Case Study: Digital Forensics Investigation of ETMS Data Breach
VerifiedAdded on 2021/06/14
|18
|2330
|179
Case Study
AI Summary
This case study presents a digital forensics investigation into a potential intellectual property theft at Exotic Mountain Tour Services (ETMS). The investigation focuses on the analysis of emails and a USB drive belonging to a contract employee, Bob Aspen, suspected of leaking sensitive data. The analysis utilizes forensic tools such as ProDiscover and WinHex to recover and examine data, including image files with altered headers. The process involves searching for specific keywords, recovering file fragments, and repairing file headers to make the data viewable. The findings suggest that the employee was indeed attempting to leak ETMS's intellectual property, leading to a conclusion that highlights the importance of forensic tools in identifying data breaches and protecting sensitive information.
[Document title]
[Document subtitle]
[DATE]
[Company name]
[Company address]
[Document subtitle]
[DATE]
[Company name]
[Company address]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Abstract..................................................................................................................................4
Introduction............................................................................................................................4
Analysis conducted................................................................................................................5
Findings................................................................................................................................16
References............................................................................................................................17
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Abstract..................................................................................................................................4
Introduction............................................................................................................................4
Analysis conducted................................................................................................................5
Findings................................................................................................................................16
References............................................................................................................................17

Task 1
The WinHex is the software tool used by forensic experts around the world for various
purposes like to repair headers of files, editing the files in binary mode and scrambling of
data which can only be reversed if the correct order is known. In order to recover the
scrambled bits we need to do the following:
Modify Data-> “left shift by 1-bit option”
Output:
The WinHex is the software tool used by forensic experts around the world for various
purposes like to repair headers of files, editing the files in binary mode and scrambling of
data which can only be reversed if the correct order is known. In order to recover the
scrambled bits we need to do the following:
Modify Data-> “left shift by 1-bit option”
Output:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
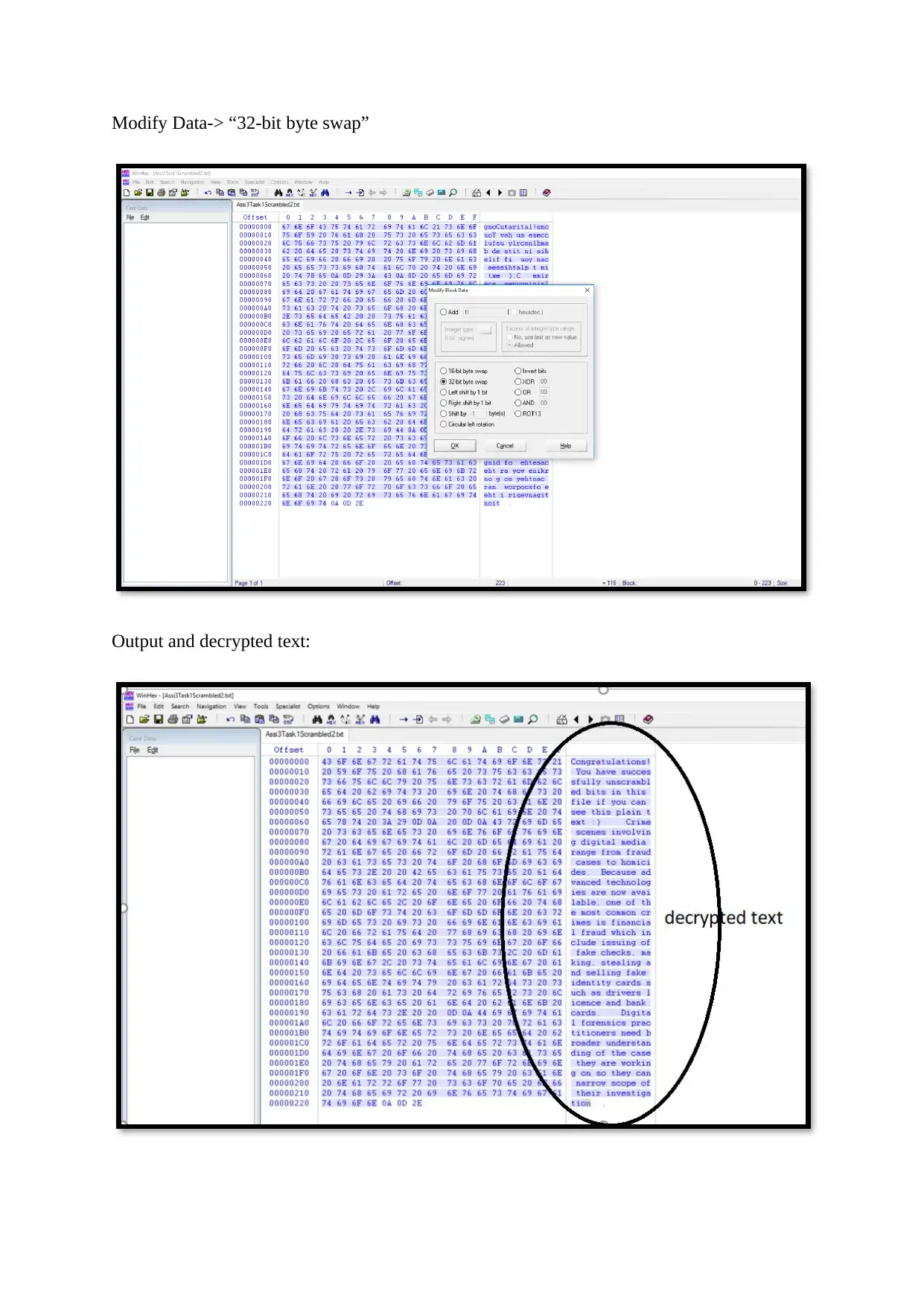
Modify Data-> “32-bit byte swap”
Output and decrypted text:
Output and decrypted text:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 2
Abstract
The case is about the possible theft of intellectual property by a contract employee of Exotic
Mountain Tour Services (ETMS), the intellectual property is the secret data that might have
been leaked by the employee to competitor who might mitigate the entire project survey done
by the ETMS along with the Superior Bicycles, LLC. The leak if true might lead to severe
loss of revenue to ETMS as they might lose out to competition their strategic advantage
gained from the survey and its results. The leak came into picture when two of the emails of
the contract employee were filtered out and the emails contained some suspicious
conversation that might have led to deliberate leakage of critical intellectual property data.
There was USB drive that was also found on the contract employee’s desk, which was
handed over for further investigations and data that was recovered from the USB drive can
help in framing correct charges against the culprit Bob Aspen.
Introduction
There are two major software that are used in the forensic investigations ProDiscover and
WinHex, both serving a desired important purpose and complementing each other. Thought
there are many different software available for the same purpose but the number of features
provided by them, make them stand out comparing to the competition.
The ProDiscover is the software that is used to develop the copies of images or disks
(physical storage media), these images are used to read sectors and clusters as desired for the
purpose of recovering of data and information regarding recovering of data from different
clusters. Thought there are number of other features that are used by forensic experts but we
use these features of this case study. The ProDiscover is also compatible with number of
other hardware as well like write block that means the process of image creation will not
affect the original device, this feature is very critical as in few cases the original device needs
to remain in the same condition as it was being found.
When the data is being recovered by the forensic expert using the ProDiscover but usually the
files have their header or some part of data corrupted or even sometimes the header of the
files have been manually altered in order to bypass major filters in organizations. The
WinHex forensic tool comes in picture for this special purpose itself, it can alter or edit the
data of files in binary mode hence managing the data like edit, copy, delete, paste, insert etc.
Abstract
The case is about the possible theft of intellectual property by a contract employee of Exotic
Mountain Tour Services (ETMS), the intellectual property is the secret data that might have
been leaked by the employee to competitor who might mitigate the entire project survey done
by the ETMS along with the Superior Bicycles, LLC. The leak if true might lead to severe
loss of revenue to ETMS as they might lose out to competition their strategic advantage
gained from the survey and its results. The leak came into picture when two of the emails of
the contract employee were filtered out and the emails contained some suspicious
conversation that might have led to deliberate leakage of critical intellectual property data.
There was USB drive that was also found on the contract employee’s desk, which was
handed over for further investigations and data that was recovered from the USB drive can
help in framing correct charges against the culprit Bob Aspen.
Introduction
There are two major software that are used in the forensic investigations ProDiscover and
WinHex, both serving a desired important purpose and complementing each other. Thought
there are many different software available for the same purpose but the number of features
provided by them, make them stand out comparing to the competition.
The ProDiscover is the software that is used to develop the copies of images or disks
(physical storage media), these images are used to read sectors and clusters as desired for the
purpose of recovering of data and information regarding recovering of data from different
clusters. Thought there are number of other features that are used by forensic experts but we
use these features of this case study. The ProDiscover is also compatible with number of
other hardware as well like write block that means the process of image creation will not
affect the original device, this feature is very critical as in few cases the original device needs
to remain in the same condition as it was being found.
When the data is being recovered by the forensic expert using the ProDiscover but usually the
files have their header or some part of data corrupted or even sometimes the header of the
files have been manually altered in order to bypass major filters in organizations. The
WinHex forensic tool comes in picture for this special purpose itself, it can alter or edit the
data of files in binary mode hence managing the data like edit, copy, delete, paste, insert etc.

of data in binary mode is made possible using this tool. This tool in simple terms can be
viewed as the binary mode editor using hexadecimal values just like any word editor that
works majorly on ASCII values. There are several types of views available like cluster view,
tree view etc. that can help in finding the related data quite simple and efficient for any
forensic expert. Generating checksum and digest of the data is quite useful tool along with
that the reporting can be done using HTML or RTF based format that is beneficial for any
forensic expert delivering important findings in their final reports sometimes.
Analysis conducted
The initial findings of the emails that were being communicated by the Bob Aspen the
contract employee at ETMS outside the ETMS official known circle were found later in the
screening of emails for all the accounts of the organization. Apart from the emails the USB
drive was also recovered form the Bob Aspen’s desk and its was being suspicious for a
contract employee to being storage device to the company having strict policy for data and
intellectual property. The emails were being scanned and with the help of traced emails, it
was clear that the contract employee was indeed trying to leak the data to one of the
competitor of the ETMS and data was altered before being send out in order to escape the
filtering policy of the organization to send an email with attachment. The emails were being
communicated to terrysadler@groowy.com to and from baspen@aol.com which meets the
Bob Aspen details registered at the organization. The emails coming from
terrysadler@groowy.com were coming from Jim Shu, the time stamp forwarded messages
were little off that means the Jim Shu must be from different time zone and must be from
western corner of the world as the timestamps are being assigned by the servers not users.
The email conversation also asked the employee to alter the extension from jpg to txt and
header information as well in order to bypass the email scanners easily.
Search for and Recovering Digital photography Evidence
This section we would be recovering the image file from the USB drive image that was being
provided by the ETMS. The initial recovering of data from the file is to search the keyword in
ASCII mode with case sensitive match of “FIF”, the reason to use “FIF” not JPEG or JFIF is
that this might lead to find the clusters with lots of previous files that might have been stored
on the USB drive. These clusters of old files are known as false positive that may lead to lost
of unwanted data to be screened by the forensic expert and ultimately leading to loss of time
and effort.
viewed as the binary mode editor using hexadecimal values just like any word editor that
works majorly on ASCII values. There are several types of views available like cluster view,
tree view etc. that can help in finding the related data quite simple and efficient for any
forensic expert. Generating checksum and digest of the data is quite useful tool along with
that the reporting can be done using HTML or RTF based format that is beneficial for any
forensic expert delivering important findings in their final reports sometimes.
Analysis conducted
The initial findings of the emails that were being communicated by the Bob Aspen the
contract employee at ETMS outside the ETMS official known circle were found later in the
screening of emails for all the accounts of the organization. Apart from the emails the USB
drive was also recovered form the Bob Aspen’s desk and its was being suspicious for a
contract employee to being storage device to the company having strict policy for data and
intellectual property. The emails were being scanned and with the help of traced emails, it
was clear that the contract employee was indeed trying to leak the data to one of the
competitor of the ETMS and data was altered before being send out in order to escape the
filtering policy of the organization to send an email with attachment. The emails were being
communicated to terrysadler@groowy.com to and from baspen@aol.com which meets the
Bob Aspen details registered at the organization. The emails coming from
terrysadler@groowy.com were coming from Jim Shu, the time stamp forwarded messages
were little off that means the Jim Shu must be from different time zone and must be from
western corner of the world as the timestamps are being assigned by the servers not users.
The email conversation also asked the employee to alter the extension from jpg to txt and
header information as well in order to bypass the email scanners easily.
Search for and Recovering Digital photography Evidence
This section we would be recovering the image file from the USB drive image that was being
provided by the ETMS. The initial recovering of data from the file is to search the keyword in
ASCII mode with case sensitive match of “FIF”, the reason to use “FIF” not JPEG or JFIF is
that this might lead to find the clusters with lots of previous files that might have been stored
on the USB drive. These clusters of old files are known as false positive that may lead to lost
of unwanted data to be screened by the forensic expert and ultimately leading to loss of time
and effort.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
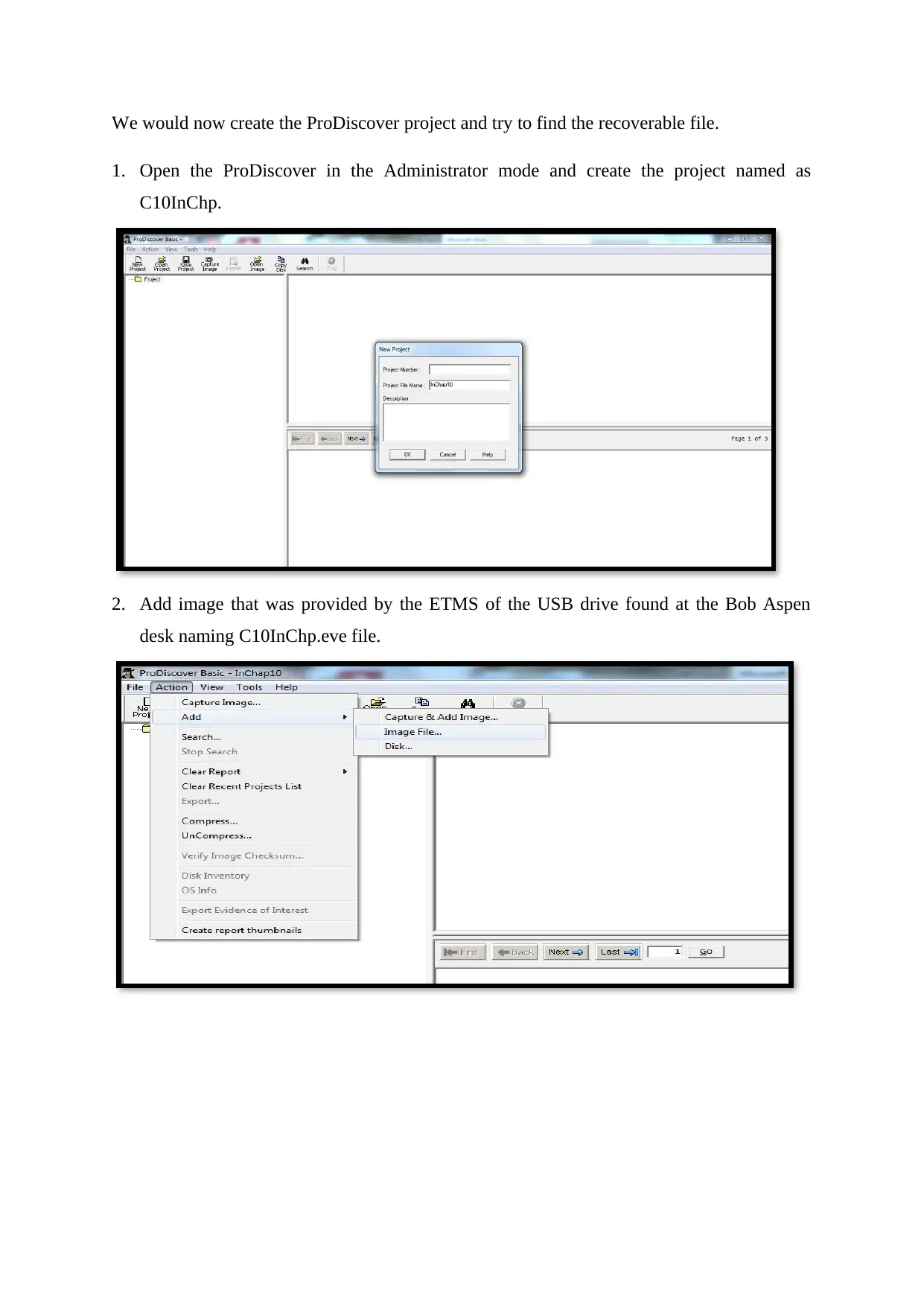
We would now create the ProDiscover project and try to find the recoverable file.
1. Open the ProDiscover in the Administrator mode and create the project named as
C10InChp.
2. Add image that was provided by the ETMS of the USB drive found at the Bob Aspen
desk naming C10InChp.eve file.
1. Open the ProDiscover in the Administrator mode and create the project named as
C10InChp.
2. Add image that was provided by the ETMS of the USB drive found at the Bob Aspen
desk naming C10InChp.eve file.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
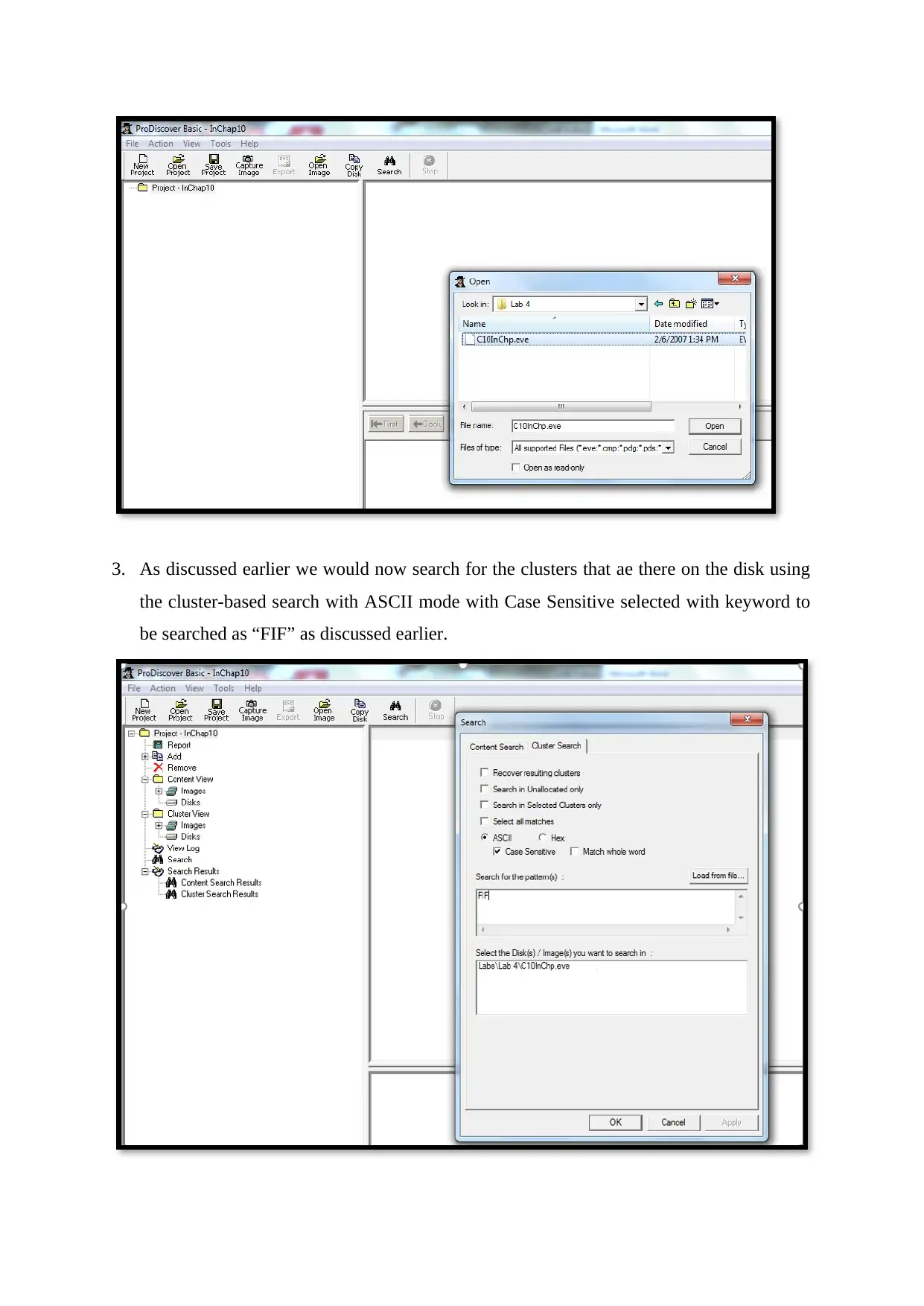
3. As discussed earlier we would now search for the clusters that ae there on the disk using
the cluster-based search with ASCII mode with Case Sensitive selected with keyword to
be searched as “FIF” as discussed earlier.
the cluster-based search with ASCII mode with Case Sensitive selected with keyword to
be searched as “FIF” as discussed earlier.
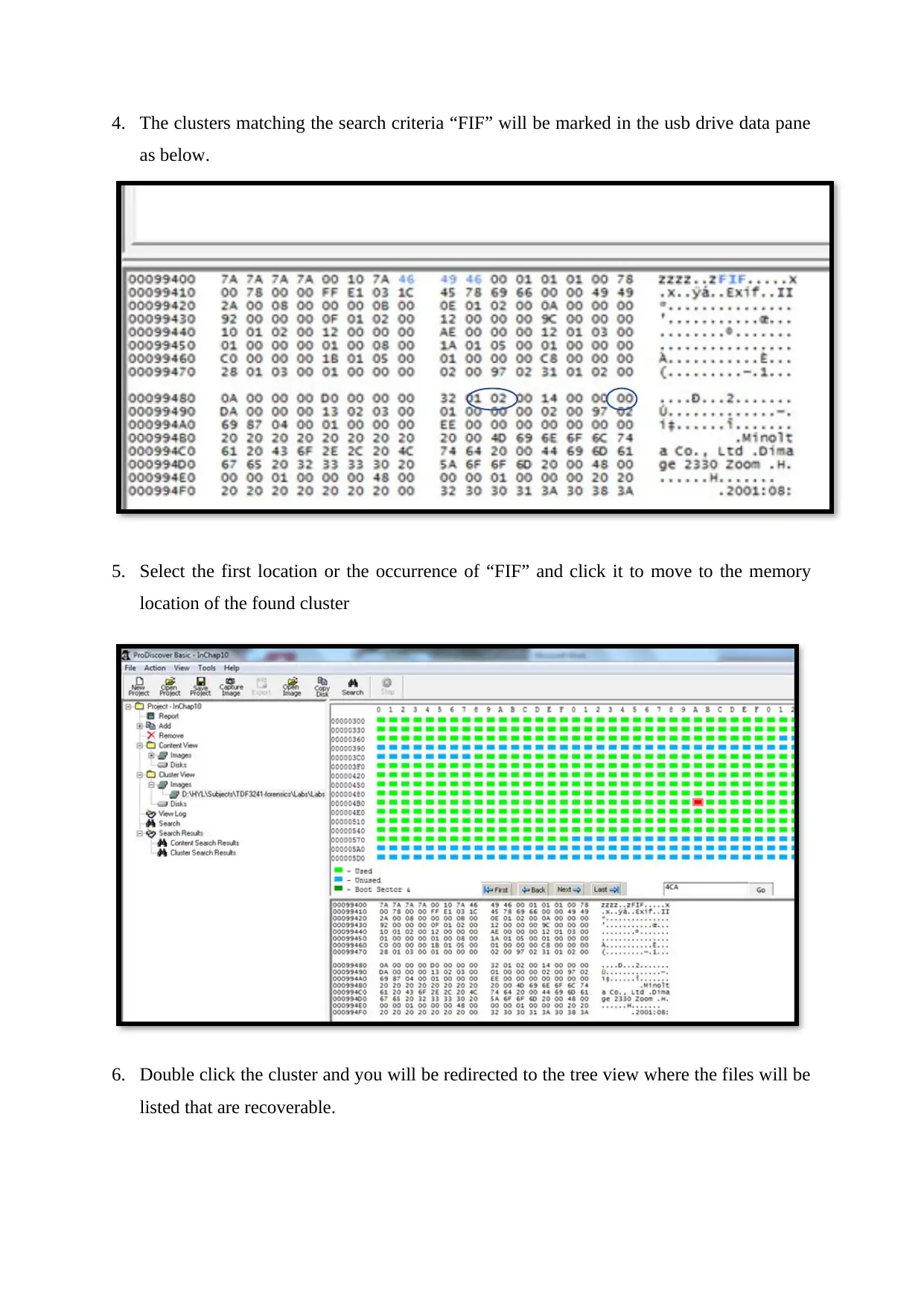
4. The clusters matching the search criteria “FIF” will be marked in the usb drive data pane
as below.
5. Select the first location or the occurrence of “FIF” and click it to move to the memory
location of the found cluster
6. Double click the cluster and you will be redirected to the tree view where the files will be
listed that are recoverable.
as below.
5. Select the first location or the occurrence of “FIF” and click it to move to the memory
location of the found cluster
6. Double click the cluster and you will be redirected to the tree view where the files will be
listed that are recoverable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
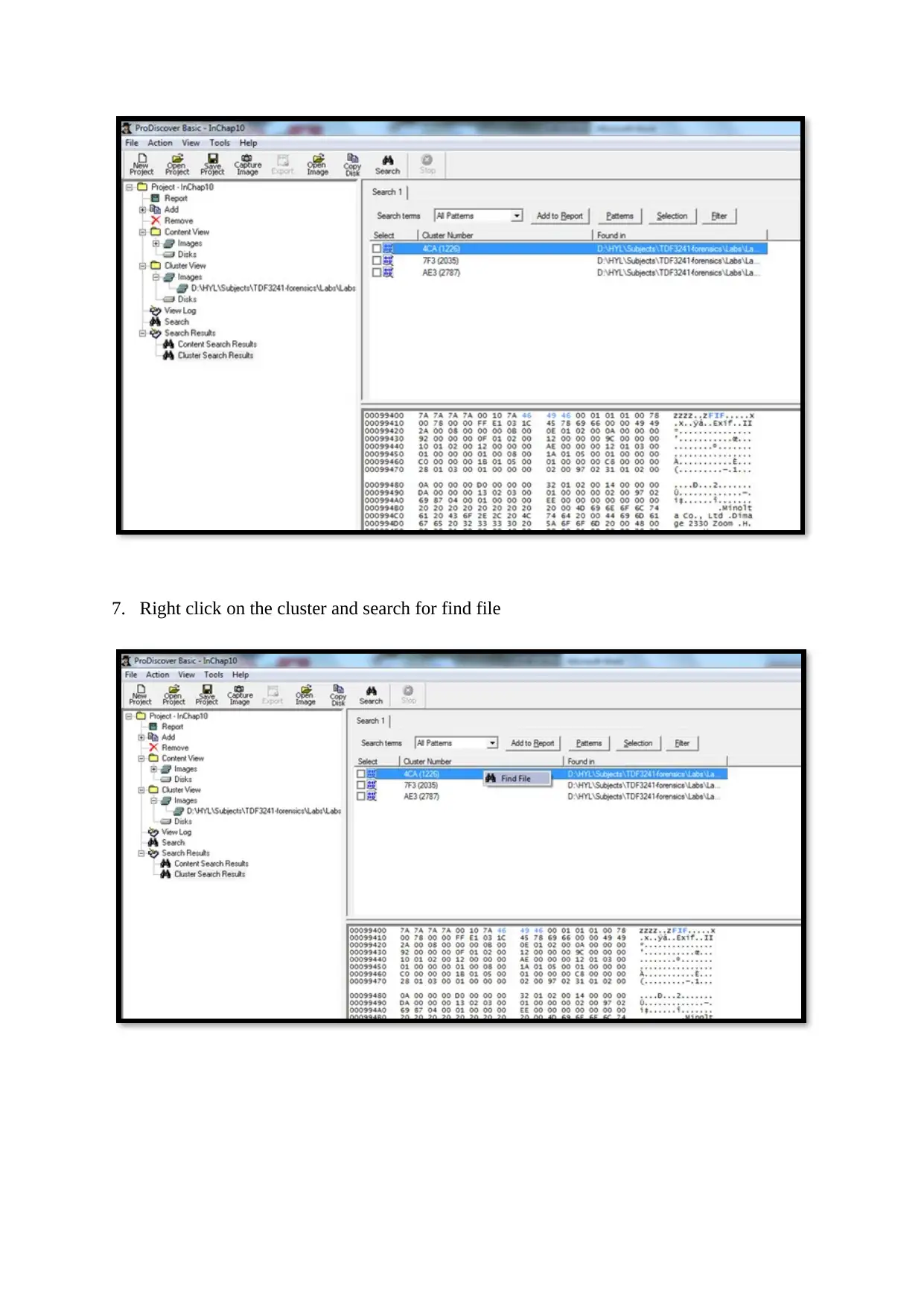
7. Right click on the cluster and search for find file
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
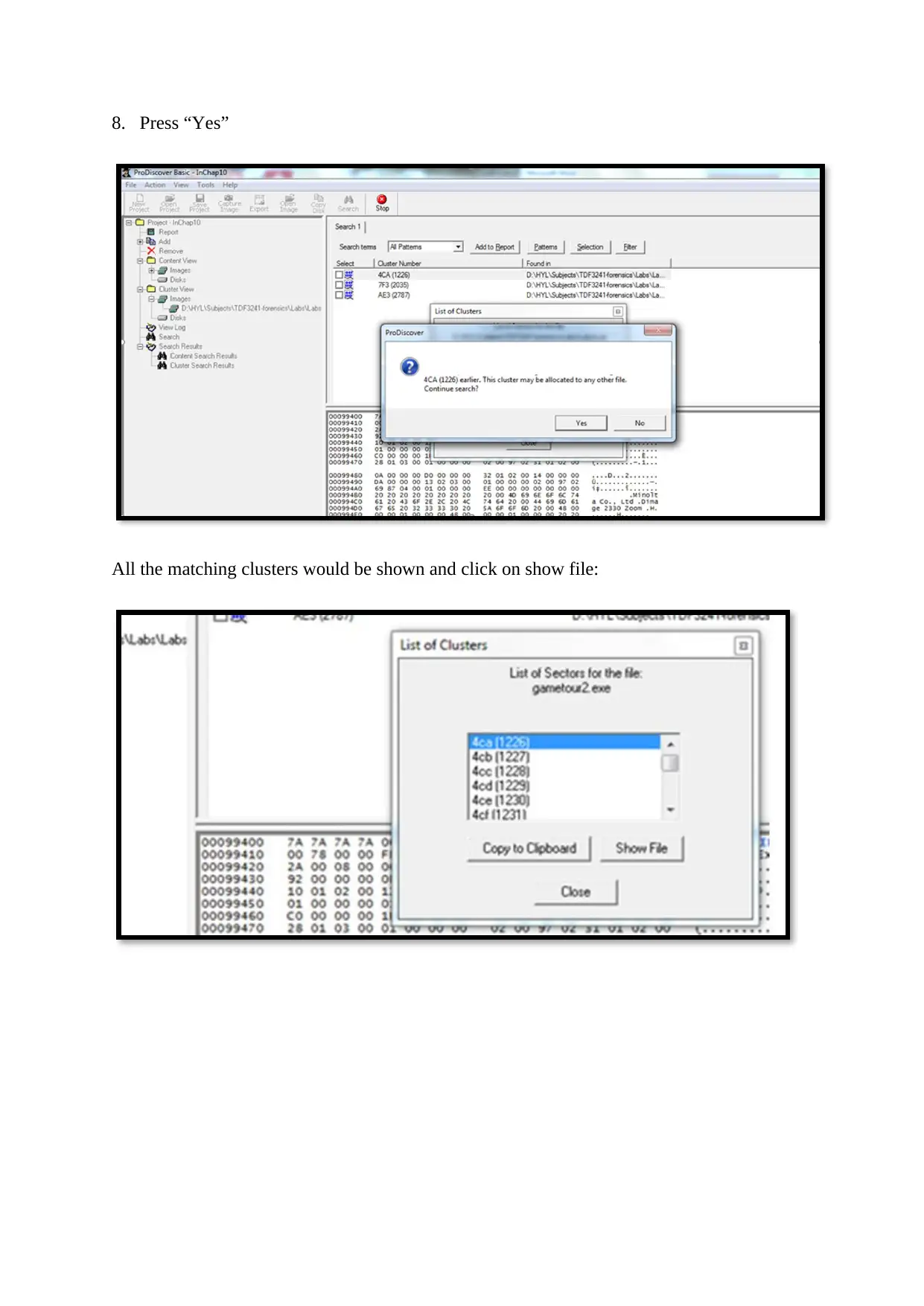
8. Press “Yes”
All the matching clusters would be shown and click on show file:
All the matching clusters would be shown and click on show file:
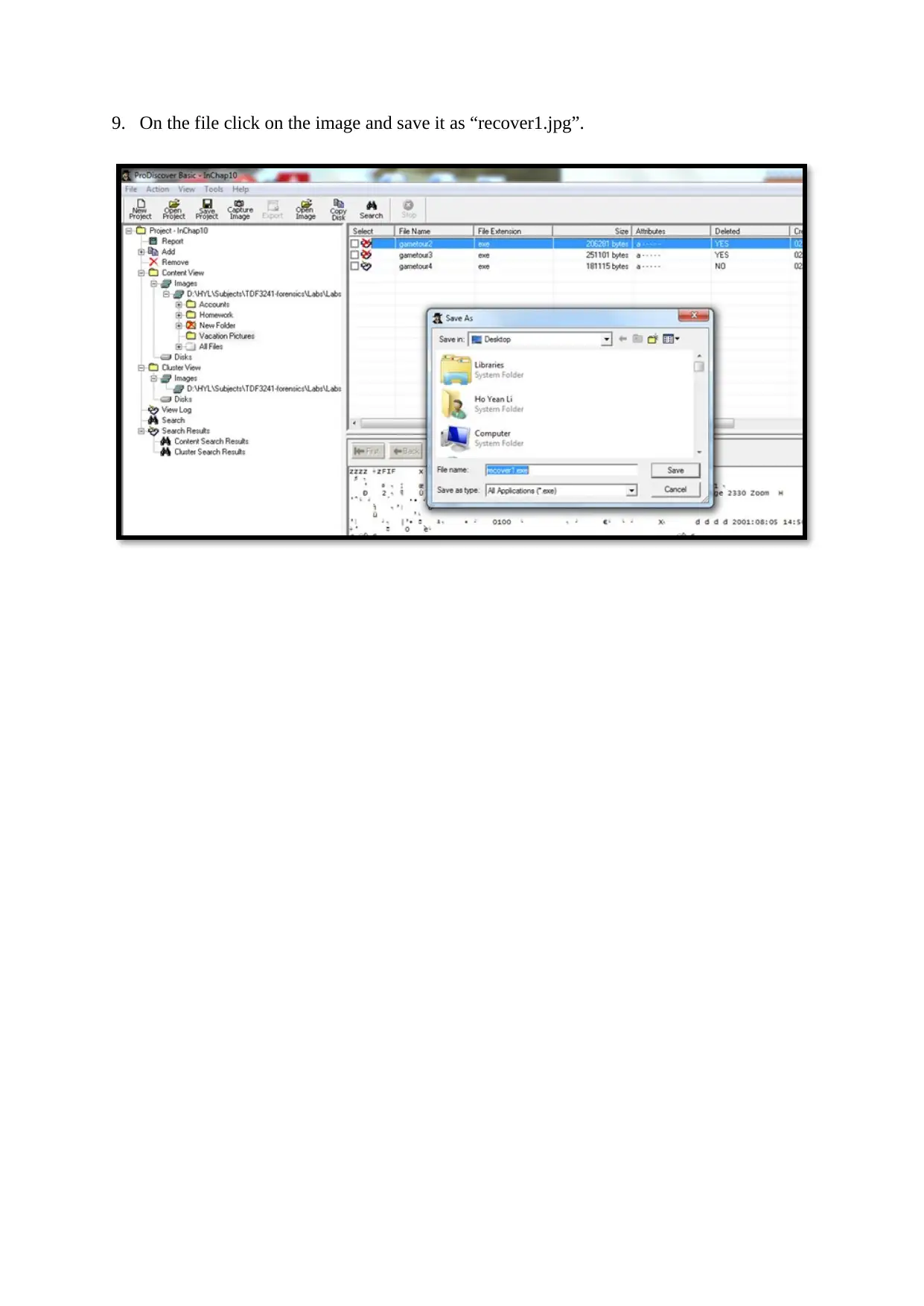
9. On the file click on the image and save it as “recover1.jpg”.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


