Information Security: Digital Signatures and Cloud Storage
VerifiedAdded on 2022/09/18
|25
|3713
|23
Report
AI Summary
This report delves into the realm of information security, exploring digital signatures, cloud storage, and PGP encryption. Part 1a defines digital signatures, explaining their role in verifying message integrity and sender identity, and details how open-source encryption like PGP utilizes cryptographic techniques for secure communication, including public key encryption, digital signatures, and symmetric key cryptography. The advantages and disadvantages of this technology are discussed, including email encryption, file encryption, and the importance of web of trust. Part 1b provides a technical installation guide for MEGA, a cloud storage service, detailing its features, data allowances, encryption methods using AES algorithm, and API. The guide is targeted towards users of Chrome browser and Windows operating system, providing step-by-step instructions for installation and highlighting the benefits and drawbacks of cloud storage, emphasizing security, accessibility, and collaboration features.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the university
Author note
INFORMATION SECURITY
Name of the Student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Part 1a
Digital Signature can be defined as mechanism of security which the certificate
authority issues and appends to digital certificate for allowing a receiver for verifying that
there has not been any alteration from the time of its creation by the sender. It is actually like
a code that has been digitalized and gets included in the digital message for sender
identification. Digital Signature guarantees the identity of the sender of the digital message; it
is used in a number of business transactions and cannot be forged. There are various
techniques for encryption which are used for ensuring that the security level is high. In 2000,
a law in the United States made it legitimate for the signing of legal documents by utilizing
digital signatures (Chen, Liu, Chen and Wang 2018). It is like there is a guarantee digitally
about the non-alteration of the information, acting like a seal that is tamper proof and is
broken if there happens to be any alteration in the content. The two important digital
signature applications are verification of file integrity and establishment of a secured website
connection. Digital Signature is a digest encryption of the file that is signed. Computation of
the digest is done from the file contents with the help of hash function that is one way, like
SHA-1 and MD5, after which encryption is done using the private part of the private/public
key pair (Shi et al. 2016). For proving that there was no tampering done to the file, public key
is used by the recipient for decrypting the signature to original digest, re-computation of new
digest from the file that was transmitted and comparing both to see if they are matching. If
both the digests match, it’s proved that there has not been any alteration by a hacker.
As per the information digital signature is the digest encryption of a file which was
created with hash function that is one-way from the contents of the file. Digital certificates
are the first important application for digital signatures and these are used for the verification
of the organization or an individual’s identity (Buldas et al. 2019). These are broadly used for
website authentication which establishes a connection encryption for confidential data and
Part 1a
Digital Signature can be defined as mechanism of security which the certificate
authority issues and appends to digital certificate for allowing a receiver for verifying that
there has not been any alteration from the time of its creation by the sender. It is actually like
a code that has been digitalized and gets included in the digital message for sender
identification. Digital Signature guarantees the identity of the sender of the digital message; it
is used in a number of business transactions and cannot be forged. There are various
techniques for encryption which are used for ensuring that the security level is high. In 2000,
a law in the United States made it legitimate for the signing of legal documents by utilizing
digital signatures (Chen, Liu, Chen and Wang 2018). It is like there is a guarantee digitally
about the non-alteration of the information, acting like a seal that is tamper proof and is
broken if there happens to be any alteration in the content. The two important digital
signature applications are verification of file integrity and establishment of a secured website
connection. Digital Signature is a digest encryption of the file that is signed. Computation of
the digest is done from the file contents with the help of hash function that is one way, like
SHA-1 and MD5, after which encryption is done using the private part of the private/public
key pair (Shi et al. 2016). For proving that there was no tampering done to the file, public key
is used by the recipient for decrypting the signature to original digest, re-computation of new
digest from the file that was transmitted and comparing both to see if they are matching. If
both the digests match, it’s proved that there has not been any alteration by a hacker.
As per the information digital signature is the digest encryption of a file which was
created with hash function that is one-way from the contents of the file. Digital certificates
are the first important application for digital signatures and these are used for the verification
of the organization or an individual’s identity (Buldas et al. 2019). These are broadly used for
website authentication which establishes a connection encryption for confidential data and

2INFORMATION SECURITY
credit card purposes. The next important application is code signing which ensures the
verification of executable file integrity that is downloaded from website. This application also
utilizes digital certificates that are signed for identity verification.
PGP refers to Pretty Good Privacy and it is the type of encryption which has become
an important part in internet security and privacy for a reason and that is allowing users for
sending encoded message without sharing the code in advance. For example if user1 wants to
send a message to user2 and he does not want any other person to discover the message
content then the best solution is to alter the same with some secret code which only user1 and
user2 are aware of and as a result if anyone else intercepts the message, the contents will not
be readable to the third person (Pooja and Yadav 2018). However there is a flaw in such a
system. If a coded message is sent to someone without sharing the code to that person then
the recipient will not be able to decode that. Hence PGP comes into picture and has a solution
of public key encryption which helps users in sending encrypted and secured messages.
The core function of PGP is enabling the users for sending secure messages without
the requirement of any prior introduction and also the recipients are allowed for the message
verification that is whether the authenticity and contents are intact. This is done by the help of
digital signatures (Yin, Fu and Chen 2016). Apart from email encryption, PGP is also
involved in the encryption of files, hard drives, instant messages and more. Many people may
not be aware that email is not a secure method of communication. Once the email is sent from
an account it transition occurs through various networks that are beyond control of the user.
The emails can be easily tampered and intercepted without the sender’s or recipient’s
knowledge.
If user has to send sensitive or valuable information, normal email is not suitable
since it can be hacked and hackers may utilize it for committing identity frauds whereas
important messages of the government can be used by spies (Ahmad and Alam 2016). To
credit card purposes. The next important application is code signing which ensures the
verification of executable file integrity that is downloaded from website. This application also
utilizes digital certificates that are signed for identity verification.
PGP refers to Pretty Good Privacy and it is the type of encryption which has become
an important part in internet security and privacy for a reason and that is allowing users for
sending encoded message without sharing the code in advance. For example if user1 wants to
send a message to user2 and he does not want any other person to discover the message
content then the best solution is to alter the same with some secret code which only user1 and
user2 are aware of and as a result if anyone else intercepts the message, the contents will not
be readable to the third person (Pooja and Yadav 2018). However there is a flaw in such a
system. If a coded message is sent to someone without sharing the code to that person then
the recipient will not be able to decode that. Hence PGP comes into picture and has a solution
of public key encryption which helps users in sending encrypted and secured messages.
The core function of PGP is enabling the users for sending secure messages without
the requirement of any prior introduction and also the recipients are allowed for the message
verification that is whether the authenticity and contents are intact. This is done by the help of
digital signatures (Yin, Fu and Chen 2016). Apart from email encryption, PGP is also
involved in the encryption of files, hard drives, instant messages and more. Many people may
not be aware that email is not a secure method of communication. Once the email is sent from
an account it transition occurs through various networks that are beyond control of the user.
The emails can be easily tampered and intercepted without the sender’s or recipient’s
knowledge.
If user has to send sensitive or valuable information, normal email is not suitable
since it can be hacked and hackers may utilize it for committing identity frauds whereas
important messages of the government can be used by spies (Ahmad and Alam 2016). To
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
avoid all such occurrences PGP was brought into picture which would protect the security in
email communication. The most important elements on which the PGP encryption depends
on are web of trust, symmetric key cryptography, digital signatures, and public key
cryptography.
In the cryptography of symmetric key the same key is used for encryption and decryption.
The asymmetric cryptography is also known as public key cryptography and in this type both
the private and public keys are used for encryption (Roh and Lee 2018). The various steps for
a PGP encryption are as follows:
1) Adding digital signature
2) Encrypting the data or information
3) Decryption of the message
4) Verification of Digital Signature
As long as security is concerned the recent PGP versions are very secure if used correctly.
Some vulnerability exists for the older version. With the development of PGP there has been
a significant addition to the encryption algorithms for tightening the security. Even for the
slightest vulnerabilities there has been quick patching done by the developers (Li, Zhong and
Takagi 2016). For those using PGP the settings in email client should be changed so that the
auto loading of images that are external can be prevented. HTML and JavaScript should also
be turned off while viewing the encrypted emails (Suprihanto and Priyambodo 2017). With
all these measures, this type of encryption is safer to use. With all the advantages PGP also
has some drawbacks and one of its major drawback is that it is not user friendly which means
it is challenging for those who are lacking technical literacy. Different versions of PGP are
available over the years with new features and algorithms and as a result the PGP with an
older version is unable to open messages encrypted by newer one.
avoid all such occurrences PGP was brought into picture which would protect the security in
email communication. The most important elements on which the PGP encryption depends
on are web of trust, symmetric key cryptography, digital signatures, and public key
cryptography.
In the cryptography of symmetric key the same key is used for encryption and decryption.
The asymmetric cryptography is also known as public key cryptography and in this type both
the private and public keys are used for encryption (Roh and Lee 2018). The various steps for
a PGP encryption are as follows:
1) Adding digital signature
2) Encrypting the data or information
3) Decryption of the message
4) Verification of Digital Signature
As long as security is concerned the recent PGP versions are very secure if used correctly.
Some vulnerability exists for the older version. With the development of PGP there has been
a significant addition to the encryption algorithms for tightening the security. Even for the
slightest vulnerabilities there has been quick patching done by the developers (Li, Zhong and
Takagi 2016). For those using PGP the settings in email client should be changed so that the
auto loading of images that are external can be prevented. HTML and JavaScript should also
be turned off while viewing the encrypted emails (Suprihanto and Priyambodo 2017). With
all these measures, this type of encryption is safer to use. With all the advantages PGP also
has some drawbacks and one of its major drawback is that it is not user friendly which means
it is challenging for those who are lacking technical literacy. Different versions of PGP are
available over the years with new features and algorithms and as a result the PGP with an
older version is unable to open messages encrypted by newer one.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
Part 1b
Cloud storage is the model of data storage of computer where digital data is kept
within logical pools. Several servers are spanned by physical storage and physical
environment typically is owned as well as managed by hosting company. Such providers of
cloud storage are responsible to keep data available as well as accessible, along with physical
environment running and protected. People as well as organizations lease or buy capacity for
storage from providers for storing user, application or organization data (Li et al. 2017). It is
model of cloud computing which stores data over internet by provider of cloud computing
who manages as well as operates storage of data as service.
Cloud storage is dependent on virtualized infrastructure having accessible interfaces,
metered, multi-tenancy and scalability resources. Data of cloud based is stored within pools
over disparate; the commodity servers are located over premises or within data center that are
managed by cloud provider of third party. By using RESTful API, a file is stored by object
storage protocol and the associated metadata as single object as well as assigns this ID
number (Xiao et al. 2017). Most services of cloud storage use several quantities of hard drive
storage systems within servers which are linked through mesh such as network architecture.
Advantages
Cloud services possess most appropriate option to store data digitally online. Best
thing of storing all data in cloud is this ensures affordability as well as data could be accessed
easily from any place. Users could drag easily as well as drop files within cloud storage. This
is easy in saving every data and file in cloud, there is no need of technical knowledge for the
purpose. Stored file in cloud could be accessed easily from any location. This is
recommended for all businesses in having backup plan for emergency. Cloud storage is
appropriate backup plan to the businesses.
Part 1b
Cloud storage is the model of data storage of computer where digital data is kept
within logical pools. Several servers are spanned by physical storage and physical
environment typically is owned as well as managed by hosting company. Such providers of
cloud storage are responsible to keep data available as well as accessible, along with physical
environment running and protected. People as well as organizations lease or buy capacity for
storage from providers for storing user, application or organization data (Li et al. 2017). It is
model of cloud computing which stores data over internet by provider of cloud computing
who manages as well as operates storage of data as service.
Cloud storage is dependent on virtualized infrastructure having accessible interfaces,
metered, multi-tenancy and scalability resources. Data of cloud based is stored within pools
over disparate; the commodity servers are located over premises or within data center that are
managed by cloud provider of third party. By using RESTful API, a file is stored by object
storage protocol and the associated metadata as single object as well as assigns this ID
number (Xiao et al. 2017). Most services of cloud storage use several quantities of hard drive
storage systems within servers which are linked through mesh such as network architecture.
Advantages
Cloud services possess most appropriate option to store data digitally online. Best
thing of storing all data in cloud is this ensures affordability as well as data could be accessed
easily from any place. Users could drag easily as well as drop files within cloud storage. This
is easy in saving every data and file in cloud, there is no need of technical knowledge for the
purpose. Stored file in cloud could be accessed easily from any location. This is
recommended for all businesses in having backup plan for emergency. Cloud storage is
appropriate backup plan to the businesses.

5INFORMATION SECURITY
Business owner could be sure after storing data within cloud, this is safe. Best thing of
cloud storage’s use is that there is distribution of server data over redundant servers as well as
data stored within cloud service is safeguarded from any kind of failure of hardware. Cloud
storage is an appropriate platform for purposes of collaboration. Multiple people are enabled
by cloud environment for accessing, editing as well as collaborating on single document or
file (Yu et al. 2016). Cloud storage is beneficial to every kind of business. It is great platform
which doesn’t need huge investment as well as could be used actively to collect and
collaborate with employees and clients.
Disadvantages
Cloud storage has formidable setback as difficulties to migrate. After selecting
specific cloud vendor to store data, difficulties could be faced while migrating data into
another vendor. Businesses store huge amount of data generally with specific cloud vendor. If
there are problems in cloud vendor, data’s migration to other cloud vendor would not be
feasible (Yu, Ren and Wang 2016). Cloud storage consists of transfer control of the
confidential information into third party organization. Hence, complete trust is required in
cloud vendor. There could be issues in privacy and security of data which are stored within
cloud storage.
In this paper the installation guide of MEGA has been given. It is a secure cloud
storage service providing users with 50 GB free storage space. This is the 3.87.0 version
comprising of new download page video viewer, file versioning, MEGAchat and MEGAdrop
public upload folder. This provides video, text as well as audio chat capability. The source
code of the software can be found at https://mega.nz/sourcecode. This is the extension that
will allow any user to install MEGA into his or her browser (MEGA Help 2020). This will
Business owner could be sure after storing data within cloud, this is safe. Best thing of
cloud storage’s use is that there is distribution of server data over redundant servers as well as
data stored within cloud service is safeguarded from any kind of failure of hardware. Cloud
storage is an appropriate platform for purposes of collaboration. Multiple people are enabled
by cloud environment for accessing, editing as well as collaborating on single document or
file (Yu et al. 2016). Cloud storage is beneficial to every kind of business. It is great platform
which doesn’t need huge investment as well as could be used actively to collect and
collaborate with employees and clients.
Disadvantages
Cloud storage has formidable setback as difficulties to migrate. After selecting
specific cloud vendor to store data, difficulties could be faced while migrating data into
another vendor. Businesses store huge amount of data generally with specific cloud vendor. If
there are problems in cloud vendor, data’s migration to other cloud vendor would not be
feasible (Yu, Ren and Wang 2016). Cloud storage consists of transfer control of the
confidential information into third party organization. Hence, complete trust is required in
cloud vendor. There could be issues in privacy and security of data which are stored within
cloud storage.
In this paper the installation guide of MEGA has been given. It is a secure cloud
storage service providing users with 50 GB free storage space. This is the 3.87.0 version
comprising of new download page video viewer, file versioning, MEGAchat and MEGAdrop
public upload folder. This provides video, text as well as audio chat capability. The source
code of the software can be found at https://mega.nz/sourcecode. This is the extension that
will allow any user to install MEGA into his or her browser (MEGA Help 2020). This will
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
bring in reductions in the loading time thus improving the download performance as well as
strengthening security.
Background information of MEGA
It is a cloud storage as well as file hosting services that is offered by the Mega
Limited, company based at Auckland. The service is provided by the medium of web-based
applications. Mega mobile phone applications are also available for Windows, Android as
well as iOS. MEGA is better known for its 50GB storage allocation that to for the free
accounts. It was launched on 19th of January in the year 2013 by Kim Dotcom (MEGA Help
2020).
Data allowances
The free account users in MEGA are receiving:
1. 15GB base storage quota
2. An additional storage of 35 GB trail that is provided at the time of signup expires after a
time span of one month.
3. Maximum permanent storage is up to 50 GB.
The paid account users in MEGA are provided with four different tiers of options that
are:
8 TB storage (8 TB bandwidth a month)
400 GB storage (1 TB bandwidth a month)
16 TB storage (16 TB bandwidth a month)
2 TB storage (2 TB bandwidth a month)
bring in reductions in the loading time thus improving the download performance as well as
strengthening security.
Background information of MEGA
It is a cloud storage as well as file hosting services that is offered by the Mega
Limited, company based at Auckland. The service is provided by the medium of web-based
applications. Mega mobile phone applications are also available for Windows, Android as
well as iOS. MEGA is better known for its 50GB storage allocation that to for the free
accounts. It was launched on 19th of January in the year 2013 by Kim Dotcom (MEGA Help
2020).
Data allowances
The free account users in MEGA are receiving:
1. 15GB base storage quota
2. An additional storage of 35 GB trail that is provided at the time of signup expires after a
time span of one month.
3. Maximum permanent storage is up to 50 GB.
The paid account users in MEGA are provided with four different tiers of options that
are:
8 TB storage (8 TB bandwidth a month)
400 GB storage (1 TB bandwidth a month)
16 TB storage (16 TB bandwidth a month)
2 TB storage (2 TB bandwidth a month)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
Data Encryption
Keeping the security of client’s data in mind, Mega service is encrypted on the client-
side and for this AES algorithm has been made use of. The encryption keys to the files that
are uploaded are not known to Mega and thus the content of the user cannot be decrypted and
viewed (MEGA, 2020). Thus, they cannot be held responsible for the contents in the
uploaded files.
API
MEGA has released some of the documentation of its API so that it can be made use
of by developers to write their own applications.
Data Encryption
Keeping the security of client’s data in mind, Mega service is encrypted on the client-
side and for this AES algorithm has been made use of. The encryption keys to the files that
are uploaded are not known to Mega and thus the content of the user cannot be decrypted and
viewed (MEGA, 2020). Thus, they cannot be held responsible for the contents in the
uploaded files.
API
MEGA has released some of the documentation of its API so that it can be made use
of by developers to write their own applications.
8INFORMATION SECURITY
Work Instruction template:
Applies to: Analysts who use the Chrome browser and Windows operating system.
Objective:
It will help a user to install Mega Cloud into its system guiding him at
every step.
Pre-Requisites
Prior to the installation it must be checked that which browser best
suits for the same and what can be the errors in the process
Date [17/04/2020]
Version of the cloud
storage Mega
3.87.0, available in 50 languages
Type: Cloud storage, File hosting service and remote backup service
Author [Name of Author]
Work Instruction template:
Applies to: Analysts who use the Chrome browser and Windows operating system.
Objective:
It will help a user to install Mega Cloud into its system guiding him at
every step.
Pre-Requisites
Prior to the installation it must be checked that which browser best
suits for the same and what can be the errors in the process
Date [17/04/2020]
Version of the cloud
storage Mega
3.87.0, available in 50 languages
Type: Cloud storage, File hosting service and remote backup service
Author [Name of Author]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INFORMATION SECURITY
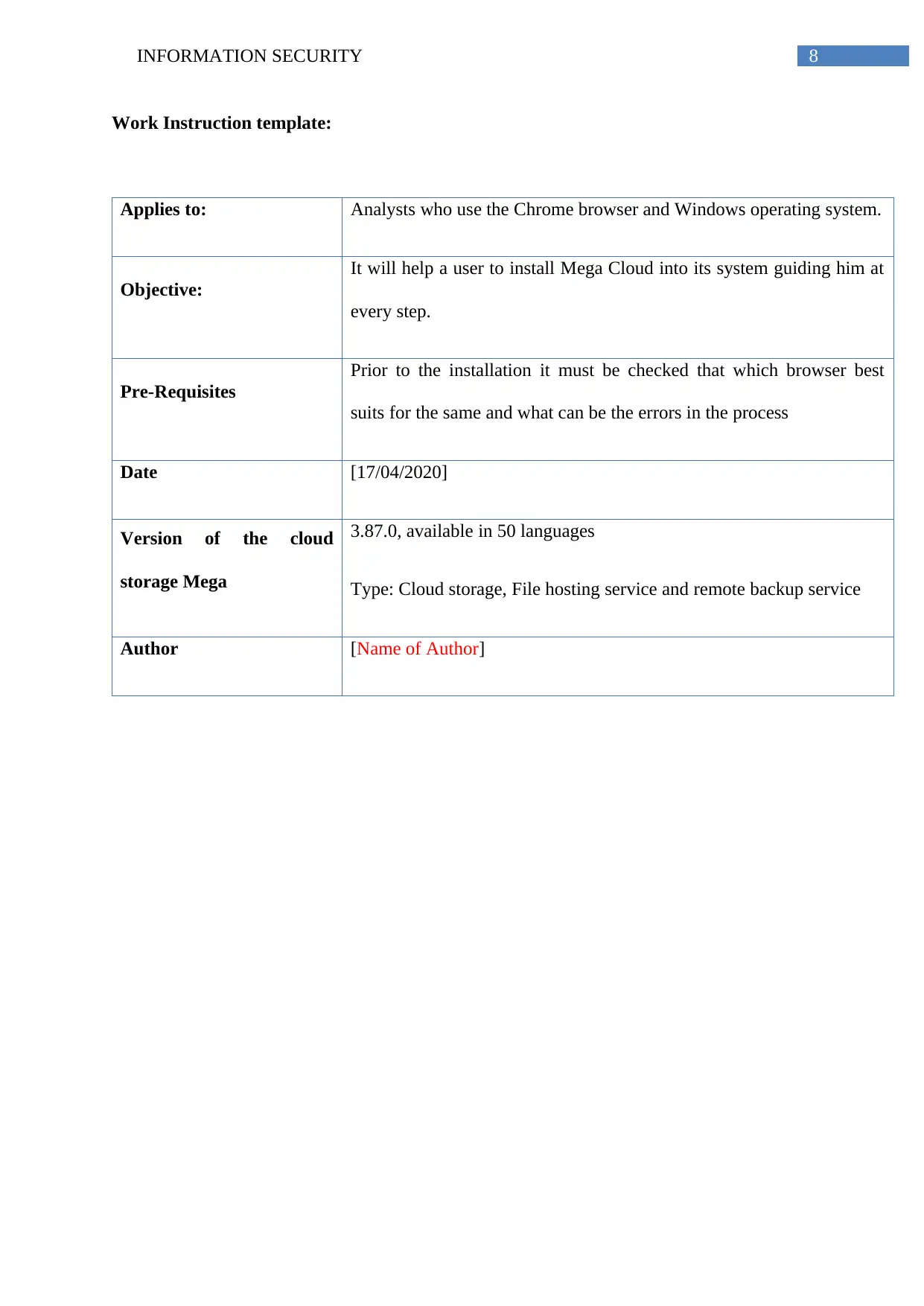
The steps that need to be followed to install the Mega cloud storage software are as follows:
Installation Guide
Step 1: Download Nextcloud from https://megasync.en.softonic.com/
Mega cloud is downloading:
Mega cloud can be downloaded from the link that is given above. Chrome browser is
recommended for this purpose.
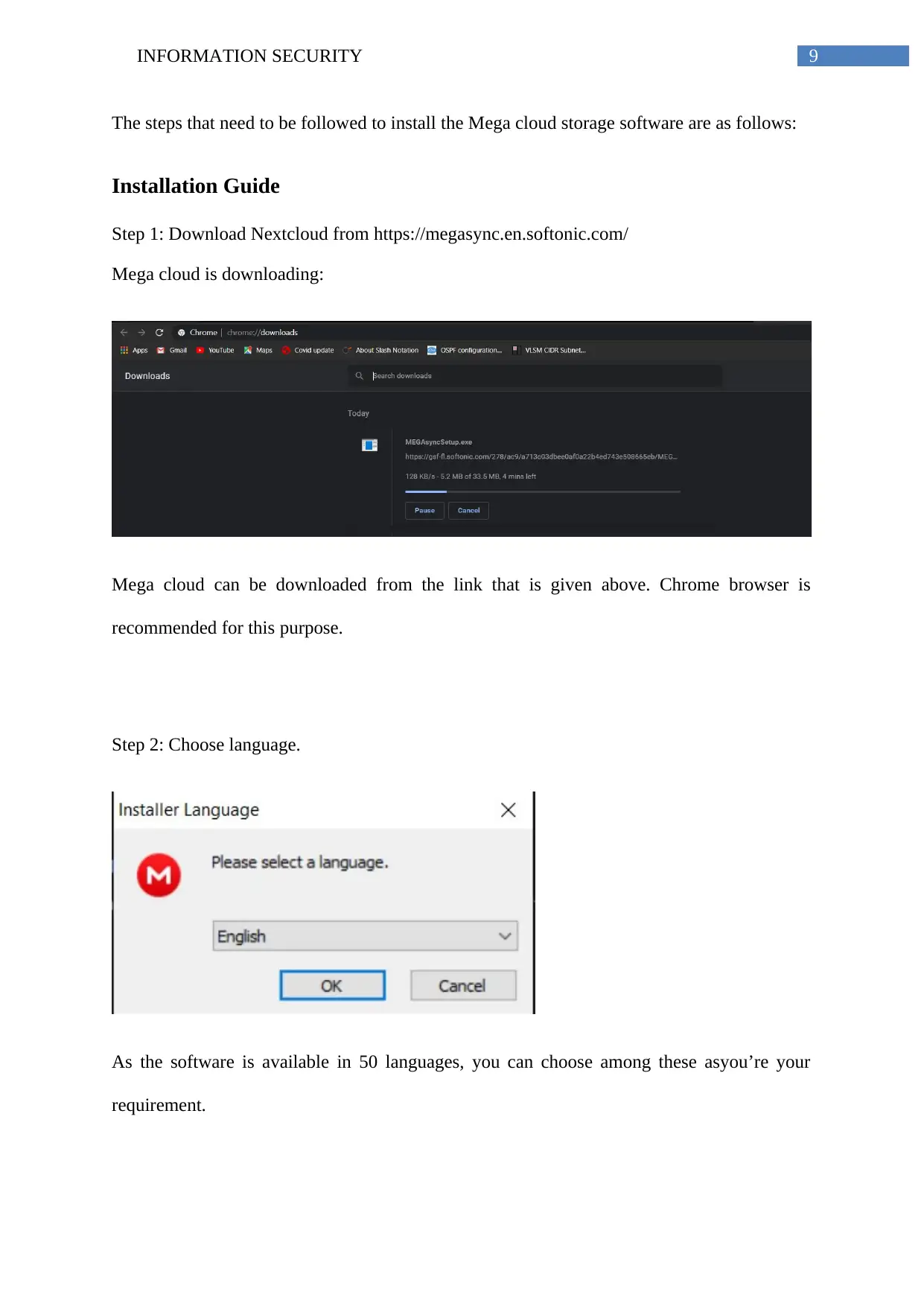
Step 2: Choose language.
As the software is available in 50 languages, you can choose among these asyou’re your
requirement.
The steps that need to be followed to install the Mega cloud storage software are as follows:
Installation Guide
Step 1: Download Nextcloud from https://megasync.en.softonic.com/
Mega cloud is downloading:
Mega cloud can be downloaded from the link that is given above. Chrome browser is
recommended for this purpose.
Step 2: Choose language.
As the software is available in 50 languages, you can choose among these asyou’re your
requirement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10INFORMATION SECURITY
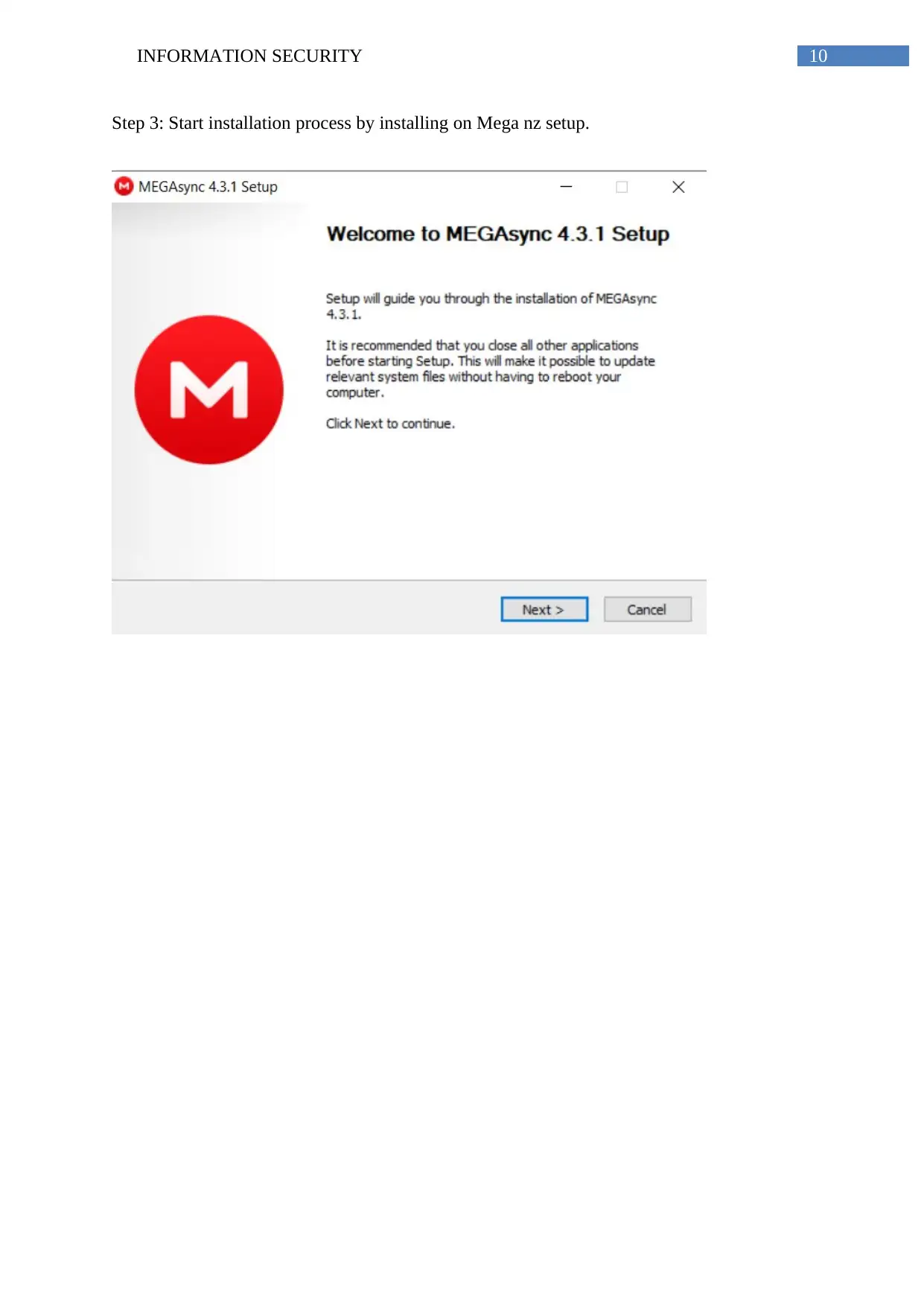
Step 3: Start installation process by installing on Mega nz setup.
Step 3: Start installation process by installing on Mega nz setup.
11INFORMATION SECURITY
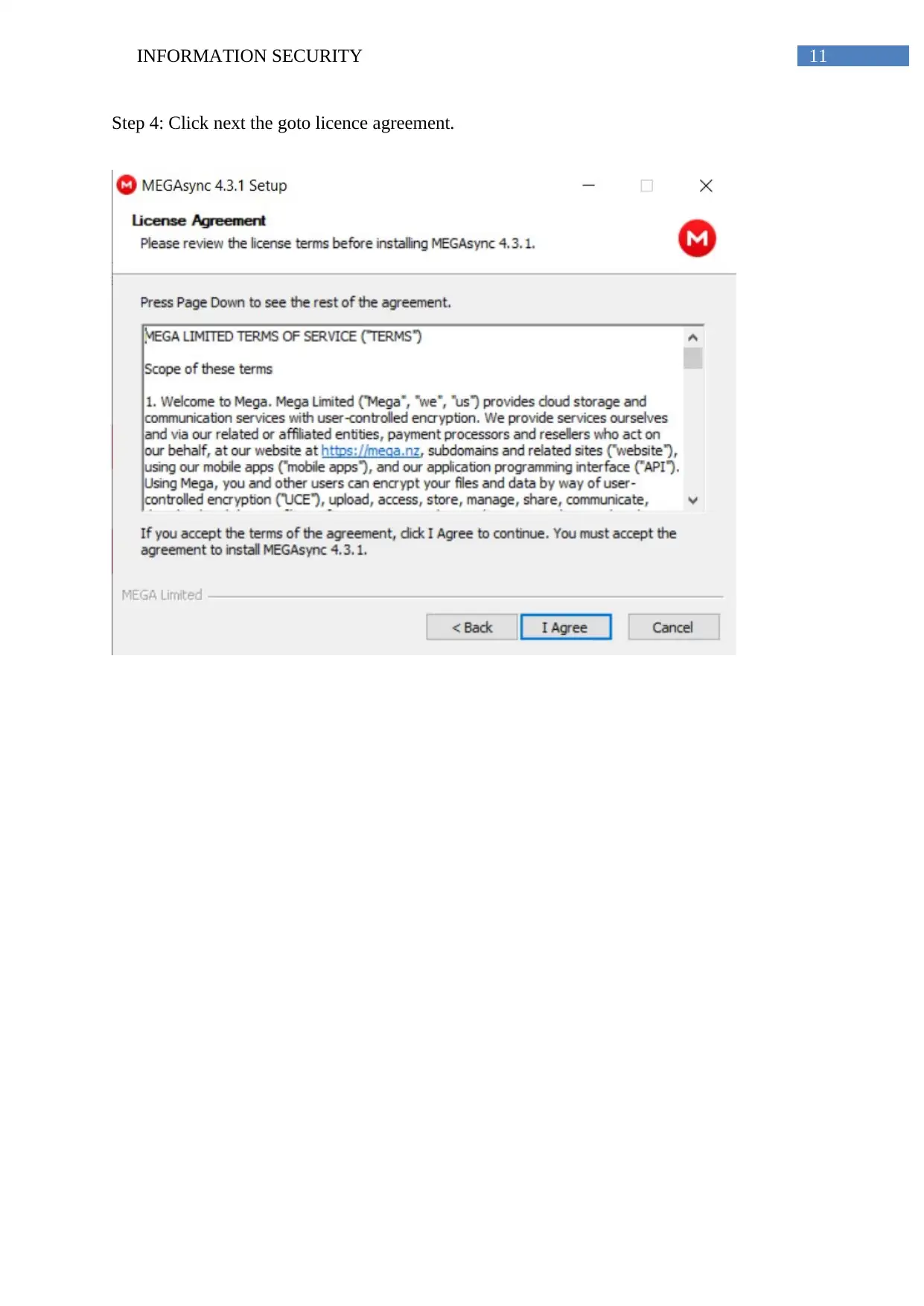
Step 4: Click next the goto licence agreement.
Step 4: Click next the goto licence agreement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




