CCE 3070: Network Management - Disaster Recovery and Risk Assessment
VerifiedAdded on 2023/04/11
|6
|297
|438
Report
AI Summary
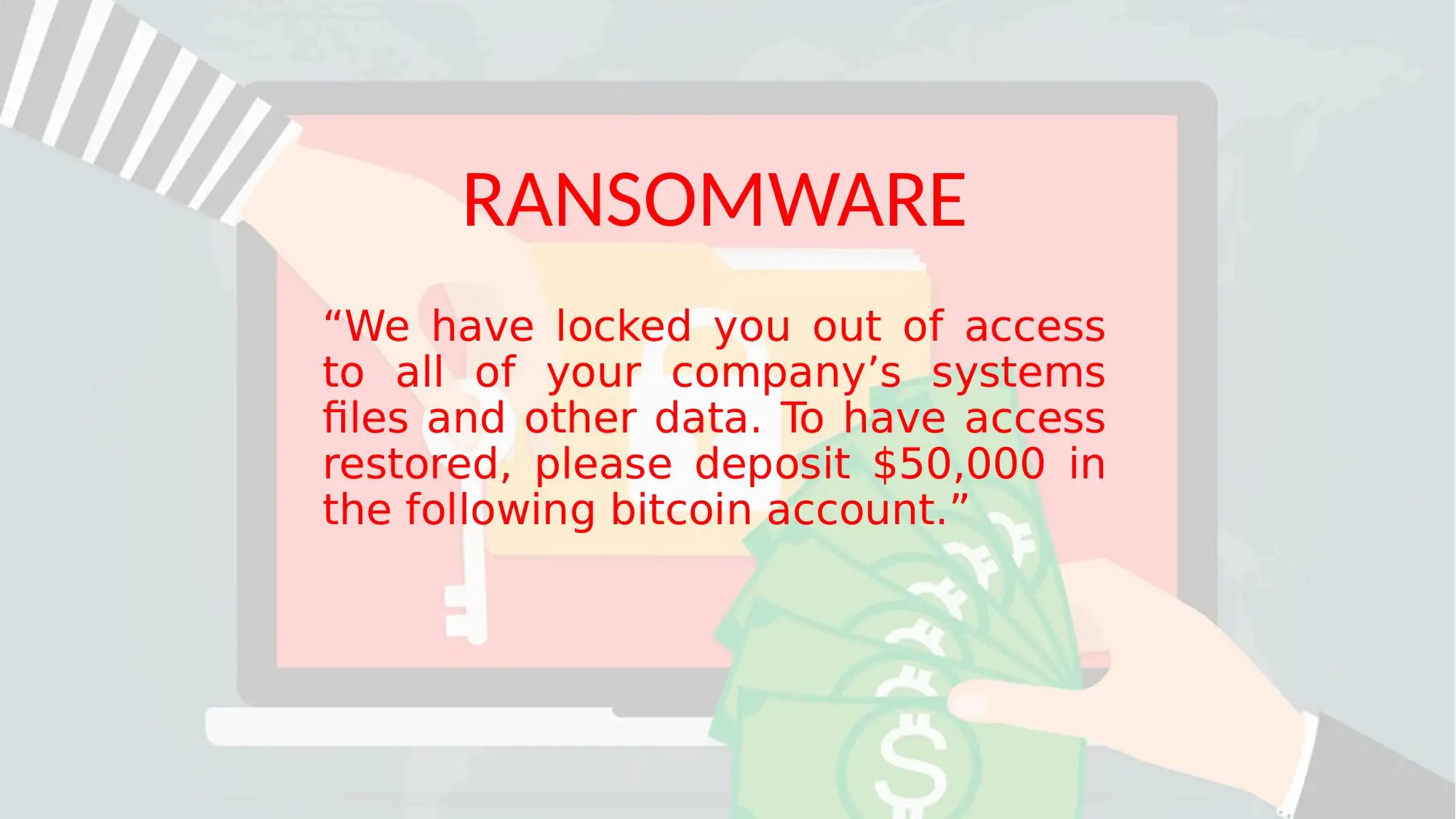
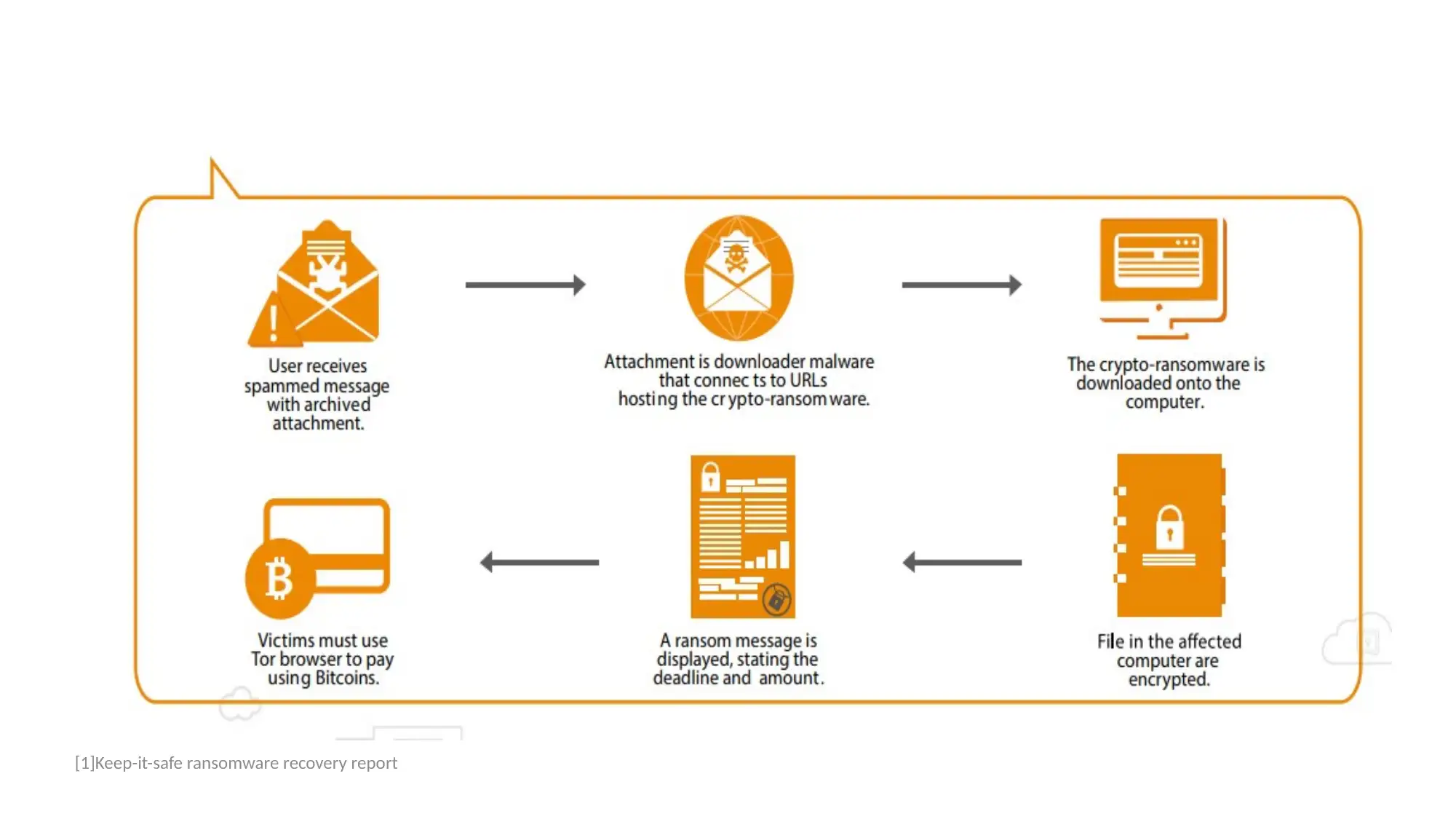
This report provides a disaster recovery plan for network management, addressing potential threats like ransomware. It outlines steps for data backup, recovery, and system protection, including the importance of regular system scans, software updates, and user training. The report details how to respond to a ransomware attack, including immediate actions, identifying the compromise, assessing the loss, and deciding whether to pay the ransom. It emphasizes the need to check shared resources, identify key data for restoration, and evaluate the recovery process. The report also references several sources that support the strategies and recommendations provided. Desklib offers this report to students as a resource for understanding and implementing effective network security measures.
1 out of 6










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)