Comprehensive Network Redesign for Heeley Trust Dissertation Project
VerifiedAdded on 2023/02/01
|80
|17820
|43
Project
AI Summary
This dissertation presents a comprehensive analysis of the Heeley Trust network, focusing on the existing design across three sites: Meersbrook Hall, Head Quarter (HQ), and SUM Studio. The study identifies critical issues such as network security vulnerabilities, scalability limitations, and performance bottlenecks. The research employs qualitative methods, including interviews with management and staff, to gather insights into the challenges faced by Heeley Trust. Based on the findings, the dissertation proposes a redesigned network architecture that incorporates a hierarchical network topology, enhanced security measures including VLAN segmentation and firewalls, and improved services like Active Directory, DHCP, and web traffic filtering. The proposed solution aims to increase bandwidth, implement redundancy, and establish secure WAN connections using VPNs, ultimately improving the reliability, scalability, and security of the Heeley Trust network. The dissertation also discusses potential future enhancements such as the use of MPLS, DMVPN, and virtualization technologies.

Abstract.
Network has benefitted from rapid growth of technology in deferent aspects of life. This
is because it has made life much easier, the functionality will be in the same line with the growth
of information technology, in particular computer network at this time provide the humanity with
more simplicity and ease functionality to communicate within seconds globally. With this rapid
growth, a lot of challenges have emerged in most entities who are considering to catch up the
latest technology to avoid to be left behind. Computer network development has left legacy
networks vulnerable to a number of challenges, like security and latency, scalability and other
factors. This will be significant to in being able to within the recent technology so that it can
keep the functions of the system to function in the right way.
In the organization environment, computer network is one of the most important elements
to be considered, as in some companies lack of good network design will affect the entire
functionality business production. Network security is one of the most important consideration
that need to be design carefully especially when working over the internet or ethernet to
transferring of confidential and sensitive information. Also, the reliability and resiliency of the
network are important in providing smooth and constant flow of the data through the network.
In this dissertation, some study and investigation have been done with regards to the
current design of the three sites for Heeley Trust network, addressed the current issues. The
issues have also been analyzed by performing an interview to the Heeley Trust management and
number of staff. There interviews helped in identifying some problems and the obstacles they are
facing, also addressed the security vulnerabilities and the level of network performance.
Furthermore, discussed the new vision of that organization management for the future aspect of
the network design. Based on the results of the new proposal, there was need to come to
Network has benefitted from rapid growth of technology in deferent aspects of life. This
is because it has made life much easier, the functionality will be in the same line with the growth
of information technology, in particular computer network at this time provide the humanity with
more simplicity and ease functionality to communicate within seconds globally. With this rapid
growth, a lot of challenges have emerged in most entities who are considering to catch up the
latest technology to avoid to be left behind. Computer network development has left legacy
networks vulnerable to a number of challenges, like security and latency, scalability and other
factors. This will be significant to in being able to within the recent technology so that it can
keep the functions of the system to function in the right way.
In the organization environment, computer network is one of the most important elements
to be considered, as in some companies lack of good network design will affect the entire
functionality business production. Network security is one of the most important consideration
that need to be design carefully especially when working over the internet or ethernet to
transferring of confidential and sensitive information. Also, the reliability and resiliency of the
network are important in providing smooth and constant flow of the data through the network.
In this dissertation, some study and investigation have been done with regards to the
current design of the three sites for Heeley Trust network, addressed the current issues. The
issues have also been analyzed by performing an interview to the Heeley Trust management and
number of staff. There interviews helped in identifying some problems and the obstacles they are
facing, also addressed the security vulnerabilities and the level of network performance.
Furthermore, discussed the new vision of that organization management for the future aspect of
the network design. Based on the results of the new proposal, there was need to come to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

redesign the entire network for the three sites to overcome the issues that existed in the current
network design.
network design.

Table of Contents
Abstract.......................................................................................................................................................1
List of Figures.............................................................................................................................................6
List of tables................................................................................................................................................7
1.0 Introduction.........................................................................................................................................8
1.1 Research Question.........................................................................................................................10
1.1.1 Research Aim........................................................................................................................10
1.1.2 Research Objective................................................................................................................11
1.2 Heeley trust Overview.........................................................................................................................12
1.2.1 Meersbrook Hall...........................................................................................................................12
1.2.2 Head Quarter (HQ).......................................................................................................................13
1.2.3 SUM Studio..................................................................................................................................13
1.3 Current Network Design..................................................................................................................13
1.3.1 Meersbrook Hall (MH).................................................................................................................15
1.3.2 Head Quarter (HQ)........................................................................................................................19
1.3.3 Sum Studio...................................................................................................................................21
1.4 Services...............................................................................................................................................24
Chapter Two..............................................................................................................................................26
2.0 Literature Review............................................................................................................................26
2.1 Company.........................................................................................................................................26
2.2 The issues with the current design....................................................................................................27
2.2.1 Flat Network...........................................................................................................................27
2.2.2 Scalability................................................................................................................................28
2.2.3 Redundancy and resiliency....................................................................................................29
2.2.4 WAN........................................................................................................................................30
2.2.5 Internet Service Providers (ISP)...............................................................................................30
2.2.6 Issues with wireless..................................................................................................................30
2.2.7 Network Audit..........................................................................................................................31
2.4 Security Issues.................................................................................................................................31
2.4.1 Physical Security Issues............................................................................................................31
2.4.2 Security Issues..........................................................................................................................32
2.4.2.4 Internet Security protection................................................................................................33
2.5 Service Issues..................................................................................................................................34
Abstract.......................................................................................................................................................1
List of Figures.............................................................................................................................................6
List of tables................................................................................................................................................7
1.0 Introduction.........................................................................................................................................8
1.1 Research Question.........................................................................................................................10
1.1.1 Research Aim........................................................................................................................10
1.1.2 Research Objective................................................................................................................11
1.2 Heeley trust Overview.........................................................................................................................12
1.2.1 Meersbrook Hall...........................................................................................................................12
1.2.2 Head Quarter (HQ).......................................................................................................................13
1.2.3 SUM Studio..................................................................................................................................13
1.3 Current Network Design..................................................................................................................13
1.3.1 Meersbrook Hall (MH).................................................................................................................15
1.3.2 Head Quarter (HQ)........................................................................................................................19
1.3.3 Sum Studio...................................................................................................................................21
1.4 Services...............................................................................................................................................24
Chapter Two..............................................................................................................................................26
2.0 Literature Review............................................................................................................................26
2.1 Company.........................................................................................................................................26
2.2 The issues with the current design....................................................................................................27
2.2.1 Flat Network...........................................................................................................................27
2.2.2 Scalability................................................................................................................................28
2.2.3 Redundancy and resiliency....................................................................................................29
2.2.4 WAN........................................................................................................................................30
2.2.5 Internet Service Providers (ISP)...............................................................................................30
2.2.6 Issues with wireless..................................................................................................................30
2.2.7 Network Audit..........................................................................................................................31
2.4 Security Issues.................................................................................................................................31
2.4.1 Physical Security Issues............................................................................................................31
2.4.2 Security Issues..........................................................................................................................32
2.4.2.4 Internet Security protection................................................................................................33
2.5 Service Issues..................................................................................................................................34
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.5.1 Standalone servers (AD)...............................................................................................................34
2.5.2 The lack of Central credentials.....................................................................................................34
2.5.3 DHCP...........................................................................................................................................34
2.5.4 Remote Desktop service (RDS)....................................................................................................35
2.5.5 VoIP system..................................................................................................................................35
2.5.6 File service...................................................................................................................................35
2.5.7 Lack the controlling/filtering web traffic......................................................................................35
2.6 Additional Issues.............................................................................................................................36
2.6.1 Lack of network Monitoring/scanning tools.................................................................................36
2.7 Chapter Summary................................................................................................................................36
Chapter Three............................................................................................................................................37
3.0 Research Methodology........................................................................................................................37
3.1 Research at a Glance............................................................................................................................37
3.2 Research Background..........................................................................................................................37
3.2.1 Inductive Research...........................................................................................................................37
3.2.2 Qualitative Research.....................................................................................................................38
3.2.3 Quantitative Research...................................................................................................................38
3.3 Research Method applied....................................................................................................................39
Chapter Four..............................................................................................................................................41
4.1 Introduction.....................................................................................................................................41
4.2 Company Background.........................................................................................................................42
4.2.1 HT Organization goals and Constraints........................................................................................42
4.2.2 HT Technical and Constraints......................................................................................................43
4.3 Proposed Solution................................................................................................................................43
4.3.1 Design...........................................................................................................................................43
4.3.1.1 Hierarchy network topology..................................................................................................45
4.3.1.2 Three tiers hierarchical model....................................................................................................46
4.3.1.3 Two-Tier / Collapse Core network architecture................................................................47
4.3.1.4 Modular Design....................................................................................................................47
4.3.1.5 Analyzing technical needs and Tradeoff................................................................................48
4.3.1.7 High availability....................................................................................................................49
4.3.1.8 VLAN, segmentation and inter VLAN routing......................................................................50
4.3.2 Security.........................................................................................................................................52
2.5.2 The lack of Central credentials.....................................................................................................34
2.5.3 DHCP...........................................................................................................................................34
2.5.4 Remote Desktop service (RDS)....................................................................................................35
2.5.5 VoIP system..................................................................................................................................35
2.5.6 File service...................................................................................................................................35
2.5.7 Lack the controlling/filtering web traffic......................................................................................35
2.6 Additional Issues.............................................................................................................................36
2.6.1 Lack of network Monitoring/scanning tools.................................................................................36
2.7 Chapter Summary................................................................................................................................36
Chapter Three............................................................................................................................................37
3.0 Research Methodology........................................................................................................................37
3.1 Research at a Glance............................................................................................................................37
3.2 Research Background..........................................................................................................................37
3.2.1 Inductive Research...........................................................................................................................37
3.2.2 Qualitative Research.....................................................................................................................38
3.2.3 Quantitative Research...................................................................................................................38
3.3 Research Method applied....................................................................................................................39
Chapter Four..............................................................................................................................................41
4.1 Introduction.....................................................................................................................................41
4.2 Company Background.........................................................................................................................42
4.2.1 HT Organization goals and Constraints........................................................................................42
4.2.2 HT Technical and Constraints......................................................................................................43
4.3 Proposed Solution................................................................................................................................43
4.3.1 Design...........................................................................................................................................43
4.3.1.1 Hierarchy network topology..................................................................................................45
4.3.1.2 Three tiers hierarchical model....................................................................................................46
4.3.1.3 Two-Tier / Collapse Core network architecture................................................................47
4.3.1.4 Modular Design....................................................................................................................47
4.3.1.5 Analyzing technical needs and Tradeoff................................................................................48
4.3.1.7 High availability....................................................................................................................49
4.3.1.8 VLAN, segmentation and inter VLAN routing......................................................................50
4.3.2 Security.........................................................................................................................................52
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4.3.2.1 Hierarchical topology Segmentation and layer3 Routing.......................................................52
4.3.2.2 Physical Security – server farm..............................................................................................52
4.3.2.3 DMZ......................................................................................................................................52
4.3.2.4 Internet security protection....................................................................................................53
4.3.2.5 Access layer security.............................................................................................................53
4.3.3 Services........................................................................................................................................54
4.3.3.1 Standalone servers (Active Directory service AD) & Central credentials..............................54
4.3.3.3 DHCP....................................................................................................................................55
4.3.3.3 DNS Service..........................................................................................................................55
4.3.3.4 Remote Desktop service (RDS).............................................................................................55
4.3.3.5 Controlling/filtering web traffic.............................................................................................55
4.3.4 Other network...............................................................................................................................56
4.3.5 WAN – VPN - Edge connectivity.................................................................................................56
4.3.6 Network Manageability................................................................................................................56
4.3.7 ISP................................................................................................................................................57
4.3.8 Data storage..................................................................................................................................57
4.3.9 Hot Standby Routing Protocol......................................................................................................57
4.3.10 Virtual Private Network VPN and Dynamic Multiple VPN DMVPN........................................58
4.4 Logical Network Design......................................................................................................................58
4.5 Physical network design......................................................................................................................61
CHAPTER FIVE.......................................................................................................................................66
5.0 Conclusion..........................................................................................................................................66
5.1 Limitation and Possible Future Enhancement................................................................................66
Use multiprotocol label switching (MPLS) technology.............................................................66
Using Dynamic Multiple VPN (DMVPN).................................................................................67
Using GLP.................................................................................................................................67
Using VSS in the core-distribution layer...................................................................................67
The use of the concepts of virtualization within a network design.............................................67
6.0 Table Index..........................................................................................................................................69
References.................................................................................................................................................75
4.3.2.2 Physical Security – server farm..............................................................................................52
4.3.2.3 DMZ......................................................................................................................................52
4.3.2.4 Internet security protection....................................................................................................53
4.3.2.5 Access layer security.............................................................................................................53
4.3.3 Services........................................................................................................................................54
4.3.3.1 Standalone servers (Active Directory service AD) & Central credentials..............................54
4.3.3.3 DHCP....................................................................................................................................55
4.3.3.3 DNS Service..........................................................................................................................55
4.3.3.4 Remote Desktop service (RDS).............................................................................................55
4.3.3.5 Controlling/filtering web traffic.............................................................................................55
4.3.4 Other network...............................................................................................................................56
4.3.5 WAN – VPN - Edge connectivity.................................................................................................56
4.3.6 Network Manageability................................................................................................................56
4.3.7 ISP................................................................................................................................................57
4.3.8 Data storage..................................................................................................................................57
4.3.9 Hot Standby Routing Protocol......................................................................................................57
4.3.10 Virtual Private Network VPN and Dynamic Multiple VPN DMVPN........................................58
4.4 Logical Network Design......................................................................................................................58
4.5 Physical network design......................................................................................................................61
CHAPTER FIVE.......................................................................................................................................66
5.0 Conclusion..........................................................................................................................................66
5.1 Limitation and Possible Future Enhancement................................................................................66
Use multiprotocol label switching (MPLS) technology.............................................................66
Using Dynamic Multiple VPN (DMVPN).................................................................................67
Using GLP.................................................................................................................................67
Using VSS in the core-distribution layer...................................................................................67
The use of the concepts of virtualization within a network design.............................................67
6.0 Table Index..........................................................................................................................................69
References.................................................................................................................................................75

List of Figures
Figure 1 HT Logical Network Current Design..............................................................................11
Figure 2 MH Network Design.......................................................................................................13
Figure 3 MH Network Physical plan.............................................................................................15
Figure 4 HQ Current Logical Network Design.............................................................................17
Figure 5 HQ Network Design Physical Plan.................................................................................18
Figure 6 Sum Studio Logical Network Design..............................................................................21
Figure 7 Sum Studio Network Physical Plan................................................................................22
Figure 8 flat network design model...............................................................................................27
Figure 9 Inductive research Diagram............................................................................................37
Figure 10 (PPDIOO Network Lifecycle Influences Design (Wilkins, 2011)...............................40
Figure 11 Hierarchical Network....................................................................................................44
Figure 12 Layers in the Hierarchical Model (Tiso et al., 2011)...................................................45
Figure 13 Collapse Core Design (Brown & Burns, 2015).............................................................46
Figure 14 Heeley Trust Physical Design.......................................................................................57
Figure 15 Head Quarter Physical Design......................................................................................58
Figure 16 SUM STUDIO Physical Design....................................................................................59
Figure 17 Logical Network Design...............................................................................................60
Figure 1 HT Logical Network Current Design..............................................................................11
Figure 2 MH Network Design.......................................................................................................13
Figure 3 MH Network Physical plan.............................................................................................15
Figure 4 HQ Current Logical Network Design.............................................................................17
Figure 5 HQ Network Design Physical Plan.................................................................................18
Figure 6 Sum Studio Logical Network Design..............................................................................21
Figure 7 Sum Studio Network Physical Plan................................................................................22
Figure 8 flat network design model...............................................................................................27
Figure 9 Inductive research Diagram............................................................................................37
Figure 10 (PPDIOO Network Lifecycle Influences Design (Wilkins, 2011)...............................40
Figure 11 Hierarchical Network....................................................................................................44
Figure 12 Layers in the Hierarchical Model (Tiso et al., 2011)...................................................45
Figure 13 Collapse Core Design (Brown & Burns, 2015).............................................................46
Figure 14 Heeley Trust Physical Design.......................................................................................57
Figure 15 Head Quarter Physical Design......................................................................................58
Figure 16 SUM STUDIO Physical Design....................................................................................59
Figure 17 Logical Network Design...............................................................................................60
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

List of tables
Table 1 Meersbrook Hall network.................................................................................................63
Table 2 HQ Network.....................................................................................................................65
Table 3 Sum Studio Network........................................................................................................66
Table 4 new design IP addresses and VLANs (Meersbrook)........................................................68
Table 5 new design IP addresses and VLANs – Head Quarter.....................................................68
Table 6 new design IP addresses and VLANs – SUM Studios.....................................................68
Table 1 Meersbrook Hall network.................................................................................................63
Table 2 HQ Network.....................................................................................................................65
Table 3 Sum Studio Network........................................................................................................66
Table 4 new design IP addresses and VLANs (Meersbrook)........................................................68
Table 5 new design IP addresses and VLANs – Head Quarter.....................................................68
Table 6 new design IP addresses and VLANs – SUM Studios.....................................................68
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Chapter One
1.0 Introduction
In networking design, there are some significant things that one need to understand. The
first step is that one must understand the problems before anything else. In understanding such
problems, one will be able to go through a dissertation with ease. The primary idea to be
explained in this research is to propose a network design that can be used by Heeley Trust
Organization for the existing three locales and thus helping them in building a network design
that will address all the objectives of the business.
In achieving this, the first process is to prepare, second is a plan and then design the
network, as a roadmap to achieve these goals. In the current era, many changes in computer
network landscape have made the network services to be critical features that make network
design of the 3rd Generation to be scalable and much more successful. The definition of such a
problem has some significant features that most designers of the network will have first to
understand the existing problems in the network. After understanding the problem, the designer
will have to analyze the process and must consider several optimization parameters that must be
selected and analyzed during the analysis process (McCabe, 2010).
The report will be explained in five chapters where each chapter defines and explains the
significant requirements. Chapter one is used to define and analyze the current network design
and explain the Heeley trust business objective. Chapter two is mainly giving an analysis of the
current network and consider the risk analysis that defines the current issues in the network. The
existing issues will help in building up a propel successful network topology and thus giving an
understanding and clarification of the relationship among the different network services.
Chapter three is a discussion of the research methodology and explain some of the reason to why
1.0 Introduction
In networking design, there are some significant things that one need to understand. The
first step is that one must understand the problems before anything else. In understanding such
problems, one will be able to go through a dissertation with ease. The primary idea to be
explained in this research is to propose a network design that can be used by Heeley Trust
Organization for the existing three locales and thus helping them in building a network design
that will address all the objectives of the business.
In achieving this, the first process is to prepare, second is a plan and then design the
network, as a roadmap to achieve these goals. In the current era, many changes in computer
network landscape have made the network services to be critical features that make network
design of the 3rd Generation to be scalable and much more successful. The definition of such a
problem has some significant features that most designers of the network will have first to
understand the existing problems in the network. After understanding the problem, the designer
will have to analyze the process and must consider several optimization parameters that must be
selected and analyzed during the analysis process (McCabe, 2010).
The report will be explained in five chapters where each chapter defines and explains the
significant requirements. Chapter one is used to define and analyze the current network design
and explain the Heeley trust business objective. Chapter two is mainly giving an analysis of the
current network and consider the risk analysis that defines the current issues in the network. The
existing issues will help in building up a propel successful network topology and thus giving an
understanding and clarification of the relationship among the different network services.
Chapter three is a discussion of the research methodology and explain some of the reason to why

a specific research method will be used in data collection, investigate the current issues in the
existing network and give an explanation to as why they have been selected. Ideally, based on
the current issues beside HT objective and goals, Chapter five will give a solution to the
problems discussed in chapter three by redesigning the network topology architecture and
selected topology.
This chapter will give an explanation of what to be researched and give an analysis of the
current network design, but before starting to investigate and analyze the network and services.
Also, there will be a review of Heeley Trust background, highlighting all the integrated services
and functionality provided to the community with regards to the network architecture and
topology. This has been highlighted and outlined as follows.
Chapter 1: This defines and analyses the current network design. It also explains the Heeley
trust business objectives.
Chapter 2: This will give an analysis of the current network and consider the risk analysis
by defining the current issues. It will be used in building up a propel successful network
topology the relationship among the different services that included in the network must be
clarified and understood.
Chapter 3: this offers a research methodology and explains the reason why a specific
research method will be used to conduct gathering the data and investigating the current
network issues and also will explain why they have been selected.
Chapter 4: Based on the current issues beside HT objective and goals will solve these
problems by redesign the network topology architecture and discuss the topology choices.
Heeley Trust is proposing to redesign its network in all its sites.There are three main sites that
HT would like to redesign and implement the network in each site and connect these sites
existing network and give an explanation to as why they have been selected. Ideally, based on
the current issues beside HT objective and goals, Chapter five will give a solution to the
problems discussed in chapter three by redesigning the network topology architecture and
selected topology.
This chapter will give an explanation of what to be researched and give an analysis of the
current network design, but before starting to investigate and analyze the network and services.
Also, there will be a review of Heeley Trust background, highlighting all the integrated services
and functionality provided to the community with regards to the network architecture and
topology. This has been highlighted and outlined as follows.
Chapter 1: This defines and analyses the current network design. It also explains the Heeley
trust business objectives.
Chapter 2: This will give an analysis of the current network and consider the risk analysis
by defining the current issues. It will be used in building up a propel successful network
topology the relationship among the different services that included in the network must be
clarified and understood.
Chapter 3: this offers a research methodology and explains the reason why a specific
research method will be used to conduct gathering the data and investigating the current
network issues and also will explain why they have been selected.
Chapter 4: Based on the current issues beside HT objective and goals will solve these
problems by redesign the network topology architecture and discuss the topology choices.
Heeley Trust is proposing to redesign its network in all its sites.There are three main sites that
HT would like to redesign and implement the network in each site and connect these sites
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
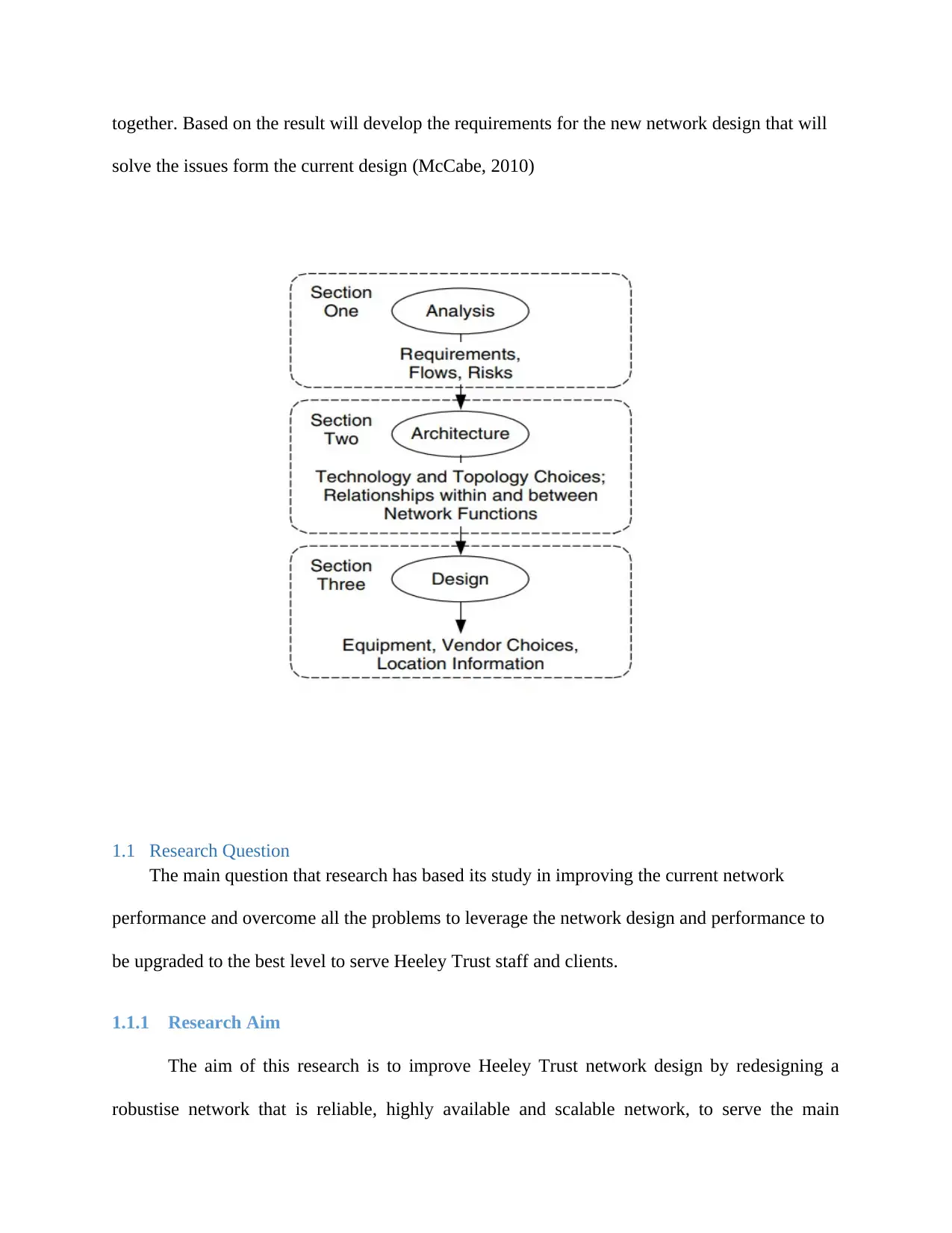
together. Based on the result will develop the requirements for the new network design that will
solve the issues form the current design (McCabe, 2010)
1.1 Research Question
The main question that research has based its study in improving the current network
performance and overcome all the problems to leverage the network design and performance to
be upgraded to the best level to serve Heeley Trust staff and clients.
1.1.1 Research Aim
The aim of this research is to improve Heeley Trust network design by redesigning a
robustise network that is reliable, highly available and scalable network, to serve the main
solve the issues form the current design (McCabe, 2010)
1.1 Research Question
The main question that research has based its study in improving the current network
performance and overcome all the problems to leverage the network design and performance to
be upgraded to the best level to serve Heeley Trust staff and clients.
1.1.1 Research Aim
The aim of this research is to improve Heeley Trust network design by redesigning a
robustise network that is reliable, highly available and scalable network, to serve the main
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

objective of Heeley Trust functionality. Ideally, by increasing the bandwidth from 100Mbs to
1000Mbs, implement redundant solutions like network devices and links, securing WAN
connection between the three sites by implementing VPN connection. This has enhanced the the
network security by introducing a physical firewalls and segment the network by creating
separate VLANs to prevent an authorised users to access critical information.
1.1.2 Research Objective
In achieving the research aims the following steps should be followed in all ways
Step 1: Propose a new network design based on the result that have been gathered from step 2.
Step 2: Will address recommendation for future network development regarding further
expansion in Heeley Trust company.
Step 3: To find what is the suitable research methodology to be used in during the research.
Step 4: Analysing the current network design and investigate the network performance to
address the issues that affect the reliability of the network.
1000Mbs, implement redundant solutions like network devices and links, securing WAN
connection between the three sites by implementing VPN connection. This has enhanced the the
network security by introducing a physical firewalls and segment the network by creating
separate VLANs to prevent an authorised users to access critical information.
1.1.2 Research Objective
In achieving the research aims the following steps should be followed in all ways
Step 1: Propose a new network design based on the result that have been gathered from step 2.
Step 2: Will address recommendation for future network development regarding further
expansion in Heeley Trust company.
Step 3: To find what is the suitable research methodology to be used in during the research.
Step 4: Analysing the current network design and investigate the network performance to
address the issues that affect the reliability of the network.

1.2 Heeley trust Overview
HT is an anchor community organization that was established in 1996, located at
Sheffield (Heeley Trust, 2018). Ideally, in the beginning, it was established to develop the
Heeley area, then it expanded its provision to serve all Sheffield. Heeley Trust has about 50
employees who usually support or offer provisions to approximately 500 customers or clients,
and at the same time, they are running a various number of projects. The main current projects
are Heeley People’s Park, Big Boulder & Heeley Festival, Heeley Institute, Sheffield Online,
Meersbrook Hall, Recycle Bikes, Sum Studios, and Sheffield Media Productions. Heeley Trust
three main buildings are: Head Quarter, Meersbrook Hall and Sum Studio
1.2.1 Meersbrook Hall
Ideally, at Meersbrook Hall they are running Sheffield Online project which
offers adult learning and wellbeing and also promoting the Digital Inclusion concept to tackle the
Digital exclusion issue in Sheffield. They also run classes, insights and outreach sessions as they
have a bank of Digital Champion volunteers who help them with onsite and outreach classes.
According to the statistic made in 2012, 1 out of 5 people in Sheffield is usually digital excluded,
by providing digital inclusion drop-in sessions across Sheffield to provide adult people with
basic tuition about how to use the computer and online activities. These sessions are usually held
in libraries, community centers, TARAs, GPs, hospitals, and other venues
HT is an anchor community organization that was established in 1996, located at
Sheffield (Heeley Trust, 2018). Ideally, in the beginning, it was established to develop the
Heeley area, then it expanded its provision to serve all Sheffield. Heeley Trust has about 50
employees who usually support or offer provisions to approximately 500 customers or clients,
and at the same time, they are running a various number of projects. The main current projects
are Heeley People’s Park, Big Boulder & Heeley Festival, Heeley Institute, Sheffield Online,
Meersbrook Hall, Recycle Bikes, Sum Studios, and Sheffield Media Productions. Heeley Trust
three main buildings are: Head Quarter, Meersbrook Hall and Sum Studio
1.2.1 Meersbrook Hall
Ideally, at Meersbrook Hall they are running Sheffield Online project which
offers adult learning and wellbeing and also promoting the Digital Inclusion concept to tackle the
Digital exclusion issue in Sheffield. They also run classes, insights and outreach sessions as they
have a bank of Digital Champion volunteers who help them with onsite and outreach classes.
According to the statistic made in 2012, 1 out of 5 people in Sheffield is usually digital excluded,
by providing digital inclusion drop-in sessions across Sheffield to provide adult people with
basic tuition about how to use the computer and online activities. These sessions are usually held
in libraries, community centers, TARAs, GPs, hospitals, and other venues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 80
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

