ITC597: Digital Forensics Report on USB Data Recovery and Analysis
VerifiedAdded on 2023/06/12
|18
|1989
|460
Report
AI Summary
This digital forensics report investigates potential intellectual property theft by a contract employee of Exotic Mountain Tour Services (EMTS). The report details the recovery of deleted and hidden data from a USB drive found on the employee's desk. Tools such as Winhex, ProDiscover, and steganography techniques were used to recover deleted images, hidden text within images, and other files. The analysis aims to determine if the USB drive contains proprietary data belonging to EMTS or Superior Bicycles, LLC, and to assess whether sensitive marketing information was compromised. The report outlines the procedures, findings, and conclusions drawn from the digital forensic examination of the USB drive.
DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This project is to create the digital forensic report for EMTS organization because this
organization needs to recover the data from the USB. It lost the suspicious data from the hard
drive, so organization chief has decided to recover the suspicious data from USB. This can be
handed by the Bob Aspen. The digital forensic report is used to investigate the probable
intellectual property which is stolen by the Bob Aspen who is working as a contract
employee of the EMTS (Exotic Mountain Tour Services). The EMTS organization has the
completed analysis and very expansive marketing process on the customer services and it is
provided by the superior bicycle LLC Company.
2
This project is to create the digital forensic report for EMTS organization because this
organization needs to recover the data from the USB. It lost the suspicious data from the hard
drive, so organization chief has decided to recover the suspicious data from USB. This can be
handed by the Bob Aspen. The digital forensic report is used to investigate the probable
intellectual property which is stolen by the Bob Aspen who is working as a contract
employee of the EMTS (Exotic Mountain Tour Services). The EMTS organization has the
completed analysis and very expansive marketing process on the customer services and it is
provided by the superior bicycle LLC Company.
2

Table of Contents
1. Introduction...................................................................................................................................4
1.1 Back ground...........................................................................................................................4
1.2 Scope.....................................................................................................................................4
1.3 Forensic Tools.......................................................................................................................5
2. Analysis.........................................................................................................................................5
2.1 Winhex Tool..........................................................................................................................5
2.2 Pro Discover Tool..................................................................................................................5
2.3 Stenography Tool...................................................................................................................6
3. Findings.........................................................................................................................................6
3.1 Recover the deleted image in the usb Using Winhex.............................................................6
3.2 Recover the hidden text in Image using Stenography tool...................................................12
3.3 Recover the files by using the Pro Discover........................................................................14
4 Conclusion...................................................................................................................................17
References...........................................................................................................................................18
3
1. Introduction...................................................................................................................................4
1.1 Back ground...........................................................................................................................4
1.2 Scope.....................................................................................................................................4
1.3 Forensic Tools.......................................................................................................................5
2. Analysis.........................................................................................................................................5
2.1 Winhex Tool..........................................................................................................................5
2.2 Pro Discover Tool..................................................................................................................5
2.3 Stenography Tool...................................................................................................................6
3. Findings.........................................................................................................................................6
3.1 Recover the deleted image in the usb Using Winhex.............................................................6
3.2 Recover the hidden text in Image using Stenography tool...................................................12
3.3 Recover the files by using the Pro Discover........................................................................14
4 Conclusion...................................................................................................................................17
References...........................................................................................................................................18
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
1.1 Back ground
This project goal is to prepare the digital forensic report for Exotic Mountain Tour
Services Organization. The digital forensic report is used to investigate the probable
intellectual property which is stolen by the Bob Aspen who is working as a contract
employee of the EMTS (Exotic Mountain Tour Services). The EMTS organization has the
completed analysis and very expansive marketing process on the customer services and it is
provided by the superior bicycle LLC Company. The EMTS organization requires the new
data recovery, because the current data recovery process does not provide the effective data
recovery from hard drives. And, it also plans to do the effective and efficient advertisement
for joining the product deal of superior bicycles which is their tour service. Generally, this
organization is used to ensure the promoting effort material under the concurrence of
disclosure with superior bicycle. The EMTS organization lost and deleted the important
information from hard drive. So, the EMTS chief has decided to recover the intriguing data
and it is handled by web server executive that is Bob Aspen. The web server executive is
ensuring the deleted data and also recovers the data by using the digital forensic tools. The
EMTS organization has web based email activity through the organization system and
distinguishes the suspicious connection. So, here the suspicious data is deleted and it needs to
be recovered from an organization.
1.2 Scope
The scope of this project is to prepare the digital forensic report for an EMTS
organization. Because, this organization lost the suspicious data and it needs to be recovered
by using the digital forensic tools. We will recover the deleted or lost file which is suspicious
data that is related to the provided case scenarios. The EMTS organization chief has decided
to recover the deleted data from USB by using the appropriate digital forensic tool. In the
provided the case scenarios, we are going to use the stenography tool to recover the hidden
text in the image, Winhex tool is used to recover the deleted image from USB and the pro
discover tool is used to recover the delete file from USB. The forensics tools are needed to
analysis before finding the evidence for an EMTS organization.
4
1.1 Back ground
This project goal is to prepare the digital forensic report for Exotic Mountain Tour
Services Organization. The digital forensic report is used to investigate the probable
intellectual property which is stolen by the Bob Aspen who is working as a contract
employee of the EMTS (Exotic Mountain Tour Services). The EMTS organization has the
completed analysis and very expansive marketing process on the customer services and it is
provided by the superior bicycle LLC Company. The EMTS organization requires the new
data recovery, because the current data recovery process does not provide the effective data
recovery from hard drives. And, it also plans to do the effective and efficient advertisement
for joining the product deal of superior bicycles which is their tour service. Generally, this
organization is used to ensure the promoting effort material under the concurrence of
disclosure with superior bicycle. The EMTS organization lost and deleted the important
information from hard drive. So, the EMTS chief has decided to recover the intriguing data
and it is handled by web server executive that is Bob Aspen. The web server executive is
ensuring the deleted data and also recovers the data by using the digital forensic tools. The
EMTS organization has web based email activity through the organization system and
distinguishes the suspicious connection. So, here the suspicious data is deleted and it needs to
be recovered from an organization.
1.2 Scope
The scope of this project is to prepare the digital forensic report for an EMTS
organization. Because, this organization lost the suspicious data and it needs to be recovered
by using the digital forensic tools. We will recover the deleted or lost file which is suspicious
data that is related to the provided case scenarios. The EMTS organization chief has decided
to recover the deleted data from USB by using the appropriate digital forensic tool. In the
provided the case scenarios, we are going to use the stenography tool to recover the hidden
text in the image, Winhex tool is used to recover the deleted image from USB and the pro
discover tool is used to recover the delete file from USB. The forensics tools are needed to
analysis before finding the evidence for an EMTS organization.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3 Forensic Tools
The EMTS organization is decided to use the below forensic tool to recover the data from
USB. These are,
Winhex tool
Pro Discover Tool
Stenography Tool
2. Analysis
2.1 Winhex Tool
The Winhex forensic tool is the most common editor for universe hex editor and it is
very useful for an EMTS organization. The Winhex tool is also useful for data recovery from
USB, hard drive and etc. It is helpful for realm of low level data editing, computer forensic
and data recovery. This tools are used to edit and recovery the following aspects like CD-
ROM, hard disks, DVD, compute flash, floppy disks, computer RAM, all types of drive and
all kinds of file. The Winhex tool supports the FAT12, FAT16, FAT32 and NTFS to provide
the effective data recovery and it is very useful for inspects and also editing the recovered lost
files, data files and all kinds of the files from corrupted file system and hard drive. It
especially supports the domain of the IT security, low level preparing, PC legal science and
information recuperation. It investigates and utilizes the wide range of lost information,
erased document and documents from hard drive and USB with degenerate the document
frameworks from advanced camera cards.Many organizations are using this tool to provide
the effective data recovery, because it is generally fast.
2.2 Pro Discover Tool
The pro discover tool is used to recover the data from hard drive, USE and more. It
provides the cutting edge feature in the industry standards for proactive computer forensics. It
is the powerful computer security tool that enables the computer professionals to locate the
all data on a computer disk and it protects the evidence. It creates the quality evidentiary
reports for used in legal proceedings. It uses the least destructive methodology to allow the
examination of files without altering the valuable Meta data such as last time accessed file.
The pro discover forensic tool is used to recover the deleted files, access windows alternate
data streams, examine the slack space and dynamically allows preview, image and search the
hardware protected area of the disk to utilizing the files by using the pioneered technology. It
5
The EMTS organization is decided to use the below forensic tool to recover the data from
USB. These are,
Winhex tool
Pro Discover Tool
Stenography Tool
2. Analysis
2.1 Winhex Tool
The Winhex forensic tool is the most common editor for universe hex editor and it is
very useful for an EMTS organization. The Winhex tool is also useful for data recovery from
USB, hard drive and etc. It is helpful for realm of low level data editing, computer forensic
and data recovery. This tools are used to edit and recovery the following aspects like CD-
ROM, hard disks, DVD, compute flash, floppy disks, computer RAM, all types of drive and
all kinds of file. The Winhex tool supports the FAT12, FAT16, FAT32 and NTFS to provide
the effective data recovery and it is very useful for inspects and also editing the recovered lost
files, data files and all kinds of the files from corrupted file system and hard drive. It
especially supports the domain of the IT security, low level preparing, PC legal science and
information recuperation. It investigates and utilizes the wide range of lost information,
erased document and documents from hard drive and USB with degenerate the document
frameworks from advanced camera cards.Many organizations are using this tool to provide
the effective data recovery, because it is generally fast.
2.2 Pro Discover Tool
The pro discover tool is used to recover the data from hard drive, USE and more. It
provides the cutting edge feature in the industry standards for proactive computer forensics. It
is the powerful computer security tool that enables the computer professionals to locate the
all data on a computer disk and it protects the evidence. It creates the quality evidentiary
reports for used in legal proceedings. It uses the least destructive methodology to allow the
examination of files without altering the valuable Meta data such as last time accessed file.
The pro discover forensic tool is used to recover the deleted files, access windows alternate
data streams, examine the slack space and dynamically allows preview, image and search the
hardware protected area of the disk to utilizing the files by using the pioneered technology. It
5

allows the users to search the entire disk for keywords, phrases, regular expression and also
uses Boolean search capability to determine the necessary data.
2.3 Stenography Tool
The steganography tool is used to hide the secret information which is invisible in an
image and audio file by using the steganography techniques. It modifies the least significant
bits of the pixels in images and adds the noise to the audio samples to hide the information. It
is used to provide the best way to protect the privacy of EMTS organization and it makes to
hard to determine that any private communications are taking place. It uses the steghide
program to perform the steganography and the files are generated to fully compatible with
steghide. The tool is used to hide a message with the function normally and the user will not
suspect just by looking the file. It has various conditions to hide the information and it needs
the secure transmission of files. It reduces the chance of data leakage.This tool has the
various ways of achieving the steganography in digital communication. It does not need to
perform the coding to achieve this. This tool can be used to hide your secret text behind the
HTML file, Docx file, image files and any other kind of file.
3. Findings
3.1 Recover the deleted image in the usb Using Winhex
The Winhex recovery tool is used to recover deleted image from USB. This is very
popular data recovery tool and it is very useful this organization. It also recovers the
corrupted images. The below screenshots is used to show the corrupted images and it needs to
be recovered by using the Winhex recovery tool (AG, 2018).
6
uses Boolean search capability to determine the necessary data.
2.3 Stenography Tool
The steganography tool is used to hide the secret information which is invisible in an
image and audio file by using the steganography techniques. It modifies the least significant
bits of the pixels in images and adds the noise to the audio samples to hide the information. It
is used to provide the best way to protect the privacy of EMTS organization and it makes to
hard to determine that any private communications are taking place. It uses the steghide
program to perform the steganography and the files are generated to fully compatible with
steghide. The tool is used to hide a message with the function normally and the user will not
suspect just by looking the file. It has various conditions to hide the information and it needs
the secure transmission of files. It reduces the chance of data leakage.This tool has the
various ways of achieving the steganography in digital communication. It does not need to
perform the coding to achieve this. This tool can be used to hide your secret text behind the
HTML file, Docx file, image files and any other kind of file.
3. Findings
3.1 Recover the deleted image in the usb Using Winhex
The Winhex recovery tool is used to recover deleted image from USB. This is very
popular data recovery tool and it is very useful this organization. It also recovers the
corrupted images. The below screenshots is used to show the corrupted images and it needs to
be recovered by using the Winhex recovery tool (AG, 2018).
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
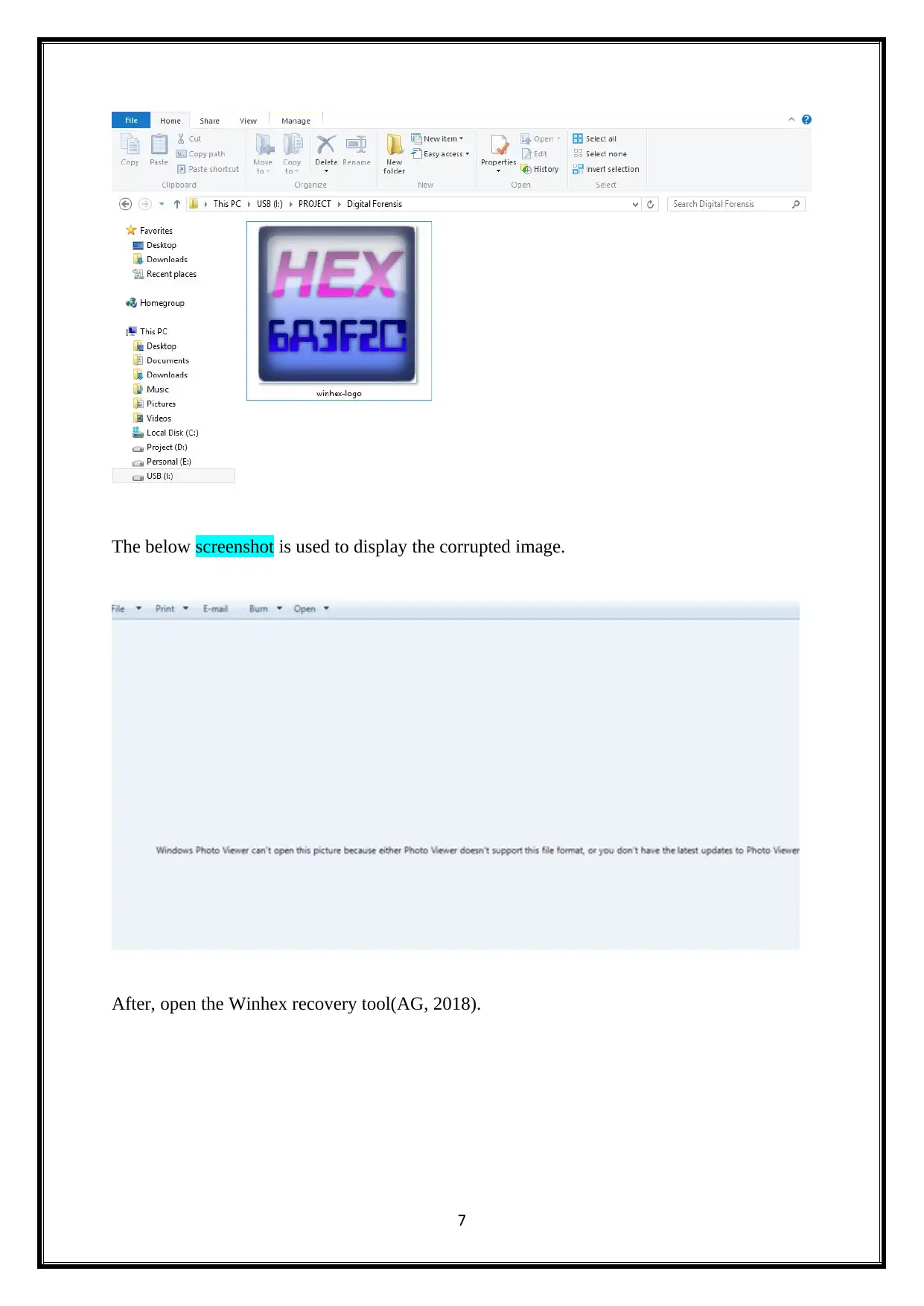
The below screenshot is used to display the corrupted image.
After, open the Winhex recovery tool(AG, 2018).
7
After, open the Winhex recovery tool(AG, 2018).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
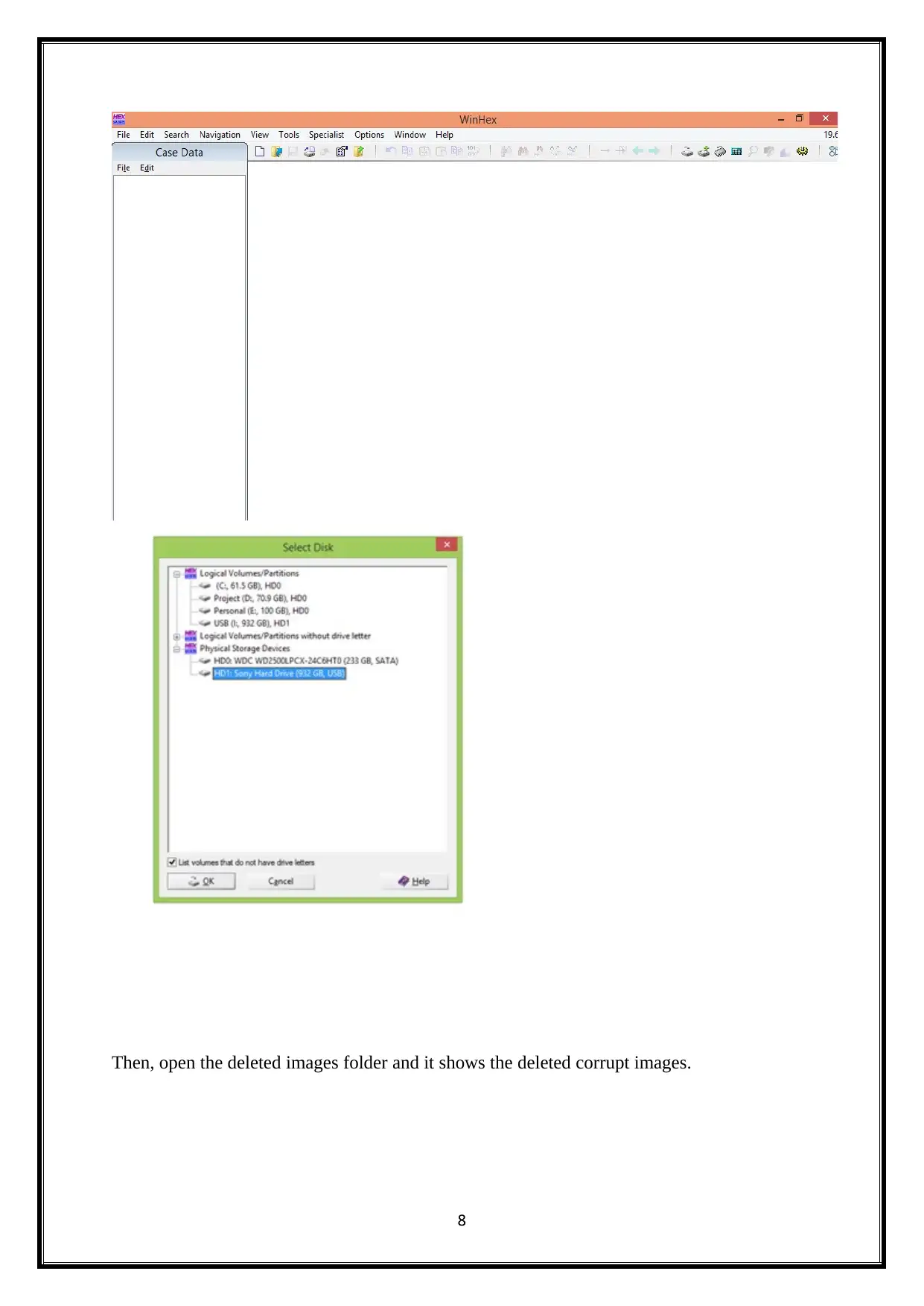
Then, open the deleted images folder and it shows the deleted corrupt images.
8
8
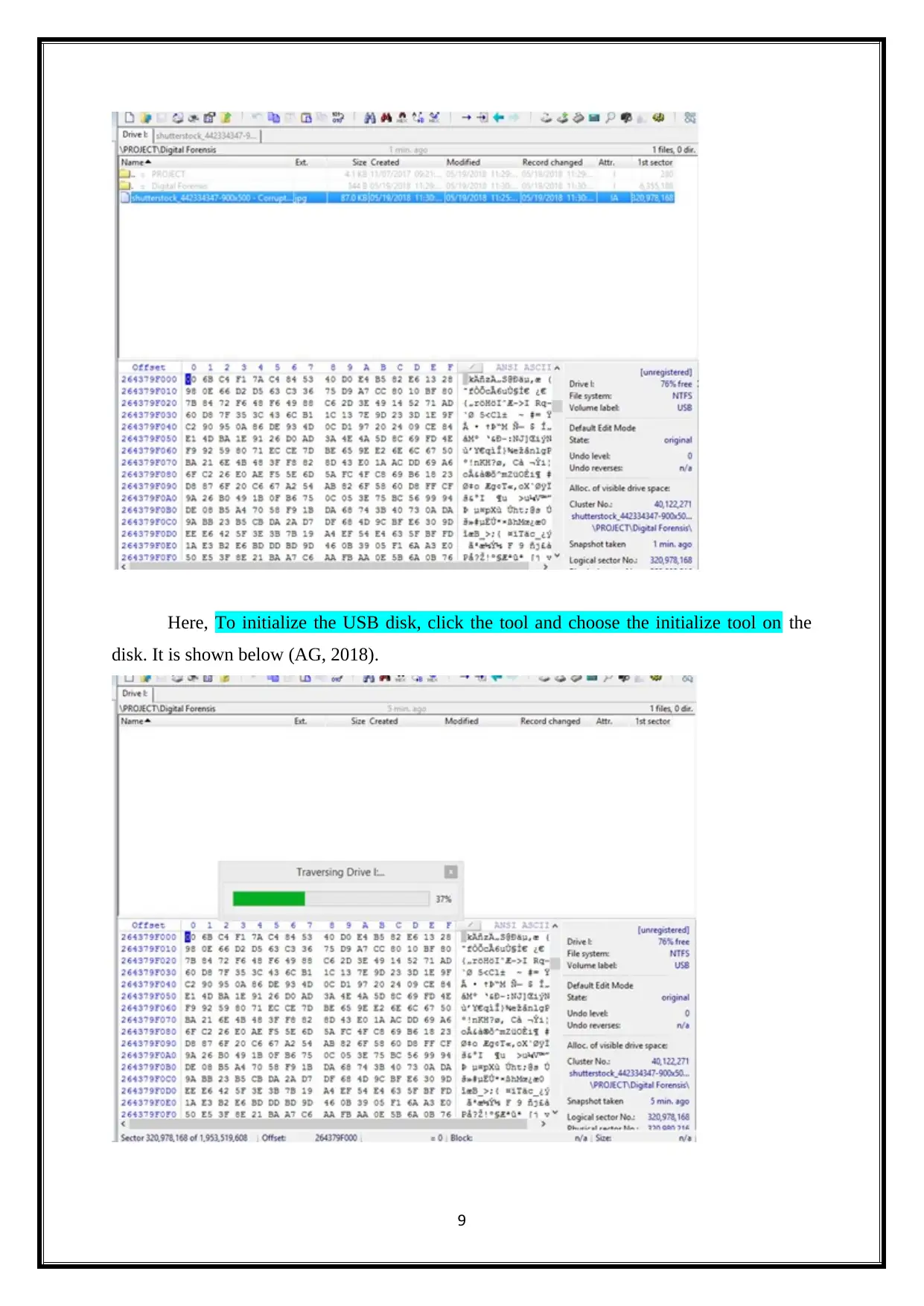
Here, To initialize the USB disk, click the tool and choose the initialize tool on the
disk. It is shown below (AG, 2018).
9
disk. It is shown below (AG, 2018).
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
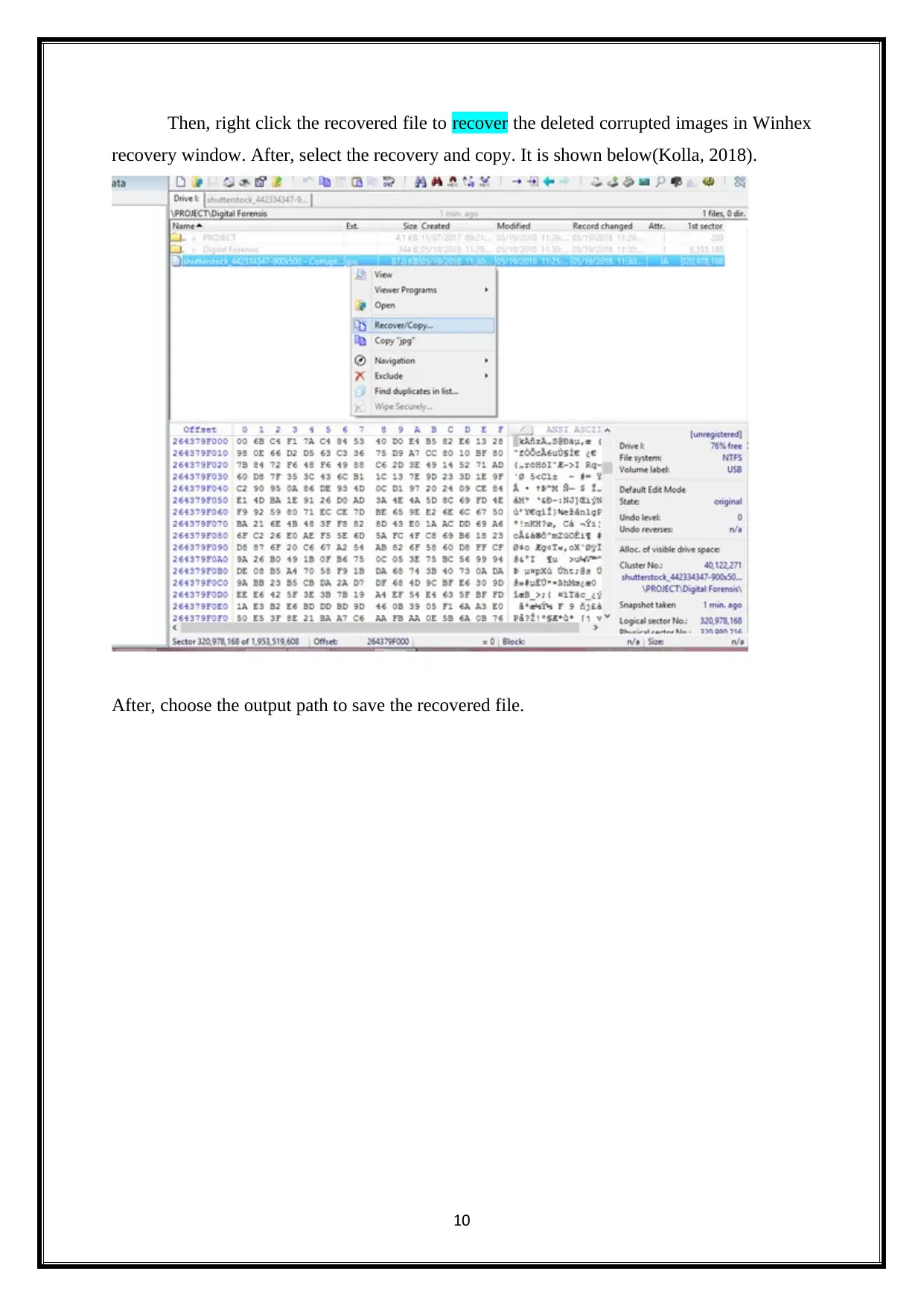
Then, right click the recovered file to recover the deleted corrupted images in Winhex
recovery window. After, select the recovery and copy. It is shown below(Kolla, 2018).
After, choose the output path to save the recovered file.
10
recovery window. After, select the recovery and copy. It is shown below(Kolla, 2018).
After, choose the output path to save the recovered file.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
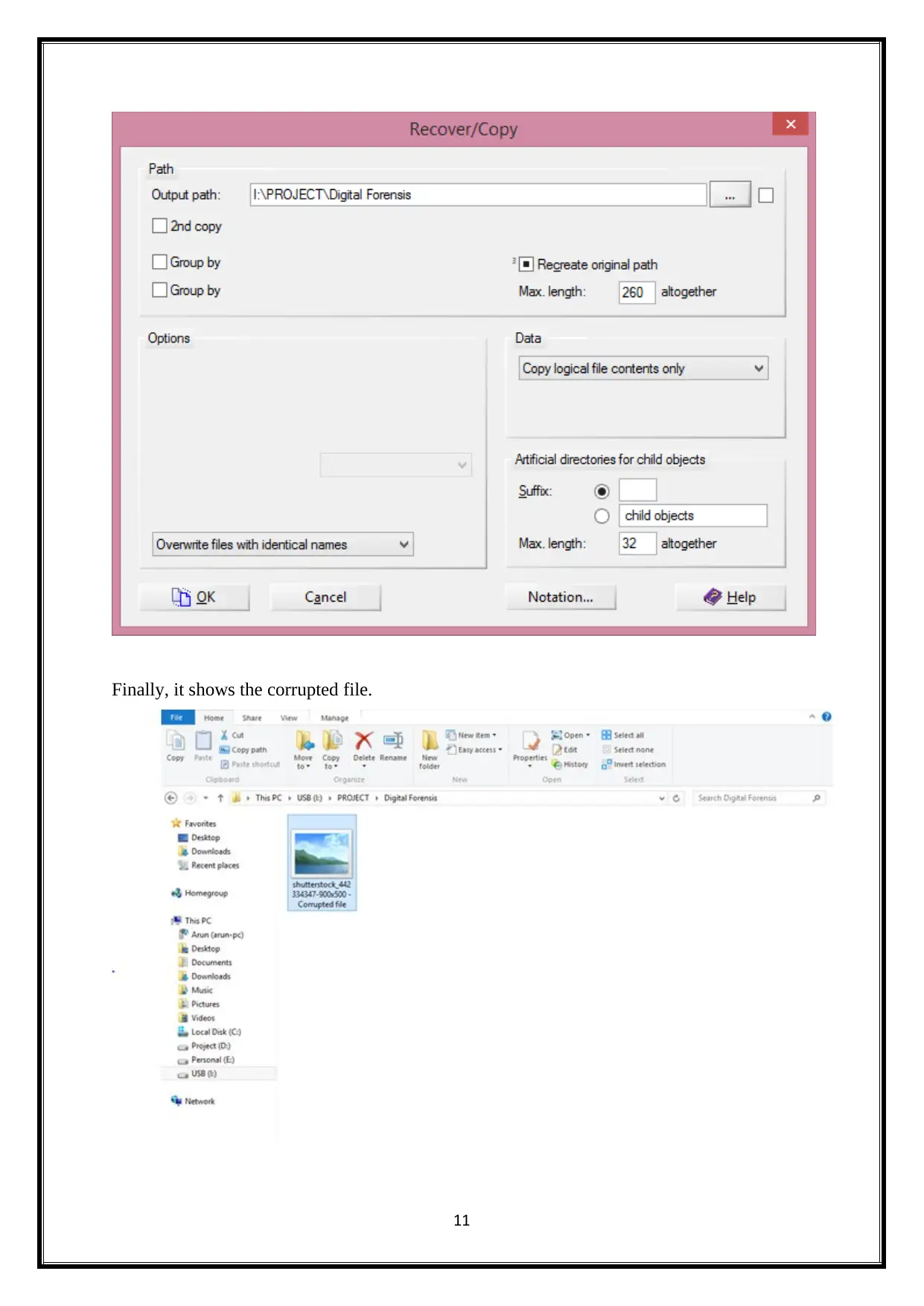
Finally, it shows the corrupted file.
11
11
3.2 Recover the hidden text in Image using Stenography tool
The stenography tool is used to recover the hidden text in image. The stenography tool
is used to give the efficient and effective data recovery for an organization. It needs to
recover the hidden text in the image from USB ("Steganography Tools", 2018). The below
image is needed to recover the hidden text by using the stenography tool.
So, open stenography software.
12
The stenography tool is used to recover the hidden text in image. The stenography tool
is used to give the efficient and effective data recovery for an organization. It needs to
recover the hidden text in the image from USB ("Steganography Tools", 2018). The below
image is needed to recover the hidden text by using the stenography tool.
So, open stenography software.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


