Deakin University: ALC303 Report on Digital Surveillance and Privacy
VerifiedAdded on 2022/12/20
|9
|1916
|37
Report
AI Summary
This report delves into the critical issues of digital surveillance and information privacy, particularly within the context of university students' social media usage. The introduction establishes the scope, highlighting the growing concerns surrounding surveillance abuse and the collection of personal data. The research question investigates the importance of social media monitoring and privacy among young adults, with hypotheses exploring the level of awareness and proactive measures taken by tertiary-educated students. A comprehensive literature review examines the threats to privacy posed by surveillance, the value of collected data, and the socio-economic dimensions of digital surveillance. The research methodology emphasizes the importance of understanding public reactions to surveillance techniques, including biometric surveillance and data collection methods. The results and discussion section analyzes the impact of surveillance on fundamental freedoms, the growing discussion around encryption, and the need for accountability. It also considers the role of intermediaries and filters in data collection and the use of methods like "scrambling" and "blurring" to protect privacy. The conclusion summarizes the key findings, emphasizing the need for clear regulations, ethical guidelines, and a balance between surveillance and individual rights. The report includes figures illustrating smartphone and internet usage, perceptions of civic activities, and gender distribution within the study, along with a list of references.

University
Semester
Digital Surveillance and Information
Privacy Introduction
Student ID
Student Name
Submission Date
1
Semester
Digital Surveillance and Information
Privacy Introduction
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction...................................................................................................................................3
2. Research Question and Hypothesis................................................................................................3
3. Literature review...........................................................................................................................3
4. Research Methodology..................................................................................................................4
5. Result and Discussion....................................................................................................................5
6. Conclusion.....................................................................................................................................6
7. Appendix.......................................................................................................................................7
References.........................................................................................................................................9
2
1. Introduction...................................................................................................................................3
2. Research Question and Hypothesis................................................................................................3
3. Literature review...........................................................................................................................3
4. Research Methodology..................................................................................................................4
5. Result and Discussion....................................................................................................................5
6. Conclusion.....................................................................................................................................6
7. Appendix.......................................................................................................................................7
References.........................................................................................................................................9
2

1. Introduction
Surveillance is simply the method of monitoring and observation. Surveillance
abuse is the use of surveillance methods or technology to monitor the activity of an individual
or group of individuals in a way which violates the social norms or laws of a society.
Nowadays, surveillance abuse has become more far-flung through corporate and industrial
use of private security firms which may be used to carry out industrial espionage, monitor
competitors, and target trade union leaders. There is a strong group of individuals and people
who believe that these methods and technics shall be used in monitoring and observing for
unwanted activities, crimes, terrorism etc. But opposing these beliefs is another side of
people and organizations that believe that these will be abused and will be used in controlling
and misuse of data and information so collected.
Data collected through various routes may be misused and can be passed on to some
elements of the society which may be harmful to the individual or the organization. Data is
stored and collected from various sources and modes. These data is collected cheaply and
also stored cheaply. Understanding these should be easy and analyzing also is easy with so
many applications and methods availability. Government policies and Authorized sectors
may make use of data so collected from the surveillance nodes and make it worthwhile for
projects that may be irrelevant at times.
2. Research Question and Hypothesis
1. RQ: What is the importance of Social Media monitoring and its privacy for
people of young age?
2. H1: A High level of self-realization (DV) about Individual Privacy and
Monitoring motives is present among the Tertiary educated university students
and they will keep an eye for this on the Social Media.
3. H0:A Low level of self-realization (DV) about Individual Privacy and Monitoring
motives is present among the Tertiary educated university students and they will
be negligent to these while accessing Social Media (Andrews, 2016).
3. Literature review
Privacy today faces growing threats from a growing surveillance apparatus that is
often justified in the name of national security. Use of tools where information and Data
collected for a particular interest is stored and this data becomes valuable to authorities and
3
Surveillance is simply the method of monitoring and observation. Surveillance
abuse is the use of surveillance methods or technology to monitor the activity of an individual
or group of individuals in a way which violates the social norms or laws of a society.
Nowadays, surveillance abuse has become more far-flung through corporate and industrial
use of private security firms which may be used to carry out industrial espionage, monitor
competitors, and target trade union leaders. There is a strong group of individuals and people
who believe that these methods and technics shall be used in monitoring and observing for
unwanted activities, crimes, terrorism etc. But opposing these beliefs is another side of
people and organizations that believe that these will be abused and will be used in controlling
and misuse of data and information so collected.
Data collected through various routes may be misused and can be passed on to some
elements of the society which may be harmful to the individual or the organization. Data is
stored and collected from various sources and modes. These data is collected cheaply and
also stored cheaply. Understanding these should be easy and analyzing also is easy with so
many applications and methods availability. Government policies and Authorized sectors
may make use of data so collected from the surveillance nodes and make it worthwhile for
projects that may be irrelevant at times.
2. Research Question and Hypothesis
1. RQ: What is the importance of Social Media monitoring and its privacy for
people of young age?
2. H1: A High level of self-realization (DV) about Individual Privacy and
Monitoring motives is present among the Tertiary educated university students
and they will keep an eye for this on the Social Media.
3. H0:A Low level of self-realization (DV) about Individual Privacy and Monitoring
motives is present among the Tertiary educated university students and they will
be negligent to these while accessing Social Media (Andrews, 2016).
3. Literature review
Privacy today faces growing threats from a growing surveillance apparatus that is
often justified in the name of national security. Use of tools where information and Data
collected for a particular interest is stored and this data becomes valuable to authorities and
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

agencies. We shall discuss about this aspect of Surveillance and how the dynamics between
Individuals Privacy and Security works out.
The government’s collection of this sensitive information is itself an invasion of
privacy. But its use of this data is also rife with abuse. Innocuous data is fed into bloated
watch lists and this remains there for unmentioned time. Use can be made of tools where
mass data is collected and processed for activities. These are more than what it was initially
meant to be used for. Thus it becomes a fight between the risk of having the data and its
purpose. There are political and socio-economic dimensions of digital surveillance. Human
rights defenders and political activists are frequently targeted for surveillance (Carradini,
2019). It questions about the use of methods and processes used in surveillance and analyses
the assessment of modern technologies that are used for this purpose. Also the topic of newer
and advanced technics used in collection of information and what are the steps being taken
for regularizing and making policies for this. This should take into account the Individual
rights and the privacy rights and without affecting the ethical entitlement (Hickson, 2017).
4. Research Methodology
Understanding the importance of the Data monitoring and individual information is
important. There are extensive uncertainties regarding public reactions to the measures being
taken. The use of advanced monitoring techniques and the scale of data collected through
various nodes and points. These may include as simple as filling up a registration form
online, or taking a picture at a private photo shop, CCTV footages , emails over internet, the
amount of time spent on web, Mobile usage and calls, visits to various places and location
data and such types of activities with the information being gathered and stored. One of the
most widely used methods of data monitoring used world-wide is Biometric surveillance is a
technology that measures and analyses human physical and/or behavioral characteristics for
authentication, identification, or screening purposes (Porter, 2017).
Individuals, People and Organizations are under constant monitoring and feel they are
controlled by the authorities and institutes. Making them to understand the importance of
monitoring and also the concerns of identifying the terrorist activities and unlawful
enforcements is vital. This was the main aim of getting the surveillance system in place and
also not to disclose the information and private data. Large amount of Data collection,
sorting, storing, analyzing and extracting information became possible. Networks, LAN’s,
WAN’s and finally the Web. It became very easy to transport and transmit large amount of
information and data of individuals and groups. These were without any knowledge of these
people and individuals. Data so gathered from various sources and nodes was joined together
4
Individuals Privacy and Security works out.
The government’s collection of this sensitive information is itself an invasion of
privacy. But its use of this data is also rife with abuse. Innocuous data is fed into bloated
watch lists and this remains there for unmentioned time. Use can be made of tools where
mass data is collected and processed for activities. These are more than what it was initially
meant to be used for. Thus it becomes a fight between the risk of having the data and its
purpose. There are political and socio-economic dimensions of digital surveillance. Human
rights defenders and political activists are frequently targeted for surveillance (Carradini,
2019). It questions about the use of methods and processes used in surveillance and analyses
the assessment of modern technologies that are used for this purpose. Also the topic of newer
and advanced technics used in collection of information and what are the steps being taken
for regularizing and making policies for this. This should take into account the Individual
rights and the privacy rights and without affecting the ethical entitlement (Hickson, 2017).
4. Research Methodology
Understanding the importance of the Data monitoring and individual information is
important. There are extensive uncertainties regarding public reactions to the measures being
taken. The use of advanced monitoring techniques and the scale of data collected through
various nodes and points. These may include as simple as filling up a registration form
online, or taking a picture at a private photo shop, CCTV footages , emails over internet, the
amount of time spent on web, Mobile usage and calls, visits to various places and location
data and such types of activities with the information being gathered and stored. One of the
most widely used methods of data monitoring used world-wide is Biometric surveillance is a
technology that measures and analyses human physical and/or behavioral characteristics for
authentication, identification, or screening purposes (Porter, 2017).
Individuals, People and Organizations are under constant monitoring and feel they are
controlled by the authorities and institutes. Making them to understand the importance of
monitoring and also the concerns of identifying the terrorist activities and unlawful
enforcements is vital. This was the main aim of getting the surveillance system in place and
also not to disclose the information and private data. Large amount of Data collection,
sorting, storing, analyzing and extracting information became possible. Networks, LAN’s,
WAN’s and finally the Web. It became very easy to transport and transmit large amount of
information and data of individuals and groups. These were without any knowledge of these
people and individuals. Data so gathered from various sources and nodes was joined together
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and analyzed to give a much bigger, better and most importantly Informative image of that
particular individual.
5. Result and Discussion
Security and Digital Privacy issues are a growing concern, especially as
the internet and new technologies have made personal information more accessible and easier
to collect access and repurpose or manipulate. When we talk about surveillance, it often
follows that we speak of the importance of privacy, of being free from observation or
disturbance, from public attention. The violation of privacy is apparent: indiscriminate, mass
surveillance goes against the basic, fundamental right to privacy that our predecessors fought
for. The negative effects of surveillance on the fundamental freedoms of expression and
association may be less evident in an era of ubiquitous digital connection, but are no less
important. Similarly, the public discussion around the use of encryption is also growing, as is
the funding and development of privacy-enhancing technologies. Also there has been an
increased funding toward tools that can be used to thwart surveillance attempts. Given the
complex nature of digital spying, data surveillance and monitoring, the interlinked set of
rights it affects, this is imperative. Ending mass surveillance requires consideration not only
of its effect on privacy, but its impact on expression and association as well. The
Authorization needs to increase accountability and responsibility, infuse the checks and
balances to exercise these surveillance powers. New technics have to be tested on the grounds
of reasonableness, fairness, proportionality and judicious exercise of powers. Another
prospect of this is the kind of electronic communications and data sharing on various media
platforms is prevalent today. This can be intercepted/ monitored and misused as there is no
provision for confidentiality and privacy.
They must be account of how the digital technologies are implicated in the problems
of opacity, arbitrariness and impunity that will be the rules and current practices of
monitoring of data. Intermediaries and filters should be set up at various collection centres
and servers.
The oversight of algorithms and programs should be employed that will hide the
identity of individuals/ groups and the digital evidence and data collection should be specific
for that technological applications. A popular method called “Scrambling” can be used to
encrypt the collected and stored data which can be opened by using special keys and
programs and the authorization for that will only be the appropriate person or organisation.
Reducing delicate data, images, speech, videos from certain or all data so collected can be
5
particular individual.
5. Result and Discussion
Security and Digital Privacy issues are a growing concern, especially as
the internet and new technologies have made personal information more accessible and easier
to collect access and repurpose or manipulate. When we talk about surveillance, it often
follows that we speak of the importance of privacy, of being free from observation or
disturbance, from public attention. The violation of privacy is apparent: indiscriminate, mass
surveillance goes against the basic, fundamental right to privacy that our predecessors fought
for. The negative effects of surveillance on the fundamental freedoms of expression and
association may be less evident in an era of ubiquitous digital connection, but are no less
important. Similarly, the public discussion around the use of encryption is also growing, as is
the funding and development of privacy-enhancing technologies. Also there has been an
increased funding toward tools that can be used to thwart surveillance attempts. Given the
complex nature of digital spying, data surveillance and monitoring, the interlinked set of
rights it affects, this is imperative. Ending mass surveillance requires consideration not only
of its effect on privacy, but its impact on expression and association as well. The
Authorization needs to increase accountability and responsibility, infuse the checks and
balances to exercise these surveillance powers. New technics have to be tested on the grounds
of reasonableness, fairness, proportionality and judicious exercise of powers. Another
prospect of this is the kind of electronic communications and data sharing on various media
platforms is prevalent today. This can be intercepted/ monitored and misused as there is no
provision for confidentiality and privacy.
They must be account of how the digital technologies are implicated in the problems
of opacity, arbitrariness and impunity that will be the rules and current practices of
monitoring of data. Intermediaries and filters should be set up at various collection centres
and servers.
The oversight of algorithms and programs should be employed that will hide the
identity of individuals/ groups and the digital evidence and data collection should be specific
for that technological applications. A popular method called “Scrambling” can be used to
encrypt the collected and stored data which can be opened by using special keys and
programs and the authorization for that will only be the appropriate person or organisation.
Reducing delicate data, images, speech, videos from certain or all data so collected can be
5
carried out and same can be replaced by safer models and replicates which is called as
“Abstractions”. Using the often used method of “Blurring” or more technical term known as
“Pixilation” where the images or the videos are made unclear so that they are not identifiable.
Time period of the data so collected and stored should be made clear and identified from the
authorized institutes. If there is a reasonable expectation of privacy, then permission
or legal authority must be sought to record or listen in on conversations using electronic
devices. The other side of this discussion is access of these data from the individual’s point of
view. Can the individual and the public in general be allowed to watch their own data? The
logical answer is yes as they are will be watching their own data and some countries like
Canada, France are allowing these rights to individuals.
6. Conclusion
So finally we come to the last part of our discussion. The question remains in our
mind is the amount of Surveillance and the Individual Right to Privacy. Digital Environment
and Data collection has become easier, less affordable, wide spread and advanced. A
company, an Organisation, Authorized Institutes or even an Individual can make use of these
and start collecting Data. Video monitoring and CCTV usage has to follow certain set of rules
and regulations. They have to follow Guidelines that not only focus on data surveillance in
public places but also to the private sector. These again leads to the doubt as to whether the
Private Sector are obliged to follow these rules for surveillance and monitoring. These
become a wider issue and should be addressed by individual governments and legal
authorities so that the rules are on an even standard platform and are applicable to all,
whether in public area or a private organisation, and they comply with a certain set of Rules.
6
“Abstractions”. Using the often used method of “Blurring” or more technical term known as
“Pixilation” where the images or the videos are made unclear so that they are not identifiable.
Time period of the data so collected and stored should be made clear and identified from the
authorized institutes. If there is a reasonable expectation of privacy, then permission
or legal authority must be sought to record or listen in on conversations using electronic
devices. The other side of this discussion is access of these data from the individual’s point of
view. Can the individual and the public in general be allowed to watch their own data? The
logical answer is yes as they are will be watching their own data and some countries like
Canada, France are allowing these rights to individuals.
6. Conclusion
So finally we come to the last part of our discussion. The question remains in our
mind is the amount of Surveillance and the Individual Right to Privacy. Digital Environment
and Data collection has become easier, less affordable, wide spread and advanced. A
company, an Organisation, Authorized Institutes or even an Individual can make use of these
and start collecting Data. Video monitoring and CCTV usage has to follow certain set of rules
and regulations. They have to follow Guidelines that not only focus on data surveillance in
public places but also to the private sector. These again leads to the doubt as to whether the
Private Sector are obliged to follow these rules for surveillance and monitoring. These
become a wider issue and should be addressed by individual governments and legal
authorities so that the rules are on an even standard platform and are applicable to all,
whether in public area or a private organisation, and they comply with a certain set of Rules.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7. Appendix
Figure 1: Smart Phone
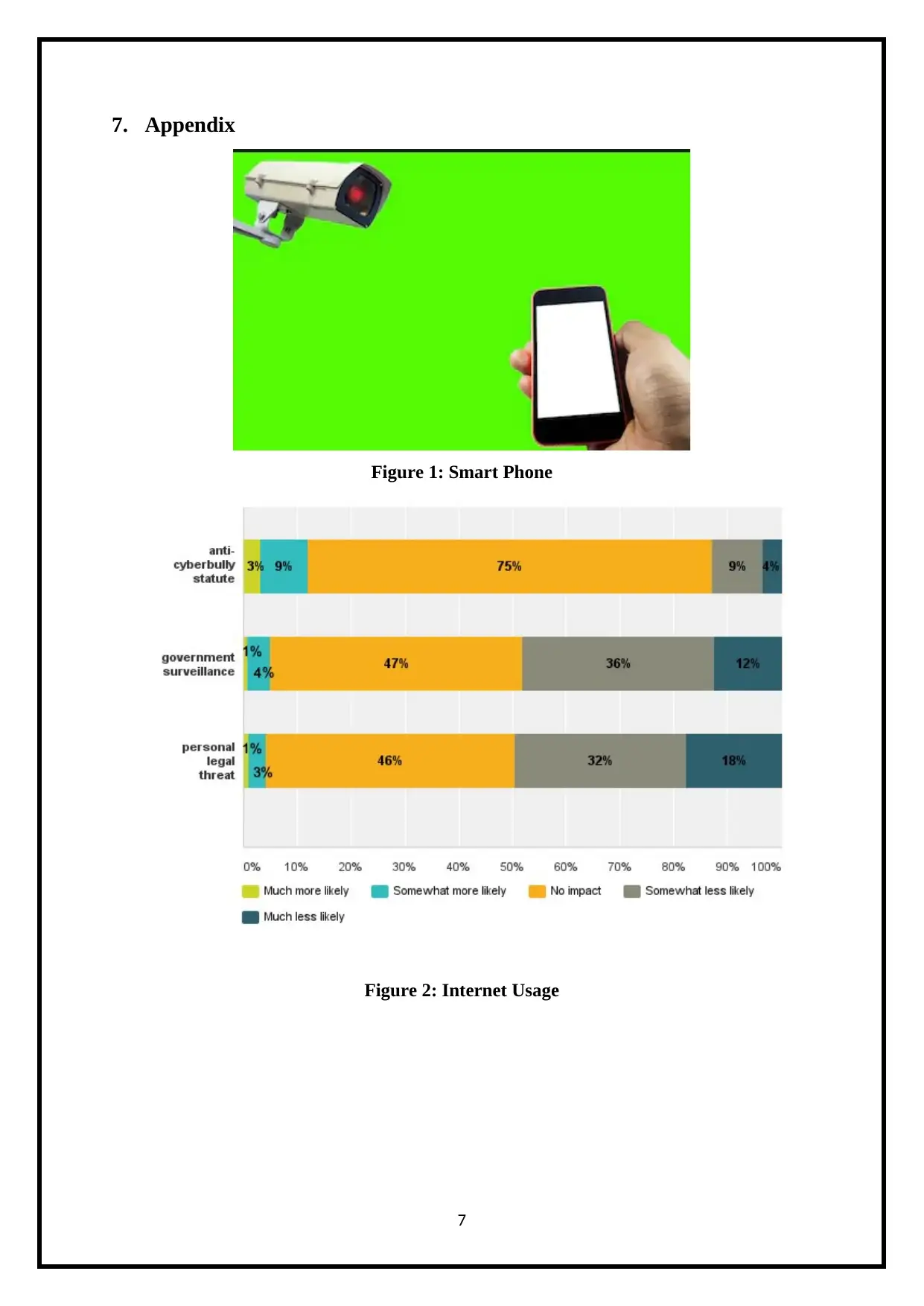
Figure 2: Internet Usage
7
Figure 1: Smart Phone
Figure 2: Internet Usage
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
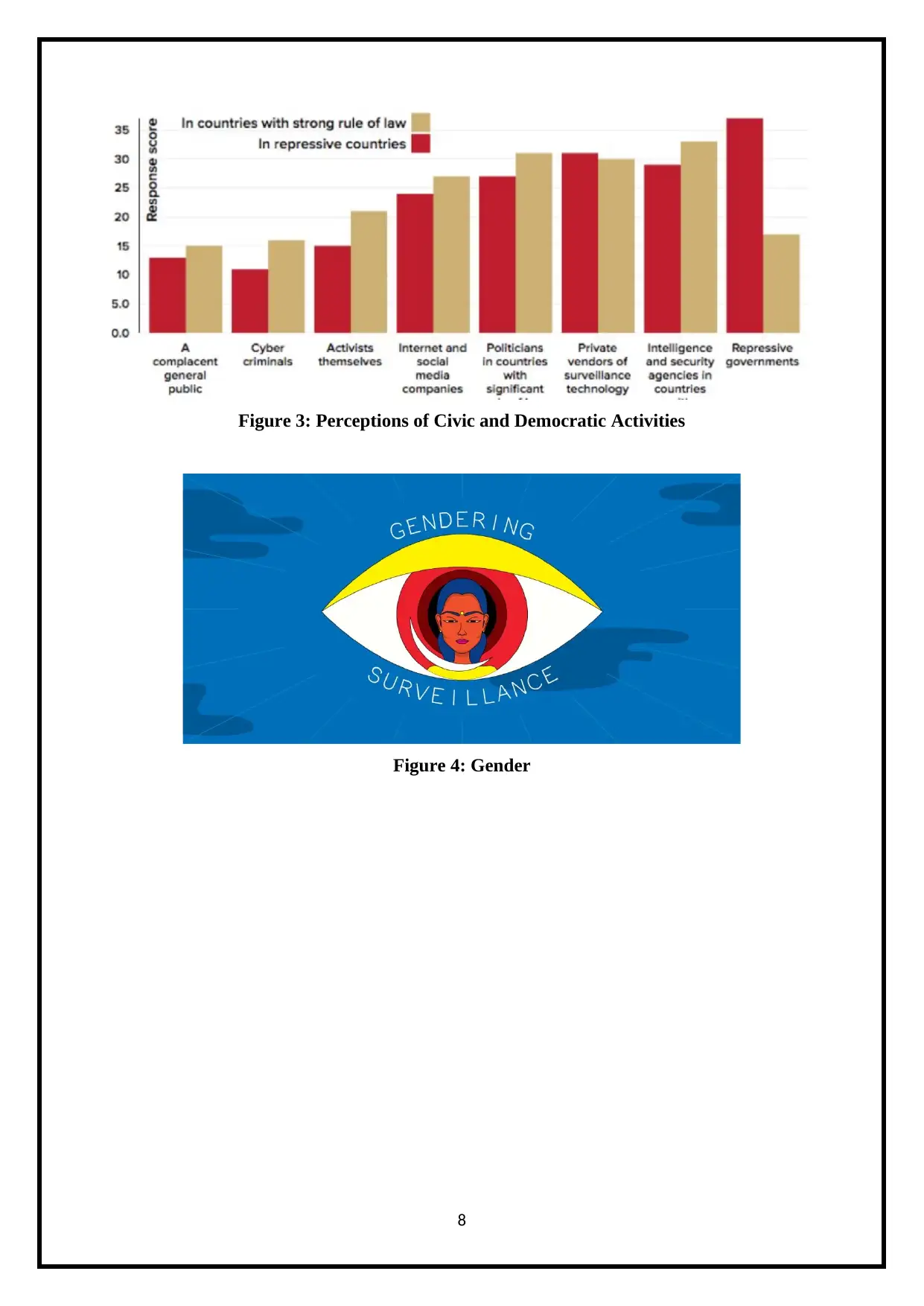
Figure 3: Perceptions of Civic and Democratic Activities
Figure 4: Gender
8
Figure 4: Gender
8

References
Andrews, D. (2016). Making the Familiar Strange. Business and Professional
Communication Quarterly, 79(1), pp.6-27.
Carradini, S. (2019). Artist Communication: An Interdisciplinary Business and Professional
Communication Course. Business and Professional Communication Quarterly,
p.232949061982611.
Hickson, M. (2017). Jim McCroskey: Professional Mentor. Communication Research
Reports, 35(1), pp.85-89.
Porter, J. (2017). Professional Communication as Phatic: From Classical Eunoia to Personal
Artificial Intelligence. Business and Professional Communication Quarterly, 80(2), pp.174-
193.
9
Andrews, D. (2016). Making the Familiar Strange. Business and Professional
Communication Quarterly, 79(1), pp.6-27.
Carradini, S. (2019). Artist Communication: An Interdisciplinary Business and Professional
Communication Course. Business and Professional Communication Quarterly,
p.232949061982611.
Hickson, M. (2017). Jim McCroskey: Professional Mentor. Communication Research
Reports, 35(1), pp.85-89.
Porter, J. (2017). Professional Communication as Phatic: From Classical Eunoia to Personal
Artificial Intelligence. Business and Professional Communication Quarterly, 80(2), pp.174-
193.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





