Digital Media Report
VerifiedAdded on 2020/02/24
|8
|1425
|62
Report
AI Summary
This report delves into the advancements in digital media, focusing on the Internet of Things (IoT) and its implications for user experience. It discusses various technologies such as sensors, RFID, and video tracking, highlighting their advantages, disadvantages, and applications. The report also addresses security concerns related to these technologies and provides insights into bandwidth growth and its impact on digital media applications. References from notable authors in the field support the findings.
report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Answer 1:.........................................................................................................................................1
Answer 2:.........................................................................................................................................1
Answer 3:.........................................................................................................................................2
Answer 4:.........................................................................................................................................5
Answer 5:.........................................................................................................................................5
Answer 6:.........................................................................................................................................6
References........................................................................................................................................7
Answer 1:.........................................................................................................................................1
Answer 2:.........................................................................................................................................1
Answer 3:.........................................................................................................................................2
Answer 4:.........................................................................................................................................5
Answer 5:.........................................................................................................................................5
Answer 6:.........................................................................................................................................6
References........................................................................................................................................7

Answer 1:
This is considered to the smarter and the simple system which is able to handle the useful setups
that makes the life easy. Along with this, there is an easy elimination of the interface to embrace
the different natural processes and work for the proper betterment of the messaging for the better
user experience. The UI is set with the constant stream of new interface which is filled with the
different menus and the buttons. This explains about the conversational apps and how the UI
interaction is able to work with the advancement in the technology with the increased invisible
apps that are set with the UI for the computer input. The designer need to manage the
applications of the bank and then work towards the better brain computer interaction. (Cui,
2016).
The examples related to this are the driving approaching the car, the taking of the smartphone out
of the wallet, turning the mobile phone on, sliding the phone to unlock, switch off and sits in the
car. The other example of the same is the shopper enters the shop, use his mobile phone and then
checks it, buy grocery and get billing. There are different possibility where a person can reach to
her destination. Hence, the no user interface is best.
Answer 2:
Twisted coaxial Fibre
Bandwidth 0-3.5 KHz 0 to 500 MHz 186 to 370 Thz
This is considered to the smarter and the simple system which is able to handle the useful setups
that makes the life easy. Along with this, there is an easy elimination of the interface to embrace
the different natural processes and work for the proper betterment of the messaging for the better
user experience. The UI is set with the constant stream of new interface which is filled with the
different menus and the buttons. This explains about the conversational apps and how the UI
interaction is able to work with the advancement in the technology with the increased invisible
apps that are set with the UI for the computer input. The designer need to manage the
applications of the bank and then work towards the better brain computer interaction. (Cui,
2016).
The examples related to this are the driving approaching the car, the taking of the smartphone out
of the wallet, turning the mobile phone on, sliding the phone to unlock, switch off and sits in the
car. The other example of the same is the shopper enters the shop, use his mobile phone and then
checks it, buy grocery and get billing. There are different possibility where a person can reach to
her destination. Hence, the no user interface is best.
Answer 2:
Twisted coaxial Fibre
Bandwidth 0-3.5 KHz 0 to 500 MHz 186 to 370 Thz
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
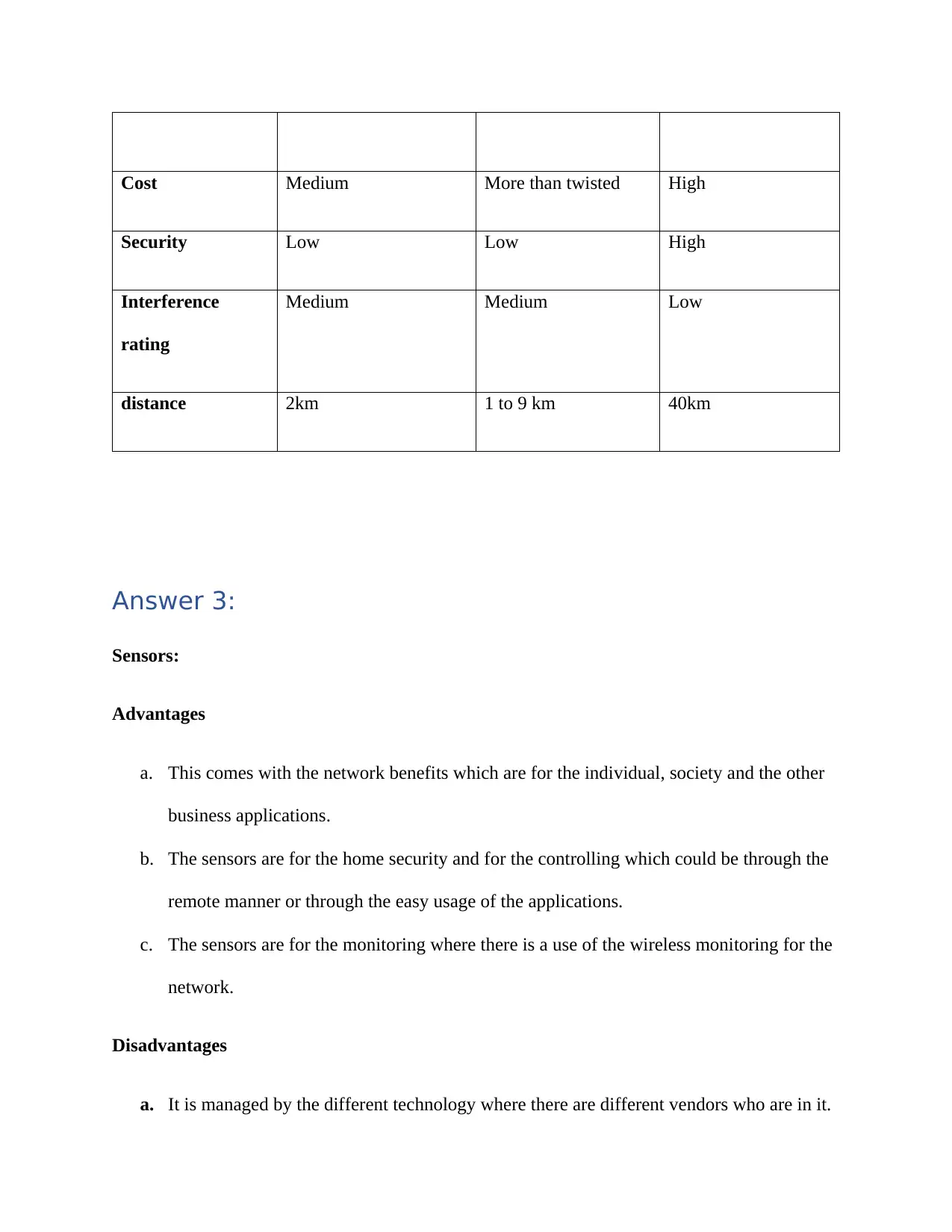
Cost Medium More than twisted High
Security Low Low High
Interference
rating
Medium Medium Low
distance 2km 1 to 9 km 40km
Answer 3:
Sensors:
Advantages
a. This comes with the network benefits which are for the individual, society and the other
business applications.
b. The sensors are for the home security and for the controlling which could be through the
remote manner or through the easy usage of the applications.
c. The sensors are for the monitoring where there is a use of the wireless monitoring for the
network.
Disadvantages
a. It is managed by the different technology where there are different vendors who are in it.
Security Low Low High
Interference
rating
Medium Medium Low
distance 2km 1 to 9 km 40km
Answer 3:
Sensors:
Advantages
a. This comes with the network benefits which are for the individual, society and the other
business applications.
b. The sensors are for the home security and for the controlling which could be through the
remote manner or through the easy usage of the applications.
c. The sensors are for the monitoring where there is a use of the wireless monitoring for the
network.
Disadvantages
a. It is managed by the different technology where there are different vendors who are in it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b. The implementation of IoT is considered to be a major loss of the job for the people with
everything on the applications. (Rifkin, 2014).
c. The issues of the multiple technologies which leads to the consumption of time in the
complex systems. with this, there is a possibility that IoT service provider have to pay hre
for the hiring and for retention of employees.
Key requirements
The requirements are based on working over the IoT systems which includes the costs for the
testing of device manufacturers and the network service providers.
Applications
This is needed in the cameras, security alarm or the door locks.
RFID
Advantages
The RFID makes use of the electromagnetic fields to identify and track the tags which are
attached to the objects. The passive tags are contained with the collect energy with interrogating
the radio waves. The active tags are handling the local power source with the RFID reader to
interrogate and handle the operations at the hundreds of meters. The barcodes are for the
embedded subject with the tracked object. (Atzori et al., 2014).
Disadvantages
everything on the applications. (Rifkin, 2014).
c. The issues of the multiple technologies which leads to the consumption of time in the
complex systems. with this, there is a possibility that IoT service provider have to pay hre
for the hiring and for retention of employees.
Key requirements
The requirements are based on working over the IoT systems which includes the costs for the
testing of device manufacturers and the network service providers.
Applications
This is needed in the cameras, security alarm or the door locks.
RFID
Advantages
The RFID makes use of the electromagnetic fields to identify and track the tags which are
attached to the objects. The passive tags are contained with the collect energy with interrogating
the radio waves. The active tags are handling the local power source with the RFID reader to
interrogate and handle the operations at the hundreds of meters. The barcodes are for the
embedded subject with the tracked object. (Atzori et al., 2014).
Disadvantages

The issues are related to the fact that RFID could be used by the multiple people for the receiving
and the transmission of the data which could lead to the interference and the radiation exposure
as well.
Key requirements
The RFID is set for the cash, clothing and the possession with the implantations in animal and
people. The concern is about the privacy and security set for handling the RFID cards, labels and
the other form factors.
Applications
RFID tags include the automobile during production which could be used to track with the
progress set under the assembly line.
Video Tracking
Advantages
It is for the tracking of the objects with the use of camera. The variety of uses which includes eh
security and surveillance, interaction, video communication and compression, augmented reality
and traffic control.
Disadvantages
The disadvantage is about the objects that are relative to the frame rate with the tracking of the
object change orientation over the time.
Key requirements
and the transmission of the data which could lead to the interference and the radiation exposure
as well.
Key requirements
The RFID is set for the cash, clothing and the possession with the implantations in animal and
people. The concern is about the privacy and security set for handling the RFID cards, labels and
the other form factors.
Applications
RFID tags include the automobile during production which could be used to track with the
progress set under the assembly line.
Video Tracking
Advantages
It is for the tracking of the objects with the use of camera. The variety of uses which includes eh
security and surveillance, interaction, video communication and compression, augmented reality
and traffic control.
Disadvantages
The disadvantage is about the objects that are relative to the frame rate with the tracking of the
object change orientation over the time.
Key requirements
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The requirements are for the checking of the target representation and the localization, using the
blob tracking which is for the identification of the human movement. (Patton et al., 2014).
Applications
For the 3D objects and for the affined transformation. The video compression is also for the
macroblocks.
Answer 4:
The issues are related to the security problems where the focus is on the communication and the
working over the users to handle the quality of the people’s live. The storage, processing phase
with the processing is based on the different activities where the future behavior of the people is
mapped to handle the data encryption or the access control mechanism. The privacy and security
issues are set with the widespread usage with the wireless sensors that involve the access and the
availability, accuracy and confidentiality problems. The issues are also related with the
transmission, storage and the processing phase. The tracking of the lifestyle, activities, with the
accessibility of the third and the unauthorized person. The issue is related to the threat and the
attacker models.
Answer 5:
Request Trigger time = 1s
Round trip propagation delay = 12 ms
blob tracking which is for the identification of the human movement. (Patton et al., 2014).
Applications
For the 3D objects and for the affined transformation. The video compression is also for the
macroblocks.
Answer 4:
The issues are related to the security problems where the focus is on the communication and the
working over the users to handle the quality of the people’s live. The storage, processing phase
with the processing is based on the different activities where the future behavior of the people is
mapped to handle the data encryption or the access control mechanism. The privacy and security
issues are set with the widespread usage with the wireless sensors that involve the access and the
availability, accuracy and confidentiality problems. The issues are also related with the
transmission, storage and the processing phase. The tracking of the lifestyle, activities, with the
accessibility of the third and the unauthorized person. The issue is related to the threat and the
attacker models.
Answer 5:
Request Trigger time = 1s
Round trip propagation delay = 12 ms
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Request processing time = 3ms
Application transportation time = 2ms
Total time: 1s+12ms+3ms+2m+2ms = 1.019 s
If the publish/subscribe communication model will be used, the request time of 1 sec will be
removed, request processing time will be removed and the round-trip time will become half due
to only one way transportation of data and hence, the total time will be:
Time = 6ms+2ms = 8ms
Answer 6:
Nielsen law of internet bandwidth includes the higher end connection speed which growth with
the year. Hence, for this, there is a connection of the constant dot which works for the telecom
companies. The users are found to be reluctant to spend the money on the bandwidth where the
user base is tending to get broad. Here, there are low end users with the high end working for the
average shift that is low. The designing applications are important for the computation with the
web designs set for the optimized usability and for the availability of the speeds. (Patton et al.,
2014).
With this, there has been observation on Moore’s law about the computer processing which
doubles every 18 months. There are high end users for the bandwidth growth in 50% with the
10% less than the Moore law. For the IoT, there is a need for the telecom companies to work
with the time to update and handle the reluctance to spend the money on the bandwidth.
Application transportation time = 2ms
Total time: 1s+12ms+3ms+2m+2ms = 1.019 s
If the publish/subscribe communication model will be used, the request time of 1 sec will be
removed, request processing time will be removed and the round-trip time will become half due
to only one way transportation of data and hence, the total time will be:
Time = 6ms+2ms = 8ms
Answer 6:
Nielsen law of internet bandwidth includes the higher end connection speed which growth with
the year. Hence, for this, there is a connection of the constant dot which works for the telecom
companies. The users are found to be reluctant to spend the money on the bandwidth where the
user base is tending to get broad. Here, there are low end users with the high end working for the
average shift that is low. The designing applications are important for the computation with the
web designs set for the optimized usability and for the availability of the speeds. (Patton et al.,
2014).
With this, there has been observation on Moore’s law about the computer processing which
doubles every 18 months. There are high end users for the bandwidth growth in 50% with the
10% less than the Moore law. For the IoT, there is a need for the telecom companies to work
with the time to update and handle the reluctance to spend the money on the bandwidth.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





