Cyber Security Risk Assessment and Treatment: Digital Fruit Report
VerifiedAdded on 2023/05/31
|31
|5453
|216
Report
AI Summary
This report provides a comprehensive analysis of cyber security management for Digital Fruit, an Estonian company specializing in mobile phone and web solutions. It identifies critical business processes, information assets, and IT assets, along with potential threats and vulnerabilities. The report includes a detailed risk assessment with probability and impact analysis, culminating in the development and implementation of cyber security controls and monitoring strategies. Key areas covered include business process dependency, asset valuation, threat categorization, vulnerability scanning, risk treatment options, and the development of a risk matrix. The report also proposes cyber-security measures and indicators for continuous improvement, including incident handling and mitigation strategies.

Running head: CYBER SECURITY MANAGEMENT
Cyber Security Management
(Digital Fruit)
Name of the student:
Name of the university:
Author Note
Cyber Security Management
(Digital Fruit)
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY MANAGEMENT
Table of Contents
List of Figures........................................................................................................................................3
List of Tables.........................................................................................................................................4
Introduction:..........................................................................................................................................6
Identifying critical business processes, information assets and IT assets:............................................6
1. Demonstrating business process and highlighting critical information systems:..........................7
2. Determining primary information assets and IT assets:................................................................7
3. Understanding asset valuations:....................................................................................................8
4. Conducting a business impact analysis:........................................................................................8
Threats and vulnerabilities identification:.............................................................................................9
5. Identification of proper threats:.....................................................................................................9
6. Identification of proper vulnerabilities through categorization:..................................................10
Probability and impact assessment:.....................................................................................................11
7. Developing a risk situation:.........................................................................................................11
8. Developing appropriate probability scale:...................................................................................12
9. Developing appropriate impact scale:.........................................................................................13
Information and cybersecurity risk assessment and risk treatment:....................................................13
10. Developing a risk matrix:..........................................................................................................14
11. Providing risk assessments:.......................................................................................................14
12. Identifying most critical risks:...................................................................................................16
Table of Contents
List of Figures........................................................................................................................................3
List of Tables.........................................................................................................................................4
Introduction:..........................................................................................................................................6
Identifying critical business processes, information assets and IT assets:............................................6
1. Demonstrating business process and highlighting critical information systems:..........................7
2. Determining primary information assets and IT assets:................................................................7
3. Understanding asset valuations:....................................................................................................8
4. Conducting a business impact analysis:........................................................................................8
Threats and vulnerabilities identification:.............................................................................................9
5. Identification of proper threats:.....................................................................................................9
6. Identification of proper vulnerabilities through categorization:..................................................10
Probability and impact assessment:.....................................................................................................11
7. Developing a risk situation:.........................................................................................................11
8. Developing appropriate probability scale:...................................................................................12
9. Developing appropriate impact scale:.........................................................................................13
Information and cybersecurity risk assessment and risk treatment:....................................................13
10. Developing a risk matrix:..........................................................................................................14
11. Providing risk assessments:.......................................................................................................14
12. Identifying most critical risks:...................................................................................................16

2CYBER SECURITY MANAGEMENT
13. Describing risk treatment options:.............................................................................................17
Information and cyber security controls development and implementation:......................................17
14. Controls to be undertaken and its order:....................................................................................17
15. Principal controls of implementation plan:................................................................................18
16. Advice provided to Digital Fruit regarding cybersecurity:........................................................19
Cyber-security measures:.....................................................................................................................20
17. Describe what to measure:.........................................................................................................20
18. Proposing some indicators:........................................................................................................20
19. Understanding cyber-security incident handling:......................................................................23
20. Improving over time:.................................................................................................................26
Conclusion:..........................................................................................................................................27
References:..........................................................................................................................................28
13. Describing risk treatment options:.............................................................................................17
Information and cyber security controls development and implementation:......................................17
14. Controls to be undertaken and its order:....................................................................................17
15. Principal controls of implementation plan:................................................................................18
16. Advice provided to Digital Fruit regarding cybersecurity:........................................................19
Cyber-security measures:.....................................................................................................................20
17. Describe what to measure:.........................................................................................................20
18. Proposing some indicators:........................................................................................................20
19. Understanding cyber-security incident handling:......................................................................23
20. Improving over time:.................................................................................................................26
Conclusion:..........................................................................................................................................27
References:..........................................................................................................................................28
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY MANAGEMENT
List of Figures
Figure 1: “Various impact scales”.......................................................................................................12
Figure 2: “Demonstrating risk assessment for Digital Fruit.”.............................................................13
Figure 3: “Risk controls to be done”...................................................................................................17
Figure 4: “Illustrating ANSII and GDPR Risk scoring”.....................................................................20
Figure 5: “Illustrating OWASP-TOP 10”............................................................................................21
Figure 6: “Illustrating Risk scoring history”.......................................................................................22
List of Figures
Figure 1: “Various impact scales”.......................................................................................................12
Figure 2: “Demonstrating risk assessment for Digital Fruit.”.............................................................13
Figure 3: “Risk controls to be done”...................................................................................................17
Figure 4: “Illustrating ANSII and GDPR Risk scoring”.....................................................................20
Figure 5: “Illustrating OWASP-TOP 10”............................................................................................21
Figure 6: “Illustrating Risk scoring history”.......................................................................................22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY MANAGEMENT
List of Tables
Table 1: Discussion on asset valuations................................................................................................8
Table 2: Identifying Threats................................................................................................................10
Table 3: Risk Analysis for the present situation..................................................................................16
Table 4: Various critical risks..............................................................................................................17
Table 5: Assessing options of risk treatments.....................................................................................17
Table 6: Different controls on implementation plans..........................................................................19
Table 7: Different measures and discussion........................................................................................20
ion on asset valuations...........................................................................................................................8
Table 5: Assessing options of risk treatments.....................................................................................17
List of Tables
Table 1: Discussion on asset valuations................................................................................................8
Table 2: Identifying Threats................................................................................................................10
Table 3: Risk Analysis for the present situation..................................................................................16
Table 4: Various critical risks..............................................................................................................17
Table 5: Assessing options of risk treatments.....................................................................................17
Table 6: Different controls on implementation plans..........................................................................19
Table 7: Different measures and discussion........................................................................................20
ion on asset valuations...........................................................................................................................8
Table 5: Assessing options of risk treatments.....................................................................................17

5CYBER SECURITY MANAGEMENT
Executive summary
Cybersecurity measures are helpful to design, implement, secure and enforce security systems. Here,
Digital Fruit, located at Estonia is considered. Their critical information systems include determining
of IT strategies, program and project management processes, change management processes, third-
party service management process, constant service assurance process, information security
management process, configuration management methods, problem management process, data
management process, physical environment management processes and IT operation management
methods. The study has analyzed a complicated business process, information assets, threats,
vulnerabilities and many more. An information risk analysis is done with a probability analysis.
Lastly, the study has demonstrated cybersecurity control developing and implementing ways of
monitoring security.
Executive summary
Cybersecurity measures are helpful to design, implement, secure and enforce security systems. Here,
Digital Fruit, located at Estonia is considered. Their critical information systems include determining
of IT strategies, program and project management processes, change management processes, third-
party service management process, constant service assurance process, information security
management process, configuration management methods, problem management process, data
management process, physical environment management processes and IT operation management
methods. The study has analyzed a complicated business process, information assets, threats,
vulnerabilities and many more. An information risk analysis is done with a probability analysis.
Lastly, the study has demonstrated cybersecurity control developing and implementing ways of
monitoring security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY MANAGEMENT
Introduction:
The cybersecurity in business is dependent on individuals having various insights. This
involves developing a secured system, designing, deploying and enforcing security systems and
policies and information management [1].
The “Digital Fruit” at Estonia has been involved in 400 projects for more than 15 years. They
are active providers of mobile phone and web solutions. Further, they are helpful to set demands of
B2B sales environment and online shops. They have been supporting clients with SEM and SEO to
develop simple websites. They are focused on customer-oriented services.
The report has involved identifying of a various complex business process, assets of
information, IT resources, vulnerabilities and threat identification. Then there are impact and
probability assessment, cybersecurity and information risk analysis and risk treatments. Further, it
has included cybersecurity and information control developing and deploying cybersecurity
monitoring.
Identifying critical business processes, information assets and IT assets:
The essential processes should be implemented quickly as any disruption take place at
Digital Fruit. This is to assure that their ability is protected. It also includes meeting critical
necessities with satisfying mandatory requirements and regulations. Next, information assets of
Digital Fruit are the body of knowledge managed and organized as one entity. Similar to corporate
assets Digital fruit’s information assets also comprises of financial value. This asset value rise in
direct relationship with various people able to use information [3]. Here, IT asset management or
Introduction:
The cybersecurity in business is dependent on individuals having various insights. This
involves developing a secured system, designing, deploying and enforcing security systems and
policies and information management [1].
The “Digital Fruit” at Estonia has been involved in 400 projects for more than 15 years. They
are active providers of mobile phone and web solutions. Further, they are helpful to set demands of
B2B sales environment and online shops. They have been supporting clients with SEM and SEO to
develop simple websites. They are focused on customer-oriented services.
The report has involved identifying of a various complex business process, assets of
information, IT resources, vulnerabilities and threat identification. Then there are impact and
probability assessment, cybersecurity and information risk analysis and risk treatments. Further, it
has included cybersecurity and information control developing and deploying cybersecurity
monitoring.
Identifying critical business processes, information assets and IT assets:
The essential processes should be implemented quickly as any disruption take place at
Digital Fruit. This is to assure that their ability is protected. It also includes meeting critical
necessities with satisfying mandatory requirements and regulations. Next, information assets of
Digital Fruit are the body of knowledge managed and organized as one entity. Similar to corporate
assets Digital fruit’s information assets also comprises of financial value. This asset value rise in
direct relationship with various people able to use information [3]. Here, IT asset management or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY MANAGEMENT
ITAM is the set of business practices joining inventory, contractual and financial functions for
supporting strategic decision making and lifecycle management to make IT environments.
1. Demonstrating business process and highlighting critical information systems:
Business process must be looking at the business of Digital Fruit as the collection of various
workflows and practices. Here, business process management has been helpful for organizations for
creating, tracking and optimizing business process. One can use solutions for getting complete
visibility for Digital Fruit. This has been helpful for discovering, automating and developing
business process. This must be done consistently in reducing costs and boosting productivity and
efficiency. Various scores of useful quality BPM software are there in the current market [2].
Selecting a proper one for particular necessities has been complicated. One can help to list the
smartest business process management as chosen by the review team, from key elements, benefits
and main features.
Thus cybersecurity has turned into a primary strategic priority. Further, for innovating and
realizing digital potentials for a customer and business goals, Digital Fruit has needed to secure
approaches. This is helpful to focus on business. This phenomenon has changed the face of Digital
Fruit.
2. Determining primary information assets and IT assets:
Any element with value and a useful object can be considered an asset. Under the IT realm,
this is seen as data, systems in which data is present. This is on the infrastructures that connect
various systems of Digital Fruit. As far as costs related to the system is considered, human resources
have required to run them and company data in those systems [5]. It is seen that Digital Fruit has
started to notice that the entire three pieces of IT paradigm have been made up of the whole
ITAM is the set of business practices joining inventory, contractual and financial functions for
supporting strategic decision making and lifecycle management to make IT environments.
1. Demonstrating business process and highlighting critical information systems:
Business process must be looking at the business of Digital Fruit as the collection of various
workflows and practices. Here, business process management has been helpful for organizations for
creating, tracking and optimizing business process. One can use solutions for getting complete
visibility for Digital Fruit. This has been helpful for discovering, automating and developing
business process. This must be done consistently in reducing costs and boosting productivity and
efficiency. Various scores of useful quality BPM software are there in the current market [2].
Selecting a proper one for particular necessities has been complicated. One can help to list the
smartest business process management as chosen by the review team, from key elements, benefits
and main features.
Thus cybersecurity has turned into a primary strategic priority. Further, for innovating and
realizing digital potentials for a customer and business goals, Digital Fruit has needed to secure
approaches. This is helpful to focus on business. This phenomenon has changed the face of Digital
Fruit.
2. Determining primary information assets and IT assets:
Any element with value and a useful object can be considered an asset. Under the IT realm,
this is seen as data, systems in which data is present. This is on the infrastructures that connect
various systems of Digital Fruit. As far as costs related to the system is considered, human resources
have required to run them and company data in those systems [5]. It is seen that Digital Fruit has
started to notice that the entire three pieces of IT paradigm have been made up of the whole
8CYBER SECURITY MANAGEMENT
operations. This also includes employees running the business, data contained in that real-world
environment of this business.
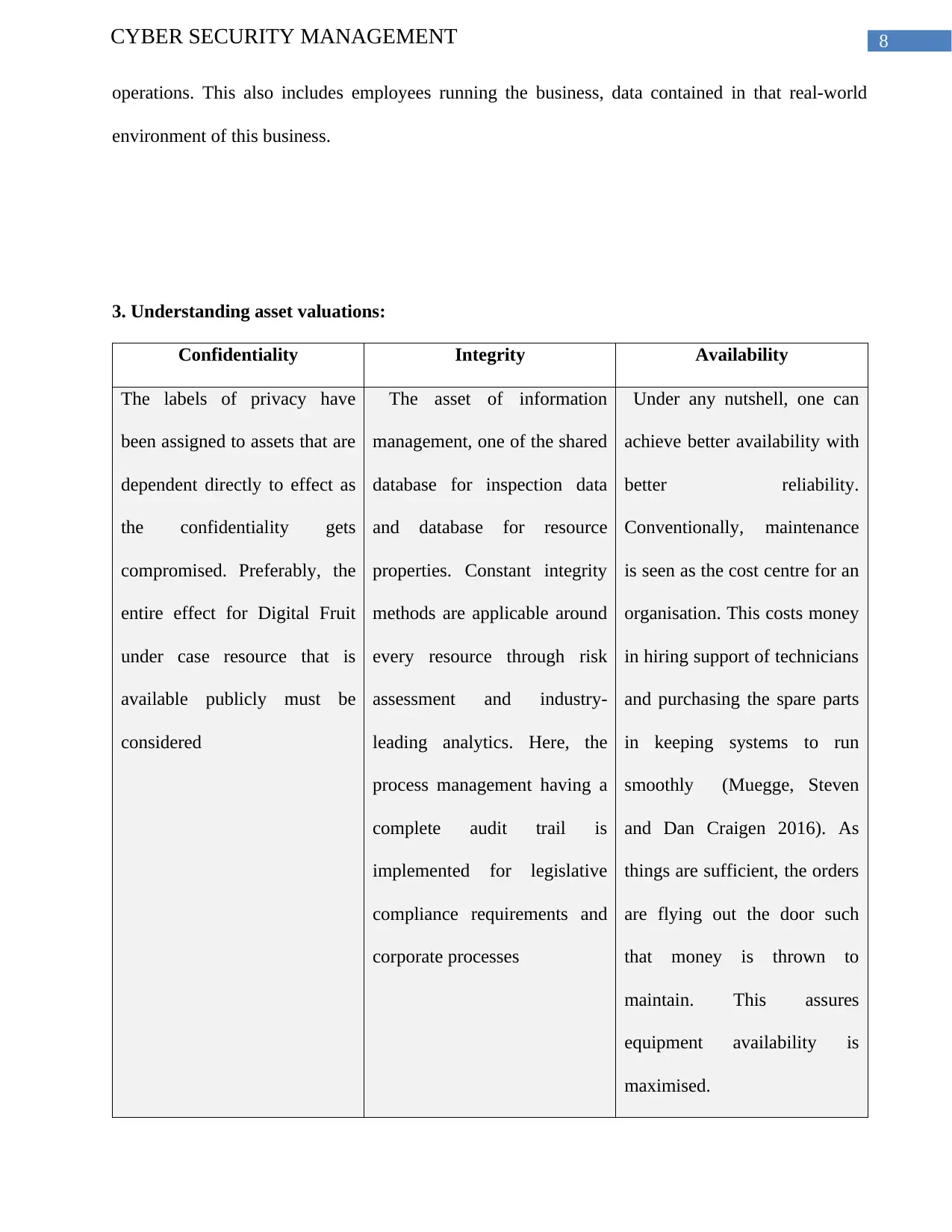
3. Understanding asset valuations:
Confidentiality Integrity Availability
The labels of privacy have
been assigned to assets that are
dependent directly to effect as
the confidentiality gets
compromised. Preferably, the
entire effect for Digital Fruit
under case resource that is
available publicly must be
considered
The asset of information
management, one of the shared
database for inspection data
and database for resource
properties. Constant integrity
methods are applicable around
every resource through risk
assessment and industry-
leading analytics. Here, the
process management having a
complete audit trail is
implemented for legislative
compliance requirements and
corporate processes
Under any nutshell, one can
achieve better availability with
better reliability.
Conventionally, maintenance
is seen as the cost centre for an
organisation. This costs money
in hiring support of technicians
and purchasing the spare parts
in keeping systems to run
smoothly (Muegge, Steven
and Dan Craigen 2016). As
things are sufficient, the orders
are flying out the door such
that money is thrown to
maintain. This assures
equipment availability is
maximised.
operations. This also includes employees running the business, data contained in that real-world
environment of this business.
3. Understanding asset valuations:
Confidentiality Integrity Availability
The labels of privacy have
been assigned to assets that are
dependent directly to effect as
the confidentiality gets
compromised. Preferably, the
entire effect for Digital Fruit
under case resource that is
available publicly must be
considered
The asset of information
management, one of the shared
database for inspection data
and database for resource
properties. Constant integrity
methods are applicable around
every resource through risk
assessment and industry-
leading analytics. Here, the
process management having a
complete audit trail is
implemented for legislative
compliance requirements and
corporate processes
Under any nutshell, one can
achieve better availability with
better reliability.
Conventionally, maintenance
is seen as the cost centre for an
organisation. This costs money
in hiring support of technicians
and purchasing the spare parts
in keeping systems to run
smoothly (Muegge, Steven
and Dan Craigen 2016). As
things are sufficient, the orders
are flying out the door such
that money is thrown to
maintain. This assures
equipment availability is
maximised.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY MANAGEMENT
Table 1: Discussion on asset valuations
4. Conducting a business impact analysis:
It is understood through business process dependency over Digital Fruit’s information
system. Complicated business processes in the format of service compositions and form of
workflows are created on distinct building blocks. These include services and activities. The
building blocks have been cooperating in achieving the entire aim of that process. In many
situations, the dependencies have been there between distinct activities. This includes executing
operations dependent on others. Here, knowledge regarding addictions is vital for managing
processes during run times. These take places in situations where problems have been taking place
and the procedures are needed to be adapted.
Threats and vulnerabilities identification:
This includes understanding common attacks and inventory of vulnerabilities. Then there are
usage of vulnerability scanning tools and analyzing risks. Here, the issue is that one has the public
access to the Internet. This needs to get secured because of the nature of various county businesses.
One never knows whether one has security breaches [8]. However, there are potentials. These are
demonstrated hereafter.
5. Identification of proper threats:
These threats are determined through categorization:
Elemental Threat Directed threats
The elemental threat approach involves
discover and assess that includes dynamic
The directed threats, on the other hand,
involves educating employees regarding the
Table 1: Discussion on asset valuations
4. Conducting a business impact analysis:
It is understood through business process dependency over Digital Fruit’s information
system. Complicated business processes in the format of service compositions and form of
workflows are created on distinct building blocks. These include services and activities. The
building blocks have been cooperating in achieving the entire aim of that process. In many
situations, the dependencies have been there between distinct activities. This includes executing
operations dependent on others. Here, knowledge regarding addictions is vital for managing
processes during run times. These take places in situations where problems have been taking place
and the procedures are needed to be adapted.
Threats and vulnerabilities identification:
This includes understanding common attacks and inventory of vulnerabilities. Then there are
usage of vulnerability scanning tools and analyzing risks. Here, the issue is that one has the public
access to the Internet. This needs to get secured because of the nature of various county businesses.
One never knows whether one has security breaches [8]. However, there are potentials. These are
demonstrated hereafter.
5. Identification of proper threats:
These threats are determined through categorization:
Elemental Threat Directed threats
The elemental threat approach involves
discover and assess that includes dynamic
The directed threats, on the other hand,
involves educating employees regarding the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY MANAGEMENT
grouping, system profiling and security posture
analysis. Next policies and controls are to be
set. This involves extensive policy library and
templates of policy baselines. Then there is
monitoring and adjustment. This includes
adaptive access controls, policy enforcement
and change management (Brass et al. 2017).
Lastly, this approach involves measuring and
reporting. This comprises multi-level reporting
and alarms, metrics of security compliances and
risk-adjusted visibility.
most effective security practices. Next, the
software regularity is to be updated. A
multilayered approach must be undertaken for
IT security. Further, the chances to keep back-
up should be highly utilized. Also, smart
security audits are to be done.
Table 2: Identifying Threats
6. Identification of proper vulnerabilities through categorization:
Regarding technology, the weaknesses can be identified through legacy software, default
configurations, lack of encryptions, remote access policies and policies and procedures as far as
people are considered lost and stolen devices are to be believed. Digital Fruit can identify proper
threats using assuring that the tools consist of password protection and various multi-factor
authentication that is enabled as soon as possible [9]. Then there are dangers with Wi-Fi. The users
should assure that hotspots are legitimate through getting connected to them. Then vulnerabilities
due to insider threats are to be determined. Here corporate solutions are helpful to track important
data whereabouts and distantly wiping complex data from devices that are stolen or lost. Besides,
grouping, system profiling and security posture
analysis. Next policies and controls are to be
set. This involves extensive policy library and
templates of policy baselines. Then there is
monitoring and adjustment. This includes
adaptive access controls, policy enforcement
and change management (Brass et al. 2017).
Lastly, this approach involves measuring and
reporting. This comprises multi-level reporting
and alarms, metrics of security compliances and
risk-adjusted visibility.
most effective security practices. Next, the
software regularity is to be updated. A
multilayered approach must be undertaken for
IT security. Further, the chances to keep back-
up should be highly utilized. Also, smart
security audits are to be done.
Table 2: Identifying Threats
6. Identification of proper vulnerabilities through categorization:
Regarding technology, the weaknesses can be identified through legacy software, default
configurations, lack of encryptions, remote access policies and policies and procedures as far as
people are considered lost and stolen devices are to be believed. Digital Fruit can identify proper
threats using assuring that the tools consist of password protection and various multi-factor
authentication that is enabled as soon as possible [9]. Then there are dangers with Wi-Fi. The users
should assure that hotspots are legitimate through getting connected to them. Then vulnerabilities
due to insider threats are to be determined. Here corporate solutions are helpful to track important
data whereabouts and distantly wiping complex data from devices that are stolen or lost. Besides,

11CYBER SECURITY MANAGEMENT
software updates are to be done. It must be assured that employees install different vendor-official
software updates promptly and according to the policies of Digital Fruit.
As for identification of threats due to vulnerabilities of an organization are considered, there
must be a determination of exposure towards external relationships. Then there is inadequate
security training for employees, slow security updates and patches and planning of dated responses.
Regarding fetching of threats due to vulnerabilities of processes, Digital Fruit must possess a
comprehensive view of their cybersecurity network [11]. Further, they must regularly make audits of
various long-established policies. There are analyzing baselines and unexpected inputs that are
applicable in multiple monitoring and processes for seeing that seeing that is outcomes are expected.
This is also vital to develop awareness under Digital Fruit and educate employees in identifying
abnormal and normal behavior. Further, enterprises must also deploy measures of cybersecurity.
This can secure networks against recognized tolls of malware instructions.
Probability and impact assessment:
Risk events, irrespective of opportunity and threats, comprises of two characteristics consists
of possibility that can occur and effect that can happen. Risks for impact and probability can be
analyzed through scales like high, medium and low. Since as the complicacy of work rises, the
sophistication of analysis also rises [15]. Here, in a detailed analysis of risk events for projects of
high complicacy and programs consists of point scale with guidelines and different numerical values
for every point on that scale.
7. Developing a risk situation:
The risks are driven through alterations in government policy, regulatory environment,
technology, customer behavior, competition and markets. New services in the sectors of IT services
software updates are to be done. It must be assured that employees install different vendor-official
software updates promptly and according to the policies of Digital Fruit.
As for identification of threats due to vulnerabilities of an organization are considered, there
must be a determination of exposure towards external relationships. Then there is inadequate
security training for employees, slow security updates and patches and planning of dated responses.
Regarding fetching of threats due to vulnerabilities of processes, Digital Fruit must possess a
comprehensive view of their cybersecurity network [11]. Further, they must regularly make audits of
various long-established policies. There are analyzing baselines and unexpected inputs that are
applicable in multiple monitoring and processes for seeing that seeing that is outcomes are expected.
This is also vital to develop awareness under Digital Fruit and educate employees in identifying
abnormal and normal behavior. Further, enterprises must also deploy measures of cybersecurity.
This can secure networks against recognized tolls of malware instructions.
Probability and impact assessment:
Risk events, irrespective of opportunity and threats, comprises of two characteristics consists
of possibility that can occur and effect that can happen. Risks for impact and probability can be
analyzed through scales like high, medium and low. Since as the complicacy of work rises, the
sophistication of analysis also rises [15]. Here, in a detailed analysis of risk events for projects of
high complicacy and programs consists of point scale with guidelines and different numerical values
for every point on that scale.
7. Developing a risk situation:
The risks are driven through alterations in government policy, regulatory environment,
technology, customer behavior, competition and markets. New services in the sectors of IT services
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




