DTGOV's Cloud Transformation: A Case Study of Hybrid Cloud Strategy
VerifiedAdded on 2023/03/23
|30
|6239
|95
Case Study
AI Summary
This report provides a comprehensive analysis of DTGOV's strategic proposal to implement a hybrid cloud structure, focusing on resource pooling and cloud bursting architectures. It explores the benefits of this implementation, such as improved collaboration, cost flexibility, and enhanced scalability, while also addressing potential issues like downtime and security risks. The report delves into the risks associated with hybrid cloud and microservice strategies, including lack of encryption, inadequate risk assessment, poor compliance, and data redundancy, offering mitigation plans for each. Furthermore, it outlines information security steps and controls, including authentication, authorization, and incident management, and provides recommendations for disaster recovery and business continuity. The analysis concludes with a checklist for ensuring a smooth transition and highlights the overall advantages of adopting a well-planned cloud strategy for DTGOV.

Running head: CLOUD COMPUTING
Cloud Computing
Name of the Student
Name of the University
Author Note
Cloud Computing
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING
Executive Summary
The report discusses the case summary of DTGOV and their proposal of implementing
hybrid cloud structure into their system. The architectures of hybrid cloud computing is
discussed in this report are resource pooling architecture and cloud bursting architecture.
Each of the models has potential advantages in promoting performance and productivity.
Thus, implementation of hybrid cloud into the system will enhance business growth for the
company.
Executive Summary
The report discusses the case summary of DTGOV and their proposal of implementing
hybrid cloud structure into their system. The architectures of hybrid cloud computing is
discussed in this report are resource pooling architecture and cloud bursting architecture.
Each of the models has potential advantages in promoting performance and productivity.
Thus, implementation of hybrid cloud into the system will enhance business growth for the
company.

2CLOUD COMPUTING
Table of Contents
Introduction................................................................................................................................4
Response 1.................................................................................................................................5
Implementation of Architecture.............................................................................................5
Resource Pooling Architecture..............................................................................................5
Cloud Bursting Architecture..................................................................................................6
Benefits of the cloud architecture..........................................................................................8
Issues of the cloud computing architecture..........................................................................10
Response 2...............................................................................................................................11
Risk associated with the Hybrid Cloud and Microservice Strategy.....................................11
Response 3...............................................................................................................................16
Information security steps and control.................................................................................16
Steps and Controls................................................................................................................16
Recommendations................................................................................................................18
Response 4...............................................................................................................................18
Inclusion of the recommendation.........................................................................................18
Disaster Recovery............................................................................................................19
Response 5...............................................................................................................................22
Table of Contents
Introduction................................................................................................................................4
Response 1.................................................................................................................................5
Implementation of Architecture.............................................................................................5
Resource Pooling Architecture..............................................................................................5
Cloud Bursting Architecture..................................................................................................6
Benefits of the cloud architecture..........................................................................................8
Issues of the cloud computing architecture..........................................................................10
Response 2...............................................................................................................................11
Risk associated with the Hybrid Cloud and Microservice Strategy.....................................11
Response 3...............................................................................................................................16
Information security steps and control.................................................................................16
Steps and Controls................................................................................................................16
Recommendations................................................................................................................18
Response 4...............................................................................................................................18
Inclusion of the recommendation.........................................................................................18
Disaster Recovery............................................................................................................19
Response 5...............................................................................................................................22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING
Checklist of Morad and Dalbhanjan....................................................................................22
Conclusion................................................................................................................................23
References................................................................................................................................25
Checklist of Morad and Dalbhanjan....................................................................................22
Conclusion................................................................................................................................23
References................................................................................................................................25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING
Introduction
The reports focus on the detailed deliberation of the security issues, risks and the
methods present in the implementation of cloud computing. The reason for standardizing the
service portfolio of DTGOV is to attain operational optimization and effective cost measures.
DTGOV has planned out several strategic proposals to achieve effectiveness and
optimization. DTGOV have three data centers out of which they want to conserve one solely
for the storage of data. The step to conserve the data centre would require the updating of
DTGOV’s Active Directory as well as the data storage infrastructure. The entire
infrastructure has to be moved into the cloud. The initial plan of DTGOV is to move the Web
Services to the cloud. This will increase HA (High Availability) level and provide an
enhanced degree of flexibility for supplying the data to the employees and consumers
(Marinescu, 2017). DTGOV can only draw advantages of scalability and the flexibility when
they change the existing wed software architecture. This can be done by moving the service
to the Microservices model. Services like Azure Functions or AWS Lambda, data services,
containers and lastly cloud edge monitoring and capability. DTGOV has propositions to
migrate their Line of Business (LOB) applications to the Public cloud. This will prove to
increase their availability and flexibility.
The strategy is used to enhance the responsiveness and flexibility of the company.
The scheme will provide the company with effective cost reduction methods and savings in
maintaining the ICT infrastructure. This will be done by shutting down the other two data
centers. The strategy will help them to manage the new Cloud infrastructure.
Introduction
The reports focus on the detailed deliberation of the security issues, risks and the
methods present in the implementation of cloud computing. The reason for standardizing the
service portfolio of DTGOV is to attain operational optimization and effective cost measures.
DTGOV has planned out several strategic proposals to achieve effectiveness and
optimization. DTGOV have three data centers out of which they want to conserve one solely
for the storage of data. The step to conserve the data centre would require the updating of
DTGOV’s Active Directory as well as the data storage infrastructure. The entire
infrastructure has to be moved into the cloud. The initial plan of DTGOV is to move the Web
Services to the cloud. This will increase HA (High Availability) level and provide an
enhanced degree of flexibility for supplying the data to the employees and consumers
(Marinescu, 2017). DTGOV can only draw advantages of scalability and the flexibility when
they change the existing wed software architecture. This can be done by moving the service
to the Microservices model. Services like Azure Functions or AWS Lambda, data services,
containers and lastly cloud edge monitoring and capability. DTGOV has propositions to
migrate their Line of Business (LOB) applications to the Public cloud. This will prove to
increase their availability and flexibility.
The strategy is used to enhance the responsiveness and flexibility of the company.
The scheme will provide the company with effective cost reduction methods and savings in
maintaining the ICT infrastructure. This will be done by shutting down the other two data
centers. The strategy will help them to manage the new Cloud infrastructure.

5CLOUD COMPUTING
Response 1
Implementation of Architecture
The company should implement numerous concepts to build scalable cloud
applications. Architectures that will be implemented are as follows:
(a) Resource Pooling Architecture and (b) Cloud Bursting Architecture
The architecture concept is critical as there is a need to measure expanding datasets,
quicker response time and unpredictable traffic flow (Caulfield et al., 2016).
Resource Pooling Architecture
The root of the resource pooling architecture lies in the pooling of similar resources
(IT) into groups. Virtual resources and physical resources are the two types in a pool. The
similar resources are grouped automatically to maintain and ensure synchronization. Physical
server pools comprise a network server which has operating systems and it can be readily
used. Storage pool comprises block storage containers and files (Fuchs et al., 2018) The CPU
pool allocates CPU resources to the virtual servers. There are pre-configured devices in the
network pool like virtual firewalls and load balancing to name a few. The significant purpose
for the deployment of this architecture is to ensure system synchronization of the IT resources
which are pooled (Samimi, Teimouri & Mukhtar, 2016).
The resources are organized in the hierarchical order to chart out the parent, sibling
and the nested pools. This is done to reduce the complexity of the process. Once the pools are
defined, each pool is taken to create in-memory pool of the IT resources which are live and
can be pulled out anytime on demand to use. Another advantage of the resource pooling
Response 1
Implementation of Architecture
The company should implement numerous concepts to build scalable cloud
applications. Architectures that will be implemented are as follows:
(a) Resource Pooling Architecture and (b) Cloud Bursting Architecture
The architecture concept is critical as there is a need to measure expanding datasets,
quicker response time and unpredictable traffic flow (Caulfield et al., 2016).
Resource Pooling Architecture
The root of the resource pooling architecture lies in the pooling of similar resources
(IT) into groups. Virtual resources and physical resources are the two types in a pool. The
similar resources are grouped automatically to maintain and ensure synchronization. Physical
server pools comprise a network server which has operating systems and it can be readily
used. Storage pool comprises block storage containers and files (Fuchs et al., 2018) The CPU
pool allocates CPU resources to the virtual servers. There are pre-configured devices in the
network pool like virtual firewalls and load balancing to name a few. The significant purpose
for the deployment of this architecture is to ensure system synchronization of the IT resources
which are pooled (Samimi, Teimouri & Mukhtar, 2016).
The resources are organized in the hierarchical order to chart out the parent, sibling
and the nested pools. This is done to reduce the complexity of the process. Once the pools are
defined, each pool is taken to create in-memory pool of the IT resources which are live and
can be pulled out anytime on demand to use. Another advantage of the resource pooling
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
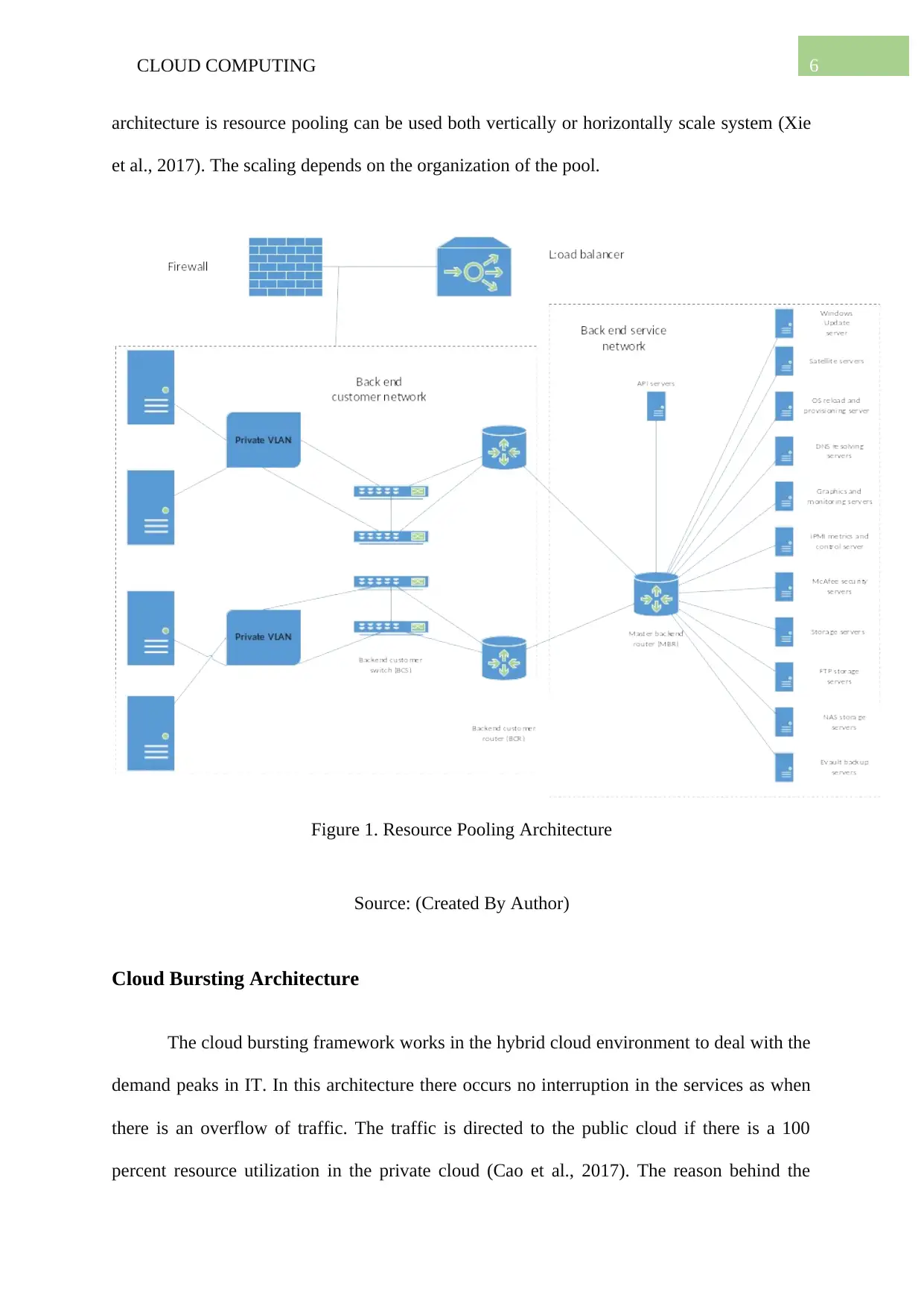
6CLOUD COMPUTING
architecture is resource pooling can be used both vertically or horizontally scale system (Xie
et al., 2017). The scaling depends on the organization of the pool.
Figure 1. Resource Pooling Architecture
Source: (Created By Author)
Cloud Bursting Architecture
The cloud bursting framework works in the hybrid cloud environment to deal with the
demand peaks in IT. In this architecture there occurs no interruption in the services as when
there is an overflow of traffic. The traffic is directed to the public cloud if there is a 100
percent resource utilization in the private cloud (Cao et al., 2017). The reason behind the
architecture is resource pooling can be used both vertically or horizontally scale system (Xie
et al., 2017). The scaling depends on the organization of the pool.
Figure 1. Resource Pooling Architecture
Source: (Created By Author)
Cloud Bursting Architecture
The cloud bursting framework works in the hybrid cloud environment to deal with the
demand peaks in IT. In this architecture there occurs no interruption in the services as when
there is an overflow of traffic. The traffic is directed to the public cloud if there is a 100
percent resource utilization in the private cloud (Cao et al., 2017). The reason behind the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING
deployment of cloud bursting architecture in the organization is that it is highly flexible and
provides self-service functionality. The major advantage of cloud bursting architecture is the
framework is highly flexible and economical. The cost lies in the additional resources if there
is a high demand for the resources, hence there is no additional cost on the extra capacity or
in the prediction of fluctuations and demand peaks. Additional advantage of Cloud burst
architecture is to meet peak demand; the application can be initially applied to private cloud
later bursting it into public cloud (Clemente-Castelló et al., 2018). When the requirement is
met, the architecture “bursts in” back to the on-premise environment The application can be
used to minimize processing burdens by removing the applications from the private cloud and
feeding it into the public cloud. This method frees up the local resources for additional
business critical applications. The very base of the architecture works on the principle of
resource replication mechanisms and automated scaling listener. The resource replication
maintains the synchronization of the IT resources (cloud based) and the on premise resource.
Automated scaling listener redirects request to the IT resources (cloud based).
deployment of cloud bursting architecture in the organization is that it is highly flexible and
provides self-service functionality. The major advantage of cloud bursting architecture is the
framework is highly flexible and economical. The cost lies in the additional resources if there
is a high demand for the resources, hence there is no additional cost on the extra capacity or
in the prediction of fluctuations and demand peaks. Additional advantage of Cloud burst
architecture is to meet peak demand; the application can be initially applied to private cloud
later bursting it into public cloud (Clemente-Castelló et al., 2018). When the requirement is
met, the architecture “bursts in” back to the on-premise environment The application can be
used to minimize processing burdens by removing the applications from the private cloud and
feeding it into the public cloud. This method frees up the local resources for additional
business critical applications. The very base of the architecture works on the principle of
resource replication mechanisms and automated scaling listener. The resource replication
maintains the synchronization of the IT resources (cloud based) and the on premise resource.
Automated scaling listener redirects request to the IT resources (cloud based).
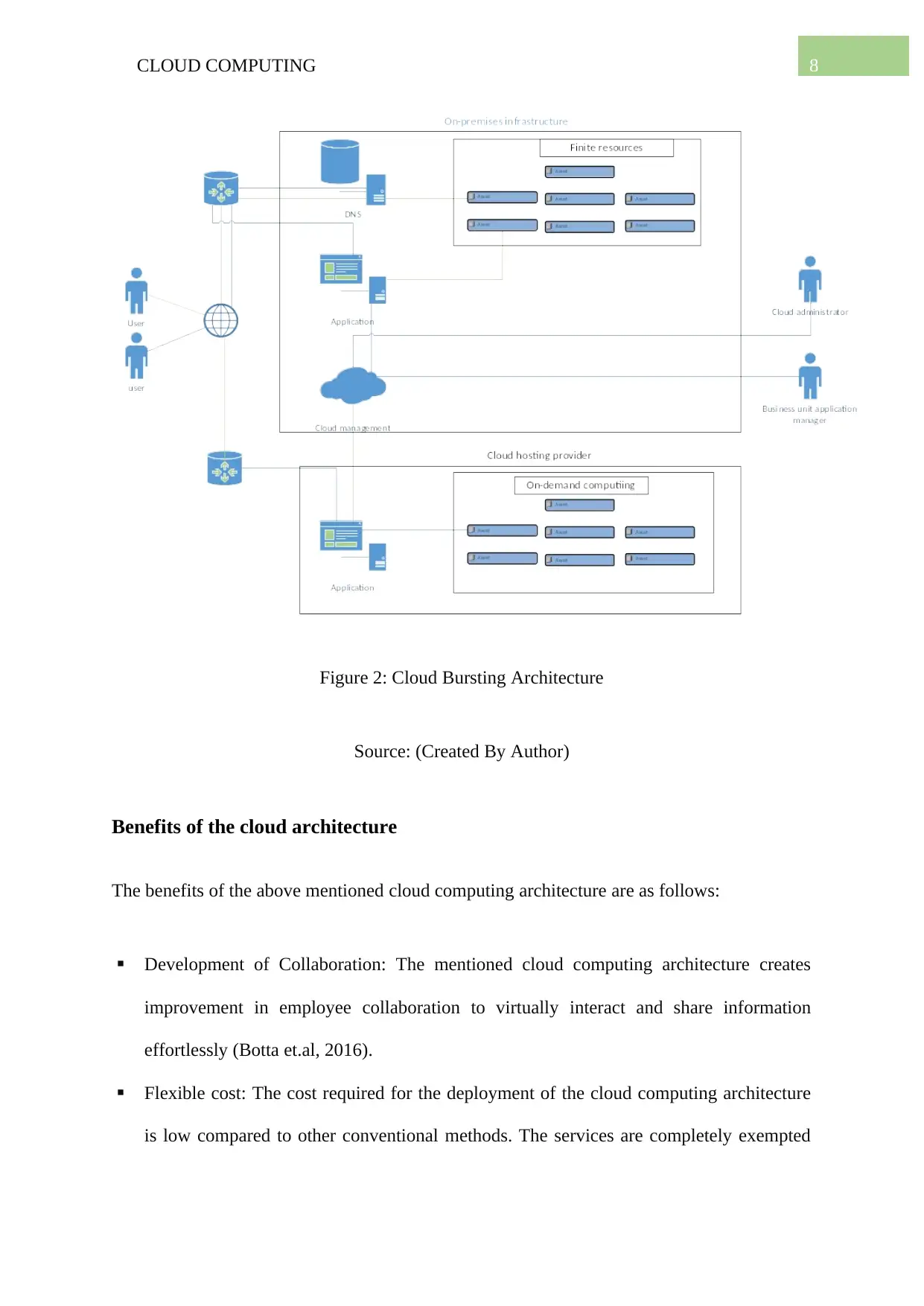
8CLOUD COMPUTING
Figure 2: Cloud Bursting Architecture
Source: (Created By Author)
Benefits of the cloud architecture
The benefits of the above mentioned cloud computing architecture are as follows:
Development of Collaboration: The mentioned cloud computing architecture creates
improvement in employee collaboration to virtually interact and share information
effortlessly (Botta et.al, 2016).
Flexible cost: The cost required for the deployment of the cloud computing architecture
is low compared to other conventional methods. The services are completely exempted
Figure 2: Cloud Bursting Architecture
Source: (Created By Author)
Benefits of the cloud architecture
The benefits of the above mentioned cloud computing architecture are as follows:
Development of Collaboration: The mentioned cloud computing architecture creates
improvement in employee collaboration to virtually interact and share information
effortlessly (Botta et.al, 2016).
Flexible cost: The cost required for the deployment of the cloud computing architecture
is low compared to other conventional methods. The services are completely exempted
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD COMPUTING
from additional capital expenditure. There is no cost in implementing of hardware. The
payment is done on the basis of the service required and no spillover costs are required.
Innovative Software: The clouds are updated to provide new opportunities, services,
flexibility, features and functionality to the numerous customers and clients.
Availability: The major benefit of the cloud computing is that the services are available
all through the day offering reliable services and certain functions even work off-line
(Martinez & Pulier, 2015).
Capacity flexibility: The cloud provides flexible services to its users and can be
controlled according to the circumstance of the user. The cloud architecture can be
adjusted to feed in data and the capacity can be shrunk to minimize cost. Cloud bursting
technology provides a failsafe mean for the enterprise to not get hamstrung by sever
crashes and overflow (Chang & Pathak, 2017).
Scalability: The introduction of the architecture into the system will enhance the
scalability of the environment it is deployed in (Li et al., 2018).
Mobility: The above mentioned cloud computing architectures will increase mobility and
availability of data easy for the employees.
Carbon Footprint: The architecture reduces carbon footprint for the organization. It
allows the utilization of the necessary quantity of the resources and aids in avoiding over
provisioning. Prevents wastage of energy and resources.
Easy management of IT resources: Implementation of the architectures eases out the
process of IT resource management and maintenance.
Strategic edge: The deployment of the cloud computing architecture provides a strategic
edge without excess upfront cost and nominal provision time.
from additional capital expenditure. There is no cost in implementing of hardware. The
payment is done on the basis of the service required and no spillover costs are required.
Innovative Software: The clouds are updated to provide new opportunities, services,
flexibility, features and functionality to the numerous customers and clients.
Availability: The major benefit of the cloud computing is that the services are available
all through the day offering reliable services and certain functions even work off-line
(Martinez & Pulier, 2015).
Capacity flexibility: The cloud provides flexible services to its users and can be
controlled according to the circumstance of the user. The cloud architecture can be
adjusted to feed in data and the capacity can be shrunk to minimize cost. Cloud bursting
technology provides a failsafe mean for the enterprise to not get hamstrung by sever
crashes and overflow (Chang & Pathak, 2017).
Scalability: The introduction of the architecture into the system will enhance the
scalability of the environment it is deployed in (Li et al., 2018).
Mobility: The above mentioned cloud computing architectures will increase mobility and
availability of data easy for the employees.
Carbon Footprint: The architecture reduces carbon footprint for the organization. It
allows the utilization of the necessary quantity of the resources and aids in avoiding over
provisioning. Prevents wastage of energy and resources.
Easy management of IT resources: Implementation of the architectures eases out the
process of IT resource management and maintenance.
Strategic edge: The deployment of the cloud computing architecture provides a strategic
edge without excess upfront cost and nominal provision time.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD COMPUTING
Issues of the cloud computing architecture
There are several concerns in using cloud computing. The most prominent disadvantage of
cloud computing is confidentiality of data. Maintaining integrity and security of data is a
major threat (Di, Polvi & Welliver, 2016). The issues associated with the mentioned cloud
computing architecture are as follows:
Downtime: The chief disadvantage of cloud architecture implementation is downtime.
The cloud computing services are completely dependent on the internet for its working.
The cloud has new entrants each day and gets overwhelmed leading to technical outages.
Overwhelming leads to the suspension of business procedures (Almorsy, Grundy &
Müller, 2016).
Security Issues: Security issues increases when business uses cloud service to run their
business. There is an increased threat when cloud is implemented in the business model.
The service provider gets the access to confidential company data. As there are multiple
users hosted on the cloud, it increases vulnerability of the cloud and chances of data theft
(Ali, Khan & Vasilakos, 2015).
Vendor lock-in: Changing service provider becomes a complicated process and it results
in vendor lock in. Switching the services involves complication (Sen, 2015).
Issues of the cloud computing architecture
There are several concerns in using cloud computing. The most prominent disadvantage of
cloud computing is confidentiality of data. Maintaining integrity and security of data is a
major threat (Di, Polvi & Welliver, 2016). The issues associated with the mentioned cloud
computing architecture are as follows:
Downtime: The chief disadvantage of cloud architecture implementation is downtime.
The cloud computing services are completely dependent on the internet for its working.
The cloud has new entrants each day and gets overwhelmed leading to technical outages.
Overwhelming leads to the suspension of business procedures (Almorsy, Grundy &
Müller, 2016).
Security Issues: Security issues increases when business uses cloud service to run their
business. There is an increased threat when cloud is implemented in the business model.
The service provider gets the access to confidential company data. As there are multiple
users hosted on the cloud, it increases vulnerability of the cloud and chances of data theft
(Ali, Khan & Vasilakos, 2015).
Vendor lock-in: Changing service provider becomes a complicated process and it results
in vendor lock in. Switching the services involves complication (Sen, 2015).

11CLOUD COMPUTING
Response 2
Risk associated with the Hybrid Cloud and Microservice Strategy
Hybrid cloud merges two cloud technologies, the public and the private cloud into one
application and allows sharing of applications and data between them. When there is a
fluctuation in processing demand, hybrid cloud provides the business the capability to scale
the infrastructure up in the public cloud and seamlessly handles the overflow if there is any
(Chang et al., 2015). The third party does not get the access to the entirety of the data. The
sensitive business details and the critical applications are safe behind the firewall while the
gaining the computing and flexibility of public cloud for non-sensitive and basic computing
tasks.
Hybrid cloud comes with its alluring advantages and as well as numerous
disadvantages. Organizations are increasingly using Hybrid cloud and others are planning to
implement the model into their infrastructure (Ghosh et al., 2017). There are several risk
factors involved in implementing and using the Hybrid cloud computing model. The hybrid
cloud system is sometime dismissed is disruptive (Gopinath & Vasudevan, 2015).
The table below scales out the potential risks associated with Hybrid cloud computing
and the prospective mitigation schemes (Puthal et al., 2015).
Risks Risk Description Mitigation plan
Lack of encryption The network systems are highly Cryptographic protocols need
Response 2
Risk associated with the Hybrid Cloud and Microservice Strategy
Hybrid cloud merges two cloud technologies, the public and the private cloud into one
application and allows sharing of applications and data between them. When there is a
fluctuation in processing demand, hybrid cloud provides the business the capability to scale
the infrastructure up in the public cloud and seamlessly handles the overflow if there is any
(Chang et al., 2015). The third party does not get the access to the entirety of the data. The
sensitive business details and the critical applications are safe behind the firewall while the
gaining the computing and flexibility of public cloud for non-sensitive and basic computing
tasks.
Hybrid cloud comes with its alluring advantages and as well as numerous
disadvantages. Organizations are increasingly using Hybrid cloud and others are planning to
implement the model into their infrastructure (Ghosh et al., 2017). There are several risk
factors involved in implementing and using the Hybrid cloud computing model. The hybrid
cloud system is sometime dismissed is disruptive (Gopinath & Vasudevan, 2015).
The table below scales out the potential risks associated with Hybrid cloud computing
and the prospective mitigation schemes (Puthal et al., 2015).
Risks Risk Description Mitigation plan
Lack of encryption The network systems are highly Cryptographic protocols need
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




