Digital Forensics Assignment: Analysis of Hard Disk Investigation
VerifiedAdded on 2023/01/16
|9
|815
|44
Practical Assignment
AI Summary
This assignment solution focuses on digital forensics, encompassing the analysis of a case study based on the ACS Code of Ethics and the investigation of a suspicious hard disk. The first task involves evaluating a software release scenario against the six values of the ACS code, identifying potential conflicts and ethical violations. The second task involves a detailed investigation of a virtual hard disk, including the use of tools like Hiren's BootCD and WinHex to identify specific files and hidden data, demonstrating practical data recovery and forensic analysis techniques. The assignment emphasizes the importance of maintaining the integrity of digital evidence and understanding file systems.

Running head: INTRODUCTION TO DIGITAL FORENSICS
Introduction to Digital Forensics
Name of the Student
Name of the University
Author’s Note
Introduction to Digital Forensics
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTRODUCTION TO DIGITAL FORENSICS
Task 1: Analysis of ACS_Ethics with the application of 6 values of ACS Code of Ethics
Case No. 6:
The selected case for releasing the software application with bugs present in its violates the ACS code of
professional conduct and have potential conflict between the legal and other acceptance. The new software package
developed by the company can help the small business and individual to figure the taxes and new tax laws. The bugs
present in the software codes can cause error in the result and thus violates the 6 values of ACS code of ethics.
The primacy of public interest – The interest of the stakeholders is not safeguarded and thus it causes a
conflict between the duty and loyalty to owe the public. The public health, environment and safety is evaluated for
finding the impact and the software can cause error in calculation of the tax and results in penalised by ATO.
Enhancement of quality of life – The impact of the application on the society and the negative effect of the
application and its continuation is evaluated. The approach for minimizing the effect of bug and promoting the access
of benefits to all the members with the application of updates and patches can help in promoting the health and safety
for the people affected with the application.
Honesty – The use of disclaimer for the resultant of the use of application is used for distinguishing the
professional and personal opinion. The scenario does not fulfil the honesty values for providing the estimation and
controlling the project. Attempt is not made for enhancing the reputation at an expense of the employee’s reputation.
Competence – The president of the company is highly competent and do not hesitate for obtaining expertise
and individuals for modify the program according to the suggestion of the user. Focus is given on providing product
and service for matching with financial and operational needs. The skills and knowledge is not misrepresented and the
responsibility of work is accepted. The property of interest of the stakeholders are not respected the rectification is
done ion demand of the user after the consequences.
Professional Development – The new technologies is evaluated and practice and standards of the work is
performed for keeping the knowledge up to dated. The industry policy is evaluated and the needs of professionals for
the rectification of the bug is analysed for increasing the public relationship.
Professionalism – The rapid changes and acquiring standards and legislation is evaluated for maintaining a
professional standard in the business. The members of the development team aware of the bug should take
appropriate action like whistle blowing for enabling the ACS member engage the unethical behaviour.
Task 2: Investigation of suspicious hard disk
INTRODUCTION TO DIGITAL FORENSICS
Task 1: Analysis of ACS_Ethics with the application of 6 values of ACS Code of Ethics
Case No. 6:
The selected case for releasing the software application with bugs present in its violates the ACS code of
professional conduct and have potential conflict between the legal and other acceptance. The new software package
developed by the company can help the small business and individual to figure the taxes and new tax laws. The bugs
present in the software codes can cause error in the result and thus violates the 6 values of ACS code of ethics.
The primacy of public interest – The interest of the stakeholders is not safeguarded and thus it causes a
conflict between the duty and loyalty to owe the public. The public health, environment and safety is evaluated for
finding the impact and the software can cause error in calculation of the tax and results in penalised by ATO.
Enhancement of quality of life – The impact of the application on the society and the negative effect of the
application and its continuation is evaluated. The approach for minimizing the effect of bug and promoting the access
of benefits to all the members with the application of updates and patches can help in promoting the health and safety
for the people affected with the application.
Honesty – The use of disclaimer for the resultant of the use of application is used for distinguishing the
professional and personal opinion. The scenario does not fulfil the honesty values for providing the estimation and
controlling the project. Attempt is not made for enhancing the reputation at an expense of the employee’s reputation.
Competence – The president of the company is highly competent and do not hesitate for obtaining expertise
and individuals for modify the program according to the suggestion of the user. Focus is given on providing product
and service for matching with financial and operational needs. The skills and knowledge is not misrepresented and the
responsibility of work is accepted. The property of interest of the stakeholders are not respected the rectification is
done ion demand of the user after the consequences.
Professional Development – The new technologies is evaluated and practice and standards of the work is
performed for keeping the knowledge up to dated. The industry policy is evaluated and the needs of professionals for
the rectification of the bug is analysed for increasing the public relationship.
Professionalism – The rapid changes and acquiring standards and legislation is evaluated for maintaining a
professional standard in the business. The members of the development team aware of the bug should take
appropriate action like whistle blowing for enabling the ACS member engage the unethical behaviour.
Task 2: Investigation of suspicious hard disk
2
INTRODUCTION TO DIGITAL FORENSICS
For the investigation of the virtual hard disk available from the module the virtual box image file is downloaded
from “https://download.ise.canberra.edu.au/wanli/”. The chunks are assembled and the setup is done in oracle virtual
box.
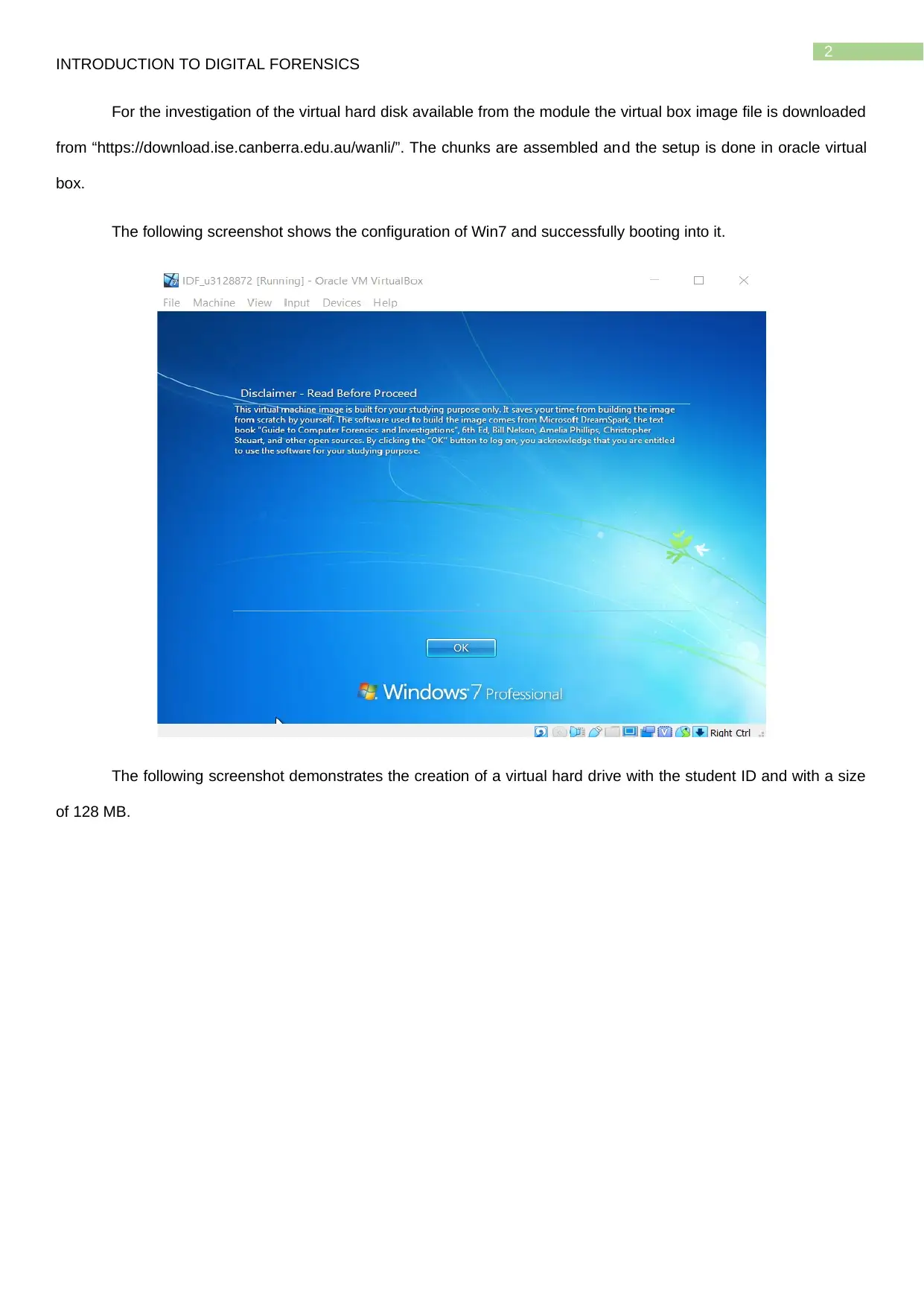
The following screenshot shows the configuration of Win7 and successfully booting into it.
The following screenshot demonstrates the creation of a virtual hard drive with the student ID and with a size
of 128 MB.
INTRODUCTION TO DIGITAL FORENSICS
For the investigation of the virtual hard disk available from the module the virtual box image file is downloaded
from “https://download.ise.canberra.edu.au/wanli/”. The chunks are assembled and the setup is done in oracle virtual
box.
The following screenshot shows the configuration of Win7 and successfully booting into it.
The following screenshot demonstrates the creation of a virtual hard drive with the student ID and with a size
of 128 MB.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTRODUCTION TO DIGITAL FORENSICS
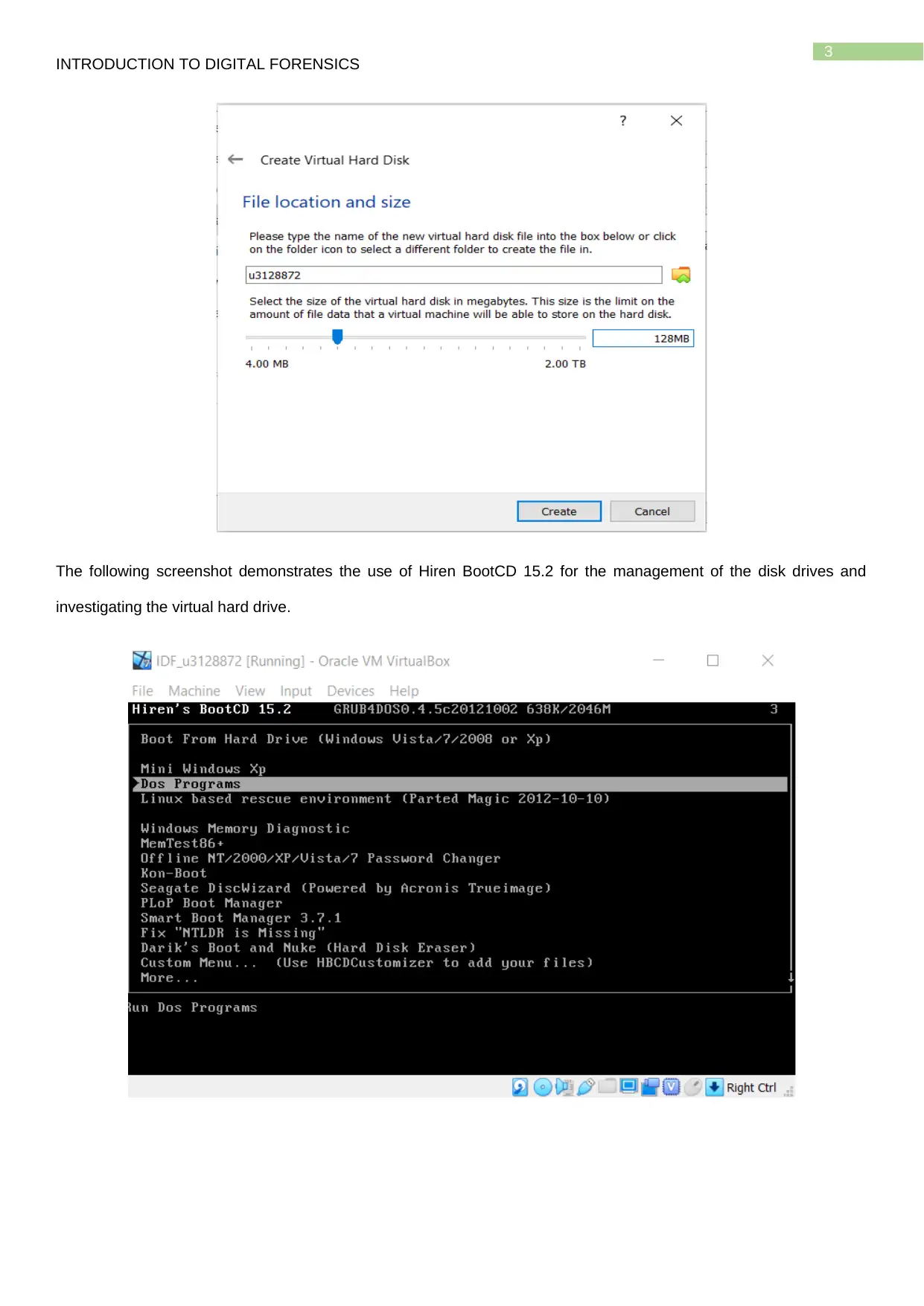
The following screenshot demonstrates the use of Hiren BootCD 15.2 for the management of the disk drives and
investigating the virtual hard drive.
INTRODUCTION TO DIGITAL FORENSICS
The following screenshot demonstrates the use of Hiren BootCD 15.2 for the management of the disk drives and
investigating the virtual hard drive.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTRODUCTION TO DIGITAL FORENSICS
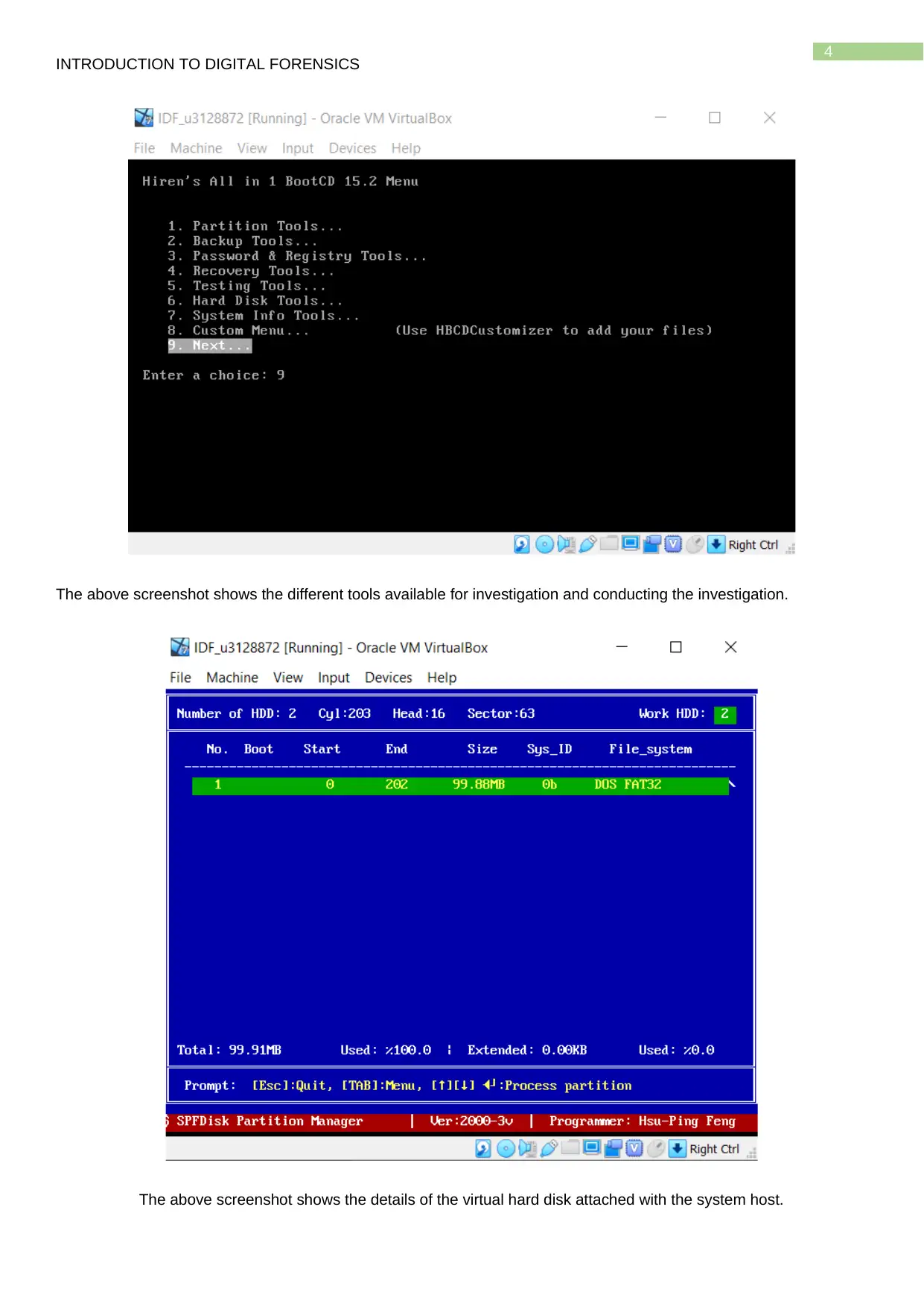
The above screenshot shows the different tools available for investigation and conducting the investigation.
The above screenshot shows the details of the virtual hard disk attached with the system host.
INTRODUCTION TO DIGITAL FORENSICS
The above screenshot shows the different tools available for investigation and conducting the investigation.
The above screenshot shows the details of the virtual hard disk attached with the system host.
5
INTRODUCTION TO DIGITAL FORENSICS
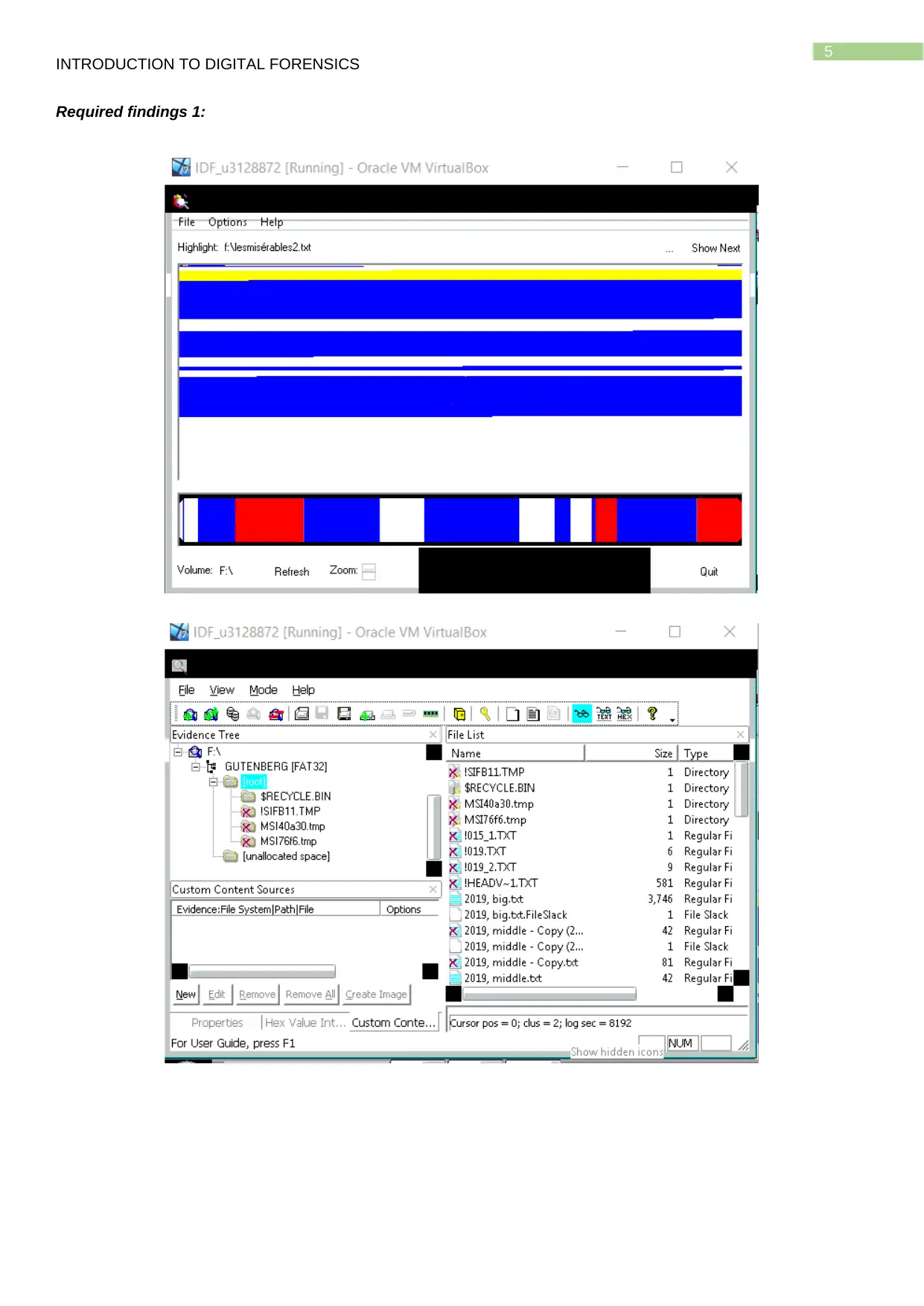
Required findings 1:
INTRODUCTION TO DIGITAL FORENSICS
Required findings 1:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTRODUCTION TO DIGITAL FORENSICS
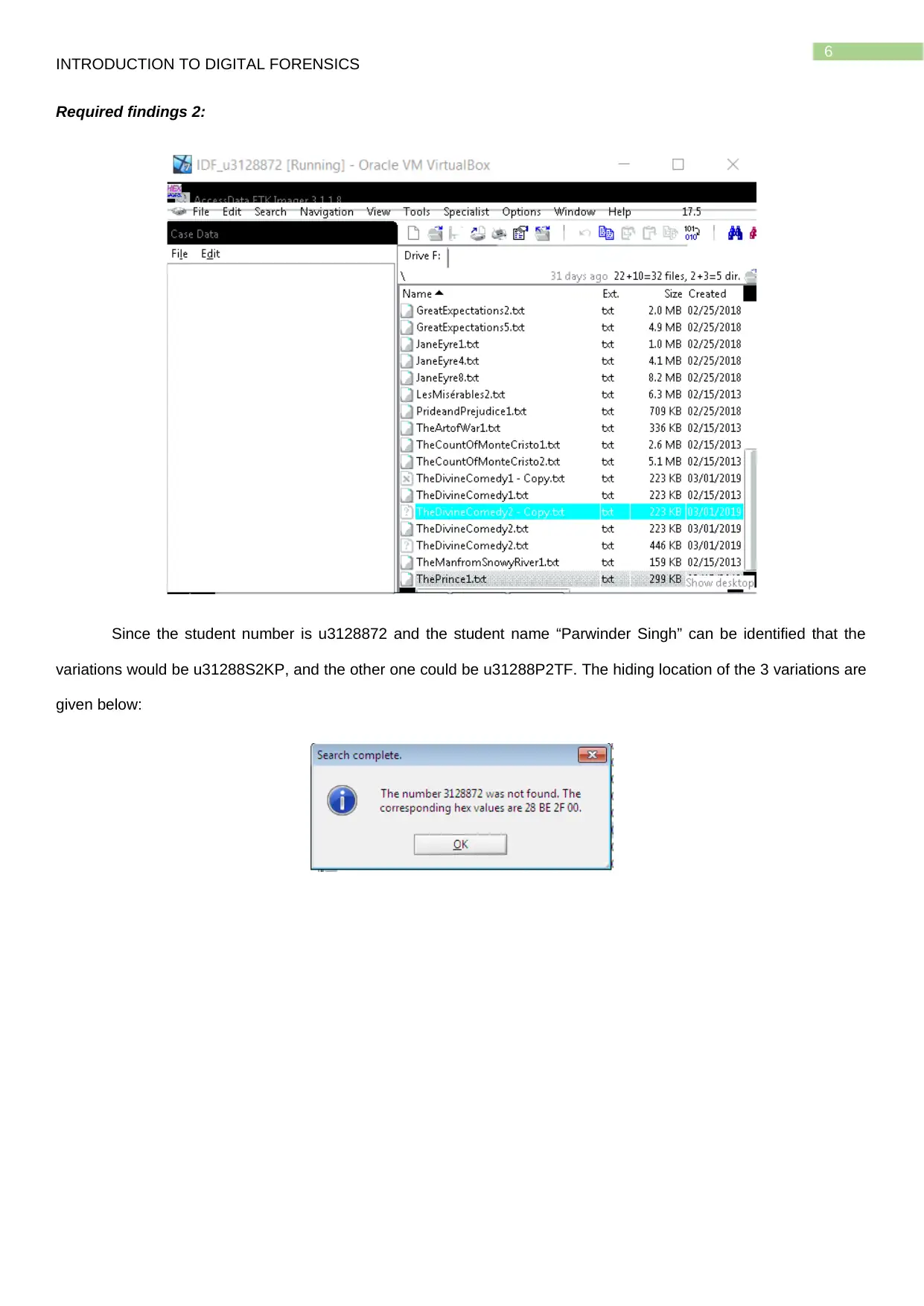
Required findings 2:
Since the student number is u3128872 and the student name “Parwinder Singh” can be identified that the
variations would be u31288S2KP, and the other one could be u31288P2TF. The hiding location of the 3 variations are
given below:
INTRODUCTION TO DIGITAL FORENSICS
Required findings 2:
Since the student number is u3128872 and the student name “Parwinder Singh” can be identified that the
variations would be u31288S2KP, and the other one could be u31288P2TF. The hiding location of the 3 variations are
given below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTRODUCTION TO DIGITAL FORENSICS
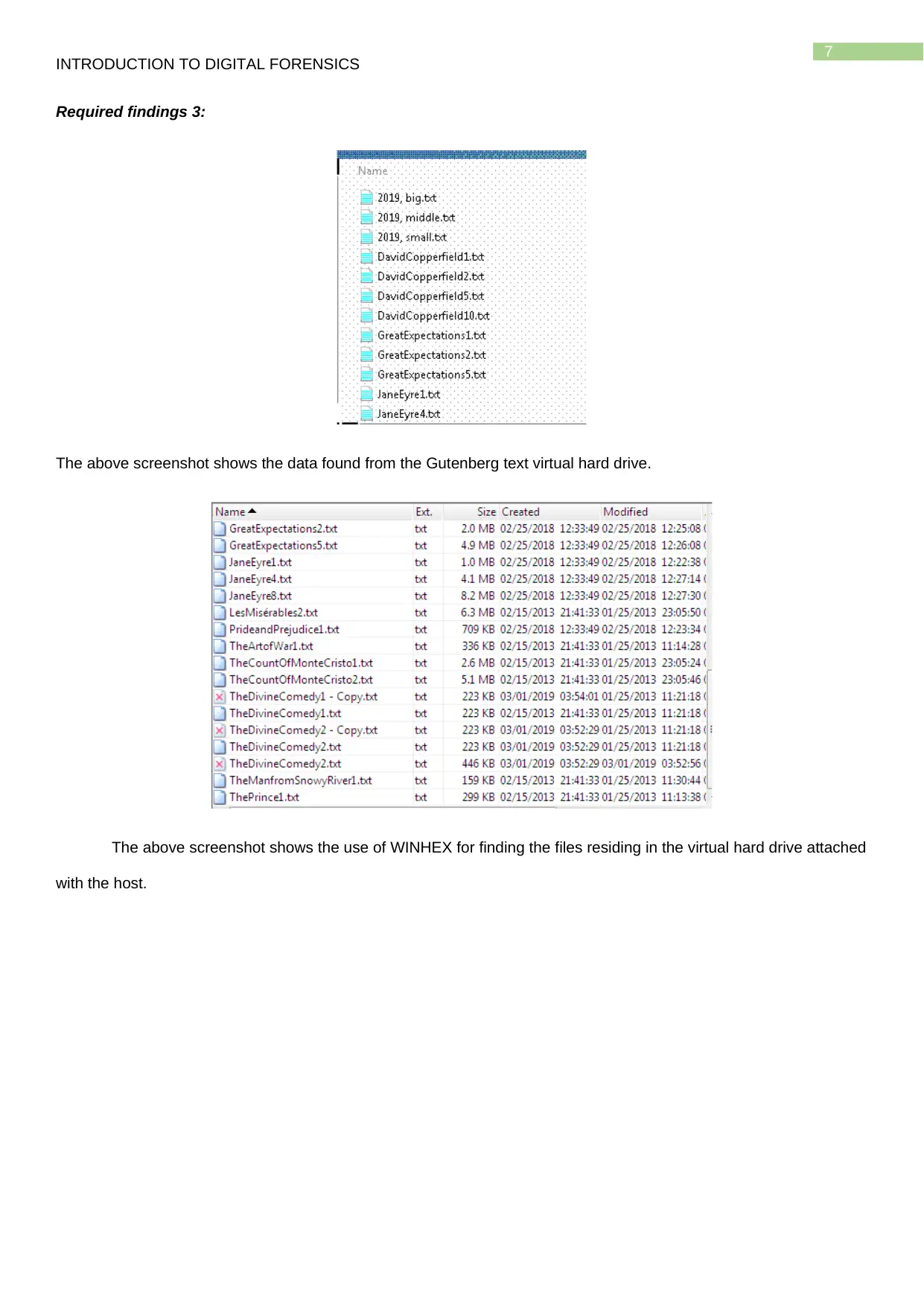
Required findings 3:
The above screenshot shows the data found from the Gutenberg text virtual hard drive.
The above screenshot shows the use of WINHEX for finding the files residing in the virtual hard drive attached
with the host.
INTRODUCTION TO DIGITAL FORENSICS
Required findings 3:
The above screenshot shows the data found from the Gutenberg text virtual hard drive.
The above screenshot shows the use of WINHEX for finding the files residing in the virtual hard drive attached
with the host.

8
INTRODUCTION TO DIGITAL FORENSICS
Bibliography
Ho, A.T. and Li, S. eds., 2015. Handbook of digital forensics of multimedia data and devices. John Wiley & Sons.
Shih, F.Y., 2017. Digital watermarking and steganography: fundamentals and techniques. CRC press.
INTRODUCTION TO DIGITAL FORENSICS
Bibliography
Ho, A.T. and Li, S. eds., 2015. Handbook of digital forensics of multimedia data and devices. John Wiley & Sons.
Shih, F.Y., 2017. Digital watermarking and steganography: fundamentals and techniques. CRC press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
