Project Management: Risk Planning for Dining Cafe Development (ITC505)
VerifiedAdded on 2022/10/17
|9
|356
|5
Project
AI Summary
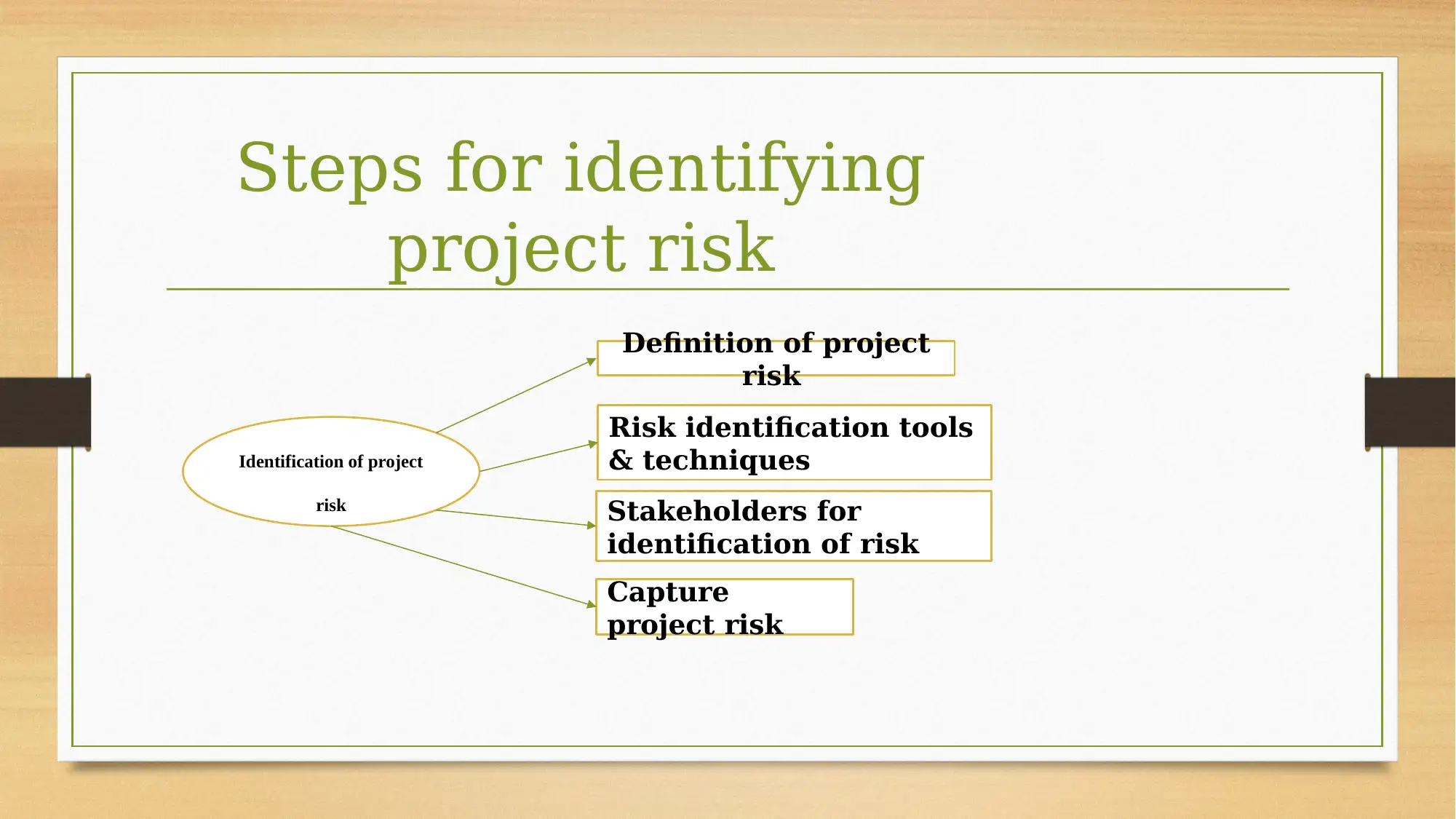
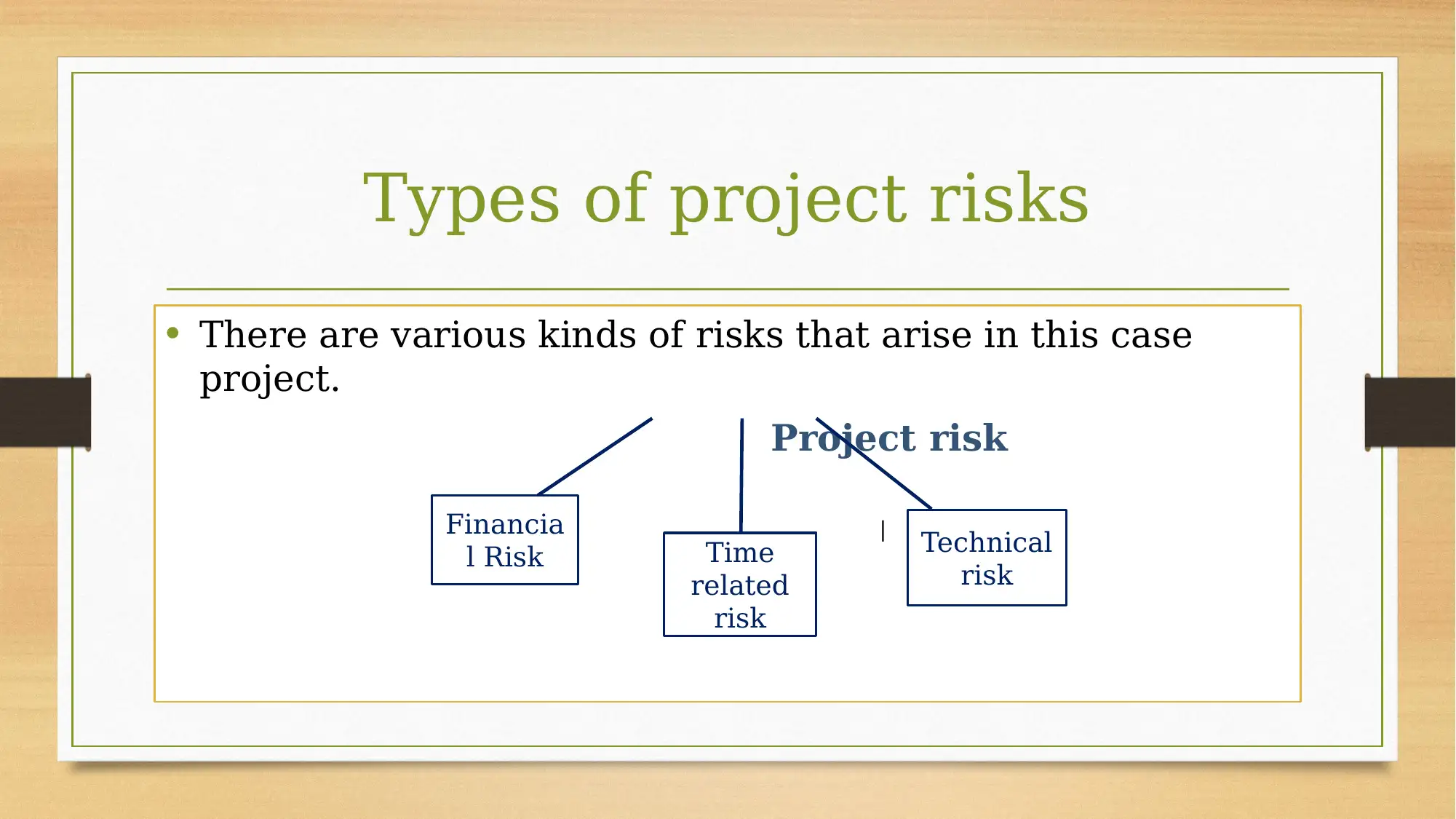
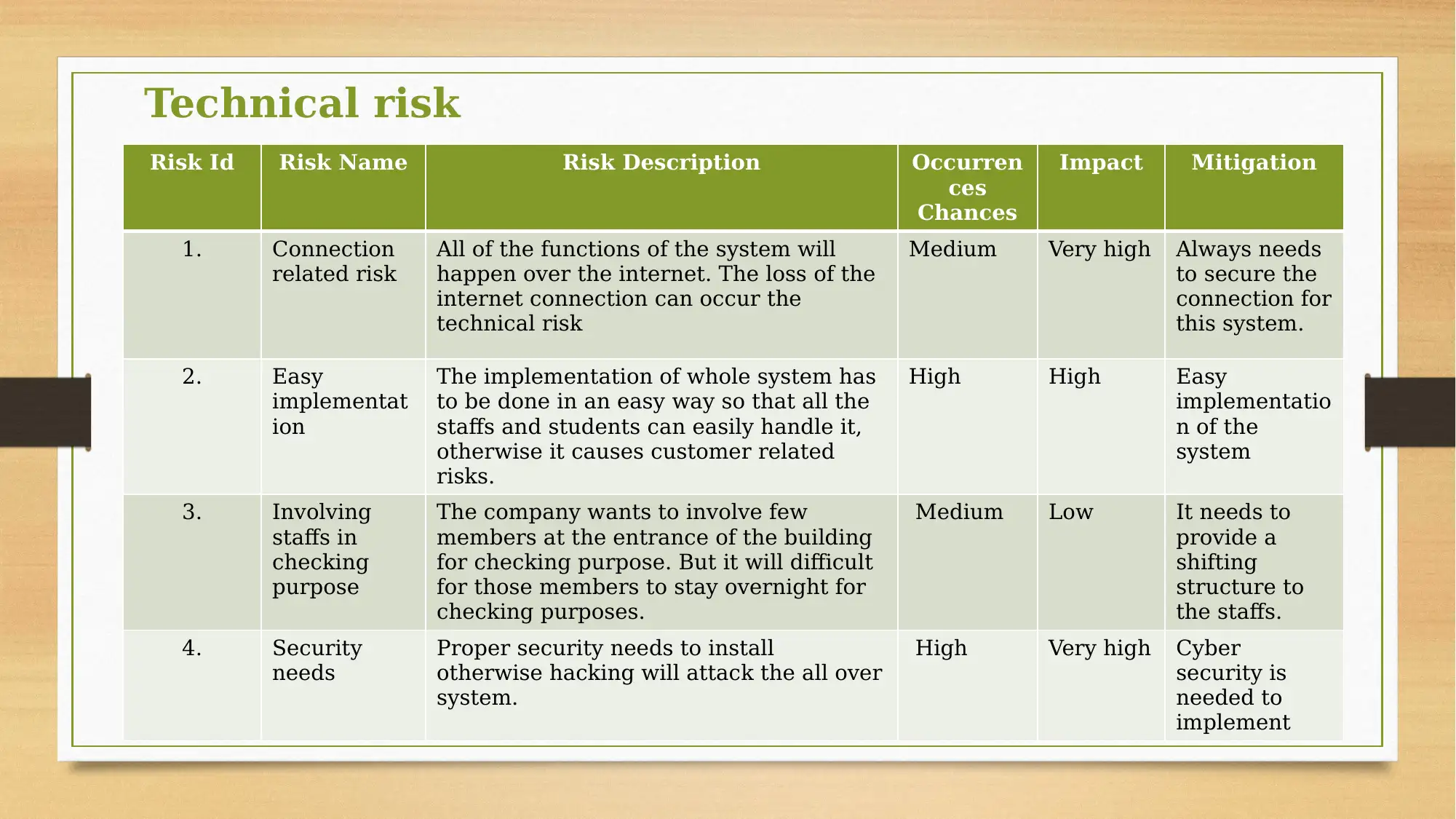
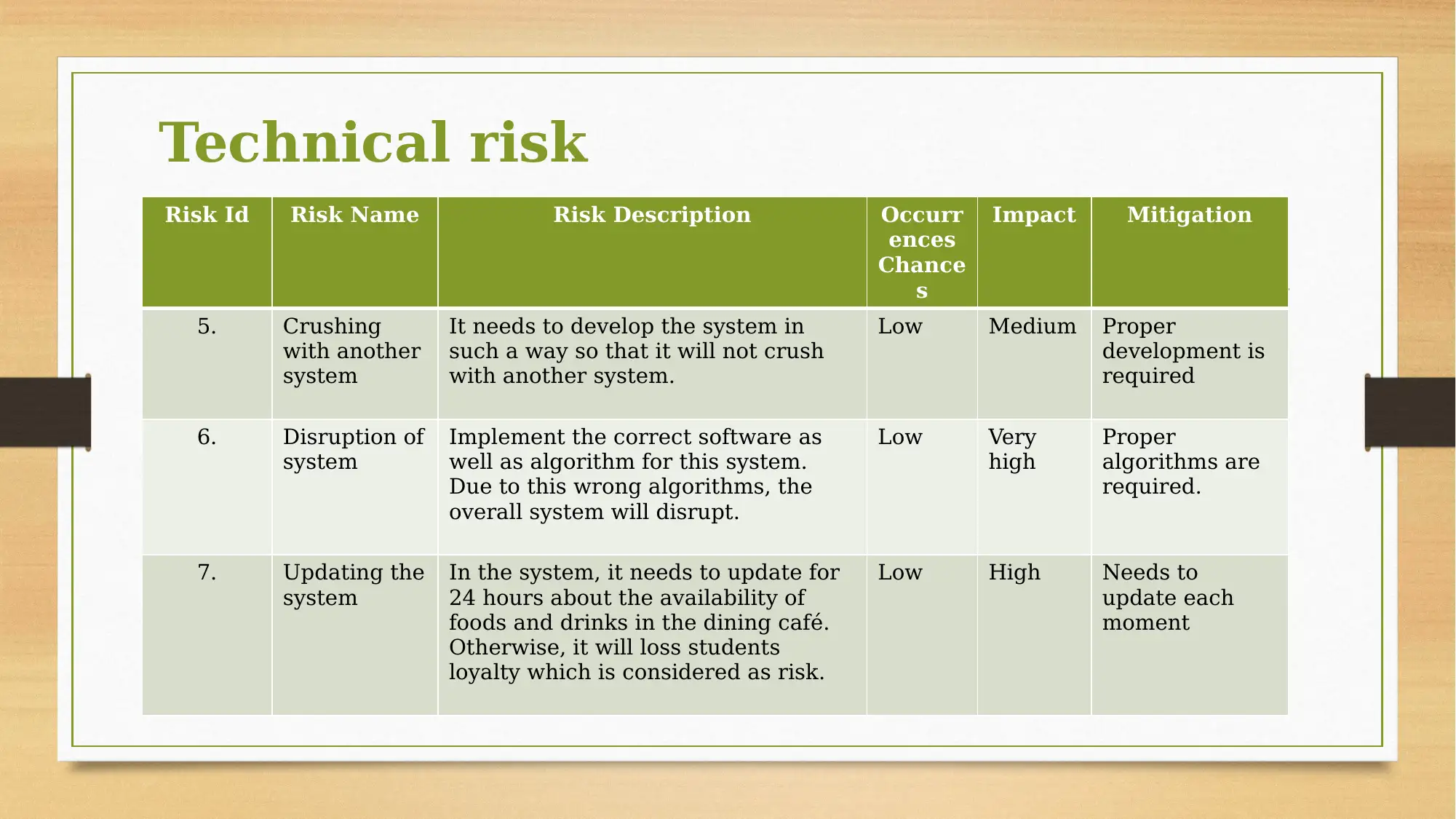
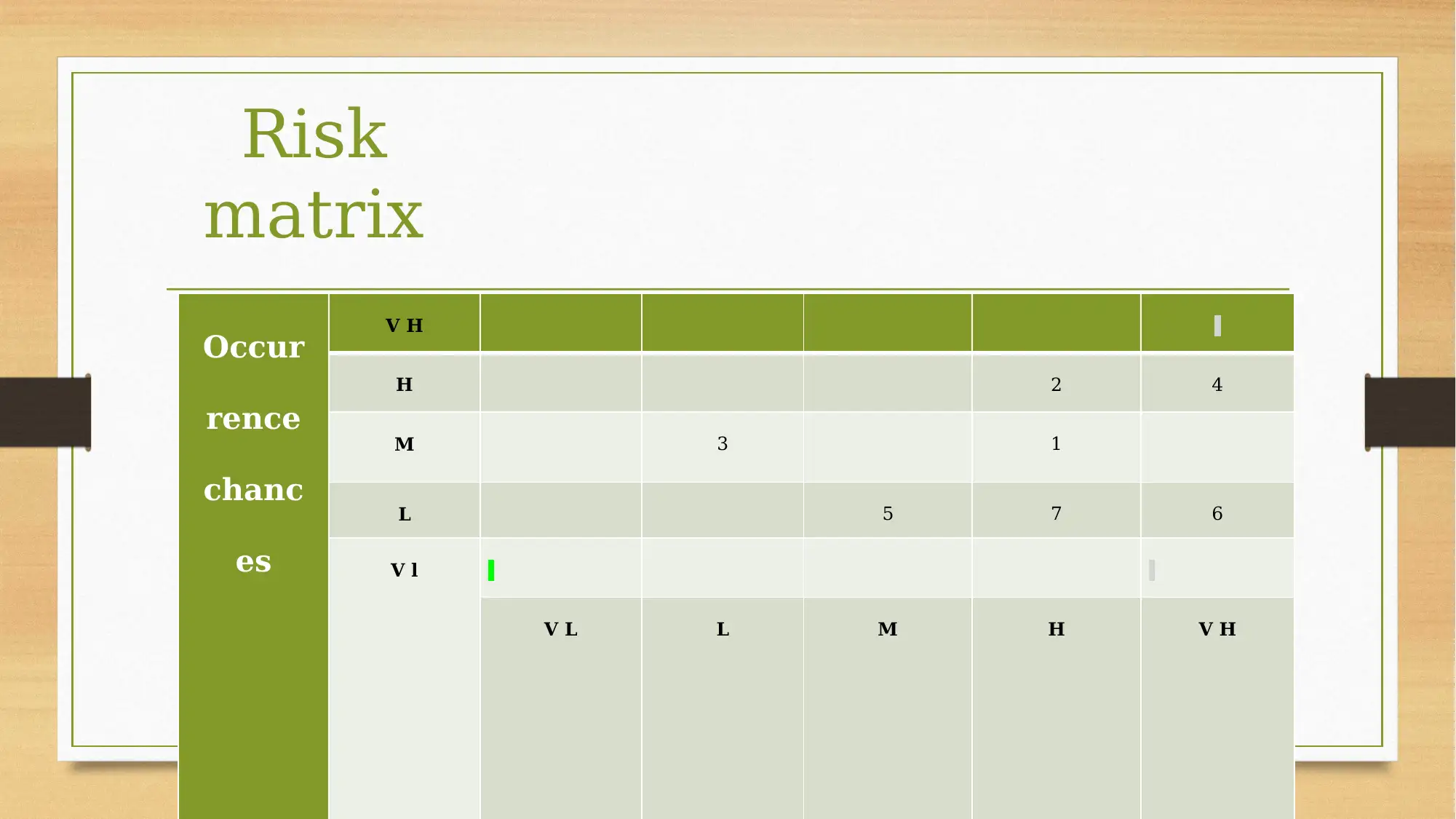
This assignment focuses on risk planning for a dining cafe development project. The project involves establishing a 24-hour dining cafe with diverse menu options and food providers. The core of the project involves the implementation of a system, requiring the installation of swipe card readers and special access cards. The assignment identifies and analyzes various risks, including financial, time-related, and technical risks. Financial risks are associated with the costs of system implementation, specifically the choice between two models, Model A and Model B. Time-related risks are linked to project delays, and technical risks are related to the project's technical aspects. The assignment also mentions a risk matrix for a comprehensive approach to risk management.
1 out of 9










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)