An Analysis of E-Commerce Security: Vulnerabilities and Solutions
VerifiedAdded on 2022/09/16
|10
|2094
|23
Report
AI Summary
This report provides an in-depth analysis of e-commerce security, exploring various vulnerabilities and threats that online businesses face. It begins with an overview of the increasing number of cyberattacks targeting e-commerce platforms, highlighting the use of advanced technologies and common vulnerabilities such as cross-site forgery requests and SQL injection. The report delves into specific vulnerabilities, including administrative security vulnerabilities like weak authentication and command execution, physical security vulnerabilities such as buffer overflow and cross-site scripting, and technical security vulnerabilities like SQL injection and manipulation of prices. The report also provides recommendations and countermeasures, emphasizing the importance of incorporating security into the web application's structure, conducting risk assessments, using firewalls, and implementing strict input validation. A logical security design is included. The conclusion stresses the importance of proactive security measures for both businesses and customers, along with the role of advancements like intrusion detection systems and programming language frameworks in improving application security. The paper also emphasizes on the importance of the e-commerce application security for the end-user and the owner of the business.

1
E-Commerce Industry
Student’s Name:
Institution Affiliation:
E-Commerce Industry
Student’s Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
Increase in online transaction has led to increase in number of attacks on online payment systems
such as e-commerce. Most of the attacks have employed latest advancement and use of third
party applications. Some other attacks have employed the use of common vulnerabilities such as
cross-site forgery request and sql injection. The paper will discuss both the use of online tools
and vulnerabilities found in web applications. Attacker have many opportunities after exploiting
the web application vulnerabilities. One of the most common impact is information exploit
which normally leads to other exploitations including transfer of money through cards. It can
also lead to the closure of the complete shut down of a business.
Keywords: Vulnerabilities, Online frauds, Attack on E-commerce, E-Commerce, Security
breach.
Introduction
Starting a business requires you to be available in Internet which exposes you to all kinds of
attacks. Most of the well established business thinks of coming up with well estalished E-
commerce websites. E-commerce is a way of buying and selling goods goods and services in
Intenet web application. For a business e-commerce application to prosper in Intenet it must have
well esatblished cyber security team which handles all sorts of vulnerabilities in an application.
Threats in Internet can come in any form, either through the server, authentication, configuration
or the client's side. Many factors promotes the vulnerabilities in a web application. The reasons
are not restrictive to these frameworks, however their effect turns out to be a lot more prominent
essentially in light of the wide introduction that an online site has, and due to the money related
nature of the exchanges.
Abstract
Increase in online transaction has led to increase in number of attacks on online payment systems
such as e-commerce. Most of the attacks have employed latest advancement and use of third
party applications. Some other attacks have employed the use of common vulnerabilities such as
cross-site forgery request and sql injection. The paper will discuss both the use of online tools
and vulnerabilities found in web applications. Attacker have many opportunities after exploiting
the web application vulnerabilities. One of the most common impact is information exploit
which normally leads to other exploitations including transfer of money through cards. It can
also lead to the closure of the complete shut down of a business.
Keywords: Vulnerabilities, Online frauds, Attack on E-commerce, E-Commerce, Security
breach.
Introduction
Starting a business requires you to be available in Internet which exposes you to all kinds of
attacks. Most of the well established business thinks of coming up with well estalished E-
commerce websites. E-commerce is a way of buying and selling goods goods and services in
Intenet web application. For a business e-commerce application to prosper in Intenet it must have
well esatblished cyber security team which handles all sorts of vulnerabilities in an application.
Threats in Internet can come in any form, either through the server, authentication, configuration
or the client's side. Many factors promotes the vulnerabilities in a web application. The reasons
are not restrictive to these frameworks, however their effect turns out to be a lot more prominent
essentially in light of the wide introduction that an online site has, and due to the money related
nature of the exchanges.

3
In various cases, we've discovered that web based business destinations tout their 128-piece SSL
authentications as evidence that their locales are all around verified. The naïveté of clients to
trust in this has decreased in the course of recent years, yet even now there are a large number of
sites showing Verisign or Thawte testament symbols as confirmation of their security.
Vulnerabilities
Vulnerabilities is a situation where an attacker lessens the authentication system and logins to the
clients or administrator account (González Briones, Chamoso, & Barriuso, 2016). In this paper
we will discuss vulnerabilities that normally occurs in e-commerce check out.
(i) Administrative security vulnerabilities in E-commerce
Weak authentication. According to Gartner’s Magic Quadrant document validation
instruments that don't disallow different fizzled logins can be attacked utilizing
apparatuses(Oliveira, Alhinho, Rita, & Dhillon, 2017). So also, if the site utilizes header
transfer control protocol Basic Authentication or does not ignore session Secure Sockets
Layer, an aggressor can sniff the traffic to find client's confirmation or potentially
approval accreditations(Wang, Liu, Yan, & Jiang, 2016, November), (Thalassinos, &
Thalassinos, 2018).
Command execution. According to Verizon Data Breach Investigation report the most
annihilating web application vulnerabilities happen when the CGI content enables an
aggressor to execute working framework directions because of lacking info
approval(Crifasi, Pike, Stuedemann, Alnaeli, & Altahat, 2018, May), (Deepa, &
Thilagam, 2016).
In various cases, we've discovered that web based business destinations tout their 128-piece SSL
authentications as evidence that their locales are all around verified. The naïveté of clients to
trust in this has decreased in the course of recent years, yet even now there are a large number of
sites showing Verisign or Thawte testament symbols as confirmation of their security.
Vulnerabilities
Vulnerabilities is a situation where an attacker lessens the authentication system and logins to the
clients or administrator account (González Briones, Chamoso, & Barriuso, 2016). In this paper
we will discuss vulnerabilities that normally occurs in e-commerce check out.
(i) Administrative security vulnerabilities in E-commerce
Weak authentication. According to Gartner’s Magic Quadrant document validation
instruments that don't disallow different fizzled logins can be attacked utilizing
apparatuses(Oliveira, Alhinho, Rita, & Dhillon, 2017). So also, if the site utilizes header
transfer control protocol Basic Authentication or does not ignore session Secure Sockets
Layer, an aggressor can sniff the traffic to find client's confirmation or potentially
approval accreditations(Wang, Liu, Yan, & Jiang, 2016, November), (Thalassinos, &
Thalassinos, 2018).
Command execution. According to Verizon Data Breach Investigation report the most
annihilating web application vulnerabilities happen when the CGI content enables an
aggressor to execute working framework directions because of lacking info
approval(Crifasi, Pike, Stuedemann, Alnaeli, & Altahat, 2018, May), (Deepa, &
Thilagam, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
(ii) Physical security vulnerabilities in E-commerce
Buffer overflow. Buffer is an area of storing data in an application. The attacker sends
data to the server with specified instructions in the web application(González Briones,
Chamoso, & Barriuso, 2016). An example of a buffer overflow is where an attacker sends
instruction to destroy or expose all the data in the web application. (Johnson, 2016).
Cross-site scripting. This kind of attack normally occurs due to improper parsing of data
from the form to the database. According to the Open Web Application Security Project
attacker might hijack the submission of the form from the user and do whatever exploits
he wants. Most advanced programming languages frameworks use cross site forgery
request to detect the traffic from outside the web application. CSRF uses tokens which is
assigned to the user after visitting the website (Oliveira, Alhinho, Rita, & Dhillon, 2017).
(iii) Technical security vulnerabilities in E-commerce
SQL Injection. SQL injection is whereby the attacker tries to validate the input through
the use of command. The attacker makes the first part and the second part correct passing
it to the database(Oliveira, Alhinho, Rita, & Dhillon, 2017). The attacker inserts SQL
command in the part of the user input. The command will exceute the database after the
submission.
(ii) Physical security vulnerabilities in E-commerce
Buffer overflow. Buffer is an area of storing data in an application. The attacker sends
data to the server with specified instructions in the web application(González Briones,
Chamoso, & Barriuso, 2016). An example of a buffer overflow is where an attacker sends
instruction to destroy or expose all the data in the web application. (Johnson, 2016).
Cross-site scripting. This kind of attack normally occurs due to improper parsing of data
from the form to the database. According to the Open Web Application Security Project
attacker might hijack the submission of the form from the user and do whatever exploits
he wants. Most advanced programming languages frameworks use cross site forgery
request to detect the traffic from outside the web application. CSRF uses tokens which is
assigned to the user after visitting the website (Oliveira, Alhinho, Rita, & Dhillon, 2017).
(iii) Technical security vulnerabilities in E-commerce
SQL Injection. SQL injection is whereby the attacker tries to validate the input through
the use of command. The attacker makes the first part and the second part correct passing
it to the database(Oliveira, Alhinho, Rita, & Dhillon, 2017). The attacker inserts SQL
command in the part of the user input. The command will exceute the database after the
submission.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
Manipulation of prices. This is a weakness that is totally interesting to web based
shopping baskets and installment portals. In the most widely recognized event of this
defenselessness, the all out payable cost of the acquired products is put away in a
shrouded hyper text markup language field of a progressively created site
page(Chatterjee, 2015, June). An attacker can utilize a web app intermediary, for
instance, to just adjust the total that is payable, when this data streams from the user's
program to the web server(Oliveira, Alhinho, Rita, & Dhillon, 2017).
Front end validation. Most of the e-commerce online web applications use Javascript
validation. Attacker can disable Javascript in the web browser and bypass the validation
check. Developers should use both front and backend validation.
Recommendations and counter measures
The most significant point is to incorporate security with the web application at the structure
arrange itself. Indeed, one of the key exercises during the plan stage ought to be a point by point
hazard evaluation work out(Rafique, Humayun, Gul, Abbas, & Javed, 2015). Here, the group
must recognize the key data resources that the web application will manage. These could
incorporate setup data, client exchange subtleties, session IDs, Visa numbers, and so on. Firewall
is essential feature in a server where you hosting your application. It protects your application
from malware. It should be configured such that all the data coming to the application comes
through firewall before being stored in the database. Every one of these data resources should be
grouped regarding affect ability(Patil, & Patil, 2015). Contingent on the provisional engineering
picked, the designers alongside security specialists must investigate the dangers, effect,
vulnerabilities and risk probabilities for the framework(Sobihah, Mohamad, Ali, & Ismail, 2015).
Manipulation of prices. This is a weakness that is totally interesting to web based
shopping baskets and installment portals. In the most widely recognized event of this
defenselessness, the all out payable cost of the acquired products is put away in a
shrouded hyper text markup language field of a progressively created site
page(Chatterjee, 2015, June). An attacker can utilize a web app intermediary, for
instance, to just adjust the total that is payable, when this data streams from the user's
program to the web server(Oliveira, Alhinho, Rita, & Dhillon, 2017).
Front end validation. Most of the e-commerce online web applications use Javascript
validation. Attacker can disable Javascript in the web browser and bypass the validation
check. Developers should use both front and backend validation.
Recommendations and counter measures
The most significant point is to incorporate security with the web application at the structure
arrange itself. Indeed, one of the key exercises during the plan stage ought to be a point by point
hazard evaluation work out(Rafique, Humayun, Gul, Abbas, & Javed, 2015). Here, the group
must recognize the key data resources that the web application will manage. These could
incorporate setup data, client exchange subtleties, session IDs, Visa numbers, and so on. Firewall
is essential feature in a server where you hosting your application. It protects your application
from malware. It should be configured such that all the data coming to the application comes
through firewall before being stored in the database. Every one of these data resources should be
grouped regarding affect ability(Patil, & Patil, 2015). Contingent on the provisional engineering
picked, the designers alongside security specialists must investigate the dangers, effect,
vulnerabilities and risk probabilities for the framework(Sobihah, Mohamad, Ali, & Ismail, 2015).
6
When these dangers are drilled down, application countermeasures must be structured and if
fundamental the design itself might be adjusted. Countermeasures ought to likewise incorporate
exacting info approval schedules, a 3-level particular design, utilization of open-source
cryptographic models, and other secure coding rehearses(Wang, Zhang, & Wu, 2015,
December).
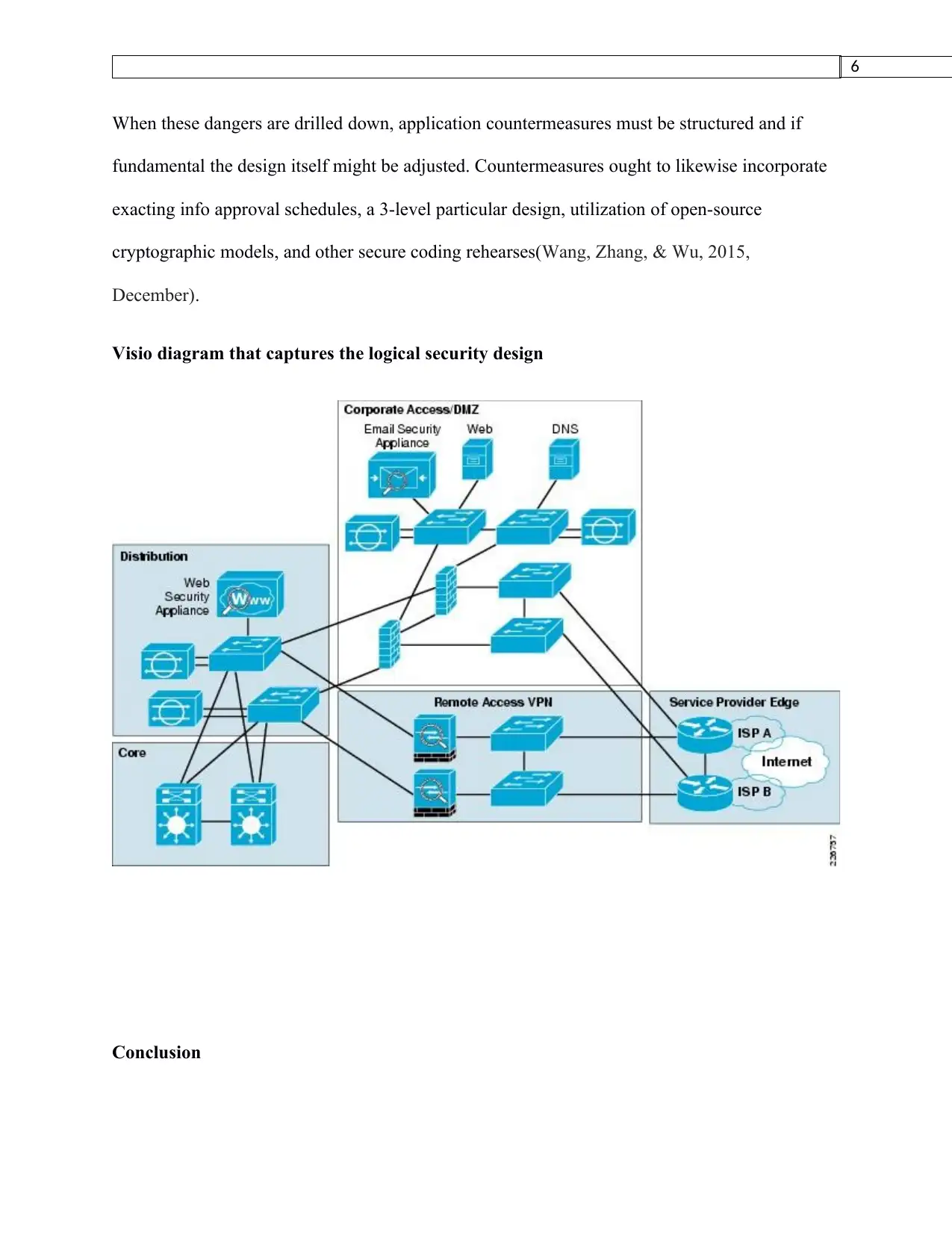
Visio diagram that captures the logical security design
Conclusion
When these dangers are drilled down, application countermeasures must be structured and if
fundamental the design itself might be adjusted. Countermeasures ought to likewise incorporate
exacting info approval schedules, a 3-level particular design, utilization of open-source
cryptographic models, and other secure coding rehearses(Wang, Zhang, & Wu, 2015,
December).
Visio diagram that captures the logical security design
Conclusion
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
It is necessary to start an online e-commerce application with prior knowledge of threats and
vulnerabilities in online transaction. Server’s operating system, programming language
framework used in bringing up the software will help solve the problem but at the same time
creates breaches in the software. Business should take proper security measures all the time.
Both the client and the owner should take their data private. We accept that there ought to be an
ensured security for the client side application and a mix of utilization of the two advances and
end customer care are the primary ground-breaking techniques for shield against web business
assaults. Advancements, for example, IDS(Intrusion discovery framework), and programming
dialects system will overhaul the weakness of the application since it has been tasted by
numerous and gets refreshed consistently. E-commerce is a way of buying and selling goods
goods and services in Intenet web application. Threats in Internet can come in any form, either
through the server, authentication, configuration or the client's side. Many factors promotes the
vulnerabilities in a web application. The reasons are not restrictive to these frameworks, however
their effect turns out to be a lot more prominent essentially in light of the wide introduction that
an online site has, and due to the money related nature of the exchanges. The vulnerabilities
talked about in this article are not really select to shopping baskets or online installment
frameworks. They could without much of a stretch be available in different kinds of web
applications too. Be that as it may, on account of web based business applications. Web
applications needs more measures since it affects many people transacting online.
It is necessary to start an online e-commerce application with prior knowledge of threats and
vulnerabilities in online transaction. Server’s operating system, programming language
framework used in bringing up the software will help solve the problem but at the same time
creates breaches in the software. Business should take proper security measures all the time.
Both the client and the owner should take their data private. We accept that there ought to be an
ensured security for the client side application and a mix of utilization of the two advances and
end customer care are the primary ground-breaking techniques for shield against web business
assaults. Advancements, for example, IDS(Intrusion discovery framework), and programming
dialects system will overhaul the weakness of the application since it has been tasted by
numerous and gets refreshed consistently. E-commerce is a way of buying and selling goods
goods and services in Intenet web application. Threats in Internet can come in any form, either
through the server, authentication, configuration or the client's side. Many factors promotes the
vulnerabilities in a web application. The reasons are not restrictive to these frameworks, however
their effect turns out to be a lot more prominent essentially in light of the wide introduction that
an online site has, and due to the money related nature of the exchanges. The vulnerabilities
talked about in this article are not really select to shopping baskets or online installment
frameworks. They could without much of a stretch be available in different kinds of web
applications too. Be that as it may, on account of web based business applications. Web
applications needs more measures since it affects many people transacting online.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Reference
Chatterjee, S. (2015, June). Security and privacy issues in E-Commerce: A proposed guidelines
to mitigate the risk. In 2015 IEEE International Advance Computing Conference (IACC)
(pp. 393-396). IEEE.
Crifasi, E., Pike, S., Stuedemann, Z., Alnaeli, S. M., & Altahat, Z. (2018, May). Cloud-Based
Source Code Security and Vulnerabilities Analysis Tool for C/C++ Software Systems.
In 2018 IEEE International Conference on Electro/Information Technology (EIT) (pp.
0651-0654). IEEE.
Deepa, G., & Thilagam, P. S. (2016). Securing web applications from injection and logic
vulnerabilities: Approaches and challenges. Information and Software Technology, 74,
160-180.
González Briones, A., Chamoso, P., & Barriuso, A. L. (2016). Review of the main security
problems with multi-agent systems used in e-commerce applications.
Johnson, A. (2016). Mobile e-Commerce Security: A Study of the End Users' Security
Reference
Chatterjee, S. (2015, June). Security and privacy issues in E-Commerce: A proposed guidelines
to mitigate the risk. In 2015 IEEE International Advance Computing Conference (IACC)
(pp. 393-396). IEEE.
Crifasi, E., Pike, S., Stuedemann, Z., Alnaeli, S. M., & Altahat, Z. (2018, May). Cloud-Based
Source Code Security and Vulnerabilities Analysis Tool for C/C++ Software Systems.
In 2018 IEEE International Conference on Electro/Information Technology (EIT) (pp.
0651-0654). IEEE.
Deepa, G., & Thilagam, P. S. (2016). Securing web applications from injection and logic
vulnerabilities: Approaches and challenges. Information and Software Technology, 74,
160-180.
González Briones, A., Chamoso, P., & Barriuso, A. L. (2016). Review of the main security
problems with multi-agent systems used in e-commerce applications.
Johnson, A. (2016). Mobile e-Commerce Security: A Study of the End Users' Security

9
Perceptions. In International Conference on Computer Science Education Innovation &
Technology (CSEIT). Proceedings (p. 129). Global Science and Technology Forum.
Oliveira, T., Alhinho, M., Rita, P., & Dhillon, G. (2017). Modelling and testing consumer trust
dimensions in e-commerce. Computers in Human Behavior, 71, 153-164.
Patil, D. K., & Patil, K. (2015). Client-side automated sanitizer for cross-site scripting
vulnerabilities. International Journal of Computer Applications, 121(20), 1-7.
Rafique, S., Humayun, M., Gul, Z., Abbas, A., & Javed, H. (2015). Systematic Review of Web
Application Security Vulnerabilities Detection Methods. Journal of Computer and
Communications, 3(09), 28.
Thalassinos, E. I., & Thalassinos, Y. (2018). Financial Crises and e-Commerce: How Are They
Related. Available at SSRN 3330169.
Sobihah, M., Mohamad, M., Ali, N. A. M., & Ismail, W. Z. W. (2015). E-commerce service
quality on customer satisfaction, belief and loyalty: a proposal. Mediterranean Journal of
Social Sciences, 6(2), 260.
Wang, M., Liu, G., Yan, C., & Jiang, C. (2016, November). Modeling and Vulnerable Points
Analysis for E-commerce Transaction System with a Known Attack. In International
Conference on Security, Privacy and Anonymity in Computation, Communication and
Perceptions. In International Conference on Computer Science Education Innovation &
Technology (CSEIT). Proceedings (p. 129). Global Science and Technology Forum.
Oliveira, T., Alhinho, M., Rita, P., & Dhillon, G. (2017). Modelling and testing consumer trust
dimensions in e-commerce. Computers in Human Behavior, 71, 153-164.
Patil, D. K., & Patil, K. (2015). Client-side automated sanitizer for cross-site scripting
vulnerabilities. International Journal of Computer Applications, 121(20), 1-7.
Rafique, S., Humayun, M., Gul, Z., Abbas, A., & Javed, H. (2015). Systematic Review of Web
Application Security Vulnerabilities Detection Methods. Journal of Computer and
Communications, 3(09), 28.
Thalassinos, E. I., & Thalassinos, Y. (2018). Financial Crises and e-Commerce: How Are They
Related. Available at SSRN 3330169.
Sobihah, M., Mohamad, M., Ali, N. A. M., & Ismail, W. Z. W. (2015). E-commerce service
quality on customer satisfaction, belief and loyalty: a proposal. Mediterranean Journal of
Social Sciences, 6(2), 260.
Wang, M., Liu, G., Yan, C., & Jiang, C. (2016, November). Modeling and Vulnerable Points
Analysis for E-commerce Transaction System with a Known Attack. In International
Conference on Security, Privacy and Anonymity in Computation, Communication and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
Storage (pp. 422-436). Springer, Cham.
Wang, X., Zhang, K., & Wu, Q. (2015, December). A Design of Security Assessment System for
E-Commerce Website. In 2015 8th International Symposium on Computational
Intelligence and Design (ISCID) (Vol. 1, pp. 137-140). IEEE.
Storage (pp. 422-436). Springer, Cham.
Wang, X., Zhang, K., & Wu, Q. (2015, December). A Design of Security Assessment System for
E-Commerce Website. In 2015 8th International Symposium on Computational
Intelligence and Design (ISCID) (Vol. 1, pp. 137-140). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




