Bank Risk Assessment: Digital Security Risks and the CISO Role
VerifiedAdded on 2023/03/23
|10
|1940
|69
Report
AI Summary
This report presents a comprehensive risk assessment for a bank, focusing on identifying and prioritizing digital security risks. It utilizes a risk assessment matrix to evaluate potential threats like unencrypted data, malware, and insider threats, along with suggesting mitigation strategies. The report also explores the critical role of a Chief Information Security Officer (CISO) in safeguarding the bank's information assets. It provides recommendations for appointing a qualified CISO, emphasizing the importance of defining requirements, assessing qualifications and experience, evaluating behavioral traits, communication skills, and leadership abilities. The report highlights the CISO's responsibility in establishing and maintaining a robust security program to protect the enterprise from IT-related risks. Desklib offers similar solved assignments and study resources for students.

P a g e | 0
Risk Management
Risk Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P a g e | 1
Executive Summary
The aim of this report is to prepare a risk register for a bank to identify different risks
which affect the operations of the banks. The first part of this report used a Risk Assessment
Matrix in order to identify and prioritise different risks along with an evaluation of policies
which can be adopted by the bank to mitigate these risks. In the second part of this report,
of the role of a Chief Information Security Officer is evaluated and recommendations are
given to for the appointment of a Chief Information Security Officer in an organisation.
Executive Summary
The aim of this report is to prepare a risk register for a bank to identify different risks
which affect the operations of the banks. The first part of this report used a Risk Assessment
Matrix in order to identify and prioritise different risks along with an evaluation of policies
which can be adopted by the bank to mitigate these risks. In the second part of this report,
of the role of a Chief Information Security Officer is evaluated and recommendations are
given to for the appointment of a Chief Information Security Officer in an organisation.

P a g e | 2
Table of Contents
Part One.....................................................................................................................................3
Identification of Risks.............................................................................................................3
Risk Assessment Matrix..........................................................................................................3
Impact of the Risks.................................................................................................................4
Part Two.....................................................................................................................................6
Recommendations on the Appointment of a CISO................................................................6
References..................................................................................................................................9
Table of Contents
Part One.....................................................................................................................................3
Identification of Risks.............................................................................................................3
Risk Assessment Matrix..........................................................................................................3
Impact of the Risks.................................................................................................................4
Part Two.....................................................................................................................................6
Recommendations on the Appointment of a CISO................................................................6
References..................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
P a g e | 3
Part One
Identification of Risks
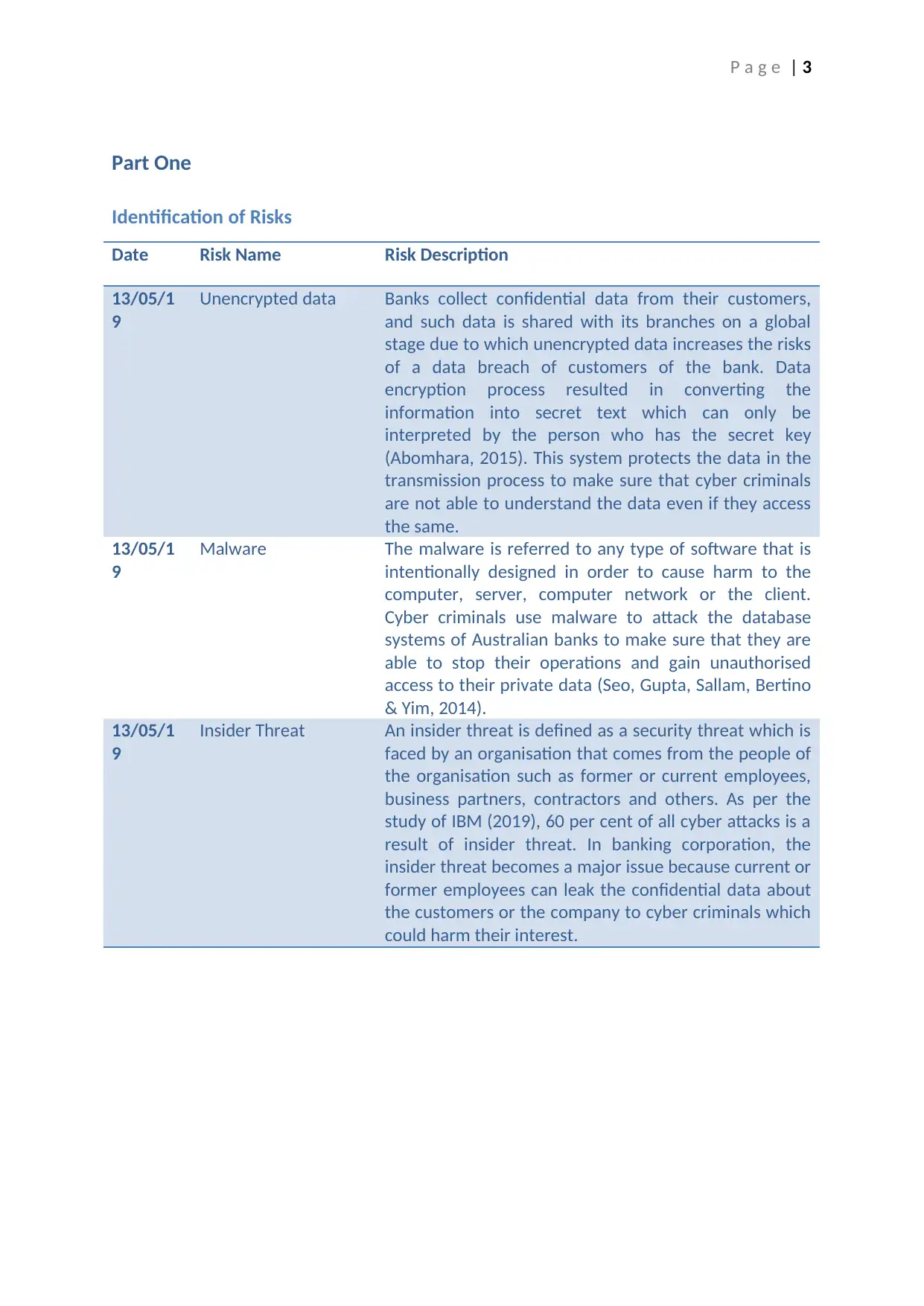
Date Risk Name Risk Description
13/05/1
9
Unencrypted data Banks collect confidential data from their customers,
and such data is shared with its branches on a global
stage due to which unencrypted data increases the risks
of a data breach of customers of the bank. Data
encryption process resulted in converting the
information into secret text which can only be
interpreted by the person who has the secret key
(Abomhara, 2015). This system protects the data in the
transmission process to make sure that cyber criminals
are not able to understand the data even if they access
the same.
13/05/1
9
Malware The malware is referred to any type of software that is
intentionally designed in order to cause harm to the
computer, server, computer network or the client.
Cyber criminals use malware to attack the database
systems of Australian banks to make sure that they are
able to stop their operations and gain unauthorised
access to their private data (Seo, Gupta, Sallam, Bertino
& Yim, 2014).
13/05/1
9
Insider Threat An insider threat is defined as a security threat which is
faced by an organisation that comes from the people of
the organisation such as former or current employees,
business partners, contractors and others. As per the
study of IBM (2019), 60 per cent of all cyber attacks is a
result of insider threat. In banking corporation, the
insider threat becomes a major issue because current or
former employees can leak the confidential data about
the customers or the company to cyber criminals which
could harm their interest.
Part One
Identification of Risks
Date Risk Name Risk Description
13/05/1
9
Unencrypted data Banks collect confidential data from their customers,
and such data is shared with its branches on a global
stage due to which unencrypted data increases the risks
of a data breach of customers of the bank. Data
encryption process resulted in converting the
information into secret text which can only be
interpreted by the person who has the secret key
(Abomhara, 2015). This system protects the data in the
transmission process to make sure that cyber criminals
are not able to understand the data even if they access
the same.
13/05/1
9
Malware The malware is referred to any type of software that is
intentionally designed in order to cause harm to the
computer, server, computer network or the client.
Cyber criminals use malware to attack the database
systems of Australian banks to make sure that they are
able to stop their operations and gain unauthorised
access to their private data (Seo, Gupta, Sallam, Bertino
& Yim, 2014).
13/05/1
9
Insider Threat An insider threat is defined as a security threat which is
faced by an organisation that comes from the people of
the organisation such as former or current employees,
business partners, contractors and others. As per the
study of IBM (2019), 60 per cent of all cyber attacks is a
result of insider threat. In banking corporation, the
insider threat becomes a major issue because current or
former employees can leak the confidential data about
the customers or the company to cyber criminals which
could harm their interest.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P a g e | 4
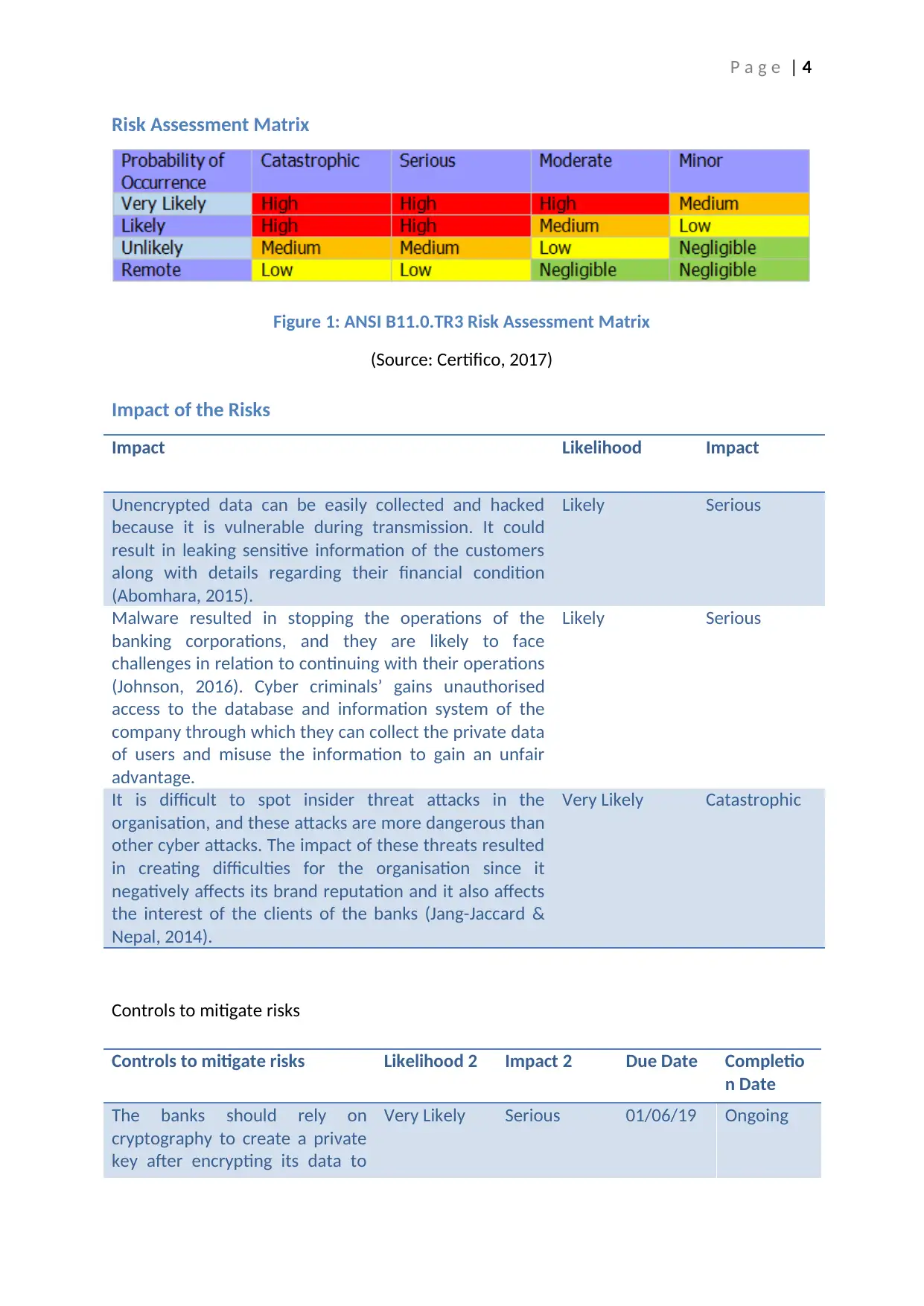
Risk Assessment Matrix
Figure 1: ANSI B11.0.TR3 Risk Assessment Matrix
(Source: Certifico, 2017)
Impact of the Risks
Impact Likelihood Impact
Unencrypted data can be easily collected and hacked
because it is vulnerable during transmission. It could
result in leaking sensitive information of the customers
along with details regarding their financial condition
(Abomhara, 2015).
Likely Serious
Malware resulted in stopping the operations of the
banking corporations, and they are likely to face
challenges in relation to continuing with their operations
(Johnson, 2016). Cyber criminals’ gains unauthorised
access to the database and information system of the
company through which they can collect the private data
of users and misuse the information to gain an unfair
advantage.
Likely Serious
It is difficult to spot insider threat attacks in the
organisation, and these attacks are more dangerous than
other cyber attacks. The impact of these threats resulted
in creating difficulties for the organisation since it
negatively affects its brand reputation and it also affects
the interest of the clients of the banks (Jang-Jaccard &
Nepal, 2014).
Very Likely Catastrophic
Controls to mitigate risks
Controls to mitigate risks Likelihood 2 Impact 2 Due Date Completio
n Date
The banks should rely on
cryptography to create a private
key after encrypting its data to
Very Likely Serious 01/06/19 Ongoing
Risk Assessment Matrix
Figure 1: ANSI B11.0.TR3 Risk Assessment Matrix
(Source: Certifico, 2017)
Impact of the Risks
Impact Likelihood Impact
Unencrypted data can be easily collected and hacked
because it is vulnerable during transmission. It could
result in leaking sensitive information of the customers
along with details regarding their financial condition
(Abomhara, 2015).
Likely Serious
Malware resulted in stopping the operations of the
banking corporations, and they are likely to face
challenges in relation to continuing with their operations
(Johnson, 2016). Cyber criminals’ gains unauthorised
access to the database and information system of the
company through which they can collect the private data
of users and misuse the information to gain an unfair
advantage.
Likely Serious
It is difficult to spot insider threat attacks in the
organisation, and these attacks are more dangerous than
other cyber attacks. The impact of these threats resulted
in creating difficulties for the organisation since it
negatively affects its brand reputation and it also affects
the interest of the clients of the banks (Jang-Jaccard &
Nepal, 2014).
Very Likely Catastrophic
Controls to mitigate risks
Controls to mitigate risks Likelihood 2 Impact 2 Due Date Completio
n Date
The banks should rely on
cryptography to create a private
key after encrypting its data to
Very Likely Serious 01/06/19 Ongoing
P a g e | 5
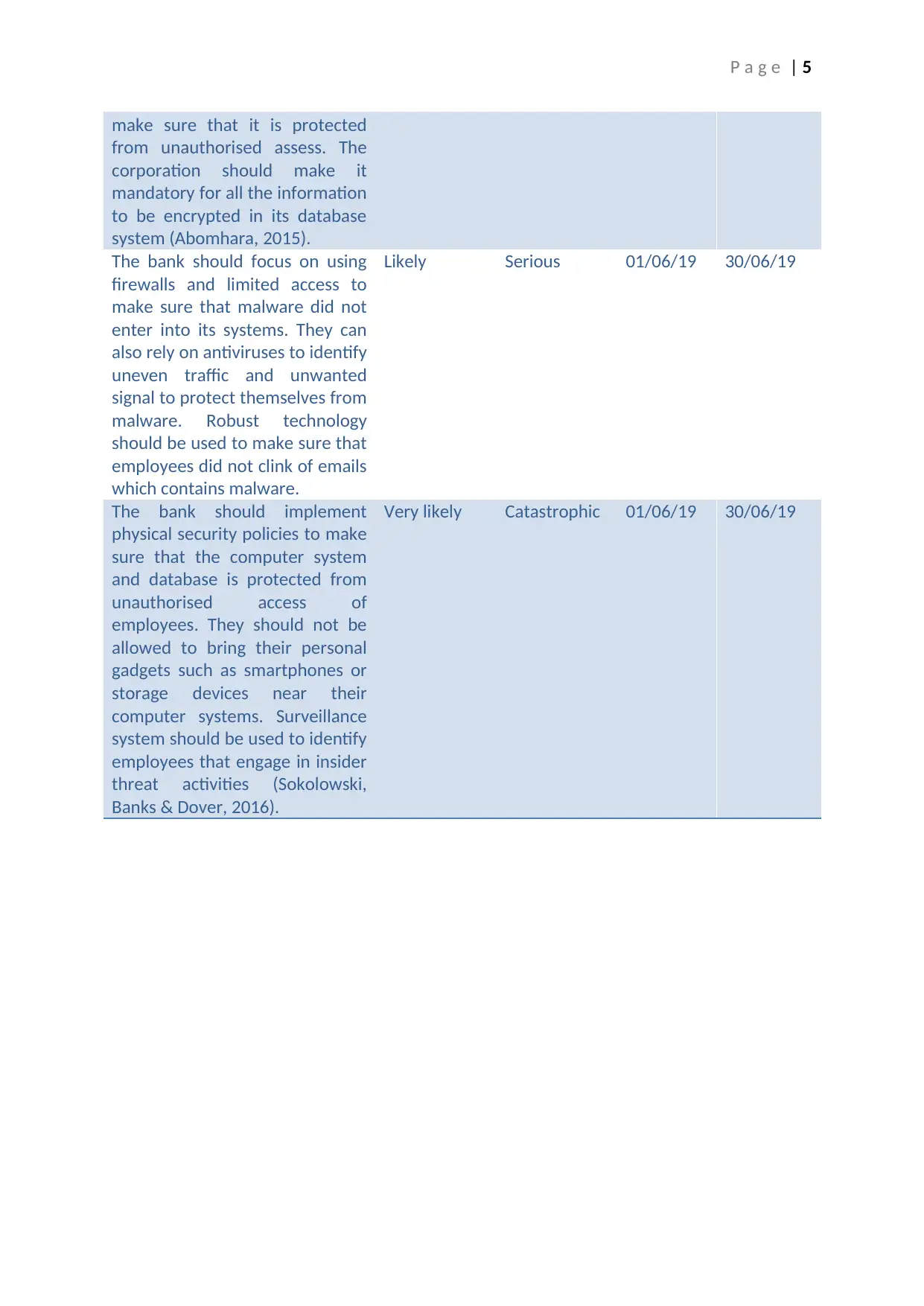
make sure that it is protected
from unauthorised assess. The
corporation should make it
mandatory for all the information
to be encrypted in its database
system (Abomhara, 2015).
The bank should focus on using
firewalls and limited access to
make sure that malware did not
enter into its systems. They can
also rely on antiviruses to identify
uneven traffic and unwanted
signal to protect themselves from
malware. Robust technology
should be used to make sure that
employees did not clink of emails
which contains malware.
Likely Serious 01/06/19 30/06/19
The bank should implement
physical security policies to make
sure that the computer system
and database is protected from
unauthorised access of
employees. They should not be
allowed to bring their personal
gadgets such as smartphones or
storage devices near their
computer systems. Surveillance
system should be used to identify
employees that engage in insider
threat activities (Sokolowski,
Banks & Dover, 2016).
Very likely Catastrophic 01/06/19 30/06/19
make sure that it is protected
from unauthorised assess. The
corporation should make it
mandatory for all the information
to be encrypted in its database
system (Abomhara, 2015).
The bank should focus on using
firewalls and limited access to
make sure that malware did not
enter into its systems. They can
also rely on antiviruses to identify
uneven traffic and unwanted
signal to protect themselves from
malware. Robust technology
should be used to make sure that
employees did not clink of emails
which contains malware.
Likely Serious 01/06/19 30/06/19
The bank should implement
physical security policies to make
sure that the computer system
and database is protected from
unauthorised access of
employees. They should not be
allowed to bring their personal
gadgets such as smartphones or
storage devices near their
computer systems. Surveillance
system should be used to identify
employees that engage in insider
threat activities (Sokolowski,
Banks & Dover, 2016).
Very likely Catastrophic 01/06/19 30/06/19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P a g e | 6
Part Two
Recommendations on the Appointment of a CISO
A Chief Information Security Officer (CISO) is referred to a senior-level executive in a
company who is responsible for a number of crucial activities. The CISO is responsible for
establishing and maintaining the vision, strategy and program in the organisation to make
sure that information assets and technologies of the enterprise are adequately protected.
The CISO focuses on identifying, developing, implementing and maintaining a number of
processes in the organisation to make sure that risks associated with information
technology (IT) are addressed in a timely manner (Dor & Elovici, 2016). Through these
policies, it becomes easier for the enterprise to make sure that adequate standards and
policies are implemented to manage security technologies and protect the sensitive data of
the enterprise. Since there are many major responsibilities which are necessary to be taken
into consideration by the CISO, the following are the key factors which should be taking into
consideration while appointing the CISO in the organisation.
1. Defining the requirements
While hiring the CISO in the organisation, the CIO should focus on defining the needs of
the company which leads to increasing the importance of hiring the CISO in the first place.
The company should asses the key factors which are necessary to be taken into
consideration that resulted in increasing the requirements of the appointment of a CISO. In
this regards, the company can focus on conducting a risk analysis to find out the key IT risks
faced by them. The risk analysis will assist the organisation in highlighting why the company
should hire the CISO in the first place.
2. Qualification and experience
The candidates who apply for the job of the CISO should be evaluated by the company
based on their qualifications and experience. The skill level of the candidates should be
judged by the company through a test and an interview in which their qualification should
be analysed as well. The company should also ensure that it hires an experienced CISO who
has enough information about these areas and who is familiar with these policies (Alexander
Part Two
Recommendations on the Appointment of a CISO
A Chief Information Security Officer (CISO) is referred to a senior-level executive in a
company who is responsible for a number of crucial activities. The CISO is responsible for
establishing and maintaining the vision, strategy and program in the organisation to make
sure that information assets and technologies of the enterprise are adequately protected.
The CISO focuses on identifying, developing, implementing and maintaining a number of
processes in the organisation to make sure that risks associated with information
technology (IT) are addressed in a timely manner (Dor & Elovici, 2016). Through these
policies, it becomes easier for the enterprise to make sure that adequate standards and
policies are implemented to manage security technologies and protect the sensitive data of
the enterprise. Since there are many major responsibilities which are necessary to be taken
into consideration by the CISO, the following are the key factors which should be taking into
consideration while appointing the CISO in the organisation.
1. Defining the requirements
While hiring the CISO in the organisation, the CIO should focus on defining the needs of
the company which leads to increasing the importance of hiring the CISO in the first place.
The company should asses the key factors which are necessary to be taken into
consideration that resulted in increasing the requirements of the appointment of a CISO. In
this regards, the company can focus on conducting a risk analysis to find out the key IT risks
faced by them. The risk analysis will assist the organisation in highlighting why the company
should hire the CISO in the first place.
2. Qualification and experience
The candidates who apply for the job of the CISO should be evaluated by the company
based on their qualifications and experience. The skill level of the candidates should be
judged by the company through a test and an interview in which their qualification should
be analysed as well. The company should also ensure that it hires an experienced CISO who
has enough information about these areas and who is familiar with these policies (Alexander
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P a g e | 7
& Cummings, 2016). A candidate who is not qualified for the job and who did not have
adequate experience in this field should not be selected by the company in the recruitment
process.
3. Behaviour requirements
Along with skill and education requirements, it is important that the candidate who is
selected for the post of the CISO should pass the behaviour requirements test. It means that
the person should have a friendly behaviour and who is a good leader. The CISO should
listen to his/her subordinations while taking decisions regarding the security measures in
the organisation (Karanja & Rosso, 2017). The CISO should also be able to work along with
others to make sure that they are able to implement policies which allow them to tackle IT-
related risks in the organisation. The CISO is required to work with low-level employees
along with the senior level executives by giving recommendations to them. These policies
should be taken into consideration by the parties while hiring the CISO for the organisation.
4. Communication skills
The candidate who is selected for the post of the CISO should be fluent in speaking with
his/her subordinates, and he/she should have adequate communication skills. The CISO has
to work along with the senior level executives and members of the board to make sure that
they have the ability to translate the complex level of IT related issues to them so that they
are able to understand them (Alexander & Cummings, 2016). They should be able to
communicate their experience and ideas with the top level management which allow them
to make effective decisions regarding the IT securities policies in the organisation.
5. Credibility and leadership ability
The CISO should have gathered credibility by carrying out the responsibilities in the field
of security, compliances and risks. The CISO should be able to demonstrate his/her ability to
assess and address the key IT related issues in the workplace which allow them to move
forward and sustain the growth of the enterprise. Since the CISO is responsible for managing
other low-level employees in the IT department, he/she must have adequate leadership
skills (Dor & Elovici, 2016). They should be able to understand the issues faced by the
& Cummings, 2016). A candidate who is not qualified for the job and who did not have
adequate experience in this field should not be selected by the company in the recruitment
process.
3. Behaviour requirements
Along with skill and education requirements, it is important that the candidate who is
selected for the post of the CISO should pass the behaviour requirements test. It means that
the person should have a friendly behaviour and who is a good leader. The CISO should
listen to his/her subordinations while taking decisions regarding the security measures in
the organisation (Karanja & Rosso, 2017). The CISO should also be able to work along with
others to make sure that they are able to implement policies which allow them to tackle IT-
related risks in the organisation. The CISO is required to work with low-level employees
along with the senior level executives by giving recommendations to them. These policies
should be taken into consideration by the parties while hiring the CISO for the organisation.
4. Communication skills
The candidate who is selected for the post of the CISO should be fluent in speaking with
his/her subordinates, and he/she should have adequate communication skills. The CISO has
to work along with the senior level executives and members of the board to make sure that
they have the ability to translate the complex level of IT related issues to them so that they
are able to understand them (Alexander & Cummings, 2016). They should be able to
communicate their experience and ideas with the top level management which allow them
to make effective decisions regarding the IT securities policies in the organisation.
5. Credibility and leadership ability
The CISO should have gathered credibility by carrying out the responsibilities in the field
of security, compliances and risks. The CISO should be able to demonstrate his/her ability to
assess and address the key IT related issues in the workplace which allow them to move
forward and sustain the growth of the enterprise. Since the CISO is responsible for managing
other low-level employees in the IT department, he/she must have adequate leadership
skills (Dor & Elovici, 2016). They should be able to understand the issues faced by the

P a g e | 8
subordinates in the IT department, and they should formulate policies which allow them to
address these issues through their effective leadership skills.
subordinates in the IT department, and they should formulate policies which allow them to
address these issues through their effective leadership skills.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P a g e | 9
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Dor, D., & Elovici, Y. (2016). A model of the information security investment decision-making
process. Computers & security, 63, 1-13.
IBM. (2019). Insider Threat Detection. Retrieved from
https://www.ibm.com/security/security-intelligence/qradar/insider-threat
Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal of
Computer and System Sciences, 80(5), 973-993.
Johnson, A. L. (2016). Cybersecurity for financial institutions: the integral role of information
sharing in cyber attack mitigation. NC Banking Inst., 20, 277.
Karanja, E., & Rosso, M. A. (2017). The chief information security officer: An exploratory
study. Journal of International Technology and Information Management, 26(2), 23-
47.
Seo, S. H., Gupta, A., Sallam, A. M., Bertino, E., & Yim, K. (2014). Detecting mobile malware
threats to homeland security through static analysis. Journal of Network and
Computer Applications, 38, 43-53.
Sokolowski, J. A., Banks, C. M., & Dover, T. J. (2016). An agent-based approach to modeling
insider threat. Computational and Mathematical Organization Theory, 22(3), 273-
287.
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Dor, D., & Elovici, Y. (2016). A model of the information security investment decision-making
process. Computers & security, 63, 1-13.
IBM. (2019). Insider Threat Detection. Retrieved from
https://www.ibm.com/security/security-intelligence/qradar/insider-threat
Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal of
Computer and System Sciences, 80(5), 973-993.
Johnson, A. L. (2016). Cybersecurity for financial institutions: the integral role of information
sharing in cyber attack mitigation. NC Banking Inst., 20, 277.
Karanja, E., & Rosso, M. A. (2017). The chief information security officer: An exploratory
study. Journal of International Technology and Information Management, 26(2), 23-
47.
Seo, S. H., Gupta, A., Sallam, A. M., Bertino, E., & Yim, K. (2014). Detecting mobile malware
threats to homeland security through static analysis. Journal of Network and
Computer Applications, 38, 43-53.
Sokolowski, J. A., Banks, C. M., & Dover, T. J. (2016). An agent-based approach to modeling
insider threat. Computational and Mathematical Organization Theory, 22(3), 273-
287.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


