Digital Forensics Case Study: Analysis of Digital Evidence Report
VerifiedAdded on 2021/05/31
|19
|2945
|55
Case Study
AI Summary
This case study presents a digital forensics investigation involving a laptop and USB drive seized from Mr. William Watson at Melbourne Airport, who was suspected of carrying drugs. The report details the custody chain, imaging process using ProDiscover to create bit-by-bit copies, and the configuration of the seized laptop. The analysis focuses on data recovery using FTKImager, revealing deleted files and potential steganography within image files. The investigation uncovered transaction data and hidden text files within images using S-Tools, indicating attempts to conceal information. The findings highlight the use of digital forensics tools and techniques to uncover hidden evidence, with the ultimate goal of providing evidence for the crime investigators. The report concludes with a summary of the findings and the importance of the evidence in framing charges against the accused.
[Document title]
[Document subtitle]
[DATE]
[Company name]
[Company address]
[Document subtitle]
[DATE]
[Company name]
[Company address]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4

Task 1
Selecting the Modify Data option, select the left shift by 1 bit.
Output:
Selecting the Modify Data option, select the left shift by 1 bit.
Output:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
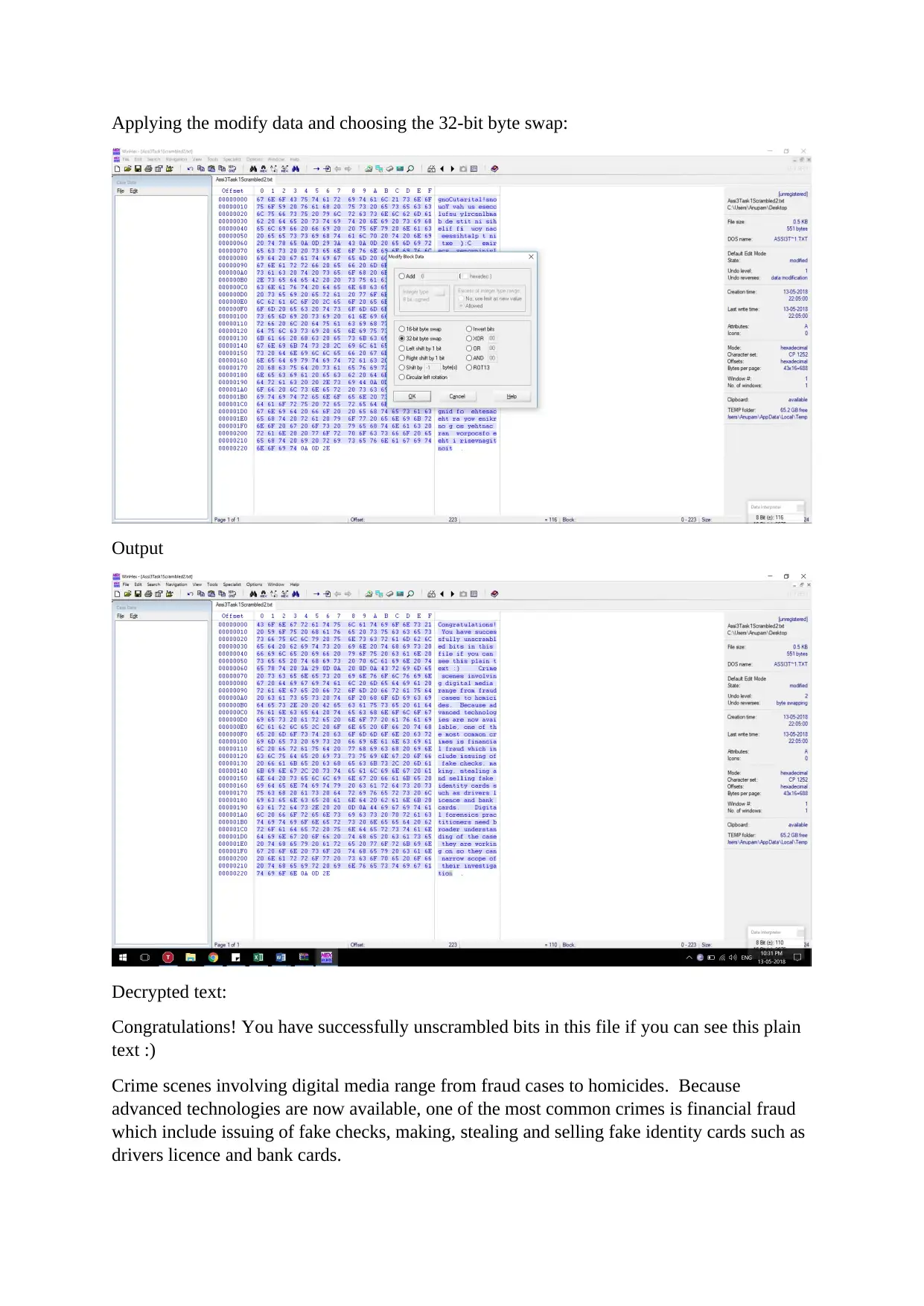
Applying the modify data and choosing the 32-bit byte swap:
Output
Decrypted text:
Congratulations! You have successfully unscrambled bits in this file if you can see this plain
text :)
Crime scenes involving digital media range from fraud cases to homicides. Because
advanced technologies are now available, one of the most common crimes is financial fraud
which include issuing of fake checks, making, stealing and selling fake identity cards such as
drivers licence and bank cards.
Output
Decrypted text:
Congratulations! You have successfully unscrambled bits in this file if you can see this plain
text :)
Crime scenes involving digital media range from fraud cases to homicides. Because
advanced technologies are now available, one of the most common crimes is financial fraud
which include issuing of fake checks, making, stealing and selling fake identity cards such as
drivers licence and bank cards.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital forensics practitioners need broader understanding of the case they are working on so
they can narrow scope of their investigation.
Task 2
Abstract
The digital investigation is about the digital device (Laptop) that was procured from the Mr.
William Watson at Melbourne Airport where he was arrested carrying drugs and other
malicious packets in his baggage. As Mr. William was returning from Pakistan (suspicious
originating country and under constant watch) and usually the passengers from such countries
are being under radar of the authorities for best reasons known to them. The digital devices
were procured were given for this digital forensic report and rest of the evidences were
handed over to narcotics department. The focus of the report is related to digital devices
procured from Mr. William Watson.
Introduction
The case is about the digital device that was procured from Mr. William Watson at
Melbourne airport where he was arrested with carrying drugs in his baggage, the evidence
was confiscated by Officer Paul Fleming. These digital devices were late handed over to
Officer Mr. Steve Taylor. The custody of the confiscated laptop is given below:
CUSTODY OF EXHIBIT
On 11th May 2018 at 23:45 the flight from Pakistan PKAU4355 landed at Melbourne Airport,
during the baggage scans some suspicious looking packages which were later confirm by
sniffer dogs were found, the baggage along with the owner of the baggage were immediately
stopped and during the further investigation apart from drugs some digital devices were being
also found, the devices which were found was a laptop from Dell make with model number
R15 7878 and Serial Number being RDFTRR44537585784 and charger for the laptop with
serial number C454563648. A USB storage device was also found with SanDisk make and
having serial number SUB345287695. (Morioka & Sharbaf, 2016)
they can narrow scope of their investigation.
Task 2
Abstract
The digital investigation is about the digital device (Laptop) that was procured from the Mr.
William Watson at Melbourne Airport where he was arrested carrying drugs and other
malicious packets in his baggage. As Mr. William was returning from Pakistan (suspicious
originating country and under constant watch) and usually the passengers from such countries
are being under radar of the authorities for best reasons known to them. The digital devices
were procured were given for this digital forensic report and rest of the evidences were
handed over to narcotics department. The focus of the report is related to digital devices
procured from Mr. William Watson.
Introduction
The case is about the digital device that was procured from Mr. William Watson at
Melbourne airport where he was arrested with carrying drugs in his baggage, the evidence
was confiscated by Officer Paul Fleming. These digital devices were late handed over to
Officer Mr. Steve Taylor. The custody of the confiscated laptop is given below:
CUSTODY OF EXHIBIT
On 11th May 2018 at 23:45 the flight from Pakistan PKAU4355 landed at Melbourne Airport,
during the baggage scans some suspicious looking packages which were later confirm by
sniffer dogs were found, the baggage along with the owner of the baggage were immediately
stopped and during the further investigation apart from drugs some digital devices were being
also found, the devices which were found was a laptop from Dell make with model number
R15 7878 and Serial Number being RDFTRR44537585784 and charger for the laptop with
serial number C454563648. A USB storage device was also found with SanDisk make and
having serial number SUB345287695. (Morioka & Sharbaf, 2016)

Analysis Conducted
The Laptop from Dell make with model number R15 7878 and Serial Number being
RDFTRR44537585784 and charger for the laptop with serial number C454563648 and a
USB storage device was also found with SanDisk make and having serial number
SUB345287695 were obtained. The laptop, charger and usb device were sealed together. The
hard-disk of the laptop and USB device storage were made copied using the ProDiscover
software using the bit by bit copy with write block hardware being used so that no accidental
as well as willing changes can be made to the storage devices. This is done in order to protect
the original devices and using the mirror image for the digital forensic purposes, so that
original devices and proofs can be preserved and they should be in the same state in which
they were being found. For backup multiple copies of the digital evidences would be made so
that devices are not being used again and again. (Shrivastava, Payal, Rastogi & Tiwari, 2013)
The evidence copy would be stored locally and in the secured cloud environment, this is done
to have the backup in case of any unwanted and unthinkable event to happen. The
configuration of the laptop that was being seized was:
Intel i7 qual core
1 TB HDD with single partition
4GB main memory
CD-ROM drive
15.6-inch screen
USB drive was of 8GB
The USB drive that was confiscated was empty and the image was created using the
ProDiscover software, using various retrieving and reading methods the USB drive was
cleanly formatted, this must have been done using a specialized software with writing the
entire disk with 0 bits. (Kumari & Mohapatra, 2016) The process followed from the imaging
purposes is as follows:
The Laptop from Dell make with model number R15 7878 and Serial Number being
RDFTRR44537585784 and charger for the laptop with serial number C454563648 and a
USB storage device was also found with SanDisk make and having serial number
SUB345287695 were obtained. The laptop, charger and usb device were sealed together. The
hard-disk of the laptop and USB device storage were made copied using the ProDiscover
software using the bit by bit copy with write block hardware being used so that no accidental
as well as willing changes can be made to the storage devices. This is done in order to protect
the original devices and using the mirror image for the digital forensic purposes, so that
original devices and proofs can be preserved and they should be in the same state in which
they were being found. For backup multiple copies of the digital evidences would be made so
that devices are not being used again and again. (Shrivastava, Payal, Rastogi & Tiwari, 2013)
The evidence copy would be stored locally and in the secured cloud environment, this is done
to have the backup in case of any unwanted and unthinkable event to happen. The
configuration of the laptop that was being seized was:
Intel i7 qual core
1 TB HDD with single partition
4GB main memory
CD-ROM drive
15.6-inch screen
USB drive was of 8GB
The USB drive that was confiscated was empty and the image was created using the
ProDiscover software, using various retrieving and reading methods the USB drive was
cleanly formatted, this must have been done using a specialized software with writing the
entire disk with 0 bits. (Kumari & Mohapatra, 2016) The process followed from the imaging
purposes is as follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In order to make the copy of the HDD the disk was mounted over the special HDD reader
which provides the no write operation switch, this means while copying the hard disk would
not be written over a single bit making it very important in such cases where the digital
devices should be procured using such hardware and software combination. The entire disk
was copied using the ProDiscover software read only mode make a double security layer to
protect digital devices being altered in any manner or unforeseen reason. (Mire, Dhok, Porey
& Mistry, 2014)
which provides the no write operation switch, this means while copying the hard disk would
not be written over a single bit making it very important in such cases where the digital
devices should be procured using such hardware and software combination. The entire disk
was copied using the ProDiscover software read only mode make a double security layer to
protect digital devices being altered in any manner or unforeseen reason. (Mire, Dhok, Porey
& Mistry, 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
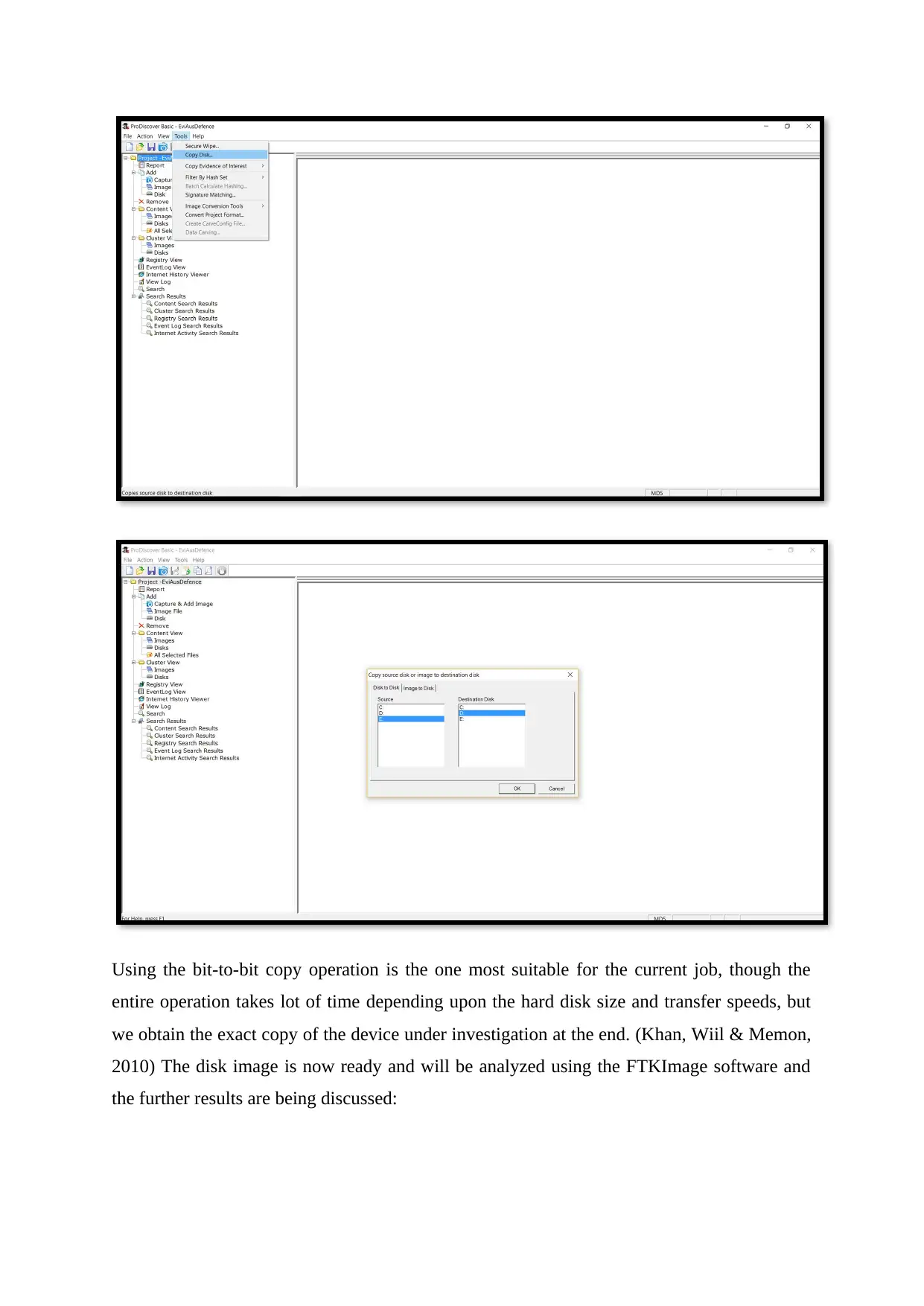
Using the bit-to-bit copy operation is the one most suitable for the current job, though the
entire operation takes lot of time depending upon the hard disk size and transfer speeds, but
we obtain the exact copy of the device under investigation at the end. (Khan, Wiil & Memon,
2010) The disk image is now ready and will be analyzed using the FTKImage software and
the further results are being discussed:
entire operation takes lot of time depending upon the hard disk size and transfer speeds, but
we obtain the exact copy of the device under investigation at the end. (Khan, Wiil & Memon,
2010) The disk image is now ready and will be analyzed using the FTKImage software and
the further results are being discussed:
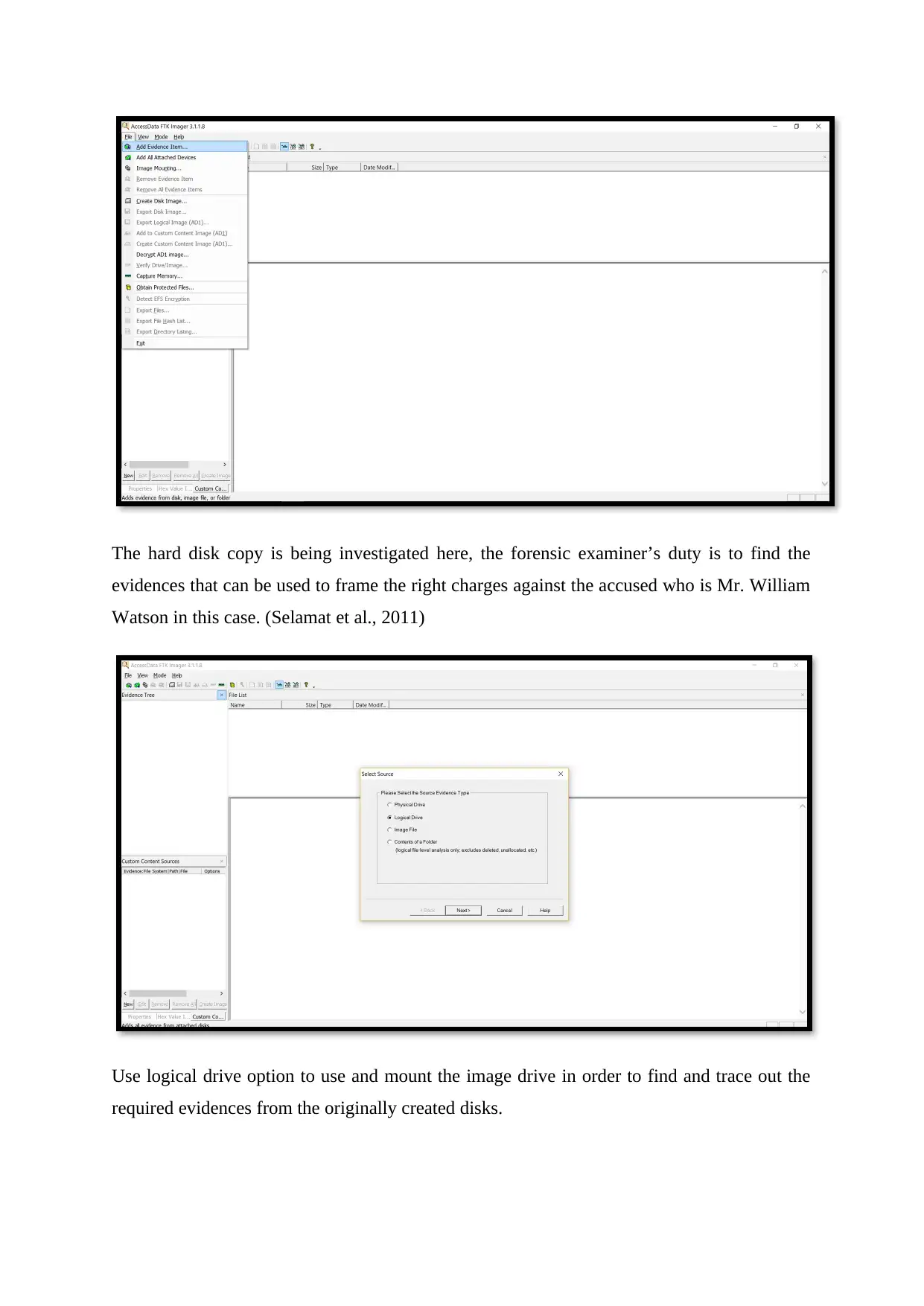
The hard disk copy is being investigated here, the forensic examiner’s duty is to find the
evidences that can be used to frame the right charges against the accused who is Mr. William
Watson in this case. (Selamat et al., 2011)
Use logical drive option to use and mount the image drive in order to find and trace out the
required evidences from the originally created disks.
evidences that can be used to frame the right charges against the accused who is Mr. William
Watson in this case. (Selamat et al., 2011)
Use logical drive option to use and mount the image drive in order to find and trace out the
required evidences from the originally created disks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
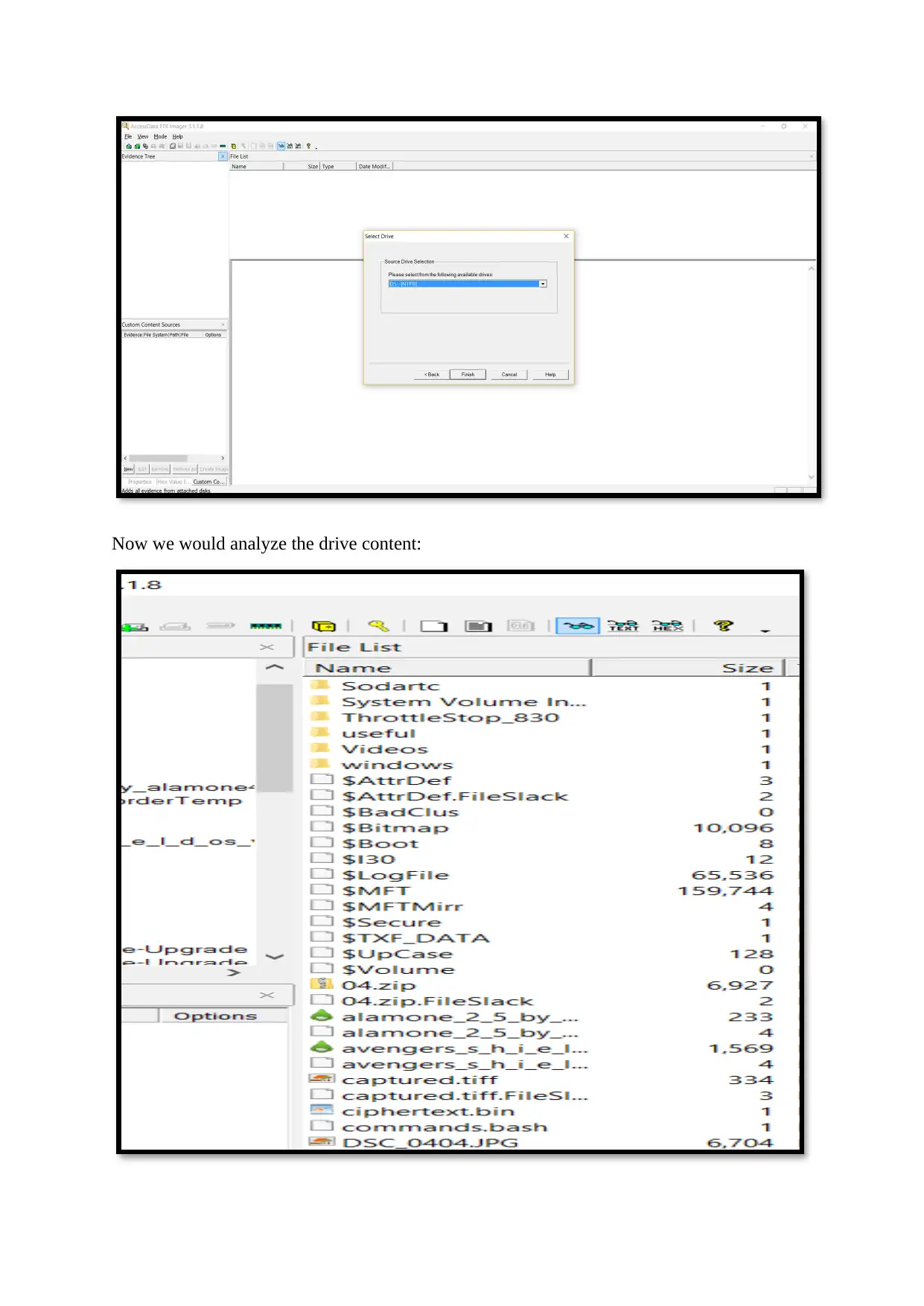
Now we would analyze the drive content:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
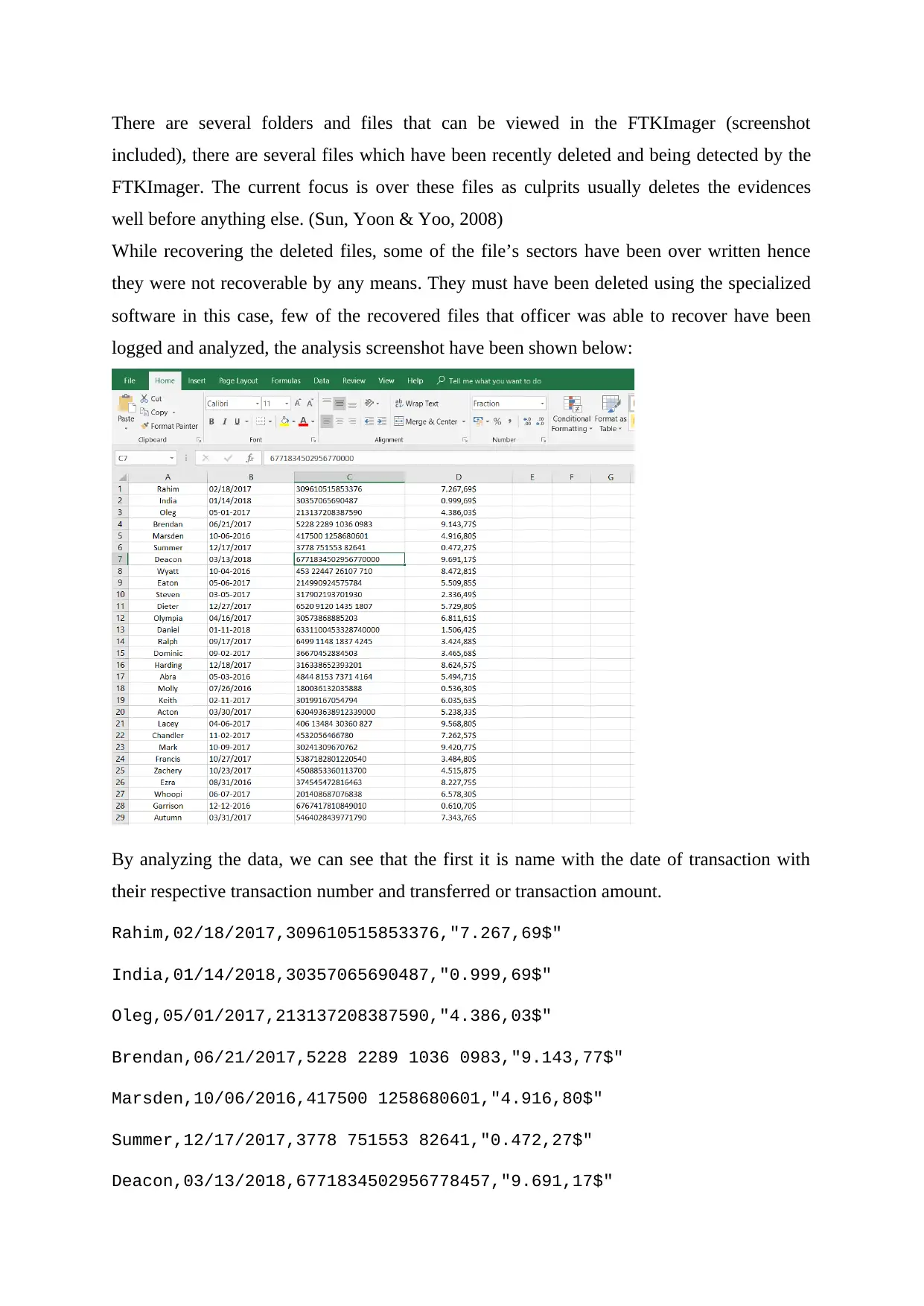
There are several folders and files that can be viewed in the FTKImager (screenshot
included), there are several files which have been recently deleted and being detected by the
FTKImager. The current focus is over these files as culprits usually deletes the evidences
well before anything else. (Sun, Yoon & Yoo, 2008)
While recovering the deleted files, some of the file’s sectors have been over written hence
they were not recoverable by any means. They must have been deleted using the specialized
software in this case, few of the recovered files that officer was able to recover have been
logged and analyzed, the analysis screenshot have been shown below:
By analyzing the data, we can see that the first it is name with the date of transaction with
their respective transaction number and transferred or transaction amount.
Rahim,02/18/2017,309610515853376,"7.267,69$"
India,01/14/2018,30357065690487,"0.999,69$"
Oleg,05/01/2017,213137208387590,"4.386,03$"
Brendan,06/21/2017,5228 2289 1036 0983,"9.143,77$"
Marsden,10/06/2016,417500 1258680601,"4.916,80$"
Summer,12/17/2017,3778 751553 82641,"0.472,27$"
Deacon,03/13/2018,6771834502956778457,"9.691,17$"
included), there are several files which have been recently deleted and being detected by the
FTKImager. The current focus is over these files as culprits usually deletes the evidences
well before anything else. (Sun, Yoon & Yoo, 2008)
While recovering the deleted files, some of the file’s sectors have been over written hence
they were not recoverable by any means. They must have been deleted using the specialized
software in this case, few of the recovered files that officer was able to recover have been
logged and analyzed, the analysis screenshot have been shown below:
By analyzing the data, we can see that the first it is name with the date of transaction with
their respective transaction number and transferred or transaction amount.
Rahim,02/18/2017,309610515853376,"7.267,69$"
India,01/14/2018,30357065690487,"0.999,69$"
Oleg,05/01/2017,213137208387590,"4.386,03$"
Brendan,06/21/2017,5228 2289 1036 0983,"9.143,77$"
Marsden,10/06/2016,417500 1258680601,"4.916,80$"
Summer,12/17/2017,3778 751553 82641,"0.472,27$"
Deacon,03/13/2018,6771834502956778457,"9.691,17$"

Wyatt,10/04/2016,453 22447 26107 710,"8.472,81$"
Eaton,05/06/2017,214990924575784,"5.509,85$"
Steven,03/05/2017,317902193701930,"2.336,49$"
Dieter,12/27/2017,6520 9120 1435 1807,"5.729,80$"
Olympia,04/16/2017,30573868885203,"6.811,61$"
Daniel,01/11/2018,6331100453328746964,"1.506,42$"
Ralph,09/17/2017,6499 1148 1837 4245,"3.424,88$"
Dominic,09/02/2017,36670452884503,"3.465,68$"
Harding,12/18/2017,316338652393201,"8.624,57$"
Abra,05/03/2016,4844 8153 7371 4164,"5.494,71$"
Molly,07/26/2016,180036132035888,"0.536,30$"
Keith,02/11/2017,30199167054794,"6.035,63$"
Acton,03/30/2017,630493638912339988,"5.238,33$"
Lacey,04/06/2017,406 13484 30360 827,"9.568,80$"
Chandler,11/02/2017,4532056466780,"7.262,57$"
Mark,10/09/2017,30241309670762,"9.420,77$"
Francis,10/27/2017,5387182801220540,"3.484,80$"
Zachery,10/23/2017,4508853360113709,"4.515,87$"
Ezra,08/31/2016,374545472816463,"8.227,75$"
Whoopi,06/07/2017,201408687076838,"6.578,30$"
Garrison,12/12/2016,6767417810849014,"0.610,70$"
Autumn,03/31/2017,5464028439771790,"7.343,76$"
Orla,03/03/2017,490556382211885184,"7.062,42$"
Deacon,08/13/2017,4916293280320,"3.920,70$"
Todd,07/18/2017,633385106638291300,"8.138,93$"
Maxwell,02/03/2017,373597377846179,"0.654,56$"
Eaton,05/06/2017,214990924575784,"5.509,85$"
Steven,03/05/2017,317902193701930,"2.336,49$"
Dieter,12/27/2017,6520 9120 1435 1807,"5.729,80$"
Olympia,04/16/2017,30573868885203,"6.811,61$"
Daniel,01/11/2018,6331100453328746964,"1.506,42$"
Ralph,09/17/2017,6499 1148 1837 4245,"3.424,88$"
Dominic,09/02/2017,36670452884503,"3.465,68$"
Harding,12/18/2017,316338652393201,"8.624,57$"
Abra,05/03/2016,4844 8153 7371 4164,"5.494,71$"
Molly,07/26/2016,180036132035888,"0.536,30$"
Keith,02/11/2017,30199167054794,"6.035,63$"
Acton,03/30/2017,630493638912339988,"5.238,33$"
Lacey,04/06/2017,406 13484 30360 827,"9.568,80$"
Chandler,11/02/2017,4532056466780,"7.262,57$"
Mark,10/09/2017,30241309670762,"9.420,77$"
Francis,10/27/2017,5387182801220540,"3.484,80$"
Zachery,10/23/2017,4508853360113709,"4.515,87$"
Ezra,08/31/2016,374545472816463,"8.227,75$"
Whoopi,06/07/2017,201408687076838,"6.578,30$"
Garrison,12/12/2016,6767417810849014,"0.610,70$"
Autumn,03/31/2017,5464028439771790,"7.343,76$"
Orla,03/03/2017,490556382211885184,"7.062,42$"
Deacon,08/13/2017,4916293280320,"3.920,70$"
Todd,07/18/2017,633385106638291300,"8.138,93$"
Maxwell,02/03/2017,373597377846179,"0.654,56$"
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

