IT Profession and Ethics: Online Privacy Breach Cases in Australia
VerifiedAdded on 2022/11/22
|8
|2043
|334
Essay
AI Summary
This essay delves into the critical aspects of IT professionalism and ethics, focusing on digital privacy within the Australian context. It begins by emphasizing the importance of online privacy for individuals and highlights recent privacy breaches, particularly those related to loyalty programs launched by Coles and Woolworths. The essay defines digital privacy, distinguishing it from general privacy, and outlines the role of the Privacy Act 1988 in Australia. It examines the potential impacts of losing online privacy, including threats to communication, location, and data privacy. The essay explores security measures such as strong passwords and two-factor authentication, while also considering the varying levels of privacy required for different individuals, including VIPs. It provides an analysis of the Coles and Woolworths loyalty program data breaches, discussing their implications and the need for legislative action and public awareness. The essay compares the Privacy Act 1988 with the General Data Protection Regulation (GDPR), highlighting key differences and similarities, and concludes by reiterating the importance of individual responsibility and legislative reform in safeguarding digital privacy.

Running head: IT PROFESSION AND ETHICS
IT Profession and Ethics
Name of the Student
Name of the University
Author Note
IT Profession and Ethics
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT PROFESSION AND ETHICS
Introduction:
Online privacy is one of the important factor in the current situation for ensuring safety of
the individual peoples (Baruh, Secinti & Cemalcilar, 2017). But in Australia there are several of
cases of online privacy breach in the recent time. In most of the cases it has been assessed that
peoples are totally unaware about their privacy on the online environment and this is a serious
issue which can lead to several of privacy breach related cases. In Australia recently this type of
two cases happened where online privacy of the peoples were breached. These two privacy
breaches were regarding loyalty program launched by the Coles and Woolworth where
significant amount of privacy related issues were seen. These privacy breaches were the perfect
example of issues regarding the digital privacy.
In this essay both of the identified data breach cases will be analysed briefly. This essay
will also describe the important factors of the online privacy and how this privacy can be
protected successfully in an online environment.
Digital Privacy:
Digital privacy of the individuals is very much important so that they can protect
themselves from various type of threats, but before proceeding directly to the digital privacy it is
very much important to clear the concept of the privacy (Salimian et al., 2016). Privacy is the
ability of the individuals through which they can protect their personals and confidential data
from being exposed to the public. In this aspect the digital privacy is also the same but digital
privacy defines protection of the confidential data in the online environment. The digital privacy
is very much important for protection of the digital identity of the user or any type of digital
information which are confidential in nature. Australia is one of the major country, where digital
Introduction:
Online privacy is one of the important factor in the current situation for ensuring safety of
the individual peoples (Baruh, Secinti & Cemalcilar, 2017). But in Australia there are several of
cases of online privacy breach in the recent time. In most of the cases it has been assessed that
peoples are totally unaware about their privacy on the online environment and this is a serious
issue which can lead to several of privacy breach related cases. In Australia recently this type of
two cases happened where online privacy of the peoples were breached. These two privacy
breaches were regarding loyalty program launched by the Coles and Woolworth where
significant amount of privacy related issues were seen. These privacy breaches were the perfect
example of issues regarding the digital privacy.
In this essay both of the identified data breach cases will be analysed briefly. This essay
will also describe the important factors of the online privacy and how this privacy can be
protected successfully in an online environment.
Digital Privacy:
Digital privacy of the individuals is very much important so that they can protect
themselves from various type of threats, but before proceeding directly to the digital privacy it is
very much important to clear the concept of the privacy (Salimian et al., 2016). Privacy is the
ability of the individuals through which they can protect their personals and confidential data
from being exposed to the public. In this aspect the digital privacy is also the same but digital
privacy defines protection of the confidential data in the online environment. The digital privacy
is very much important for protection of the digital identity of the user or any type of digital
information which are confidential in nature. Australia is one of the major country, where digital

2IT PROFESSION AND ETHICS
privacy is one of the major factor and looking at this Australian government has implemented the
Privacy Act 1988 for protecting the confidentiality of the individual users (Watts & Casanovas,
2018). This privacy act of Australia currently regulates how the Australian Government agencies
and the organization will be handling the personal information of the individual users which has
been collected by them. The Privacy Act 1988 is consisting some important principles for the
regulating these organization and Government agencies and in a collective form these principles
are known as the APP entities.
Impact of losing the Online Privacy and Threats:
Individuals must be protected from the online privacy breach related issues as this can
lead to exposure of the confidential information of them, with that it also ensures the safety of
the peoples. For the digital type of materials there can be various type of privacy issues as
privacy can be leaked easily if the digital materials are not protected properly. Privacy of the
individuals can be violated easily due to the improper protection of the digital materials (Hwang,
2015). With the individual privacy the digital materials can also violate communication privacy,
location related privacy, and the privacy regarding data and image. Due to this reason, all types
of digital materials must be protected using proper privacy so that above kind of issues can be
avoided.
In such type of cases where the online privacy of the users is not maintained there can be
several types of threats. In this cases, if the online privacy of the peoples are not protected using
proper measures then the important and confidential data of them can be easily collected from
the peoples without acknowledgement of those peoples by the ISPs of them (Bartsch & Dienlin,
2016). Some more threats can occur in this type of cases regarding the reason of online privacy
breach which are the information loss and security loss. This privacy can be protected properly if
privacy is one of the major factor and looking at this Australian government has implemented the
Privacy Act 1988 for protecting the confidentiality of the individual users (Watts & Casanovas,
2018). This privacy act of Australia currently regulates how the Australian Government agencies
and the organization will be handling the personal information of the individual users which has
been collected by them. The Privacy Act 1988 is consisting some important principles for the
regulating these organization and Government agencies and in a collective form these principles
are known as the APP entities.
Impact of losing the Online Privacy and Threats:
Individuals must be protected from the online privacy breach related issues as this can
lead to exposure of the confidential information of them, with that it also ensures the safety of
the peoples. For the digital type of materials there can be various type of privacy issues as
privacy can be leaked easily if the digital materials are not protected properly. Privacy of the
individuals can be violated easily due to the improper protection of the digital materials (Hwang,
2015). With the individual privacy the digital materials can also violate communication privacy,
location related privacy, and the privacy regarding data and image. Due to this reason, all types
of digital materials must be protected using proper privacy so that above kind of issues can be
avoided.
In such type of cases where the online privacy of the users is not maintained there can be
several types of threats. In this cases, if the online privacy of the peoples are not protected using
proper measures then the important and confidential data of them can be easily collected from
the peoples without acknowledgement of those peoples by the ISPs of them (Bartsch & Dienlin,
2016). Some more threats can occur in this type of cases regarding the reason of online privacy
breach which are the information loss and security loss. This privacy can be protected properly if
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT PROFESSION AND ETHICS
proper security measures are followed. All the personnel must be implementing a strong
password and a unique passwords for all of their online accounts. Also, many online platforms
provide two factor authentication for some extra security. This security measures can be used for
the protection of online privacy of the individual peoples.
Google, Facebook, iCloud, all are very much popular online platforms and currently used
by millions of users worldwide. Due to this fact it is crucial to ensure the online privacy of this
online platform users. In this case also, the users of this online platforms need to follow some of
the important security measures so that they can ensure their online privacy (Das, Dev &
Srinivasan, 2018). In this aspect the users must always use different types of passwords for
different types of online accounts. Also, logging out from these online platforms is also crucial.
Users of this online platform always need to logout from their account whenever their needs are
finished and it will ensure that online privacy of the users are being protected.
Privacy is a crucial aspect for each and every peoples as this is ensures the privacy of the
users where they are working in an online environment, but necessarily it is not important that all
the peoples will be having same level of privacy. For the VIP persons the level of privacy need
to be increased more as they might be carrying some crucial data with them (Herzig & Auerbach,
2017). This VIP persons can be the president or prime ministers of any nations and can be some
important officers of the nation. Generally this type of peoples always have some crucial
information which might need to be passed securely to others in an online environment. Due to
this reason the above kind of peoples must be having some extra level of privacy.
proper security measures are followed. All the personnel must be implementing a strong
password and a unique passwords for all of their online accounts. Also, many online platforms
provide two factor authentication for some extra security. This security measures can be used for
the protection of online privacy of the individual peoples.
Google, Facebook, iCloud, all are very much popular online platforms and currently used
by millions of users worldwide. Due to this fact it is crucial to ensure the online privacy of this
online platform users. In this case also, the users of this online platforms need to follow some of
the important security measures so that they can ensure their online privacy (Das, Dev &
Srinivasan, 2018). In this aspect the users must always use different types of passwords for
different types of online accounts. Also, logging out from these online platforms is also crucial.
Users of this online platform always need to logout from their account whenever their needs are
finished and it will ensure that online privacy of the users are being protected.
Privacy is a crucial aspect for each and every peoples as this is ensures the privacy of the
users where they are working in an online environment, but necessarily it is not important that all
the peoples will be having same level of privacy. For the VIP persons the level of privacy need
to be increased more as they might be carrying some crucial data with them (Herzig & Auerbach,
2017). This VIP persons can be the president or prime ministers of any nations and can be some
important officers of the nation. Generally this type of peoples always have some crucial
information which might need to be passed securely to others in an online environment. Due to
this reason the above kind of peoples must be having some extra level of privacy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT PROFESSION AND ETHICS
Online Privacy Breach Cases in Australia:
In the history of Australia there was various cases of online privacy breach and in this
aspect one of the breach case was the Coles’ flybuys and Woolworths Rewards breach case. In
this aspect privacy related issue occurred due to their loyalty program. In this loyalty program
both of the organizations launched their loyalty card and basically the main aim of this card was
collecting shopping behavioural data of the users. But both of the organizations used this data
unethically as this data was shared by them to the other organizations in the foreign counties for
which they were gaining organizational benefits. As both of the organizations were sharing the
shopping behavioural data of the customer online privacy of the peoples got hampered (Aloysius
et al., 2018). This case was identified later and legal steps were taken against those organizations
as per the Privacy Act 1988. In this aspect it has been assessed that as the overall nature of the
online privacy breach cases is increasing it is important that the legislators must pass some new
types of law for controlling this online privacy breach cases. In this aspect it has been also
assessed that many of the users are not so much aware about their online privacy cases and they
does not bother about that. It happens as the peoples does not know how most if the
organizations collect their data and how this data collection can create problem for them. Due to
this reason proper awareness must be created among the peoples so that they becomes careful
about the fact that how data is being collected from them.
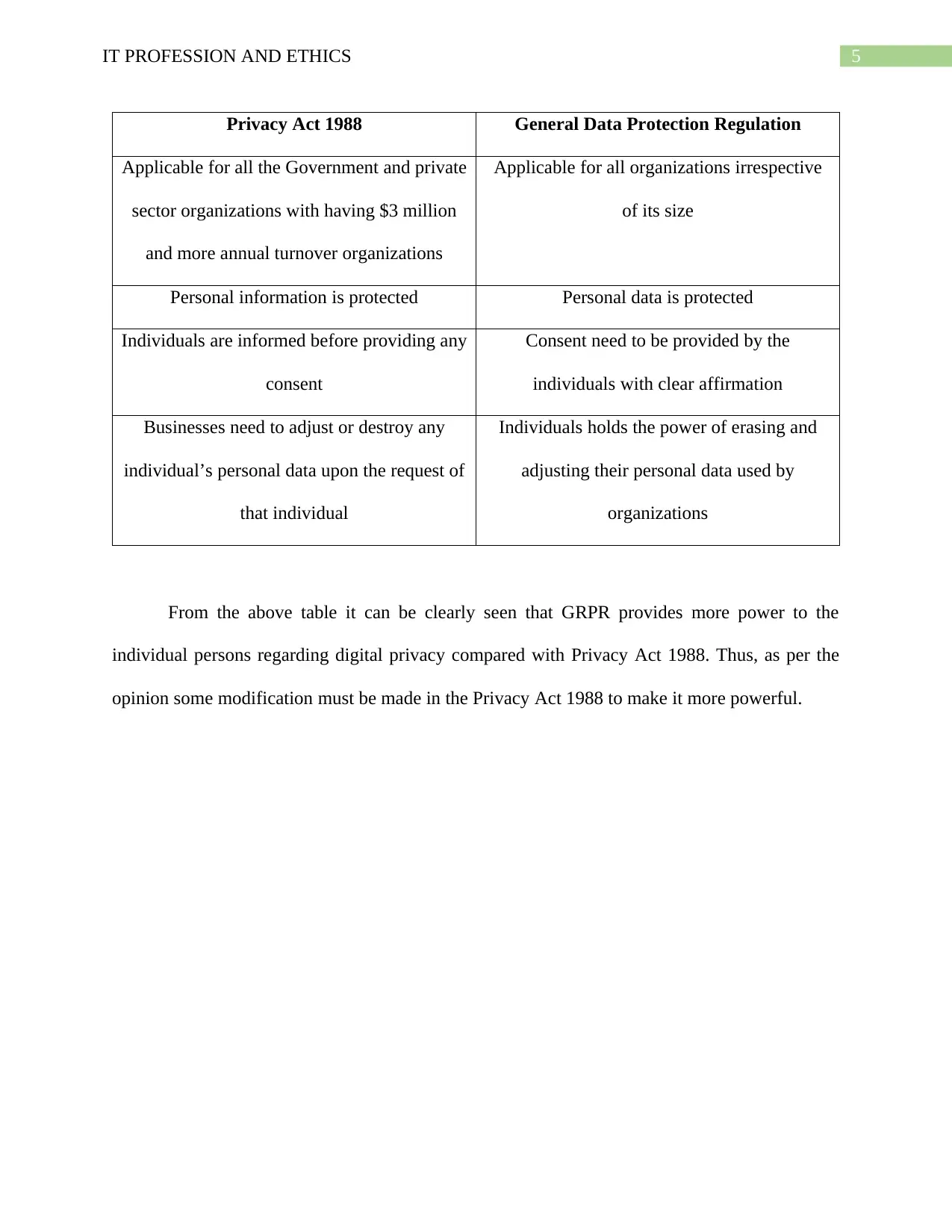
In Australia all the digital privacy of the users are regulated by the Privacy Act 1988
while in Europe this digital privacy of the users are regulated by the General Data Protection
Regulation or the GDPR (Albrecht, 2016). There are some important differences and similarities
among the Privacy Act 1988 and GDPR. Following table demonstrates comparison between
Privacy Act 1988 and GDPR.
Online Privacy Breach Cases in Australia:
In the history of Australia there was various cases of online privacy breach and in this
aspect one of the breach case was the Coles’ flybuys and Woolworths Rewards breach case. In
this aspect privacy related issue occurred due to their loyalty program. In this loyalty program
both of the organizations launched their loyalty card and basically the main aim of this card was
collecting shopping behavioural data of the users. But both of the organizations used this data
unethically as this data was shared by them to the other organizations in the foreign counties for
which they were gaining organizational benefits. As both of the organizations were sharing the
shopping behavioural data of the customer online privacy of the peoples got hampered (Aloysius
et al., 2018). This case was identified later and legal steps were taken against those organizations
as per the Privacy Act 1988. In this aspect it has been assessed that as the overall nature of the
online privacy breach cases is increasing it is important that the legislators must pass some new
types of law for controlling this online privacy breach cases. In this aspect it has been also
assessed that many of the users are not so much aware about their online privacy cases and they
does not bother about that. It happens as the peoples does not know how most if the
organizations collect their data and how this data collection can create problem for them. Due to
this reason proper awareness must be created among the peoples so that they becomes careful
about the fact that how data is being collected from them.
In Australia all the digital privacy of the users are regulated by the Privacy Act 1988
while in Europe this digital privacy of the users are regulated by the General Data Protection
Regulation or the GDPR (Albrecht, 2016). There are some important differences and similarities
among the Privacy Act 1988 and GDPR. Following table demonstrates comparison between
Privacy Act 1988 and GDPR.
5IT PROFESSION AND ETHICS
Privacy Act 1988 General Data Protection Regulation
Applicable for all the Government and private
sector organizations with having $3 million
and more annual turnover organizations
Applicable for all organizations irrespective
of its size
Personal information is protected Personal data is protected
Individuals are informed before providing any
consent
Consent need to be provided by the
individuals with clear affirmation
Businesses need to adjust or destroy any
individual’s personal data upon the request of
that individual
Individuals holds the power of erasing and
adjusting their personal data used by
organizations
From the above table it can be clearly seen that GRPR provides more power to the
individual persons regarding digital privacy compared with Privacy Act 1988. Thus, as per the
opinion some modification must be made in the Privacy Act 1988 to make it more powerful.
Privacy Act 1988 General Data Protection Regulation
Applicable for all the Government and private
sector organizations with having $3 million
and more annual turnover organizations
Applicable for all organizations irrespective
of its size
Personal information is protected Personal data is protected
Individuals are informed before providing any
consent
Consent need to be provided by the
individuals with clear affirmation
Businesses need to adjust or destroy any
individual’s personal data upon the request of
that individual
Individuals holds the power of erasing and
adjusting their personal data used by
organizations
From the above table it can be clearly seen that GRPR provides more power to the
individual persons regarding digital privacy compared with Privacy Act 1988. Thus, as per the
opinion some modification must be made in the Privacy Act 1988 to make it more powerful.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT PROFESSION AND ETHICS
Conclusion:
Above discussion implies that digital privacy is important for the individuals so that they
can effectively protect their personal information. This essay has briefly discussed about the
digital privacy factors in Australia and why this is important for the individuals. This essay has
also discussed about the privacy related concern which the individuals are facing regarding the
digital materials. From this essay it has been also assessed that every users does not requires
same type of privacy. For the VIP persons the amount privacy need to be increased further as
they possesses crucial data. It has been also assessed that individuals also need to take
responsibility for protecting their own privacy. Also, form the essay it has been assessed that
legislators must be passing some new laws against the current situation regarding online privacy.
Conclusion:
Above discussion implies that digital privacy is important for the individuals so that they
can effectively protect their personal information. This essay has briefly discussed about the
digital privacy factors in Australia and why this is important for the individuals. This essay has
also discussed about the privacy related concern which the individuals are facing regarding the
digital materials. From this essay it has been also assessed that every users does not requires
same type of privacy. For the VIP persons the amount privacy need to be increased further as
they possesses crucial data. It has been also assessed that individuals also need to take
responsibility for protecting their own privacy. Also, form the essay it has been assessed that
legislators must be passing some new laws against the current situation regarding online privacy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT PROFESSION AND ETHICS
References:
Albrecht, J. P. (2016). How the GDPR will change the world. Eur. Data Prot. L. Rev., 2, 287.
Aloysius, J. A., Hoehle, H., Goodarzi, S., & Venkatesh, V. (2018). Big data initiatives in retail
environments: Linking service process perceptions to shopping outcomes. Annals of
operations research, 270(1-2), 25-51.
Bartsch, M., & Dienlin, T. (2016). Control your Facebook: An analysis of online privacy
literacy. Computers in Human Behavior, 56, 147-154.
Baruh, L., Secinti, E., & Cemalcilar, Z. (2017). Online privacy concerns and privacy
management: A meta-analytical review. Journal of Communication, 67(1), 26-53.
Das, S., Dev, J., & Srinivasan, K. (2018, October). Modularity is the Key A New Approach to
Social Media Privacy Policies. In Proceedings of the 7th Mexican Conference on
Human-Computer Interaction (p. 13). ACM.
Herzig, S. J., & Auerbach, A. (2017). Perceived safety and value of inpatient “very important
person” services. Journal of hospital medicine, 12(3).
Hwang, Y. H. (2015, April). Iot security & privacy: threats and challenges. In Proceedings of the
1st ACM Workshop on IoT Privacy, Trust, and Security (pp. 1-1). ACM.
Salimian, M. H., Reilly, D., Brooks, S., & MacKay, B. (2016, November). Physical-digital
privacy interfaces for mixed reality collaboration: an exploratory study. In Proceedings
of the 2016 ACM International Conference on Interactive Surfaces and Spaces (pp. 261-
270). ACM.
Watts, D., & Casanovas, P. (2018). Privacy and Data Protection in Australia: a Critical overview.
References:
Albrecht, J. P. (2016). How the GDPR will change the world. Eur. Data Prot. L. Rev., 2, 287.
Aloysius, J. A., Hoehle, H., Goodarzi, S., & Venkatesh, V. (2018). Big data initiatives in retail
environments: Linking service process perceptions to shopping outcomes. Annals of
operations research, 270(1-2), 25-51.
Bartsch, M., & Dienlin, T. (2016). Control your Facebook: An analysis of online privacy
literacy. Computers in Human Behavior, 56, 147-154.
Baruh, L., Secinti, E., & Cemalcilar, Z. (2017). Online privacy concerns and privacy
management: A meta-analytical review. Journal of Communication, 67(1), 26-53.
Das, S., Dev, J., & Srinivasan, K. (2018, October). Modularity is the Key A New Approach to
Social Media Privacy Policies. In Proceedings of the 7th Mexican Conference on
Human-Computer Interaction (p. 13). ACM.
Herzig, S. J., & Auerbach, A. (2017). Perceived safety and value of inpatient “very important
person” services. Journal of hospital medicine, 12(3).
Hwang, Y. H. (2015, April). Iot security & privacy: threats and challenges. In Proceedings of the
1st ACM Workshop on IoT Privacy, Trust, and Security (pp. 1-1). ACM.
Salimian, M. H., Reilly, D., Brooks, S., & MacKay, B. (2016, November). Physical-digital
privacy interfaces for mixed reality collaboration: an exploratory study. In Proceedings
of the 2016 ACM International Conference on Interactive Surfaces and Spaces (pp. 261-
270). ACM.
Watts, D., & Casanovas, P. (2018). Privacy and Data Protection in Australia: a Critical overview.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
![NIT2201 - Online Privacy: An Analytical Essay - [University Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fgc%2F0656cbdd520f46bb97c676d8d876831a.jpg&w=256&q=75)




