Forensic Analysis of Digital Devices: Melbourne Airport Case Study
VerifiedAdded on 2020/04/01
|22
|4008
|316
Project
AI Summary
This project details a digital forensics investigation involving devices confiscated at Melbourne International Airport. The investigation uses tools like Hex Workshop, S-Tools, ProDiscover, and FTKImager to recover scrambled bits, hidden files, and analyze hard drive data. The project involves examining a laptop and USB drive, recovering deleted files, and identifying potential associates of a suspect. The analysis includes bit-by-bit copying of the hard drive, recovery of financial transaction records, and the use of steganography to uncover hidden files within images. The findings reveal financial transactions and hidden data, providing evidence for further investigation and potential charges against the suspect and their associates. The project demonstrates the application of forensic techniques in a real-world scenario, emphasizing the importance of data recovery and evidence analysis in criminal investigations.

[Document Title]
[Document Subtitle]
[Author]
ABSTRACT
[Type the abstract of the document here. The abstract is typically a short summary of the
contents of the document.]
[Document Subtitle]
[Author]
ABSTRACT
[Type the abstract of the document here. The abstract is typically a short summary of the
contents of the document.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1......................................................................................................................................3
Scrambling bits recovery..................................................................................................................3
Task 2......................................................................................................................................4
Task 3......................................................................................................................................6
References.............................................................................................................................22
2
Task 1......................................................................................................................................3
Scrambling bits recovery..................................................................................................................3
Task 2......................................................................................................................................4
Task 3......................................................................................................................................6
References.............................................................................................................................22
2
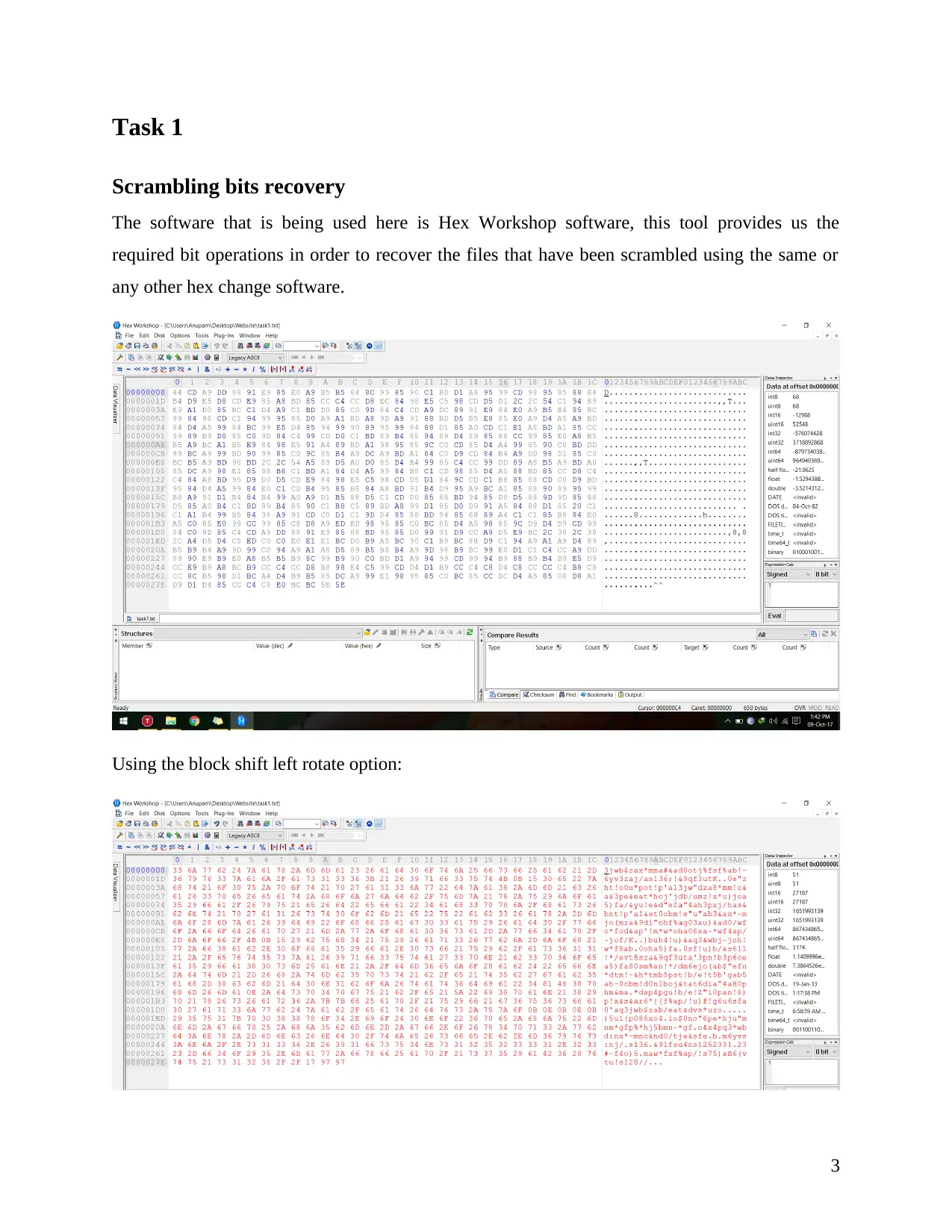
Task 1
Scrambling bits recovery
The software that is being used here is Hex Workshop software, this tool provides us the
required bit operations in order to recover the files that have been scrambled using the same or
any other hex change software.
Using the block shift left rotate option:
3
Scrambling bits recovery
The software that is being used here is Hex Workshop software, this tool provides us the
required bit operations in order to recover the files that have been scrambled using the same or
any other hex change software.
Using the block shift left rotate option:
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
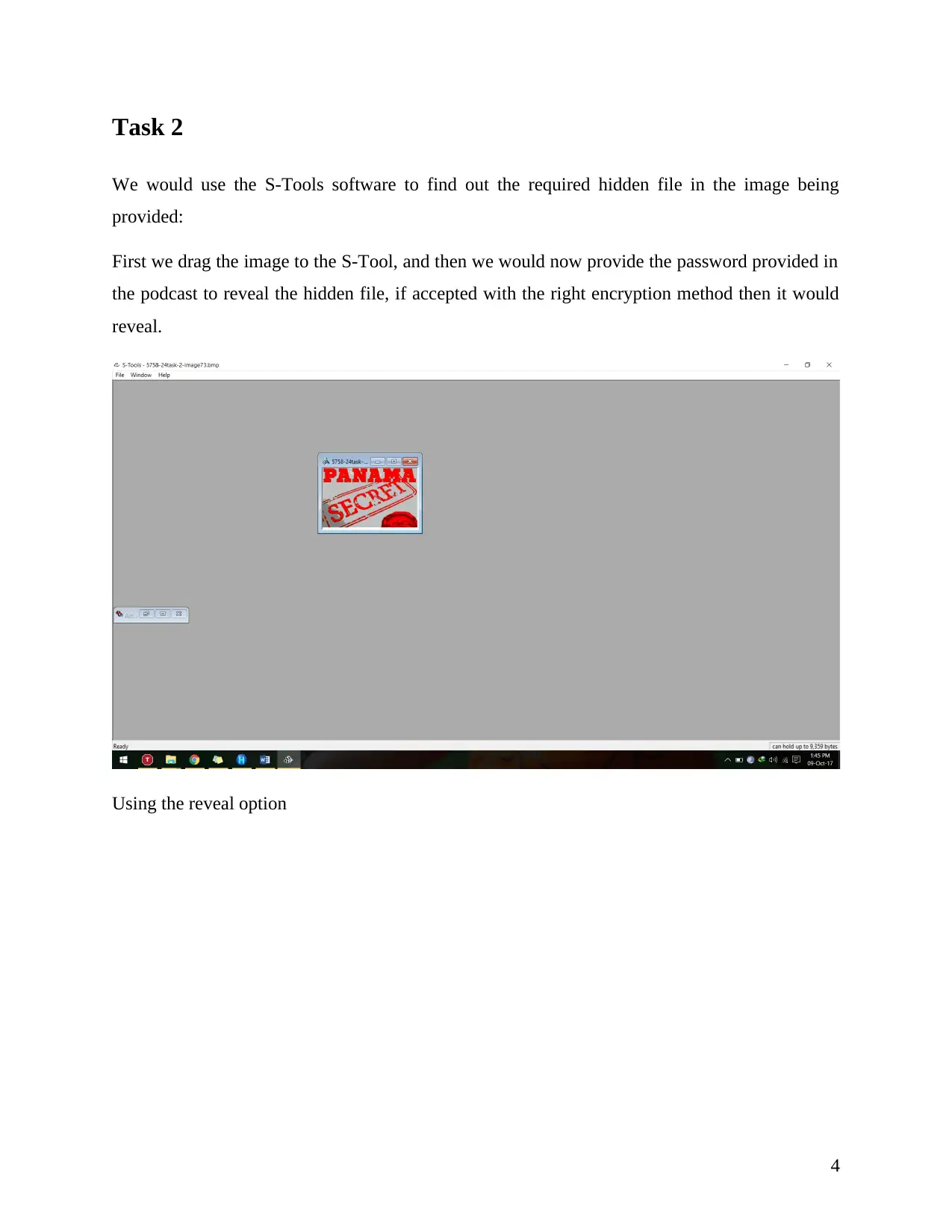
Task 2
We would use the S-Tools software to find out the required hidden file in the image being
provided:
First we drag the image to the S-Tool, and then we would now provide the password provided in
the podcast to reveal the hidden file, if accepted with the right encryption method then it would
reveal.
Using the reveal option
4
We would use the S-Tools software to find out the required hidden file in the image being
provided:
First we drag the image to the S-Tool, and then we would now provide the password provided in
the podcast to reveal the hidden file, if accepted with the right encryption method then it would
reveal.
Using the reveal option
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
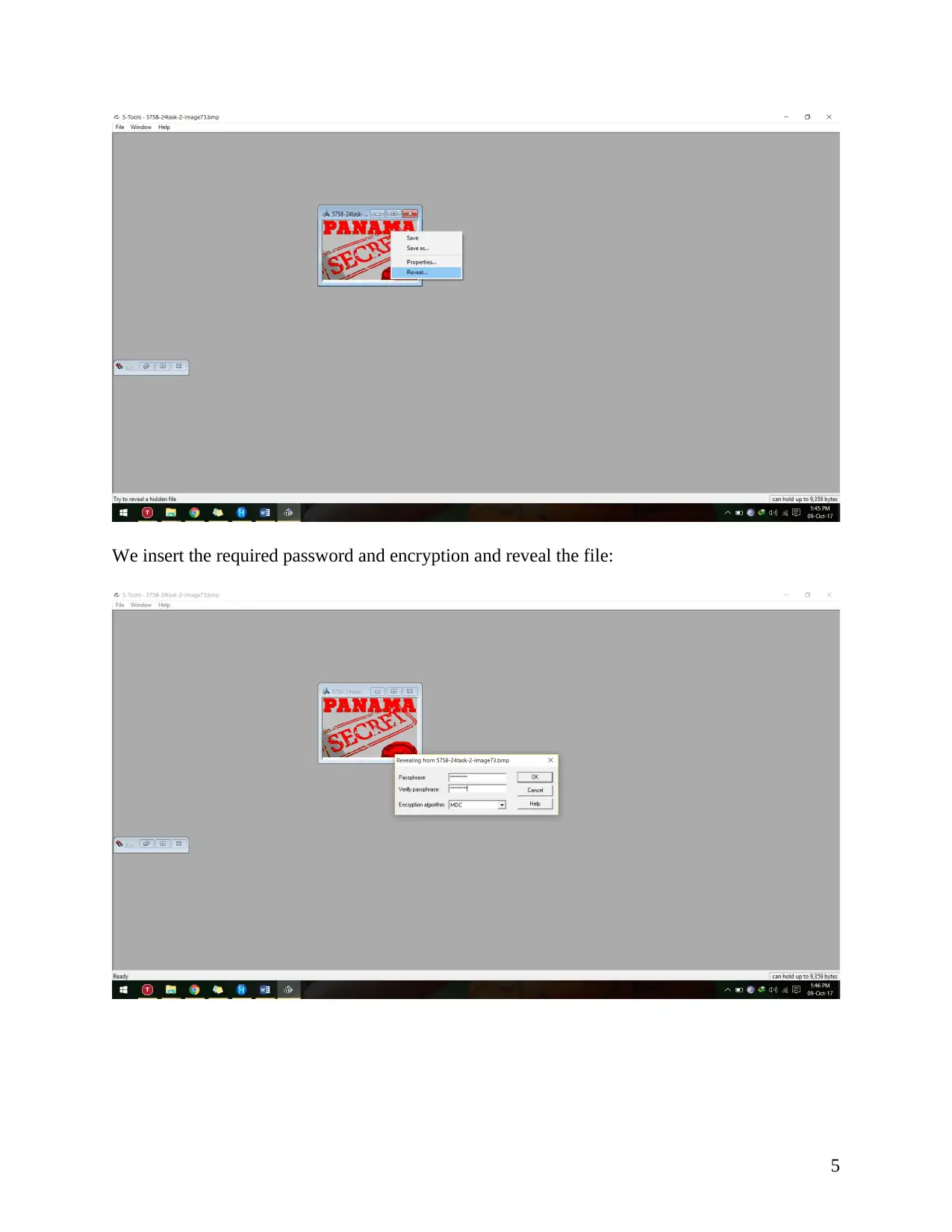
We insert the required password and encryption and reveal the file:
5
5

Task 3
Abstract
The project is about the investigation of the laptop which was being confiscated during the
search operation that went down at Melbourne International Airport. Mr. Watson looked quite
suspicious in his approach and could answer some regular questions. Later when the baggage
was being confiscated and searched few of digital devices that included a laptop and USB drive
was confiscated apart from the few packets of white powder, which when further investigated
were drugs. The drugs were handed over to the narcotics department and digital evidence.
Another reason for suspicion was that Mr. Watson was flying back from Cambodia.
Table of Contents
Introduction……………………………………………………………………………………... 08
Analysis Conducted ………………………………………...…………………………………. 09
Findings……………………………………………………………………………...………… 17
Conclusion……………………………………………………………………………...……… 20
Summary ………………………………….…………………………………………………… 20
Introduction
The case is related to investigation of the digital devices that includes Laptop and USB drive
which were confiscated from Mr. Watson at the Melbourne International Airport. The Malicious
looking Mr. Watson had intentions of supplying the bag full of drugs into Australia. The digital
devices were being handed over to the Officer Smith for further investigation against the culprit
and try to find out if anyone of his associates is there in Australia or around the world. (Burrows
and Zadeh, 2016)
CUSTODY OF EXHIBIT
On 1st Oct 2017 at 3:15 pm (GMT+0) the flight from Cambodia landed at the Airport, the flight
numbered AiRCol32442, during the baggage scan the malicious packets were found in the
6
Abstract
The project is about the investigation of the laptop which was being confiscated during the
search operation that went down at Melbourne International Airport. Mr. Watson looked quite
suspicious in his approach and could answer some regular questions. Later when the baggage
was being confiscated and searched few of digital devices that included a laptop and USB drive
was confiscated apart from the few packets of white powder, which when further investigated
were drugs. The drugs were handed over to the narcotics department and digital evidence.
Another reason for suspicion was that Mr. Watson was flying back from Cambodia.
Table of Contents
Introduction……………………………………………………………………………………... 08
Analysis Conducted ………………………………………...…………………………………. 09
Findings……………………………………………………………………………...………… 17
Conclusion……………………………………………………………………………...……… 20
Summary ………………………………….…………………………………………………… 20
Introduction
The case is related to investigation of the digital devices that includes Laptop and USB drive
which were confiscated from Mr. Watson at the Melbourne International Airport. The Malicious
looking Mr. Watson had intentions of supplying the bag full of drugs into Australia. The digital
devices were being handed over to the Officer Smith for further investigation against the culprit
and try to find out if anyone of his associates is there in Australia or around the world. (Burrows
and Zadeh, 2016)
CUSTODY OF EXHIBIT
On 1st Oct 2017 at 3:15 pm (GMT+0) the flight from Cambodia landed at the Airport, the flight
numbered AiRCol32442, during the baggage scan the malicious packets were found in the
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

baggage and stopped for further investigations. The evidences that were found includes the drugs
and some digital evidences the model of laptop was RE3234 with serial number being
ER43432DDFF6767. The baggage was stopped and all the devices were being confiscated and
handed over to the investigation team. The initial investigation revealed that the laptop didn’t
had any password to login and USB drive had the capacity of 4GB.
Analysis Conducted
The devices under investigation were the Laptop with RE3234 with serial number being
ER43432DDFF6767 and along with the laptop charger model number RE43345 with serial
number RER45538793. These items were handed over to the investigation team situated at the
forensic department in Melbourne in the sealed envelope. The other device USB drive with serial
number REDF76769 was digitally copied and real device being kept under the proofs for the
subject. The copy of the hard disk and was made using the bit by bit copy operation using the
ProDiscover software using the read only hardware that protects any type of write operations
using the software. (Burrows and Zadeh, 2016)
The images that have been created are being kept on the backup devices as well as on cloud so
that in case of any damage then evidence images can be used from the backup as well. The
Laptop configuration was:
Intel i5 dual core
500 GB HDD with different size partition
2 GB RAM
CD-ROM (empty)
USB drive was of 8 GB
The USB drive was imaged though the entire USB drive was empty, the recovery software was
used but nothing came up so it means entire drive was being formatted well using some un-
recoverable software. The analysis on all the images were done using the ProDiscover software,
the process with screenshot is shown below:
7
and some digital evidences the model of laptop was RE3234 with serial number being
ER43432DDFF6767. The baggage was stopped and all the devices were being confiscated and
handed over to the investigation team. The initial investigation revealed that the laptop didn’t
had any password to login and USB drive had the capacity of 4GB.
Analysis Conducted
The devices under investigation were the Laptop with RE3234 with serial number being
ER43432DDFF6767 and along with the laptop charger model number RE43345 with serial
number RER45538793. These items were handed over to the investigation team situated at the
forensic department in Melbourne in the sealed envelope. The other device USB drive with serial
number REDF76769 was digitally copied and real device being kept under the proofs for the
subject. The copy of the hard disk and was made using the bit by bit copy operation using the
ProDiscover software using the read only hardware that protects any type of write operations
using the software. (Burrows and Zadeh, 2016)
The images that have been created are being kept on the backup devices as well as on cloud so
that in case of any damage then evidence images can be used from the backup as well. The
Laptop configuration was:
Intel i5 dual core
500 GB HDD with different size partition
2 GB RAM
CD-ROM (empty)
USB drive was of 8 GB
The USB drive was imaged though the entire USB drive was empty, the recovery software was
used but nothing came up so it means entire drive was being formatted well using some un-
recoverable software. The analysis on all the images were done using the ProDiscover software,
the process with screenshot is shown below:
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
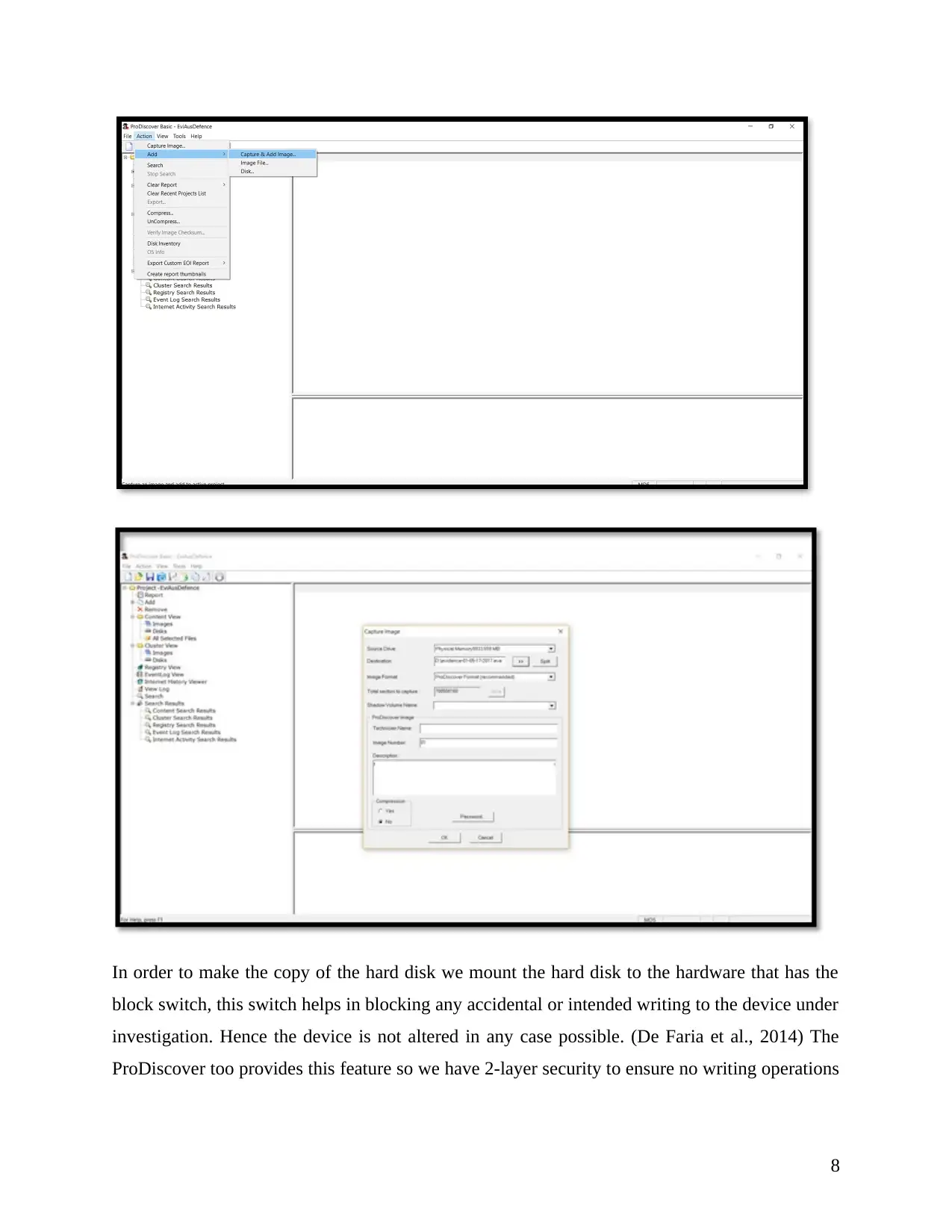
In order to make the copy of the hard disk we mount the hard disk to the hardware that has the
block switch, this switch helps in blocking any accidental or intended writing to the device under
investigation. Hence the device is not altered in any case possible. (De Faria et al., 2014) The
ProDiscover too provides this feature so we have 2-layer security to ensure no writing operations
8
block switch, this switch helps in blocking any accidental or intended writing to the device under
investigation. Hence the device is not altered in any case possible. (De Faria et al., 2014) The
ProDiscover too provides this feature so we have 2-layer security to ensure no writing operations
8
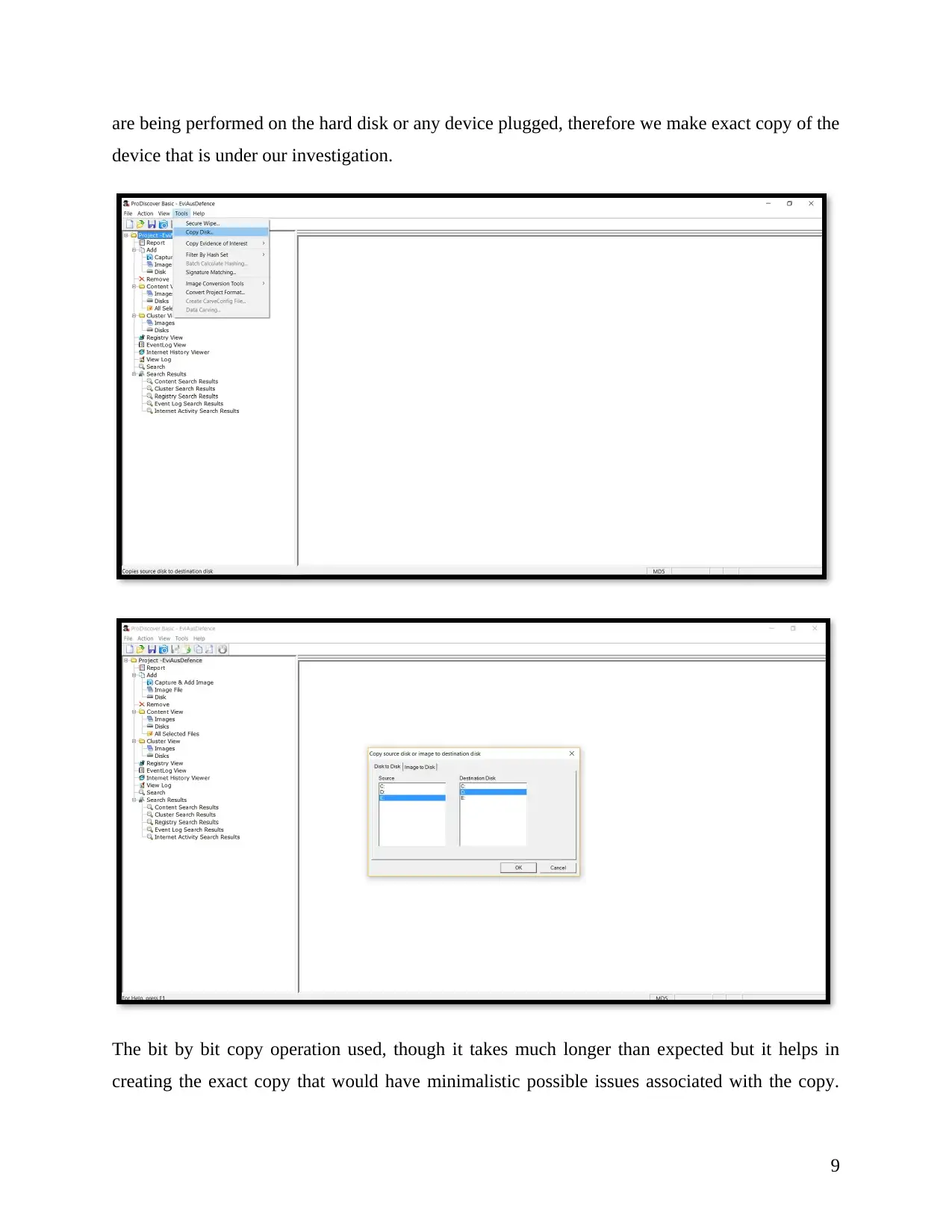
are being performed on the hard disk or any device plugged, therefore we make exact copy of the
device that is under our investigation.
The bit by bit copy operation used, though it takes much longer than expected but it helps in
creating the exact copy that would have minimalistic possible issues associated with the copy.
9
device that is under our investigation.
The bit by bit copy operation used, though it takes much longer than expected but it helps in
creating the exact copy that would have minimalistic possible issues associated with the copy.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
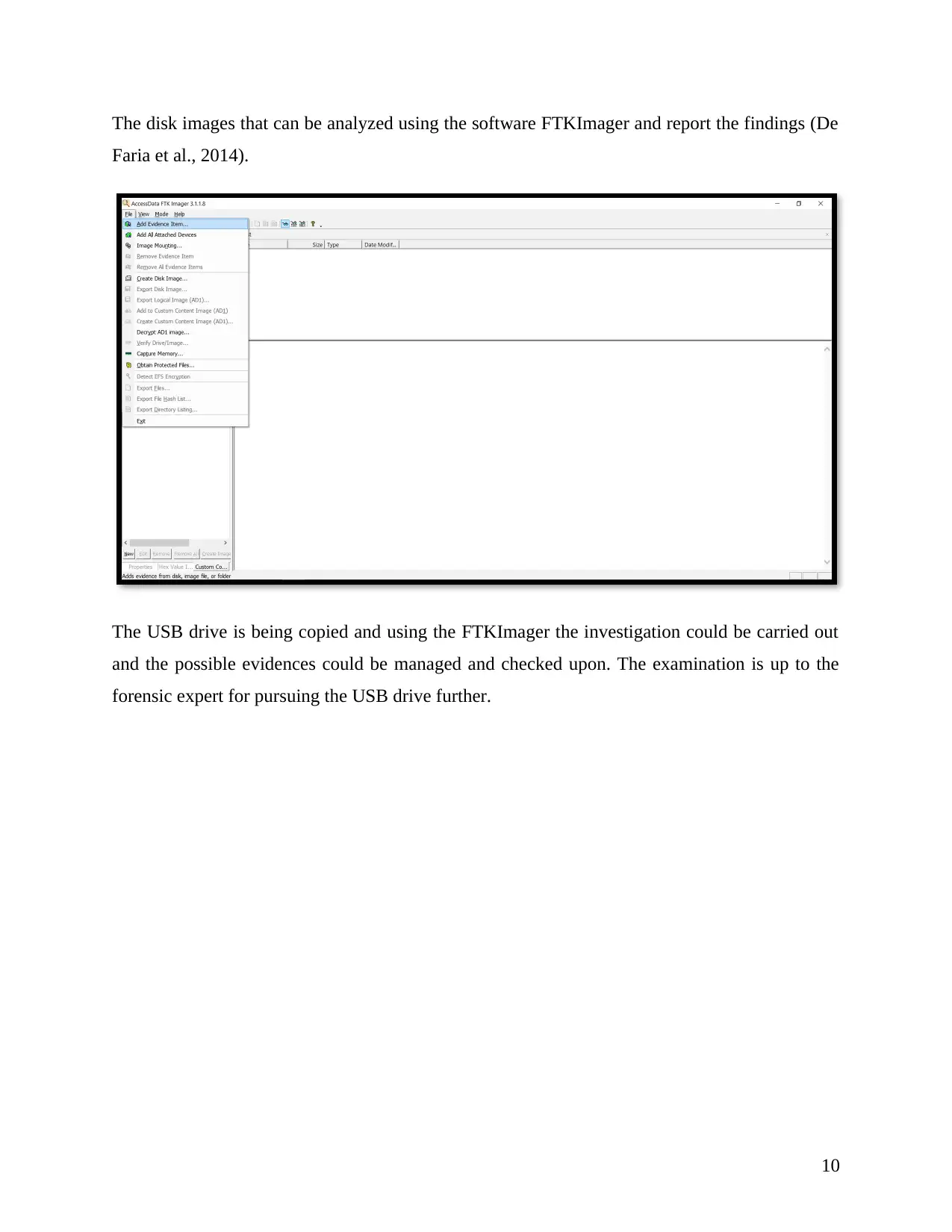
The disk images that can be analyzed using the software FTKImager and report the findings (De
Faria et al., 2014).
The USB drive is being copied and using the FTKImager the investigation could be carried out
and the possible evidences could be managed and checked upon. The examination is up to the
forensic expert for pursuing the USB drive further.
10
Faria et al., 2014).
The USB drive is being copied and using the FTKImager the investigation could be carried out
and the possible evidences could be managed and checked upon. The examination is up to the
forensic expert for pursuing the USB drive further.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
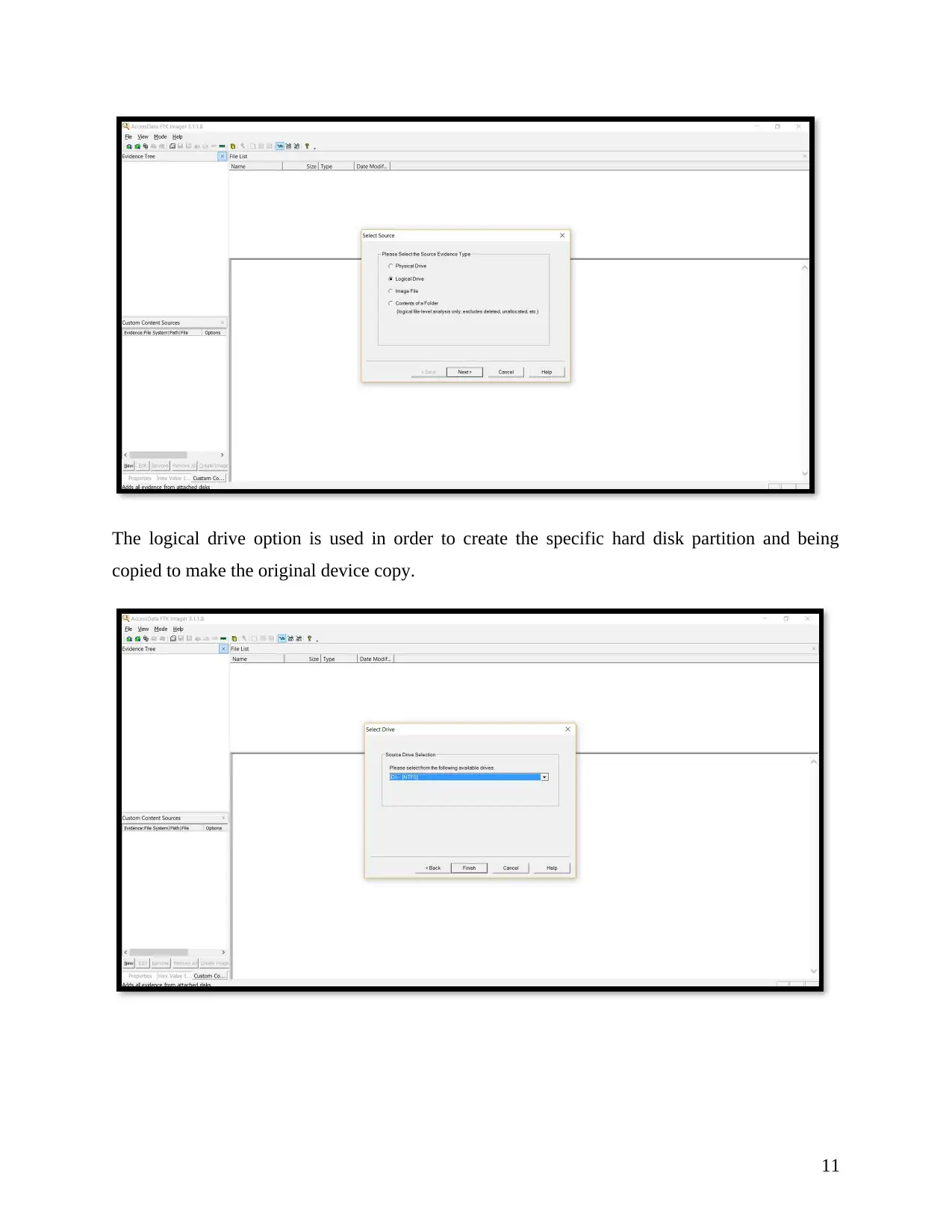
The logical drive option is used in order to create the specific hard disk partition and being
copied to make the original device copy.
11
copied to make the original device copy.
11
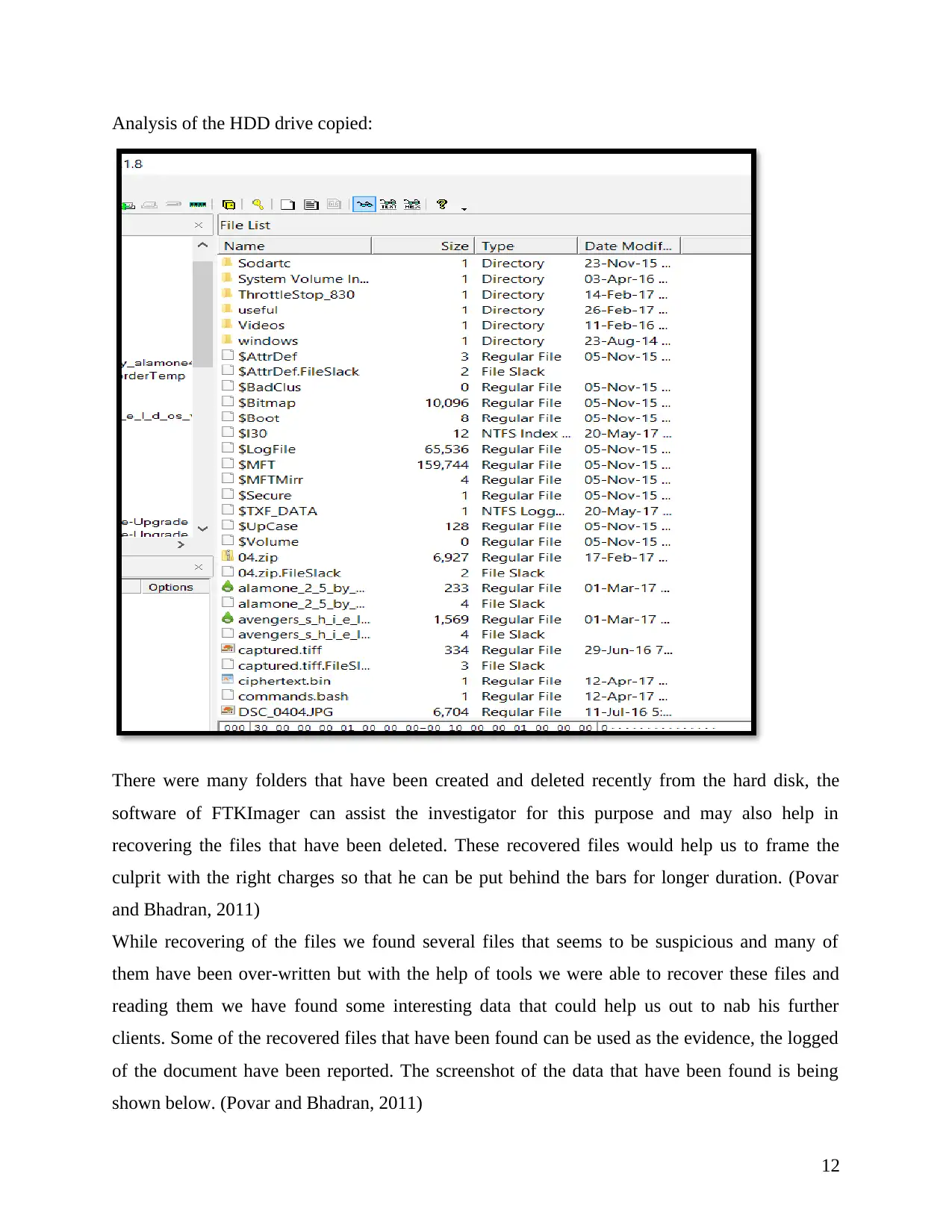
Analysis of the HDD drive copied:
There were many folders that have been created and deleted recently from the hard disk, the
software of FTKImager can assist the investigator for this purpose and may also help in
recovering the files that have been deleted. These recovered files would help us to frame the
culprit with the right charges so that he can be put behind the bars for longer duration. (Povar
and Bhadran, 2011)
While recovering of the files we found several files that seems to be suspicious and many of
them have been over-written but with the help of tools we were able to recover these files and
reading them we have found some interesting data that could help us out to nab his further
clients. Some of the recovered files that have been found can be used as the evidence, the logged
of the document have been reported. The screenshot of the data that have been found is being
shown below. (Povar and Bhadran, 2011)
12
There were many folders that have been created and deleted recently from the hard disk, the
software of FTKImager can assist the investigator for this purpose and may also help in
recovering the files that have been deleted. These recovered files would help us to frame the
culprit with the right charges so that he can be put behind the bars for longer duration. (Povar
and Bhadran, 2011)
While recovering of the files we found several files that seems to be suspicious and many of
them have been over-written but with the help of tools we were able to recover these files and
reading them we have found some interesting data that could help us out to nab his further
clients. Some of the recovered files that have been found can be used as the evidence, the logged
of the document have been reported. The screenshot of the data that have been found is being
shown below. (Povar and Bhadran, 2011)
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


