DSL vs Cable, VPN Functionality, and T1 vs Frame Relay Comparison
VerifiedAdded on 2023/06/14
|6
|1023
|370
Homework Assignment
AI Summary
This assignment provides a detailed comparison of DSL and Cable home services, explaining their differences in terms of speed, connection type, and signal degradation. It elucidates how a VPN works to protect data by encrypting traffic and routing it through a secure server, preventing eavesdropping. Furthermore, the assignment differentiates between T1 lines, which offer dedicated connections, and Frame Relay, a packet-switching protocol used for WANs, highlighting their respective speeds, costs, and applications. The document references academic sources to support its explanations, offering a concise overview of these key data communication technologies. Desklib provides access to this and many other solved assignments for students.

Running head: DATA COMMUNICATIONS
DATA COMMUNICATIONS
Name of the university
Name of the student
Author Note
DATA COMMUNICATIONS
Name of the university
Name of the student
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA COMMUNICATIONS
1. Depict/Explain in detail the difference between DSL and Cable home service. Is
one better than the other?
DSL (Digital Subscriber Line) or TDSL transmits data by using the telephone lines
(copper) that exists in businesses and homes. One of the example of DSL is ADSL or
Asymmetrical Digital Subscriber Line.
Cable home service provides broadband access (high speed) with the help of a coaxial
cable and a cable modem.
An active phone line is required for DSL. An active POTS service from the telephone
provider is needed or a dry loop linked to a home (which requires an extra fee) is required for
maintain the connection. This is why DSL is a dedicated line. Whereas, Cable consists of a
branch of wires that is connected to neighbouring houses. If the branch is not wide enough,
then the speed suffers. Hence, cable can be called as a shared connection1.
In a DSL line, as the distance from the remote with which the home is connected
increases, the quality suffers. Due to interference and resistance, the signal deteriorates as it
travels. Whereas in a cable line, due to heavy shielding of the coaxial cables, the distance
does not deteriorates the signal.
If faster speed is the main concern, then Cable home service is better than DSL lines.
1 Horrigan, John B., and Maeve Duggan. "Home broadband 2015." Pew Research Center,
December 21 (2015): 4.
1. Depict/Explain in detail the difference between DSL and Cable home service. Is
one better than the other?
DSL (Digital Subscriber Line) or TDSL transmits data by using the telephone lines
(copper) that exists in businesses and homes. One of the example of DSL is ADSL or
Asymmetrical Digital Subscriber Line.
Cable home service provides broadband access (high speed) with the help of a coaxial
cable and a cable modem.
An active phone line is required for DSL. An active POTS service from the telephone
provider is needed or a dry loop linked to a home (which requires an extra fee) is required for
maintain the connection. This is why DSL is a dedicated line. Whereas, Cable consists of a
branch of wires that is connected to neighbouring houses. If the branch is not wide enough,
then the speed suffers. Hence, cable can be called as a shared connection1.
In a DSL line, as the distance from the remote with which the home is connected
increases, the quality suffers. Due to interference and resistance, the signal deteriorates as it
travels. Whereas in a cable line, due to heavy shielding of the coaxial cables, the distance
does not deteriorates the signal.
If faster speed is the main concern, then Cable home service is better than DSL lines.
1 Horrigan, John B., and Maeve Duggan. "Home broadband 2015." Pew Research Center,
December 21 (2015): 4.
2DATA COMMUNICATIONS
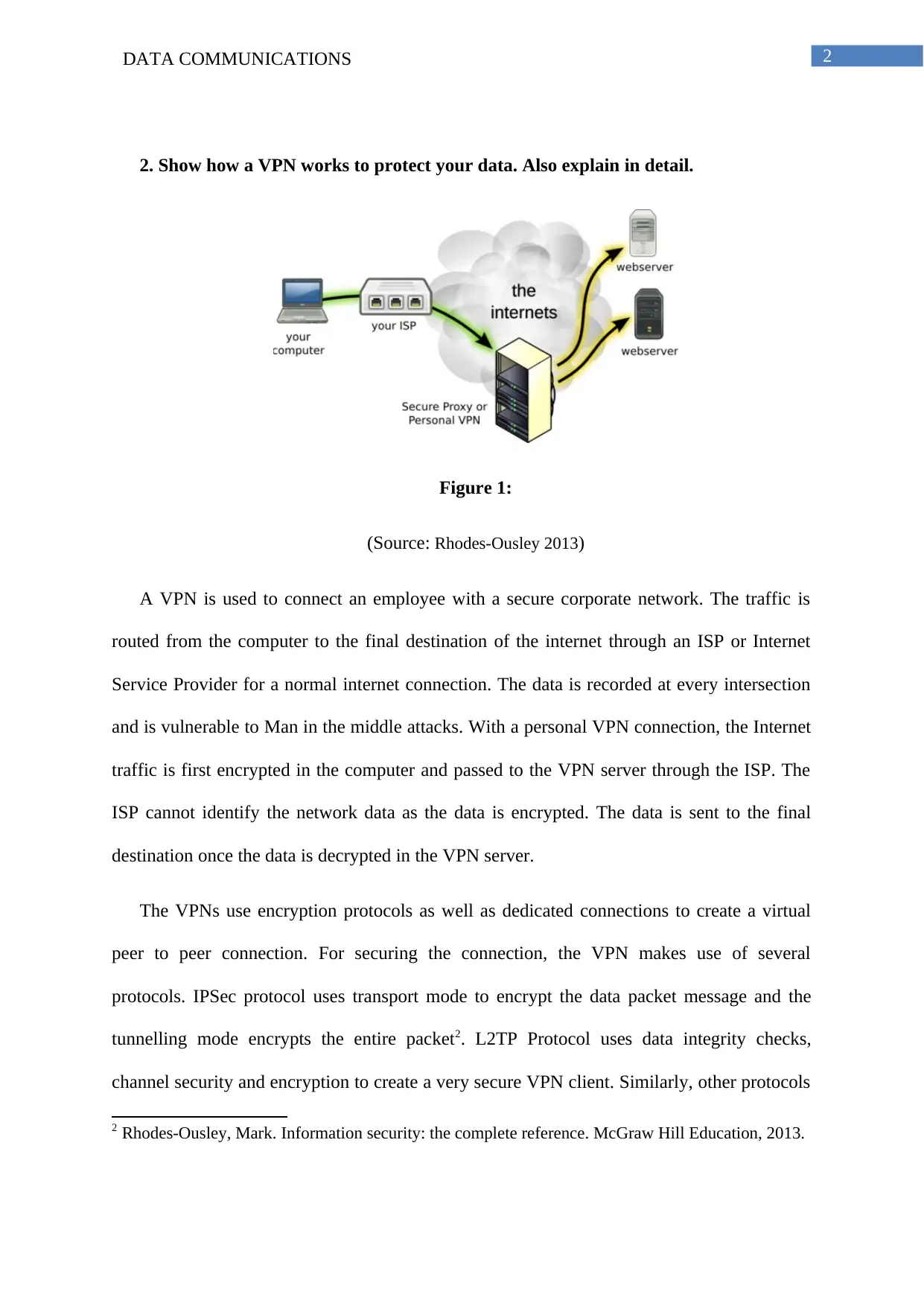
2. Show how a VPN works to protect your data. Also explain in detail.
Figure 1:
(Source: Rhodes-Ousley 2013)
A VPN is used to connect an employee with a secure corporate network. The traffic is
routed from the computer to the final destination of the internet through an ISP or Internet
Service Provider for a normal internet connection. The data is recorded at every intersection
and is vulnerable to Man in the middle attacks. With a personal VPN connection, the Internet
traffic is first encrypted in the computer and passed to the VPN server through the ISP. The
ISP cannot identify the network data as the data is encrypted. The data is sent to the final
destination once the data is decrypted in the VPN server.
The VPNs use encryption protocols as well as dedicated connections to create a virtual
peer to peer connection. For securing the connection, the VPN makes use of several
protocols. IPSec protocol uses transport mode to encrypt the data packet message and the
tunnelling mode encrypts the entire packet2. L2TP Protocol uses data integrity checks,
channel security and encryption to create a very secure VPN client. Similarly, other protocols
2 Rhodes-Ousley, Mark. Information security: the complete reference. McGraw Hill Education, 2013.
2. Show how a VPN works to protect your data. Also explain in detail.
Figure 1:
(Source: Rhodes-Ousley 2013)
A VPN is used to connect an employee with a secure corporate network. The traffic is
routed from the computer to the final destination of the internet through an ISP or Internet
Service Provider for a normal internet connection. The data is recorded at every intersection
and is vulnerable to Man in the middle attacks. With a personal VPN connection, the Internet
traffic is first encrypted in the computer and passed to the VPN server through the ISP. The
ISP cannot identify the network data as the data is encrypted. The data is sent to the final
destination once the data is decrypted in the VPN server.
The VPNs use encryption protocols as well as dedicated connections to create a virtual
peer to peer connection. For securing the connection, the VPN makes use of several
protocols. IPSec protocol uses transport mode to encrypt the data packet message and the
tunnelling mode encrypts the entire packet2. L2TP Protocol uses data integrity checks,
channel security and encryption to create a very secure VPN client. Similarly, other protocols
2 Rhodes-Ousley, Mark. Information security: the complete reference. McGraw Hill Education, 2013.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA COMMUNICATIONS
such as PPTP or Point-to-Point Tunneling Protocol and SSH or Secure Shell are used to
forward traffic in an encrypted format.
3. Depict/Explain in detail the difference between T1 and Frame Relay.
A T1 line consists of a dedicated phone connection that has 1.544Mbits/second. The
dedicated connection consists of 24 individual channels each having a speed of
64Kbits/second3. These lines are sometimes refereed as DS1 lines and each individual
channel can be configured to carry data traffic or voice. Telephone companies sometimes lets
the user buy the individual lines known as fractional T1 access. Businesses as well as ISPs
use the T1 lines to connect with the internet backbone. With growing distance from the
network provider, the cost of implementing a dedicated T1 service increases.
For connecting particular devices on a WAN or Wide Area Network, Frame Relay is used
as a protocol for packet switching. Networks supporting frame relay can support speeds up to
45 Mbps (T3) and 1.544 Mbps (T1). Frame relay can be used with the existing T3 and T1
lines of a service provider4. These connections are provided by telephone companies to
customers who want speed below T1 speeds. This technology is very inexpensive and is
quickly replaced by another network technology known as ATM or Asynchronous Transfer
3 Fil, Thom, and Camille Ryan. Computer and internet use in the united states, 2013. US Department
of Commerce, Economics and Statistics Administration, US Census Bureau, 2014.
4 Senarath, Nimal Gamini, Israfil Bahceci, Mo-Han Fong, Peiying Zhu, Derek Yu, Hang Zhang, Wen
Tong, and Sheng Sun. "System and method for wireless relay frame structure, protocol, and
operation." U.S. Patent 8,576,753, issued November 5, 2013.
such as PPTP or Point-to-Point Tunneling Protocol and SSH or Secure Shell are used to
forward traffic in an encrypted format.
3. Depict/Explain in detail the difference between T1 and Frame Relay.
A T1 line consists of a dedicated phone connection that has 1.544Mbits/second. The
dedicated connection consists of 24 individual channels each having a speed of
64Kbits/second3. These lines are sometimes refereed as DS1 lines and each individual
channel can be configured to carry data traffic or voice. Telephone companies sometimes lets
the user buy the individual lines known as fractional T1 access. Businesses as well as ISPs
use the T1 lines to connect with the internet backbone. With growing distance from the
network provider, the cost of implementing a dedicated T1 service increases.
For connecting particular devices on a WAN or Wide Area Network, Frame Relay is used
as a protocol for packet switching. Networks supporting frame relay can support speeds up to
45 Mbps (T3) and 1.544 Mbps (T1). Frame relay can be used with the existing T3 and T1
lines of a service provider4. These connections are provided by telephone companies to
customers who want speed below T1 speeds. This technology is very inexpensive and is
quickly replaced by another network technology known as ATM or Asynchronous Transfer
3 Fil, Thom, and Camille Ryan. Computer and internet use in the united states, 2013. US Department
of Commerce, Economics and Statistics Administration, US Census Bureau, 2014.
4 Senarath, Nimal Gamini, Israfil Bahceci, Mo-Han Fong, Peiying Zhu, Derek Yu, Hang Zhang, Wen
Tong, and Sheng Sun. "System and method for wireless relay frame structure, protocol, and
operation." U.S. Patent 8,576,753, issued November 5, 2013.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DATA COMMUNICATIONS
Mode. With growing distance from the network provider, the cost of implementing a
dedicated Frame relay service is lesser than T1 services.
Mode. With growing distance from the network provider, the cost of implementing a
dedicated Frame relay service is lesser than T1 services.

5DATA COMMUNICATIONS
References
Fil, Thom, and Camille Ryan. Computer and internet use in the united states, 2013. US
Department of Commerce, Economics and Statistics Administration, US Census Bureau,
2014.
Horrigan, John B., and Maeve Duggan. "Home broadband 2015." Pew Research Center,
December 21 (2015): 4.
Rhodes-Ousley, Mark. Information security: the complete reference. McGraw Hill Education,
2013.
Senarath, Nimal Gamini, Israfil Bahceci, Mo-Han Fong, Peiying Zhu, Derek Yu, Hang
Zhang, Wen Tong, and Sheng Sun. "System and method for wireless relay frame structure,
protocol, and operation." U.S. Patent 8,576,753, issued November 5, 2013.
References
Fil, Thom, and Camille Ryan. Computer and internet use in the united states, 2013. US
Department of Commerce, Economics and Statistics Administration, US Census Bureau,
2014.
Horrigan, John B., and Maeve Duggan. "Home broadband 2015." Pew Research Center,
December 21 (2015): 4.
Rhodes-Ousley, Mark. Information security: the complete reference. McGraw Hill Education,
2013.
Senarath, Nimal Gamini, Israfil Bahceci, Mo-Han Fong, Peiying Zhu, Derek Yu, Hang
Zhang, Wen Tong, and Sheng Sun. "System and method for wireless relay frame structure,
protocol, and operation." U.S. Patent 8,576,753, issued November 5, 2013.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





