Mohammad Alhawawsha: E-Government Online Voting System Project
VerifiedAdded on 2019/09/26
|34
|9196
|323
Project
AI Summary
This project proposes a Java-based e-government system designed to facilitate online voting. The paper begins with an abstract highlighting the system's purpose: to improve government-public interaction and service reach by enabling citizens to vote securely from any location and time, while ensuring privacy and preventing vote theft. The introduction explains the concept of e-government and its role in facilitating citizen engagement and the use of information and communication technology. The research aims to understand existing e-government systems and propose a new online voting system, assessing its merits and demerits. The paper reviews existing solutions for online voting and proposes a new system, including voter registration and login processes, to address challenges such as security and accessibility. The system aims to enable voting from home, reducing interruptions for citizens. The methodology involves secondary research, referencing various sources to gather information. The results section examines current e-governance models, service delivery, and adoption rates in different countries. It then presents a proposed Java-based online voting system with voter registration and login processes. The system stores voter information securely and facilitates secure voting. The project underscores the importance of trust, security, and citizen awareness in the successful implementation of e-government systems.

E-GOVERNMENT SYSTEM ONLINE VOTING SYSTEM
Mohammad Alhawawsha
Abstract
E-government systems are meant to improve the level of interaction of
government with the public and to improve the reach of services provided by the
government to the public. A java based e-government system has been suggested in
this paper that will allow the government to conduct online voting. It will ensure that
the individuals vote from their preferred location and time without getting concerned
about privacy and vote theft.
Keyword: E-government system, election, java, technology
1. Introduction
The current paper is concerned with understanding the various aspects of e-
government system. In addition, a new e-government system has been proposed that
is likely to support the government in handling the election polling. E-government
system refers to the use of electronic mediums to facilitate the services to the public
of the country (Becker et al, 2004).
The e-government system allows the citizen to engage with the government at
all the levels and along with gaining benefit from the actions of the government, it
contributes to the action of the government. With the use of e-government system, the
citizens involved in the local and national governance. The information and
communication technology is used to facilitate these actions. As per United Nations,
the e-government is referred to as the actions of the government that lead to the use
of information technology to facilitate the delivery of government services to the
citizens (Gil-Garcia and Pardo, 2005).
At present, the United Nations conducts e-government survey twice a year to
assess the readiness of the governments of different countries regarding the use of
information and technology to conduct their business and cater to the masses. As a
model, the e-government system should be able to allow any individual visiting the
city or country website to engage in communication with the employees of the local
government using the internet, GUI, and IM.
The current paper is concerned with understanding the current e-government
system and proposing an additional system that can aide in the current system. The
second chapter assesses the current e-government system and then proposes an
additional online system in the next chapter. Also, it identifies the potential merits
and limitations of the proposed online system.
2. The object of research and its technological audit
At present, due to the technological advancement, almost every household has
the access to the technology. This allows the government to implement technology
based solutions that can help in making the lives of the people simpler. At present, it
has been found that the people are required to stand in the line to vote for their
respective candidates. This leads to the challenging situation for government and the
Mohammad Alhawawsha
Abstract
E-government systems are meant to improve the level of interaction of
government with the public and to improve the reach of services provided by the
government to the public. A java based e-government system has been suggested in
this paper that will allow the government to conduct online voting. It will ensure that
the individuals vote from their preferred location and time without getting concerned
about privacy and vote theft.
Keyword: E-government system, election, java, technology
1. Introduction
The current paper is concerned with understanding the various aspects of e-
government system. In addition, a new e-government system has been proposed that
is likely to support the government in handling the election polling. E-government
system refers to the use of electronic mediums to facilitate the services to the public
of the country (Becker et al, 2004).
The e-government system allows the citizen to engage with the government at
all the levels and along with gaining benefit from the actions of the government, it
contributes to the action of the government. With the use of e-government system, the
citizens involved in the local and national governance. The information and
communication technology is used to facilitate these actions. As per United Nations,
the e-government is referred to as the actions of the government that lead to the use
of information technology to facilitate the delivery of government services to the
citizens (Gil-Garcia and Pardo, 2005).
At present, the United Nations conducts e-government survey twice a year to
assess the readiness of the governments of different countries regarding the use of
information and technology to conduct their business and cater to the masses. As a
model, the e-government system should be able to allow any individual visiting the
city or country website to engage in communication with the employees of the local
government using the internet, GUI, and IM.
The current paper is concerned with understanding the current e-government
system and proposing an additional system that can aide in the current system. The
second chapter assesses the current e-government system and then proposes an
additional online system in the next chapter. Also, it identifies the potential merits
and limitations of the proposed online system.
2. The object of research and its technological audit
At present, due to the technological advancement, almost every household has
the access to the technology. This allows the government to implement technology
based solutions that can help in making the lives of the people simpler. At present, it
has been found that the people are required to stand in the line to vote for their
respective candidates. This leads to the challenging situation for government and the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

public as well. On one hand where the government is required to make improved
management of the voting, on the other the public are required to get away from their
daily course and stand in the line to vote. There is a necessity that a system is brought
in the picture that can resolve this challenge. Interestingly, due to the increased
adoption of technological devices by the public in the past decades, the
implementation of online system has become easier for the government, as long as it
is suitable and useful for all the concerned stakeholders.
3. The aim and objectives of research
The aim of the research is to come up with a suitable e-government system that
can assist the government in improve its voting.
The objectives of the research are:
- to understand the existing solutions available for voting
- to propose a new e-government voting system
- to assess the merits and demerits of the proposed system
4. Research of existing solutions of the problem
One can witness numerous researches that have been conducted regarding the
usage of technologies to facilitate in the elections (Mcclure et al, 2001; Kohno et al,
2004; Draper and Brown, 2004; Kennedy and Cutts, 2005). Some of these studies
have warned against the rapid adaptation of the technology as it can be challenging
for the stakeholders to get used to it. However, with the improved security measures,
the technologies can be a beneficial tool. The elections conducted in various countries
uses technologies in different way. As for instance, the election conducted in Florida
(United States) in 2000 used punch card voting system which was later adopted by
wide population. This new electronic voting system allows the voters to have a
government issued token or smartcard which they can take to the nearest voting
terminal in their locality and then swipe the card. The system also allows them to
make any changes if they want by entering pin. This has been considered appreciable
in comparison to the traditional method where the voters approach the voting booth to
cast their vote by first showing their voter id and proving who they are. On the other
hand, the direct recording electronic (DRE) voting system allows the users to have
quick voting experience with faster service. There are only few instances of adoption
of this system, as there are still countries where the method of voting is traditional
and cumbersome (Mercuri, 2002; Bederson et al, 2003). Here, it can be stated that
despite the DRE, the government are required to make arrangements for the voting
terminals. However, the goal should be to ensure that the voters do not need to leave
their home to vote and can vote from their comfort zone. This should be filled as it
will reduce the interruption for public who can vote from their comfort.
One of the important aspects to understand here is that the parties in the election
can get the benefit of the system if they identify any loopholes to utilize the system
flaw. The recent development has found that the governments of few countries have
adopted the usage of the DRE without considering or questioning the security of the
system which can be a fatal mistake. Here, it is necessary that a voting system that is
robust and secure is required to be developed (Stuart et al, 2004). The introduction of
end to end encryption can also improve the security of the system. The end to end
management of the voting, on the other the public are required to get away from their
daily course and stand in the line to vote. There is a necessity that a system is brought
in the picture that can resolve this challenge. Interestingly, due to the increased
adoption of technological devices by the public in the past decades, the
implementation of online system has become easier for the government, as long as it
is suitable and useful for all the concerned stakeholders.
3. The aim and objectives of research
The aim of the research is to come up with a suitable e-government system that
can assist the government in improve its voting.
The objectives of the research are:
- to understand the existing solutions available for voting
- to propose a new e-government voting system
- to assess the merits and demerits of the proposed system
4. Research of existing solutions of the problem
One can witness numerous researches that have been conducted regarding the
usage of technologies to facilitate in the elections (Mcclure et al, 2001; Kohno et al,
2004; Draper and Brown, 2004; Kennedy and Cutts, 2005). Some of these studies
have warned against the rapid adaptation of the technology as it can be challenging
for the stakeholders to get used to it. However, with the improved security measures,
the technologies can be a beneficial tool. The elections conducted in various countries
uses technologies in different way. As for instance, the election conducted in Florida
(United States) in 2000 used punch card voting system which was later adopted by
wide population. This new electronic voting system allows the voters to have a
government issued token or smartcard which they can take to the nearest voting
terminal in their locality and then swipe the card. The system also allows them to
make any changes if they want by entering pin. This has been considered appreciable
in comparison to the traditional method where the voters approach the voting booth to
cast their vote by first showing their voter id and proving who they are. On the other
hand, the direct recording electronic (DRE) voting system allows the users to have
quick voting experience with faster service. There are only few instances of adoption
of this system, as there are still countries where the method of voting is traditional
and cumbersome (Mercuri, 2002; Bederson et al, 2003). Here, it can be stated that
despite the DRE, the government are required to make arrangements for the voting
terminals. However, the goal should be to ensure that the voters do not need to leave
their home to vote and can vote from their comfort zone. This should be filled as it
will reduce the interruption for public who can vote from their comfort.
One of the important aspects to understand here is that the parties in the election
can get the benefit of the system if they identify any loopholes to utilize the system
flaw. The recent development has found that the governments of few countries have
adopted the usage of the DRE without considering or questioning the security of the
system which can be a fatal mistake. Here, it is necessary that a voting system that is
robust and secure is required to be developed (Stuart et al, 2004). The introduction of
end to end encryption can also improve the security of the system. The end to end

encryption has become a necessary tool for the current systems due to the increasing
security threats (Bannet et al, 2004; Boneh and Franklin, 2001; Clarkson et al, 2008).
5. Methods of research
The method of research used for the current paper is secondary. The researcher
referred to various secondary resources for the collection of the information that were
relevant to the study. The secondary research allows desk-based study of the required
research area. The study could have been taken further by conducting primary
research to gain more input for the required system, however due to the time
constraint, secondary research was preferred.
6. Research results
The current chapter assesses the current e-governance system keeping in view
the current position of various countries such as United States, United Kingdom, and
India. In general, there are four models of service delivery from the government.
They are from a government to the citizens, from a government to businesses
operating in the country, from one department of government to another, and from
the government to its employees.
The adoption rate of e-government system is different in the different parts of
the world. The developed economies such as The United States and The United
Kingdom have an appreciable rate of adoption in comparison to developing nations
like India. The developed nations also witnesses improved usage rate of the system
by the citizens whereas same can be found far below in the developing nations
(Altameen et al, 2006).
The improved usage of e-government system requires that the citizens of the
country are well aware of modern information and communication technology and
how to use them. If a government is willing to use the e-government system, then it is
important that an education drive should be facilitated that can educate the citizens
about the same. This will help them get the intended benefit from the system.
The governments can use the information and communication technologies to
improve their governance capability. The IT can be implemented in almost all aspects
of the government activities and all can be coordinated together to provide better
service to the masses. Also, the internet can help the government in establishing
better coordination among the departments and improving the internal and external
relations.
In general, when the discussion of e-government comes up, people think about
the internet which is appreciable as it is the only thing at present that should be
guiding all the technological adoption by the government. However, there also exists
e-government which is not based on the internet. The use of SMS, telephone, wireless
networks, smart cards, CCTV, and others are also on the premise of information and
technology and thus are also the integral part of the e-government system. However,
the definition of the e-government has not changed to something that allows inclusion
of citizens with the government and this can only be facilitated by the use of the
internet (Al-khamayseh et al, 2006).
security threats (Bannet et al, 2004; Boneh and Franklin, 2001; Clarkson et al, 2008).
5. Methods of research
The method of research used for the current paper is secondary. The researcher
referred to various secondary resources for the collection of the information that were
relevant to the study. The secondary research allows desk-based study of the required
research area. The study could have been taken further by conducting primary
research to gain more input for the required system, however due to the time
constraint, secondary research was preferred.
6. Research results
The current chapter assesses the current e-governance system keeping in view
the current position of various countries such as United States, United Kingdom, and
India. In general, there are four models of service delivery from the government.
They are from a government to the citizens, from a government to businesses
operating in the country, from one department of government to another, and from
the government to its employees.
The adoption rate of e-government system is different in the different parts of
the world. The developed economies such as The United States and The United
Kingdom have an appreciable rate of adoption in comparison to developing nations
like India. The developed nations also witnesses improved usage rate of the system
by the citizens whereas same can be found far below in the developing nations
(Altameen et al, 2006).
The improved usage of e-government system requires that the citizens of the
country are well aware of modern information and communication technology and
how to use them. If a government is willing to use the e-government system, then it is
important that an education drive should be facilitated that can educate the citizens
about the same. This will help them get the intended benefit from the system.
The governments can use the information and communication technologies to
improve their governance capability. The IT can be implemented in almost all aspects
of the government activities and all can be coordinated together to provide better
service to the masses. Also, the internet can help the government in establishing
better coordination among the departments and improving the internal and external
relations.
In general, when the discussion of e-government comes up, people think about
the internet which is appreciable as it is the only thing at present that should be
guiding all the technological adoption by the government. However, there also exists
e-government which is not based on the internet. The use of SMS, telephone, wireless
networks, smart cards, CCTV, and others are also on the premise of information and
technology and thus are also the integral part of the e-government system. However,
the definition of the e-government has not changed to something that allows inclusion
of citizens with the government and this can only be facilitated by the use of the
internet (Al-khamayseh et al, 2006).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

One of the important things, however, to consider is that the use of e-
government system is different in various countries and it impacts the level of
equality. The countries, where fewer people are aware of the internet and technology,
such as India face a lack of equality. On one hand where the citizens who are aware
of IT, gains the benefit from the improved government communication, however, the
other part of the citizens who are still unaware of this aspect face challenge.
There are many such people who are homeless, have lower income and cannot
learn or purchase IT devices, or are living in the remotest of the locations where there
is no IT infrastructure. In such scenarios, it is difficult for the government to provide
benefit to these people directly with the use of e-government modules. Here, the
elementary step of the government would be to train these people about the new
technology and install right infrastructure (Chircu and Lee, 2005).
In addition to above, it is important that the citizens trust the e-government
model for whether it will perform as expected. Interestingly, the e-government
system is still in developing phase from the most developed economies to the
underdeveloped economies. Even countries like US and UK has not fully adopted e-
government mechanism due to various reasons.
6.1 Proposed E-Government System
The e-government system consists of various modules and infrastructures that
cater to different aspects of government functioning. The current chapter will propose
a new module to the current e-government system that is likely to assist the
government in getting more digitalized.
The system that is proposed is an online voting system for the elections. This
system is still in a debate that whether a government should adopt this method of
voting considering various challenges, such as identity manipulation, data theft, and
others.
The system that has been suggested is Java based system which will allow the
government to hold voting at the local or national level. The citizens will use this
system to enter their personal details and then cast their vote for their preferred
candidate. The image below shows the information that will be entered by the users
before they engage in voting.
government system is different in various countries and it impacts the level of
equality. The countries, where fewer people are aware of the internet and technology,
such as India face a lack of equality. On one hand where the citizens who are aware
of IT, gains the benefit from the improved government communication, however, the
other part of the citizens who are still unaware of this aspect face challenge.
There are many such people who are homeless, have lower income and cannot
learn or purchase IT devices, or are living in the remotest of the locations where there
is no IT infrastructure. In such scenarios, it is difficult for the government to provide
benefit to these people directly with the use of e-government modules. Here, the
elementary step of the government would be to train these people about the new
technology and install right infrastructure (Chircu and Lee, 2005).
In addition to above, it is important that the citizens trust the e-government
model for whether it will perform as expected. Interestingly, the e-government
system is still in developing phase from the most developed economies to the
underdeveloped economies. Even countries like US and UK has not fully adopted e-
government mechanism due to various reasons.
6.1 Proposed E-Government System
The e-government system consists of various modules and infrastructures that
cater to different aspects of government functioning. The current chapter will propose
a new module to the current e-government system that is likely to assist the
government in getting more digitalized.
The system that is proposed is an online voting system for the elections. This
system is still in a debate that whether a government should adopt this method of
voting considering various challenges, such as identity manipulation, data theft, and
others.
The system that has been suggested is Java based system which will allow the
government to hold voting at the local or national level. The citizens will use this
system to enter their personal details and then cast their vote for their preferred
candidate. The image below shows the information that will be entered by the users
before they engage in voting.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
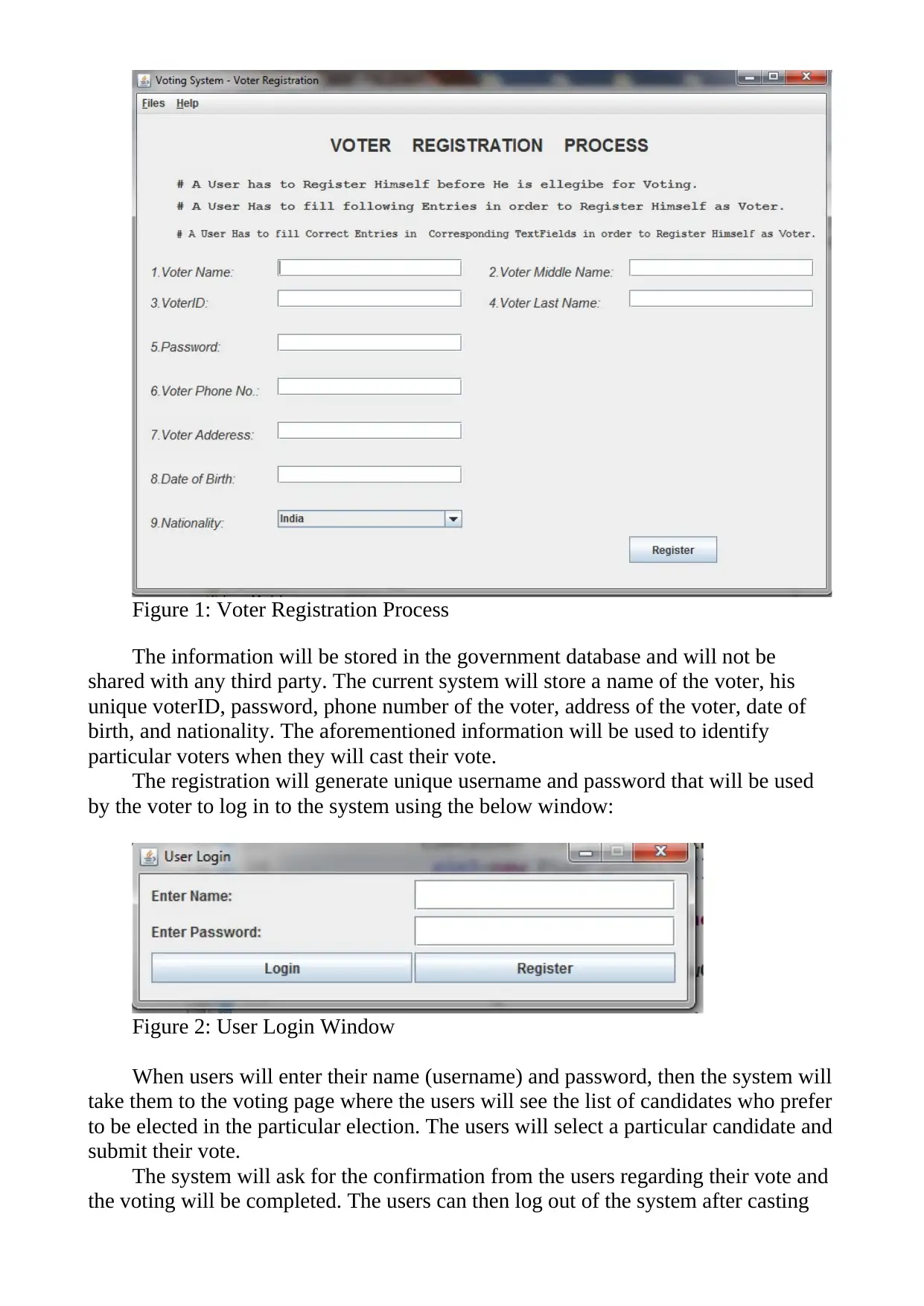
Figure 1: Voter Registration Process
The information will be stored in the government database and will not be
shared with any third party. The current system will store a name of the voter, his
unique voterID, password, phone number of the voter, address of the voter, date of
birth, and nationality. The aforementioned information will be used to identify
particular voters when they will cast their vote.
The registration will generate unique username and password that will be used
by the voter to log in to the system using the below window:
Figure 2: User Login Window
When users will enter their name (username) and password, then the system will
take them to the voting page where the users will see the list of candidates who prefer
to be elected in the particular election. The users will select a particular candidate and
submit their vote.
The system will ask for the confirmation from the users regarding their vote and
the voting will be completed. The users can then log out of the system after casting
The information will be stored in the government database and will not be
shared with any third party. The current system will store a name of the voter, his
unique voterID, password, phone number of the voter, address of the voter, date of
birth, and nationality. The aforementioned information will be used to identify
particular voters when they will cast their vote.
The registration will generate unique username and password that will be used
by the voter to log in to the system using the below window:
Figure 2: User Login Window
When users will enter their name (username) and password, then the system will
take them to the voting page where the users will see the list of candidates who prefer
to be elected in the particular election. The users will select a particular candidate and
submit their vote.
The system will ask for the confirmation from the users regarding their vote and
the voting will be completed. The users can then log out of the system after casting
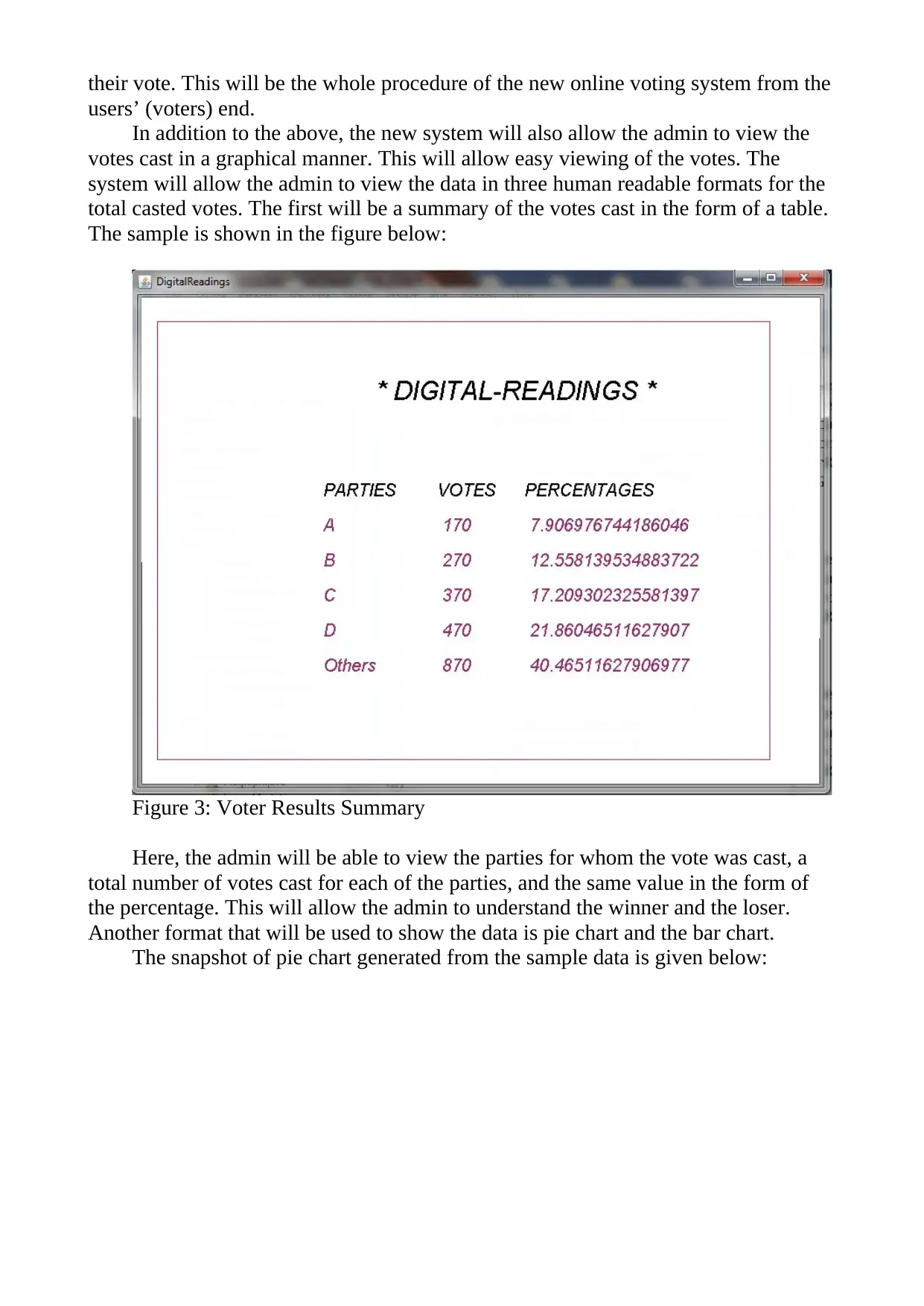
their vote. This will be the whole procedure of the new online voting system from the
users’ (voters) end.
In addition to the above, the new system will also allow the admin to view the
votes cast in a graphical manner. This will allow easy viewing of the votes. The
system will allow the admin to view the data in three human readable formats for the
total casted votes. The first will be a summary of the votes cast in the form of a table.
The sample is shown in the figure below:
Figure 3: Voter Results Summary
Here, the admin will be able to view the parties for whom the vote was cast, a
total number of votes cast for each of the parties, and the same value in the form of
the percentage. This will allow the admin to understand the winner and the loser.
Another format that will be used to show the data is pie chart and the bar chart.
The snapshot of pie chart generated from the sample data is given below:
users’ (voters) end.
In addition to the above, the new system will also allow the admin to view the
votes cast in a graphical manner. This will allow easy viewing of the votes. The
system will allow the admin to view the data in three human readable formats for the
total casted votes. The first will be a summary of the votes cast in the form of a table.
The sample is shown in the figure below:
Figure 3: Voter Results Summary
Here, the admin will be able to view the parties for whom the vote was cast, a
total number of votes cast for each of the parties, and the same value in the form of
the percentage. This will allow the admin to understand the winner and the loser.
Another format that will be used to show the data is pie chart and the bar chart.
The snapshot of pie chart generated from the sample data is given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
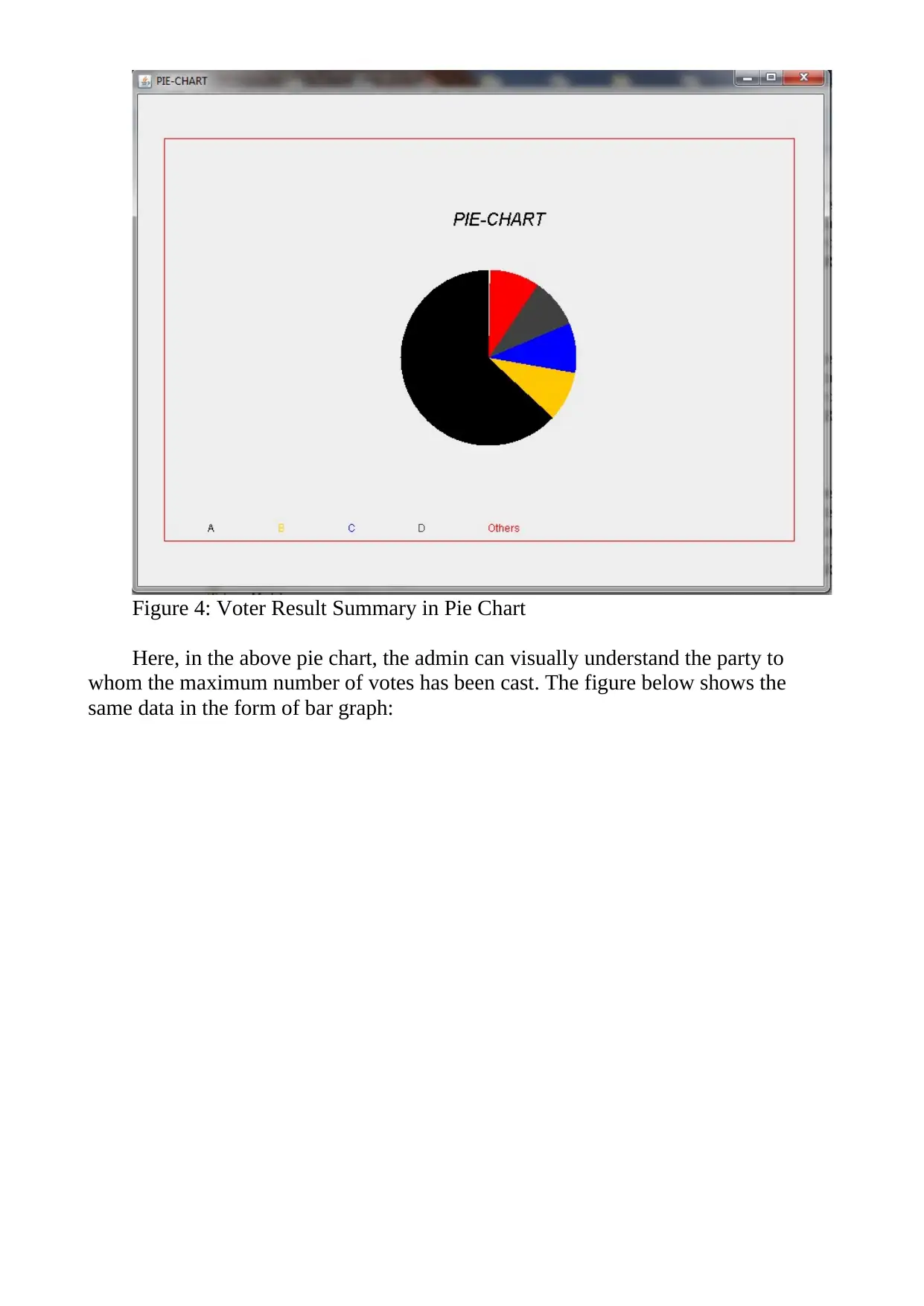
Figure 4: Voter Result Summary in Pie Chart
Here, in the above pie chart, the admin can visually understand the party to
whom the maximum number of votes has been cast. The figure below shows the
same data in the form of bar graph:
Here, in the above pie chart, the admin can visually understand the party to
whom the maximum number of votes has been cast. The figure below shows the
same data in the form of bar graph:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
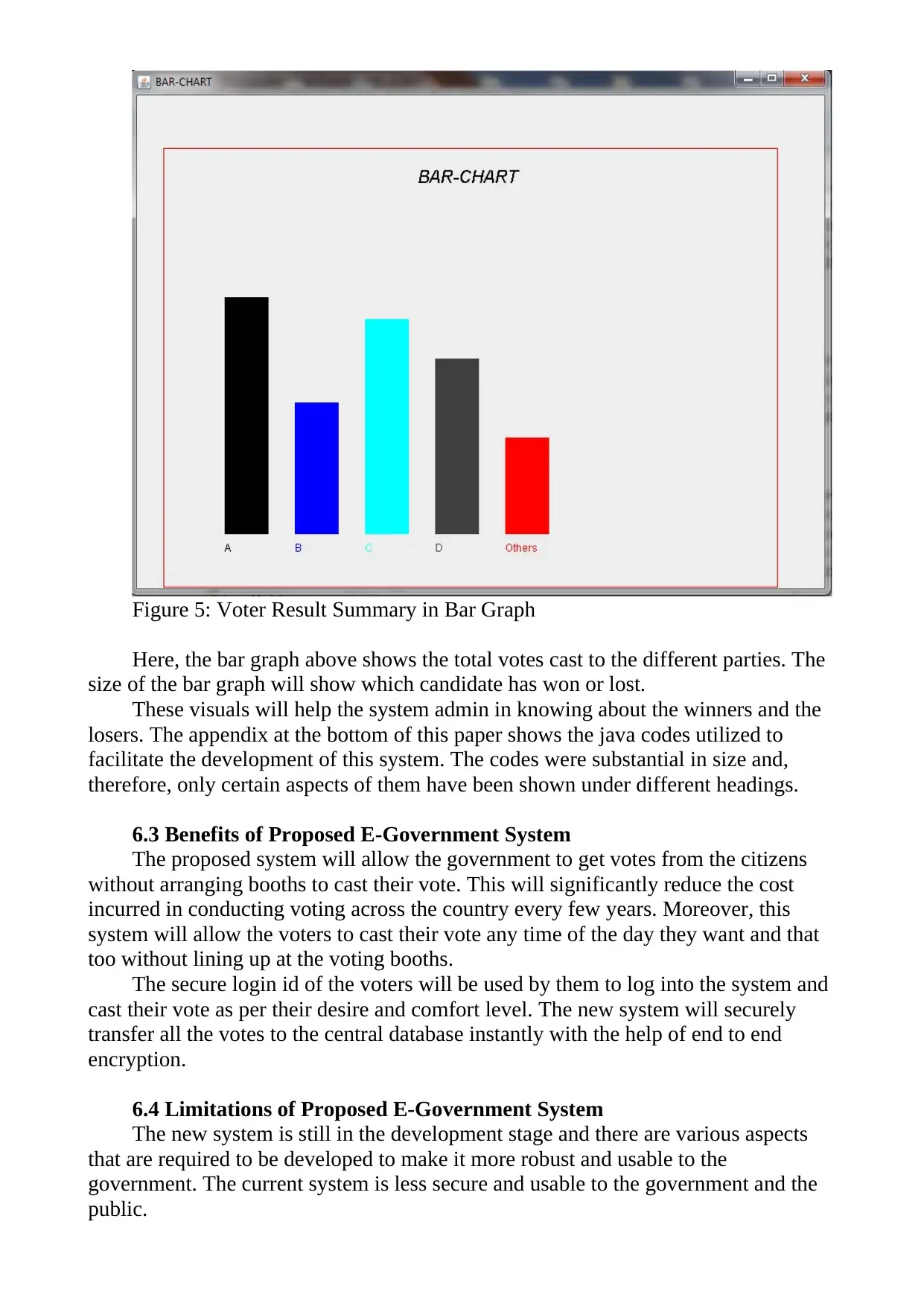
Figure 5: Voter Result Summary in Bar Graph
Here, the bar graph above shows the total votes cast to the different parties. The
size of the bar graph will show which candidate has won or lost.
These visuals will help the system admin in knowing about the winners and the
losers. The appendix at the bottom of this paper shows the java codes utilized to
facilitate the development of this system. The codes were substantial in size and,
therefore, only certain aspects of them have been shown under different headings.
6.3 Benefits of Proposed E-Government System
The proposed system will allow the government to get votes from the citizens
without arranging booths to cast their vote. This will significantly reduce the cost
incurred in conducting voting across the country every few years. Moreover, this
system will allow the voters to cast their vote any time of the day they want and that
too without lining up at the voting booths.
The secure login id of the voters will be used by them to log into the system and
cast their vote as per their desire and comfort level. The new system will securely
transfer all the votes to the central database instantly with the help of end to end
encryption.
6.4 Limitations of Proposed E-Government System
The new system is still in the development stage and there are various aspects
that are required to be developed to make it more robust and usable to the
government. The current system is less secure and usable to the government and the
public.
Here, the bar graph above shows the total votes cast to the different parties. The
size of the bar graph will show which candidate has won or lost.
These visuals will help the system admin in knowing about the winners and the
losers. The appendix at the bottom of this paper shows the java codes utilized to
facilitate the development of this system. The codes were substantial in size and,
therefore, only certain aspects of them have been shown under different headings.
6.3 Benefits of Proposed E-Government System
The proposed system will allow the government to get votes from the citizens
without arranging booths to cast their vote. This will significantly reduce the cost
incurred in conducting voting across the country every few years. Moreover, this
system will allow the voters to cast their vote any time of the day they want and that
too without lining up at the voting booths.
The secure login id of the voters will be used by them to log into the system and
cast their vote as per their desire and comfort level. The new system will securely
transfer all the votes to the central database instantly with the help of end to end
encryption.
6.4 Limitations of Proposed E-Government System
The new system is still in the development stage and there are various aspects
that are required to be developed to make it more robust and usable to the
government. The current system is less secure and usable to the government and the
public.

There are some demerits to the current system also. The use of current system
requires that the voters know how to cast their votes through this system. In addition
to this, there are other prerequisites such as the users should be able to operate
computers, access internet, open browser, and establish the connection.
7. SWOT analysis of research results
The current section will look into the strength, weakness, opportunities, and
threats for the system.
- Strengths: The current system will allow the government to conduct online
elections. It will be easier for the government to conduct the election without
engaging extra resources. The system will allow the voters to vote securely
with end to end encryption.
- Weaknesses: The current system is in its development stage and the
implementation of the system will require robust security measures and it is a
mission critical system and can attract external challenges.
- Opportunities: The new system will likely open opportunities in other
governmental department at smaller to larger scale to conduct the voting. The
use of the system is likely to increase.
- Threats: The threats are in the form of hackers who might try to infiltrate the
system to steal the voter data.
8. Conclusion
The use of e-government system is likely to improve if the governments of
various countries make effort to educate their population. The use of e-government
system will help in the easy management of most of the governmental activities and
also facilitate the successful interaction with the citizens.
The current paper proposed an online voting system that is expected to be used
by the government to conducting voting. The voters will cast votes by logging into
the system which will be then summarized by the system automatically in the form of
a table, pie chart and bar chart to know the result of the election.
9. References
[1] Al-khamayseh, S., Lawrence, E. and Zmijewska, A., 2006, December.
Towards understanding success factors in interactive mobile government. In the
Proceedings of Euro mGov.
[2] Altameem, T., Zairi, M. and Alshawi, S., 2006, November. Critical success
factors of e-government: A proposed model for e-government implementation.
In Innovations in Information Technology, 2006 (pp. 1-5). IEEE.
[3] Becker, J., Niehaves, B., Algermissen, L., Delfmann, P. and Falk, T., 2004.
E-government success factors. Electronic Government, pp.503-506.
[4] Chircu, A.M. and Lee, D.H.D., 2005. E-government: key success factors for
value discovery and realisation. Electronic Government, an International
Journal, 2(1), pp.11-25.
requires that the voters know how to cast their votes through this system. In addition
to this, there are other prerequisites such as the users should be able to operate
computers, access internet, open browser, and establish the connection.
7. SWOT analysis of research results
The current section will look into the strength, weakness, opportunities, and
threats for the system.
- Strengths: The current system will allow the government to conduct online
elections. It will be easier for the government to conduct the election without
engaging extra resources. The system will allow the voters to vote securely
with end to end encryption.
- Weaknesses: The current system is in its development stage and the
implementation of the system will require robust security measures and it is a
mission critical system and can attract external challenges.
- Opportunities: The new system will likely open opportunities in other
governmental department at smaller to larger scale to conduct the voting. The
use of the system is likely to increase.
- Threats: The threats are in the form of hackers who might try to infiltrate the
system to steal the voter data.
8. Conclusion
The use of e-government system is likely to improve if the governments of
various countries make effort to educate their population. The use of e-government
system will help in the easy management of most of the governmental activities and
also facilitate the successful interaction with the citizens.
The current paper proposed an online voting system that is expected to be used
by the government to conducting voting. The voters will cast votes by logging into
the system which will be then summarized by the system automatically in the form of
a table, pie chart and bar chart to know the result of the election.
9. References
[1] Al-khamayseh, S., Lawrence, E. and Zmijewska, A., 2006, December.
Towards understanding success factors in interactive mobile government. In the
Proceedings of Euro mGov.
[2] Altameem, T., Zairi, M. and Alshawi, S., 2006, November. Critical success
factors of e-government: A proposed model for e-government implementation.
In Innovations in Information Technology, 2006 (pp. 1-5). IEEE.
[3] Becker, J., Niehaves, B., Algermissen, L., Delfmann, P. and Falk, T., 2004.
E-government success factors. Electronic Government, pp.503-506.
[4] Chircu, A.M. and Lee, D.H.D., 2005. E-government: key success factors for
value discovery and realisation. Electronic Government, an International
Journal, 2(1), pp.11-25.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[5] Gil-García, J.R. and Pardo, T.A., 2005. E-government success factors:
Mapping practical tools to theoretical foundations. Government information
quarterly, 22(2), pp.187-216.
[6] Mcclure, N. and Lohry, K., MCCLURE NEIL and LOHRY KERMIT,
2001. Electronic voting system. U.S. Patent 6,250,548.
[7] Kohno, T., Stubblefield, A., Rubin, A.D. and Wallach, D.S., 2004, May.
Analysis of an electronic voting system. In Security and Privacy, 2004. Proceedings.
2004 IEEE Symposium on (pp. 27-40). IEEE.
[8] Draper, S.W. and Brown, M.I., 2004. Increasing interactivity in lectures
using an electronic voting system. Journal of computer assisted learning, 20(2),
pp.81-94.
[9] Kennedy, G.E. and Cutts, Q.I., 2005. The association between students' use
of an electronic voting system and their learning outcomes. Journal of Computer
Assisted Learning, 21(4), pp.260-268.
[10] Stuart, S.A., Brown, M.I. and Draper, S.W., 2004. Using an electronic
voting system in logic lectures: one practitioner's application. Journal of Computer
Assisted Learning, 20(2), pp.95-102.
[11] Mercuri, R., 2002. A better ballot box?. IEEE spectrum, 39(10), pp.46-50.
[12] Bederson, B.B., Lee, B., Sherman, R.M., Herrnson, P.S. and Niemi, R.G.,
2003, April. Electronic voting system usability issues. In Proceedings of the SIGCHI
conference on Human factors in computing systems (pp. 145-152). ACM.
[13] Bannet, J., Price, D.W., Rudys, A., Singer, J. and Wallach, D.S., 2004.
Hack-a-vote: Security issues with electronic voting systems. IEEE Security &
Privacy, 2(1), pp.32-37.
[14] Boneh, D. and Franklin, M., 2001, August. Identity-based encryption from
the Weil pairing. In Annual International Cryptology Conference (pp. 213-229).
Springer Berlin Heidelberg.
[15] Clarkson, M.R., Chong, S. and Myers, A.C., 2008, May. Civitas: Toward a
secure voting system. In Security and Privacy, 2008. SP 2008. IEEE Symposium
on (pp. 354-368). IEEE.
Summary of the article
The current paper was focused on proposing a new electronic voting system that
will assist the government in conducting the online voting for the elections. The
system will be secure with the end to end encryption to ensure that no data theft
occurs during the transfer. The key demerit of the system is the security from the end
of the government. It has to be ensured that all the external threats are kept at bay
when using the online voting system. The secondary research approach was
considered to mine the information required to conduct the study and develop the
system. Overall, it can be stated that the new system will allow the government and
public to have improved voting experience if implemented successfully.
Appendix
Mapping practical tools to theoretical foundations. Government information
quarterly, 22(2), pp.187-216.
[6] Mcclure, N. and Lohry, K., MCCLURE NEIL and LOHRY KERMIT,
2001. Electronic voting system. U.S. Patent 6,250,548.
[7] Kohno, T., Stubblefield, A., Rubin, A.D. and Wallach, D.S., 2004, May.
Analysis of an electronic voting system. In Security and Privacy, 2004. Proceedings.
2004 IEEE Symposium on (pp. 27-40). IEEE.
[8] Draper, S.W. and Brown, M.I., 2004. Increasing interactivity in lectures
using an electronic voting system. Journal of computer assisted learning, 20(2),
pp.81-94.
[9] Kennedy, G.E. and Cutts, Q.I., 2005. The association between students' use
of an electronic voting system and their learning outcomes. Journal of Computer
Assisted Learning, 21(4), pp.260-268.
[10] Stuart, S.A., Brown, M.I. and Draper, S.W., 2004. Using an electronic
voting system in logic lectures: one practitioner's application. Journal of Computer
Assisted Learning, 20(2), pp.95-102.
[11] Mercuri, R., 2002. A better ballot box?. IEEE spectrum, 39(10), pp.46-50.
[12] Bederson, B.B., Lee, B., Sherman, R.M., Herrnson, P.S. and Niemi, R.G.,
2003, April. Electronic voting system usability issues. In Proceedings of the SIGCHI
conference on Human factors in computing systems (pp. 145-152). ACM.
[13] Bannet, J., Price, D.W., Rudys, A., Singer, J. and Wallach, D.S., 2004.
Hack-a-vote: Security issues with electronic voting systems. IEEE Security &
Privacy, 2(1), pp.32-37.
[14] Boneh, D. and Franklin, M., 2001, August. Identity-based encryption from
the Weil pairing. In Annual International Cryptology Conference (pp. 213-229).
Springer Berlin Heidelberg.
[15] Clarkson, M.R., Chong, S. and Myers, A.C., 2008, May. Civitas: Toward a
secure voting system. In Security and Privacy, 2008. SP 2008. IEEE Symposium
on (pp. 354-368). IEEE.
Summary of the article
The current paper was focused on proposing a new electronic voting system that
will assist the government in conducting the online voting for the elections. The
system will be secure with the end to end encryption to ensure that no data theft
occurs during the transfer. The key demerit of the system is the security from the end
of the government. It has to be ensured that all the external threats are kept at bay
when using the online voting system. The secondary research approach was
considered to mine the information required to conduct the study and develop the
system. Overall, it can be stated that the new system will allow the government and
public to have improved voting experience if implemented successfully.
Appendix
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Server Side
Pie graph
package ServerSide;
import java.awt.*;
import java.util.Map;
import java.util.TreeMap;
import java.awt.event.*;
import javax.swing.*;
import java.util.*;
import java.lang.*;
import javax.swing.JPanel;
import java.sql.*;
class Piegraph extends JFrame {
PiegraphBuild pie1;
public Piegraph() {
buildWindow();
}
protected void buildWindow() {
Container con=getContentPane();
pie1=new PiegraphBuild();
addWindowListener(new WindowAdapter()
{
public void windowClosing(WindowEvent e)
{
System.exit(0);
}
});
con.add(pie1);
setTitle("PIE-CHART");
setSize(800,600);
setVisible(true);
}
public static void main(String []args) {
new Piegraph();
}
Pie graph
package ServerSide;
import java.awt.*;
import java.util.Map;
import java.util.TreeMap;
import java.awt.event.*;
import javax.swing.*;
import java.util.*;
import java.lang.*;
import javax.swing.JPanel;
import java.sql.*;
class Piegraph extends JFrame {
PiegraphBuild pie1;
public Piegraph() {
buildWindow();
}
protected void buildWindow() {
Container con=getContentPane();
pie1=new PiegraphBuild();
addWindowListener(new WindowAdapter()
{
public void windowClosing(WindowEvent e)
{
System.exit(0);
}
});
con.add(pie1);
setTitle("PIE-CHART");
setSize(800,600);
setVisible(true);
}
public static void main(String []args) {
new Piegraph();
}

}
class PiegraphBuild extends JPanel
{
Connection con;
Statement stmt;
ResultSet rs;
String sql,sql1;
private Map<String,Integer> pieData;
PiegraphBuild()
{
pieData = new TreeMap<String,Integer>();
getConnection();
initializeData();
setBackground(Color.white);
}
///////////////////////getdata///////////////////////
protected void getConnection()
{
System.out.println("DataBase is connected");
try
{
Class.forName("sun.jdbc.odbc.JdbcOdbcDriver");
con=DriverManager.getConnection("jdbc:odbc:voting");
}
catch(Exception e)
{
System.out.println("JDBC:ODBC driver failed to load.");
return;
}
try
{
stmt = con.createStatement();
}
class PiegraphBuild extends JPanel
{
Connection con;
Statement stmt;
ResultSet rs;
String sql,sql1;
private Map<String,Integer> pieData;
PiegraphBuild()
{
pieData = new TreeMap<String,Integer>();
getConnection();
initializeData();
setBackground(Color.white);
}
///////////////////////getdata///////////////////////
protected void getConnection()
{
System.out.println("DataBase is connected");
try
{
Class.forName("sun.jdbc.odbc.JdbcOdbcDriver");
con=DriverManager.getConnection("jdbc:odbc:voting");
}
catch(Exception e)
{
System.out.println("JDBC:ODBC driver failed to load.");
return;
}
try
{
stmt = con.createStatement();
}
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 34
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





