Comprehensive Disaster Recovery and Risk Management Plan
VerifiedAdded on 2023/04/22
|9
|1670
|328
Report
AI Summary
This report details a comprehensive disaster recovery plan, emphasizing the importance of data security and business continuity. It identifies potential threats such as malware, ransomware, and DDoS attacks, and outlines strategies for data backup, including critical applications, customer details, and employee information. The plan includes a schedule for full and incremental backups to the cloud, along with risk mitigation policies focused on avoiding data loss through security measures like anti-virus software and cloud storage. Legislative and regulatory constraints related to customer data are also considered, ensuring compliance and preventing legal issues. The report further describes the stages of disaster recovery, from understanding organizational infrastructure to testing the disaster recovery plan, highlighting the critical role of cloud computing in modern disaster recovery strategies. Desklib offers this document as part of its extensive library of solved assignments and past papers.
Running Head: Disaster Recovery Plan 0
Disaster Recovery Plan
Report
Students name
Disaster Recovery Plan
Report
Students name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disaster Recovery Plan 1
Table of Contents
Question 1: 5....................................................................................................................................1
Threats that could impact.............................................................................................................1
Question 2: 6....................................................................................................................................1
Applications and files that you will backup.................................................................................1
Questions 3: 6..................................................................................................................................1
Data listed as important may be subject to legislative or regulatory constraints.........................1
Question 4........................................................................................................................................2
The planned schedule...................................................................................................................2
Some of the major risk migration policies are.................................................................................5
References........................................................................................................................................6
Table of Contents
Question 1: 5....................................................................................................................................1
Threats that could impact.............................................................................................................1
Question 2: 6....................................................................................................................................1
Applications and files that you will backup.................................................................................1
Questions 3: 6..................................................................................................................................1
Data listed as important may be subject to legislative or regulatory constraints.........................1
Question 4........................................................................................................................................2
The planned schedule...................................................................................................................2
Some of the major risk migration policies are.................................................................................5
References........................................................................................................................................6
Disaster Recovery Plan 2
Question 1: 5
Threats that could impact
Any organisation keeping data is one of the most important things that are to be done by
the management and the IT team of the organization. Some of the major threats that the
organisations face are Malware and ransom wares. Virus and spywares these are some of the
most horrific threats that the organisation can face (Stallings 2017). While the virus and the
malware affect the system hardware of the organisation, the spyware can extract information
from the systems of the organisation. Other than this there can be threats like the DDOS attract,
and the server side attract. Other than this some of the other major problems that the organisation
can face is the unpatched servers and software vulnerabilities (Gai et al. 2016). These are the
most dangerous vulnerabilities that can hamper the regular work of the organisation. The
organization needs a very specific security services so that it come overcome the working of
these threats and the organisation can work on smoothly.
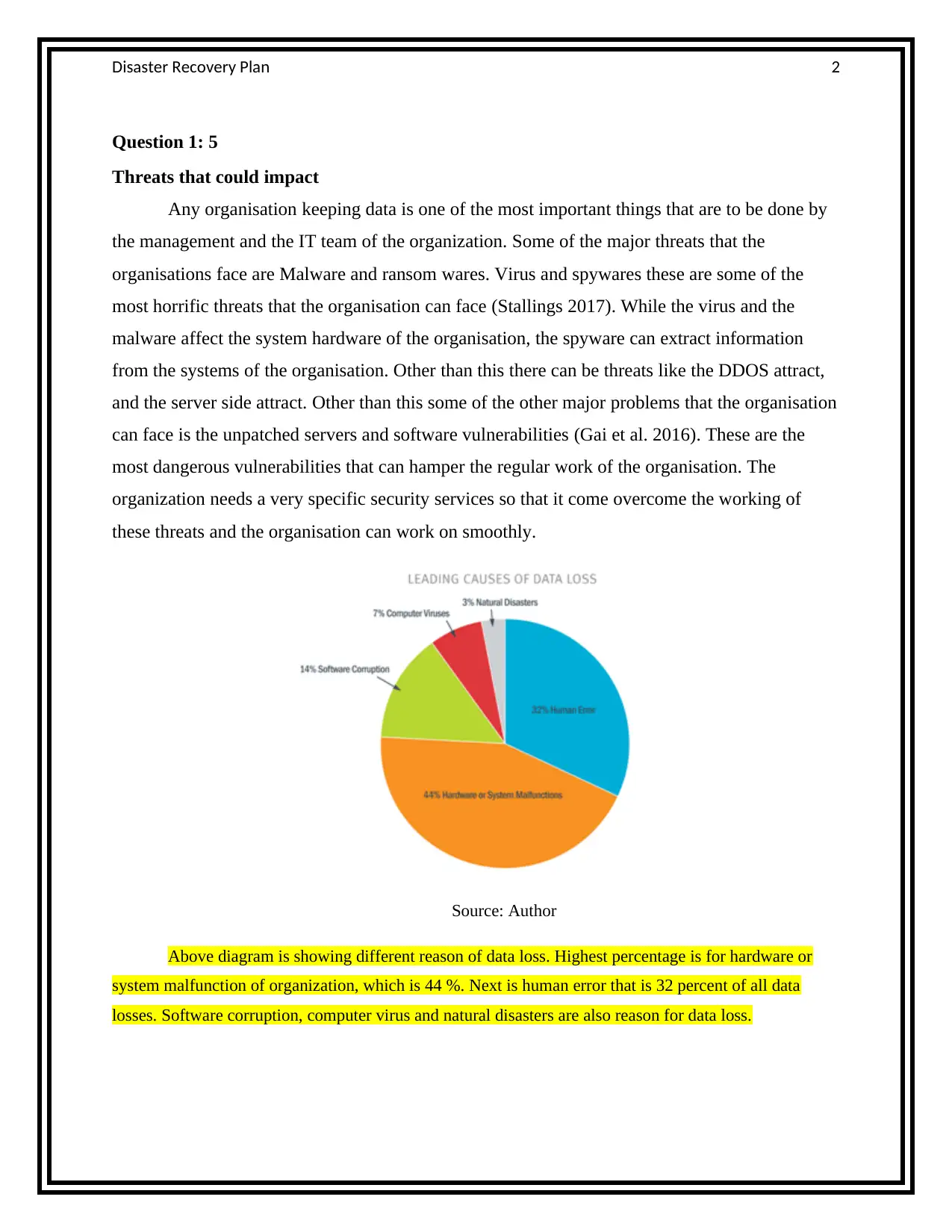
Source: Author
Above diagram is showing different reason of data loss. Highest percentage is for hardware or
system malfunction of organization, which is 44 %. Next is human error that is 32 percent of all data
losses. Software corruption, computer virus and natural disasters are also reason for data loss.
Question 1: 5
Threats that could impact
Any organisation keeping data is one of the most important things that are to be done by
the management and the IT team of the organization. Some of the major threats that the
organisations face are Malware and ransom wares. Virus and spywares these are some of the
most horrific threats that the organisation can face (Stallings 2017). While the virus and the
malware affect the system hardware of the organisation, the spyware can extract information
from the systems of the organisation. Other than this there can be threats like the DDOS attract,
and the server side attract. Other than this some of the other major problems that the organisation
can face is the unpatched servers and software vulnerabilities (Gai et al. 2016). These are the
most dangerous vulnerabilities that can hamper the regular work of the organisation. The
organization needs a very specific security services so that it come overcome the working of
these threats and the organisation can work on smoothly.
Source: Author
Above diagram is showing different reason of data loss. Highest percentage is for hardware or
system malfunction of organization, which is 44 %. Next is human error that is 32 percent of all data
losses. Software corruption, computer virus and natural disasters are also reason for data loss.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disaster Recovery Plan 3
Question 2: 6
Applications and files that you will backup
If there is any case of the security violation there needs to proper follow up and there
files that are needed to be moved to safe archives. As all the employees of the organisation
depends on the email and the database present in the online application. As the database
contains the records off all the customer details and billing information, these are some of the
most important data that have to be archived and stored safe (Chang and Ramachandran 2016)
Other than this the employee details, the information about the billings and accounts are
some of the most important things that are to be backup (Rahim and Ikhwan 2016). Other than
this, the regular data like the regular work information things that can be saved. If these system
data are not properly saved, then it can hamper the smooth flow of the organisation. These are
some of the most important things that are to be backed.
Questions 3: 6
Data listed as important may be subject to legislative or regulatory constraints
The data of the customers’ details are some of the most useful for the customer
and they are subject to the legislative and regulatory constraints for the information. These are
some of the most important thing that is to be made safe (Sun et al. 2014). Thus making some of
the most important data that is properly backed up. Loss of this information can lead to legal
cases against the customer.
Question 4
Disaster recovery plan
Every organization should have a disaster recovery plan for business continuity. Now
days, it is a common process that every organizations implement a back plan or disaster recovery
plan. It can be any type of disaster, such as natural and human oriented. Cyber-attacks are
common now days. Therefore, organization must have their disaster recovery plan to avoid any
failure as well as ransom. Few malwares are hacked the system and they require ransom for
accessing their own system. Different stages in disaster recovery are showing in below diagram.
Question 2: 6
Applications and files that you will backup
If there is any case of the security violation there needs to proper follow up and there
files that are needed to be moved to safe archives. As all the employees of the organisation
depends on the email and the database present in the online application. As the database
contains the records off all the customer details and billing information, these are some of the
most important data that have to be archived and stored safe (Chang and Ramachandran 2016)
Other than this the employee details, the information about the billings and accounts are
some of the most important things that are to be backup (Rahim and Ikhwan 2016). Other than
this, the regular data like the regular work information things that can be saved. If these system
data are not properly saved, then it can hamper the smooth flow of the organisation. These are
some of the most important things that are to be backed.
Questions 3: 6
Data listed as important may be subject to legislative or regulatory constraints
The data of the customers’ details are some of the most useful for the customer
and they are subject to the legislative and regulatory constraints for the information. These are
some of the most important thing that is to be made safe (Sun et al. 2014). Thus making some of
the most important data that is properly backed up. Loss of this information can lead to legal
cases against the customer.
Question 4
Disaster recovery plan
Every organization should have a disaster recovery plan for business continuity. Now
days, it is a common process that every organizations implement a back plan or disaster recovery
plan. It can be any type of disaster, such as natural and human oriented. Cyber-attacks are
common now days. Therefore, organization must have their disaster recovery plan to avoid any
failure as well as ransom. Few malwares are hacked the system and they require ransom for
accessing their own system. Different stages in disaster recovery are showing in below diagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Disaster Recovery Plan 4
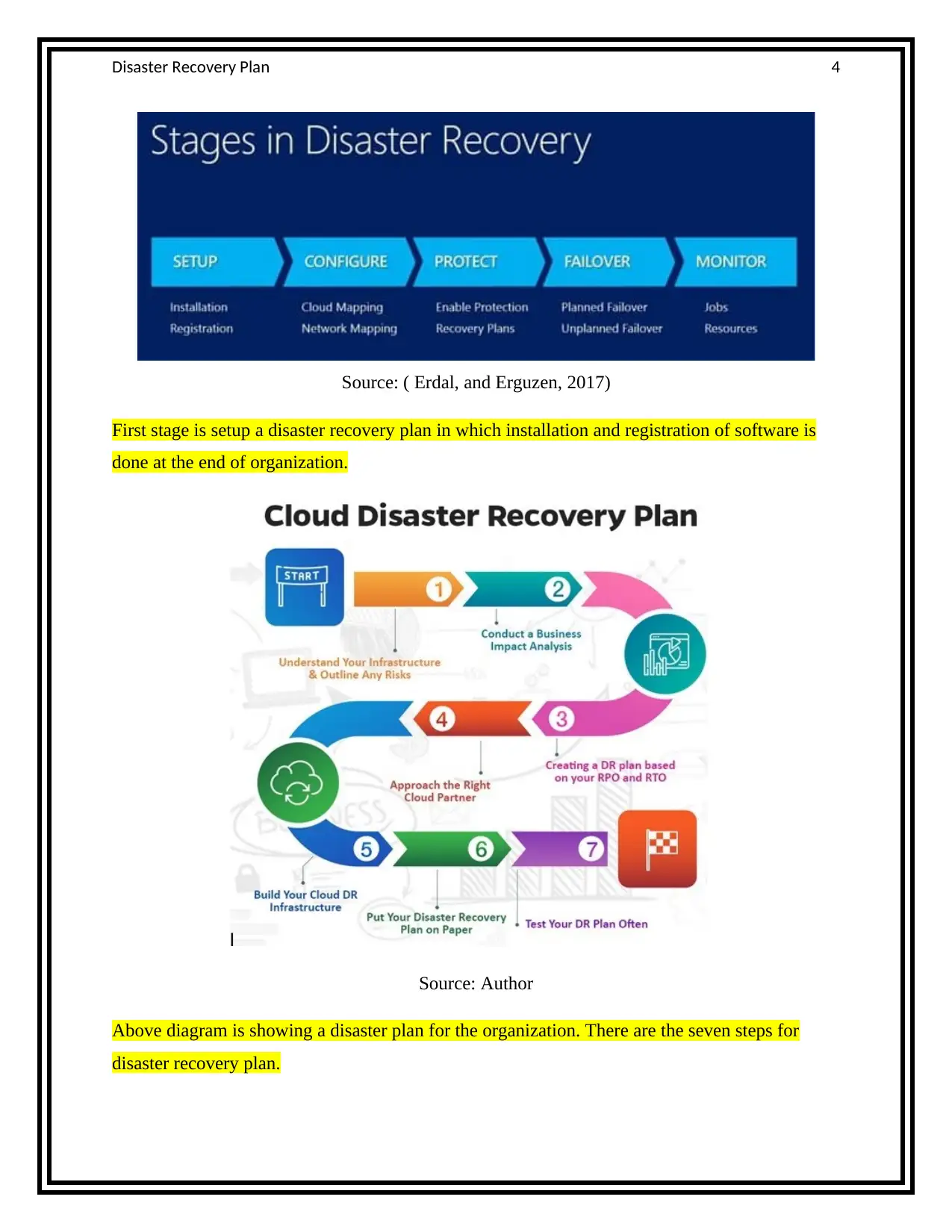
Source: ( Erdal, and Erguzen, 2017)
First stage is setup a disaster recovery plan in which installation and registration of software is
done at the end of organization.
Source: Author
Above diagram is showing a disaster plan for the organization. There are the seven steps for
disaster recovery plan.
Source: ( Erdal, and Erguzen, 2017)
First stage is setup a disaster recovery plan in which installation and registration of software is
done at the end of organization.
Source: Author
Above diagram is showing a disaster plan for the organization. There are the seven steps for
disaster recovery plan.
Disaster Recovery Plan 5
1. Understand organization infrastructure
2. Conduct a business impact analysis
3. Creating a DR plan based on RPO and RTO
4. Approach the right cloud partner
5. Build organization cloud DR infrastructure
6. Put organization disaster recovery plan on a paper
7. Test organization DR plan often
All these steps are used for DR plan in cloud computing infrastructure.
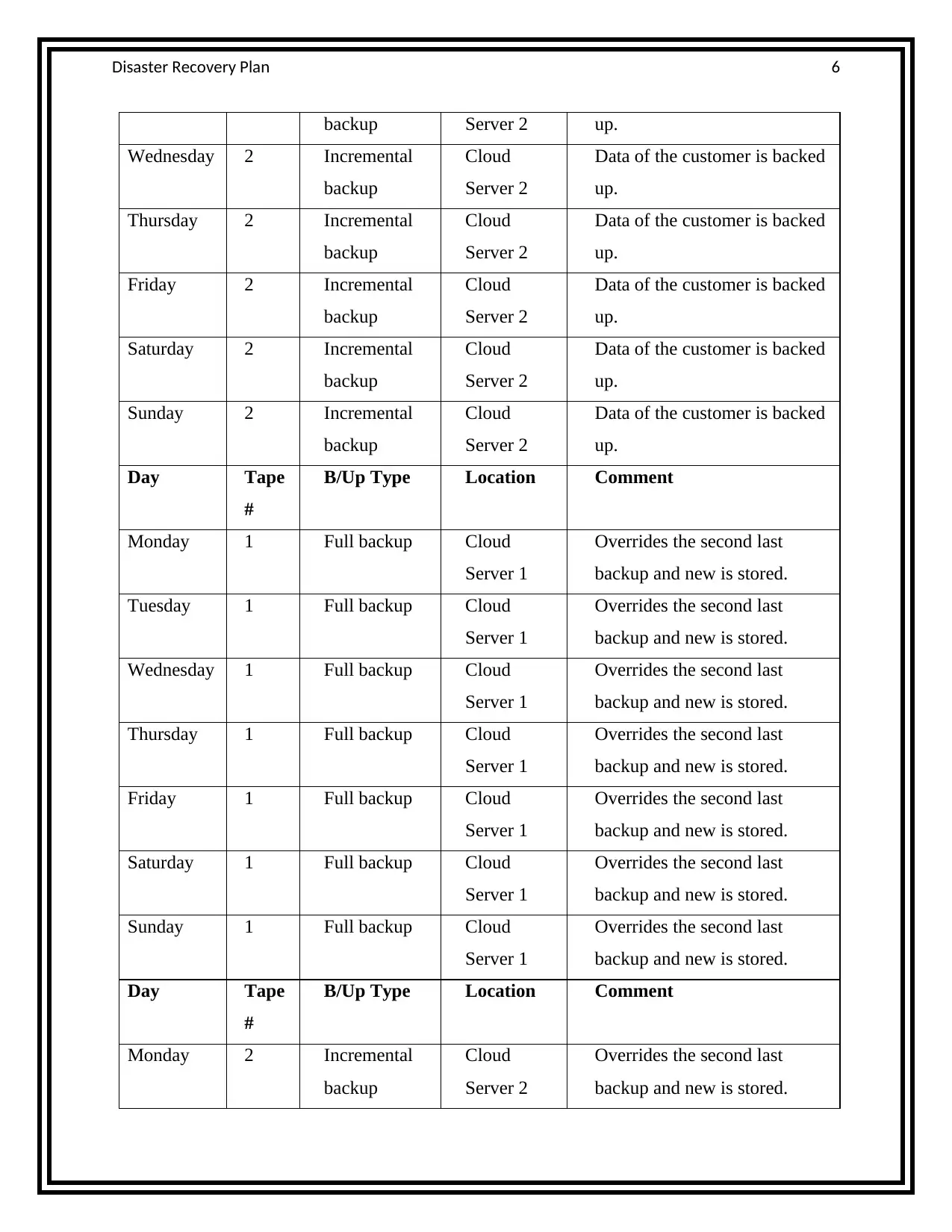
The planned schedule
Day Tape
#
B/Up Type Location Comment
Monday 1 Full backup Cloud
Server 1
Full data backup is done
Tuesday 1 Full backup Cloud
Server 1
Full data backup is done
Wednesday 1 Full backup Cloud
Server 1
Full data backup is done
Thursday 1 Full backup Cloud
Server 1
Full data backup is done
Friday 1 Full backup Cloud
Server 1
Full data backup is done
Saturday 1 Full backup Cloud
Server 1
Full data backup is done
Sunday 1 Full backup Cloud
Server 1
Full data backup is done
Day Tape
#
B/Up Type Location Comment
Monday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Tuesday 2 Incremental Cloud Data of the customer is backed
1. Understand organization infrastructure
2. Conduct a business impact analysis
3. Creating a DR plan based on RPO and RTO
4. Approach the right cloud partner
5. Build organization cloud DR infrastructure
6. Put organization disaster recovery plan on a paper
7. Test organization DR plan often
All these steps are used for DR plan in cloud computing infrastructure.
The planned schedule
Day Tape
#
B/Up Type Location Comment
Monday 1 Full backup Cloud
Server 1
Full data backup is done
Tuesday 1 Full backup Cloud
Server 1
Full data backup is done
Wednesday 1 Full backup Cloud
Server 1
Full data backup is done
Thursday 1 Full backup Cloud
Server 1
Full data backup is done
Friday 1 Full backup Cloud
Server 1
Full data backup is done
Saturday 1 Full backup Cloud
Server 1
Full data backup is done
Sunday 1 Full backup Cloud
Server 1
Full data backup is done
Day Tape
#
B/Up Type Location Comment
Monday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Tuesday 2 Incremental Cloud Data of the customer is backed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Disaster Recovery Plan 6
backup Server 2 up.
Wednesday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Thursday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Friday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Saturday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Sunday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
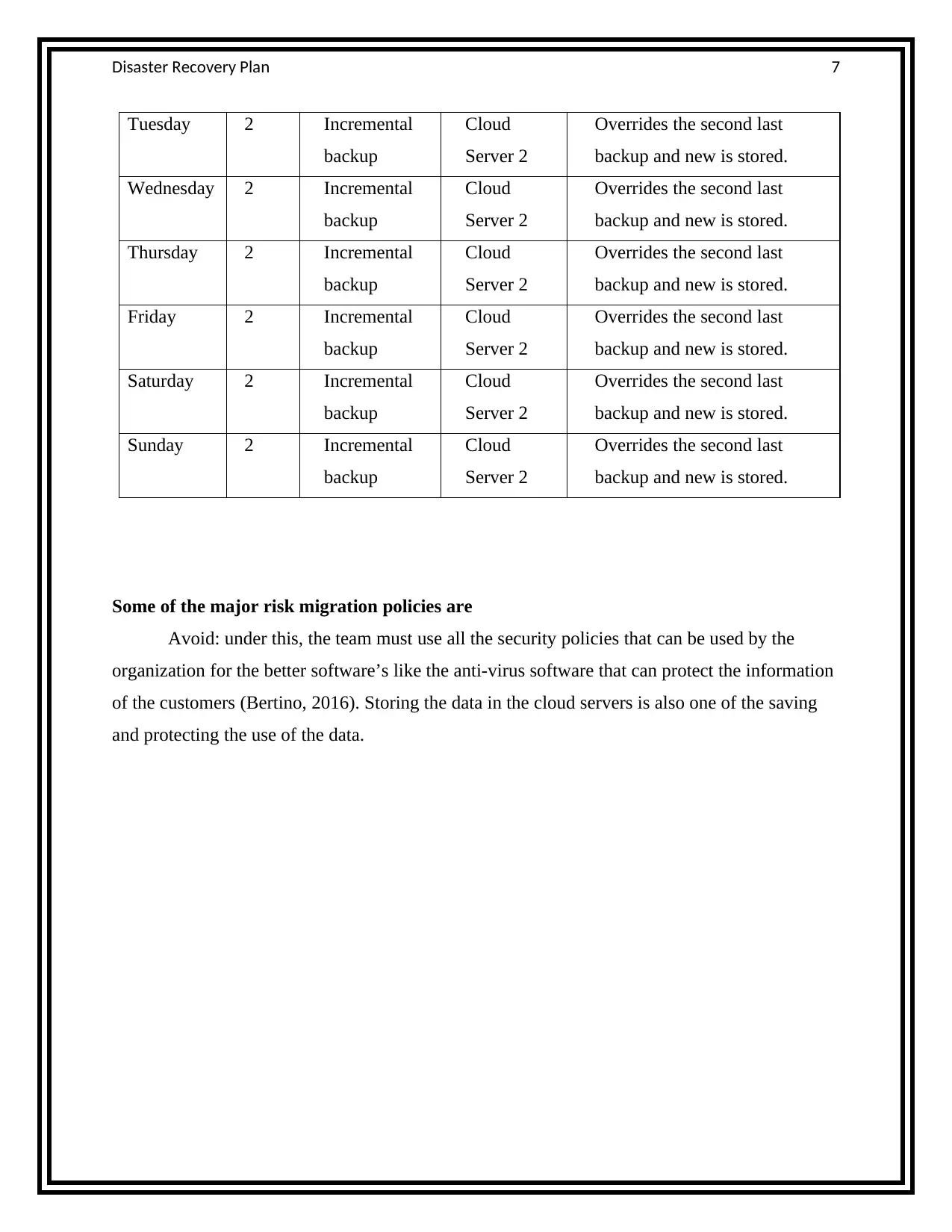
Day Tape
#
B/Up Type Location Comment
Monday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Tuesday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Wednesday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Thursday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Friday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Saturday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Sunday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Day Tape
#
B/Up Type Location Comment
Monday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
backup Server 2 up.
Wednesday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Thursday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Friday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Saturday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Sunday 2 Incremental
backup
Cloud
Server 2
Data of the customer is backed
up.
Day Tape
#
B/Up Type Location Comment
Monday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Tuesday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Wednesday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Thursday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Friday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Saturday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Sunday 1 Full backup Cloud
Server 1
Overrides the second last
backup and new is stored.
Day Tape
#
B/Up Type Location Comment
Monday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Disaster Recovery Plan 7
Tuesday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Wednesday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Thursday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Friday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Saturday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Sunday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Some of the major risk migration policies are
Avoid: under this, the team must use all the security policies that can be used by the
organization for the better software’s like the anti-virus software that can protect the information
of the customers (Bertino, 2016). Storing the data in the cloud servers is also one of the saving
and protecting the use of the data.
Tuesday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Wednesday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Thursday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Friday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Saturday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Sunday 2 Incremental
backup
Cloud
Server 2
Overrides the second last
backup and new is stored.
Some of the major risk migration policies are
Avoid: under this, the team must use all the security policies that can be used by the
organization for the better software’s like the anti-virus software that can protect the information
of the customers (Bertino, 2016). Storing the data in the cloud servers is also one of the saving
and protecting the use of the data.

Disaster Recovery Plan 8
References
Bertino, E., 2016, March. Data Security and Privacy in the IoT. In EDBT (Vol. 2016, pp. 1-3).
Chang, V. and Ramachandran, M., 2016. Towards achieving data security with the cloud
computing adoption framework. IEEE Trans. Services Computing, 9(1), pp.138-151.
Erdal, E. and Erguzen, A. 2017. The New Era of Medical Imaging: Cloud. International Journal
of Advances in Electronics and Computer Science 4, pp. 28-32.
Gai, K., Qiu, M. and Zhao, H., 2016, April. Security-aware efficient mass distributed storage
approach for cloud systems in big data. In Big Data Security on Cloud (BigDataSecurity),
IEEE International Conference on High Performance and Smart Computing (HPSC),
and IEEE International Conference on Intelligent Data and Security (IDS), 2016 IEEE
2nd International Conference on (pp. 140-145). IEEE.
Rahim, R. and Ikhwan, A., 2016. Study of Three Pass Protocol on Data Security. Int. J. Sci.
Res, 5(11), pp.102-104.
Stallings, W., 2017. Cryptography and network security: principles and practice (pp. 743).
Upper Saddle River, NJ: Pearson.
Sun, Y., Zhang, J., Xiong, Y. and Zhu, G., 2014. Data security and privacy in cloud
computing. International Journal of Distributed Sensor Networks, 10(7), pp.190903
References
Bertino, E., 2016, March. Data Security and Privacy in the IoT. In EDBT (Vol. 2016, pp. 1-3).
Chang, V. and Ramachandran, M., 2016. Towards achieving data security with the cloud
computing adoption framework. IEEE Trans. Services Computing, 9(1), pp.138-151.
Erdal, E. and Erguzen, A. 2017. The New Era of Medical Imaging: Cloud. International Journal
of Advances in Electronics and Computer Science 4, pp. 28-32.
Gai, K., Qiu, M. and Zhao, H., 2016, April. Security-aware efficient mass distributed storage
approach for cloud systems in big data. In Big Data Security on Cloud (BigDataSecurity),
IEEE International Conference on High Performance and Smart Computing (HPSC),
and IEEE International Conference on Intelligent Data and Security (IDS), 2016 IEEE
2nd International Conference on (pp. 140-145). IEEE.
Rahim, R. and Ikhwan, A., 2016. Study of Three Pass Protocol on Data Security. Int. J. Sci.
Res, 5(11), pp.102-104.
Stallings, W., 2017. Cryptography and network security: principles and practice (pp. 743).
Upper Saddle River, NJ: Pearson.
Sun, Y., Zhang, J., Xiong, Y. and Zhu, G., 2014. Data security and privacy in cloud
computing. International Journal of Distributed Sensor Networks, 10(7), pp.190903
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





