COIT20267: Computer Forensics Case Study and Investigation Plan
VerifiedAdded on 2022/10/02
|15
|4933
|158
Case Study
AI Summary
This case study examines a computer forensics investigation at Creative Minds, a technology company in Australia. Following a network breach and suspected sabotage after the firing of an IT manager, the assignment outlines a detailed digital forensics investigation plan. The plan encompasses the collection and analysis of digital evidence from servers, personal computers, email accounts, social media, and cloud storage. It justifies the use of digital forensics over other methods, describes necessary skills, software, and hardware, and details the identification, acquisition, and evaluation of evidence. The case study also provides steps for network analysis and offers recommendations for preventing future cybercrimes, demonstrating a comprehensive approach to cybersecurity and forensic analysis within a corporate setting. The report also discusses various digital forensics methodologies, including Kruise & Heiser Model and the Systematic Digital Forensics Investigation Model (SRDFIM), highlighting their steps and importance in evidence collection, preservation, and analysis.

Running Head: COMPUTER FORENSICS 1
Name:
Tutor:
Date:
Institution:
Name:
Tutor:
Date:
Institution:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER FORENSICS 2
EXECUTIVE SUMMARY
A case study of a technology company in Australia which produces a wide variety of
computers and office equipment for businesses, that is, the Creative Minds, was conducted. The
company lost focus on the application frame and upgrading the networks. This led to users
accessing systems and servers from different offices with no restrictions. Due to the unrestricted
network environment, loggings and intrusion detection were implemented on the system, causing
malfunction (Bradley et al., 2016). At the headquarters harassment complaints from several
female workers were reported leading to the firing of the store information technology manager
from his job. After firing the information technology manager, the next day, the employees
realized that the computer networks were not operating and the servers had been formatted.
Basing on the previous issue, the fired information technology manager was suspected, even
though the surveillance cameras had no evidence of his involvement.
Following the crime in the company, I have been obligated by the management to form a
team of investigators of computer forensics and dig into the crime. This will be by analyzing
digital forensic that involves collecting digital evidence from servers, personal computers, and
email accounts, analyzing the network, conducting social media, and cloud investigation (Maras
2015). For it to be a successful and subsequent, a detailed computer forensics investigation plan
must be developed. This plan must provide relevant policies of security for the Creative Minds
technology company (Schory et al.,2015). A justified summary of the main procedures for the
crime investigation and why use digital forensics approach is highly acceptable besides other
methods is included. A description of the required skills, software, and hardware to conduct the
digital forensic investigation of the crime is also necessary. An outline for the identification of
evidence and acquisition that should happen to identify and evaluate the digital evidence
collected should be provided (Quick & Choo 2018). Another overview of steps and procedures
to be used during the analysis of the network that explains the requirements of the servers,
emails, personal computers, cloud, and social media investigation is also provided (Rathore
2017). Moreover, recommendations for future crimes that may arise in the technology company
are also listed.
TABLE OF CONTENTS
EXECUTIVE SUMMARY
A case study of a technology company in Australia which produces a wide variety of
computers and office equipment for businesses, that is, the Creative Minds, was conducted. The
company lost focus on the application frame and upgrading the networks. This led to users
accessing systems and servers from different offices with no restrictions. Due to the unrestricted
network environment, loggings and intrusion detection were implemented on the system, causing
malfunction (Bradley et al., 2016). At the headquarters harassment complaints from several
female workers were reported leading to the firing of the store information technology manager
from his job. After firing the information technology manager, the next day, the employees
realized that the computer networks were not operating and the servers had been formatted.
Basing on the previous issue, the fired information technology manager was suspected, even
though the surveillance cameras had no evidence of his involvement.
Following the crime in the company, I have been obligated by the management to form a
team of investigators of computer forensics and dig into the crime. This will be by analyzing
digital forensic that involves collecting digital evidence from servers, personal computers, and
email accounts, analyzing the network, conducting social media, and cloud investigation (Maras
2015). For it to be a successful and subsequent, a detailed computer forensics investigation plan
must be developed. This plan must provide relevant policies of security for the Creative Minds
technology company (Schory et al.,2015). A justified summary of the main procedures for the
crime investigation and why use digital forensics approach is highly acceptable besides other
methods is included. A description of the required skills, software, and hardware to conduct the
digital forensic investigation of the crime is also necessary. An outline for the identification of
evidence and acquisition that should happen to identify and evaluate the digital evidence
collected should be provided (Quick & Choo 2018). Another overview of steps and procedures
to be used during the analysis of the network that explains the requirements of the servers,
emails, personal computers, cloud, and social media investigation is also provided (Rathore
2017). Moreover, recommendations for future crimes that may arise in the technology company
are also listed.
TABLE OF CONTENTS

COMPUTER FORENSICS 3
INTRODUCTION...........................................................................................................................................3
JUSTIFICATION OF THE METHODOLOGY USED IN DIGITAL FORENSICS.......................................................5
RESOURCES REQUIRED TO CARRY OUT THE DIGITAL FORENSICS................................................................9
SECURITY POLICIES TO BE IMPLEMENTED.................................................................................................11
RECOMMENDATIONS................................................................................................................................11
CONCLUSION.............................................................................................................................................12
INTRODUCTION...........................................................................................................................................3
JUSTIFICATION OF THE METHODOLOGY USED IN DIGITAL FORENSICS.......................................................5
RESOURCES REQUIRED TO CARRY OUT THE DIGITAL FORENSICS................................................................9
SECURITY POLICIES TO BE IMPLEMENTED.................................................................................................11
RECOMMENDATIONS................................................................................................................................11
CONCLUSION.............................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER FORENSICS 4
INTRODUCTION
When cybercrimes are committed, for instance, the crime of computers that the
technology company in Australia is facing, an investigation is conducted. It will be done by
applying scientific methods and approaches to this issue using a court of law (Zawoad & Hasan
2015). The most appropriate application is computer forensic. It involves examination of digital
devices and methodologies to identify, preserve, retrace, analyze, and present evidence in a
proper way for presentation in the court of law. Computer forensics requires a few methods for
investigation according to the requirement of the law. Some of them include deleted files, cross
drive analysis, live analysis, stochastic forensics, and steganography. Having a number of these
methodologies maximizes on detailed information that helps in analyzing the crime (Boroumand,
Chen & Fridrich 2018). In our case study, it was found out that after the firing of the Information
Technology manager, a crime occurred. The technological company suspected the former
Information Manager, but for clarity, investigations had to be done. This was to point out
answers on how it happened and give recommendations to prevent such a crime from happening
again. They assigned me the task of conducting them liaising with the interrogative experts. I had
to come up with a plan that will help me in the computer forensics investigations
Preparations for these investigations, the plan should fit some requirements listed. For its
effectiveness, I should adopt the different methodologies that ensure the systematic flow and
success of the investigations. One of the methods outshines the others, and much is reflected in
it. This report provides an analysis of the findings of the Creative Minds company that includes
the crime that the company is facing. A summary of the examined evidence is also presented and
the primary strategy to be used, that is, the digital forensics methodology. Being a technological
company, this kind of crime is likely to happen. Thus recommendations on how to avoid this
kind of crime from happening again in the future are well discussed in detail.
BODY OF THE REPORT
It is crucial for an organization to have a useful and practical approach towards how they
can prevent or even learn about cyber threats that may be facing them (Bays ea tl., 2015). If an
organization should be faced with a security issue, those responsible for investigating the root of
the problem are supposed to follow a well-structured, informed, and effective approach towards
resolving this matter (Vincze 2016). Good cybersecurity practices are valuable and critical for all
INTRODUCTION
When cybercrimes are committed, for instance, the crime of computers that the
technology company in Australia is facing, an investigation is conducted. It will be done by
applying scientific methods and approaches to this issue using a court of law (Zawoad & Hasan
2015). The most appropriate application is computer forensic. It involves examination of digital
devices and methodologies to identify, preserve, retrace, analyze, and present evidence in a
proper way for presentation in the court of law. Computer forensics requires a few methods for
investigation according to the requirement of the law. Some of them include deleted files, cross
drive analysis, live analysis, stochastic forensics, and steganography. Having a number of these
methodologies maximizes on detailed information that helps in analyzing the crime (Boroumand,
Chen & Fridrich 2018). In our case study, it was found out that after the firing of the Information
Technology manager, a crime occurred. The technological company suspected the former
Information Manager, but for clarity, investigations had to be done. This was to point out
answers on how it happened and give recommendations to prevent such a crime from happening
again. They assigned me the task of conducting them liaising with the interrogative experts. I had
to come up with a plan that will help me in the computer forensics investigations
Preparations for these investigations, the plan should fit some requirements listed. For its
effectiveness, I should adopt the different methodologies that ensure the systematic flow and
success of the investigations. One of the methods outshines the others, and much is reflected in
it. This report provides an analysis of the findings of the Creative Minds company that includes
the crime that the company is facing. A summary of the examined evidence is also presented and
the primary strategy to be used, that is, the digital forensics methodology. Being a technological
company, this kind of crime is likely to happen. Thus recommendations on how to avoid this
kind of crime from happening again in the future are well discussed in detail.
BODY OF THE REPORT
It is crucial for an organization to have a useful and practical approach towards how they
can prevent or even learn about cyber threats that may be facing them (Bays ea tl., 2015). If an
organization should be faced with a security issue, those responsible for investigating the root of
the problem are supposed to follow a well-structured, informed, and effective approach towards
resolving this matter (Vincze 2016). Good cybersecurity practices are valuable and critical for all
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER FORENSICS 5
organizations irrespective of their size (Baig EA TL.,2017). In an organization, security controls
and the general configuration of the information technology environment are deeply analyzed in
order to obtain information and gather evidence in case of cybercrime. This process of collecting
digital data and evidence to determine the extent of damage caused by cybercrime or find out
who was behind the attack is known as digital forensics. With digital forensics, you can
determine what happened during a specific period and attribute this action to a particular person
(Holt, Bossler & Seigfried-Spellar 2017). And with such information, appropriate measures can
be undertaken. This kind of forensics depends on the acquisition and analysis of data in a
systematic approach that allows evidence to be obtained from the computer systems (Zawoad &
Hasan 2015).
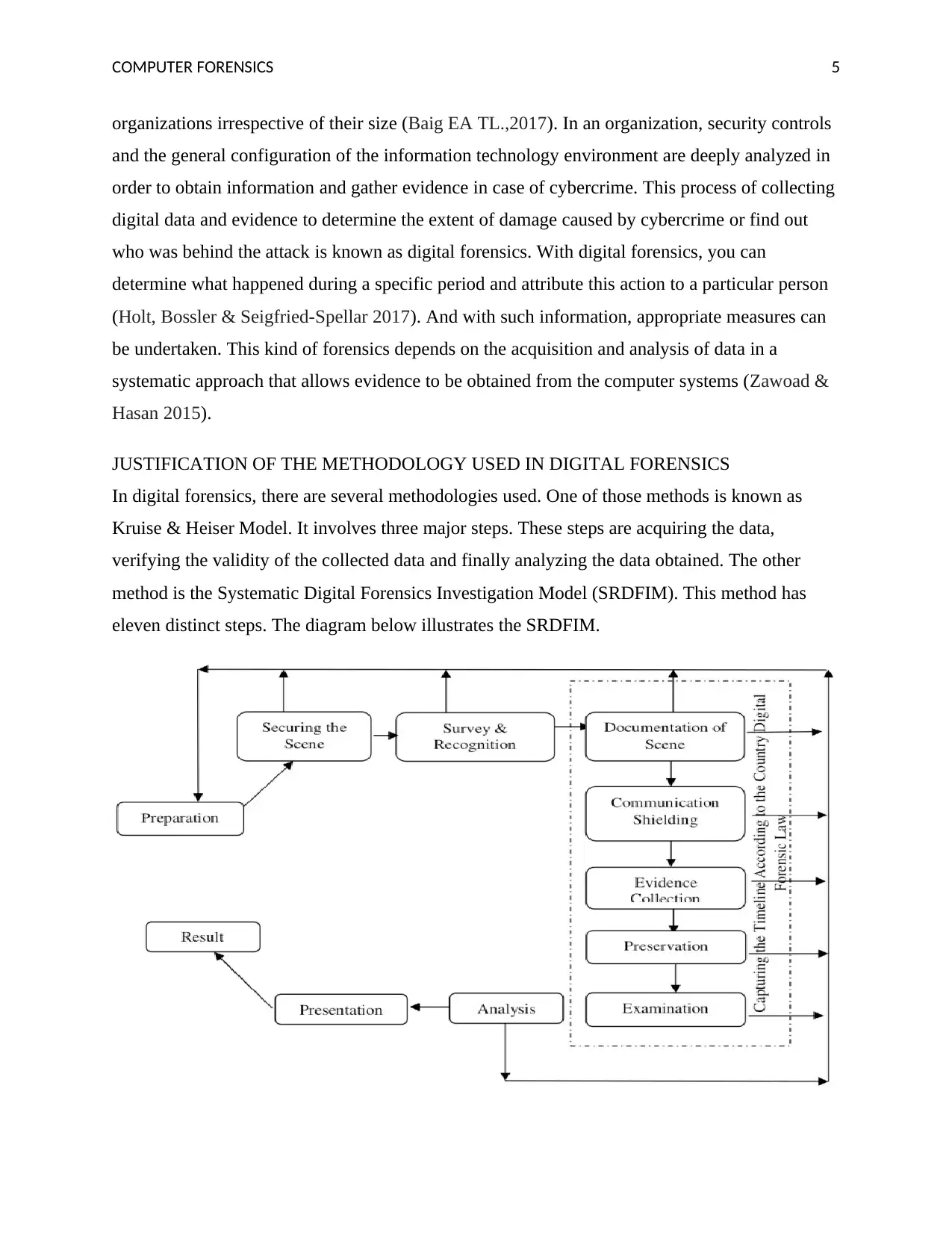
JUSTIFICATION OF THE METHODOLOGY USED IN DIGITAL FORENSICS
In digital forensics, there are several methodologies used. One of those methods is known as
Kruise & Heiser Model. It involves three major steps. These steps are acquiring the data,
verifying the validity of the collected data and finally analyzing the data obtained. The other
method is the Systematic Digital Forensics Investigation Model (SRDFIM). This method has
eleven distinct steps. The diagram below illustrates the SRDFIM.
organizations irrespective of their size (Baig EA TL.,2017). In an organization, security controls
and the general configuration of the information technology environment are deeply analyzed in
order to obtain information and gather evidence in case of cybercrime. This process of collecting
digital data and evidence to determine the extent of damage caused by cybercrime or find out
who was behind the attack is known as digital forensics. With digital forensics, you can
determine what happened during a specific period and attribute this action to a particular person
(Holt, Bossler & Seigfried-Spellar 2017). And with such information, appropriate measures can
be undertaken. This kind of forensics depends on the acquisition and analysis of data in a
systematic approach that allows evidence to be obtained from the computer systems (Zawoad &
Hasan 2015).
JUSTIFICATION OF THE METHODOLOGY USED IN DIGITAL FORENSICS
In digital forensics, there are several methodologies used. One of those methods is known as
Kruise & Heiser Model. It involves three major steps. These steps are acquiring the data,
verifying the validity of the collected data and finally analyzing the data obtained. The other
method is the Systematic Digital Forensics Investigation Model (SRDFIM). This method has
eleven distinct steps. The diagram below illustrates the SRDFIM.

COMPUTER FORENSICS 6
i) Step one –Preparation
This stage involves understanding the nature of the crime and the activities involved. Materials
for packing the evidence are also obtained in this stage. Before proceeding to the scene of the
crime, it is mandatory to have a search warrant, as well as the required authorizations. A legal
notice should be issued to all parties affected indicating there will be a forensics investigation
around. It is very important that a strategy for that very investigation be prepared taking into
account the nature of that crime and other legal and corporate factors. This phase happens to be
important because it increases the quality of the evidence obtained and minimize the risks that
may rise during the investigation.
ii) Step two- Securing the scene
This stage deals with protecting the scene of crime from an unauthorized access and preserving
the evidence to avoid contamination. It is the duty of the investigator to identify the scope of the
crime and establish the perimeter. The priority at this stage, is to ensure that all people in the
scene are safe and the integrity of the evidence obtained is maintained. The investigator should
take control of the scene and no unauthorized personnel should be allowed to interfere so as to
minimize the chances of evidence corruption or destruction. Anything that could be part of the
evidence should not be interfered with to make sure that the evidence obtained is quality.
iii) Step three- Survey and recognition
This is where the investigators conduct the initial survey of the scene of crime. It is crucial in
order to identify potential sources of evidence and develop an effective plan for the investigation.
The investigators must obtain maximum information from the people in the crime of scene
without violating any jurisdictional laws or corporate policies. Electronic equipment at the scene
of crime are also evaluated. If a need arises to search for items that are not included in the search
warranty, it is important that the current warrant be amended to include these items. A plan for
collecting and analyzing evidence is developed at this stage.
iv) Step four- Documenting the scene.
This stage involves documentation of the scene of crime as well as photographing, sketching and
crime scene mapping. Electronic gadgets that are in the scene of crime must be photographed
i) Step one –Preparation
This stage involves understanding the nature of the crime and the activities involved. Materials
for packing the evidence are also obtained in this stage. Before proceeding to the scene of the
crime, it is mandatory to have a search warrant, as well as the required authorizations. A legal
notice should be issued to all parties affected indicating there will be a forensics investigation
around. It is very important that a strategy for that very investigation be prepared taking into
account the nature of that crime and other legal and corporate factors. This phase happens to be
important because it increases the quality of the evidence obtained and minimize the risks that
may rise during the investigation.
ii) Step two- Securing the scene
This stage deals with protecting the scene of crime from an unauthorized access and preserving
the evidence to avoid contamination. It is the duty of the investigator to identify the scope of the
crime and establish the perimeter. The priority at this stage, is to ensure that all people in the
scene are safe and the integrity of the evidence obtained is maintained. The investigator should
take control of the scene and no unauthorized personnel should be allowed to interfere so as to
minimize the chances of evidence corruption or destruction. Anything that could be part of the
evidence should not be interfered with to make sure that the evidence obtained is quality.
iii) Step three- Survey and recognition
This is where the investigators conduct the initial survey of the scene of crime. It is crucial in
order to identify potential sources of evidence and develop an effective plan for the investigation.
The investigators must obtain maximum information from the people in the crime of scene
without violating any jurisdictional laws or corporate policies. Electronic equipment at the scene
of crime are also evaluated. If a need arises to search for items that are not included in the search
warranty, it is important that the current warrant be amended to include these items. A plan for
collecting and analyzing evidence is developed at this stage.
iv) Step four- Documenting the scene.
This stage involves documentation of the scene of crime as well as photographing, sketching and
crime scene mapping. Electronic gadgets that are in the scene of crime must be photographed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER FORENSICS 7
along with the accessories. In case there is a mobile device at the scene of crime whatever is
appearing on the screen must be documented. All this information will be important when the
investigator has to testify in a court of law. Everything in the scene of crime, including those
who reported the crime, those who were present and the actual dates and time must be recorded.
v) Step five- Communication shielding
In this stage, all possible communications of devices in the scene of crime should be blocked.
This will to ensure that further communication does not lead to overwriting of information,
which would contaminate the evidence. Electronic devices may still be sending signals using
wireless or Bluetooth even if they are switched off. The best option to avoid this, is by
completely disabling the communication capabilities of these devices.
vi) Step six- Evidence collection
this is a very crucial stage which involve a proper procedure so that it can be effective. Evidence
collection is categorized into two. Volatile evidence collection majorly involves mobile devices
that are unstable in nature. This kind of evidence can be challenging to obtain. Therefore, a
combination of tools must be used in order to obtain optimum results. The device should also be
scanned for any malicious software that could have been installed by the user. Non-volatile
evidence collection involves collecting evidence from external storage media which include
memory cards, compact flash cards, memory sticks, secure digital cards and USB memory sticks.
Evidence from computers that might have been synchronized with these devices must also be
collected. It is vital for investigators to use appropriate forensics tools to ensure that the evidence
collected is admissible in a court of law. Integrity and authenticity of the evidence obtained must
be ensured using techniques like hashing, or light protect. Investigators should consider looking
for evidence in non-electronic nature. For example, written passwords, hardware and software
manuals, computer print outs, and others.
vii) Step seven- Preservation
In this phase, packaging, transportation and storage is done. Necessary procedures are followed
to ensure that the integrity of electronic evidence collected is maintained. Identification and
labelling of all sources of evidence is performed in this stage. Anti-static package of evidence is
crucial since ordinary bags may cause static electricity. All devices and gadgets together with
along with the accessories. In case there is a mobile device at the scene of crime whatever is
appearing on the screen must be documented. All this information will be important when the
investigator has to testify in a court of law. Everything in the scene of crime, including those
who reported the crime, those who were present and the actual dates and time must be recorded.
v) Step five- Communication shielding
In this stage, all possible communications of devices in the scene of crime should be blocked.
This will to ensure that further communication does not lead to overwriting of information,
which would contaminate the evidence. Electronic devices may still be sending signals using
wireless or Bluetooth even if they are switched off. The best option to avoid this, is by
completely disabling the communication capabilities of these devices.
vi) Step six- Evidence collection
this is a very crucial stage which involve a proper procedure so that it can be effective. Evidence
collection is categorized into two. Volatile evidence collection majorly involves mobile devices
that are unstable in nature. This kind of evidence can be challenging to obtain. Therefore, a
combination of tools must be used in order to obtain optimum results. The device should also be
scanned for any malicious software that could have been installed by the user. Non-volatile
evidence collection involves collecting evidence from external storage media which include
memory cards, compact flash cards, memory sticks, secure digital cards and USB memory sticks.
Evidence from computers that might have been synchronized with these devices must also be
collected. It is vital for investigators to use appropriate forensics tools to ensure that the evidence
collected is admissible in a court of law. Integrity and authenticity of the evidence obtained must
be ensured using techniques like hashing, or light protect. Investigators should consider looking
for evidence in non-electronic nature. For example, written passwords, hardware and software
manuals, computer print outs, and others.
vii) Step seven- Preservation
In this phase, packaging, transportation and storage is done. Necessary procedures are followed
to ensure that the integrity of electronic evidence collected is maintained. Identification and
labelling of all sources of evidence is performed in this stage. Anti-static package of evidence is
crucial since ordinary bags may cause static electricity. All devices and gadgets together with
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER FORENSICS 8
their accessories must be put in an envelope and sealed before putting them in the evidence bag.
All the evidence bags are stored in a radio frequency isolation container to block any further
communication. All these containers must be labelled properly. The evidence is stored in a
secure location free from electronic radiation, heat, moisture or dust. Only authorized persons
should have access to the evidence room.
viii) Step eight- Examination
This phase involves examining and analyzing content of the collected evidence as well as
extracting information which is critical for the investigation. The huge amount of data collected
during the volatile and non-volatile phase has to be reduced into a manageable size. During this
phase, data filtering, pattern matching, validation and search for particular keywords with regard
to the crime are some major steps involved (Conklin et al., 2015). The power of the forensic tool
used by the examiner plays an important role in determining the results of this phase. It is
essential to prove that the evidence has not been altered by using hashing technique like MD5.
ix) Step nine- Analysis
It is a more technical stage conducted by the investigative team depending on the results of
the examination phase. The activities performed in this stage include identifying connection
between fragments of data, analyzing hidden data, determining the importance of information
obtained in the examination phase, reconstruction of event data and arriving at a proper
conclusion. A combination of tools must be used in this stage to get better results that must
be complete and accurately documented.
x) Step ten- Presentation
The information obtained may be presented to law enforcement officials, technical experts, legal
experts or corporate managers. Here, an agreement or disagreement is met concerning the claims.
Supporting materials like copies of the digital evidence. Chain of custody documents and
printouts of some evidence together with a detailed report should be submitted in this phase.
xi) Step eleven- Results and Review
their accessories must be put in an envelope and sealed before putting them in the evidence bag.
All the evidence bags are stored in a radio frequency isolation container to block any further
communication. All these containers must be labelled properly. The evidence is stored in a
secure location free from electronic radiation, heat, moisture or dust. Only authorized persons
should have access to the evidence room.
viii) Step eight- Examination
This phase involves examining and analyzing content of the collected evidence as well as
extracting information which is critical for the investigation. The huge amount of data collected
during the volatile and non-volatile phase has to be reduced into a manageable size. During this
phase, data filtering, pattern matching, validation and search for particular keywords with regard
to the crime are some major steps involved (Conklin et al., 2015). The power of the forensic tool
used by the examiner plays an important role in determining the results of this phase. It is
essential to prove that the evidence has not been altered by using hashing technique like MD5.
ix) Step nine- Analysis
It is a more technical stage conducted by the investigative team depending on the results of
the examination phase. The activities performed in this stage include identifying connection
between fragments of data, analyzing hidden data, determining the importance of information
obtained in the examination phase, reconstruction of event data and arriving at a proper
conclusion. A combination of tools must be used in this stage to get better results that must
be complete and accurately documented.
x) Step ten- Presentation
The information obtained may be presented to law enforcement officials, technical experts, legal
experts or corporate managers. Here, an agreement or disagreement is met concerning the claims.
Supporting materials like copies of the digital evidence. Chain of custody documents and
printouts of some evidence together with a detailed report should be submitted in this phase.
xi) Step eleven- Results and Review

COMPUTER FORENSICS 9
It is the final stage of the whole process. In involves going through all the steps of the
investigations and identifying areas that need improvement. The information obtained will help
establish better procedures and policies for future use.
After reviewing all the possible methodologies, I settled on SRDFIM. This is because it has a
number of steps that makes it easier to data mine detailed evidence as required. It is also
associated with highly accurate results.
RESOURCES REQUIRED TO CARRY OUT THE DIGITAL FORENSICS
There are several software’s that can be used for digital forensics. One of them is the
EnCase. This particular software can be used to recover evidence from hard drives. With EnCase
you can perform a deep analysis of user files in order to collect evidence such as documents,
internet history, windows registry information and pictures. Another software that can be used is
the forensic toolkit (FTK). It is created by access data. It mainly scans a hard drive as it is
searching for certain information. It can also locate emails that are deleted and scan a disk for
text strings to use them as a password dictionary to crack encryption.
There are many specialized tools that are needed in order for this exercise to be
successful. This tools are mostly important since the information we are looking for is not readily
available. Among this tools, is the computer COP. It is an application that is used to monitor and
control the content traffic in a computer system. It analyzes everything in a computer including
images, web browsing history, images and videos. Another tool necessary is the digital detective.
Digital detective is a network analysis tool that is used to analyze and extract the network
protocols, user activities and network traffic. It is also useful in web browsing forensics, network
filtering and searching, cache exports as well as web page building. In addition to all that it also
offers a data recovery solution. There are a number of hardware tools that are used for this
process. The most important tool is a computer which will be used important software and store
the evidence acquired
APPROACH FOR EVIDENCE ACQUISITION AND IDENTIFICATION
Evidence acquisition is sampling of signals that are used to measure real life occurrences
and then converting this information into numeric values that can be analyzed by a computer.
It is the final stage of the whole process. In involves going through all the steps of the
investigations and identifying areas that need improvement. The information obtained will help
establish better procedures and policies for future use.
After reviewing all the possible methodologies, I settled on SRDFIM. This is because it has a
number of steps that makes it easier to data mine detailed evidence as required. It is also
associated with highly accurate results.
RESOURCES REQUIRED TO CARRY OUT THE DIGITAL FORENSICS
There are several software’s that can be used for digital forensics. One of them is the
EnCase. This particular software can be used to recover evidence from hard drives. With EnCase
you can perform a deep analysis of user files in order to collect evidence such as documents,
internet history, windows registry information and pictures. Another software that can be used is
the forensic toolkit (FTK). It is created by access data. It mainly scans a hard drive as it is
searching for certain information. It can also locate emails that are deleted and scan a disk for
text strings to use them as a password dictionary to crack encryption.
There are many specialized tools that are needed in order for this exercise to be
successful. This tools are mostly important since the information we are looking for is not readily
available. Among this tools, is the computer COP. It is an application that is used to monitor and
control the content traffic in a computer system. It analyzes everything in a computer including
images, web browsing history, images and videos. Another tool necessary is the digital detective.
Digital detective is a network analysis tool that is used to analyze and extract the network
protocols, user activities and network traffic. It is also useful in web browsing forensics, network
filtering and searching, cache exports as well as web page building. In addition to all that it also
offers a data recovery solution. There are a number of hardware tools that are used for this
process. The most important tool is a computer which will be used important software and store
the evidence acquired
APPROACH FOR EVIDENCE ACQUISITION AND IDENTIFICATION
Evidence acquisition is sampling of signals that are used to measure real life occurrences
and then converting this information into numeric values that can be analyzed by a computer.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER FORENSICS 10
Identification involves searching and documenting digital evidence. During the identification
phase, the investigator has to examine all devices that were involved in the crime. it is also
advisable to analyze virtual components like cloud computing. After identifying the evidence, all
the devices involved should be assembled in a central location or moved into the laboratory for
further analysis. The acquisition of data is performed next and it mainly involves collecting data
from electronic media. There are four main methods that can be applied for this. They involve
disk-to-disk copy, disk-to-image file, logical disk-to-disk file and finally sparse data copy of a
file or folder.
ANALYSIS OF DATA
This phase involves collecting and validating evidence to obtain facts for your
investigation Since data will have been collected from numerous sources, it requires to be
compiled to draw a complete and clear image of the situation. During compilation, this
information should be matched over time to identify evidence that supports each other. It will
involve examining the sensitive data, deleted data, recently used data, all other important files,
and programs. Work should be done systematically by running the hypothesis drawn for the
investigation, the sampled test to agree or disagree with any theories that could be present. This
analysis must be done accurately and within the given time frame. It is advisable to conduct the
analysis of evidence twice for verification and surety of the correctness of the obtained
information. After a complete analysis of the evidence, additional information to help in the
investigation might still be necessary.
ANALYSIS OF THE FINDINGS IN CREATIVE MINDS COMPANY.
It was discovered that the security at the Creative Minds was not effective by all
dimensions. To begin with, after investing in information technology in order to support their
business functioning, they later lost track of updating the applications and network infrastructure.
By failing to update software, it means that the organization was being supported by old
technology which is not efficient (Panozzo et al., 2017). Every software upgrade comes with the
latest technology which has better and improved performance. Another issue facing this
organization is the use of windows based servers and work stations. Windows operating system
has been associated mostly with viruses attacked, which makes it less secure to handles
important operations. The network and firewalls were not properly configured throughout the
Identification involves searching and documenting digital evidence. During the identification
phase, the investigator has to examine all devices that were involved in the crime. it is also
advisable to analyze virtual components like cloud computing. After identifying the evidence, all
the devices involved should be assembled in a central location or moved into the laboratory for
further analysis. The acquisition of data is performed next and it mainly involves collecting data
from electronic media. There are four main methods that can be applied for this. They involve
disk-to-disk copy, disk-to-image file, logical disk-to-disk file and finally sparse data copy of a
file or folder.
ANALYSIS OF DATA
This phase involves collecting and validating evidence to obtain facts for your
investigation Since data will have been collected from numerous sources, it requires to be
compiled to draw a complete and clear image of the situation. During compilation, this
information should be matched over time to identify evidence that supports each other. It will
involve examining the sensitive data, deleted data, recently used data, all other important files,
and programs. Work should be done systematically by running the hypothesis drawn for the
investigation, the sampled test to agree or disagree with any theories that could be present. This
analysis must be done accurately and within the given time frame. It is advisable to conduct the
analysis of evidence twice for verification and surety of the correctness of the obtained
information. After a complete analysis of the evidence, additional information to help in the
investigation might still be necessary.
ANALYSIS OF THE FINDINGS IN CREATIVE MINDS COMPANY.
It was discovered that the security at the Creative Minds was not effective by all
dimensions. To begin with, after investing in information technology in order to support their
business functioning, they later lost track of updating the applications and network infrastructure.
By failing to update software, it means that the organization was being supported by old
technology which is not efficient (Panozzo et al., 2017). Every software upgrade comes with the
latest technology which has better and improved performance. Another issue facing this
organization is the use of windows based servers and work stations. Windows operating system
has been associated mostly with viruses attacked, which makes it less secure to handles
important operations. The network and firewalls were not properly configured throughout the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER FORENSICS 11
organizations. Such a situation raises multiple security concerns (Reybok et al., 2018). The most
basic concern is the one evident in Creative Minds; that is, users from different offices and
departments were able to access the file in the other offices. Another risk associated with that
would be a cyber-attack. A hacker can tap into the company’s network and introduce malicious
programs that are intended to destroy files, copy data, or even stop the whole organization from
functioning using denial of services (Ormazabal,Verizon Patent & Licensing Inc 2015).
SECURITY POLICIES TO BE IMPLEMENTED
Security policies define what is needed for a system or organization to be termed as secure. They
define the minimum requirements and rule to be followed by users or workers in an organization
in order to maintain the security of the body. I would implement new security policies for the
Creative minds to ensure such an occurrence will never happen again. First of all, they should
install biometric systems for all doors that lead to sensitive rooms. The system will keep logs of
all people who access a certain room which will be very helpful in case there is an issue. In
addition to that a network professional is supposed to be hired so that the network can be
properly configured. The specialist should also configure a firewall to protect the network from
un authorized external access. Access control must be implemented in the network. This will
ensure there is controlled access of resource across the offices and departments. This few
policies guarantee the safety of this organization in terms of network security.
RECOMMENDATIONS
After a careful analysis of the computer systems in Creative Minds company so as to
gather facts and evidence pertaining to the crime, I would provide a few recommendations
depending on the issues evident in order to ensure that such a problem will never arise again. The
company needs to implement new security policies or amend the existing ones to provide a
secure working environment (Vange et al., 2017). Secondly, the network and application
infrastructure needs to be regularly updated. The updates should be performed at fixed intervals,
and documentation should follow this process. In addition to that, a network security expert
should be hired in order to configure the firewall and the network at large (Acemoglu et al.,
2016). Access control should be applied in the network to avoid inter-office interaction except
where necessary. The firewall will be used to protect the network from external attacks. Final,
the company, should consider using a different operating system from Microsoft windows. This
organizations. Such a situation raises multiple security concerns (Reybok et al., 2018). The most
basic concern is the one evident in Creative Minds; that is, users from different offices and
departments were able to access the file in the other offices. Another risk associated with that
would be a cyber-attack. A hacker can tap into the company’s network and introduce malicious
programs that are intended to destroy files, copy data, or even stop the whole organization from
functioning using denial of services (Ormazabal,Verizon Patent & Licensing Inc 2015).
SECURITY POLICIES TO BE IMPLEMENTED
Security policies define what is needed for a system or organization to be termed as secure. They
define the minimum requirements and rule to be followed by users or workers in an organization
in order to maintain the security of the body. I would implement new security policies for the
Creative minds to ensure such an occurrence will never happen again. First of all, they should
install biometric systems for all doors that lead to sensitive rooms. The system will keep logs of
all people who access a certain room which will be very helpful in case there is an issue. In
addition to that a network professional is supposed to be hired so that the network can be
properly configured. The specialist should also configure a firewall to protect the network from
un authorized external access. Access control must be implemented in the network. This will
ensure there is controlled access of resource across the offices and departments. This few
policies guarantee the safety of this organization in terms of network security.
RECOMMENDATIONS
After a careful analysis of the computer systems in Creative Minds company so as to
gather facts and evidence pertaining to the crime, I would provide a few recommendations
depending on the issues evident in order to ensure that such a problem will never arise again. The
company needs to implement new security policies or amend the existing ones to provide a
secure working environment (Vange et al., 2017). Secondly, the network and application
infrastructure needs to be regularly updated. The updates should be performed at fixed intervals,
and documentation should follow this process. In addition to that, a network security expert
should be hired in order to configure the firewall and the network at large (Acemoglu et al.,
2016). Access control should be applied in the network to avoid inter-office interaction except
where necessary. The firewall will be used to protect the network from external attacks. Final,
the company, should consider using a different operating system from Microsoft windows. This

COMPUTER FORENSICS 12
is because Microsoft Windows is easily infected by viruses and worms. Other operating systems
like mackintosh and Linux are much safer when it comes to dealing with viruses and penetration.
I would, therefore, advise the Creative Minds to adopt such operating systems so as to be a step
ahead towards controlling such incidences.
CONCLUSION
In summary, the computer forensics field of science is adopted regarding the kind of
crime. For the Creative Minds case, this was the most appropriate type as the circumstances of
their case was fit. This calls for the company needs to understand computer forensics and its
importance in conducting the investigations. For clarity of the crime, the evidence collected, a
few methodologies have been detailed to provide additive information. Each of the approaches,
provide a go ahead and enough information towards gathering, analyzing, reporting, and
presenting the evidence. To achieve using these methods effectively, I had to come up with a
plan for computer forensics investigation. This plan had to be prepared before the investigations
began, and it involved a few steps. It helped me create a detailed plan that met all its
requirements. Even with the numerous strategies, the digital computer forensics procedure tends
to be of major interest as it is more efficient and advantageous for a successful investigation. It is
mainly advisable because it will help in finding valid and exact evidence that we need to support
the reported crime according to the law.
is because Microsoft Windows is easily infected by viruses and worms. Other operating systems
like mackintosh and Linux are much safer when it comes to dealing with viruses and penetration.
I would, therefore, advise the Creative Minds to adopt such operating systems so as to be a step
ahead towards controlling such incidences.
CONCLUSION
In summary, the computer forensics field of science is adopted regarding the kind of
crime. For the Creative Minds case, this was the most appropriate type as the circumstances of
their case was fit. This calls for the company needs to understand computer forensics and its
importance in conducting the investigations. For clarity of the crime, the evidence collected, a
few methodologies have been detailed to provide additive information. Each of the approaches,
provide a go ahead and enough information towards gathering, analyzing, reporting, and
presenting the evidence. To achieve using these methods effectively, I had to come up with a
plan for computer forensics investigation. This plan had to be prepared before the investigations
began, and it involved a few steps. It helped me create a detailed plan that met all its
requirements. Even with the numerous strategies, the digital computer forensics procedure tends
to be of major interest as it is more efficient and advantageous for a successful investigation. It is
mainly advisable because it will help in finding valid and exact evidence that we need to support
the reported crime according to the law.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




