University Report: Assessment of the Department of Defense EA Program
VerifiedAdded on 2023/06/04
|12
|3455
|124
Report
AI Summary
This report assesses the Department of Defense (DoD) Enterprise Architecture (EA) program, focusing on its challenges and proposing solutions. The study, conducted from the perspective of an expert consultant, examines the program's goals, necessary conditions for success, and identifies key issues such as ineffective management, lack of communication, and undeveloped program plans. The report uses models like the Current Running Tree and Evaporating Cloud Conflict chart to analyze the root causes of these problems and suggest improvements. The analysis highlights the need for better governance, active configuration management, and the development of measurable program plans. The report recommends assigning a new leadership team to better manage and utilize the existing structure and protocol, aiming to optimize the DoD's business processes and improve alignment between IT and business concerns. The overall goal is to enhance the usefulness and effectiveness of the DoD EA program, ultimately leading to cost savings and improved information sharing.

Running head: ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Name of the Student
Name of the University
Author note
ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Introduction
The Department of Defense is unable to achieve the goals and success because of the various
problems. The Department of Defense is unable to follow the recommendations of GEO, and
there has been rise several issues which mainly rose due to the lacking of proper managerial
function. According to the theory of constraints, the organisation needs to change the model for
profit improvement, and its important concept is that every organisation should contain at least
one constraint. The constraint is the factor, which limits the organisation from getting what it
strives for making a profit. For the Department of Defense, there are several constraints, and it
needs to be recovered by identifying the system constraints, deciding how to exploit the
constraint, subordinating everything else the constraint, elevating the constraint and then again
continuing this for getting the desired outcome (Navarra et al., 2017). The logical thinking needs
to be adopted by the Department of Defence, as its main objective is to increase the company’s
profit. The logical thinking is mainly done by specifying the value of the services or product
from the perspective of the customer, identifying the value streams, flow in the production and
perfection in the production process (Craib, 2015). This study focuses the issues associated with
the DoD EA program and the issues are identified and the reason behind it from the perspective
of an expert consultant. This study will develop the models and explain them to address the
issues rose with the DoD EA program.
Task 1
The purpose of Department of Defense EA program is the greater alignment between IT and the
business concerns and the main purpose of the enterprise architecture is to guide the process if
planning and designing the IT capabilities of the enterprise to meet the desired organisation
Introduction
The Department of Defense is unable to achieve the goals and success because of the various
problems. The Department of Defense is unable to follow the recommendations of GEO, and
there has been rise several issues which mainly rose due to the lacking of proper managerial
function. According to the theory of constraints, the organisation needs to change the model for
profit improvement, and its important concept is that every organisation should contain at least
one constraint. The constraint is the factor, which limits the organisation from getting what it
strives for making a profit. For the Department of Defense, there are several constraints, and it
needs to be recovered by identifying the system constraints, deciding how to exploit the
constraint, subordinating everything else the constraint, elevating the constraint and then again
continuing this for getting the desired outcome (Navarra et al., 2017). The logical thinking needs
to be adopted by the Department of Defence, as its main objective is to increase the company’s
profit. The logical thinking is mainly done by specifying the value of the services or product
from the perspective of the customer, identifying the value streams, flow in the production and
perfection in the production process (Craib, 2015). This study focuses the issues associated with
the DoD EA program and the issues are identified and the reason behind it from the perspective
of an expert consultant. This study will develop the models and explain them to address the
issues rose with the DoD EA program.
Task 1
The purpose of Department of Defense EA program is the greater alignment between IT and the
business concerns and the main purpose of the enterprise architecture is to guide the process if
planning and designing the IT capabilities of the enterprise to meet the desired organisation

2ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
activities. The department of defence is required to develop the business enterprise architecture,
which covers all the defence business systems (Rouhani et al., 2013). This can be the guide for
the systems, and the architecture is intended to help for achieving the goals:
Enabling Department of Defense to meet the terms of all the applicable laws and
including the financial management, federal accounting and the requirements for
reporting
To permit, constrain and guide the operation of the defence business systems.
Department of Defense needs to produce timely, accurately and with the financial
information for managing the business.
The architecture helps in maintaining the systematic dimension of the performance levels
like the skill of producing relevant, reliable and time cost information (Evans et al.,
2015).
This architecture facilitates the combination of budget, accounting information and the
program information systems.
Achieving the intended outcomes, the department of defence will be able to use
architecture to realise the important benefits like the cost savings, avoidance and others.
Like if, the direct architecture permits and implements the practical system, which would
contribute to the increase in information sharing and improves the system ability
(Kotusev, 2016).
This is described in the statute that the Department of Defense’s business enterprise
architecture and the process re-engineering labours are not completely reaching the future
outcomes. In respect to the process re-engineering, the managers reported that the efforts were
effective for streamlining the business process. This is necessary for the Department of Defense
activities. The department of defence is required to develop the business enterprise architecture,
which covers all the defence business systems (Rouhani et al., 2013). This can be the guide for
the systems, and the architecture is intended to help for achieving the goals:
Enabling Department of Defense to meet the terms of all the applicable laws and
including the financial management, federal accounting and the requirements for
reporting
To permit, constrain and guide the operation of the defence business systems.
Department of Defense needs to produce timely, accurately and with the financial
information for managing the business.
The architecture helps in maintaining the systematic dimension of the performance levels
like the skill of producing relevant, reliable and time cost information (Evans et al.,
2015).
This architecture facilitates the combination of budget, accounting information and the
program information systems.
Achieving the intended outcomes, the department of defence will be able to use
architecture to realise the important benefits like the cost savings, avoidance and others.
Like if, the direct architecture permits and implements the practical system, which would
contribute to the increase in information sharing and improves the system ability
(Kotusev, 2016).
This is described in the statute that the Department of Defense’s business enterprise
architecture and the process re-engineering labours are not completely reaching the future
outcomes. In respect to the process re-engineering, the managers reported that the efforts were
effective for streamlining the business process. This is necessary for the Department of Defense
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
to improve the usefulness and the effectiveness of the business enterprises. The portfolio
managers have cited the challenges obstructing the usefulness and the efficiency of the initiatives
like the accessibility of the training, parochialism and the absence of the skilled and efficient
staff members and the cultural struggle to the changes. Department of Defense has opted for
various efforts of improvement to address few challenges. Although the extra work is needed for,
the managers for closing the gap provide the improvement and the suggestions. Most
importantly, the detection of the challenges helps to increase the usefulness and the efficiency of
these initiatives (Fischer et al., 2013).
This is necessary for the Department of Defense to adopt the various efforts to efficiently
modernise the nonintegrated and the duplicative business system and operation. This is also
necessary for the Department of Defense to advance and use the definite and explained business
entrepreneur structures. However, it does not contain such architecture and the products, which
has provided a sufficient amount of the utility to the effective guide and constrains the planned
systems investments (Smith, 2016). The necessary conditions, which are the recommendations
the department of the defence need to follow, and they are:
Department of Defense needs to develop an active governance structure and the active
communication strategy for achieving the stakeholders. In particular, the structure from
2001 lacks the authority and the effective responsibility. This also lacks the key units that
made up the structure that has not completed as per their charters (Wan, Luo, & Luo,
2014).
Department of Defense lacks the developed program plans, which identifies the
measurable goals for identifying the goals and measuring the outcomes that need to be
achieved. This also does not have any defined task to be performed for achieving the
to improve the usefulness and the effectiveness of the business enterprises. The portfolio
managers have cited the challenges obstructing the usefulness and the efficiency of the initiatives
like the accessibility of the training, parochialism and the absence of the skilled and efficient
staff members and the cultural struggle to the changes. Department of Defense has opted for
various efforts of improvement to address few challenges. Although the extra work is needed for,
the managers for closing the gap provide the improvement and the suggestions. Most
importantly, the detection of the challenges helps to increase the usefulness and the efficiency of
these initiatives (Fischer et al., 2013).
This is necessary for the Department of Defense to adopt the various efforts to efficiently
modernise the nonintegrated and the duplicative business system and operation. This is also
necessary for the Department of Defense to advance and use the definite and explained business
entrepreneur structures. However, it does not contain such architecture and the products, which
has provided a sufficient amount of the utility to the effective guide and constrains the planned
systems investments (Smith, 2016). The necessary conditions, which are the recommendations
the department of the defence need to follow, and they are:
Department of Defense needs to develop an active governance structure and the active
communication strategy for achieving the stakeholders. In particular, the structure from
2001 lacks the authority and the effective responsibility. This also lacks the key units that
made up the structure that has not completed as per their charters (Wan, Luo, & Luo,
2014).
Department of Defense lacks the developed program plans, which identifies the
measurable goals for identifying the goals and measuring the outcomes that need to be
achieved. This also does not have any defined task to be performed for achieving the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
goals and the required outcomes and the resources required for performing the task.
Department of Defense has also not assessed the workforce capabilities as a part of the
program planning, this is needed for the effective management of the architecture
labours, and it does not have any plan for doing so (Gottron et al., 2017).
Department of Defense needs to perform the active configuration management, and this
is the official approach in controlling the parts of the product for ensuring the integrity.
The configuration management plan and the charter of the configuration control board are
the drafts, and the board also has limited authority, even after the four years of
development, the department has not signed any configuration manager (Bernal et al.,
2016).
Department of Defense recognizes that all the above mentioned weakness should be addressed
and this has just allotted the new business enterprise architecture leadership team. Department of
Defense has also begun steps and stated the intentions to revise the governance structure and
develop the program baseline, which will be used as the oversight and the managerial tool to
assign the resources, measures, reports the progress and manages risks. Department of Defense
also revises the architecture scope and establishes the fresh approaches for developing the scope
of the architecture. However, there are much of the remains, which are needed to be
accomplished for the establishment of the effective architecture program; until this is done the
business system, modernization effort will remain at the high-risk (O'Rourke, 2015).
Task 2
Unhappy
stakeholders
Ineffective
configuration
management
Weaken
integrity
Undeveloped
program plans
Undesirable effect Undesirable effect Undesirable effect Undesirable effect
goals and the required outcomes and the resources required for performing the task.
Department of Defense has also not assessed the workforce capabilities as a part of the
program planning, this is needed for the effective management of the architecture
labours, and it does not have any plan for doing so (Gottron et al., 2017).
Department of Defense needs to perform the active configuration management, and this
is the official approach in controlling the parts of the product for ensuring the integrity.
The configuration management plan and the charter of the configuration control board are
the drafts, and the board also has limited authority, even after the four years of
development, the department has not signed any configuration manager (Bernal et al.,
2016).
Department of Defense recognizes that all the above mentioned weakness should be addressed
and this has just allotted the new business enterprise architecture leadership team. Department of
Defense has also begun steps and stated the intentions to revise the governance structure and
develop the program baseline, which will be used as the oversight and the managerial tool to
assign the resources, measures, reports the progress and manages risks. Department of Defense
also revises the architecture scope and establishes the fresh approaches for developing the scope
of the architecture. However, there are much of the remains, which are needed to be
accomplished for the establishment of the effective architecture program; until this is done the
business system, modernization effort will remain at the high-risk (O'Rourke, 2015).
Task 2
Unhappy
stakeholders
Ineffective
configuration
management
Weaken
integrity
Undeveloped
program plans
Undesirable effect Undesirable effect Undesirable effect Undesirable effect
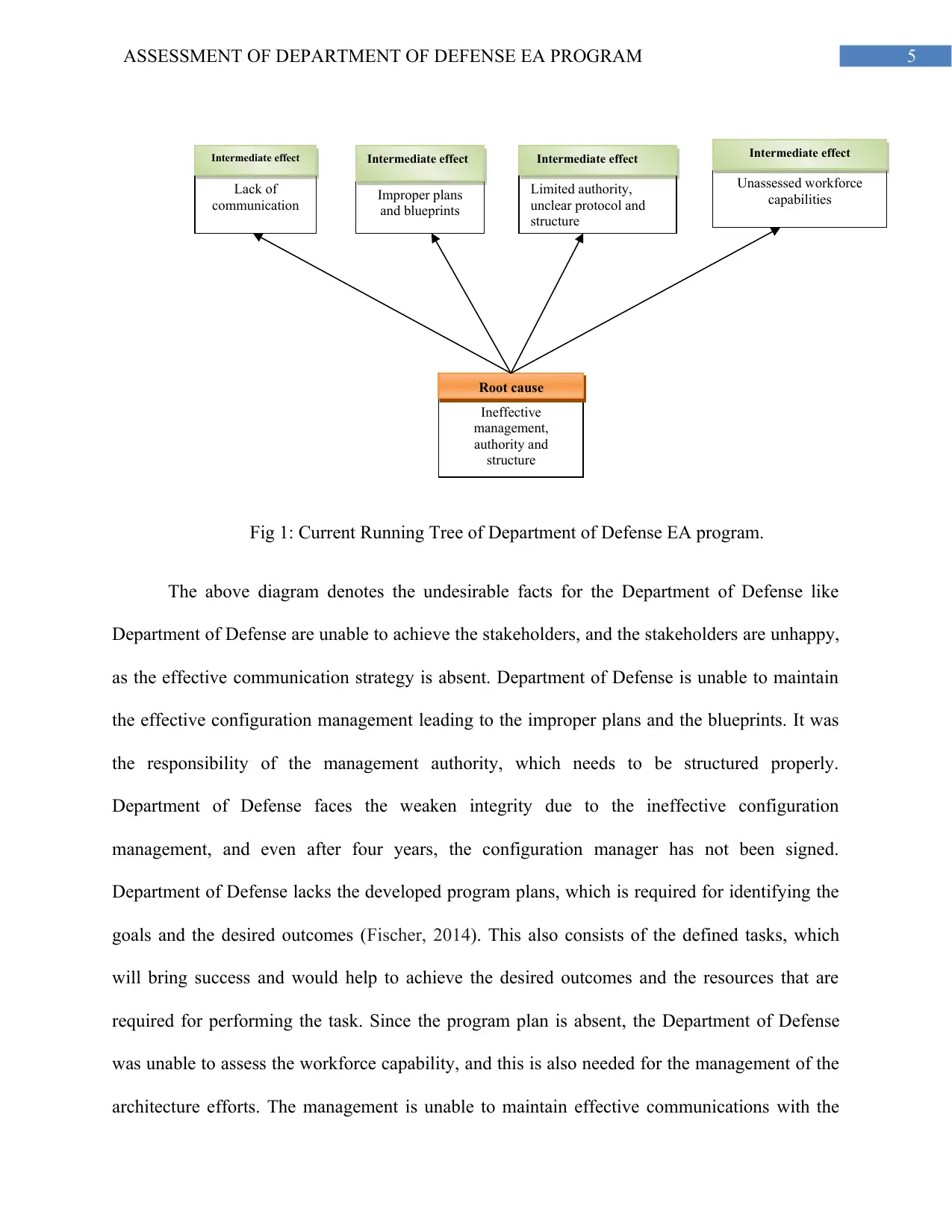
5ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Fig 1: Current Running Tree of Department of Defense EA program.
The above diagram denotes the undesirable facts for the Department of Defense like
Department of Defense are unable to achieve the stakeholders, and the stakeholders are unhappy,
as the effective communication strategy is absent. Department of Defense is unable to maintain
the effective configuration management leading to the improper plans and the blueprints. It was
the responsibility of the management authority, which needs to be structured properly.
Department of Defense faces the weaken integrity due to the ineffective configuration
management, and even after four years, the configuration manager has not been signed.
Department of Defense lacks the developed program plans, which is required for identifying the
goals and the desired outcomes (Fischer, 2014). This also consists of the defined tasks, which
will bring success and would help to achieve the desired outcomes and the resources that are
required for performing the task. Since the program plan is absent, the Department of Defense
was unable to assess the workforce capability, and this is also needed for the management of the
architecture efforts. The management is unable to maintain effective communications with the
Lack of
communication Improper plans
and blueprints
Limited authority,
unclear protocol and
structure
Unassessed workforce
capabilities
Ineffective
management,
authority and
structure
Intermediate effect Intermediate effect Intermediate effect Intermediate effect
Root cause
Fig 1: Current Running Tree of Department of Defense EA program.
The above diagram denotes the undesirable facts for the Department of Defense like
Department of Defense are unable to achieve the stakeholders, and the stakeholders are unhappy,
as the effective communication strategy is absent. Department of Defense is unable to maintain
the effective configuration management leading to the improper plans and the blueprints. It was
the responsibility of the management authority, which needs to be structured properly.
Department of Defense faces the weaken integrity due to the ineffective configuration
management, and even after four years, the configuration manager has not been signed.
Department of Defense lacks the developed program plans, which is required for identifying the
goals and the desired outcomes (Fischer, 2014). This also consists of the defined tasks, which
will bring success and would help to achieve the desired outcomes and the resources that are
required for performing the task. Since the program plan is absent, the Department of Defense
was unable to assess the workforce capability, and this is also needed for the management of the
architecture efforts. The management is unable to maintain effective communications with the
Lack of
communication Improper plans
and blueprints
Limited authority,
unclear protocol and
structure
Unassessed workforce
capabilities
Ineffective
management,
authority and
structure
Intermediate effect Intermediate effect Intermediate effect Intermediate effect
Root cause
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
stakeholders. The management needs to have an effective communication strategy, which is the
root cause of not being able to retain the stakeholders (Tate et al., 2015). The management
authority needs to be structured, and they need to be more trained for recovering the weakness,
and the program plan needs to be done by the management. This is the most important factor,
which the management needs to maintain to figure out the aims of the company. The
management also needs to figure out and measures the future goals of the company, and it is also
important for the management to assess the workforce capability which cannot be assessed due
to the absence of the proper program plan (White, Fisch, & Pooch, 2017).
Task 3
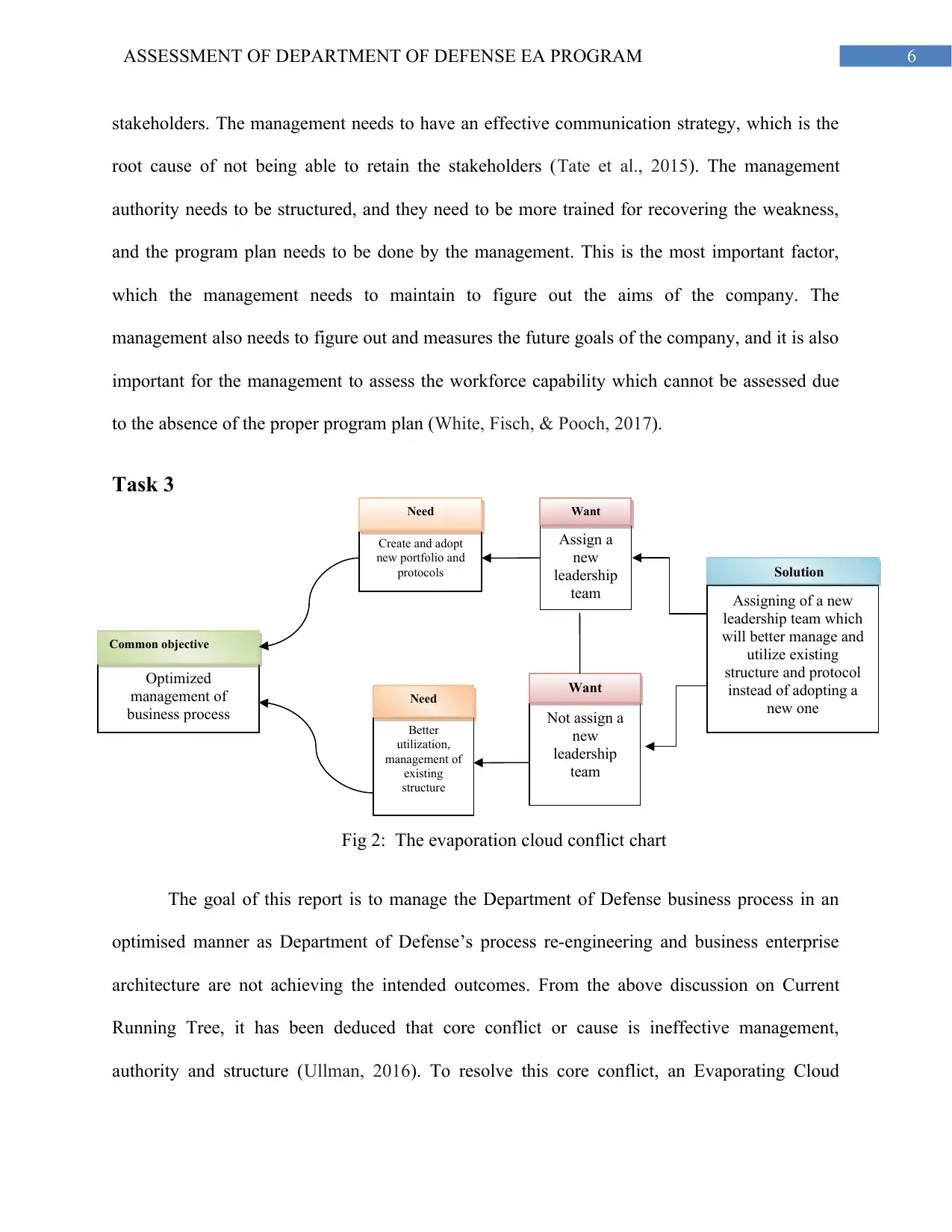
Fig 2: The evaporation cloud conflict chart
The goal of this report is to manage the Department of Defense business process in an
optimised manner as Department of Defense’s process re-engineering and business enterprise
architecture are not achieving the intended outcomes. From the above discussion on Current
Running Tree, it has been deduced that core conflict or cause is ineffective management,
authority and structure (Ullman, 2016). To resolve this core conflict, an Evaporating Cloud
Optimized
management of
business process
Create and adopt
new portfolio and
protocols
Assign a
new
leadership
team
Better
utilization,
management of
existing
structure
Not assign a
new
leadership
team
Assigning of a new
leadership team which
will better manage and
utilize existing
structure and protocol
instead of adopting a
new one
Common objective
Need Want
Solution
Need Want
stakeholders. The management needs to have an effective communication strategy, which is the
root cause of not being able to retain the stakeholders (Tate et al., 2015). The management
authority needs to be structured, and they need to be more trained for recovering the weakness,
and the program plan needs to be done by the management. This is the most important factor,
which the management needs to maintain to figure out the aims of the company. The
management also needs to figure out and measures the future goals of the company, and it is also
important for the management to assess the workforce capability which cannot be assessed due
to the absence of the proper program plan (White, Fisch, & Pooch, 2017).
Task 3
Fig 2: The evaporation cloud conflict chart
The goal of this report is to manage the Department of Defense business process in an
optimised manner as Department of Defense’s process re-engineering and business enterprise
architecture are not achieving the intended outcomes. From the above discussion on Current
Running Tree, it has been deduced that core conflict or cause is ineffective management,
authority and structure (Ullman, 2016). To resolve this core conflict, an Evaporating Cloud
Optimized
management of
business process
Create and adopt
new portfolio and
protocols
Assign a
new
leadership
team
Better
utilization,
management of
existing
structure
Not assign a
new
leadership
team
Assigning of a new
leadership team which
will better manage and
utilize existing
structure and protocol
instead of adopting a
new one
Common objective
Need Want
Solution
Need Want
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Conflict chart has been prepared based on those perceived issues. The Evaporating Cloud
Conflict chart can be seen below in figure 2. As the Evaporating Cloud Conflict structure
dictates, it has two conflicting ‘Want’, their prerequisite ‘Need’, a shared objective or goal and
injection, which can also be perceived as a solution. In this conflict cloud, the two conflicting
‘Want’ is as follows: assigning a new leadership team and not assigning a new leadership team
(Boito et al., 2018). The prerequisite for assigning a new leadership team is that it will help
develop and adopt new policies and protocol, which will help increase the efficiency of
Department of Defense (Hudson, & Tsurumaki, 2017). On the other hand, the prerequisite for
not assigning a new leadership team is that the current leadership team will utilise the existing
structure and workforce in a better way to increase the efficiency of the organisation (Bulluss et
al., 2014). The prerequisite for the both ‘Want’ serves the commonly shared objective, which is
to better management of the business process of Department of Defense. However, the
prerequisites are also at odds with each other. If no new leadership team were assigned, they
could not implement new policies or ideas whereas if new leadership were to be assigned, they
would reconstruct the existing structure, which will be a waste of existing structure. Hence, there
are two conflicting ‘Want’ for this particular cause. Both pathways can be able to achieve the
shared objective in a standalone manner. However, it might not be the most optimised ways to
achieve the common goal for either of the arguments. The assumptions between these two
arguments are that one cannot co-exist with the other even though neither of them is the most
optimized pathways. Hence, there is a need for a solution which is also known as ‘Injection’ in
the Evaporating Cloud Conflict structure. For this study, the injection can be the assigning of a
new leadership team which will implement new structure and policies using the existing
workforce. In this way, both of the problems can be handled at once, and conflict between the
Conflict chart has been prepared based on those perceived issues. The Evaporating Cloud
Conflict chart can be seen below in figure 2. As the Evaporating Cloud Conflict structure
dictates, it has two conflicting ‘Want’, their prerequisite ‘Need’, a shared objective or goal and
injection, which can also be perceived as a solution. In this conflict cloud, the two conflicting
‘Want’ is as follows: assigning a new leadership team and not assigning a new leadership team
(Boito et al., 2018). The prerequisite for assigning a new leadership team is that it will help
develop and adopt new policies and protocol, which will help increase the efficiency of
Department of Defense (Hudson, & Tsurumaki, 2017). On the other hand, the prerequisite for
not assigning a new leadership team is that the current leadership team will utilise the existing
structure and workforce in a better way to increase the efficiency of the organisation (Bulluss et
al., 2014). The prerequisite for the both ‘Want’ serves the commonly shared objective, which is
to better management of the business process of Department of Defense. However, the
prerequisites are also at odds with each other. If no new leadership team were assigned, they
could not implement new policies or ideas whereas if new leadership were to be assigned, they
would reconstruct the existing structure, which will be a waste of existing structure. Hence, there
are two conflicting ‘Want’ for this particular cause. Both pathways can be able to achieve the
shared objective in a standalone manner. However, it might not be the most optimised ways to
achieve the common goal for either of the arguments. The assumptions between these two
arguments are that one cannot co-exist with the other even though neither of them is the most
optimized pathways. Hence, there is a need for a solution which is also known as ‘Injection’ in
the Evaporating Cloud Conflict structure. For this study, the injection can be the assigning of a
new leadership team which will implement new structure and policies using the existing
workforce. In this way, both of the problems can be handled at once, and conflict between the

8ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
two ‘Want’ will dissolve. The new leadership team will be able to tackle the weakness, and the
authoritative problem showed by the existing leadership team (Fischer, 2014). Along with that,
they will also be able to make full use of existing structure and experienced workforce. This way
it will be a much-optimised pathway to achieve the commonly shared objectives. The solution or
injection also nullify the conflicts between two pathways and showed the way for better singular
alternative (Rouhani et al., 2015). To summarise, by using the Evaporating Cloud Conflict
model, this singular alternative way managed to avoid confrontation and creates a win-win
situation for the organisation for optimised management of the business process.
Conclusion
Therefore, from the above discussion, it can be concluded that the Department of Defense
is facing various issues, which are affecting the company’s profit and not allowing the company
to measure their goals. The Department of Defense has to structure the management department
as there is lacking proper effective communication with the stakeholders, customers and the
absence of proper program plan and others. The managerial department is required to be
structured by following the theory of constraints, which ensures that every company should have
at least one constraints and this constraint are identified in this study, which is needed to be
reduced by the logical thinking process. The main objective of the logical thinking and the theory
of constraints to increase the business profit of the company, which the Department of Defense is
lacking behind. The Department of Defense can be able to solve the issues by the theory of
constraints, logical thinking and following the recommendations.
two ‘Want’ will dissolve. The new leadership team will be able to tackle the weakness, and the
authoritative problem showed by the existing leadership team (Fischer, 2014). Along with that,
they will also be able to make full use of existing structure and experienced workforce. This way
it will be a much-optimised pathway to achieve the commonly shared objectives. The solution or
injection also nullify the conflicts between two pathways and showed the way for better singular
alternative (Rouhani et al., 2015). To summarise, by using the Evaporating Cloud Conflict
model, this singular alternative way managed to avoid confrontation and creates a win-win
situation for the organisation for optimised management of the business process.
Conclusion
Therefore, from the above discussion, it can be concluded that the Department of Defense
is facing various issues, which are affecting the company’s profit and not allowing the company
to measure their goals. The Department of Defense has to structure the management department
as there is lacking proper effective communication with the stakeholders, customers and the
absence of proper program plan and others. The managerial department is required to be
structured by following the theory of constraints, which ensures that every company should have
at least one constraints and this constraint are identified in this study, which is needed to be
reduced by the logical thinking process. The main objective of the logical thinking and the theory
of constraints to increase the business profit of the company, which the Department of Defense is
lacking behind. The Department of Defense can be able to solve the issues by the theory of
constraints, logical thinking and following the recommendations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
References
Bernal, W. N., Caballero, G. C., Sánchez, J. O., & Paéz-Logreira, H. (2016, May). Enterprise
architecture framework oriented to cloud computing services. In Computers
Communications and Control (ICCCC), 2016 6th International Conference on (pp. 64-
69). IEEE.
Boito, M., Conley, T., Fleming, J., Ramos, A., & Anania, K. (2018). Expanding Operating and
Support Cost Analysis for Major Programs During the DoD Acquisition Process.
Bulluss, G. J., O'Shea, K., Tay, N. T., & Pong, P. (2014, June). Innovations in understanding the
whole of Australian defence system of systems. In System of Systems Engineering
(SOSE), 2014 9th International Conference on (pp. 171-176). IEEE.
Craib, I. (2015). Modern social theory. Routledge.
Evans, W., Nielsen, P. E., Szekely, D. R., Bihm, J. W., Murray, E. A., Snider, J., & Abroms, L.
C. (2015). Dose-response effects of the text4baby mobile health program: randomised
controlled trial. JMIR mHealth and uHealth, 3(1).
Fischer, E. A. (2014). Federal laws relating to cybersecurity: Overview of major issues, current
laws, and proposed legislation. Congressional Research Service, 7(5700), 6-12.
Fischer, E. A., Liu, E. C., Rollins, J., & Theohary, C. A. (2013). The 2013 cybersecurity
executive order: Overview and considerations for congress. Washington: Congressional
Research Service.
References
Bernal, W. N., Caballero, G. C., Sánchez, J. O., & Paéz-Logreira, H. (2016, May). Enterprise
architecture framework oriented to cloud computing services. In Computers
Communications and Control (ICCCC), 2016 6th International Conference on (pp. 64-
69). IEEE.
Boito, M., Conley, T., Fleming, J., Ramos, A., & Anania, K. (2018). Expanding Operating and
Support Cost Analysis for Major Programs During the DoD Acquisition Process.
Bulluss, G. J., O'Shea, K., Tay, N. T., & Pong, P. (2014, June). Innovations in understanding the
whole of Australian defence system of systems. In System of Systems Engineering
(SOSE), 2014 9th International Conference on (pp. 171-176). IEEE.
Craib, I. (2015). Modern social theory. Routledge.
Evans, W., Nielsen, P. E., Szekely, D. R., Bihm, J. W., Murray, E. A., Snider, J., & Abroms, L.
C. (2015). Dose-response effects of the text4baby mobile health program: randomised
controlled trial. JMIR mHealth and uHealth, 3(1).
Fischer, E. A. (2014). Federal laws relating to cybersecurity: Overview of major issues, current
laws, and proposed legislation. Congressional Research Service, 7(5700), 6-12.
Fischer, E. A., Liu, E. C., Rollins, J., & Theohary, C. A. (2013). The 2013 cybersecurity
executive order: Overview and considerations for congress. Washington: Congressional
Research Service.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Fischer, J. (2014). Department of Defense Technology Transfer (T2) Program. OFFICE OF THE
ASSISTANT SECRETARY OF DEFENSE (RESEARCH AND ENGINEERING)
WASHINGTON DC DEFENSE LABS ENTERPRISE OFFICE.
Gottron, F., Bracmort, K., Carter, N. T., Comay, L. B., Cowan, T., Dabrowska, A., ... & Gallo,
M. E. (2017). Science and Technology Issues in the 115th Congress.
Hudson, J., & Tsurumaki, N. S. (2017). US Licensed School Nurses Working in an International
Setting. OJIN: The Online Journal of Issues in Nursing, 22(3).
Kotusev, S. (2016). Enterprise Architecture Frameworks: The Fad of the Century. British
Computer Society (BCS), July.
Navarra, A., Marambio, H., Oyarzún, F., Parra, R., & Mucciardi, F. (2017). System dynamics
and discrete event simulation of copper smelters. Minerals & Metallurgical
Processing, 34(2), 96-106.
O'Rourke, R. (2015). Navy Ford (CVN-78) Class Aircraft Carrier Program: Background and
Issues for Congress (No. CRS-RS20643). Congressional Research Service Washington.
Rouhani, B. D., Mahrin, M. N. R., Nikpay, F., Najafabadi, M. K., & Nikfard, P. (2015). A
Framework for Evaluation of Enterprise Architecture Implementation
Methodologies. International Journal of Social, Behavioral, Educational Economic,
Business and Industrial Engineering, 9(1).
Rouhani, B. D., Mahrin, M. N., Nikpay, F., & Nikfard, P. (2013, September). A comparison
enterprise architecture implementation methodologies. In Informatics and Creative
Multimedia (ICICM), 2013 International Conference on (pp. 1-6). IEEE.
Fischer, J. (2014). Department of Defense Technology Transfer (T2) Program. OFFICE OF THE
ASSISTANT SECRETARY OF DEFENSE (RESEARCH AND ENGINEERING)
WASHINGTON DC DEFENSE LABS ENTERPRISE OFFICE.
Gottron, F., Bracmort, K., Carter, N. T., Comay, L. B., Cowan, T., Dabrowska, A., ... & Gallo,
M. E. (2017). Science and Technology Issues in the 115th Congress.
Hudson, J., & Tsurumaki, N. S. (2017). US Licensed School Nurses Working in an International
Setting. OJIN: The Online Journal of Issues in Nursing, 22(3).
Kotusev, S. (2016). Enterprise Architecture Frameworks: The Fad of the Century. British
Computer Society (BCS), July.
Navarra, A., Marambio, H., Oyarzún, F., Parra, R., & Mucciardi, F. (2017). System dynamics
and discrete event simulation of copper smelters. Minerals & Metallurgical
Processing, 34(2), 96-106.
O'Rourke, R. (2015). Navy Ford (CVN-78) Class Aircraft Carrier Program: Background and
Issues for Congress (No. CRS-RS20643). Congressional Research Service Washington.
Rouhani, B. D., Mahrin, M. N. R., Nikpay, F., Najafabadi, M. K., & Nikfard, P. (2015). A
Framework for Evaluation of Enterprise Architecture Implementation
Methodologies. International Journal of Social, Behavioral, Educational Economic,
Business and Industrial Engineering, 9(1).
Rouhani, B. D., Mahrin, M. N., Nikpay, F., & Nikfard, P. (2013, September). A comparison
enterprise architecture implementation methodologies. In Informatics and Creative
Multimedia (ICICM), 2013 International Conference on (pp. 1-6). IEEE.

11ASSESSMENT OF DEPARTMENT OF DEFENSE EA PROGRAM
Smith, E. A., Poston, W. S., Haddock, C. K., & Malone, R. E. (2016). Installation tobacco
control programs in the US military. Military medicine, 181(6), 596-601.
Tate, D. F., Wilde, E. A., Bouix, S., & McCauley, S. R. (2015). Introduction to the brain imaging
and behavior special issue: mild traumatic brain injury among active duty service
members and veterans. Brain imaging and behavior, 9(3), 355-357.
Ullman, D. G. (2016). A Decision Architecture Whitepaper Part 2/2 Decision Architecture in EA
Standards and Agile Programming.
Wan, H., Luo, A., & Luo, X. (2014, May). How Enterprise architecture formative critical success
facets might affect Enterprise architecture success: A literature analysis. In International
Conference on Informatics and Semiotics in Organisations (pp. 197-209). Springer,
Berlin, Heidelberg.
White, G. B., Fisch, E. A., & Pooch, U. W. (2017). Computer system and network security. CRC
press.
Smith, E. A., Poston, W. S., Haddock, C. K., & Malone, R. E. (2016). Installation tobacco
control programs in the US military. Military medicine, 181(6), 596-601.
Tate, D. F., Wilde, E. A., Bouix, S., & McCauley, S. R. (2015). Introduction to the brain imaging
and behavior special issue: mild traumatic brain injury among active duty service
members and veterans. Brain imaging and behavior, 9(3), 355-357.
Ullman, D. G. (2016). A Decision Architecture Whitepaper Part 2/2 Decision Architecture in EA
Standards and Agile Programming.
Wan, H., Luo, A., & Luo, X. (2014, May). How Enterprise architecture formative critical success
facets might affect Enterprise architecture success: A literature analysis. In International
Conference on Informatics and Semiotics in Organisations (pp. 197-209). Springer,
Berlin, Heidelberg.
White, G. B., Fisch, E. A., & Pooch, U. W. (2017). Computer system and network security. CRC
press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





