CSI6202: Analysis and Mitigation of DoS Attacks on Web Servers
VerifiedAdded on 2023/03/21
|16
|2585
|39
Report
AI Summary
This report provides a detailed analysis of a Denial-of-Service (DoS) attack scenario originating from a vendor's network targeting a web server within a DMZ environment. The analysis begins with an introduction to DoS attacks, their purpose, and various attack methods, including reflective DoS attacks. It then outlines the assumptions made regarding the network architecture and security posture. The report proposes network, web application, and infrastructure protective measures to mitigate the attack. Potential evidence that can be acquired using an Intrusion Detection System (IDS) is discussed, followed by a practical guide on configuring Snort IDS. The configuration includes creating users, directories, and setting up rules to detect and respond to DoS attacks. The report includes a practical demonstration of performing a DoS attack using Kali Linux and hping3 to illustrate the attack and the effectiveness of the proposed mitigation strategies. The conclusion emphasizes the importance of robust security measures, particularly for web applications, to prevent such attacks. The report also provides references to support the analysis.

Assignment
DOS Attack from the vendor's network
DOS Attack from the vendor's network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of contents
1. Introduction …………………………………………………………………………………… 2
2. Reflective DOS attack scenario ………………………………………………………………. 3
3. Assumptions ………………………………………………………………………………….. 4
4. Network protective measures ………………………………………………………………… 4
5. Web applications protective measures ………………………………………………………. 4
6. Infrastructure protective measures ………………………………………………………….. 4
7. Potential evidence found in snort IDS ………………………………………………………. 5
8. Configuring IDS …………………………………………………………………………….. 6
9. Implementation of IDS configuration ………………………………………………………. 8
10. Conclusion ………………………………………………………………………………… 12
11. Reference ………………………………………………………………………………….. 13
Page 1
1. Introduction …………………………………………………………………………………… 2
2. Reflective DOS attack scenario ………………………………………………………………. 3
3. Assumptions ………………………………………………………………………………….. 4
4. Network protective measures ………………………………………………………………… 4
5. Web applications protective measures ………………………………………………………. 4
6. Infrastructure protective measures ………………………………………………………….. 4
7. Potential evidence found in snort IDS ………………………………………………………. 5
8. Configuring IDS …………………………………………………………………………….. 6
9. Implementation of IDS configuration ………………………………………………………. 8
10. Conclusion ………………………………………………………………………………… 12
11. Reference ………………………………………………………………………………….. 13
Page 1

Introduction
Denial of Service (DoS) attack may turn into a major threat to current PC systems. Indeed, even a
young person can lunch the DoS attack by utilizing readymade DoS instruments. The main purpose
of DOS is to hide resources from the server from being accessed by the clients. The objective of the
DoS attack is to forestall genuine clients to get to the administrations, not to pick up unapproved
access or resources. Aggressors anticipate the real clients to get to the administrations by doing
flooding of the system, upset associations between two machines, and disturb administration to a
particular client. In basic words, Denial of Service attack on a system is intended to bring down the
system by sending an expansive number of irregular packets.
Reflective DOS attack scenario
The attacker utilizes an authentic PC to dispatch an attack against the victim by concealing its very
own IP address. The typical way is the assailant sends a little bundle to a genuine machine
subsequent to manufacturing the sender of the parcel to look as though it has been sent from the
person in question. We can call the genuine PCs reflectors and this sort of attack, where the
assailant sends little information and the victim individual gets a bigger measure of information, is
called an enhancement attack. Since the aggressor does not straightforwardly utilize PCs
constrained by him and rather utilizes real PCs, it's known as an intelligent DDoS attack:
It tends to be a DNS demand or a Networking Time Protocol (NTP) demand, etc (Yuan, Yuan, Guo,
Yang, & Sun, 2016).
DNS enhancement attacks, WordPress pingback attacks, and NTP attacks are intensification
attacks. In a DNS enhancement attack, the attacker sends a fashioned parcel to the
Page 2
Denial of Service (DoS) attack may turn into a major threat to current PC systems. Indeed, even a
young person can lunch the DoS attack by utilizing readymade DoS instruments. The main purpose
of DOS is to hide resources from the server from being accessed by the clients. The objective of the
DoS attack is to forestall genuine clients to get to the administrations, not to pick up unapproved
access or resources. Aggressors anticipate the real clients to get to the administrations by doing
flooding of the system, upset associations between two machines, and disturb administration to a
particular client. In basic words, Denial of Service attack on a system is intended to bring down the
system by sending an expansive number of irregular packets.
Reflective DOS attack scenario
The attacker utilizes an authentic PC to dispatch an attack against the victim by concealing its very
own IP address. The typical way is the assailant sends a little bundle to a genuine machine
subsequent to manufacturing the sender of the parcel to look as though it has been sent from the
person in question. We can call the genuine PCs reflectors and this sort of attack, where the
assailant sends little information and the victim individual gets a bigger measure of information, is
called an enhancement attack. Since the aggressor does not straightforwardly utilize PCs
constrained by him and rather utilizes real PCs, it's known as an intelligent DDoS attack:
It tends to be a DNS demand or a Networking Time Protocol (NTP) demand, etc (Yuan, Yuan, Guo,
Yang, & Sun, 2016).
DNS enhancement attacks, WordPress pingback attacks, and NTP attacks are intensification
attacks. In a DNS enhancement attack, the attacker sends a fashioned parcel to the
Page 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DNS server containing the IP address of the person in question. The DNS server answers back to
the unfortunate casualty
rather with bigger information. Different sorts of intensification attack incorporate SMTP, SSDP,
etc. The PCs that are utilized to send traffic to the injured individual are not the bargained ones and
are called reflectors.
Assumptions.
• A start to finish burrowing architecture: the organization transparently builds up a passage over
the interPLMN spine straightforwardly towards a Packet Data Gateway in the HPLMN
• Tunnel foundation is free of the underlying WLAN Access Authentication and Authorisation
(specifically, it is autonomously verified and approved)
• After passage foundation, channels can be given to the VPLMN which permit characterization of
traffic-related with a solitary passage in the VPLMN
a) Network protective measures
The main vector where a security layer might be executed is the network infrastructure since it is
the passageway to given administrations(Peng, Li, & Fei, 2017). At the point when online
administrations utilize a corporate system, one of the main estimates that should be considered is
introducing a switch between this corporate system and the Internet Service Provider (ISP), with the
goal that security layers, for example, an entrance control list (ACL), which manages organize get
too dependent on mentioning IP addresses, as well as a firewall, might be effectively
actualized(Ding, Li, Quevedo, Dey, & Shi, 2017).
Moreover, if online administrations are facilitated on outer facilitating servers, VPS or committed
servers, the defensive measures offered by the switch and portrayed in the above section must be
Page 3
the unfortunate casualty
rather with bigger information. Different sorts of intensification attack incorporate SMTP, SSDP,
etc. The PCs that are utilized to send traffic to the injured individual are not the bargained ones and
are called reflectors.
Assumptions.
• A start to finish burrowing architecture: the organization transparently builds up a passage over
the interPLMN spine straightforwardly towards a Packet Data Gateway in the HPLMN
• Tunnel foundation is free of the underlying WLAN Access Authentication and Authorisation
(specifically, it is autonomously verified and approved)
• After passage foundation, channels can be given to the VPLMN which permit characterization of
traffic-related with a solitary passage in the VPLMN
a) Network protective measures
The main vector where a security layer might be executed is the network infrastructure since it is
the passageway to given administrations(Peng, Li, & Fei, 2017). At the point when online
administrations utilize a corporate system, one of the main estimates that should be considered is
introducing a switch between this corporate system and the Internet Service Provider (ISP), with the
goal that security layers, for example, an entrance control list (ACL), which manages organize get
too dependent on mentioning IP addresses, as well as a firewall, might be effectively
actualized(Ding, Li, Quevedo, Dey, & Shi, 2017).
Moreover, if online administrations are facilitated on outer facilitating servers, VPS or committed
servers, the defensive measures offered by the switch and portrayed in the above section must be
Page 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

executed basically, that is, as server administrations, or with the assistance of the supplier set-up
boards. In addition, the default preventive estimates actualized by the supplier all through their
system must be evaluated and counseled(Dridi, Zhani, 2016, October).
b) Web applications protective measures
When planning defensive measures for web applications, it is critical to consider a few
cybersecurity-related perspectives which will expand your framework's versatility and in this
manner your customer's trust in your administrations(Wu, Zhang, & Yue,2016).
Most occasions, refusal of-administrations attacks planned for web applications are not executed by
methods for over-burdening the framework, soaking the administration or gobbling up all accessible
transmission capacity yet by misusing vulnerabilities in your applications. In the event that your
application has been explicitly created, reviews must be led so as to recognize and take care of any
security issues(Wei, Fung, 2015, June).
Also, it is exceptionally fitting to have a CAPTCHA framework on your site shapes. These
frameworks will deflect any automatized assault which is expected to be helped out through these
structures.
c) Infrastructure protective measures
Another methodology is securing framework, which comprises of servers and other system gadgets,
for example, switches or switches.
In such gadgets, it is important to confirm programming status normally. A few DoS assaults are
completed by abusing gadget security disappointments. Therefore, it is critical to visit the maker's
authentic site and be state-of-the-art to any new discharges.
Page 4
boards. In addition, the default preventive estimates actualized by the supplier all through their
system must be evaluated and counseled(Dridi, Zhani, 2016, October).
b) Web applications protective measures
When planning defensive measures for web applications, it is critical to consider a few
cybersecurity-related perspectives which will expand your framework's versatility and in this
manner your customer's trust in your administrations(Wu, Zhang, & Yue,2016).
Most occasions, refusal of-administrations attacks planned for web applications are not executed by
methods for over-burdening the framework, soaking the administration or gobbling up all accessible
transmission capacity yet by misusing vulnerabilities in your applications. In the event that your
application has been explicitly created, reviews must be led so as to recognize and take care of any
security issues(Wei, Fung, 2015, June).
Also, it is exceptionally fitting to have a CAPTCHA framework on your site shapes. These
frameworks will deflect any automatized assault which is expected to be helped out through these
structures.
c) Infrastructure protective measures
Another methodology is securing framework, which comprises of servers and other system gadgets,
for example, switches or switches.
In such gadgets, it is important to confirm programming status normally. A few DoS assaults are
completed by abusing gadget security disappointments. Therefore, it is critical to visit the maker's
authentic site and be state-of-the-art to any new discharges.
Page 4

Deactivate all superfluous server ports when the server is only expected for facilitating web
administrations. If so, ports 80/TCP or 8080/TCP for HTTP demands, or 443/TCP for HTTPS
demands must be open. On the off chance that DNS administrations should be facilitated, ports
53/TCP, as well as 53/UDP, might be open. In addition, it is prudent to drop every single unused
administration so as to evade any potential abuse of such administrations.
Potential evidence that can be acquired using the IDS to support the preliminary findings of
cyber attack
Host interference area structures (HIDS) continue running on all PCs or contraptions in the
framework with direct access to both the web and the undertaking inward framework. HIDS
have great position over NIDS in that they may in all likelihood distinguish odd framework
packages that start from inside the affiliation or noxious traffic that a NIDS has fail to
perceive.
Imprint based intrusion acknowledgment structures screen all of the packs crossing the
framework and take a gander at them against a database of imprints or attributes of known
malevolent risks, much like antivirus programming.
Irregularity based intrusion acknowledgment structures screen mastermind traffic and
consider it against a setup design, to make sense of what is seen as run of the mill for the
framework in regards to exchange speed, shows, ports, and various devices. This kind of
IDS alerts heads to potentially malicious activity(Gope, Lee, & Quek, 2016).
Page 5
administrations. If so, ports 80/TCP or 8080/TCP for HTTP demands, or 443/TCP for HTTPS
demands must be open. On the off chance that DNS administrations should be facilitated, ports
53/TCP, as well as 53/UDP, might be open. In addition, it is prudent to drop every single unused
administration so as to evade any potential abuse of such administrations.
Potential evidence that can be acquired using the IDS to support the preliminary findings of
cyber attack
Host interference area structures (HIDS) continue running on all PCs or contraptions in the
framework with direct access to both the web and the undertaking inward framework. HIDS
have great position over NIDS in that they may in all likelihood distinguish odd framework
packages that start from inside the affiliation or noxious traffic that a NIDS has fail to
perceive.
Imprint based intrusion acknowledgment structures screen all of the packs crossing the
framework and take a gander at them against a database of imprints or attributes of known
malevolent risks, much like antivirus programming.
Irregularity based intrusion acknowledgment structures screen mastermind traffic and
consider it against a setup design, to make sense of what is seen as run of the mill for the
framework in regards to exchange speed, shows, ports, and various devices. This kind of
IDS alerts heads to potentially malicious activity(Gope, Lee, & Quek, 2016).
Page 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Setting Up an Intrusion Detection System
IDS can log the movement, send a caution to comfort or pager, and send a direction to firewalls or
switches. The most widely recognized activity is to log the occasion - doing as such gives
criminological information to breaking down effective endeavors and refreshing firewall, switch
and server arrangements to avert repeats.
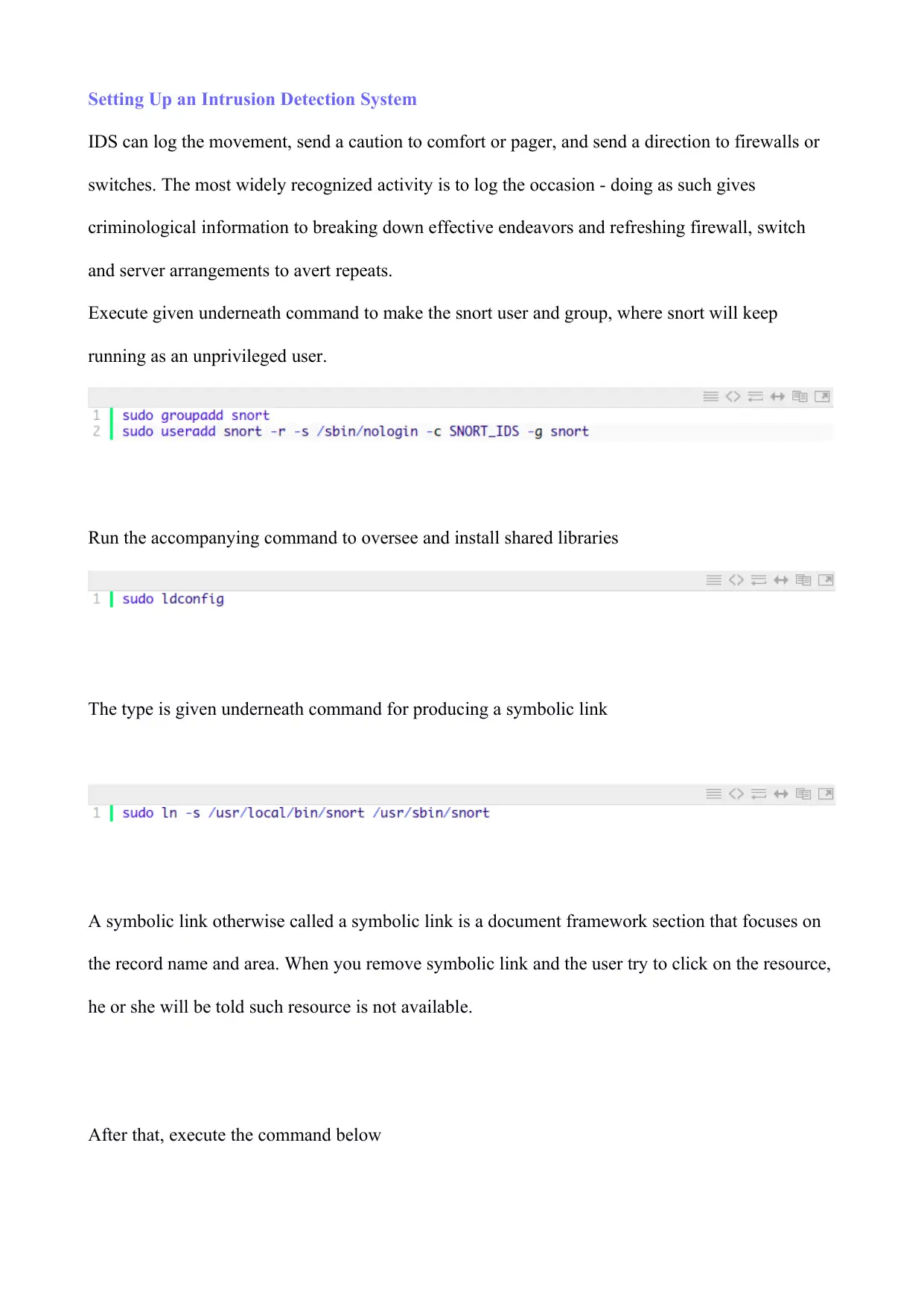
Execute given underneath command to make the snort user and group, where snort will keep
running as an unprivileged user.
Run the accompanying command to oversee and install shared libraries
The type is given underneath command for producing a symbolic link
A symbolic link otherwise called a symbolic link is a document framework section that focuses on
the record name and area. When you remove symbolic link and the user try to click on the resource,
he or she will be told such resource is not available.
After that, execute the command below
IDS can log the movement, send a caution to comfort or pager, and send a direction to firewalls or
switches. The most widely recognized activity is to log the occasion - doing as such gives
criminological information to breaking down effective endeavors and refreshing firewall, switch
and server arrangements to avert repeats.
Execute given underneath command to make the snort user and group, where snort will keep
running as an unprivileged user.
Run the accompanying command to oversee and install shared libraries
The type is given underneath command for producing a symbolic link
A symbolic link otherwise called a symbolic link is a document framework section that focuses on
the record name and area. When you remove symbolic link and the user try to click on the resource,
he or she will be told such resource is not available.
After that, execute the command below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 6
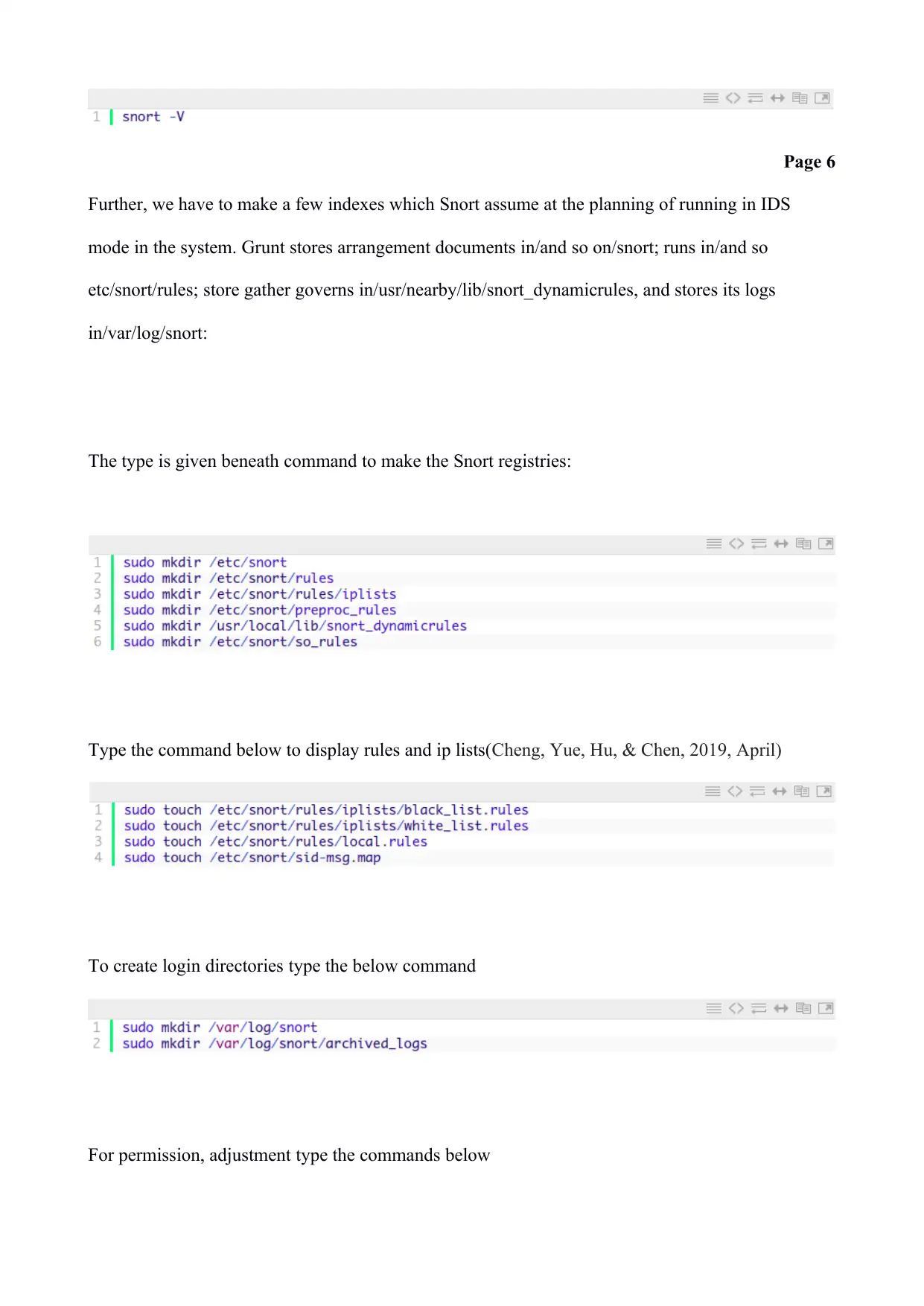
Further, we have to make a few indexes which Snort assume at the planning of running in IDS
mode in the system. Grunt stores arrangement documents in/and so on/snort; runs in/and so
etc/snort/rules; store gather governs in/usr/nearby/lib/snort_dynamicrules, and stores its logs
in/var/log/snort:
The type is given beneath command to make the Snort registries:
Type the command below to display rules and ip lists(Cheng, Yue, Hu, & Chen, 2019, April)
To create login directories type the below command
For permission, adjustment type the commands below
Further, we have to make a few indexes which Snort assume at the planning of running in IDS
mode in the system. Grunt stores arrangement documents in/and so on/snort; runs in/and so
etc/snort/rules; store gather governs in/usr/nearby/lib/snort_dynamicrules, and stores its logs
in/var/log/snort:
The type is given beneath command to make the Snort registries:
Type the command below to display rules and ip lists(Cheng, Yue, Hu, & Chen, 2019, April)
To create login directories type the below command
For permission, adjustment type the commands below
Page 7
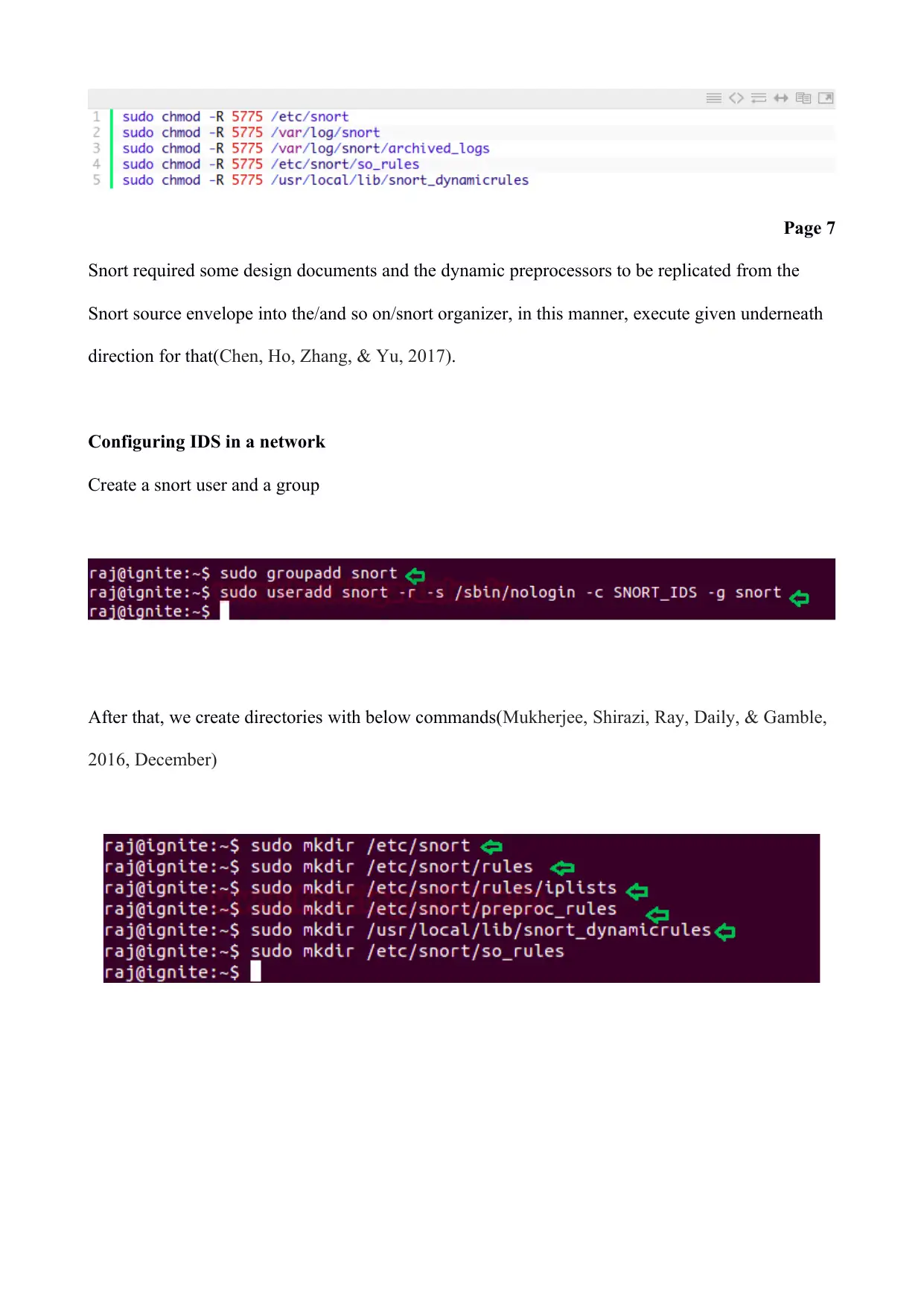
Snort required some design documents and the dynamic preprocessors to be replicated from the
Snort source envelope into the/and so on/snort organizer, in this manner, execute given underneath
direction for that(Chen, Ho, Zhang, & Yu, 2017).
Configuring IDS in a network
Create a snort user and a group
After that, we create directories with below commands(Mukherjee, Shirazi, Ray, Daily, & Gamble,
2016, December)
Snort required some design documents and the dynamic preprocessors to be replicated from the
Snort source envelope into the/and so on/snort organizer, in this manner, execute given underneath
direction for that(Chen, Ho, Zhang, & Yu, 2017).
Configuring IDS in a network
Create a snort user and a group
After that, we create directories with below commands(Mukherjee, Shirazi, Ray, Daily, & Gamble,
2016, December)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
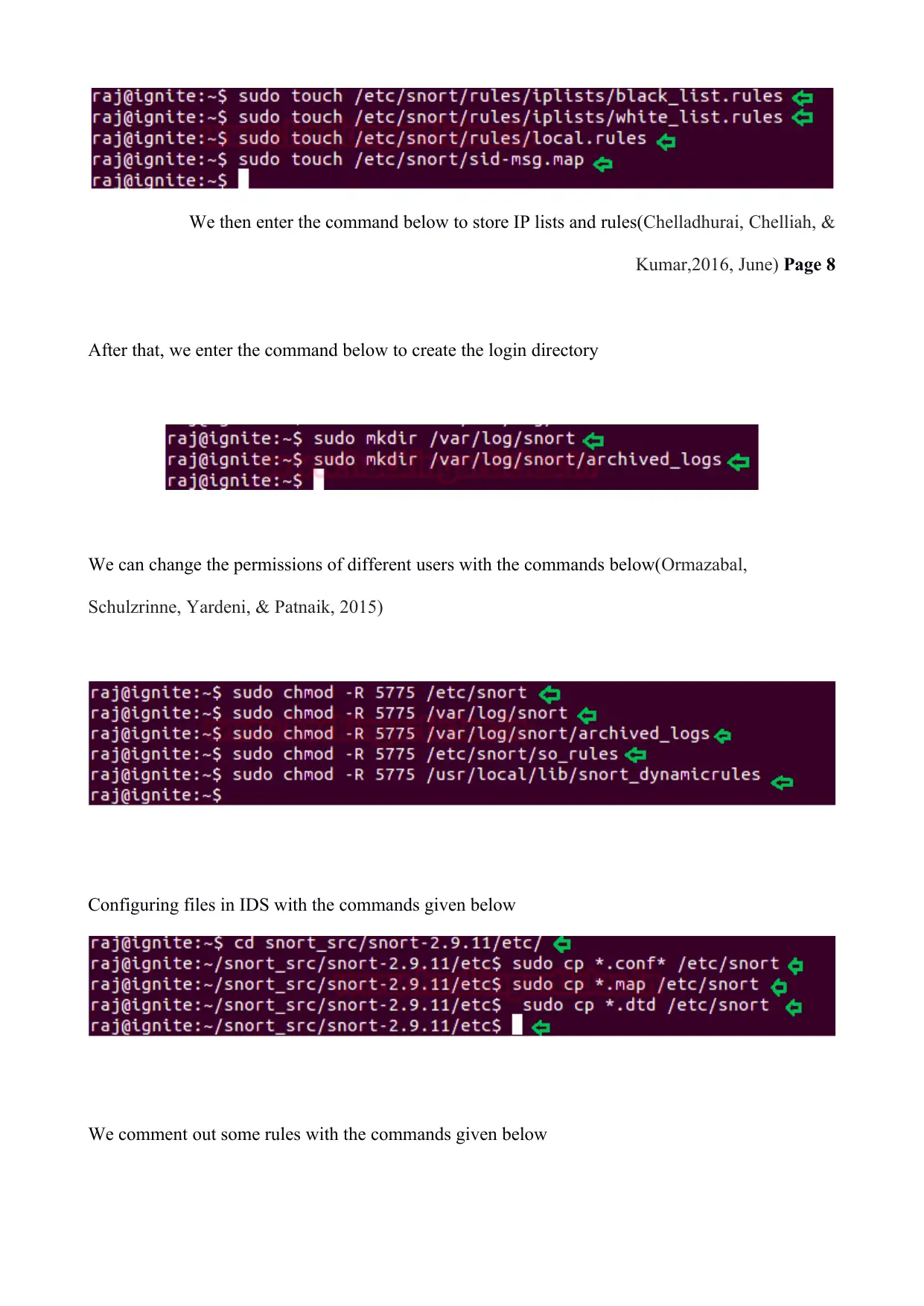
We then enter the command below to store IP lists and rules(Chelladhurai, Chelliah, &
Kumar,2016, June) Page 8
After that, we enter the command below to create the login directory
We can change the permissions of different users with the commands below(Ormazabal,
Schulzrinne, Yardeni, & Patnaik, 2015)
Configuring files in IDS with the commands given below
We comment out some rules with the commands given below
Kumar,2016, June) Page 8
After that, we enter the command below to create the login directory
We can change the permissions of different users with the commands below(Ormazabal,
Schulzrinne, Yardeni, & Patnaik, 2015)
Configuring files in IDS with the commands given below
We comment out some rules with the commands given below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
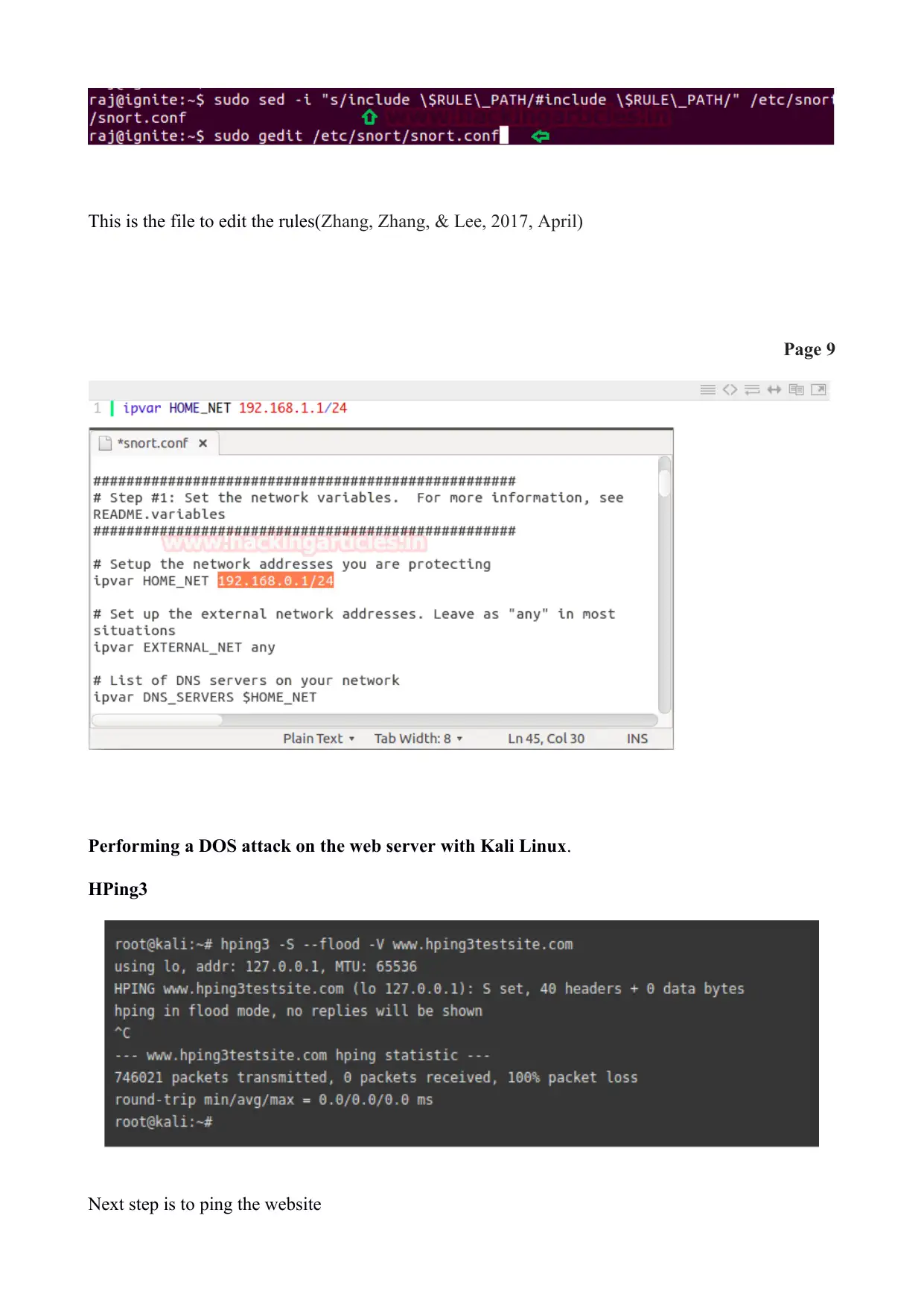
This is the file to edit the rules(Zhang, Zhang, & Lee, 2017, April)
Page 9
Performing a DOS attack on the web server with Kali Linux.
HPing3
Next step is to ping the website
Page 9
Performing a DOS attack on the web server with Kali Linux.
HPing3
Next step is to ping the website
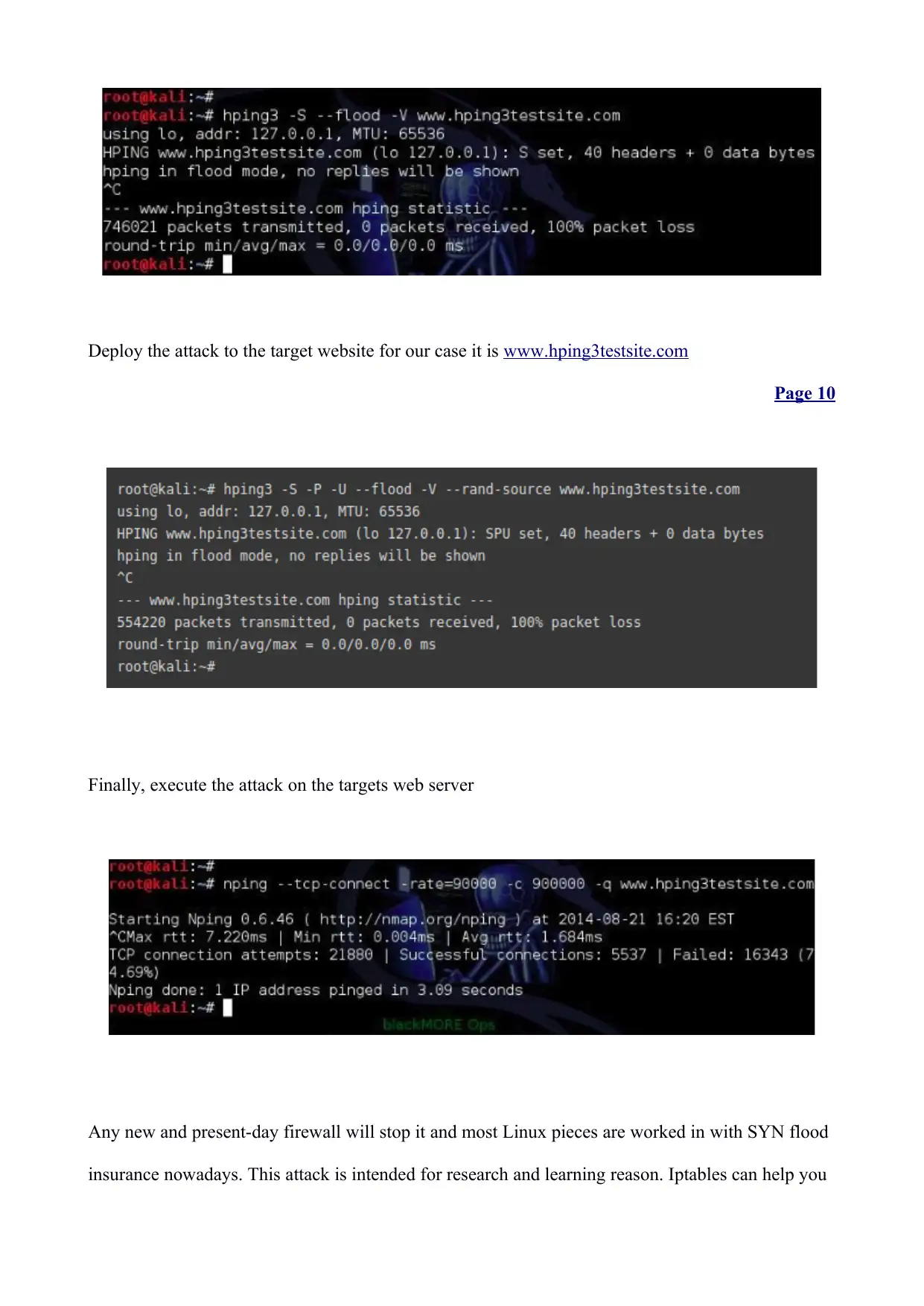
Deploy the attack to the target website for our case it is www.hping3testsite.com
Page 10
Finally, execute the attack on the targets web server
Any new and present-day firewall will stop it and most Linux pieces are worked in with SYN flood
insurance nowadays. This attack is intended for research and learning reason. Iptables can help you
Page 10
Finally, execute the attack on the targets web server
Any new and present-day firewall will stop it and most Linux pieces are worked in with SYN flood
insurance nowadays. This attack is intended for research and learning reason. Iptables can help you
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





