Forensic Analysis of the Apple iPad: Tools, Methods, and Challenges
VerifiedAdded on 2022/08/29
|17
|6364
|25
Report
AI Summary
This report, "Evaluating Digital Forensic Options for the Apple iPad," analyzes the tools and methods available for conducting forensic examinations of the Apple iPad. The research explores commercial software tools, jailbreaking techniques, and the analysis of iTunes backup files. The study reveals that while commercial tools offer promise, a comprehensive examination often requires jailbreaking to perform forensic duplication and manual analysis of media content. The paper highlights the limitations of existing tools, particularly for newer iOS versions, and emphasizes the importance of data integrity. The report also details the process of jailbreaking and imaging iPad media, along with the enumeration of forensically relevant content and the specification of file locations. The findings emphasize the challenges of iPad forensics, including the need for updated methodologies and the importance of understanding the device's security features and file system structure. The report concludes by discussing the challenges and potential solutions for recovering evidence from iPads, contributing to the field of mobile device forensics.

Chapter 20
EVALUATING DIGITAL FORENSIC
OPTIONS FOR THE APPLE iPAD
Andrew Hay, Dennis Krill, Benjamin Kuhar and Gilbert Peterson
Abstract The iPod Touch, iPhone and iPad from Apple are among the most
popular mobile computing platforms in use today.These devices are
of forensic interest because oftheir high adoption rate and potential
for containing digital evidence.The uniformity in their design and un-
derlying operating system (iOS) also allows forensic tools and methods
to be shared across product types.This paper analyzes the tools and
methods available for conducting forensic examinations ofthe Apple
iPad. These include commercialsoftware products,updated method-
ologies based on existing jailbreaking processes and the analysis of the
device backup contents provided by iTunes.While many of the available
commercial tools offer promise, the results of our analysis indicate that
most comprehensive examination ofthe iPad requires jailbreaking to
perform forensic duplication and manual analysis of its media content.
Keywords: Apple iPad, forensic examinations, iOS logical file system analysis
1. Introduction
Launched in April2010,the iPad [2]joined the iPhone and iPod
Touch to become the latest mobile device to adopt Apple’s iOS operatin
system [13].With three million devices sold in the first 80 days since its
launch [2] and 250,000 third party applications available on the platform
[13],the iPad is a major addition to the crowded mobile computing
market.The iPad supports multiple networking protocols and GPS, and
provides up to 64 GB of storage [4].As such,it represents a fusion of
technology, which is of interest to digital evidence examiners for many
the same reasons as traditional computing hardware and mobile phone
In contrast with the relatively open security models embraced by OS
X and the iPods that preceded it,iPhone OS (the predecessor to iOS)
is a closed operating environment without a traditional file system and
G. Peterson and S. Shenoi (Eds.): Advances in Digital Forensics VII, IFIP AICT 361, pp. 257–273, 2011.
cIFIP International Federation for Information Processing 2011
EVALUATING DIGITAL FORENSIC
OPTIONS FOR THE APPLE iPAD
Andrew Hay, Dennis Krill, Benjamin Kuhar and Gilbert Peterson
Abstract The iPod Touch, iPhone and iPad from Apple are among the most
popular mobile computing platforms in use today.These devices are
of forensic interest because oftheir high adoption rate and potential
for containing digital evidence.The uniformity in their design and un-
derlying operating system (iOS) also allows forensic tools and methods
to be shared across product types.This paper analyzes the tools and
methods available for conducting forensic examinations ofthe Apple
iPad. These include commercialsoftware products,updated method-
ologies based on existing jailbreaking processes and the analysis of the
device backup contents provided by iTunes.While many of the available
commercial tools offer promise, the results of our analysis indicate that
most comprehensive examination ofthe iPad requires jailbreaking to
perform forensic duplication and manual analysis of its media content.
Keywords: Apple iPad, forensic examinations, iOS logical file system analysis
1. Introduction
Launched in April2010,the iPad [2]joined the iPhone and iPod
Touch to become the latest mobile device to adopt Apple’s iOS operatin
system [13].With three million devices sold in the first 80 days since its
launch [2] and 250,000 third party applications available on the platform
[13],the iPad is a major addition to the crowded mobile computing
market.The iPad supports multiple networking protocols and GPS, and
provides up to 64 GB of storage [4].As such,it represents a fusion of
technology, which is of interest to digital evidence examiners for many
the same reasons as traditional computing hardware and mobile phone
In contrast with the relatively open security models embraced by OS
X and the iPods that preceded it,iPhone OS (the predecessor to iOS)
is a closed operating environment without a traditional file system and
G. Peterson and S. Shenoi (Eds.): Advances in Digital Forensics VII, IFIP AICT 361, pp. 257–273, 2011.
cIFIP International Federation for Information Processing 2011
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
258 ADVANCES IN DIGITAL FORENSICS VII
device disk mode.The version of iOS launched with the iPad addition-
ally supports security features such as application sandboxing,manda-
tory code signing and 256-bit AES hardware-based data encryption [3].
These features prevent many ofthe traditionaldigital forensic media
duplication and analysis processes from being employed effectively on
the iPad.
The iPhone OS has also largely invalidated the existing strategies
available for iPod forensics [16, 22], a problem addressed by Zdziarski i
the case of iPhone forensics [25].Zdziarski’s process requires an iPhone
to be hacked in a process known as “jailbreaking.” Before the develop-
ment of this process,severalcommercialforensic tools were developed.
Hoog and Gaffaney [11] present a survey of the principal tools, and Mis
lan [19]discusses iOS analysis in the context ofgeneralmobile device
forensics.However, existing tools and methods do not yet support iOS
versions 3.x and above,and the manualextraction and analysis of the
iTunes backup file from a computer system paired with an iPad.Both
these research gaps are addressed in this paper.
This paper makes four contributions to the field of mobile device fore
sics.The first is a survey of commercial software tools marketed for the
forensic analysis ofiPads, which have yet to be formally reviewed by
NIST [20]. The second is a variation ofZdziarski’s method [25]for
manually imaging iPad media using jailbreaking techniques.The third
is the enumeration ofthe forensically relevant content available on an
iPad and the specification of the locations of target files in the file sys-
tem. The fourth contribution is an analysis ofthe reviewed tools and
methods along with a technique for recovering evidence from the devic
backup file generated by iTunes.Note that our analysis does not include
any of the optional security measures that may be enabled on an iPad,
such as remote wiping, passcode locking and iTunes backup encryption
Zdziarski [25] has addressed the issue of passcode locking for iPhone O
2.x, but iTunes backup encryption remains a major obstacle for many
of the tools and techniques discussed in this paper.
2. Commercial Software Tools
Three untested commercial tools with iPad compatibility are currently
being marketed:Lantern [14], Mobilyze [5] and Oxygen Forensics Suite
2010 [21].Our analysis focuses on the evidence extracted using these
tools and the suitability of these tools when there is an expectation of
forensic soundness.Note that the analysis is limited to the free trial
versions ofthe marketed products whose capabilities may differ from
the fully licensed versions.
device disk mode.The version of iOS launched with the iPad addition-
ally supports security features such as application sandboxing,manda-
tory code signing and 256-bit AES hardware-based data encryption [3].
These features prevent many ofthe traditionaldigital forensic media
duplication and analysis processes from being employed effectively on
the iPad.
The iPhone OS has also largely invalidated the existing strategies
available for iPod forensics [16, 22], a problem addressed by Zdziarski i
the case of iPhone forensics [25].Zdziarski’s process requires an iPhone
to be hacked in a process known as “jailbreaking.” Before the develop-
ment of this process,severalcommercialforensic tools were developed.
Hoog and Gaffaney [11] present a survey of the principal tools, and Mis
lan [19]discusses iOS analysis in the context ofgeneralmobile device
forensics.However, existing tools and methods do not yet support iOS
versions 3.x and above,and the manualextraction and analysis of the
iTunes backup file from a computer system paired with an iPad.Both
these research gaps are addressed in this paper.
This paper makes four contributions to the field of mobile device fore
sics.The first is a survey of commercial software tools marketed for the
forensic analysis ofiPads, which have yet to be formally reviewed by
NIST [20]. The second is a variation ofZdziarski’s method [25]for
manually imaging iPad media using jailbreaking techniques.The third
is the enumeration ofthe forensically relevant content available on an
iPad and the specification of the locations of target files in the file sys-
tem. The fourth contribution is an analysis ofthe reviewed tools and
methods along with a technique for recovering evidence from the devic
backup file generated by iTunes.Note that our analysis does not include
any of the optional security measures that may be enabled on an iPad,
such as remote wiping, passcode locking and iTunes backup encryption
Zdziarski [25] has addressed the issue of passcode locking for iPhone O
2.x, but iTunes backup encryption remains a major obstacle for many
of the tools and techniques discussed in this paper.
2. Commercial Software Tools
Three untested commercial tools with iPad compatibility are currently
being marketed:Lantern [14], Mobilyze [5] and Oxygen Forensics Suite
2010 [21].Our analysis focuses on the evidence extracted using these
tools and the suitability of these tools when there is an expectation of
forensic soundness.Note that the analysis is limited to the free trial
versions ofthe marketed products whose capabilities may differ from
the fully licensed versions.

Hay, Krill, Kuhar & Peterson 259
Lantern (version 1.0.6.0 demo; now 1.0.9 with iOS 4.2.1 support) pro-
vides an easy-to-use interface for reviewing a limited subset of iPad dat
The extraction of information is quick – it took less than seven minutes
for an iPad configured with minimalmedia content.Multiple process-
ing errors were listed in the error log after extraction,but no explicit
warnings were raised to notify the user that something had gone wrong
Lantern [14]extracts evidence into two categories:media and ev-
erything else.The product does not support the manualbrowsing of
extracted data,most ofwhich is hidden in a single file with a propri-
etary format.All media is stored and hashed individually;everything
else is maintained in the archive file,whose hash value is displayed on
the main Lantern screen.Files are hashed using MD5,but there is no
facility for verifying that the exported evidence matches the archive be
cause ofa format conversion during exportation.A usability bug was
identified with respect to Lantern’s export data feature:the output file
is written without an extension, although the file is in the CSV format
and can be manually opened as such.
Mobilyze (version 1.1), which is now part of the BlackLight Forensic
Suite, provides graphical information in an intuitive and organized fash-
ion, but it only permits the viewing of a limited selection of iPad data.
Device acquisition took 27 minutes – the process copies the majority of
files in the iPad’s user partition and includes allthe media resources.
The copied files are individually hashed with MD5 and the values stored
in a separate log.The files are archived in a non-propriety package that
can be browsed manually using the OS X file browser or the built-in
Mobilyze browser.Mobilyze also offers built-in viewers for SQLite and
Property List files, for which no graphical module is available.
One of the major advantages of Mobilyze is the flexible and intuitive
evidence tagging and reporting facility.All the items of interest in the
graphicalmodules can be tagged,and individualdata files may be ex-
amined using the application file browser.Tagged items are formatted
in rich HTML when exported as a report,with the data files clearly
displaying the associated file path and hash value.
Oxygen Forensics Suite 2010 (version 2.8.1) reportedly supports evi-
dence acquisition and analysis for more than 1,650 mobile devices.The
Oxygen Connection Wizard requires the installation ofOxyAgent on
many target devices before acquisition can take place.Device acquisi-
tion took seventeen minutes; the process individually hashes all the file
The Oxygen Connection Wizard provides an extraction option for a full
reading ofthe iPad file structure,but this option yields files from the
user partition and does not capture any system resources.The company
has released severalupdates since our analysis.However,while the re-
Lantern (version 1.0.6.0 demo; now 1.0.9 with iOS 4.2.1 support) pro-
vides an easy-to-use interface for reviewing a limited subset of iPad dat
The extraction of information is quick – it took less than seven minutes
for an iPad configured with minimalmedia content.Multiple process-
ing errors were listed in the error log after extraction,but no explicit
warnings were raised to notify the user that something had gone wrong
Lantern [14]extracts evidence into two categories:media and ev-
erything else.The product does not support the manualbrowsing of
extracted data,most ofwhich is hidden in a single file with a propri-
etary format.All media is stored and hashed individually;everything
else is maintained in the archive file,whose hash value is displayed on
the main Lantern screen.Files are hashed using MD5,but there is no
facility for verifying that the exported evidence matches the archive be
cause ofa format conversion during exportation.A usability bug was
identified with respect to Lantern’s export data feature:the output file
is written without an extension, although the file is in the CSV format
and can be manually opened as such.
Mobilyze (version 1.1), which is now part of the BlackLight Forensic
Suite, provides graphical information in an intuitive and organized fash-
ion, but it only permits the viewing of a limited selection of iPad data.
Device acquisition took 27 minutes – the process copies the majority of
files in the iPad’s user partition and includes allthe media resources.
The copied files are individually hashed with MD5 and the values stored
in a separate log.The files are archived in a non-propriety package that
can be browsed manually using the OS X file browser or the built-in
Mobilyze browser.Mobilyze also offers built-in viewers for SQLite and
Property List files, for which no graphical module is available.
One of the major advantages of Mobilyze is the flexible and intuitive
evidence tagging and reporting facility.All the items of interest in the
graphicalmodules can be tagged,and individualdata files may be ex-
amined using the application file browser.Tagged items are formatted
in rich HTML when exported as a report,with the data files clearly
displaying the associated file path and hash value.
Oxygen Forensics Suite 2010 (version 2.8.1) reportedly supports evi-
dence acquisition and analysis for more than 1,650 mobile devices.The
Oxygen Connection Wizard requires the installation ofOxyAgent on
many target devices before acquisition can take place.Device acquisi-
tion took seventeen minutes; the process individually hashes all the file
The Oxygen Connection Wizard provides an extraction option for a full
reading ofthe iPad file structure,but this option yields files from the
user partition and does not capture any system resources.The company
has released severalupdates since our analysis.However,while the re-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

260 ADVANCES IN DIGITAL FORENSICS VII
lease notes include severalreferences to Apple,they do not specifically
mention the iPad or the latest Apple iOS.
3. Manual Search Methodology
The iPad file system is “jailed” by firmware restrictions that prevent
users from accessing it directly.The device itself has no disk mode to
facilitate the viewing and copying of media content.Apple’s philosophy
is that all interactions with the device should occur through the iTunes
portal. Similarly, third party applications are restricted to executing in
a sandbox to prevent subversion of the iOS environment.
Three methods exist for manually recovering digital evidence from an
iPad, and severaltools are available for performing an analysis.Apple
may assist law enforcement examinations with disk-mode unlocking of
the device, essentially enabling the iPad to function as a regular exter-
nal USB drive. The other two methods are jailbreaking the iPad and
analyzing the iTunes backup file.
3.1 Jailbreaking and Imaging
One means ofgaining root access to the iPad file system is to jail-
break its firmware.With such access,the examiner can installthird
party packages to image and transfer the device data to a computer
via SSH. Zdziarski[25]has described the jailbreaking process for the
iPhone OS v2.x. Updates are available for law enforcement [26],but
further information is only available via an access-controlled site [12].
Unfortunately,the jailbreaking and package installation strategies that
are publicly described are not effective for the iOS software on an iPad,
although the imaging and transfer steps remain largely unchanged.
For iOS version 3.2,the user space jailbreaks,Spirit [23]and Jail-
breakMe [6], provide access and automatically install the Cydia packag
manager [10]to support the installation of additionalsoftware.Cydia
is decidedly forensically-unfriendly – it installs severalfiles in the user
partition,and while its code is open source,the same cannot be said
for its jailbreaking technique.Current (publicly available) jailbreaks for
the iPad do not permit an examiner to access the device by installing a
forensically-friendly jailbreaking tool that write-protects the user parti-
tion. Additionally, while the Spirit jailbreak can be performed without
user manipulation, both methods require interaction with the iPad user
interface to install the OpenSSH and netcat packages required for imag
ing and transfer.
Two jailbreaks can be applied to devices running iOS 4.2.1:Pwnage-
Tool 4.1.3 [7]and redsn0w 0.96b6 [7].PwnageTooldoes not currently
lease notes include severalreferences to Apple,they do not specifically
mention the iPad or the latest Apple iOS.
3. Manual Search Methodology
The iPad file system is “jailed” by firmware restrictions that prevent
users from accessing it directly.The device itself has no disk mode to
facilitate the viewing and copying of media content.Apple’s philosophy
is that all interactions with the device should occur through the iTunes
portal. Similarly, third party applications are restricted to executing in
a sandbox to prevent subversion of the iOS environment.
Three methods exist for manually recovering digital evidence from an
iPad, and severaltools are available for performing an analysis.Apple
may assist law enforcement examinations with disk-mode unlocking of
the device, essentially enabling the iPad to function as a regular exter-
nal USB drive. The other two methods are jailbreaking the iPad and
analyzing the iTunes backup file.
3.1 Jailbreaking and Imaging
One means ofgaining root access to the iPad file system is to jail-
break its firmware.With such access,the examiner can installthird
party packages to image and transfer the device data to a computer
via SSH. Zdziarski[25]has described the jailbreaking process for the
iPhone OS v2.x. Updates are available for law enforcement [26],but
further information is only available via an access-controlled site [12].
Unfortunately,the jailbreaking and package installation strategies that
are publicly described are not effective for the iOS software on an iPad,
although the imaging and transfer steps remain largely unchanged.
For iOS version 3.2,the user space jailbreaks,Spirit [23]and Jail-
breakMe [6], provide access and automatically install the Cydia packag
manager [10]to support the installation of additionalsoftware.Cydia
is decidedly forensically-unfriendly – it installs severalfiles in the user
partition,and while its code is open source,the same cannot be said
for its jailbreaking technique.Current (publicly available) jailbreaks for
the iPad do not permit an examiner to access the device by installing a
forensically-friendly jailbreaking tool that write-protects the user parti-
tion. Additionally, while the Spirit jailbreak can be performed without
user manipulation, both methods require interaction with the iPad user
interface to install the OpenSSH and netcat packages required for imag
ing and transfer.
Two jailbreaks can be applied to devices running iOS 4.2.1:Pwnage-
Tool 4.1.3 [7]and redsn0w 0.96b6 [7].PwnageTooldoes not currently
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hay, Krill, Kuhar & Peterson 261
support the iPad and requires packages to be manually installed.How-
ever, redsn0w 0.9.6b6 is effective on an iPad running iOS 4.2.1 and can
also install the Cydia package manager.
Zdziarski [25] justifies the forensic soundness of using a jailbreak bas
on hashing the entire user partition prior to imaging its contents.The
problem with implementing this step is that the Cydia package manage
does not contain an MD5 implementation.Using the MD5 version sup-
plied with the OpenSSH package resulted in the spontaneous rebooting
of an iPad during our tests.
Two additionalforensic challenges exist with regard to jailbreaking.
Relying on an available jailbreak means that there is no guarantee that
a suitable tool will be available for a particular device and iOS version
when an investigation is to be performed.Also, after an iPad is jail-
broken, it requires software to be installed in order to recover the data.
This software, which is installed from the Cydia server, is outside the di-
rect control of the examiner and, therefore, does not qualify as a truste
executable.
Zdziarski’s [25] jailbreaking method copies only a subset of an iPad’s
file system (which Zdziarski calls the “user partition”).This restriction
derives from the fact that an iPad must be booted to create an image o
its media, and only the portions of the file system that are mounted as
read-only can be imaged.Ideally,a forensic media duplication process
should be comprehensive.The system partition accounts for a limited
portion of the file system and this partition generally does not contain
files of investigative value.Most free space, all application support files,
and third party executables are stored in the user partition.
The entire file system of an iPad can be examined on a jailbroken de-
vice using an iOS device browser leveraging the AFC2Add package pro-
vided by Phone Disk [17].To obtain root access, the AFC2Add package
must be installed using Cydia,which unlocks the device and provides
full access over USB when the device is running.This combination per-
mits the iPad’s root contents to mount in the OS X file browser as a
MacFUSE file system.Because MacFUSE mounted volumes communi-
cate via the Apple Filing Protocol, they do not receive a disk identifier
and low-level copying of their contents is not possible.However, the file
system can be navigated and individualfiles hashed and copied from
the command line.Examiners must take precautions when using this
method because the mounting is done as read-write,which means that
the files can be altered inadvertently.
support the iPad and requires packages to be manually installed.How-
ever, redsn0w 0.9.6b6 is effective on an iPad running iOS 4.2.1 and can
also install the Cydia package manager.
Zdziarski [25] justifies the forensic soundness of using a jailbreak bas
on hashing the entire user partition prior to imaging its contents.The
problem with implementing this step is that the Cydia package manage
does not contain an MD5 implementation.Using the MD5 version sup-
plied with the OpenSSH package resulted in the spontaneous rebooting
of an iPad during our tests.
Two additionalforensic challenges exist with regard to jailbreaking.
Relying on an available jailbreak means that there is no guarantee that
a suitable tool will be available for a particular device and iOS version
when an investigation is to be performed.Also, after an iPad is jail-
broken, it requires software to be installed in order to recover the data.
This software, which is installed from the Cydia server, is outside the di-
rect control of the examiner and, therefore, does not qualify as a truste
executable.
Zdziarski’s [25] jailbreaking method copies only a subset of an iPad’s
file system (which Zdziarski calls the “user partition”).This restriction
derives from the fact that an iPad must be booted to create an image o
its media, and only the portions of the file system that are mounted as
read-only can be imaged.Ideally,a forensic media duplication process
should be comprehensive.The system partition accounts for a limited
portion of the file system and this partition generally does not contain
files of investigative value.Most free space, all application support files,
and third party executables are stored in the user partition.
The entire file system of an iPad can be examined on a jailbroken de-
vice using an iOS device browser leveraging the AFC2Add package pro-
vided by Phone Disk [17].To obtain root access, the AFC2Add package
must be installed using Cydia,which unlocks the device and provides
full access over USB when the device is running.This combination per-
mits the iPad’s root contents to mount in the OS X file browser as a
MacFUSE file system.Because MacFUSE mounted volumes communi-
cate via the Apple Filing Protocol, they do not receive a disk identifier
and low-level copying of their contents is not possible.However, the file
system can be navigated and individualfiles hashed and copied from
the command line.Examiners must take precautions when using this
method because the mounting is done as read-write,which means that
the files can be altered inadvertently.
262 ADVANCES IN DIGITAL FORENSICS VII
3.2 Performing Custom Examinations
None of the commercialtools assessed proved to be as versatile and
comprehensive as a manual examination of the iPad’s file system.What
constitutes relevant evidence depends on the circumstances ofa case,
but not one of the commercial tools can provide results for all scenarios
This means that an examiner will eventually have to conduct a manual
process.Certain software resources and methods allow an examiner to
comprehensively search for and analyze the contents of an iPad after a
forensic duplicate of its media has been created.
Two reoccurring file types employed as support files across several
iPad applications are Property List (Plist) files and SQLite database
files. The Mac OS X command line offers built-in capabilities to read
both file types using the defaults command forPlist files and the
sqlite3 client for databases.Alternatively, PlistEdit Pro [9] and Base
[18]may be used;these applications use syntax highlighting to present
the text content of files in a readable format.The exact format of the
Plist files varies by application;in many cases,they can be read by an
equivalent application on the Mac if the iPad version of the file is copied
to the equivalent OS X user directory location.These files also store
application configuration settings and state information.
In contrast, database files are not as interchangeable, although iTune
does have the ability to sync contacts, calendars, bookmarks, notes and
media database content with a computer for viewing.Note that a one-
way sync is not possible from an iPad,so an examiner should only at-
tempting syncing after a forensic duplicate has been created.An alter-
native to syncing is the PhoneView application for the Mac [8].This
tool provides graphical browsing and searching of contacts, notes, open
websites, browser history, bookmarks and media.
3.3 Analyzing the iTunes Backup File
Syncing an iPad with a computer creates an iTunes backup file, which
holds the majority of the data stored on the iPad.Analysis of the iTunes
backup file can be performed independently of the iPad.A disadvantage
of this method is that the iPad should have been previously configured
to not encrypt backups.The location of the backup file varies by host
operating system [1].The backup file contains several binary Plist files
stored in a directory named with a unique identifier; a summary of the
backup file contents is provided at Apple’s support site [1].iPhone
Backup Extractor [15]can be used to convert the binary Plist format
to permit the contents of the backup file to be viewed using the OS X
3.2 Performing Custom Examinations
None of the commercialtools assessed proved to be as versatile and
comprehensive as a manual examination of the iPad’s file system.What
constitutes relevant evidence depends on the circumstances ofa case,
but not one of the commercial tools can provide results for all scenarios
This means that an examiner will eventually have to conduct a manual
process.Certain software resources and methods allow an examiner to
comprehensively search for and analyze the contents of an iPad after a
forensic duplicate of its media has been created.
Two reoccurring file types employed as support files across several
iPad applications are Property List (Plist) files and SQLite database
files. The Mac OS X command line offers built-in capabilities to read
both file types using the defaults command forPlist files and the
sqlite3 client for databases.Alternatively, PlistEdit Pro [9] and Base
[18]may be used;these applications use syntax highlighting to present
the text content of files in a readable format.The exact format of the
Plist files varies by application;in many cases,they can be read by an
equivalent application on the Mac if the iPad version of the file is copied
to the equivalent OS X user directory location.These files also store
application configuration settings and state information.
In contrast, database files are not as interchangeable, although iTune
does have the ability to sync contacts, calendars, bookmarks, notes and
media database content with a computer for viewing.Note that a one-
way sync is not possible from an iPad,so an examiner should only at-
tempting syncing after a forensic duplicate has been created.An alter-
native to syncing is the PhoneView application for the Mac [8].This
tool provides graphical browsing and searching of contacts, notes, open
websites, browser history, bookmarks and media.
3.3 Analyzing the iTunes Backup File
Syncing an iPad with a computer creates an iTunes backup file, which
holds the majority of the data stored on the iPad.Analysis of the iTunes
backup file can be performed independently of the iPad.A disadvantage
of this method is that the iPad should have been previously configured
to not encrypt backups.The location of the backup file varies by host
operating system [1].The backup file contains several binary Plist files
stored in a directory named with a unique identifier; a summary of the
backup file contents is provided at Apple’s support site [1].iPhone
Backup Extractor [15]can be used to convert the binary Plist format
to permit the contents of the backup file to be viewed using the OS X
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Hay, Krill, Kuhar & Peterson 263
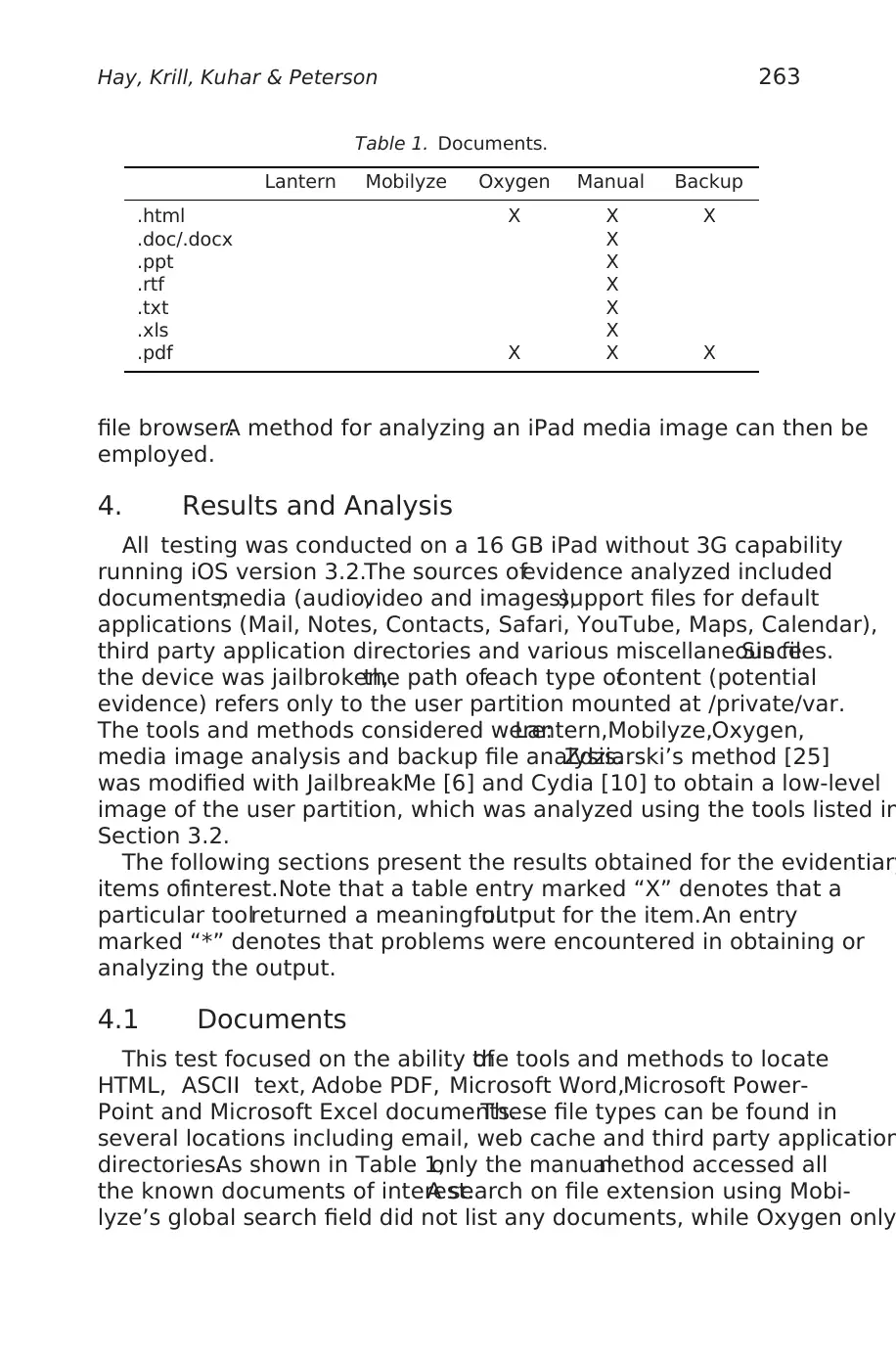
Table 1. Documents.
Lantern Mobilyze Oxygen Manual Backup
.html X X X
.doc/.docx X
.ppt X
.rtf X
.txt X
.xls X
.pdf X X X
file browser.A method for analyzing an iPad media image can then be
employed.
4. Results and Analysis
All testing was conducted on a 16 GB iPad without 3G capability
running iOS version 3.2.The sources ofevidence analyzed included
documents,media (audio,video and images),support files for default
applications (Mail, Notes, Contacts, Safari, YouTube, Maps, Calendar),
third party application directories and various miscellaneous files.Since
the device was jailbroken,the path ofeach type ofcontent (potential
evidence) refers only to the user partition mounted at /private/var.
The tools and methods considered were:Lantern,Mobilyze,Oxygen,
media image analysis and backup file analysis.Zdziarski’s method [25]
was modified with JailbreakMe [6] and Cydia [10] to obtain a low-level
image of the user partition, which was analyzed using the tools listed in
Section 3.2.
The following sections present the results obtained for the evidentiary
items ofinterest.Note that a table entry marked “X” denotes that a
particular toolreturned a meaningfuloutput for the item.An entry
marked “*” denotes that problems were encountered in obtaining or
analyzing the output.
4.1 Documents
This test focused on the ability ofthe tools and methods to locate
HTML, ASCII text, Adobe PDF, Microsoft Word,Microsoft Power-
Point and Microsoft Excel documents.These file types can be found in
several locations including email, web cache and third party application
directories.As shown in Table 1,only the manualmethod accessed all
the known documents of interest.A search on file extension using Mobi-
lyze’s global search field did not list any documents, while Oxygen only
Table 1. Documents.
Lantern Mobilyze Oxygen Manual Backup
.html X X X
.doc/.docx X
.ppt X
.rtf X
.txt X
.xls X
.pdf X X X
file browser.A method for analyzing an iPad media image can then be
employed.
4. Results and Analysis
All testing was conducted on a 16 GB iPad without 3G capability
running iOS version 3.2.The sources ofevidence analyzed included
documents,media (audio,video and images),support files for default
applications (Mail, Notes, Contacts, Safari, YouTube, Maps, Calendar),
third party application directories and various miscellaneous files.Since
the device was jailbroken,the path ofeach type ofcontent (potential
evidence) refers only to the user partition mounted at /private/var.
The tools and methods considered were:Lantern,Mobilyze,Oxygen,
media image analysis and backup file analysis.Zdziarski’s method [25]
was modified with JailbreakMe [6] and Cydia [10] to obtain a low-level
image of the user partition, which was analyzed using the tools listed in
Section 3.2.
The following sections present the results obtained for the evidentiary
items ofinterest.Note that a table entry marked “X” denotes that a
particular toolreturned a meaningfuloutput for the item.An entry
marked “*” denotes that problems were encountered in obtaining or
analyzing the output.
4.1 Documents
This test focused on the ability ofthe tools and methods to locate
HTML, ASCII text, Adobe PDF, Microsoft Word,Microsoft Power-
Point and Microsoft Excel documents.These file types can be found in
several locations including email, web cache and third party application
directories.As shown in Table 1,only the manualmethod accessed all
the known documents of interest.A search on file extension using Mobi-
lyze’s global search field did not list any documents, while Oxygen only
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
264 ADVANCES IN DIGITAL FORENSICS VII
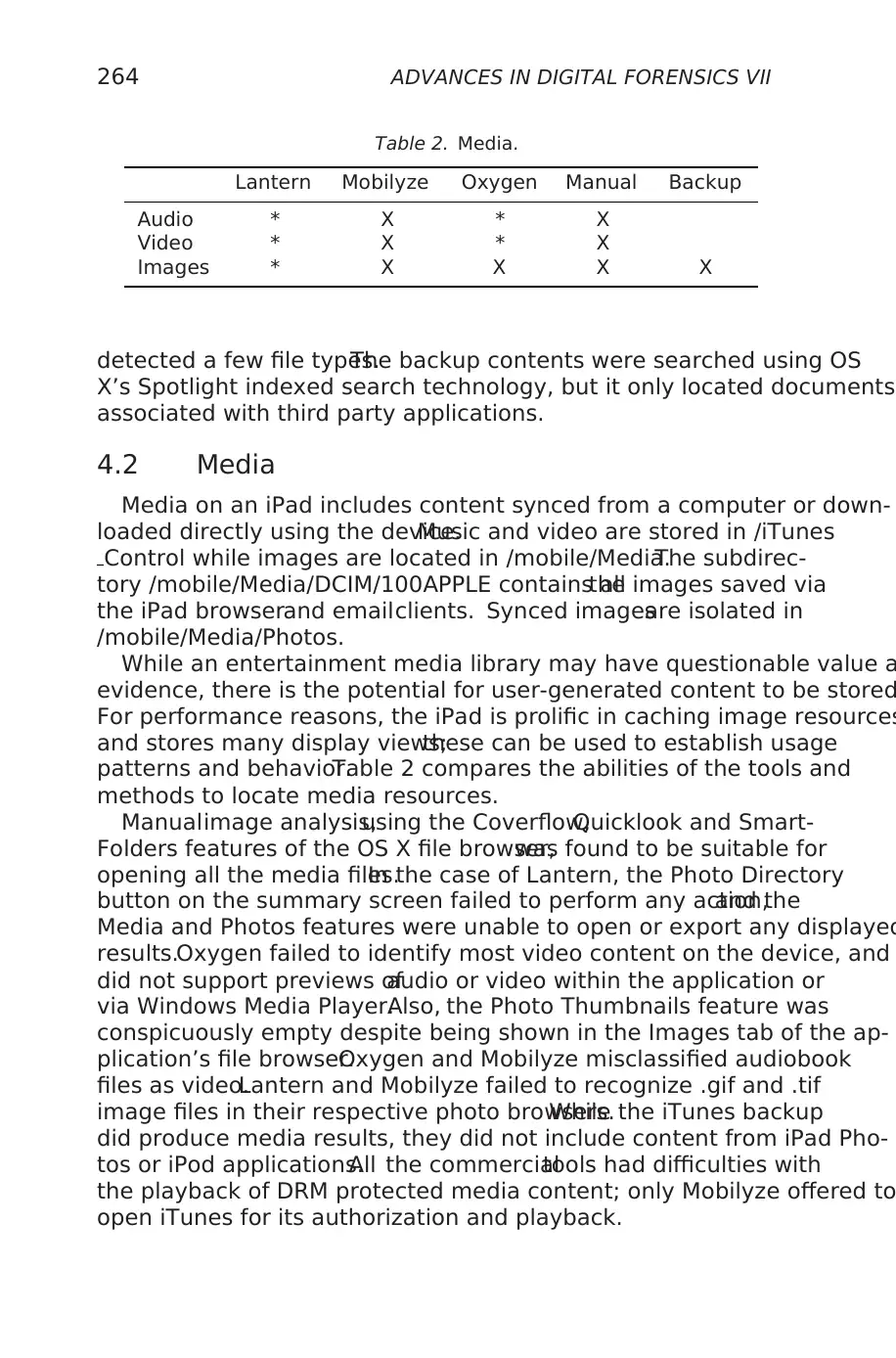
Table 2. Media.
Lantern Mobilyze Oxygen Manual Backup
Audio * X * X
Video * X * X
Images * X X X X
detected a few file types.The backup contents were searched using OS
X’s Spotlight indexed search technology, but it only located documents
associated with third party applications.
4.2 Media
Media on an iPad includes content synced from a computer or down-
loaded directly using the device.Music and video are stored in /iTunes
Control while images are located in /mobile/Media.The subdirec-
tory /mobile/Media/DCIM/100APPLE contains allthe images saved via
the iPad browserand emailclients. Synced imagesare isolated in
/mobile/Media/Photos.
While an entertainment media library may have questionable value a
evidence, there is the potential for user-generated content to be stored
For performance reasons, the iPad is prolific in caching image resources
and stores many display views;these can be used to establish usage
patterns and behavior.Table 2 compares the abilities of the tools and
methods to locate media resources.
Manualimage analysis,using the Coverflow,Quicklook and Smart-
Folders features of the OS X file browser,was found to be suitable for
opening all the media files.In the case of Lantern, the Photo Directory
button on the summary screen failed to perform any action,and the
Media and Photos features were unable to open or export any displayed
results.Oxygen failed to identify most video content on the device, and
did not support previews ofaudio or video within the application or
via Windows Media Player.Also, the Photo Thumbnails feature was
conspicuously empty despite being shown in the Images tab of the ap-
plication’s file browser.Oxygen and Mobilyze misclassified audiobook
files as video.Lantern and Mobilyze failed to recognize .gif and .tif
image files in their respective photo browsers.While the iTunes backup
did produce media results, they did not include content from iPad Pho-
tos or iPod applications.All the commercialtools had difficulties with
the playback of DRM protected media content; only Mobilyze offered to
open iTunes for its authorization and playback.
Table 2. Media.
Lantern Mobilyze Oxygen Manual Backup
Audio * X * X
Video * X * X
Images * X X X X
detected a few file types.The backup contents were searched using OS
X’s Spotlight indexed search technology, but it only located documents
associated with third party applications.
4.2 Media
Media on an iPad includes content synced from a computer or down-
loaded directly using the device.Music and video are stored in /iTunes
Control while images are located in /mobile/Media.The subdirec-
tory /mobile/Media/DCIM/100APPLE contains allthe images saved via
the iPad browserand emailclients. Synced imagesare isolated in
/mobile/Media/Photos.
While an entertainment media library may have questionable value a
evidence, there is the potential for user-generated content to be stored
For performance reasons, the iPad is prolific in caching image resources
and stores many display views;these can be used to establish usage
patterns and behavior.Table 2 compares the abilities of the tools and
methods to locate media resources.
Manualimage analysis,using the Coverflow,Quicklook and Smart-
Folders features of the OS X file browser,was found to be suitable for
opening all the media files.In the case of Lantern, the Photo Directory
button on the summary screen failed to perform any action,and the
Media and Photos features were unable to open or export any displayed
results.Oxygen failed to identify most video content on the device, and
did not support previews ofaudio or video within the application or
via Windows Media Player.Also, the Photo Thumbnails feature was
conspicuously empty despite being shown in the Images tab of the ap-
plication’s file browser.Oxygen and Mobilyze misclassified audiobook
files as video.Lantern and Mobilyze failed to recognize .gif and .tif
image files in their respective photo browsers.While the iTunes backup
did produce media results, they did not include content from iPad Pho-
tos or iPod applications.All the commercialtools had difficulties with
the playback of DRM protected media content; only Mobilyze offered to
open iTunes for its authorization and playback.
Hay, Krill, Kuhar & Peterson 265
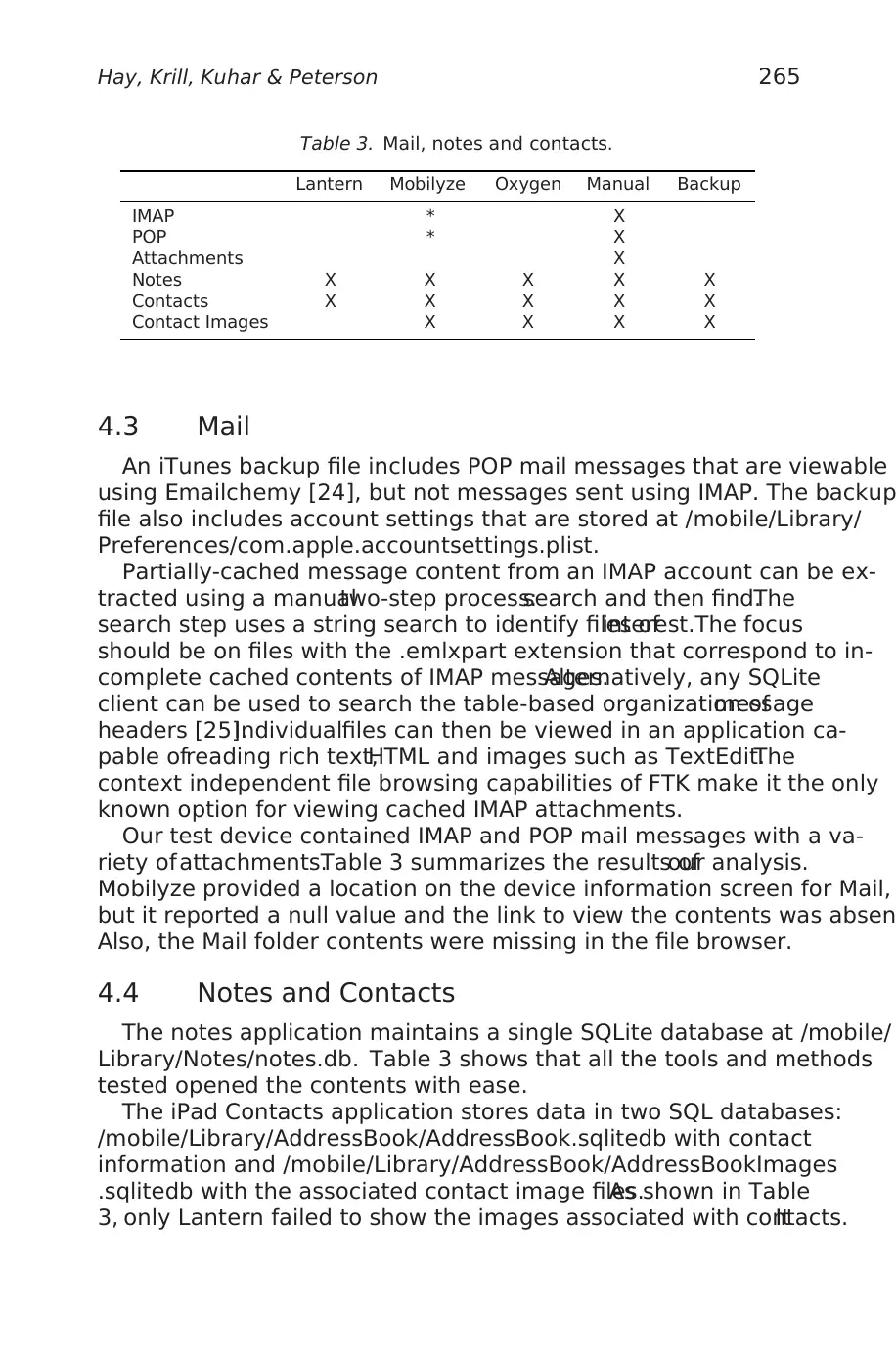
Table 3. Mail, notes and contacts.
Lantern Mobilyze Oxygen Manual Backup
IMAP * X
POP * X
Attachments X
Notes X X X X X
Contacts X X X X X
Contact Images X X X X
4.3 Mail
An iTunes backup file includes POP mail messages that are viewable
using Emailchemy [24], but not messages sent using IMAP. The backup
file also includes account settings that are stored at /mobile/Library/
Preferences/com.apple.accountsettings.plist.
Partially-cached message content from an IMAP account can be ex-
tracted using a manualtwo-step process:search and then find.The
search step uses a string search to identify files ofinterest.The focus
should be on files with the .emlxpart extension that correspond to in-
complete cached contents of IMAP messages.Alternatively, any SQLite
client can be used to search the table-based organization ofmessage
headers [25].Individualfiles can then be viewed in an application ca-
pable ofreading rich text,HTML and images such as TextEdit.The
context independent file browsing capabilities of FTK make it the only
known option for viewing cached IMAP attachments.
Our test device contained IMAP and POP mail messages with a va-
riety of attachments.Table 3 summarizes the results ofour analysis.
Mobilyze provided a location on the device information screen for Mail,
but it reported a null value and the link to view the contents was absen
Also, the Mail folder contents were missing in the file browser.
4.4 Notes and Contacts
The notes application maintains a single SQLite database at /mobile/
Library/Notes/notes.db. Table 3 shows that all the tools and methods
tested opened the contents with ease.
The iPad Contacts application stores data in two SQL databases:
/mobile/Library/AddressBook/AddressBook.sqlitedb with contact
information and /mobile/Library/AddressBook/AddressBookImages
.sqlitedb with the associated contact image files.As shown in Table
3, only Lantern failed to show the images associated with contacts.It
Table 3. Mail, notes and contacts.
Lantern Mobilyze Oxygen Manual Backup
IMAP * X
POP * X
Attachments X
Notes X X X X X
Contacts X X X X X
Contact Images X X X X
4.3 Mail
An iTunes backup file includes POP mail messages that are viewable
using Emailchemy [24], but not messages sent using IMAP. The backup
file also includes account settings that are stored at /mobile/Library/
Preferences/com.apple.accountsettings.plist.
Partially-cached message content from an IMAP account can be ex-
tracted using a manualtwo-step process:search and then find.The
search step uses a string search to identify files ofinterest.The focus
should be on files with the .emlxpart extension that correspond to in-
complete cached contents of IMAP messages.Alternatively, any SQLite
client can be used to search the table-based organization ofmessage
headers [25].Individualfiles can then be viewed in an application ca-
pable ofreading rich text,HTML and images such as TextEdit.The
context independent file browsing capabilities of FTK make it the only
known option for viewing cached IMAP attachments.
Our test device contained IMAP and POP mail messages with a va-
riety of attachments.Table 3 summarizes the results ofour analysis.
Mobilyze provided a location on the device information screen for Mail,
but it reported a null value and the link to view the contents was absen
Also, the Mail folder contents were missing in the file browser.
4.4 Notes and Contacts
The notes application maintains a single SQLite database at /mobile/
Library/Notes/notes.db. Table 3 shows that all the tools and methods
tested opened the contents with ease.
The iPad Contacts application stores data in two SQL databases:
/mobile/Library/AddressBook/AddressBook.sqlitedb with contact
information and /mobile/Library/AddressBook/AddressBookImages
.sqlitedb with the associated contact image files.As shown in Table
3, only Lantern failed to show the images associated with contacts.It
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

266 ADVANCES IN DIGITAL FORENSICS VII
also represented business contacts as blank entries and suffered from
readability problems.
4.5 Safari
The Safari browser stores relevant information in several different file
/mobile/Library/Safari/Bookmarks.db
− Bookmarked websites.
/mobile/Library/Safari/History.plist
− Previously visited websites.
/mobile/Library/Cookies/Cookies.plist
− Cookies installed by visited websites, possibly including website
account information.
/mobile/Library/Caches/Safari/Thumbnails
− Cached images.
/mobile/Library/Caches/Safari/RecentSearches.plist
− Last twenty search strings entered in the Safari search bar.
/mobile/Library/Safari/SuspendState.plist
− Last Safari configuration (open windows and associated URLs)
before it was quit.
/mobile/Media/WebClips
− Bookmarks saved to the iPad’s home screen; these are shortcuts
to websites that launch in Safari and use the favicons of the pages
as their home screen icons.
PhoneView was used to successfully display and search the bookmark
and history files.Since the history file is a Plist file,it could also be
copied to the ∼/Library/Safari directory on a Mac and viewed using
the OS X version of Safari.This method also enabled some cached web
content from the history file to be browsed via Coverflow.The cookies
file could be copied to ∼/Library/Cookies on the Mac and its contents
viewed by selecting Security → Show Cookies from the Safari application
preferences.As a performance measure, many apps (including Safari on
the iPad) cache a screenshot ofthe last view ofan application before
quitting to increase the perceived speed on relaunch.This image can
be identified based on its creation date in the Thumbnails directory,
enabling the verification of the last item viewed in Safari.
Table 4 presents the test results.Lantern,Mobilyze and Oxygen all
contain an interface element for displaying bookmarks, but they failed t
also represented business contacts as blank entries and suffered from
readability problems.
4.5 Safari
The Safari browser stores relevant information in several different file
/mobile/Library/Safari/Bookmarks.db
− Bookmarked websites.
/mobile/Library/Safari/History.plist
− Previously visited websites.
/mobile/Library/Cookies/Cookies.plist
− Cookies installed by visited websites, possibly including website
account information.
/mobile/Library/Caches/Safari/Thumbnails
− Cached images.
/mobile/Library/Caches/Safari/RecentSearches.plist
− Last twenty search strings entered in the Safari search bar.
/mobile/Library/Safari/SuspendState.plist
− Last Safari configuration (open windows and associated URLs)
before it was quit.
/mobile/Media/WebClips
− Bookmarks saved to the iPad’s home screen; these are shortcuts
to websites that launch in Safari and use the favicons of the pages
as their home screen icons.
PhoneView was used to successfully display and search the bookmark
and history files.Since the history file is a Plist file,it could also be
copied to the ∼/Library/Safari directory on a Mac and viewed using
the OS X version of Safari.This method also enabled some cached web
content from the history file to be browsed via Coverflow.The cookies
file could be copied to ∼/Library/Cookies on the Mac and its contents
viewed by selecting Security → Show Cookies from the Safari application
preferences.As a performance measure, many apps (including Safari on
the iPad) cache a screenshot ofthe last view ofan application before
quitting to increase the perceived speed on relaunch.This image can
be identified based on its creation date in the Thumbnails directory,
enabling the verification of the last item viewed in Safari.
Table 4 presents the test results.Lantern,Mobilyze and Oxygen all
contain an interface element for displaying bookmarks, but they failed t
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hay, Krill, Kuhar & Peterson 267
Table 4. Safari.
Lantern Mobilyze Oxygen Manual Backup
History X X X X X
Cookies X X
Recent Searches X
SuspendState X X
Bookmarks * * * X X
Cache X
WebClips X X
show the results that were known to be present.The marketed version
of Oxygen provides an optional cache analyzer, but this is not included
in the trial version of the tool used in our tests.The backup file excluded
most cached application contents, including those from Safari.
4.6 YouTube
YouTube is a defaultapplication in iOS thathas severalsupport
files.A value string in the history dictionary is accessed on the web by
prepending the value with http://www.youtube.com/watch ?v= in a
web browser.The values are found in /mobile/Library/Preferences/
com.apple.youtube.plist, which maintains a list of video bookmarks,
the last search string used in the application search bar and the video
viewing history.The user’s account name is stored in /mobile/Library/
Preferences/com.apple.youtubeframework.plist.
Table 5. YouTube.
Lantern Mobilyze Oxygen Manual Backup
Account Details X
Search History X X
Viewing History X X
Bookmarks * * *
The results ofthe tests are shown in Table 5.Mobilyze provides
an interface element for YouTube Bookmarks on the device information
screen,but it displayed a nullvalue despite the fact that severalbook-
marks were created during our tests.Curiously,the Bookmarks key in
the first Plist file also had a null value, indicating that YouTube Book-
marks may not be stored locally,but are pulled from the web.The
iTunes backup file version of com.apple.youtubeframework.plist ex-
cludes the key and value for YouTubeAccount, although the file itself is
present.
Table 4. Safari.
Lantern Mobilyze Oxygen Manual Backup
History X X X X X
Cookies X X
Recent Searches X
SuspendState X X
Bookmarks * * * X X
Cache X
WebClips X X
show the results that were known to be present.The marketed version
of Oxygen provides an optional cache analyzer, but this is not included
in the trial version of the tool used in our tests.The backup file excluded
most cached application contents, including those from Safari.
4.6 YouTube
YouTube is a defaultapplication in iOS thathas severalsupport
files.A value string in the history dictionary is accessed on the web by
prepending the value with http://www.youtube.com/watch ?v= in a
web browser.The values are found in /mobile/Library/Preferences/
com.apple.youtube.plist, which maintains a list of video bookmarks,
the last search string used in the application search bar and the video
viewing history.The user’s account name is stored in /mobile/Library/
Preferences/com.apple.youtubeframework.plist.
Table 5. YouTube.
Lantern Mobilyze Oxygen Manual Backup
Account Details X
Search History X X
Viewing History X X
Bookmarks * * *
The results ofthe tests are shown in Table 5.Mobilyze provides
an interface element for YouTube Bookmarks on the device information
screen,but it displayed a nullvalue despite the fact that severalbook-
marks were created during our tests.Curiously,the Bookmarks key in
the first Plist file also had a null value, indicating that YouTube Book-
marks may not be stored locally,but are pulled from the web.The
iTunes backup file version of com.apple.youtubeframework.plist ex-
cludes the key and value for YouTubeAccount, although the file itself is
present.
268 ADVANCES IN DIGITAL FORENSICS VII
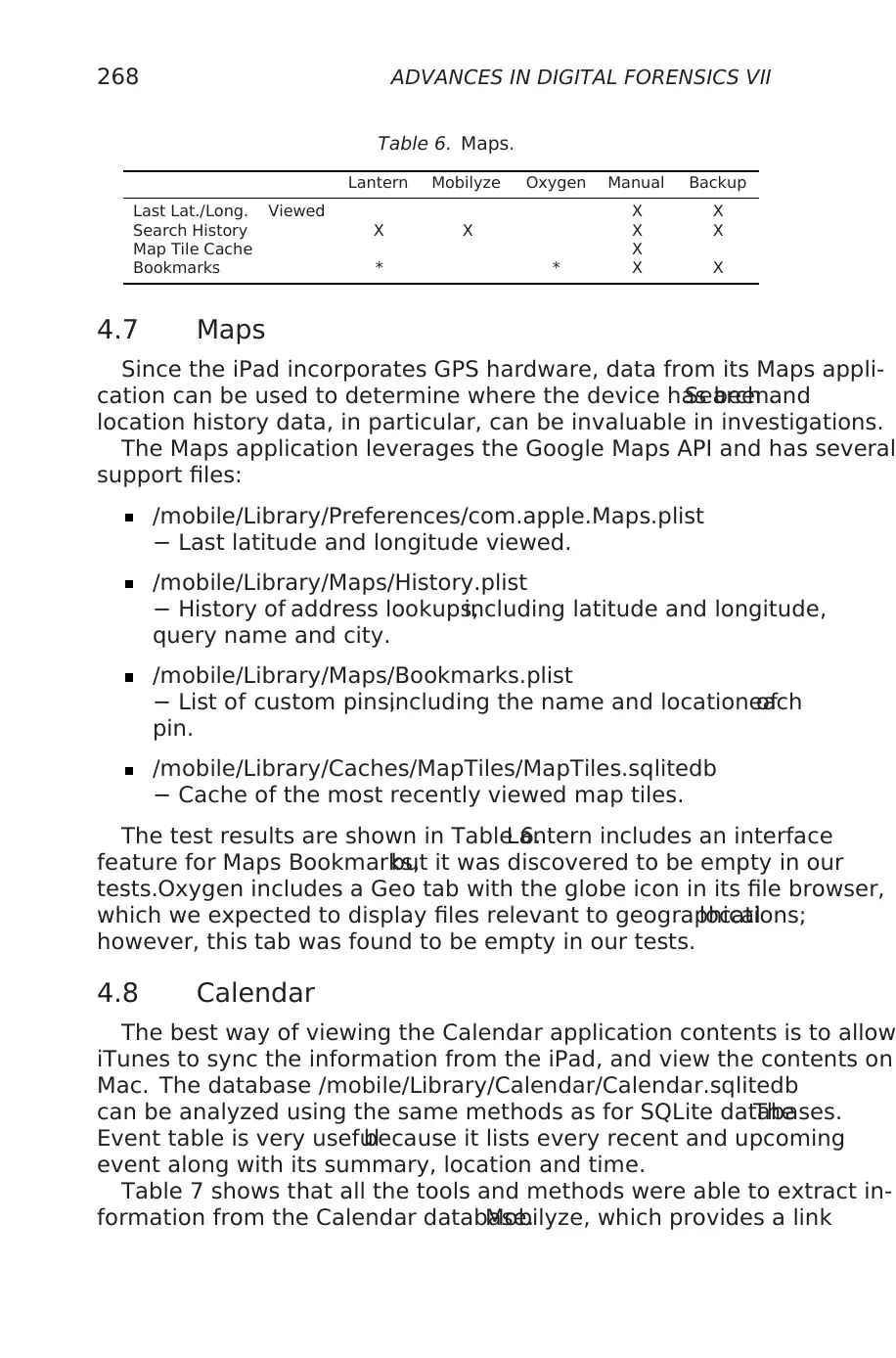
Table 6. Maps.
Lantern Mobilyze Oxygen Manual Backup
Last Lat./Long. Viewed X X
Search History X X X X
Map Tile Cache X
Bookmarks * * X X
4.7 Maps
Since the iPad incorporates GPS hardware, data from its Maps appli-
cation can be used to determine where the device has been.Search and
location history data, in particular, can be invaluable in investigations.
The Maps application leverages the Google Maps API and has several
support files:
/mobile/Library/Preferences/com.apple.Maps.plist
− Last latitude and longitude viewed.
/mobile/Library/Maps/History.plist
− History of address lookups,including latitude and longitude,
query name and city.
/mobile/Library/Maps/Bookmarks.plist
− List of custom pins,including the name and location ofeach
pin.
/mobile/Library/Caches/MapTiles/MapTiles.sqlitedb
− Cache of the most recently viewed map tiles.
The test results are shown in Table 6.Lantern includes an interface
feature for Maps Bookmarks,but it was discovered to be empty in our
tests.Oxygen includes a Geo tab with the globe icon in its file browser,
which we expected to display files relevant to geographicallocations;
however, this tab was found to be empty in our tests.
4.8 Calendar
The best way of viewing the Calendar application contents is to allow
iTunes to sync the information from the iPad, and view the contents on
Mac. The database /mobile/Library/Calendar/Calendar.sqlitedb
can be analyzed using the same methods as for SQLite databases.The
Event table is very usefulbecause it lists every recent and upcoming
event along with its summary, location and time.
Table 7 shows that all the tools and methods were able to extract in-
formation from the Calendar database.Mobilyze, which provides a link
Table 6. Maps.
Lantern Mobilyze Oxygen Manual Backup
Last Lat./Long. Viewed X X
Search History X X X X
Map Tile Cache X
Bookmarks * * X X
4.7 Maps
Since the iPad incorporates GPS hardware, data from its Maps appli-
cation can be used to determine where the device has been.Search and
location history data, in particular, can be invaluable in investigations.
The Maps application leverages the Google Maps API and has several
support files:
/mobile/Library/Preferences/com.apple.Maps.plist
− Last latitude and longitude viewed.
/mobile/Library/Maps/History.plist
− History of address lookups,including latitude and longitude,
query name and city.
/mobile/Library/Maps/Bookmarks.plist
− List of custom pins,including the name and location ofeach
pin.
/mobile/Library/Caches/MapTiles/MapTiles.sqlitedb
− Cache of the most recently viewed map tiles.
The test results are shown in Table 6.Lantern includes an interface
feature for Maps Bookmarks,but it was discovered to be empty in our
tests.Oxygen includes a Geo tab with the globe icon in its file browser,
which we expected to display files relevant to geographicallocations;
however, this tab was found to be empty in our tests.
4.8 Calendar
The best way of viewing the Calendar application contents is to allow
iTunes to sync the information from the iPad, and view the contents on
Mac. The database /mobile/Library/Calendar/Calendar.sqlitedb
can be analyzed using the same methods as for SQLite databases.The
Event table is very usefulbecause it lists every recent and upcoming
event along with its summary, location and time.
Table 7 shows that all the tools and methods were able to extract in-
formation from the Calendar database.Mobilyze, which provides a link
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




