ITC 506 Assignment 1: Early Launch Scenario Ethical Analysis Report
VerifiedAdded on 2020/03/04
|8
|2384
|63
Homework Assignment
AI Summary
This assignment analyzes the 'Early Launch' scenario, focusing on an IT company's ethical dilemma regarding a project's encryption. The Program Director faces pressure to deliver the 'Willis project' early by omitting encryption, a decision that the Project Manager opposes due to security concerns. The analysis uses the 'Doing Ethics Technique' to explore the facts, non-ethical and ethical issues, and the stakeholders affected. The assignment identifies the ethical implications of different options, such as delivering the project without encryption to meet deadlines, or prioritizing data security and ethical business practices. The document concludes with a recommendation to prioritize data security and maintain the company's reputation, highlighting the importance of ethical decision-making in project management. The assignment also includes a comprehensive reference list supporting the analysis, adhering to APA style guidelines.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Early Launch/Scenario 3
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1250
Early Launch/Scenario 3
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1250
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Early Launch/Scenario 3
Q1. What's going on?
The title of this video is ‘Early Launch’. It starts with a scenario where the Program Director
of the company is talking over the phone with the Chief Information Officer ("Scenario 3:
Early Launch", 2017). Then the Project Manager enters the room. The Program Director
informs him that the Chief Executive Officer of the company is creating pressure on the
Chief Information Officer regarding early delivery of the ‘Willis project’. The CIA of the
company even asked the Program Director whether their team will be able to deliver the
Willis project one month earlier by eliminating the encryption part of the project. The CIA
was worried whether the client company will sign the next contract or not whose worth is
over and above 3 million. In reply the Project Manager said that according to Jason, the
Senior Developer of the company, encryption is an important requirement for the Willey
system that is needed to done. The Program Director on the other hand said that the
chances of the system to get hacked is very little and if they deliver the project earlier then
this will open several opportunities for the company in future. The situation depicted
tension and dilemma between the Program director and the Project Manager of the
company.
Q2. What are the facts?
The scenario depicts an IT based company. There is a confusion regarding what can be done.
The Program Director suggests that if the project team delivers the project one month
earlier then there will be several opportunities for the company as well as the team.
Delivering the project earlier will convince the client company to sign the next contract
whose worth is more than 3 million. The company will definitely gain and even the project
Your Name
Q1. What's going on?
The title of this video is ‘Early Launch’. It starts with a scenario where the Program Director
of the company is talking over the phone with the Chief Information Officer ("Scenario 3:
Early Launch", 2017). Then the Project Manager enters the room. The Program Director
informs him that the Chief Executive Officer of the company is creating pressure on the
Chief Information Officer regarding early delivery of the ‘Willis project’. The CIA of the
company even asked the Program Director whether their team will be able to deliver the
Willis project one month earlier by eliminating the encryption part of the project. The CIA
was worried whether the client company will sign the next contract or not whose worth is
over and above 3 million. In reply the Project Manager said that according to Jason, the
Senior Developer of the company, encryption is an important requirement for the Willey
system that is needed to done. The Program Director on the other hand said that the
chances of the system to get hacked is very little and if they deliver the project earlier then
this will open several opportunities for the company in future. The situation depicted
tension and dilemma between the Program director and the Project Manager of the
company.
Q2. What are the facts?
The scenario depicts an IT based company. There is a confusion regarding what can be done.
The Program Director suggests that if the project team delivers the project one month
earlier then there will be several opportunities for the company as well as the team.
Delivering the project earlier will convince the client company to sign the next contract
whose worth is more than 3 million. The company will definitely gain and even the project
Your Name

Early Launch/Scenario 3
team will earn huge bonuses. The project team can deliver the Willis project one month
earlier by not including the encryption part and later on attach encryption software after
few weeks (Stallings & Tahiliani, 2014). The Project manager on the other hand has a
different point of view. According to him, encryption is an essential part of the Willey
system and not encrypting it can cause serious trouble for the client company. It will also
affect the reputation of the vendor company.
Q3. What are the issues (non-ethical)?
There is a severe non ethical issue in this matter. The ethics of encryption is an important
part of organization or business ethics (Bellwood et al., 2014). When a vendor company
delivers software, then it is the key responsibility of the client company to incorporate the
security matter in the software project that it is delivering. If the company delivers the
Willis project without encryption then it is a major non ethical issue in the security of the
business organization. This will show that the company is not responsible enough to take
care of the security of its client. Later on if the software of the Willey system gets hacked,
then this will cause a loss of several sensitive data of the client company. If the vendor
company does not encrypt the software that it is delivering to the client company just to
deliver it before one month, then this becomes a non ethical issue in terms of business
security and safety.
Q4. Who is affected?
If the vendor company delivers the Willis project to the client company without encrypting it
then there will a lot affected people. First of all, if the unprotected and unencrypted
software gets hacked then this will cause a severe loss of sensitive information. This will in
Your Name
team will earn huge bonuses. The project team can deliver the Willis project one month
earlier by not including the encryption part and later on attach encryption software after
few weeks (Stallings & Tahiliani, 2014). The Project manager on the other hand has a
different point of view. According to him, encryption is an essential part of the Willey
system and not encrypting it can cause serious trouble for the client company. It will also
affect the reputation of the vendor company.
Q3. What are the issues (non-ethical)?
There is a severe non ethical issue in this matter. The ethics of encryption is an important
part of organization or business ethics (Bellwood et al., 2014). When a vendor company
delivers software, then it is the key responsibility of the client company to incorporate the
security matter in the software project that it is delivering. If the company delivers the
Willis project without encryption then it is a major non ethical issue in the security of the
business organization. This will show that the company is not responsible enough to take
care of the security of its client. Later on if the software of the Willey system gets hacked,
then this will cause a loss of several sensitive data of the client company. If the vendor
company does not encrypt the software that it is delivering to the client company just to
deliver it before one month, then this becomes a non ethical issue in terms of business
security and safety.
Q4. Who is affected?
If the vendor company delivers the Willis project to the client company without encrypting it
then there will a lot affected people. First of all, if the unprotected and unencrypted
software gets hacked then this will cause a severe loss of sensitive information. This will in
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Early Launch/Scenario 3
turn affect millions of people whose sensitive data is lost. Millions of people might lose their
financial and other important information to the hackers. This can spoil the entire life of the
people. Secondly, if the system gets hacked then the vendor company’s reputation will fall
to a great extent. Other companies will not give them any contracts in the future and this
will generate huge loss for the vendor company. Delivering a product that is not secured
and protected will not reflect well on the company. This will harm the company in future.
The company will either have to shut down or will run at huge loss (Bednarz, 2013). If the
client company files a complaint against the vendor company then this will lead to legal
proceedings which will be extremely harmful for the company. So it can be concluded that it
will affect the people whose data is stolen and also the vendor company in terms of their
reputation.
Q5. What are the ethical issues and their implications?
There are several ethical issues in this scenario. The Program Director agrees to what the
Project Manager says and delivers a safe and secured product to the client company. In this
case the code of business ethics is followed. Though the vendor company does not deliver
the product before the given deadline but it delivers a product that is safe and reliable. This
will be good for the company in the future. Another issue can be that the Project Manager
agrees to what the Director says and delivers the product before time but with no
encryption. Here the implication can be severe. Later on when the system gets hacked then
it not only affects the millions of users but also the project team of the company along with
the reputation of the company. There can be another ethical issue that is the Project
Manager disagrees to provide non encrypted software to the client (Martin, 2017). Here the
Your Name
turn affect millions of people whose sensitive data is lost. Millions of people might lose their
financial and other important information to the hackers. This can spoil the entire life of the
people. Secondly, if the system gets hacked then the vendor company’s reputation will fall
to a great extent. Other companies will not give them any contracts in the future and this
will generate huge loss for the vendor company. Delivering a product that is not secured
and protected will not reflect well on the company. This will harm the company in future.
The company will either have to shut down or will run at huge loss (Bednarz, 2013). If the
client company files a complaint against the vendor company then this will lead to legal
proceedings which will be extremely harmful for the company. So it can be concluded that it
will affect the people whose data is stolen and also the vendor company in terms of their
reputation.
Q5. What are the ethical issues and their implications?
There are several ethical issues in this scenario. The Program Director agrees to what the
Project Manager says and delivers a safe and secured product to the client company. In this
case the code of business ethics is followed. Though the vendor company does not deliver
the product before the given deadline but it delivers a product that is safe and reliable. This
will be good for the company in the future. Another issue can be that the Project Manager
agrees to what the Director says and delivers the product before time but with no
encryption. Here the implication can be severe. Later on when the system gets hacked then
it not only affects the millions of users but also the project team of the company along with
the reputation of the company. There can be another ethical issue that is the Project
Manager disagrees to provide non encrypted software to the client (Martin, 2017). Here the
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Early Launch/Scenario 3
project manager can be removed from this responsibility. This will demotivate the
employees of the company.
Q6. What can be done about it?
There are several possibilities that can be done about this situation. The Project Director can
agree with the Project Manager and explains the CIA regarding the need of encryption in the
company. In this case, the company will deliver the project within the original deadline but
will not be able to deliver one month earlier. But on the other hand the company will not
lose its reputation and will do well in the future (Lazo & Strider, 2015). This will result in
giving high protection to the data and also raise the reputation of the company. The Project
director must have faith on the Project Manager and follow no shortcut approach.
Q7. What are the options?
There are three options available in the video. First option is that the Project Manager
agrees to what the Project director says and then they proceed to deliver the project before
one month without encryption of the software. The consequence of this is dangerous in
case of any hack in the future. The reputation of the company is spoilt. And on the other
hand the job of the Project Manager is at risk. The second option is that the Project
Manager disagrees with the Project Director. Here the Project Manager is taken off from the
project. This will lead to dissatisfaction of employees in the organization (Franks & Davis,
2015). The third option is that the Project Director agrees with the Project Manager and
does not follow any shortcut. Here the company’s reputation is maintained and there will
not be any loss of sensitive data in the future. This will be ethically correct.
Your Name
project manager can be removed from this responsibility. This will demotivate the
employees of the company.
Q6. What can be done about it?
There are several possibilities that can be done about this situation. The Project Director can
agree with the Project Manager and explains the CIA regarding the need of encryption in the
company. In this case, the company will deliver the project within the original deadline but
will not be able to deliver one month earlier. But on the other hand the company will not
lose its reputation and will do well in the future (Lazo & Strider, 2015). This will result in
giving high protection to the data and also raise the reputation of the company. The Project
director must have faith on the Project Manager and follow no shortcut approach.
Q7. What are the options?
There are three options available in the video. First option is that the Project Manager
agrees to what the Project director says and then they proceed to deliver the project before
one month without encryption of the software. The consequence of this is dangerous in
case of any hack in the future. The reputation of the company is spoilt. And on the other
hand the job of the Project Manager is at risk. The second option is that the Project
Manager disagrees with the Project Director. Here the Project Manager is taken off from the
project. This will lead to dissatisfaction of employees in the organization (Franks & Davis,
2015). The third option is that the Project Director agrees with the Project Manager and
does not follow any shortcut. Here the company’s reputation is maintained and there will
not be any loss of sensitive data in the future. This will be ethically correct.
Your Name

Early Launch/Scenario 3
Q8. Which option is the best and why?
The best option for the company is to encrypt the software and then deliver it. This is the
best option because this is ethically correct. This will not only protect the users from any
loss but also will protect the company from loss of reputation ("Scenario III 3 Program
Director Listens to team", 2017). The company will deliver a safe and reliable project to the
client. This will enhance its reputation. This option will help in maintaining the ethics of the
business and organization.
References
Bednarz, T. F. (2013). Ethics in Business. Practical Ethics for Food Professionals: Ethics in
Research, Education and the Workplace, 75-91.
Bellwood, T. A., Chumbley, R. B., Rutkowski, M. F., & Tarpinian, A. (2014). U.S. Patent No.
8,724,811. Washington, DC: U.S. Patent and Trademark Office.
Franks, D. M., & Davis, R. (2015). The costs of conflict. SUSTAIN: Cutting Edge Business
Solutions, 2(February), 58-59.
Lazo, A., & Strider, S. H. (2015). Preparing students to be ethical decision
makers. International Journal of Research in Social Sciences, 5(1), 388-409.
Martin, J. A. (2017). Encryption Backdoors: A Discussion of Feasibility, Ethics, and the Future
of Cryptography.
Scenario 3: Early Launch. (2017). YouTube. Retrieved 9 August 2017, from
https://www.youtube.com/watch?v=v5M7ohdZ6qA
Scenario III 3 Program Director Listens to team. (2017). YouTube. Retrieved 9 August 2017,
from https://www.youtube.com/watch?
annotation_id=annotation_726259537&feature=iv&src_vid=BEtvmNou7r8&v=JjLK_Jj
Au48
Stallings, W., & Tahiliani, M. P. (2014). Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.
Do not remove the following marking sheet.
Your Name
Q8. Which option is the best and why?
The best option for the company is to encrypt the software and then deliver it. This is the
best option because this is ethically correct. This will not only protect the users from any
loss but also will protect the company from loss of reputation ("Scenario III 3 Program
Director Listens to team", 2017). The company will deliver a safe and reliable project to the
client. This will enhance its reputation. This option will help in maintaining the ethics of the
business and organization.
References
Bednarz, T. F. (2013). Ethics in Business. Practical Ethics for Food Professionals: Ethics in
Research, Education and the Workplace, 75-91.
Bellwood, T. A., Chumbley, R. B., Rutkowski, M. F., & Tarpinian, A. (2014). U.S. Patent No.
8,724,811. Washington, DC: U.S. Patent and Trademark Office.
Franks, D. M., & Davis, R. (2015). The costs of conflict. SUSTAIN: Cutting Edge Business
Solutions, 2(February), 58-59.
Lazo, A., & Strider, S. H. (2015). Preparing students to be ethical decision
makers. International Journal of Research in Social Sciences, 5(1), 388-409.
Martin, J. A. (2017). Encryption Backdoors: A Discussion of Feasibility, Ethics, and the Future
of Cryptography.
Scenario 3: Early Launch. (2017). YouTube. Retrieved 9 August 2017, from
https://www.youtube.com/watch?v=v5M7ohdZ6qA
Scenario III 3 Program Director Listens to team. (2017). YouTube. Retrieved 9 August 2017,
from https://www.youtube.com/watch?
annotation_id=annotation_726259537&feature=iv&src_vid=BEtvmNou7r8&v=JjLK_Jj
Au48
Stallings, W., & Tahiliani, M. P. (2014). Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.
Do not remove the following marking sheet.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Early Launch/Scenario 3
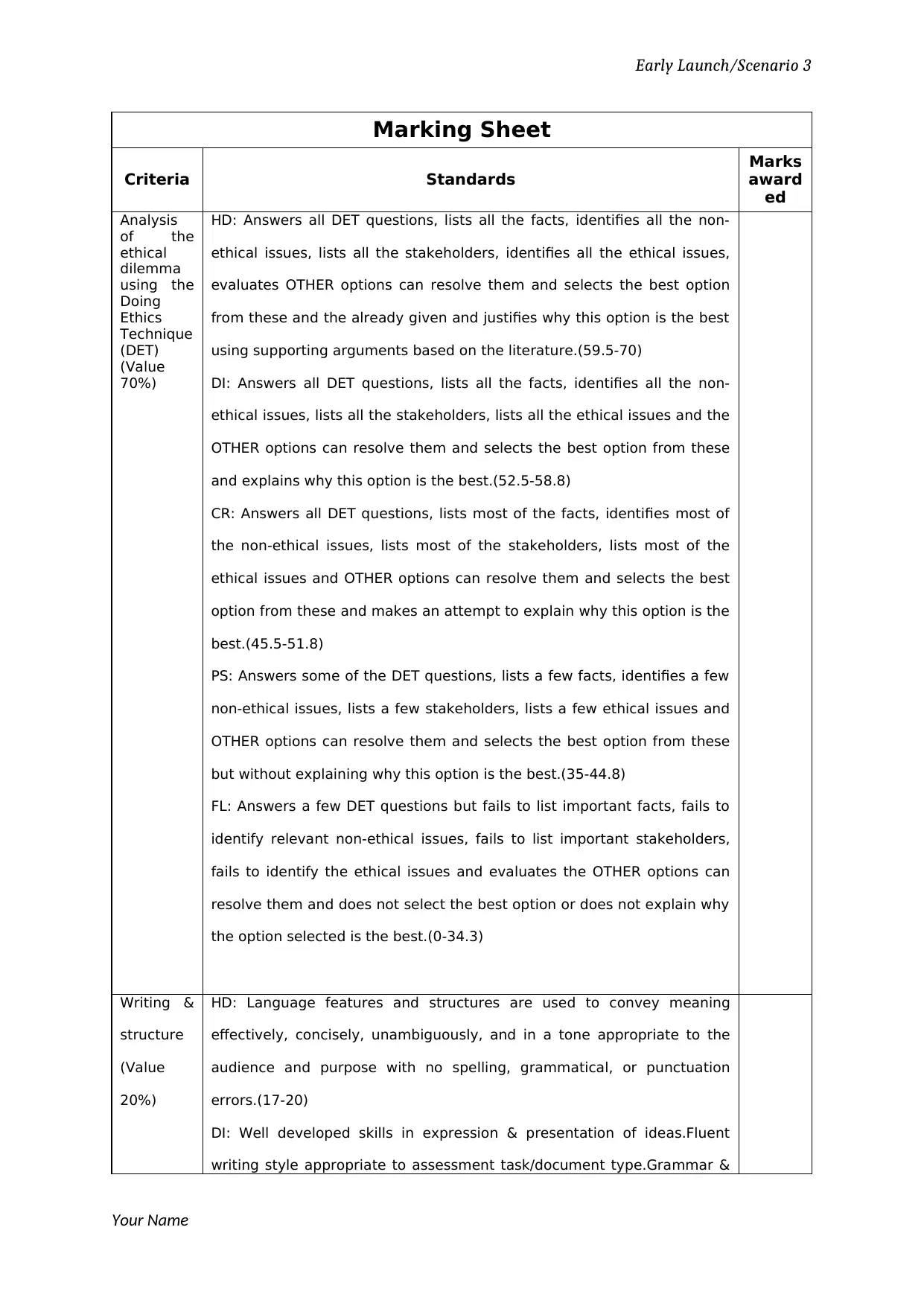
Marking Sheet
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates OTHER options can resolve them and selects the best option
from these and the already given and justifies why this option is the best
using supporting arguments based on the literature.(59.5-70)
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and the
OTHER options can resolve them and selects the best option from these
and explains why this option is the best.(52.5-58.8)
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and OTHER options can resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.(45.5-51.8)
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
OTHER options can resolve them and selects the best option from these
but without explaining why this option is the best.(35-44.8)
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the OTHER options can
resolve them and does not select the best option or does not explain why
the option selected is the best.(0-34.3)
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.(17-20)
DI: Well developed skills in expression & presentation of ideas.Fluent
writing style appropriate to assessment task/document type.Grammar &
Your Name
Marking Sheet
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates OTHER options can resolve them and selects the best option
from these and the already given and justifies why this option is the best
using supporting arguments based on the literature.(59.5-70)
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and the
OTHER options can resolve them and selects the best option from these
and explains why this option is the best.(52.5-58.8)
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and OTHER options can resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.(45.5-51.8)
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
OTHER options can resolve them and selects the best option from these
but without explaining why this option is the best.(35-44.8)
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the OTHER options can
resolve them and does not select the best option or does not explain why
the option selected is the best.(0-34.3)
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.(17-20)
DI: Well developed skills in expression & presentation of ideas.Fluent
writing style appropriate to assessment task/document type.Grammar &
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Early Launch/Scenario 3
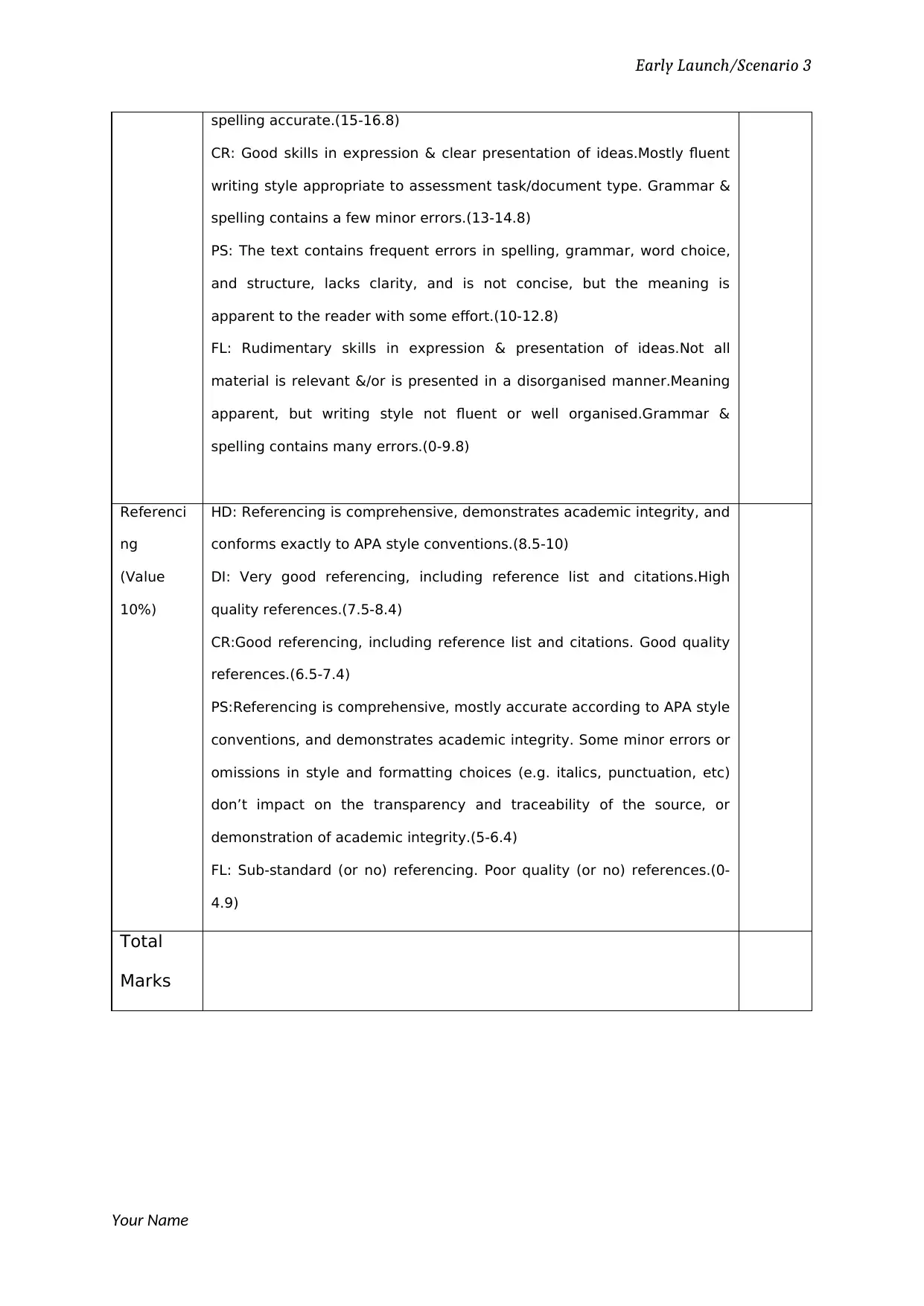
spelling accurate.(15-16.8)
CR: Good skills in expression & clear presentation of ideas.Mostly fluent
writing style appropriate to assessment task/document type. Grammar &
spelling contains a few minor errors.(13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.(10-12.8)
FL: Rudimentary skills in expression & presentation of ideas.Not all
material is relevant &/or is presented in a disorganised manner.Meaning
apparent, but writing style not fluent or well organised.Grammar &
spelling contains many errors.(0-9.8)
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.(8.5-10)
DI: Very good referencing, including reference list and citations.High
quality references.(7.5-8.4)
CR:Good referencing, including reference list and citations. Good quality
references.(6.5-7.4)
PS:Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.(5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references.(0-
4.9)
Total
Marks
Your Name
spelling accurate.(15-16.8)
CR: Good skills in expression & clear presentation of ideas.Mostly fluent
writing style appropriate to assessment task/document type. Grammar &
spelling contains a few minor errors.(13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.(10-12.8)
FL: Rudimentary skills in expression & presentation of ideas.Not all
material is relevant &/or is presented in a disorganised manner.Meaning
apparent, but writing style not fluent or well organised.Grammar &
spelling contains many errors.(0-9.8)
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.(8.5-10)
DI: Very good referencing, including reference list and citations.High
quality references.(7.5-8.4)
CR:Good referencing, including reference list and citations. Good quality
references.(6.5-7.4)
PS:Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.(5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references.(0-
4.9)
Total
Marks
Your Name
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





