Digital Forensics Report: Analysis of a Workplace Crime Investigation
VerifiedAdded on 2022/10/17
|23
|7039
|53
Report
AI Summary
This report presents a detailed analysis of a workplace crime investigation using digital forensics, specifically focusing on network forensics and email analysis. The investigation utilizes Wireshark to intercept and analyze email packets, uncovering a chain of events involving suspected SPECTRE agents. The report outlines the steps taken, including the use of Network Miner for file categorization and the analysis of 'secret.pcap' and 'trash.dd' files. The chain of events reveals communication threads between the suspects, including discussions about intercepted files, leveraging information from a secretary, and the exchange of sensitive data. The report also covers the interaction between the suspects and the secretary, detailing the tactics used to obtain information. The analysis further explores a cloud-based forensics scenario. The report provides a comprehensive overview of the investigation, the tools used, and the key findings in solving the workplace crime.

Contents
Executive Summary.................................................................................................................. 2
Task 1..................................................................................................................................... 2
Introduction............................................................................................................................. 2
Chain of Events........................................................................................................................ 4
Tasks....................................................................................................................................... 8
Detailed Map of the suspects and their victims...........................................................................12
Timeline of events.................................................................................................................. 14
Task 2................................................................................................................................... 14
Introduction........................................................................................................................... 14
Previous Research................................................................................................................... 15
New Digital Forensics Project..................................................................................................17
Conclusion............................................................................................................................. 18
References............................................................................................................................. 20
Executive Summary.................................................................................................................. 2
Task 1..................................................................................................................................... 2
Introduction............................................................................................................................. 2
Chain of Events........................................................................................................................ 4
Tasks....................................................................................................................................... 8
Detailed Map of the suspects and their victims...........................................................................12
Timeline of events.................................................................................................................. 14
Task 2................................................................................................................................... 14
Introduction........................................................................................................................... 14
Previous Research................................................................................................................... 15
New Digital Forensics Project..................................................................................................17
Conclusion............................................................................................................................. 18
References............................................................................................................................. 20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Due to the increasing proliferation of technology since the middle 20th century as well as the
eventual importance of this technology in the conduct of criminal activity, the field of digital
forensics has become commonplace. The proof is usually visible in conventional forensics,
which could distinguish the suspect, such as skin, saliva, including fingerprints. Digital
forensics, on the other hand, deals with electronically processed data and information from
digital devices. Digital forensic science is a widely used term for identifying, collecting and
analyzing digital evidence from much more than just devices like smartphones, laptops, the
Internet of Things or perhaps even data which are deposited in the cloud. Network forensic
science is a sub-branch of digital forensics related to computer network traffic surveillance as
well as analysis for information collection, legal documentation, including intrusion detection
applications. In this paper, a practical case of workplace crime is analyzed and solved using
tools available in the sub-branch of digital forensics that is network forensics. Further ahead
in the paper, a report-based theoretical analysis on cloud-based forensics is also provided.
Task 1
Introduction
Steps used to carry out the investigation using the primary tool of investigation Wireshark:
● To begin with, several hundred packets were analyzed earlier in an attempt to uncover
the essence of what was going on.
● Upon analyzing, it was clear that the relevant packets were that of the Email protocol
where the essence of the case was.
● As a result, all of the email packets were intercepted and analyzed which then helped
frame the below mentioned chain of events.
● For this to happen, the latest version of Wireshark was used on Windows and step-by-
step each of the Email packets were intercepted and analyzed. The chain of events is
depicted further into the report below.
● Further ahead, network miner was used to help intercept all the files in the packet
capture. It further helped in categorizing different file types and placed it in different
sections.
● Without, Network miner, it would have been very difficult to carve the file as
removing the header information from the captured packets in order to isolate the DD
Due to the increasing proliferation of technology since the middle 20th century as well as the
eventual importance of this technology in the conduct of criminal activity, the field of digital
forensics has become commonplace. The proof is usually visible in conventional forensics,
which could distinguish the suspect, such as skin, saliva, including fingerprints. Digital
forensics, on the other hand, deals with electronically processed data and information from
digital devices. Digital forensic science is a widely used term for identifying, collecting and
analyzing digital evidence from much more than just devices like smartphones, laptops, the
Internet of Things or perhaps even data which are deposited in the cloud. Network forensic
science is a sub-branch of digital forensics related to computer network traffic surveillance as
well as analysis for information collection, legal documentation, including intrusion detection
applications. In this paper, a practical case of workplace crime is analyzed and solved using
tools available in the sub-branch of digital forensics that is network forensics. Further ahead
in the paper, a report-based theoretical analysis on cloud-based forensics is also provided.
Task 1
Introduction
Steps used to carry out the investigation using the primary tool of investigation Wireshark:
● To begin with, several hundred packets were analyzed earlier in an attempt to uncover
the essence of what was going on.
● Upon analyzing, it was clear that the relevant packets were that of the Email protocol
where the essence of the case was.
● As a result, all of the email packets were intercepted and analyzed which then helped
frame the below mentioned chain of events.
● For this to happen, the latest version of Wireshark was used on Windows and step-by-
step each of the Email packets were intercepted and analyzed. The chain of events is
depicted further into the report below.
● Further ahead, network miner was used to help intercept all the files in the packet
capture. It further helped in categorizing different file types and placed it in different
sections.
● Without, Network miner, it would have been very difficult to carve the file as
removing the header information from the captured packets in order to isolate the DD
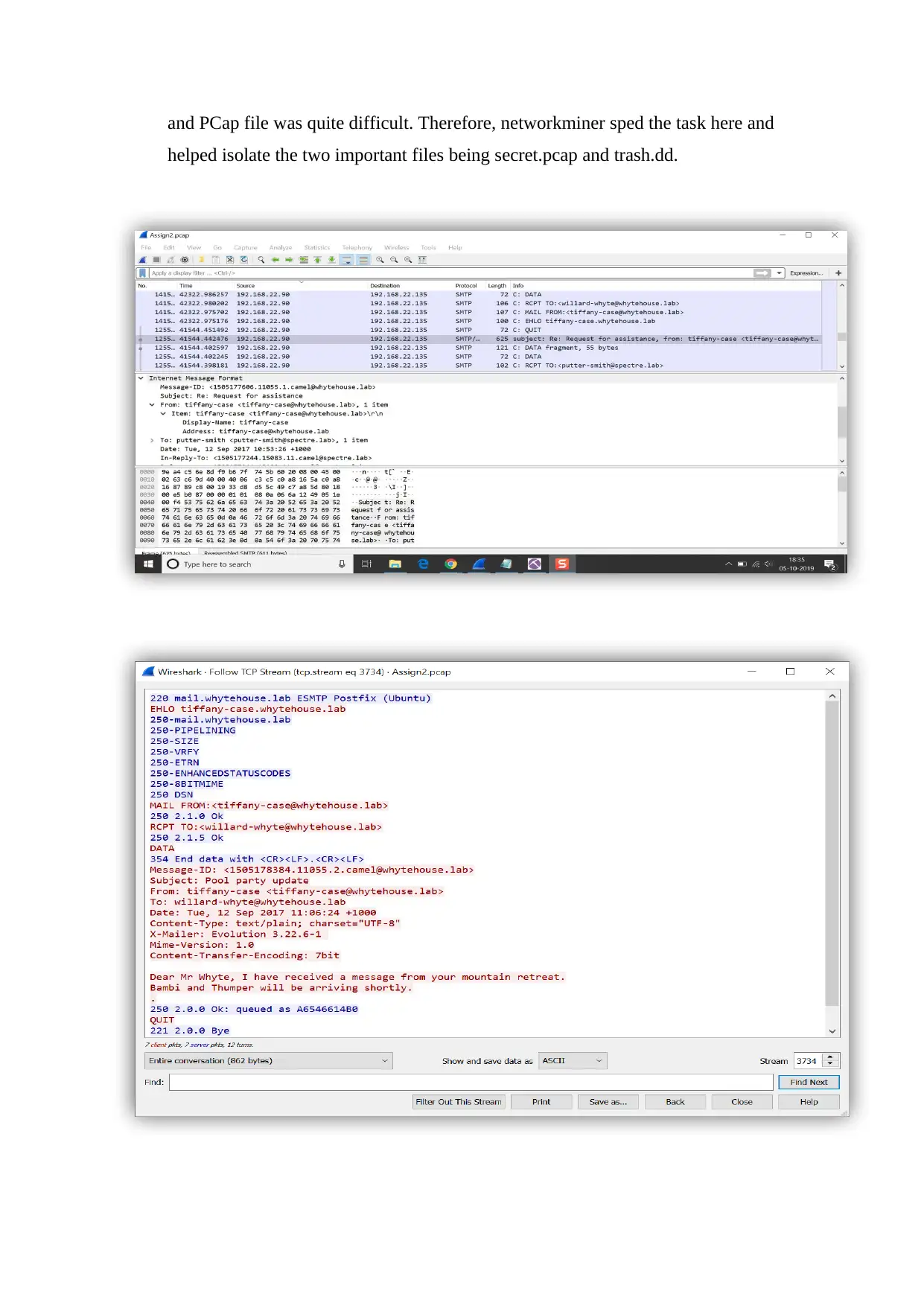
and PCap file was quite difficult. Therefore, networkminer sped the task here and
helped isolate the two important files being secret.pcap and trash.dd.
helped isolate the two important files being secret.pcap and trash.dd.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
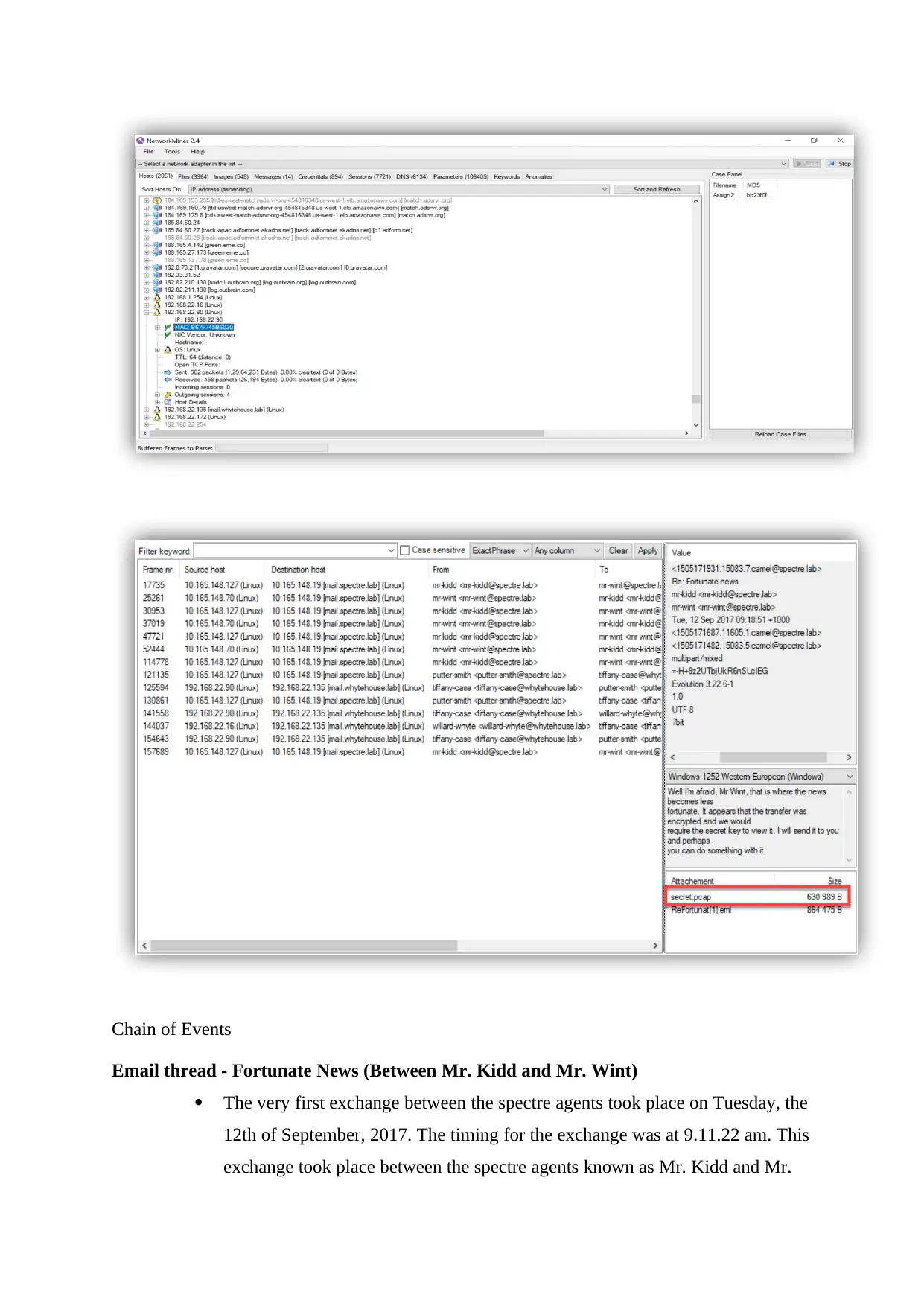
Chain of Events
Email thread - Fortunate News (Between Mr. Kidd and Mr. Wint)
The very first exchange between the spectre agents took place on Tuesday, the
12th of September, 2017. The timing for the exchange was at 9.11.22 am. This
exchange took place between the spectre agents known as Mr. Kidd and Mr.
Email thread - Fortunate News (Between Mr. Kidd and Mr. Wint)
The very first exchange between the spectre agents took place on Tuesday, the
12th of September, 2017. The timing for the exchange was at 9.11.22 am. This
exchange took place between the spectre agents known as Mr. Kidd and Mr.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wint. The message was sent by Mr. Kidd and the recipient being Mr. Fint. The
message was sent from Evolution mail client which is at version 3.22 and was
developed by the GNOME and is part of the Linux environment. The
message’s subject was ‘Fortunate News’ which indicates that Mr. Kidd was
bringing up some critical development updates to Mr. Fint. The message
contained a message that said that Mr. Kidd has found or perhaps intercepted a
file transfer sent by Mr. Whyte who at this point is an unknown entity as to
whether he is a part of Spectre or something else. Also, the relationship with
the other two Spectre agents are unknown at this point. The message said that
the file has been intercepted by Mr. Kidd and that the file had come from
slumber.inc.
A follow-up reply was done by the Spectre agent Mr. Wint who approved of
the message and praised Mr. Kidd. This follow-up reply was sent by Mr. Wint
to Mr. Kidd by 9.14.47 am of the same day which is 12th September, 2017
and was within 3 minutes of the first message being sent. The message
specifically said that Mr. Wint was curious as to whether the file that had been
intercepted by Mr. Kidd had been the ‘one’ that they were after. This means
that, both of these Spectre agents were specifically after some information
involving Mr. Whyte and Slumber.inc and that this file interception could
have been that.
A follow-up reply was done by the Spectre agent Mr. Kidd who initially broke
the fortunate news to Mr. Wint. This message was a bit of disapproval. This
message was sent by Mr. Kidd to Mr. Wint by 9.18 which is again within 3 to
4 minutes of the previous reply by Mr. Wint. The message said that the file
intercepted by Mr. Kidd was encrypted and that it needs a key to decode or
analyze it. The message further said that the file would then be sent by Mr.
Kidd to Mr. Wint so that he can see if he can do anything about it.
Simultaneously, in the same conversation email Mr. Kidd had attached the file
as an attachment. This file was named as ‘secret.pcap’ indicating that this was
perhaps a packet capture of Mr. Whyte’s internet traffic.
message was sent from Evolution mail client which is at version 3.22 and was
developed by the GNOME and is part of the Linux environment. The
message’s subject was ‘Fortunate News’ which indicates that Mr. Kidd was
bringing up some critical development updates to Mr. Fint. The message
contained a message that said that Mr. Kidd has found or perhaps intercepted a
file transfer sent by Mr. Whyte who at this point is an unknown entity as to
whether he is a part of Spectre or something else. Also, the relationship with
the other two Spectre agents are unknown at this point. The message said that
the file has been intercepted by Mr. Kidd and that the file had come from
slumber.inc.
A follow-up reply was done by the Spectre agent Mr. Wint who approved of
the message and praised Mr. Kidd. This follow-up reply was sent by Mr. Wint
to Mr. Kidd by 9.14.47 am of the same day which is 12th September, 2017
and was within 3 minutes of the first message being sent. The message
specifically said that Mr. Wint was curious as to whether the file that had been
intercepted by Mr. Kidd had been the ‘one’ that they were after. This means
that, both of these Spectre agents were specifically after some information
involving Mr. Whyte and Slumber.inc and that this file interception could
have been that.
A follow-up reply was done by the Spectre agent Mr. Kidd who initially broke
the fortunate news to Mr. Wint. This message was a bit of disapproval. This
message was sent by Mr. Kidd to Mr. Wint by 9.18 which is again within 3 to
4 minutes of the previous reply by Mr. Wint. The message said that the file
intercepted by Mr. Kidd was encrypted and that it needs a key to decode or
analyze it. The message further said that the file would then be sent by Mr.
Kidd to Mr. Wint so that he can see if he can do anything about it.
Simultaneously, in the same conversation email Mr. Kidd had attached the file
as an attachment. This file was named as ‘secret.pcap’ indicating that this was
perhaps a packet capture of Mr. Whyte’s internet traffic.
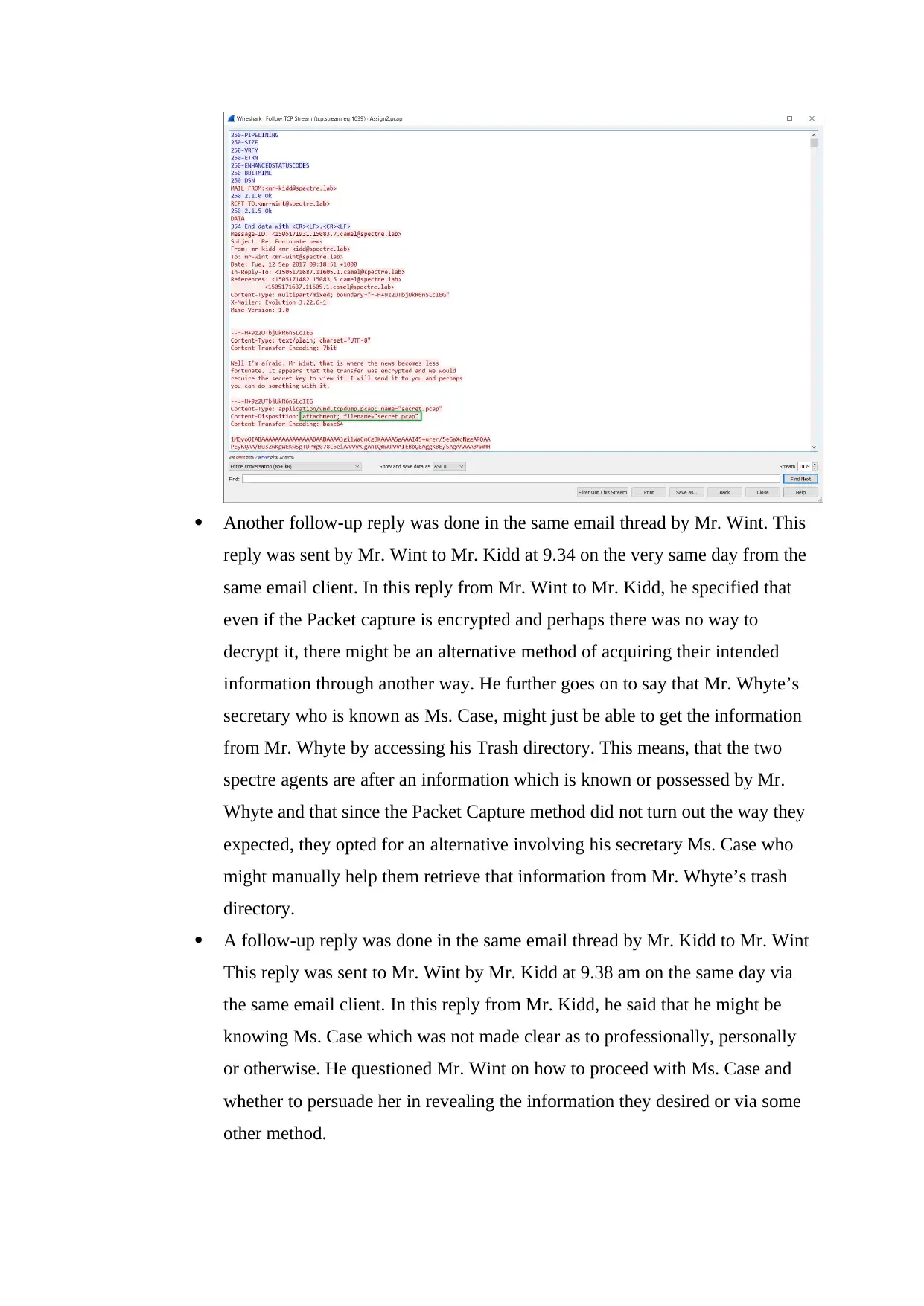
Another follow-up reply was done in the same email thread by Mr. Wint. This
reply was sent by Mr. Wint to Mr. Kidd at 9.34 on the very same day from the
same email client. In this reply from Mr. Wint to Mr. Kidd, he specified that
even if the Packet capture is encrypted and perhaps there was no way to
decrypt it, there might be an alternative method of acquiring their intended
information through another way. He further goes on to say that Mr. Whyte’s
secretary who is known as Ms. Case, might just be able to get the information
from Mr. Whyte by accessing his Trash directory. This means, that the two
spectre agents are after an information which is known or possessed by Mr.
Whyte and that since the Packet Capture method did not turn out the way they
expected, they opted for an alternative involving his secretary Ms. Case who
might manually help them retrieve that information from Mr. Whyte’s trash
directory.
A follow-up reply was done in the same email thread by Mr. Kidd to Mr. Wint
This reply was sent to Mr. Wint by Mr. Kidd at 9.38 am on the same day via
the same email client. In this reply from Mr. Kidd, he said that he might be
knowing Ms. Case which was not made clear as to professionally, personally
or otherwise. He questioned Mr. Wint on how to proceed with Ms. Case and
whether to persuade her in revealing the information they desired or via some
other method.
reply was sent by Mr. Wint to Mr. Kidd at 9.34 on the very same day from the
same email client. In this reply from Mr. Wint to Mr. Kidd, he specified that
even if the Packet capture is encrypted and perhaps there was no way to
decrypt it, there might be an alternative method of acquiring their intended
information through another way. He further goes on to say that Mr. Whyte’s
secretary who is known as Ms. Case, might just be able to get the information
from Mr. Whyte by accessing his Trash directory. This means, that the two
spectre agents are after an information which is known or possessed by Mr.
Whyte and that since the Packet Capture method did not turn out the way they
expected, they opted for an alternative involving his secretary Ms. Case who
might manually help them retrieve that information from Mr. Whyte’s trash
directory.
A follow-up reply was done in the same email thread by Mr. Kidd to Mr. Wint
This reply was sent to Mr. Wint by Mr. Kidd at 9.38 am on the same day via
the same email client. In this reply from Mr. Kidd, he said that he might be
knowing Ms. Case which was not made clear as to professionally, personally
or otherwise. He questioned Mr. Wint on how to proceed with Ms. Case and
whether to persuade her in revealing the information they desired or via some
other method.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Another follow-up reply was done in the same email thread. This reply was
sent at 9.56 am. The reply was sent by Mr. Wint to Mr. Kidd. Based on the
previous conversation, Mr. Kidd has asked Mr. Wint on how to persuade Ms.
Case to reveal the information they were after from Mr. Whyte. So now, Mr.
Wint had come up with an idea. In this email, Mr. Wint, reveals that there was
a memory dump of Ms. Case’s computer while she was working at the office
and was perhaps doing something personal, un-professional, unethical or
illegal. This memory dump was found by Mr. Wint and it could be used to
expose the activity of Ms. Case which would get Ms. Case in trouble. Now,
this memory dump was kept at Slumber.inc and Mr. Wint instructed to see this
memory dump and use that as leverage against Ms. Case to pursue her to do
what these two Spectre agents were after.
A simple follow-up reply was done in the same email thread by Mr. Kidd to
Mr. Wint at 10.42 am using the same email client. In this email, Mr. Kidd
thanked Mr. Wint of helping him with this information which could help them
both use Ms. Case to carry out their ulterior motives. This conversation ended
here, indicating that Mr. Kidd might continue with the plan.
A new email was sent by Mr. Kidd to Mr. Wint at around 11.26 am. This
email was sent on the very same email thread which was originally titled
‘Fortunate News’. This email by Mr. Kidd revealed that he had found the
information sent by Mr. Wint to be useful and that he has now what he needs.
This implies that, in the previous email that was sent by Mr. Kidd to Mr. Wint
at 10.42 am, Mr. Wint had told him that there was a secret information that
could be used as a leverage point against Ms. Case. So, it essentially proves
that the leverage against Ms. Case was successful and that the image of trash
directory sent by Ms. Case as a result of using that leverage had also proved to
be exactly what they were after.
Email Thread - Request for Assistance (Between Mr. Smith and Ms. Case)
A new email was sent by Mr. Smith to Ms. Case on the very same day that is
Tuesday, the 12th of September, 2017 at 10.47 am. This message was sent by Mr.
Smith using the same email client and within 5 minutes of the previous conversation
between Mr. Kidd and Mr. Wint wherein they decided to take up the matter with Ms.
Case. The email was sent with a subject as ‘Request for Assistance’ and the message
said that Mr. Smith was from the IT department at the Whytehouse and that he was
sent at 9.56 am. The reply was sent by Mr. Wint to Mr. Kidd. Based on the
previous conversation, Mr. Kidd has asked Mr. Wint on how to persuade Ms.
Case to reveal the information they were after from Mr. Whyte. So now, Mr.
Wint had come up with an idea. In this email, Mr. Wint, reveals that there was
a memory dump of Ms. Case’s computer while she was working at the office
and was perhaps doing something personal, un-professional, unethical or
illegal. This memory dump was found by Mr. Wint and it could be used to
expose the activity of Ms. Case which would get Ms. Case in trouble. Now,
this memory dump was kept at Slumber.inc and Mr. Wint instructed to see this
memory dump and use that as leverage against Ms. Case to pursue her to do
what these two Spectre agents were after.
A simple follow-up reply was done in the same email thread by Mr. Kidd to
Mr. Wint at 10.42 am using the same email client. In this email, Mr. Kidd
thanked Mr. Wint of helping him with this information which could help them
both use Ms. Case to carry out their ulterior motives. This conversation ended
here, indicating that Mr. Kidd might continue with the plan.
A new email was sent by Mr. Kidd to Mr. Wint at around 11.26 am. This
email was sent on the very same email thread which was originally titled
‘Fortunate News’. This email by Mr. Kidd revealed that he had found the
information sent by Mr. Wint to be useful and that he has now what he needs.
This implies that, in the previous email that was sent by Mr. Kidd to Mr. Wint
at 10.42 am, Mr. Wint had told him that there was a secret information that
could be used as a leverage point against Ms. Case. So, it essentially proves
that the leverage against Ms. Case was successful and that the image of trash
directory sent by Ms. Case as a result of using that leverage had also proved to
be exactly what they were after.
Email Thread - Request for Assistance (Between Mr. Smith and Ms. Case)
A new email was sent by Mr. Smith to Ms. Case on the very same day that is
Tuesday, the 12th of September, 2017 at 10.47 am. This message was sent by Mr.
Smith using the same email client and within 5 minutes of the previous conversation
between Mr. Kidd and Mr. Wint wherein they decided to take up the matter with Ms.
Case. The email was sent with a subject as ‘Request for Assistance’ and the message
said that Mr. Smith was from the IT department at the Whytehouse and that he was
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
looking for Ms. Case’s assistance. For the same, Mr. Smith had requested Ms. Case to
take an ‘image’ of Mr. Whyte’s trash directory and send it to him.
An immediate reply was given by Ms. Case to Mr. Smith on the very same email
thread on the very same day after a few minutes at 10.53 am. The reply said that, she
was aware that Mr. Smith was not from the same IT Department and that this ‘Social
Engineering’ tactic that Mr. Smith tried to pull off with Ms. Case did not work. Ms.
Case therefore showed hesitation and reluctance in doing the task she was asked to
do.
A follow-up reply was sent by Mr. Smith to Ms. Case on the same email thread on the
same day at 10.58 am and it said that Mr. Smith insisted on handling this matter in
civilized manner. He said that he was aware of Ms. Case doing something that she
was not supposed to be doing and that too during working hours of the company. He
further specified that she was doing it again in the same morning and that he would
tell on her to Mr. Whyte regarding the same.
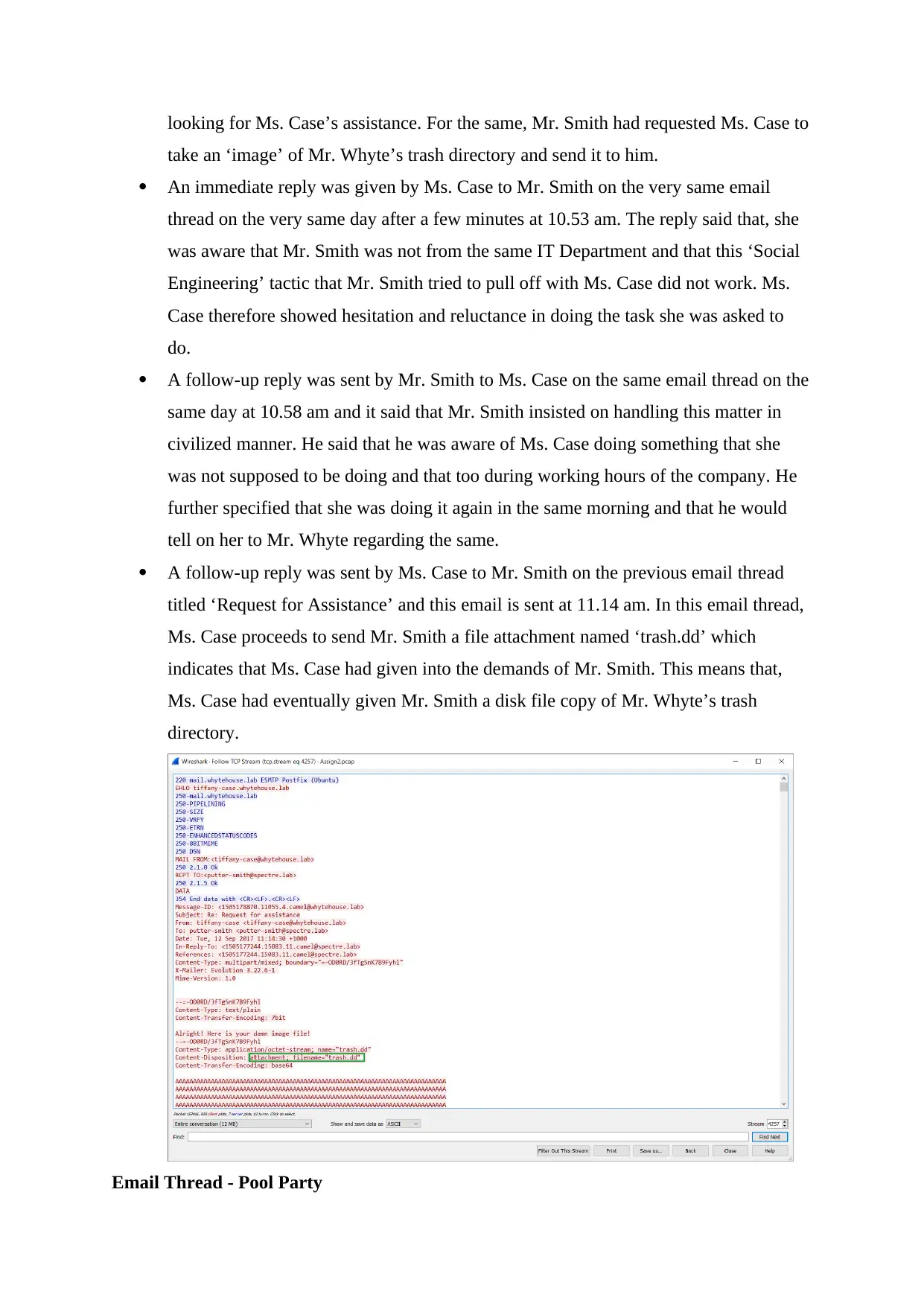
A follow-up reply was sent by Ms. Case to Mr. Smith on the previous email thread
titled ‘Request for Assistance’ and this email is sent at 11.14 am. In this email thread,
Ms. Case proceeds to send Mr. Smith a file attachment named ‘trash.dd’ which
indicates that Ms. Case had given into the demands of Mr. Smith. This means that,
Ms. Case had eventually given Mr. Smith a disk file copy of Mr. Whyte’s trash
directory.
Email Thread - Pool Party
take an ‘image’ of Mr. Whyte’s trash directory and send it to him.
An immediate reply was given by Ms. Case to Mr. Smith on the very same email
thread on the very same day after a few minutes at 10.53 am. The reply said that, she
was aware that Mr. Smith was not from the same IT Department and that this ‘Social
Engineering’ tactic that Mr. Smith tried to pull off with Ms. Case did not work. Ms.
Case therefore showed hesitation and reluctance in doing the task she was asked to
do.
A follow-up reply was sent by Mr. Smith to Ms. Case on the same email thread on the
same day at 10.58 am and it said that Mr. Smith insisted on handling this matter in
civilized manner. He said that he was aware of Ms. Case doing something that she
was not supposed to be doing and that too during working hours of the company. He
further specified that she was doing it again in the same morning and that he would
tell on her to Mr. Whyte regarding the same.
A follow-up reply was sent by Ms. Case to Mr. Smith on the previous email thread
titled ‘Request for Assistance’ and this email is sent at 11.14 am. In this email thread,
Ms. Case proceeds to send Mr. Smith a file attachment named ‘trash.dd’ which
indicates that Ms. Case had given into the demands of Mr. Smith. This means that,
Ms. Case had eventually given Mr. Smith a disk file copy of Mr. Whyte’s trash
directory.
Email Thread - Pool Party

A new email was initiated by Ms. Case to Mr. Whyte on the same day at 11.06 am
which was around 7 minutes after their email conversation with Mr. Smith. The
subject was titled as ‘Pool Party Update’ and it mentioned something about two
people arriving for the mountain retreat. The email also mentioned about some people
called as Bambi and Thumper.
A follow-up reply was sent by Mr. Whyte to Ms. Case immediately by 11.09 am on
the same day and email thread. The message instructed Ms. Case to cancel Mr.
Whyte’s all afternoon meetings.
Tasks
1. What was the first communication between the suspected SPECTRE agents?
The very first communication took place on September 12th, 2017. This was an email
conversation and it took place between Mr. Wint and Mr. Kidd as being the two suspected
Spectre agents. It was sent by Mr. Kidd to Mr. Wint and it was sent at 9.11 in the morning.
2. What did the suspected SPECTRE agents exchange?
The two spectre agents being Mr. Kidd and Mr. Wint were exchanging conversations over
Emails in the morning of September 12trh, 2017. Their conversation was covert type. Mr.
Kidd and Mr. Wint began talking about having the good news wherein they had intercepted
some conversation from Mr. Whyte. This communication was captured in a packet capture
file. They further continued having this conversation over several emails wherein it was
revealed that they would eventually make use of Ms. Case who works at Whytehouse and is a
secretary to Mr. Whyte. Their plan was to either hoodwink or blackmail her into sending
them a file which was from Mr. Whyte. They planned and executed this operation over
several emails and ultimately leading to success in the end when Ms. Case finally give into
their demands and eventually send them the requested file.
3. What was used to blackmail Tiffany Case?
It was not made completely clear as to what was used to Blackmail Ms. Case. However, Mr.
Smith on his Email to Ms. Case on 12th September, 2017. The very first mail by Mr. Smith at
10.47 used a social engineering tactic wherein Mr. Smith claimed to work in the same
organization as that of Ms. Case. In this social engineering tactic, Mr. Smith further claimed
that he worked in the IT department and that he needed the image file of the trash directory of
which was around 7 minutes after their email conversation with Mr. Smith. The
subject was titled as ‘Pool Party Update’ and it mentioned something about two
people arriving for the mountain retreat. The email also mentioned about some people
called as Bambi and Thumper.
A follow-up reply was sent by Mr. Whyte to Ms. Case immediately by 11.09 am on
the same day and email thread. The message instructed Ms. Case to cancel Mr.
Whyte’s all afternoon meetings.
Tasks
1. What was the first communication between the suspected SPECTRE agents?
The very first communication took place on September 12th, 2017. This was an email
conversation and it took place between Mr. Wint and Mr. Kidd as being the two suspected
Spectre agents. It was sent by Mr. Kidd to Mr. Wint and it was sent at 9.11 in the morning.
2. What did the suspected SPECTRE agents exchange?
The two spectre agents being Mr. Kidd and Mr. Wint were exchanging conversations over
Emails in the morning of September 12trh, 2017. Their conversation was covert type. Mr.
Kidd and Mr. Wint began talking about having the good news wherein they had intercepted
some conversation from Mr. Whyte. This communication was captured in a packet capture
file. They further continued having this conversation over several emails wherein it was
revealed that they would eventually make use of Ms. Case who works at Whytehouse and is a
secretary to Mr. Whyte. Their plan was to either hoodwink or blackmail her into sending
them a file which was from Mr. Whyte. They planned and executed this operation over
several emails and ultimately leading to success in the end when Ms. Case finally give into
their demands and eventually send them the requested file.
3. What was used to blackmail Tiffany Case?
It was not made completely clear as to what was used to Blackmail Ms. Case. However, Mr.
Smith on his Email to Ms. Case on 12th September, 2017. The very first mail by Mr. Smith at
10.47 used a social engineering tactic wherein Mr. Smith claimed to work in the same
organization as that of Ms. Case. In this social engineering tactic, Mr. Smith further claimed
that he worked in the IT department and that he needed the image file of the trash directory of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mr. Whyte in order to debug some errors in the system they were having. This was a made-
up story that was conceived to deceive Ms. Case, however, Ms. Case’s alertness and
vigilance proved helpful here and she was able to prevent Mr. Smith’s social engineering
attack. Later on, however, Mr. Smith came up with another plan wherein he figured out that
there was a memory dump of Ms. Case’s computer and they knew what she was doing during
the company’s time. This was discussed between Mr. Wint and Mr. Kidd in the 9.56 am
Email that was exchanged between them. Mr. Smith, then used this information to blackmail
her in a follow-up email at 10.58 am. In the final email sent by Ms. Case to Mr. Smith, it can
be observed that, she finally had acquired the image file and sent it to Mr. Smith in the email
timed 11.14 am.
Who is Putter Smith?
Mr. Smith very first appeared in the packet capture when he sent the first Email to Ms. Case
asking for Assistance using the aforementioned social engineering tactic. He was trying to
hoodwink Ms. Case by telling her he was from the same company and their IT Department.
The very first email which was with the subject line - ‘Request for Assistance’ was sent to
Ms. Case at 10.47 am. Prior to that, 5 minutes ago, between Mr. Wint and Mr. Kidd wherein
Mr. Kidd had revealed that he has some information that can be used as a leverage point
against Ms. Case. Right after that in 5 minutes, the email was sent to Ms. Case titled ‘Request
for Assistance’ wherein Mr. Smith used a social engineering tactic on her. Upon failing that,
Mr. Smith quickly retorted to sending another email wherein he blackmailed her of having an
information against her wherein she was doing something during company’s official working
hours. Ms. Case sent the requested file to Mr. Smith at around 11.14 am and 12 minutes post
that, Mr. Kidd sent an email to Mr. Wint wherein he said that he had what they needed. So,
this implies that there is a possibility that Mr. Kidd is Mr. Smith wherein Mr. Smith is just a
Pseudonym or Alias used by Mr. Kidd to carry out their ulterior motives. This deduction,
further becomes a probability that Mr. Kidd is Mr. Smith because both of the email addresses
typically originate from the IP address - 10.165.148.127.
up story that was conceived to deceive Ms. Case, however, Ms. Case’s alertness and
vigilance proved helpful here and she was able to prevent Mr. Smith’s social engineering
attack. Later on, however, Mr. Smith came up with another plan wherein he figured out that
there was a memory dump of Ms. Case’s computer and they knew what she was doing during
the company’s time. This was discussed between Mr. Wint and Mr. Kidd in the 9.56 am
Email that was exchanged between them. Mr. Smith, then used this information to blackmail
her in a follow-up email at 10.58 am. In the final email sent by Ms. Case to Mr. Smith, it can
be observed that, she finally had acquired the image file and sent it to Mr. Smith in the email
timed 11.14 am.
Who is Putter Smith?
Mr. Smith very first appeared in the packet capture when he sent the first Email to Ms. Case
asking for Assistance using the aforementioned social engineering tactic. He was trying to
hoodwink Ms. Case by telling her he was from the same company and their IT Department.
The very first email which was with the subject line - ‘Request for Assistance’ was sent to
Ms. Case at 10.47 am. Prior to that, 5 minutes ago, between Mr. Wint and Mr. Kidd wherein
Mr. Kidd had revealed that he has some information that can be used as a leverage point
against Ms. Case. Right after that in 5 minutes, the email was sent to Ms. Case titled ‘Request
for Assistance’ wherein Mr. Smith used a social engineering tactic on her. Upon failing that,
Mr. Smith quickly retorted to sending another email wherein he blackmailed her of having an
information against her wherein she was doing something during company’s official working
hours. Ms. Case sent the requested file to Mr. Smith at around 11.14 am and 12 minutes post
that, Mr. Kidd sent an email to Mr. Wint wherein he said that he had what they needed. So,
this implies that there is a possibility that Mr. Kidd is Mr. Smith wherein Mr. Smith is just a
Pseudonym or Alias used by Mr. Kidd to carry out their ulterior motives. This deduction,
further becomes a probability that Mr. Kidd is Mr. Smith because both of the email addresses
typically originate from the IP address - 10.165.148.127.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
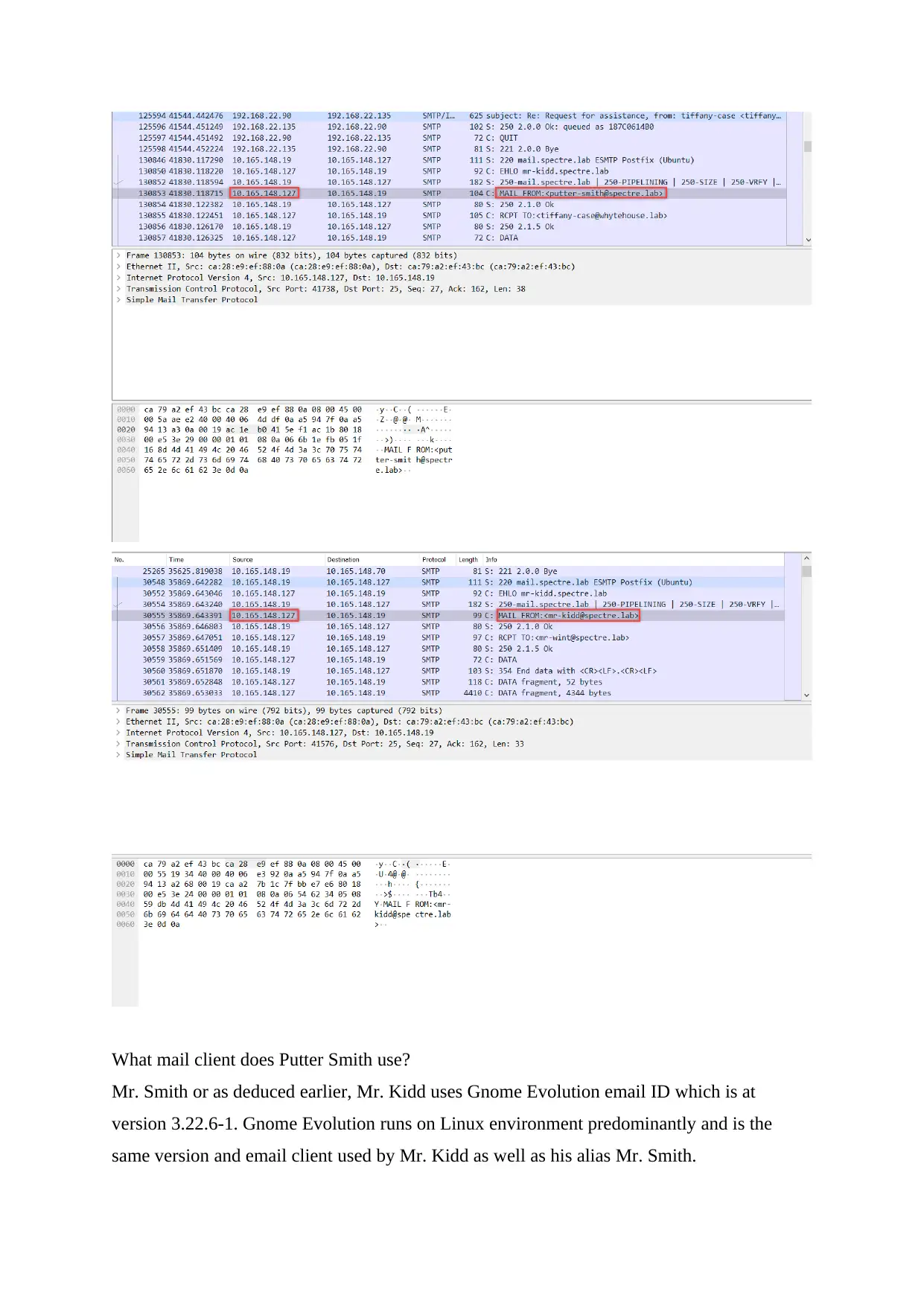
What mail client does Putter Smith use?
Mr. Smith or as deduced earlier, Mr. Kidd uses Gnome Evolution email ID which is at
version 3.22.6-1. Gnome Evolution runs on Linux environment predominantly and is the
same version and email client used by Mr. Kidd as well as his alias Mr. Smith.
Mr. Smith or as deduced earlier, Mr. Kidd uses Gnome Evolution email ID which is at
version 3.22.6-1. Gnome Evolution runs on Linux environment predominantly and is the
same version and email client used by Mr. Kidd as well as his alias Mr. Smith.

What was the operating system running on Tiffany Case’s PC?
Ms. Case is the secretary of Mr. Whyte at Whytehouse and is first introduced properly in the
Packet Capture chain of events when she receives an email from Mr. Smith with the subject
line - Request for Assistance sent at 10.47 am. The operating system running on Ms. Case’s
PC is Ubuntu OS.
What was Tiffany Case looking at that she shouldn’t be?
Ms. Case is introduced first in the chain of events of packet capture is in the 4th email
exchange between Mr. Wint and Mr. Kidd wherein Mr. Wint reveals that he has some
information on Ms. Case acquired through her PC’s memory dump wherein she was looking
at something during company hours which she shouldn’t be. The nature of the activity is not
disclosed by the two anywhere and is neither mentioned by Ms. Case. Also, at the same time,
it is also not made clear as to whether it was a highly illegal activity being done by Ms. Case.
This goes on to conclude that perhaps she was looking at something she wasn’t supposed to
during company hours. This means, that it could be anything such as being on personal Social
Media, Personal Email, watching videos for entertainment and so on. However, it would be
against the company policy to do so, which might’ve gotten her startled which eventually led
her to give into the demands of Mr. Smith or Mr. Kidd.
What was in the trash directory?
The trash.dd file was first introduced in Packet Capture chain of events in the fourth email
being discussed between Mr. Kidd and Mr. Wint wherein they mentioned about accessing
Mr. Whyte’s directory. As a result, through the eventual course of action and because of the
well-executed plan, they find Mr. Whyte’s trash directory image. Upon examining this image
file, it was found that it has ext4 file extension indicating that it originated from a Linux
based operating system. Further ahead, the file image contains the following list of files:
a) .journal file b) Inode c) secret.key d) secret.pcap (deleted file). The secret.key file when
viewed with text editor, shows SSL/TLS encrypted records of website visits. This is the same
key file that Mr. Kidd had mentioned to Mr. Wint that they needed to decode the encrypted
transfer of Mr. Whyte.
In order to see what was in the trash directory, FTK Imager as well as WINHex was used.
The FTK imager helped in mounting the image file into Windows directory. Post this,
WinHex was used to read the image file mounted. However, it won’t read the logical volume
Ms. Case is the secretary of Mr. Whyte at Whytehouse and is first introduced properly in the
Packet Capture chain of events when she receives an email from Mr. Smith with the subject
line - Request for Assistance sent at 10.47 am. The operating system running on Ms. Case’s
PC is Ubuntu OS.
What was Tiffany Case looking at that she shouldn’t be?
Ms. Case is introduced first in the chain of events of packet capture is in the 4th email
exchange between Mr. Wint and Mr. Kidd wherein Mr. Wint reveals that he has some
information on Ms. Case acquired through her PC’s memory dump wherein she was looking
at something during company hours which she shouldn’t be. The nature of the activity is not
disclosed by the two anywhere and is neither mentioned by Ms. Case. Also, at the same time,
it is also not made clear as to whether it was a highly illegal activity being done by Ms. Case.
This goes on to conclude that perhaps she was looking at something she wasn’t supposed to
during company hours. This means, that it could be anything such as being on personal Social
Media, Personal Email, watching videos for entertainment and so on. However, it would be
against the company policy to do so, which might’ve gotten her startled which eventually led
her to give into the demands of Mr. Smith or Mr. Kidd.
What was in the trash directory?
The trash.dd file was first introduced in Packet Capture chain of events in the fourth email
being discussed between Mr. Kidd and Mr. Wint wherein they mentioned about accessing
Mr. Whyte’s directory. As a result, through the eventual course of action and because of the
well-executed plan, they find Mr. Whyte’s trash directory image. Upon examining this image
file, it was found that it has ext4 file extension indicating that it originated from a Linux
based operating system. Further ahead, the file image contains the following list of files:
a) .journal file b) Inode c) secret.key d) secret.pcap (deleted file). The secret.key file when
viewed with text editor, shows SSL/TLS encrypted records of website visits. This is the same
key file that Mr. Kidd had mentioned to Mr. Wint that they needed to decode the encrypted
transfer of Mr. Whyte.
In order to see what was in the trash directory, FTK Imager as well as WINHex was used.
The FTK imager helped in mounting the image file into Windows directory. Post this,
WinHex was used to read the image file mounted. However, it won’t read the logical volume
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
