Drotos Engineering: Cloud Migration Data Recovery/BC Strategy
VerifiedAdded on 2022/09/25
|8
|1213
|139
Project
AI Summary
This project presents a Data Recovery/Business Continuity (DR/BC) plan for Drotos Engineering, focusing on its cloud migration. The plan emphasizes a 99.9% uptime requirement, detailing patch management strategies, backup strategies, and the use of automated tools to ensure secure and robust migration. It outlines a patch management strategy that includes regular vulnerability scanning, a single patching solution, and inventory management. The backup strategy covers understanding cloud provider responsibilities, implementing third-party solutions, employee training, data access policies, and restore testing. The project also details the use of automation tools for disaster recovery, security, and compliance. Furthermore, it identifies potential disasters like data breaches, application failures, and natural disasters, along with a schedule for incremental backups. The DR/BC playbook includes procedures for a hacking/data breach event, defining responsibilities, initial actions, and troubleshooting steps, as well as business continuity measures to maintain operations during recovery. The document also provides references to support the proposed strategies.

Running Head: Drotos Engineering DR/BC Strategy
Course Title:
Student’s Name:
Date of Submission:
1
Course Title:
Student’s Name:
Date of Submission:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head: Drotos Engineering DR/BC Strategy
1.0 Introduction
Drotos Engineering Company is planning to migrate its business to cloud computing. The
company’s applications require a 99.9% uptime. To ensure business continuity and limited
disruption of usual business processes, the company management wishes to have a clear and
concise Data Recovery/Business Continuity plan. This document presents the company
management with the Data Recovery and Business Continuity strategies that would ensure
secure and robust migration plan, ensuring little or no interruptions and recovery in case of any
disaster. This summary begins with an overview of patch management strategy that would be
employed, back-up strategy and the planned use of automated tools. A number of possible risks
that would arise are discussed in brief.
1.1 Patch Management Strategy
Patch management is an important aspect in networking that enables fixing of vulnerabilities and
ensuring that software is up to date, while fixing security flaws (Monate & Signoles, 2008). In
migrating to cloud, cloud providers take responsibility for cloud security and not being
responsible for a company’s applications, data and server security (Zissis & Lekkas, 2012). For
instance, AWS cloud provider share responsibility of security with their end users (Ullrich,
Cropper, Fruhwirt, & Weippl, 2016). Therefore, patch management is critical as Drotos
Engineering Company migrates to the cloud computing. Below is a patch management strategy
that can be employed:
i. Regular vulnerability scanning- search for patches from cloud services used by
company on a regular basis e.g. file storage systems.
2
1.0 Introduction
Drotos Engineering Company is planning to migrate its business to cloud computing. The
company’s applications require a 99.9% uptime. To ensure business continuity and limited
disruption of usual business processes, the company management wishes to have a clear and
concise Data Recovery/Business Continuity plan. This document presents the company
management with the Data Recovery and Business Continuity strategies that would ensure
secure and robust migration plan, ensuring little or no interruptions and recovery in case of any
disaster. This summary begins with an overview of patch management strategy that would be
employed, back-up strategy and the planned use of automated tools. A number of possible risks
that would arise are discussed in brief.
1.1 Patch Management Strategy
Patch management is an important aspect in networking that enables fixing of vulnerabilities and
ensuring that software is up to date, while fixing security flaws (Monate & Signoles, 2008). In
migrating to cloud, cloud providers take responsibility for cloud security and not being
responsible for a company’s applications, data and server security (Zissis & Lekkas, 2012). For
instance, AWS cloud provider share responsibility of security with their end users (Ullrich,
Cropper, Fruhwirt, & Weippl, 2016). Therefore, patch management is critical as Drotos
Engineering Company migrates to the cloud computing. Below is a patch management strategy
that can be employed:
i. Regular vulnerability scanning- search for patches from cloud services used by
company on a regular basis e.g. file storage systems.
2

Running Head: Drotos Engineering DR/BC Strategy
ii. Use single patching solution – if Drotos intends to migrate to the cloud and have
some of applications running on their servers, a single patch solution has to be used.
iii. Manage inventory of devices and servers so as to reduce time that IT manager spends
assessing patch status.
1.2 Back-up Strategy
As companies move to cloud, they mostly don’t understand that cloud service providers only
provide redundant backup systems from their end and not responsible for a user’s end
application (Sharma & Singh, 2012). Therefore, in case of accidental data loss from the end
user’s side, it may become a disaster. Therefore, a clear backup strategy has to be
formulated.
i. Understand what cloud service provider covers in data protection
ii. Implementing a third party backup solution
iii. Train employees in backup best practices associated with the cloud so as to prevent
or limit human errors that would lead to data loss.
iv. Setup data access policies among staff. Roles and permissions have to be assigned
well to ensure data read/write is done only by authorized personnel.
v. Test company’s restore to help understand how long, in the event of disaster, will it
take to recover from data loss and help in coming up with appropriate contingency
plan
3
ii. Use single patching solution – if Drotos intends to migrate to the cloud and have
some of applications running on their servers, a single patch solution has to be used.
iii. Manage inventory of devices and servers so as to reduce time that IT manager spends
assessing patch status.
1.2 Back-up Strategy
As companies move to cloud, they mostly don’t understand that cloud service providers only
provide redundant backup systems from their end and not responsible for a user’s end
application (Sharma & Singh, 2012). Therefore, in case of accidental data loss from the end
user’s side, it may become a disaster. Therefore, a clear backup strategy has to be
formulated.
i. Understand what cloud service provider covers in data protection
ii. Implementing a third party backup solution
iii. Train employees in backup best practices associated with the cloud so as to prevent
or limit human errors that would lead to data loss.
iv. Setup data access policies among staff. Roles and permissions have to be assigned
well to ensure data read/write is done only by authorized personnel.
v. Test company’s restore to help understand how long, in the event of disaster, will it
take to recover from data loss and help in coming up with appropriate contingency
plan
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running Head: Drotos Engineering DR/BC Strategy
1.3 Planned use of automated tools
As organizations migrate to cloud computing, it is important to first assess which cloud
platform would best suit the organization’s workloads while keeping the workload secure
and compliant to the cloud (Brevold, 2020). Cloud automation helps to reduce costs, reduce
errors otherwise made by humans, tightens security in that response towards a data breach is
almost instant and also providing greater resilience. Drotos Engineering has to make use of
cloud automation tools. Below are the automation tools that would be utilized;
i. Disaster recovery/Backup automation tool – this ensures data replications at pre-set
intervals, ensuring recovery in case of a disaster.
ii. Security automation tools- response to pre-known security threats can have to be
automated hence reducing response and recovery time
iii. Compliance automation tools – this tool will enable automatic disconnecting of
services that at one point violates compliance to cloud best practices.
1.4 Types of Disasters and potential causes of interruption
These are the possible risks during migration to cloud;
i. Improper user privileges
ii. Data loss
iii. Issues with secure deletion
iv. Hacking/Data breach
Disasters
Application failure
Building disaster (fire/theft)
4
1.3 Planned use of automated tools
As organizations migrate to cloud computing, it is important to first assess which cloud
platform would best suit the organization’s workloads while keeping the workload secure
and compliant to the cloud (Brevold, 2020). Cloud automation helps to reduce costs, reduce
errors otherwise made by humans, tightens security in that response towards a data breach is
almost instant and also providing greater resilience. Drotos Engineering has to make use of
cloud automation tools. Below are the automation tools that would be utilized;
i. Disaster recovery/Backup automation tool – this ensures data replications at pre-set
intervals, ensuring recovery in case of a disaster.
ii. Security automation tools- response to pre-known security threats can have to be
automated hence reducing response and recovery time
iii. Compliance automation tools – this tool will enable automatic disconnecting of
services that at one point violates compliance to cloud best practices.
1.4 Types of Disasters and potential causes of interruption
These are the possible risks during migration to cloud;
i. Improper user privileges
ii. Data loss
iii. Issues with secure deletion
iv. Hacking/Data breach
Disasters
Application failure
Building disaster (fire/theft)
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running Head: Drotos Engineering DR/BC Strategy
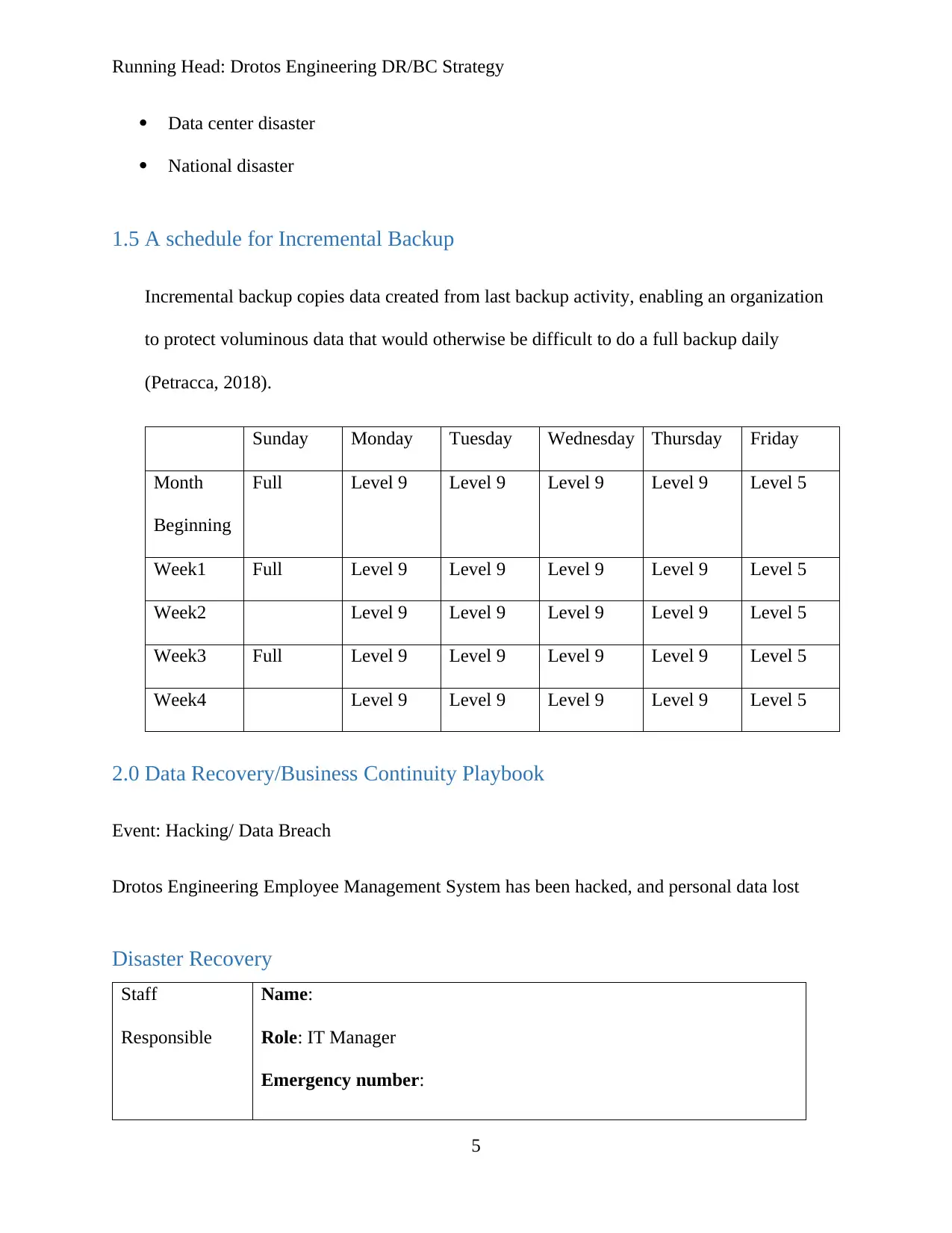
Data center disaster
National disaster
1.5 A schedule for Incremental Backup
Incremental backup copies data created from last backup activity, enabling an organization
to protect voluminous data that would otherwise be difficult to do a full backup daily
(Petracca, 2018).
Sunday Monday Tuesday Wednesday Thursday Friday
Month
Beginning
Full Level 9 Level 9 Level 9 Level 9 Level 5
Week1 Full Level 9 Level 9 Level 9 Level 9 Level 5
Week2 Level 9 Level 9 Level 9 Level 9 Level 5
Week3 Full Level 9 Level 9 Level 9 Level 9 Level 5
Week4 Level 9 Level 9 Level 9 Level 9 Level 5
2.0 Data Recovery/Business Continuity Playbook
Event: Hacking/ Data Breach
Drotos Engineering Employee Management System has been hacked, and personal data lost
Disaster Recovery
Staff
Responsible
Name:
Role: IT Manager
Emergency number:
5
Data center disaster
National disaster
1.5 A schedule for Incremental Backup
Incremental backup copies data created from last backup activity, enabling an organization
to protect voluminous data that would otherwise be difficult to do a full backup daily
(Petracca, 2018).
Sunday Monday Tuesday Wednesday Thursday Friday
Month
Beginning
Full Level 9 Level 9 Level 9 Level 9 Level 5
Week1 Full Level 9 Level 9 Level 9 Level 9 Level 5
Week2 Level 9 Level 9 Level 9 Level 9 Level 5
Week3 Full Level 9 Level 9 Level 9 Level 9 Level 5
Week4 Level 9 Level 9 Level 9 Level 9 Level 5
2.0 Data Recovery/Business Continuity Playbook
Event: Hacking/ Data Breach
Drotos Engineering Employee Management System has been hacked, and personal data lost
Disaster Recovery
Staff
Responsible
Name:
Role: IT Manager
Emergency number:
5
Running Head: Drotos Engineering DR/BC Strategy
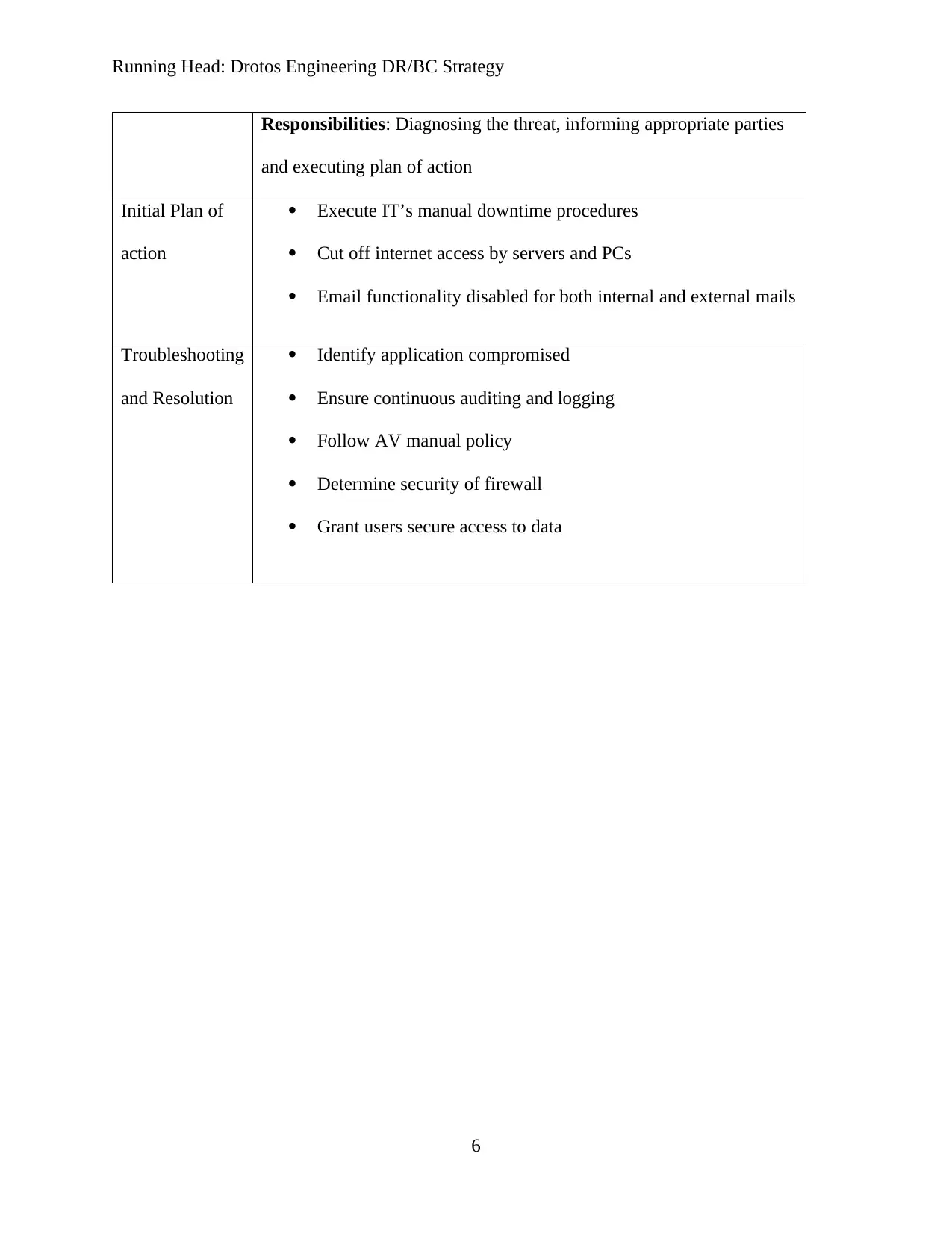
Responsibilities: Diagnosing the threat, informing appropriate parties
and executing plan of action
Initial Plan of
action
Execute IT’s manual downtime procedures
Cut off internet access by servers and PCs
Email functionality disabled for both internal and external mails
Troubleshooting
and Resolution
Identify application compromised
Ensure continuous auditing and logging
Follow AV manual policy
Determine security of firewall
Grant users secure access to data
6
Responsibilities: Diagnosing the threat, informing appropriate parties
and executing plan of action
Initial Plan of
action
Execute IT’s manual downtime procedures
Cut off internet access by servers and PCs
Email functionality disabled for both internal and external mails
Troubleshooting
and Resolution
Identify application compromised
Ensure continuous auditing and logging
Follow AV manual policy
Determine security of firewall
Grant users secure access to data
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running Head: Drotos Engineering DR/BC Strategy
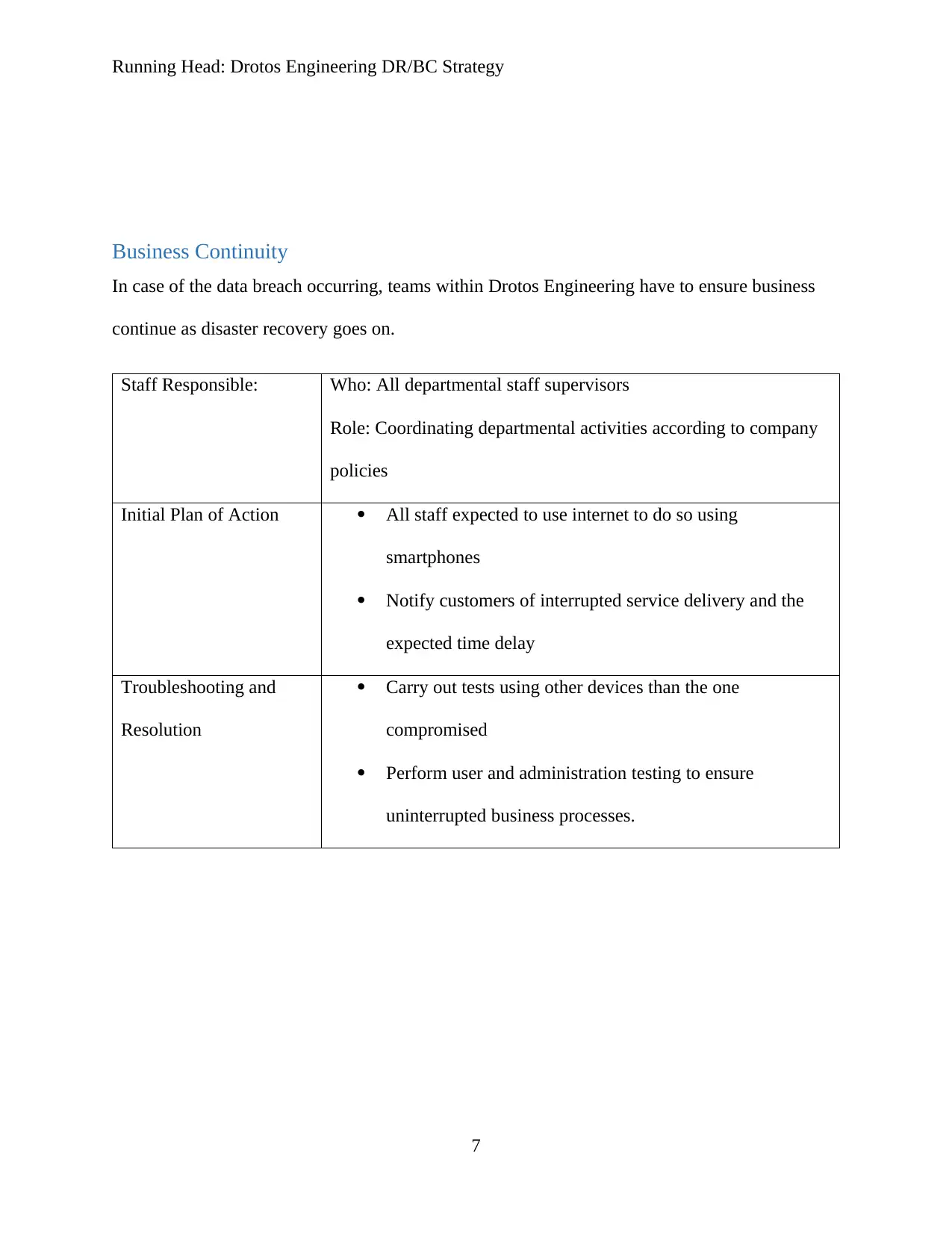
Business Continuity
In case of the data breach occurring, teams within Drotos Engineering have to ensure business
continue as disaster recovery goes on.
Staff Responsible: Who: All departmental staff supervisors
Role: Coordinating departmental activities according to company
policies
Initial Plan of Action All staff expected to use internet to do so using
smartphones
Notify customers of interrupted service delivery and the
expected time delay
Troubleshooting and
Resolution
Carry out tests using other devices than the one
compromised
Perform user and administration testing to ensure
uninterrupted business processes.
7
Business Continuity
In case of the data breach occurring, teams within Drotos Engineering have to ensure business
continue as disaster recovery goes on.
Staff Responsible: Who: All departmental staff supervisors
Role: Coordinating departmental activities according to company
policies
Initial Plan of Action All staff expected to use internet to do so using
smartphones
Notify customers of interrupted service delivery and the
expected time delay
Troubleshooting and
Resolution
Carry out tests using other devices than the one
compromised
Perform user and administration testing to ensure
uninterrupted business processes.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head: Drotos Engineering DR/BC Strategy
References
Brevold, H. P. (2020). Towards factories of the future: migration of industrial legacy automation
systems in the cloud computing and internet of things context. Enterprise Information
Systems, 542-562.
Monate, B., & Signoles, J. (2008). Slicing for security of code. International conference on
Trusted Computing, 133-142.
Petracca, T. (2018). Incremental backup of computer data files. US Patent, 746.
Sharma, K., & Singh, K. R. (2012). Online data back-up and disaster recovery techniques in
cloud computing: A review. International Journal of Engineering and Innovation
Technology (IJEIT), 2(5), 249-254.
Ullrich, J., Cropper, J., Fruhwirt, P., & Weippl, E. (2016). Cloud Security. EURASIP Journal on
Infromation Security.
Zissis, D., & Lekkas, D. (2012). Addresssing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
8
References
Brevold, H. P. (2020). Towards factories of the future: migration of industrial legacy automation
systems in the cloud computing and internet of things context. Enterprise Information
Systems, 542-562.
Monate, B., & Signoles, J. (2008). Slicing for security of code. International conference on
Trusted Computing, 133-142.
Petracca, T. (2018). Incremental backup of computer data files. US Patent, 746.
Sharma, K., & Singh, K. R. (2012). Online data back-up and disaster recovery techniques in
cloud computing: A review. International Journal of Engineering and Innovation
Technology (IJEIT), 2(5), 249-254.
Ullrich, J., Cropper, J., Fruhwirt, P., & Weippl, E. (2016). Cloud Security. EURASIP Journal on
Infromation Security.
Zissis, D., & Lekkas, D. (2012). Addresssing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




