COIT12201 - Digital Forensics Investigation of M57 Patents Case
VerifiedAdded on 2023/06/04
|19
|5417
|87
Case Study
AI Summary
This report details a digital forensic investigation into the M57 patents case, involving a patent search organization suspected of internal illegal activities. The investigation begins after a workstation from M57 is recovered, leading to a full examination of the company's digital assets, including computers, handsets, and USB drives. The report outlines the network layout, workstation setup, and a literature review of digital forensic methodologies. Activities performed include examining RAM snapshots, generating file hashes, and comparing memory images to identify potential keyloggers and unauthorized software installations on the CEO's computer. The findings suggest the presence and removal of a keylogger, raising concerns about potential email spying and data exfiltration. The investigation employs various digital forensic tools and techniques to analyze the evidence and reconstruct the events, providing insights into the organization's security vulnerabilities and potential internal threats. The assignment is a practical application of digital forensic principles and tools in a real-world scenario.

Digital forensic investigation 1
Digital forensic investigation on M57 patents case
Student
Course
Tutor
Institutional Affiliations
State
Date
Digital forensic investigation on M57 patents case
Student
Course
Tutor
Institutional Affiliations
State
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital forensic investigation 2
Table of Contents
Introduction...............................................................................................................................................2
M57 patents scenario details.................................................................................................................4
M57.bizz Network..................................................................................................................................5
The organization workstation devices..................................................................................................6
Literature analysis.....................................................................................................................................6
Activity 1....................................................................................................................................................8
Activity 2....................................................................................................................................................9
Activity 3..................................................................................................................................................11
Discussion.................................................................................................................................................13
Conclusion................................................................................................................................................14
Reference list............................................................................................................................................15
Introduction
With the progress in time and advancement as well as evolution in technology, the use of
computers has and will increase in our daily lives. This owes to the fact that the digitalized
generation has become more dependent on computers to an extent that computers are used in
nearly all facets of our daily activities including organizations, institutions, and for personal use.
It is safe to calculate the rise of crime that has been facilitated by the advanced technology by
Table of Contents
Introduction...............................................................................................................................................2
M57 patents scenario details.................................................................................................................4
M57.bizz Network..................................................................................................................................5
The organization workstation devices..................................................................................................6
Literature analysis.....................................................................................................................................6
Activity 1....................................................................................................................................................8
Activity 2....................................................................................................................................................9
Activity 3..................................................................................................................................................11
Discussion.................................................................................................................................................13
Conclusion................................................................................................................................................14
Reference list............................................................................................................................................15
Introduction
With the progress in time and advancement as well as evolution in technology, the use of
computers has and will increase in our daily lives. This owes to the fact that the digitalized
generation has become more dependent on computers to an extent that computers are used in
nearly all facets of our daily activities including organizations, institutions, and for personal use.
It is safe to calculate the rise of crime that has been facilitated by the advanced technology by

Digital forensic investigation 3
evaluating the past trends of technology. Findings from various studies cite that criminals have
put a strain in computer forensic examiners today (Taylor, Haggerty, Gresty, and Lamb, 2011,
pp.4-10; Grispos, Storer, and Glisson, 2012, pp.28-48). This is due to the reason that a
significant number of crime, nowadays, are often facilitated by computers as well as other
computing devices of some sort including smartphones among other gadgets. Moreover, the
computer hardware and software, as well as the wireless technology, are getting more
sophisticated and portable thus increasing the level of crime (Damshenas, Dehghantanha,
Mahmoud and bin Shamsuddin, 2013, p.543).
Considering the evolution in technology as well as updates on what is to be considered
evidence, a proper training, and education in computer forensics should be considered (Chung,
Park, Lee, and Kang, 2012, pp.81-95; Rekhis and Boudriga, 2012, pp.635-650). It is important to
find out what a crime entails where computers are involved, it is also important to examine any
potential evidence of a crime on the digital media. There has been a considerable growth in
crime rates, as such, computer forensics is becoming increasingly important (Agarwal, and
Kothari, 2015, pp. 561-571; Liberatore, Erdely, Kerle, Levine, and Shields, 2010, pp.S95-S103).
Computer forensic entails expertise as well as the methods drawn from information and
communication technology domain, psychology, and criminology among other related fields
(Raghavan, 2013, pp.91-114; Seo, Lim, and Lee, 2009, pp.182-190; Valjarevic, and Venter,
2013, pp. 1-9). It is essential not just for mastering the digital forensic tools but also to have and
understanding of the advantages and limitations of the tools in their application in the real world
situation.
One critical issue in digital forensics is that real data is always not stable because of the
presence of confidential information. As such, there is need of disks for memory dumps, images,
evaluating the past trends of technology. Findings from various studies cite that criminals have
put a strain in computer forensic examiners today (Taylor, Haggerty, Gresty, and Lamb, 2011,
pp.4-10; Grispos, Storer, and Glisson, 2012, pp.28-48). This is due to the reason that a
significant number of crime, nowadays, are often facilitated by computers as well as other
computing devices of some sort including smartphones among other gadgets. Moreover, the
computer hardware and software, as well as the wireless technology, are getting more
sophisticated and portable thus increasing the level of crime (Damshenas, Dehghantanha,
Mahmoud and bin Shamsuddin, 2013, p.543).
Considering the evolution in technology as well as updates on what is to be considered
evidence, a proper training, and education in computer forensics should be considered (Chung,
Park, Lee, and Kang, 2012, pp.81-95; Rekhis and Boudriga, 2012, pp.635-650). It is important to
find out what a crime entails where computers are involved, it is also important to examine any
potential evidence of a crime on the digital media. There has been a considerable growth in
crime rates, as such, computer forensics is becoming increasingly important (Agarwal, and
Kothari, 2015, pp. 561-571; Liberatore, Erdely, Kerle, Levine, and Shields, 2010, pp.S95-S103).
Computer forensic entails expertise as well as the methods drawn from information and
communication technology domain, psychology, and criminology among other related fields
(Raghavan, 2013, pp.91-114; Seo, Lim, and Lee, 2009, pp.182-190; Valjarevic, and Venter,
2013, pp. 1-9). It is essential not just for mastering the digital forensic tools but also to have and
understanding of the advantages and limitations of the tools in their application in the real world
situation.
One critical issue in digital forensics is that real data is always not stable because of the
presence of confidential information. As such, there is need of disks for memory dumps, images,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Digital forensic investigation 4
and packet dumps for use, however, the resulting data is rarely realistic (Chung et al. 2012,
pp.81-95; Beebe, 2009, pp. 17-36; Grispos, Storer, and Glisson, 2012, pp.28-48). The primary
objective of this report is to demonstrate the practical use of the digital forensic tools through
analysis of M57 organization cyber-crime scenario.
As this article attempts to meet the stated objective, it seeks to respond to the questions
stated below:
i. What are the appropriate digital forensic tools for addressing the M57 scenario?
ii. What is the process involved in addressing the scenario?
M57 patents scenario details
As stated in the scenario, the M57 is a patent search organization that do investigations
for its clients’ patent information. The scenario starts when the company has four employees
including the founder and the CEO of the organization named Pat McGoo, the company’s
administrator Terry Johnston and two patent researchers called Jo Smith and Charlie Brown. The
organization has a plan for employing more employees as it books new clients. Since the
organization needs to employ more personnel, they must be having more technology at hand that
is not utilized.
The roles of the organization’s employees are checking and writing emails, staging and
conducting various illegal or malicious activities surfing the internet, using document creation
software including office among other responsibilities. The illegal activities associated with the
organization’s employees are not limited to theft of the organization’s property, using spyware
including loggers, proprietary information exfiltration and viewing illegal content using the
and packet dumps for use, however, the resulting data is rarely realistic (Chung et al. 2012,
pp.81-95; Beebe, 2009, pp. 17-36; Grispos, Storer, and Glisson, 2012, pp.28-48). The primary
objective of this report is to demonstrate the practical use of the digital forensic tools through
analysis of M57 organization cyber-crime scenario.
As this article attempts to meet the stated objective, it seeks to respond to the questions
stated below:
i. What are the appropriate digital forensic tools for addressing the M57 scenario?
ii. What is the process involved in addressing the scenario?
M57 patents scenario details
As stated in the scenario, the M57 is a patent search organization that do investigations
for its clients’ patent information. The scenario starts when the company has four employees
including the founder and the CEO of the organization named Pat McGoo, the company’s
administrator Terry Johnston and two patent researchers called Jo Smith and Charlie Brown. The
organization has a plan for employing more employees as it books new clients. Since the
organization needs to employ more personnel, they must be having more technology at hand that
is not utilized.
The roles of the organization’s employees are checking and writing emails, staging and
conducting various illegal or malicious activities surfing the internet, using document creation
software including office among other responsibilities. The illegal activities associated with the
organization’s employees are not limited to theft of the organization’s property, using spyware
including loggers, proprietary information exfiltration and viewing illegal content using the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital forensic investigation 5
organization’s computer. The illegal content consists of the pictures of common house cats that
have no copyrights.
This episode, however, ends when an individual outside the M57 Company reports an
information to a police station. The person had bought a desktop workstation from an
advertisement on Craigslist. This individual found the cat's photographs mentioned earlier in the
device and investigators trace the machine then find that it belongs to the M57 organization.
Upon calling the organization’s CEO, Pat confirm that the device was stolen and further provide
more organization’s properties that have been stolen along with the computer. The CEO tells the
investigators to search the organization and image all M57 Company’s properties including the
organization’s handsets, computers, and the machine’s removable USB drives. McGoo, however,
has no idea that several of the organization’s employees are involved in this illegal act including
extortion, theft of the organization’s property, and data exfiltration.
M57.bizz Network
The organization’s network layout includes four computers which are connected to one
switch configured with a gateway which enabled internet connection as shown in figure 1. Jo
Smith needed two machines according to the scenario, by then, he had one machine connected to
the network. The organization made a replacement because of his hardware fail which was one
week before the scenario commenced.
organization’s computer. The illegal content consists of the pictures of common house cats that
have no copyrights.
This episode, however, ends when an individual outside the M57 Company reports an
information to a police station. The person had bought a desktop workstation from an
advertisement on Craigslist. This individual found the cat's photographs mentioned earlier in the
device and investigators trace the machine then find that it belongs to the M57 organization.
Upon calling the organization’s CEO, Pat confirm that the device was stolen and further provide
more organization’s properties that have been stolen along with the computer. The CEO tells the
investigators to search the organization and image all M57 Company’s properties including the
organization’s handsets, computers, and the machine’s removable USB drives. McGoo, however,
has no idea that several of the organization’s employees are involved in this illegal act including
extortion, theft of the organization’s property, and data exfiltration.
M57.bizz Network
The organization’s network layout includes four computers which are connected to one
switch configured with a gateway which enabled internet connection as shown in figure 1. Jo
Smith needed two machines according to the scenario, by then, he had one machine connected to
the network. The organization made a replacement because of his hardware fail which was one
week before the scenario commenced.
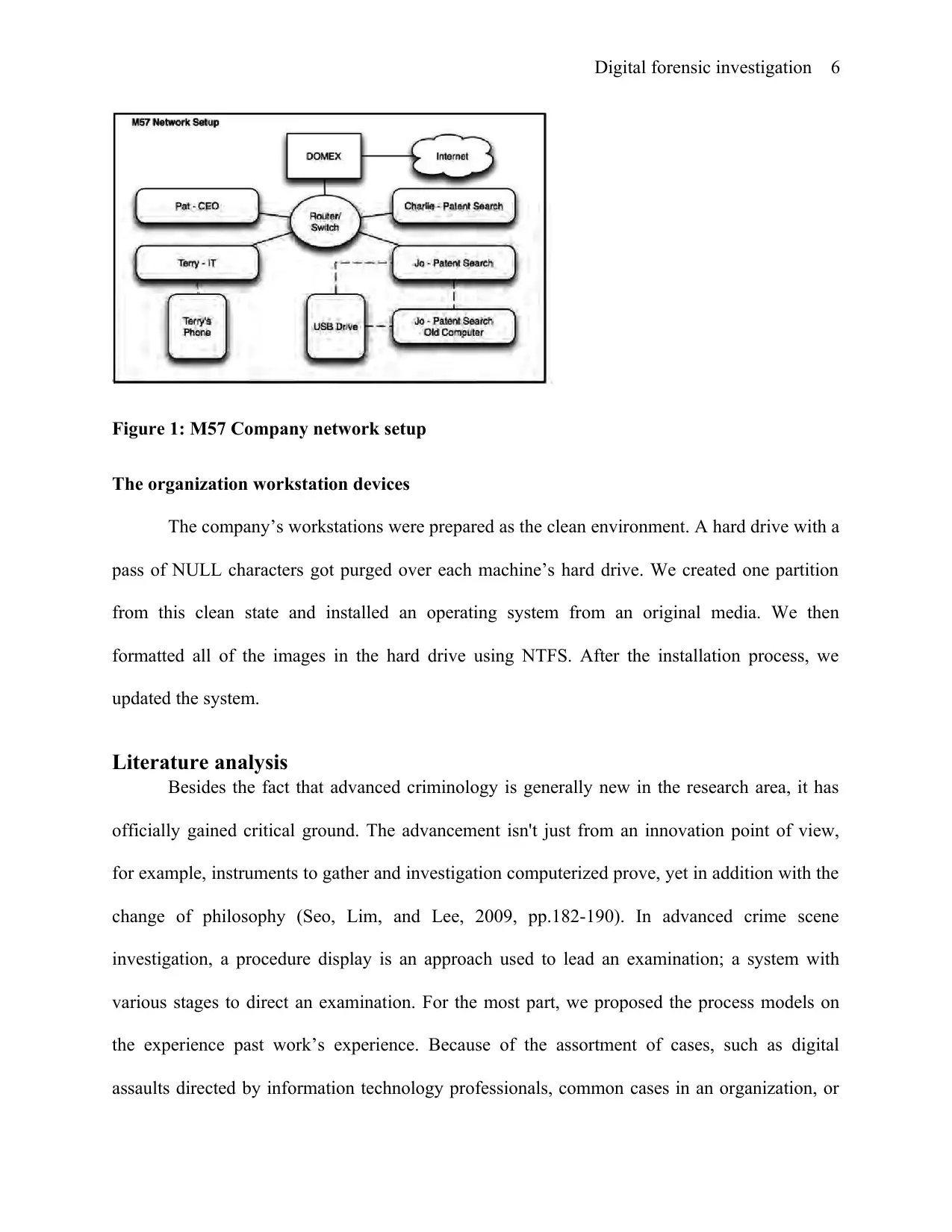
Digital forensic investigation 6
Figure 1: M57 Company network setup
The organization workstation devices
The company’s workstations were prepared as the clean environment. A hard drive with a
pass of NULL characters got purged over each machine’s hard drive. We created one partition
from this clean state and installed an operating system from an original media. We then
formatted all of the images in the hard drive using NTFS. After the installation process, we
updated the system.
Literature analysis
Besides the fact that advanced criminology is generally new in the research area, it has
officially gained critical ground. The advancement isn't just from an innovation point of view,
for example, instruments to gather and investigation computerized prove, yet in addition with the
change of philosophy (Seo, Lim, and Lee, 2009, pp.182-190). In advanced crime scene
investigation, a procedure display is an approach used to lead an examination; a system with
various stages to direct an examination. For the most part, we proposed the process models on
the experience past work’s experience. Because of the assortment of cases, such as digital
assaults directed by information technology professionals, common cases in an organization, or
Figure 1: M57 Company network setup
The organization workstation devices
The company’s workstations were prepared as the clean environment. A hard drive with a
pass of NULL characters got purged over each machine’s hard drive. We created one partition
from this clean state and installed an operating system from an original media. We then
formatted all of the images in the hard drive using NTFS. After the installation process, we
updated the system.
Literature analysis
Besides the fact that advanced criminology is generally new in the research area, it has
officially gained critical ground. The advancement isn't just from an innovation point of view,
for example, instruments to gather and investigation computerized prove, yet in addition with the
change of philosophy (Seo, Lim, and Lee, 2009, pp.182-190). In advanced crime scene
investigation, a procedure display is an approach used to lead an examination; a system with
various stages to direct an examination. For the most part, we proposed the process models on
the experience past work’s experience. Because of the assortment of cases, such as digital
assaults directed by information technology professionals, common cases in an organization, or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Digital forensic investigation 7
illegal cases, diverse specialists have a tendency to take after various strategies in their
investigative procedure, there is no standard work process in a computerized scientific
examination.
A standard system in advanced crime scene investigation examination comprises of a
meaning of the succession of activities vital in the examination (Valjarevic, and Venter, 2013,
pp. 1-9). A structure, in the event that it is excessively shortsighted or has fewer stages, probably
won't give much direction to the examination procedure. A system with more stages and each
stage with sub-ventures, with more impediment of its use situation, may demonstrate more
helpful. Despite the fact that it is relatively difficult to plan an impeccable procedure demonstrate
that can manage any examination, a perfect system ought to be general, which implies that it
could be connected to whatever number cases as would be prudent.
Moreover, considering that methods develop so quickly, a very much characterized
structure ought to likewise with the ability to embrace new strategies during the time spent
examination (Rekhis and Boudriga, 2012, pp.635-650). The authors have proposed various
process models. For the most part, every system endeavors to refine the standard strategy for a
given case and each of the procedure models adopts an extensively comparable strategy. The
most punctual research focused on characterizing the procedure of advanced measurable
examination. All the more as of late, process display inquires about revolves around fathoming
more particular issues - particular utilize cases or spotlight on specific advances (confirm
gathering, safeguarding or examination, investigation). The triage show is successful for cases
that are time touchy. Through the help of computerized criminology triage, specialists could find
appropriate proof, what's more, the police could get the whereabouts the criminal sooner rather
sitting tight for the entire report which could take a while or even years.
illegal cases, diverse specialists have a tendency to take after various strategies in their
investigative procedure, there is no standard work process in a computerized scientific
examination.
A standard system in advanced crime scene investigation examination comprises of a
meaning of the succession of activities vital in the examination (Valjarevic, and Venter, 2013,
pp. 1-9). A structure, in the event that it is excessively shortsighted or has fewer stages, probably
won't give much direction to the examination procedure. A system with more stages and each
stage with sub-ventures, with more impediment of its use situation, may demonstrate more
helpful. Despite the fact that it is relatively difficult to plan an impeccable procedure demonstrate
that can manage any examination, a perfect system ought to be general, which implies that it
could be connected to whatever number cases as would be prudent.
Moreover, considering that methods develop so quickly, a very much characterized
structure ought to likewise with the ability to embrace new strategies during the time spent
examination (Rekhis and Boudriga, 2012, pp.635-650). The authors have proposed various
process models. For the most part, every system endeavors to refine the standard strategy for a
given case and each of the procedure models adopts an extensively comparable strategy. The
most punctual research focused on characterizing the procedure of advanced measurable
examination. All the more as of late, process display inquires about revolves around fathoming
more particular issues - particular utilize cases or spotlight on specific advances (confirm
gathering, safeguarding or examination, investigation). The triage show is successful for cases
that are time touchy. Through the help of computerized criminology triage, specialists could find
appropriate proof, what's more, the police could get the whereabouts the criminal sooner rather
sitting tight for the entire report which could take a while or even years.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital forensic investigation 8
Cloud computing has turned out to be typical in this day and age. As one precedent, cloud
storage, for example, Google Drive, Dropbox, Apple's iCloud, and so on, are broadly utilized by
buyers worldwide. Advancement this innovation is a twofold edged sword from a computerized
criminological point of view; the wide utilization of cloud framework and applications conveys
unpredictability to directing computerized measurable examinations while utilizing this on-
request, the rapid innovation could likewise make a big deal about the investigative procedure
fundamentally more proficient.
Nonetheless, in view of the present writing in the territory, digital forensic is
considerably more famous, for example recuperating proof from cloud administrations and
applications (Beebe, 2009, pp. 17-36). Survey on DFaaS very constrained up to now in the
digital scientific network. The DFaaS is particularly still considered in its outset. In the most
recent decade, numerous partnerships have completed their preparing as well as information
relocation from their own servers to the cloud benefit sellers, for example, Amazon or
Rackspace. In like manner, during the time spent advanced scientific examination, the DFaaS
could bring a few enhancements over the current procedure. There are various advantages of
making utilization of cloud computing for scientific examination. Right off the bat, remotely
interfacing with ground-breaking servers rather than every single gadget not just offer the agents
more grounded processing power for confirming examination yet, in addition, dispose of the area
impediment that the investigation could just be led in the research center.
Activity 1
According to the scenario script, there is suspicion that a certain employee spy on the
M57 organization CEO by e-mail. In this case, the hypothesis is that the illegal act was done on
the individual’s computer.
Cloud computing has turned out to be typical in this day and age. As one precedent, cloud
storage, for example, Google Drive, Dropbox, Apple's iCloud, and so on, are broadly utilized by
buyers worldwide. Advancement this innovation is a twofold edged sword from a computerized
criminological point of view; the wide utilization of cloud framework and applications conveys
unpredictability to directing computerized measurable examinations while utilizing this on-
request, the rapid innovation could likewise make a big deal about the investigative procedure
fundamentally more proficient.
Nonetheless, in view of the present writing in the territory, digital forensic is
considerably more famous, for example recuperating proof from cloud administrations and
applications (Beebe, 2009, pp. 17-36). Survey on DFaaS very constrained up to now in the
digital scientific network. The DFaaS is particularly still considered in its outset. In the most
recent decade, numerous partnerships have completed their preparing as well as information
relocation from their own servers to the cloud benefit sellers, for example, Amazon or
Rackspace. In like manner, during the time spent advanced scientific examination, the DFaaS
could bring a few enhancements over the current procedure. There are various advantages of
making utilization of cloud computing for scientific examination. Right off the bat, remotely
interfacing with ground-breaking servers rather than every single gadget not just offer the agents
more grounded processing power for confirming examination yet, in addition, dispose of the area
impediment that the investigation could just be led in the research center.
Activity 1
According to the scenario script, there is suspicion that a certain employee spy on the
M57 organization CEO by e-mail. In this case, the hypothesis is that the illegal act was done on
the individual’s computer.

Digital forensic investigation 9
Because there was limited information with respect to timing to support the process of
investigation, all of the Pat’s RAM snap short were examined as well as the attempts to establish
all of the executables which are in the memory. During the process, we generated various file
hashes, every one of Pat's disks was mounted and hashed the majority of the individual
documents which took around one and a half an hour for eighteen images of 260 GB. The
memory pictures from Pat's PC were contrasted and the hashes of the .dll and the .exe records
which are on the circle pictures in his PC's disk in order to find out the code that were run on the
computer (Perumal, Norwawi, and Raman, 2015, pp. 19-23; Dykstra, and Sherman, 2013,
pp.S87-S95.).
Sampling size for four filters was used to compare images (Valjarevic, and Venter, 2015,
pp.1467-1483; Shields, Frieder, and Maloof, 2011, pp.3-13). It took approximately eight minutes
to relate the base image executables to the 21 RAM previews and roughly ten minutes to look at
the executables from that day picture circle to the accommodating RAM depictions. As indicated
by the distinction and a couple of lines of light scripting a timeline of the entire process was
established along with certain routine activities which can be discerned easily (Shields, Frieder,
and Maloof, 2011, pp.S3-S13). The size of the difference which actually grew over time was also
given for the same day, the days, as well as weekends that had no interesting results, were
skipped.
Based on the investigation, it is apparent that keylogger was installed on Pat’s computer
and later removed. If the RealVNC was not installed by Pat on the same date the keylogger was
installed, it could have also been used to look over his shoulder (Alazab, Venkatraman, and
Watters, 2009, pp.551-558; Garfinkel, 2010, pp.S64-S73). The total triage time for queries was
30 minutes plus an additional one and a half an hour for file hashing.
Because there was limited information with respect to timing to support the process of
investigation, all of the Pat’s RAM snap short were examined as well as the attempts to establish
all of the executables which are in the memory. During the process, we generated various file
hashes, every one of Pat's disks was mounted and hashed the majority of the individual
documents which took around one and a half an hour for eighteen images of 260 GB. The
memory pictures from Pat's PC were contrasted and the hashes of the .dll and the .exe records
which are on the circle pictures in his PC's disk in order to find out the code that were run on the
computer (Perumal, Norwawi, and Raman, 2015, pp. 19-23; Dykstra, and Sherman, 2013,
pp.S87-S95.).
Sampling size for four filters was used to compare images (Valjarevic, and Venter, 2015,
pp.1467-1483; Shields, Frieder, and Maloof, 2011, pp.3-13). It took approximately eight minutes
to relate the base image executables to the 21 RAM previews and roughly ten minutes to look at
the executables from that day picture circle to the accommodating RAM depictions. As indicated
by the distinction and a couple of lines of light scripting a timeline of the entire process was
established along with certain routine activities which can be discerned easily (Shields, Frieder,
and Maloof, 2011, pp.S3-S13). The size of the difference which actually grew over time was also
given for the same day, the days, as well as weekends that had no interesting results, were
skipped.
Based on the investigation, it is apparent that keylogger was installed on Pat’s computer
and later removed. If the RealVNC was not installed by Pat on the same date the keylogger was
installed, it could have also been used to look over his shoulder (Alazab, Venkatraman, and
Watters, 2009, pp.551-558; Garfinkel, 2010, pp.S64-S73). The total triage time for queries was
30 minutes plus an additional one and a half an hour for file hashing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Digital forensic investigation 10
Activity 2
For the purpose of this activity, Paraben email was downloaded and used as a tool for
investigation (Lillis, Becker, O'Sullivan, and Scanlon, 2016, pp. 75-134). Before diving into the
investigation, it is important to look at the importance of the email headers in the cases like the
scenario. Due to the fact that exfiltration occurs through email, it is essential to know what is
meant by the headers. The email headers keep a plentiful of data which are related to the specific
message in the email (Sindhu, and Meshram, 2012, p.39; Quick, and Choo, 2014, pp.273-294).
They are normally hidden, as such, only the text of the email is shown to the recipient of the
email. The email headers can be easily forgotten, they are also not veracious. Following this
rationale, the only part of the email which can be trusted is the part which is generated by the
user’s service i.e. the received part.
The investigation commenced by replicating the M57 organization employees’ emails
stated in the scenario script and then replica was mounted for analysis. The format of the image
was in the proprietary EnCase format (Mumba, and Venter, 2014, pp. 1-10; Zainudin, Merabti,
and Llewellyn-Jones, 2010, pp. 21-22). Various forensic software was used in mounting the
images including GUI front-end for the Sleuth kit tools as shown in figure 2.
Activity 2
For the purpose of this activity, Paraben email was downloaded and used as a tool for
investigation (Lillis, Becker, O'Sullivan, and Scanlon, 2016, pp. 75-134). Before diving into the
investigation, it is important to look at the importance of the email headers in the cases like the
scenario. Due to the fact that exfiltration occurs through email, it is essential to know what is
meant by the headers. The email headers keep a plentiful of data which are related to the specific
message in the email (Sindhu, and Meshram, 2012, p.39; Quick, and Choo, 2014, pp.273-294).
They are normally hidden, as such, only the text of the email is shown to the recipient of the
email. The email headers can be easily forgotten, they are also not veracious. Following this
rationale, the only part of the email which can be trusted is the part which is generated by the
user’s service i.e. the received part.
The investigation commenced by replicating the M57 organization employees’ emails
stated in the scenario script and then replica was mounted for analysis. The format of the image
was in the proprietary EnCase format (Mumba, and Venter, 2014, pp. 1-10; Zainudin, Merabti,
and Llewellyn-Jones, 2010, pp. 21-22). Various forensic software was used in mounting the
images including GUI front-end for the Sleuth kit tools as shown in figure 2.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Digital forensic investigation 11
Figure 2: the GUI front end for the Sleuth kit tools
According to the scenario, this case involves the emails that were sent using M57
organization machines. It is suspected that someone has spilled data concerning M57
organization's insider facts. We inspected the manner in which Charlie got to his messages. With
the end goal of this paper, we direct our concentration toward Charlie's machine and contrast the
executable from circle pictures and the comparing RAM depiction of the day. This examination
is encouraged by an example size of four where a correlation between each of the 18 RAM
pictures was done in 31 minutes (Perumal, 2009, pp.38-44; Casey, 2011, pp. 39-47; Seo, Lim,
and Lee, 2009, pp.182-190). During the study, we recognized the occurrence of a “Cygnus free
edition” hex editor as well as a program called “invisible secretes 2.1”. The program had a doll
called “bmpcarrier,” “blowfish,” and “jpgcarrier” supporting the suspicion that it is a
steganography tool (Rekhis, and Boudriga, 2011, pp.376-396; Taylor, Fritsch, and Liederbach,
2014). Another program named “insecr2.exe” which can be found on the network trace for date
19th November was found on Charlie’s USB drive, this is an evident that the file was
downloaded around the same time. The following stage was to recognize the information that
may have been exfiltrated in the USB drive.
After examination of the USB drive, the “astronaut” and “microscope” pairs of images
appeared to look the same, however, their hashes are not identical, and this supports the
suspicion that they must have been used for stego as carriers. The investigation of the
accompanying emails also supports the hypothesis. Investigating other possible exfiltration
carriers, it is found that seven zip files are present and the files were installed on date 24th
November. A password protected archive was also found in the USB drive which contains two
files apparently (Casey, Back, and Barnum, 2015, 12, pp.102-110). Examination of other files
Figure 2: the GUI front end for the Sleuth kit tools
According to the scenario, this case involves the emails that were sent using M57
organization machines. It is suspected that someone has spilled data concerning M57
organization's insider facts. We inspected the manner in which Charlie got to his messages. With
the end goal of this paper, we direct our concentration toward Charlie's machine and contrast the
executable from circle pictures and the comparing RAM depiction of the day. This examination
is encouraged by an example size of four where a correlation between each of the 18 RAM
pictures was done in 31 minutes (Perumal, 2009, pp.38-44; Casey, 2011, pp. 39-47; Seo, Lim,
and Lee, 2009, pp.182-190). During the study, we recognized the occurrence of a “Cygnus free
edition” hex editor as well as a program called “invisible secretes 2.1”. The program had a doll
called “bmpcarrier,” “blowfish,” and “jpgcarrier” supporting the suspicion that it is a
steganography tool (Rekhis, and Boudriga, 2011, pp.376-396; Taylor, Fritsch, and Liederbach,
2014). Another program named “insecr2.exe” which can be found on the network trace for date
19th November was found on Charlie’s USB drive, this is an evident that the file was
downloaded around the same time. The following stage was to recognize the information that
may have been exfiltrated in the USB drive.
After examination of the USB drive, the “astronaut” and “microscope” pairs of images
appeared to look the same, however, their hashes are not identical, and this supports the
suspicion that they must have been used for stego as carriers. The investigation of the
accompanying emails also supports the hypothesis. Investigating other possible exfiltration
carriers, it is found that seven zip files are present and the files were installed on date 24th
November. A password protected archive was also found in the USB drive which contains two
files apparently (Casey, Back, and Barnum, 2015, 12, pp.102-110). Examination of other files

Digital forensic investigation 12
from the USB drive in all RAM images of Charlie, the two files were found in memory. When
the zip files were correlated with the mail traffic, it was revealed that the file was part of
extortion scheme rather than exfiltration.
Activity 3
From the investigation in the activity 1, there is a satisfactory reason to suspect that one
of the organization’s computers was used in for illegal practices. The suspicion arose when one
of the computers the computers used by Jo got replaced and then sold online. As much as the
employee might have attempted to cover his tracks when the computer was investigated by the
police at the end of the scenario, however, it was already clear that one of the organization’s
computers was used for the illegal practices and the computer was initially used by Jo.
To additionally demonstrate that Jo was engaged with the act, the majority of Jo's
pictures were first questioned with the kitty sets. Since a full correlation thinks about the
majority of the process segments to the question records to the process parts of the objective
documents which would take a lot of time as 55 minutes at least will be taken to go through the
21 circle pictures, an option quicker technique was utilized (Imran, Aljawarneh, and Sakib, 2016,
pp.494-520; Omeleze, and Venter, 2013, pp. 1-8). The technique includes a significantly quicker
output by viably examining as just four bits of the first records were searched for. We turned out
to be more forceful and further utilized an inspecting size of two, which yield a similar outcome
for this situation at the expense of 96 seconds just for the majority of the pictures in the hard
plate of Jo's PC.
The results showing the number of record matches for every one of the dates of the
scenario were obtained and this provided the basics of initial hypothesis. From the results, it was
from the USB drive in all RAM images of Charlie, the two files were found in memory. When
the zip files were correlated with the mail traffic, it was revealed that the file was part of
extortion scheme rather than exfiltration.
Activity 3
From the investigation in the activity 1, there is a satisfactory reason to suspect that one
of the organization’s computers was used in for illegal practices. The suspicion arose when one
of the computers the computers used by Jo got replaced and then sold online. As much as the
employee might have attempted to cover his tracks when the computer was investigated by the
police at the end of the scenario, however, it was already clear that one of the organization’s
computers was used for the illegal practices and the computer was initially used by Jo.
To additionally demonstrate that Jo was engaged with the act, the majority of Jo's
pictures were first questioned with the kitty sets. Since a full correlation thinks about the
majority of the process segments to the question records to the process parts of the objective
documents which would take a lot of time as 55 minutes at least will be taken to go through the
21 circle pictures, an option quicker technique was utilized (Imran, Aljawarneh, and Sakib, 2016,
pp.494-520; Omeleze, and Venter, 2013, pp. 1-8). The technique includes a significantly quicker
output by viably examining as just four bits of the first records were searched for. We turned out
to be more forceful and further utilized an inspecting size of two, which yield a similar outcome
for this situation at the expense of 96 seconds just for the majority of the pictures in the hard
plate of Jo's PC.
The results showing the number of record matches for every one of the dates of the
scenario were obtained and this provided the basics of initial hypothesis. From the results, it was
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.