying to defame and reduce the business of the company, other board
members may not be willing to proceed further in the case against Smith due to a large number
of reasons. One reason may be the company is not willing to spend significant amount of funds
for suing only one individual while another reason maybe the company is not willing to make
internal affairs public (Dang-Nguyen et al. 2015). Whatever be the reason, some of the board
members may not cooperate during the interview session and provide fake information regarding
the case. This can be a serious problem as it will be very hard to extract necessary data and will
need strong convincing to finally open them up.
Spy – As previously discussed, there might be a spy or a person inside the organization
who is actually working for Mortimer Smith and leaks internal information to him. If the
interview is called with the knowledge of all other employees, such persons may leak the
information to Smith and he will get careful and may escape before a case with solid evidence
can be set up.
Wrong Person – There can be another serious issue regarding this case. Although it is
apparently clear that Mortimer Smith violated the company’s policies and used the CEO’s faith
and trust on him for his own personal benefit. However, another possible explanation is that
three personnel, other employees and stakeholders of the company will also be interviewed for
any piece of information that might be useful in the case. Without sufficient evidence, motive
and eye witnesses (if possible), the case against Mortimer Smith cannot be arranged that can be
presented in the court for continuing the charge of Needful Things Ltd. However, there may be
several issues arising during this interview meeting. These are as follows.
No Cooperation – Although Ricardo Sanchez is willing to build up a case against
Mortimer Smith for trying to defame and reduce the business of the company, other board
members may not be willing to proceed further in the case against Smith due to a large number
of reasons. One reason may be the company is not willing to spend significant amount of funds
for suing only one individual while another reason maybe the company is not willing to make
internal affairs public (Dang-Nguyen et al. 2015). Whatever be the reason, some of the board
members may not cooperate during the interview session and provide fake information regarding
the case. This can be a serious problem as it will be very hard to extract necessary data and will
need strong convincing to finally open them up.
Spy – As previously discussed, there might be a spy or a person inside the organization
who is actually working for Mortimer Smith and leaks internal information to him. If the
interview is called with the knowledge of all other employees, such persons may leak the
information to Smith and he will get careful and may escape before a case with solid evidence
can be set up.
Wrong Person – There can be another serious issue regarding this case. Although it is
apparently clear that Mortimer Smith violated the company’s policies and used the CEO’s faith
and trust on him for his own personal benefit. However, another possible explanation is that

5DIGITAL FORENSICS
Mortimer Smith is not the wrongdoer at all. Each and every evidence found may be set up by
Ricardo Sanchez himself or one of his employees in order to take revenge on Smith for leaving
the organization (Agarwal and Kothari 2015). This possibility arises because in most of the cases
related to crime, the wrongdoer generally tries to hide all the evidences after committing the
crime whereas in this case, all the circumstantial evidences are left open (including the
workstation) after Mortimer Smith left the organization, which is a bit unusual for an efficient
employee as Smith. This issue will require detailed investigation and it can be done using the
interview process as nobody will admit that Mortimer Smith has been set up and he is not the
wrongdoer.
Answer to C
After the phone and the desktop are presented, they will be carefully handled as
preservation of fingerprints will be required for the purpose of the investigation. Investigation
will be stated on the spot for gathering sufficient evident that may lead to the conclusion of the
case. The evidences will be sent to the forensic lab for the following tests.
Fingerprint – As discussed previously, there are two possible explanations to the case.
Hence, finding the fingerprints on the devices is necessary that may lead to a strong trail in the
project. However, it is unlikely that if the board members and Sanchez are trying to set up Smith,
there will be any relevant fingerprints on the devices as they will remove any prints before
setting Smith up (Bartol and Bartol 2018). Hence, to analyze the possibility in this investigation,
extraction of fingerprints will be necessary.
Contents of Phone – The phone will be sent to the IT forensics for checking its contents
by unlocking it by breaking its password. However, the problem is that the phone is not provided
Mortimer Smith is not the wrongdoer at all. Each and every evidence found may be set up by
Ricardo Sanchez himself or one of his employees in order to take revenge on Smith for leaving
the organization (Agarwal and Kothari 2015). This possibility arises because in most of the cases
related to crime, the wrongdoer generally tries to hide all the evidences after committing the
crime whereas in this case, all the circumstantial evidences are left open (including the
workstation) after Mortimer Smith left the organization, which is a bit unusual for an efficient
employee as Smith. This issue will require detailed investigation and it can be done using the
interview process as nobody will admit that Mortimer Smith has been set up and he is not the
wrongdoer.
Answer to C
After the phone and the desktop are presented, they will be carefully handled as
preservation of fingerprints will be required for the purpose of the investigation. Investigation
will be stated on the spot for gathering sufficient evident that may lead to the conclusion of the
case. The evidences will be sent to the forensic lab for the following tests.
Fingerprint – As discussed previously, there are two possible explanations to the case.
Hence, finding the fingerprints on the devices is necessary that may lead to a strong trail in the
project. However, it is unlikely that if the board members and Sanchez are trying to set up Smith,
there will be any relevant fingerprints on the devices as they will remove any prints before
setting Smith up (Bartol and Bartol 2018). Hence, to analyze the possibility in this investigation,
extraction of fingerprints will be necessary.
Contents of Phone – The phone will be sent to the IT forensics for checking its contents
by unlocking it by breaking its password. However, the problem is that the phone is not provided
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DIGITAL FORENSICS
by the company and should be Mortimer Smith’s personal property. The phone can only be
analyzed for checking its calls and other important files or messages that may lead to the charge
against Smith. Another possible charge that can be brought against Smith is that he misused the
company’s resources (bill payments for the mobile phone usage) to make his personal work as
well as trying the damage the company’s business while working in it.
Contents of the Workstation – This is by far the biggest evidence that can be used to
prepare the case against Smith. The suspicious contents found in the workstation of Smith are
password protected and hence, the forensic department will need to break through the passwords
and then check the contents of the files. If the files really have the contents that Sanchez thinks,
then it will be significant evidence to set up the case against Mortimer Smith. However, some
other subtle details need to be checked before the case is set up against Smith (Thethi and Keane
2014). These details include the properties of the files (date created, author and source of the
file). These details can entirely turn the case in a different direction and Smith may be proved to
be not guilty. It is a possibility that the files have been created elsewhere and transferred to
Smith’s system in order to set him up. Hence, checking the source and contents of the files are all
necessary.
Other Evidences – Other evidences for the case includes the USB memory key and the
CDs that also have some suspicious files. These will also be checked for the contents in order to
set up the case against Smith. In addition to the material evidences, the interview results will be
used to prepare the entire case before prosecuting Smith.
The chain of custody is prepared as follows.
EVIDENCE CHAIN OF CUSTODY TRACKING FORM
by the company and should be Mortimer Smith’s personal property. The phone can only be
analyzed for checking its calls and other important files or messages that may lead to the charge
against Smith. Another possible charge that can be brought against Smith is that he misused the
company’s resources (bill payments for the mobile phone usage) to make his personal work as
well as trying the damage the company’s business while working in it.
Contents of the Workstation – This is by far the biggest evidence that can be used to
prepare the case against Smith. The suspicious contents found in the workstation of Smith are
password protected and hence, the forensic department will need to break through the passwords
and then check the contents of the files. If the files really have the contents that Sanchez thinks,
then it will be significant evidence to set up the case against Mortimer Smith. However, some
other subtle details need to be checked before the case is set up against Smith (Thethi and Keane
2014). These details include the properties of the files (date created, author and source of the
file). These details can entirely turn the case in a different direction and Smith may be proved to
be not guilty. It is a possibility that the files have been created elsewhere and transferred to
Smith’s system in order to set him up. Hence, checking the source and contents of the files are all
necessary.
Other Evidences – Other evidences for the case includes the USB memory key and the
CDs that also have some suspicious files. These will also be checked for the contents in order to
set up the case against Smith. In addition to the material evidences, the interview results will be
used to prepare the entire case before prosecuting Smith.
The chain of custody is prepared as follows.
EVIDENCE CHAIN OF CUSTODY TRACKING FORM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
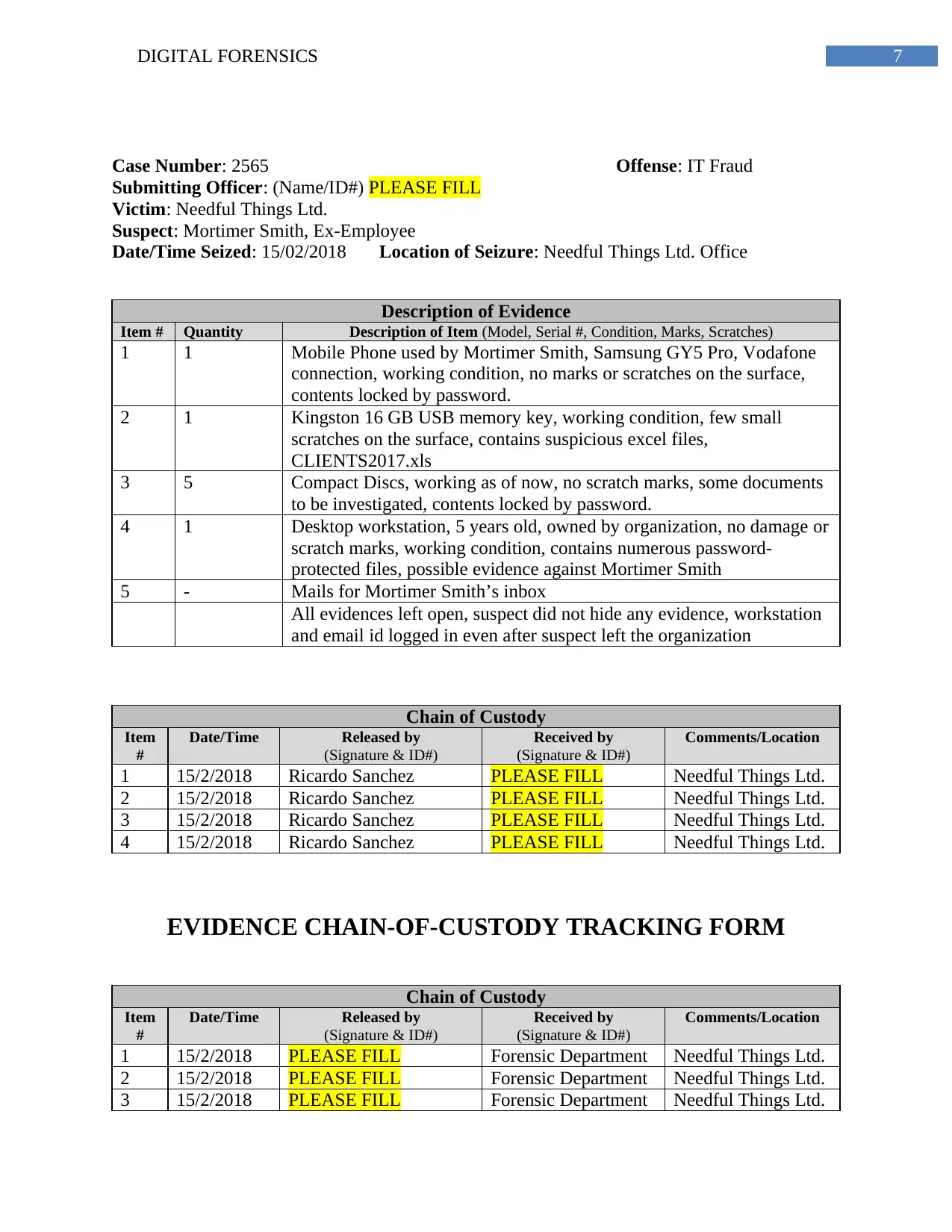
7DIGITAL FORENSICS
Case Number: 2565 Offense: IT Fraud
Submitting Officer: (Name/ID#) PLEASE FILL
Victim: Needful Things Ltd.
Suspect: Mortimer Smith, Ex-Employee
Date/Time Seized: 15/02/2018 Location of Seizure: Needful Things Ltd. Office
Description of Evidence
Item # Quantity Description of Item (Model, Serial #, Condition, Marks, Scratches)
1 1 Mobile Phone used by Mortimer Smith, Samsung GY5 Pro, Vodafone
connection, working condition, no marks or scratches on the surface,
contents locked by password.
2 1 Kingston 16 GB USB memory key, working condition, few small
scratches on the surface, contains suspicious excel files,
CLIENTS2017.xls
3 5 Compact Discs, working as of now, no scratch marks, some documents
to be investigated, contents locked by password.
4 1 Desktop workstation, 5 years old, owned by organization, no damage or
scratch marks, working condition, contains numerous password-
protected files, possible evidence against Mortimer Smith
5 - Mails for Mortimer Smith’s inbox
All evidences left open, suspect did not hide any evidence, workstation
and email id logged in even after suspect left the organization
Chain of Custody
Item
#
Date/Time Released by
(Signature & ID#)
Received by
(Signature & ID#)
Comments/Location
1 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
2 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
3 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
4 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
EVIDENCE CHAIN-OF-CUSTODY TRACKING FORM
Chain of Custody
Item
#
Date/Time Released by
(Signature & ID#)
Received by
(Signature & ID#)
Comments/Location
1 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
2 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
3 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
Case Number: 2565 Offense: IT Fraud
Submitting Officer: (Name/ID#) PLEASE FILL
Victim: Needful Things Ltd.
Suspect: Mortimer Smith, Ex-Employee
Date/Time Seized: 15/02/2018 Location of Seizure: Needful Things Ltd. Office
Description of Evidence
Item # Quantity Description of Item (Model, Serial #, Condition, Marks, Scratches)
1 1 Mobile Phone used by Mortimer Smith, Samsung GY5 Pro, Vodafone
connection, working condition, no marks or scratches on the surface,
contents locked by password.
2 1 Kingston 16 GB USB memory key, working condition, few small
scratches on the surface, contains suspicious excel files,
CLIENTS2017.xls
3 5 Compact Discs, working as of now, no scratch marks, some documents
to be investigated, contents locked by password.
4 1 Desktop workstation, 5 years old, owned by organization, no damage or
scratch marks, working condition, contains numerous password-
protected files, possible evidence against Mortimer Smith
5 - Mails for Mortimer Smith’s inbox
All evidences left open, suspect did not hide any evidence, workstation
and email id logged in even after suspect left the organization
Chain of Custody
Item
#
Date/Time Released by
(Signature & ID#)
Received by
(Signature & ID#)
Comments/Location
1 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
2 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
3 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
4 15/2/2018 Ricardo Sanchez PLEASE FILL Needful Things Ltd.
EVIDENCE CHAIN-OF-CUSTODY TRACKING FORM
Chain of Custody
Item
#
Date/Time Released by
(Signature & ID#)
Received by
(Signature & ID#)
Comments/Location
1 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
2 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
3 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.

8DIGITAL FORENSICS
4 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
Final Disposal Authority
Authorization for Disposal
Item(s) #: __________ on this document pertaining to (suspect): ____________________________________________
is(are) no longer needed as evidence and is/are authorized for disposal by (check appropriate disposal method)
☐ Return to Owner ☐ Auction/Destroy/Divert
Name & ID# of Authorizing Officer: ____________________________ Signature: ______________________Date: _______________
Witness to Destruction of Evidence
Item(s) #: __________ on this document were destroyed by Evidence Custodian ___________________________ID#:______
in my presence on (date) __________________________.
Name & ID# of Witness to destruction: ________________________ Signature: ______________________Date: _______________
Release to Lawful Owner
Item(s) #: __2, 3, 4 ________ on this document was/were released by Evidence Custodian ________________________ID#:_________ to
Name _________Ricardo Sanchez____________________________________________________________________
Address: ________Needful Things Ltd.________________________________________ City: ____________________State: _______ Zip
Code: __________
Telephone Number: (_____) ___________________________________
Under penalty of law, I certify that I am the lawful owner of the above item(s).
Signature: ______________Ricardo Sanchez_________________________________________ Date: ________15/2/2018______
Copy of Government-issued photo identification is attached. ☐ Yes ☐ No
This Evidence Chain-of-Custody form is to be retained as a permanent record by the Police Department.
4 15/2/2018 PLEASE FILL Forensic Department Needful Things Ltd.
Final Disposal Authority
Authorization for Disposal
Item(s) #: __________ on this document pertaining to (suspect): ____________________________________________
is(are) no longer needed as evidence and is/are authorized for disposal by (check appropriate disposal method)
☐ Return to Owner ☐ Auction/Destroy/Divert
Name & ID# of Authorizing Officer: ____________________________ Signature: ______________________Date: _______________
Witness to Destruction of Evidence
Item(s) #: __________ on this document were destroyed by Evidence Custodian ___________________________ID#:______
in my presence on (date) __________________________.
Name & ID# of Witness to destruction: ________________________ Signature: ______________________Date: _______________
Release to Lawful Owner
Item(s) #: __2, 3, 4 ________ on this document was/were released by Evidence Custodian ________________________ID#:_________ to
Name _________Ricardo Sanchez____________________________________________________________________
Address: ________Needful Things Ltd.________________________________________ City: ____________________State: _______ Zip
Code: __________
Telephone Number: (_____) ___________________________________
Under penalty of law, I certify that I am the lawful owner of the above item(s).
Signature: ______________Ricardo Sanchez_________________________________________ Date: ________15/2/2018______
Copy of Government-issued photo identification is attached. ☐ Yes ☐ No
This Evidence Chain-of-Custody form is to be retained as a permanent record by the Police Department.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DIGITAL FORENSICS
Question 2
Alex Pritchard
Director
Central Bureau of Forensic Investigation
London, UK
<NAME>
Head of IT Forensics
Central Bureau of Forensic Investigation
London, UK
Re: Case No. 2565, IT Fraud Case, Needful Things Ltd., London
Sir,
The Department of IT Forensics, Central Bureau of Forensic Investigation has been able to
attend the call made by Mr. Ricardo Sanchez, CEO, Needful Things Ltd., a maintenance services
company based in London. Mr. Sanchez has reported a case of IT fraud where an ex-employee of
the organization has been found to have misused the IT resources of the organization for
personal work as well as steal important confidential and strategic information of the
Question 2
Alex Pritchard
Director
Central Bureau of Forensic Investigation
London, UK
<NAME>
Head of IT Forensics
Central Bureau of Forensic Investigation
London, UK
Re: Case No. 2565, IT Fraud Case, Needful Things Ltd., London
Sir,
The Department of IT Forensics, Central Bureau of Forensic Investigation has been able to
attend the call made by Mr. Ricardo Sanchez, CEO, Needful Things Ltd., a maintenance services
company based in London. Mr. Sanchez has reported a case of IT fraud where an ex-employee of
the organization has been found to have misused the IT resources of the organization for
personal work as well as steal important confidential and strategic information of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DIGITAL FORENSICS
organization that he will possibly use for the development and growth of his own company.
Following are the details known till now.
Background
Needful Things Ltd. is a small business organization that provides maintenance services for
industrial batteries. There are 20 staff members and 5 board members including Ricardo
Sanchez, the CEO. Mortimer Smith was a trusted and efficient employee of the company who
recently resigned from the organization stating the reason that wants to open and run his own
company. Within few days of Smith’s leave, another employee, Avon Burman also resigned
from his post. Mr. Sanchez has reported that both of these two employees are now directors of a
new company that provides the same services as Needful Things Ltd. After both of them left,
Mr. Sanchez found certain evidences in Mortimer Smith’s desk that lead to a possible conclusion
that Smith planned his resignation from a long time ago and only used the organization’s IT
resources in order to set up his own company and he also used and stole confidential information
of the organization (like client data) for benefitting the growth of his own company.
The Evidences
Several evidences have been found on site including a mobile phone used by Mortimer Smith,
the workstation used by Smith, a flash USB drive and 5 CDs. The workstation, USB drive and
the discs contain several password protected files that may contain very important information
regarding the case and that can be enough to frame Mr. Smith guilty. The flash drive contains an
excel file named CLIENTS2017.xls, which is password protected. Mr. Sanchez suspects that this
file contains the list of all existing clients of the company and Mr. Smith will try to use this list to
get customers in his company that will result in loss of customer base of Needful Things. All the
organization that he will possibly use for the development and growth of his own company.
Following are the details known till now.
Background
Needful Things Ltd. is a small business organization that provides maintenance services for
industrial batteries. There are 20 staff members and 5 board members including Ricardo
Sanchez, the CEO. Mortimer Smith was a trusted and efficient employee of the company who
recently resigned from the organization stating the reason that wants to open and run his own
company. Within few days of Smith’s leave, another employee, Avon Burman also resigned
from his post. Mr. Sanchez has reported that both of these two employees are now directors of a
new company that provides the same services as Needful Things Ltd. After both of them left,
Mr. Sanchez found certain evidences in Mortimer Smith’s desk that lead to a possible conclusion
that Smith planned his resignation from a long time ago and only used the organization’s IT
resources in order to set up his own company and he also used and stole confidential information
of the organization (like client data) for benefitting the growth of his own company.
The Evidences
Several evidences have been found on site including a mobile phone used by Mortimer Smith,
the workstation used by Smith, a flash USB drive and 5 CDs. The workstation, USB drive and
the discs contain several password protected files that may contain very important information
regarding the case and that can be enough to frame Mr. Smith guilty. The flash drive contains an
excel file named CLIENTS2017.xls, which is password protected. Mr. Sanchez suspects that this
file contains the list of all existing clients of the company and Mr. Smith will try to use this list to
get customers in his company that will result in loss of customer base of Needful Things. All the

11DIGITAL FORENSICS
evidences found at the desk of Mortimer Smith have been collected and sent to forensic lab for
further analysis and extraction of information. Some data and information have also been
collected from the interview with the CEO, HR and an IT member and noted down for further
investigation.
There is one lack of continuity in the evidences gathered. Mr. Sanchez told that he found the
workstation of Mr. Smith in open mode with the email id logged in. However, generally it is seen
that the criminal tries to hide evidences as much as he can before leaving the scene. Here, it is
seen that the Mr. Smith apparently left the evidences wide open to be viewed by anyone who
visits his desk. This is a very unusual behavior from the criminal and it is a possibility that Mr.
Smith has been framed by Mr. Sanchez or any other board member of Needful Things. However,
further investigation is needed be sure whether any possibility is accurate and true.
The evidences will be sent directly to the forensic lab for analysis including gathering of
fingerprints, collection of data from the documents found by breaking the passwords, call history
checking, mails sent and received and others. After collection of data, the workstation will be
returned to Mr. Sanchez promptly.
Possible Information
There can be various types of information that may be found in the workstation and the flash
drive. As Mr. Sanchez reported, the contents of the files can help to prepare a suitable case
against Mr. Smith if these documents are found to contain confidential information of the
organization. Furthermore, the mailbox of Mr. Smith will be checked to find out whether he had
sent the organization’s confidential information to some other sources or entities. Also, the
evidences found at the desk of Mortimer Smith have been collected and sent to forensic lab for
further analysis and extraction of information. Some data and information have also been
collected from the interview with the CEO, HR and an IT member and noted down for further
investigation.
There is one lack of continuity in the evidences gathered. Mr. Sanchez told that he found the
workstation of Mr. Smith in open mode with the email id logged in. However, generally it is seen
that the criminal tries to hide evidences as much as he can before leaving the scene. Here, it is
seen that the Mr. Smith apparently left the evidences wide open to be viewed by anyone who
visits his desk. This is a very unusual behavior from the criminal and it is a possibility that Mr.
Smith has been framed by Mr. Sanchez or any other board member of Needful Things. However,
further investigation is needed be sure whether any possibility is accurate and true.
The evidences will be sent directly to the forensic lab for analysis including gathering of
fingerprints, collection of data from the documents found by breaking the passwords, call history
checking, mails sent and received and others. After collection of data, the workstation will be
returned to Mr. Sanchez promptly.
Possible Information
There can be various types of information that may be found in the workstation and the flash
drive. As Mr. Sanchez reported, the contents of the files can help to prepare a suitable case
against Mr. Smith if these documents are found to contain confidential information of the
organization. Furthermore, the mailbox of Mr. Smith will be checked to find out whether he had
sent the organization’s confidential information to some other sources or entities. Also, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
