Risk Management Plan: ORANGE E-commerce Business Growth Strategy
VerifiedAdded on 2023/01/04
|11
|2640
|92
Report
AI Summary
This report details a risk management plan tailored for ORANGE, an e-commerce company specializing in mail-order retail. The plan addresses potential risks associated with e-commerce, including security breaches, payment fraud, and data protection. The report outlines strategies to mitigate these risks, such as staff training, customer policy implementation, Payment Card Industry (PCI) compliance, system security measures, and strict legal frameworks. It also highlights the importance of encryption, digital signatures, and password management to ensure secure transactions. The plan aims to support ORANGE's goal of increasing sales by 30% over two years and expanding its internal staff by 15% within the next year. The report emphasizes the significance of customer trust and the need for comprehensive security measures to ensure the long-term success of the e-commerce business. The report incorporates previous individual and team assessments, modified based on instructor feedback.

Running head: RISK MANAGEMENT PLAN
RISK MANAGEMENT PLAN
Name of the Student
Name of the University
Author Note
RISK MANAGEMENT PLAN
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT PLAN 1
Abstract:
The motivation behind this paper is to make a risk management plan for ORANGE that is a
web-based business organization represent considerable authority in mail-request retail.
Throughout the following two years, the organization wants to build deals by 30%, just as
increment its inside staff by 15% throughout the following year to help this exertion.
Abstract:
The motivation behind this paper is to make a risk management plan for ORANGE that is a
web-based business organization represent considerable authority in mail-request retail.
Throughout the following two years, the organization wants to build deals by 30%, just as
increment its inside staff by 15% throughout the following year to help this exertion.

2RISK MANAGEMENT PLAN
Introduction:
Electronic trade or internet business is the purchasing of goods as well as selling of
products. It's prominent to purchase anything as well as pay web based, transmitting
information or assets over the electronic based system, fundamentally the Internet. These
exchanges of the business happen business-to-purchaser, business to business, customer to
buyer as well as shopper to business. The terms e commerce as well as e-business are
frequently utilized reciprocally (Trautman, 2015). At present days the individuals are not
setting off to that that are physical for purchasing things that are necessary, yet by checking
rather the subtleties as well as photos of that particular item on such of a gadget, on the point
by requesting as well as paying on the internet based pay system; following by a couple of
times, the sellers shall convey that the things to the entry way of the customers. The
electronic based business is such a kind of a procedure which empowers the deal or even in
buying of necessary products as well as ventures over the mobile or PC based systems with
some of the techniques intended for the particular reason. The main purpose of this paper is
to make a risk management plan for ORANGE that is a web-based business organization
represent considerable authority in mail-request retail. The security is one of the most of the
fundamental worry in web-based shopping. In light of security, purchasers have been
frightened to buy things from the e commerce websites, as well as this influences in the e-
organizations. The disappointment or achievement of an internet based shopping or business
that relies upon the entire security as well as protection issues, as well as the trust of the
clients' is fundamental for the improvement in the web based business (Stiles et al., 2014).
Web based business for the most part, it is made by utilizing a blend of phone, fax, TV, PCs,
the web, electronic instalments, cash exchange frameworks as well as electronic information
trade. In this investigation, we just consider electronic business exchanges which are made by
means of the web.
Introduction:
Electronic trade or internet business is the purchasing of goods as well as selling of
products. It's prominent to purchase anything as well as pay web based, transmitting
information or assets over the electronic based system, fundamentally the Internet. These
exchanges of the business happen business-to-purchaser, business to business, customer to
buyer as well as shopper to business. The terms e commerce as well as e-business are
frequently utilized reciprocally (Trautman, 2015). At present days the individuals are not
setting off to that that are physical for purchasing things that are necessary, yet by checking
rather the subtleties as well as photos of that particular item on such of a gadget, on the point
by requesting as well as paying on the internet based pay system; following by a couple of
times, the sellers shall convey that the things to the entry way of the customers. The
electronic based business is such a kind of a procedure which empowers the deal or even in
buying of necessary products as well as ventures over the mobile or PC based systems with
some of the techniques intended for the particular reason. The main purpose of this paper is
to make a risk management plan for ORANGE that is a web-based business organization
represent considerable authority in mail-request retail. The security is one of the most of the
fundamental worry in web-based shopping. In light of security, purchasers have been
frightened to buy things from the e commerce websites, as well as this influences in the e-
organizations. The disappointment or achievement of an internet based shopping or business
that relies upon the entire security as well as protection issues, as well as the trust of the
clients' is fundamental for the improvement in the web based business (Stiles et al., 2014).
Web based business for the most part, it is made by utilizing a blend of phone, fax, TV, PCs,
the web, electronic instalments, cash exchange frameworks as well as electronic information
trade. In this investigation, we just consider electronic business exchanges which are made by
means of the web.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK MANAGEMENT PLAN
Evaluation of e-commerce:
Online business is additionally improving business connections. It encourages the
system type of association where little, adaptable firms depend on accomplice organizations
for provisions as well as conveyance to satisfy changing client need all the more successfully.
In the course of recent years, internet business has developed quickly, offering focal points to
the two organizations as well as customers since the principal web-based business exchange
in 1995 (Sharma & Lijuan, 2014). As the changing guidelines lower hindrances to internet
business, it is normal that online business will keep on advancing later on (Patil & Divekar,
2014). Spread of web get to as well as the rising desires that accompany these are two of the
fundamental drivers to the advancement of internet business. New web clients come online
consistently; as of now, almost 40% of the total populace has a web association.
Risks and Security in the way of E-commerce:
The security is the key aspect among a huge part of the key worry in internet based
shopping. In light of security, purchasers have been startled to buy things from the web
business destinations, similarly as this effect in the e-affiliations. The disappointment or
achievement of an electronic shopping or business that relies in general security similarly as
protection issues, similarly as the trust of the clients' is vital for the improvement in the online
business (Stiles et al., 2014). Online business for the most part, it is made by utilizing a blend
of phone, fax, TV, PCs, the web, electronic bits, cash exchange frameworks similarly as
electronic information trade. The achievement or disappointment of an electronic business
relies on security similarly as affirmation. Clients' trust is vital to business improvement.
With the progression of electronic segment, security related issues have changed into a key
issue. Burglary of individual information similarly as unapproved get to are totally significant
issues in electronic business for clients similarly as master networks alike. Security is the
Evaluation of e-commerce:
Online business is additionally improving business connections. It encourages the
system type of association where little, adaptable firms depend on accomplice organizations
for provisions as well as conveyance to satisfy changing client need all the more successfully.
In the course of recent years, internet business has developed quickly, offering focal points to
the two organizations as well as customers since the principal web-based business exchange
in 1995 (Sharma & Lijuan, 2014). As the changing guidelines lower hindrances to internet
business, it is normal that online business will keep on advancing later on (Patil & Divekar,
2014). Spread of web get to as well as the rising desires that accompany these are two of the
fundamental drivers to the advancement of internet business. New web clients come online
consistently; as of now, almost 40% of the total populace has a web association.
Risks and Security in the way of E-commerce:
The security is the key aspect among a huge part of the key worry in internet based
shopping. In light of security, purchasers have been startled to buy things from the web
business destinations, similarly as this effect in the e-affiliations. The disappointment or
achievement of an electronic shopping or business that relies in general security similarly as
protection issues, similarly as the trust of the clients' is vital for the improvement in the online
business (Stiles et al., 2014). Online business for the most part, it is made by utilizing a blend
of phone, fax, TV, PCs, the web, electronic bits, cash exchange frameworks similarly as
electronic information trade. The achievement or disappointment of an electronic business
relies on security similarly as affirmation. Clients' trust is vital to business improvement.
With the progression of electronic segment, security related issues have changed into a key
issue. Burglary of individual information similarly as unapproved get to are totally significant
issues in electronic business for clients similarly as master networks alike. Security is the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RISK MANAGEMENT PLAN
point of confinement of a person for controlling the terms under which their own data is
gotten similarly as utilized (Mohapatra, 2013).
Risk management to reduce e-commerce:
At present, internet business has turned into a pattern of present-day economy with
the own exceptional stage called Magento. Since it's another pattern so online storekeeper
can't stay away from dangers in exchanges. The administration of risk in online business
exchanges is viewed as the most significant factor for the haul that is long, survival of users’
business.
Those dangers may identify with web extortion, data security, installment techniques
or even web-based business enactment. Once getting into one of these dangers, this would be
exorbitant for the business for fathoming as well as to recoup (Mayayise & Olusegun
Osunmakinde, 2014). Every year, it costs internet business as well as direct promoting the
organisations billions of dollars per year, by making this the basic for the traders for
comprehending the dangers that are related with working with together on the e commerce.
So, entrepreneurs ought for building up an inside arrangement for addressing the dangers that
are potential as well as train the staff on the execution of this. By following are the most
significant methodology for overseeing risk in internet business transactions. The risk
Electronic installment is a simple, brisk as well as shabby installment framework dependent
on electronic correspondence. Purchasers as well as merchants do their arrangements without
seeing one another. The fast advancement of the web conveyed internet business to open
consideration, as well as it was recognized to be loaded with potential (Hajli, 2013). In online
business, there are numerous manners by which a corrupt individual can swindle clients. In
the beginning of the web, the prevalence of web-based business relied on whether
point of confinement of a person for controlling the terms under which their own data is
gotten similarly as utilized (Mohapatra, 2013).
Risk management to reduce e-commerce:
At present, internet business has turned into a pattern of present-day economy with
the own exceptional stage called Magento. Since it's another pattern so online storekeeper
can't stay away from dangers in exchanges. The administration of risk in online business
exchanges is viewed as the most significant factor for the haul that is long, survival of users’
business.
Those dangers may identify with web extortion, data security, installment techniques
or even web-based business enactment. Once getting into one of these dangers, this would be
exorbitant for the business for fathoming as well as to recoup (Mayayise & Olusegun
Osunmakinde, 2014). Every year, it costs internet business as well as direct promoting the
organisations billions of dollars per year, by making this the basic for the traders for
comprehending the dangers that are related with working with together on the e commerce.
So, entrepreneurs ought for building up an inside arrangement for addressing the dangers that
are potential as well as train the staff on the execution of this. By following are the most
significant methodology for overseeing risk in internet business transactions. The risk
Electronic installment is a simple, brisk as well as shabby installment framework dependent
on electronic correspondence. Purchasers as well as merchants do their arrangements without
seeing one another. The fast advancement of the web conveyed internet business to open
consideration, as well as it was recognized to be loaded with potential (Hajli, 2013). In online
business, there are numerous manners by which a corrupt individual can swindle clients. In
the beginning of the web, the prevalence of web-based business relied on whether

5RISK MANAGEMENT PLAN
information exchanges could be made more secure. Despite the fact that the accompanying
choices cannot be useful for closure risk in online business, they may decrease it:
1. Training to team on e-commerce risks:
Train users’ group in risk management approaches as well as methodology, as well as the
misrepresentation as well as security dangers engaged with an online business exchange
(Verbano, & Venturini, 2013). The more educated users’ association is, the simpler this will
be to battle online dangers as well as to complete risk mitigating measures.
2. Spread organizational policies to customers:
Make beyond any doubt users’ site gives direction to clients as users’ protection
approach, data security, shipping as well as charging arrangements, as well as discount
arrangements. This is likewise useful to evade disappointment as well as debate.
3. Ensure Payment Card Industry (PCI) consistence:
All internet business associations are needed to be the PCI-agreeable as well as must
cling to this principle that are illustrated by the Payment Card Industry Security Standards
Council (Elzamly & Hussin, 2014). In the event that users’ association isn't PCI-agreeable,
this should be presented for the serious fines as well as the loss of the capacity of instalment
of it.
4. Protect the web-based business from interruption:
Check the framework for infections as well as programmers, make programming
updates, change passwords, as well as check delicate information all the time for making the
framework secure for internet business exchanges.
information exchanges could be made more secure. Despite the fact that the accompanying
choices cannot be useful for closure risk in online business, they may decrease it:
1. Training to team on e-commerce risks:
Train users’ group in risk management approaches as well as methodology, as well as the
misrepresentation as well as security dangers engaged with an online business exchange
(Verbano, & Venturini, 2013). The more educated users’ association is, the simpler this will
be to battle online dangers as well as to complete risk mitigating measures.
2. Spread organizational policies to customers:
Make beyond any doubt users’ site gives direction to clients as users’ protection
approach, data security, shipping as well as charging arrangements, as well as discount
arrangements. This is likewise useful to evade disappointment as well as debate.
3. Ensure Payment Card Industry (PCI) consistence:
All internet business associations are needed to be the PCI-agreeable as well as must
cling to this principle that are illustrated by the Payment Card Industry Security Standards
Council (Elzamly & Hussin, 2014). In the event that users’ association isn't PCI-agreeable,
this should be presented for the serious fines as well as the loss of the capacity of instalment
of it.
4. Protect the web-based business from interruption:
Check the framework for infections as well as programmers, make programming
updates, change passwords, as well as check delicate information all the time for making the
framework secure for internet business exchanges.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6RISK MANAGEMENT PLAN
5. Know details of the payment service provider contract:
Be comfortable with the agreement, specially the zones which allude for holding the
reserves as well as the risk of chargeback. By knowing the time span as well as the conditions
under that stores could be held, as well as known risk for deceitful exchanges.
6. Make strict laws:
To group web-based business extortion as a kind of wrongdoing in which culprits meddle
with web-based business with the end goal of sick the gains that are gotten.
7 Privacy-enhancing technologies:
Although there having some numerous advances utilized for reconnaissance, the
advances for framing understandings about the arrival of private information, the advances
for naming as well as trust, and the protection improving advances (PETs) ought to be a lot
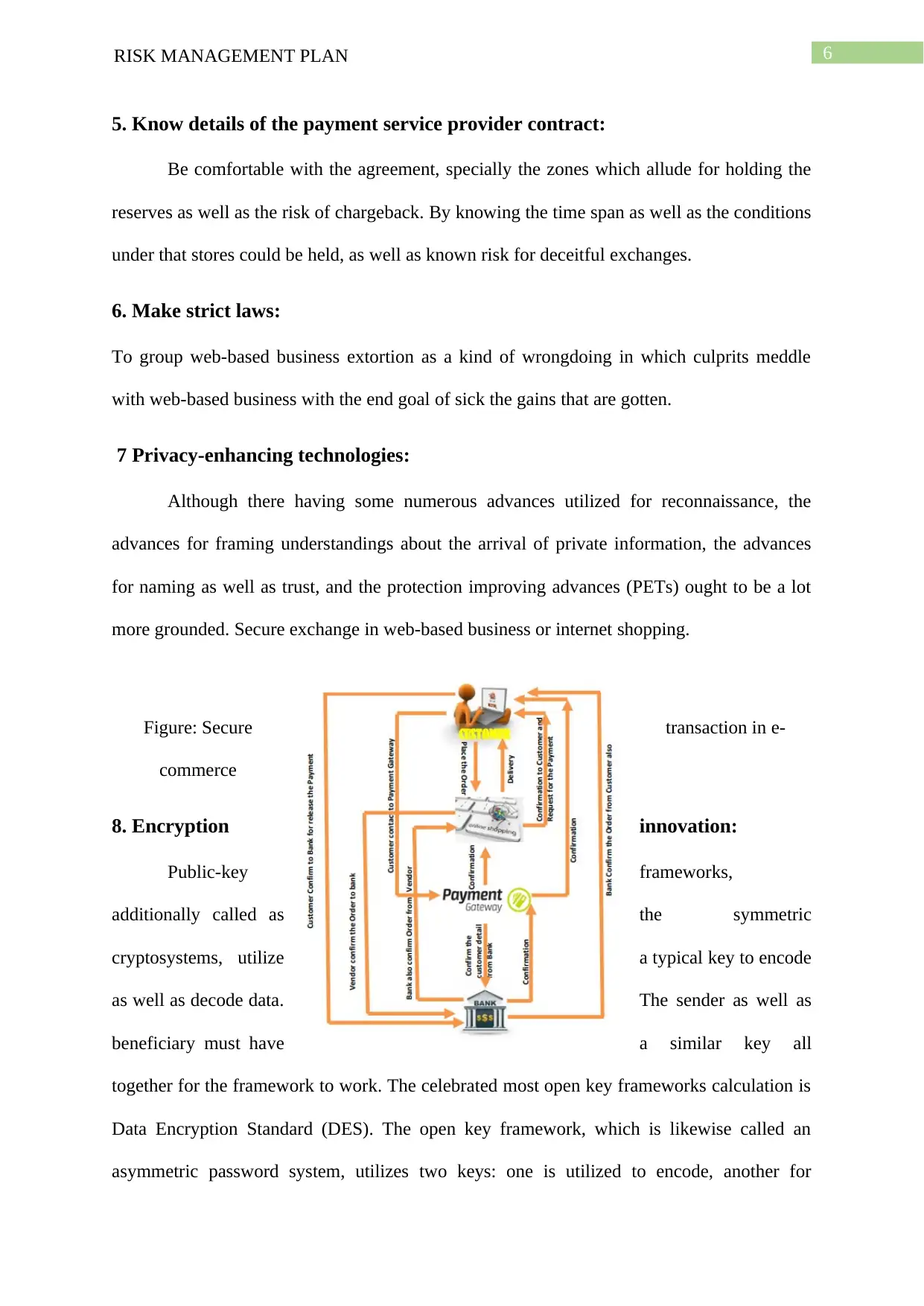
more grounded. Secure exchange in web-based business or internet shopping.
Figure: Secure transaction in e-
commerce
8. Encryption innovation:
Public-key frameworks,
additionally called as the symmetric
cryptosystems, utilize a typical key to encode
as well as decode data. The sender as well as
beneficiary must have a similar key all
together for the framework to work. The celebrated most open key frameworks calculation is
Data Encryption Standard (DES). The open key framework, which is likewise called an
asymmetric password system, utilizes two keys: one is utilized to encode, another for
5. Know details of the payment service provider contract:
Be comfortable with the agreement, specially the zones which allude for holding the
reserves as well as the risk of chargeback. By knowing the time span as well as the conditions
under that stores could be held, as well as known risk for deceitful exchanges.
6. Make strict laws:
To group web-based business extortion as a kind of wrongdoing in which culprits meddle
with web-based business with the end goal of sick the gains that are gotten.
7 Privacy-enhancing technologies:
Although there having some numerous advances utilized for reconnaissance, the
advances for framing understandings about the arrival of private information, the advances
for naming as well as trust, and the protection improving advances (PETs) ought to be a lot
more grounded. Secure exchange in web-based business or internet shopping.
Figure: Secure transaction in e-
commerce
8. Encryption innovation:
Public-key frameworks,
additionally called as the symmetric
cryptosystems, utilize a typical key to encode
as well as decode data. The sender as well as
beneficiary must have a similar key all
together for the framework to work. The celebrated most open key frameworks calculation is
Data Encryption Standard (DES). The open key framework, which is likewise called an
asymmetric password system, utilizes two keys: one is utilized to encode, another for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK MANAGEMENT PLAN
unscrambling. Every client has two keys: an open key as well as a private key (Clemons et
al., 2015). Clients can convey an open key; due to the scientific connection between these
two keys, anybody with the open key can encode information, however just a client with the
help of the private key can decode it. So as to ensure the private key is the stayed discreet, all
clients' keys ought to act naturally created. Cryptographic advances can be utilized at
different focuses in the installment framework.
9. Computerized signature:
An advanced mark is one cryptographic label which just a single creator is able to
figure. The tag may be attached with any sort of data or even information which the main
creator would make, as well as the legitimacy of the labels can be checked by any of the
individual who can get to the data or the information (Chiu et al., 2014). A computerized
mark is the striking utilization of open key cryptography, as well as is a similarity of a
transcribed mark.
10. Change Password:
It is constantly prescribed to change or modify one's secret key all the time, as well as the
secret key shouldn't be anything but difficult to figure.
Conclusion:
Over the most recent couple of years, numerous specialists have offered answers for
the security as well as protection issues which are existed in the provisos in web-based
business exchanges. Web based business incorporates the transmission as well as trade of
data, items, as well as administrations—online exchanges as well as installment, as well as
furthermore asset sharing between endeavours. In that push for making the electronic
business secure, there are numerous issues to be comprehended past protection as well as
security (Chaffey, 2015). Past purchasers as well as dealers, budgetary establishments,
unscrambling. Every client has two keys: an open key as well as a private key (Clemons et
al., 2015). Clients can convey an open key; due to the scientific connection between these
two keys, anybody with the open key can encode information, however just a client with the
help of the private key can decode it. So as to ensure the private key is the stayed discreet, all
clients' keys ought to act naturally created. Cryptographic advances can be utilized at
different focuses in the installment framework.
9. Computerized signature:
An advanced mark is one cryptographic label which just a single creator is able to
figure. The tag may be attached with any sort of data or even information which the main
creator would make, as well as the legitimacy of the labels can be checked by any of the
individual who can get to the data or the information (Chiu et al., 2014). A computerized
mark is the striking utilization of open key cryptography, as well as is a similarity of a
transcribed mark.
10. Change Password:
It is constantly prescribed to change or modify one's secret key all the time, as well as the
secret key shouldn't be anything but difficult to figure.
Conclusion:
Over the most recent couple of years, numerous specialists have offered answers for
the security as well as protection issues which are existed in the provisos in web-based
business exchanges. Web based business incorporates the transmission as well as trade of
data, items, as well as administrations—online exchanges as well as installment, as well as
furthermore asset sharing between endeavours. In that push for making the electronic
business secure, there are numerous issues to be comprehended past protection as well as
security (Chaffey, 2015). Past purchasers as well as dealers, budgetary establishments,

8RISK MANAGEMENT PLAN
government offices, affirmation bodies, circulation focuses, as well as different associations
must contribute arrangements. Be that as it may, authoritative approaches as well as
electronic mark innovation may assume as significant a job in security as well as protection
as some other arrangement.
government offices, affirmation bodies, circulation focuses, as well as different associations
must contribute arrangements. Be that as it may, authoritative approaches as well as
electronic mark innovation may assume as significant a job in security as well as protection
as some other arrangement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK MANAGEMENT PLAN
References:
Chaffey, D. (2015). Digital business and e-commerce management. London: Pearson
Education Limited.
Chiu, C. M., Wang, E. T., Fang, Y. H., & Huang, H. Y. (2014). Understanding customers'
repeat purchase intentions in B2C e‐commerce: the roles of utilitarian value, hedonic
value and perceived risk. Information Systems Journal, 24(1), 85-114.
Clemons, E. K., Jin, F., Wilson, J., Ren, F., Matt, C., Hess, T., & Koh, N. (2013, January).
The role of trust in successful ecommerce websites in china: Field observations and
experimental studies. In 2013 46th Hawaii International Conference on System
Sciences (pp. 4002-4011). IEEE.
Elzamly, A., & Hussin, B. (2014). A comparison of fuzzy and stepwise multiple regression
analysis techniques for managing software project risks: Implementation
phase. International Management Review, 10(1), 43-54.
Flanagin, A. J., Metzger, M. J., Pure, R., Markov, A., & Hartsell, E. (2014). Mitigating risk in
ecommerce transactions: perceptions of information credibility and the role of user-
generated ratings in product quality and purchase intention. Electronic Commerce
Research, 14(1), 1-23.
Hajli, M. (2013). A research framework for social commerce adoption. Information
Management & Computer Security, 21(3), 144-154.
Mayayise, T., & Olusegun Osunmakinde, I. (2014). E-commerce assurance models and
trustworthiness issues: an empirical study. Information Management & Computer
Security, 22(1), 76-96.
References:
Chaffey, D. (2015). Digital business and e-commerce management. London: Pearson
Education Limited.
Chiu, C. M., Wang, E. T., Fang, Y. H., & Huang, H. Y. (2014). Understanding customers'
repeat purchase intentions in B2C e‐commerce: the roles of utilitarian value, hedonic
value and perceived risk. Information Systems Journal, 24(1), 85-114.
Clemons, E. K., Jin, F., Wilson, J., Ren, F., Matt, C., Hess, T., & Koh, N. (2013, January).
The role of trust in successful ecommerce websites in china: Field observations and
experimental studies. In 2013 46th Hawaii International Conference on System
Sciences (pp. 4002-4011). IEEE.
Elzamly, A., & Hussin, B. (2014). A comparison of fuzzy and stepwise multiple regression
analysis techniques for managing software project risks: Implementation
phase. International Management Review, 10(1), 43-54.
Flanagin, A. J., Metzger, M. J., Pure, R., Markov, A., & Hartsell, E. (2014). Mitigating risk in
ecommerce transactions: perceptions of information credibility and the role of user-
generated ratings in product quality and purchase intention. Electronic Commerce
Research, 14(1), 1-23.
Hajli, M. (2013). A research framework for social commerce adoption. Information
Management & Computer Security, 21(3), 144-154.
Mayayise, T., & Olusegun Osunmakinde, I. (2014). E-commerce assurance models and
trustworthiness issues: an empirical study. Information Management & Computer
Security, 22(1), 76-96.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK MANAGEMENT PLAN
Mohapatra, S. (2013). E-commerce Strategy. In E-Commerce Strategy (pp. 155-171).
Springer, Boston, MA.
Patil, H., & Divekar, B. R. (2014). Inventory management challenges for B2C e-commerce
retailers. Procedia Economics and Finance, 11, 561-571.
Sharma, G., & Lijuan, W. (2014). Ethical perspectives on e-commerce: an empirical
investigation. Internet Research, 24(4), 414-435.
Stiles, P. W., McIndoe, D. B., & Meyer, M. G. (2014). U.S. Patent No. 8,775,195.
Washington, DC: U.S. Patent and Trademark Office.
Trautman, L. J. (2015). E-Commerce, cyber, and electronic payment system risks: lessons
from PayPal. UC Davis Bus. LJ, 16, 261.
Verbano, C., & Venturini, K. (2013). Managing risks in SMEs: A literature review and
research agenda. Journal of technology management & innovation, 8(3), 186-197.
Mohapatra, S. (2013). E-commerce Strategy. In E-Commerce Strategy (pp. 155-171).
Springer, Boston, MA.
Patil, H., & Divekar, B. R. (2014). Inventory management challenges for B2C e-commerce
retailers. Procedia Economics and Finance, 11, 561-571.
Sharma, G., & Lijuan, W. (2014). Ethical perspectives on e-commerce: an empirical
investigation. Internet Research, 24(4), 414-435.
Stiles, P. W., McIndoe, D. B., & Meyer, M. G. (2014). U.S. Patent No. 8,775,195.
Washington, DC: U.S. Patent and Trademark Office.
Trautman, L. J. (2015). E-Commerce, cyber, and electronic payment system risks: lessons
from PayPal. UC Davis Bus. LJ, 16, 261.
Verbano, C., & Venturini, K. (2013). Managing risks in SMEs: A literature review and
research agenda. Journal of technology management & innovation, 8(3), 186-197.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





