Digital Forensics Investigation: Cyberattack Analysis and Improvements
VerifiedAdded on 2023/06/17
|10
|806
|309
Report
AI Summary
This report delves into digital forensics, examining hardware and software tools used in investigations, file system structures across various operating systems (MS-DOS, Windows, UNIX, Linux, Mac OS, Android), and a comparative analysis of network forensic tools, specifically Silent Runner and NetIntercept. A practical digital forensic investigation is conducted using NetIntercept to analyze Signal app traffic, focusing on connectivity and communication patterns through network topology. The report critically evaluates the investigation process, recommending improvements such as implementing event logging policies and procedures to enhance digital forensics guidelines, processes, and procedures. References to relevant research and publications are included to support the analysis and recommendations.

UNIT 24 FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of contents
• Hardware and software tools that can be used to conduct digital Forensic Investigation.
• The file system structure of several Operating Systems e.g. MS-DOS, Windows, UNIX, Linux,
Mac OS, Android, etc.
• Comparison of two tools that can be used to conduct digital Forensic Investigation.
• Following your presentation, you are required to carry out a digital Forensic Investigation on a
device or network or cyberattack conducted by you with evidence.
• Critically evaluate your investigation and suggest improvements to the current digital Forensic
Investigation guidelines, processes and procedures.
• Hardware and software tools that can be used to conduct digital Forensic Investigation.
• The file system structure of several Operating Systems e.g. MS-DOS, Windows, UNIX, Linux,
Mac OS, Android, etc.
• Comparison of two tools that can be used to conduct digital Forensic Investigation.
• Following your presentation, you are required to carry out a digital Forensic Investigation on a
device or network or cyberattack conducted by you with evidence.
• Critically evaluate your investigation and suggest improvements to the current digital Forensic
Investigation guidelines, processes and procedures.

Hardware and software tools that can be used to
conduct digital Forensic Investigation.
• It has been identified that forensic
investigation are the always being
challenging, as the investigator
have to gather all information for
the evidence and mitigation plan.
• There are some most essential
computer forensic investigation
tools. Such as Autopsy, encrypted
disk detector, wire-shark, magnet
RAM capture, network miner, NMAP,
FAW, crowd repose, EXIF tool etc.
conduct digital Forensic Investigation.
• It has been identified that forensic
investigation are the always being
challenging, as the investigator
have to gather all information for
the evidence and mitigation plan.
• There are some most essential
computer forensic investigation
tools. Such as Autopsy, encrypted
disk detector, wire-shark, magnet
RAM capture, network miner, NMAP,
FAW, crowd repose, EXIF tool etc.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The file system structure of several Operating Systems e.g.
MS-DOS, Windows, UNIX, Linux, Mac OS, Android, etc.
• A file is a collection of interrelated
information that is basically recorded on
secondary storage such as magnetic disks,
tapes, and optical disks.
• The file system is a method of information
collection that is generally used as a base for
providing input as well as receiving output
from that program. A file is a sequence of
bits, bytes or records whose definition is
explained by the creator of the file and user.
MS-DOS, Windows, UNIX, Linux, Mac OS, Android, etc.
• A file is a collection of interrelated
information that is basically recorded on
secondary storage such as magnetic disks,
tapes, and optical disks.
• The file system is a method of information
collection that is generally used as a base for
providing input as well as receiving output
from that program. A file is a sequence of
bits, bytes or records whose definition is
explained by the creator of the file and user.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
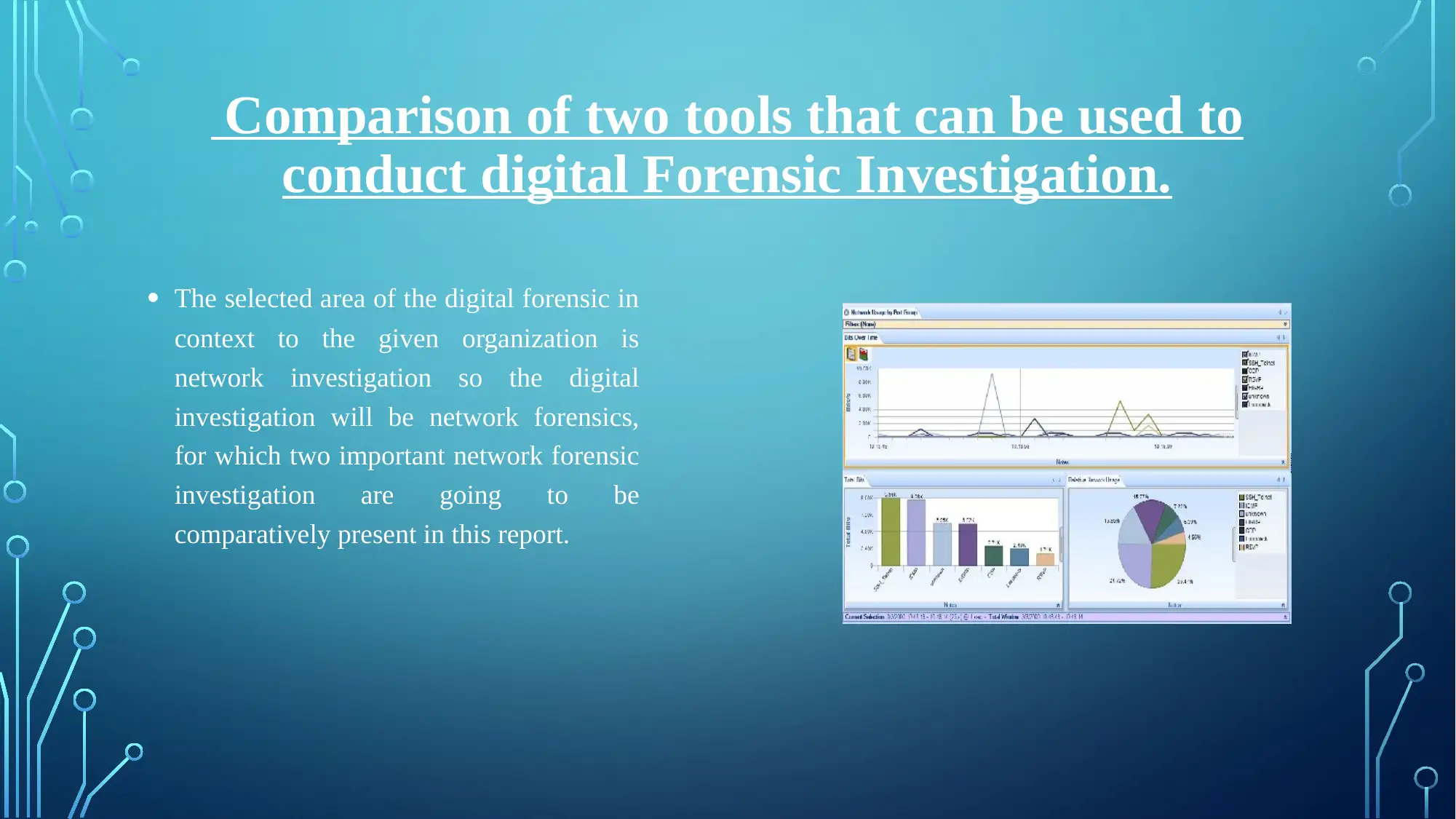
Comparison of two tools that can be used to
conduct digital Forensic Investigation.
• The selected area of the digital forensic in
context to the given organization is
network investigation so the digital
investigation will be network forensics,
for which two important network forensic
investigation are going to be
comparatively present in this report.
conduct digital Forensic Investigation.
• The selected area of the digital forensic in
context to the given organization is
network investigation so the digital
investigation will be network forensics,
for which two important network forensic
investigation are going to be
comparatively present in this report.
Continue
Silent Runner NetIntercept
This is the network forensic tool by access data, this offer
data capture, analysis and visualization of the data.
This is including the data loading into the relational data
base to provide complex query.
The main part of SilentRunner system is loaders,
database, analysis workstations and collector capture the
network traffic through its system.
This also helps in the searching transactions, selecting
protocols, and performing queries.
This is the tool use to analyse the traffic from a forensic
prospective, this is commonly known as the NFAT.
This is the library that allows to intercept network traffic
without privileges and create clean pcap files.
This is having the natural sentiment in the development
of community. s no vulnerabilities reported, and its
dependent libraries have no vulnerabilities reported.
This licensed under the MIT license is permissive, use
most of the projects.
This is reusable tool.
Silent Runner NetIntercept
This is the network forensic tool by access data, this offer
data capture, analysis and visualization of the data.
This is including the data loading into the relational data
base to provide complex query.
The main part of SilentRunner system is loaders,
database, analysis workstations and collector capture the
network traffic through its system.
This also helps in the searching transactions, selecting
protocols, and performing queries.
This is the tool use to analyse the traffic from a forensic
prospective, this is commonly known as the NFAT.
This is the library that allows to intercept network traffic
without privileges and create clean pcap files.
This is having the natural sentiment in the development
of community. s no vulnerabilities reported, and its
dependent libraries have no vulnerabilities reported.
This licensed under the MIT license is permissive, use
most of the projects.
This is reusable tool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Following your presentation, you are required to carry out
a digital Forensic Investigation on a device or network or
cyberattack conducted by you with evidence.
• In context to the network digital forensics investigation, the NetIntercept tool is going to be
implemented. Extensive traffic analysis of the signal app by incorporating the Net Intercept approach
investigation is done.
• This helps to assess the pattern of connectivity and communication activities. The main technique
used under the process of the inquiry is topology, which is use to define or describe the arrangement of
various types of telecommunication networks
a digital Forensic Investigation on a device or network or
cyberattack conducted by you with evidence.
• In context to the network digital forensics investigation, the NetIntercept tool is going to be
implemented. Extensive traffic analysis of the signal app by incorporating the Net Intercept approach
investigation is done.
• This helps to assess the pattern of connectivity and communication activities. The main technique
used under the process of the inquiry is topology, which is use to define or describe the arrangement of
various types of telecommunication networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Critically evaluate your investigation and suggest
improvements to the current digital Forensic Investigation
guidelines, processes and procedures.
• The critical recommendation after the
evaluation of the investigation for the
improvement of current digital forensics
improvement are putting a process in place,
making a plan, acquire the talent.
• Such as there is the need of event logging
policies implementation and procedures to
capture, aggregate and store log files.
improvements to the current digital Forensic Investigation
guidelines, processes and procedures.
• The critical recommendation after the
evaluation of the investigation for the
improvement of current digital forensics
improvement are putting a process in place,
making a plan, acquire the talent.
• Such as there is the need of event logging
policies implementation and procedures to
capture, aggregate and store log files.

References
• Messier, R., 2017. Network forensics. John Wiley & Sons.
• Årnes, A. ed., 2017. Digital forensics. John Wiley & Sons.
• Pichan, A., Lazarescu, M. and Soh, S.T., 2018. Towards a practical
cloud forensics logging framework. Journal of information security and
applications, 42, pp.18-28.
• Daryabar, F., Dehghantanha, A. and Choo, K.K.R., 2017. Cloud storage
forensics: MEGA as a case study. Australian Journal of Forensic
Sciences, 49(3), pp.344-357.
• Messier, R., 2017. Network forensics. John Wiley & Sons.
• Årnes, A. ed., 2017. Digital forensics. John Wiley & Sons.
• Pichan, A., Lazarescu, M. and Soh, S.T., 2018. Towards a practical
cloud forensics logging framework. Journal of information security and
applications, 42, pp.18-28.
• Daryabar, F., Dehghantanha, A. and Choo, K.K.R., 2017. Cloud storage
forensics: MEGA as a case study. Australian Journal of Forensic
Sciences, 49(3), pp.344-357.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

THANK YOU
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





