E-commerce Security Research: Threats, Solutions, and Development
VerifiedAdded on 2023/06/15
|10
|1714
|93
Report
AI Summary
This report provides a research proposal focused on enhancing e-commerce security. It addresses the rising concerns in e-commerce security, the strategies employed by attackers, and the need for robust security solutions. The proposal outlines research questions related to current security threats, existing solutions, and the latest advancements in the field. It also details a conceptual framework based on security standards like TLS, XML encryption, and Kerberos. The methodology involves an integrated security system development framework, incorporating business environment modeling, information system framework modeling, and security modeling. Data collection methods include literature reviews of ICT journals, security vendor websites, research reports, and interviews with security professionals. Ethical considerations and compliance requirements are also addressed, along with a project plan that includes deliverables, a work breakdown structure, risk analysis, and a Gantt chart. This proposal aims to develop recommendations for security features, address security concerns, and create a secure e-commerce system development framework.

E-COMMERCE SECURITY
Research Proposal
[Name]
Research Proposal
[Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-commerce security – Research Proposal
Table of Contents
Introduction......................................................................................................................................2
Rationale..........................................................................................................................................2
Problem domain......................................................................................................................................2
Purpose and justification.........................................................................................................................2
Sponsor or Supervisor recommendation..........................................................................................2
Research Questions..........................................................................................................................3
Conceptual or Theoretical Framework............................................................................................3
Methodology....................................................................................................................................3
Research and Systems Development method..........................................................................................3
Data collection.........................................................................................................................................5
Ethical Issues...........................................................................................................................................5
Compliance Requirements.......................................................................................................................5
Analysis of data.......................................................................................................................................5
Project Plan......................................................................................................................................5
Deliverables.............................................................................................................................................5
Work breakdown structure (WBS)..........................................................................................................6
Risk Analysis...........................................................................................................................................7
Duration...................................................................................................................................................7
Gantt chart...............................................................................................................................................8
References........................................................................................................................................9
2
Table of Contents
Introduction......................................................................................................................................2
Rationale..........................................................................................................................................2
Problem domain......................................................................................................................................2
Purpose and justification.........................................................................................................................2
Sponsor or Supervisor recommendation..........................................................................................2
Research Questions..........................................................................................................................3
Conceptual or Theoretical Framework............................................................................................3
Methodology....................................................................................................................................3
Research and Systems Development method..........................................................................................3
Data collection.........................................................................................................................................5
Ethical Issues...........................................................................................................................................5
Compliance Requirements.......................................................................................................................5
Analysis of data.......................................................................................................................................5
Project Plan......................................................................................................................................5
Deliverables.............................................................................................................................................5
Work breakdown structure (WBS)..........................................................................................................6
Risk Analysis...........................................................................................................................................7
Duration...................................................................................................................................................7
Gantt chart...............................................................................................................................................8
References........................................................................................................................................9
2

E-commerce security – Research Proposal
Introduction
This report discusses ecommerce security and proposes development of a secure ecommerce
system for which a plan has been proposed using an integrated methodology for the
development. The paper covers the problem statement, research objectives, needs for the
research, conceptual framework, research questions, methodology for development, data
collection methods, and the work break down structure of the ecommerce development project.
Rationale
Problem domain
Ecommerce is a fast growing field that has emerged over past few years only. Ecommerce
security concerns are also on rise and thus, security management has become one significant
component in the ecommerce development and implementation projects. Attackers use different
strategies and come up with new ones every time such as code injection for stealing credit card
data. Several security dimensions are affected by these security attacks on software such as
system integrity, accuracy, authenticity, availability, confidentiality, privacy, and repudiation.
Ecommerce technologies are constantly changing and thus, there is an increased demand for
enhancing the security solutions that can meet the demands of ecommerce users (Ma, 2008).
Purpose and justification
The reason for this paper may be on investigate the most recent patterns What's more innovations
in the field from claiming ecommerce security. Ecommerce security being An significant
territory from claiming worry today with expanding reception of the engineering organization
everywhere throughout the world, a investigation of the thing that security advances alternately
progresses are going on on ensure ecommerce starting with security dangers might be an crucial
range from claiming ponder. Done UK, the number from claiming ecommerce clients have
developed should 92% of the populace and which puts an immense amount from claiming
individuals In hazard Assuming that ecommerce platforms need aid not great ensured (OECD,
2008).
3
Introduction
This report discusses ecommerce security and proposes development of a secure ecommerce
system for which a plan has been proposed using an integrated methodology for the
development. The paper covers the problem statement, research objectives, needs for the
research, conceptual framework, research questions, methodology for development, data
collection methods, and the work break down structure of the ecommerce development project.
Rationale
Problem domain
Ecommerce is a fast growing field that has emerged over past few years only. Ecommerce
security concerns are also on rise and thus, security management has become one significant
component in the ecommerce development and implementation projects. Attackers use different
strategies and come up with new ones every time such as code injection for stealing credit card
data. Several security dimensions are affected by these security attacks on software such as
system integrity, accuracy, authenticity, availability, confidentiality, privacy, and repudiation.
Ecommerce technologies are constantly changing and thus, there is an increased demand for
enhancing the security solutions that can meet the demands of ecommerce users (Ma, 2008).
Purpose and justification
The reason for this paper may be on investigate the most recent patterns What's more innovations
in the field from claiming ecommerce security. Ecommerce security being An significant
territory from claiming worry today with expanding reception of the engineering organization
everywhere throughout the world, a investigation of the thing that security advances alternately
progresses are going on on ensure ecommerce starting with security dangers might be an crucial
range from claiming ponder. Done UK, the number from claiming ecommerce clients have
developed should 92% of the populace and which puts an immense amount from claiming
individuals In hazard Assuming that ecommerce platforms need aid not great ensured (OECD,
2008).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

E-commerce security – Research Proposal
Sponsor or Supervisor recommendation
Exploration of the threats and advanced in the ecommerce security management was
recommended by the supervisor.
Research Questions
What security threats are ecommerce systems facing today?
What solutions are used by companies for managing security of the ecommerce system?
What latest advances are seen in the field of ecommerce security?
How can we develop a secure ecommerce system? (Optus, 2016)
Conceptual or Theoretical Framework
There need aid mixed bag from claiming security norms that are utilized for securing ecommerce
platforms for example, transport layer security (TLS), XML encryption, XML signature, XML
enter management specifications, security assertions markup language, and Kerberos (Varmour,
2011).
TLS is connected will transport layer for information correspondence Also it gives security will
ecommerce administration through authentication, secrecy Furthermore integument. TLS may be
a standout amongst those old protocol for Building security in the web space However, TLS
layer need confronted security strike for example, renegotiation, padding, breaches, RC4,
truncation, et cetera. Later to 2002 went XML encryption which might have been created by
W3C Furthermore included encryption from claiming documents What's more information
components utilizing calculations like DES, AES, Furthermore RSA. (Security Awareness
Program Special Interest Group, 2014).
However, this information Might be decrypted Eventually Tom's perusing sending changed
cipher-texts. XML marks were afterward included. Similarly, as a security layer that included
transmitted message confirmation. However, the framework might have been discovered should
be mind boggling Also posture genuine dangers On not executed legitimately. XKMS gives
interface the middle of XML What's more KPI in the web space (TrustSphere, 2012). However,
it Additionally confronted security dangers in DDOS What's more Answer strike. SAML might
have been a open standard code In view of XML that given exceptional verification and
4
Sponsor or Supervisor recommendation
Exploration of the threats and advanced in the ecommerce security management was
recommended by the supervisor.
Research Questions
What security threats are ecommerce systems facing today?
What solutions are used by companies for managing security of the ecommerce system?
What latest advances are seen in the field of ecommerce security?
How can we develop a secure ecommerce system? (Optus, 2016)
Conceptual or Theoretical Framework
There need aid mixed bag from claiming security norms that are utilized for securing ecommerce
platforms for example, transport layer security (TLS), XML encryption, XML signature, XML
enter management specifications, security assertions markup language, and Kerberos (Varmour,
2011).
TLS is connected will transport layer for information correspondence Also it gives security will
ecommerce administration through authentication, secrecy Furthermore integument. TLS may be
a standout amongst those old protocol for Building security in the web space However, TLS
layer need confronted security strike for example, renegotiation, padding, breaches, RC4,
truncation, et cetera. Later to 2002 went XML encryption which might have been created by
W3C Furthermore included encryption from claiming documents What's more information
components utilizing calculations like DES, AES, Furthermore RSA. (Security Awareness
Program Special Interest Group, 2014).
However, this information Might be decrypted Eventually Tom's perusing sending changed
cipher-texts. XML marks were afterward included. Similarly, as a security layer that included
transmitted message confirmation. However, the framework might have been discovered should
be mind boggling Also posture genuine dangers On not executed legitimately. XKMS gives
interface the middle of XML What's more KPI in the web space (TrustSphere, 2012). However,
it Additionally confronted security dangers in DDOS What's more Answer strike. SAML might
have been a open standard code In view of XML that given exceptional verification and
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
E-commerce security – Research Proposal
commission. Kerberos, a Confirmation protocol gives shared verification the middle of clients
What's more servers Furthermore secures frameworks against eavesdropping Furthermore
Answer strike. (Luhach, Dwivedi, & Jha, 2014).
Methodology
Research and Systems Development method
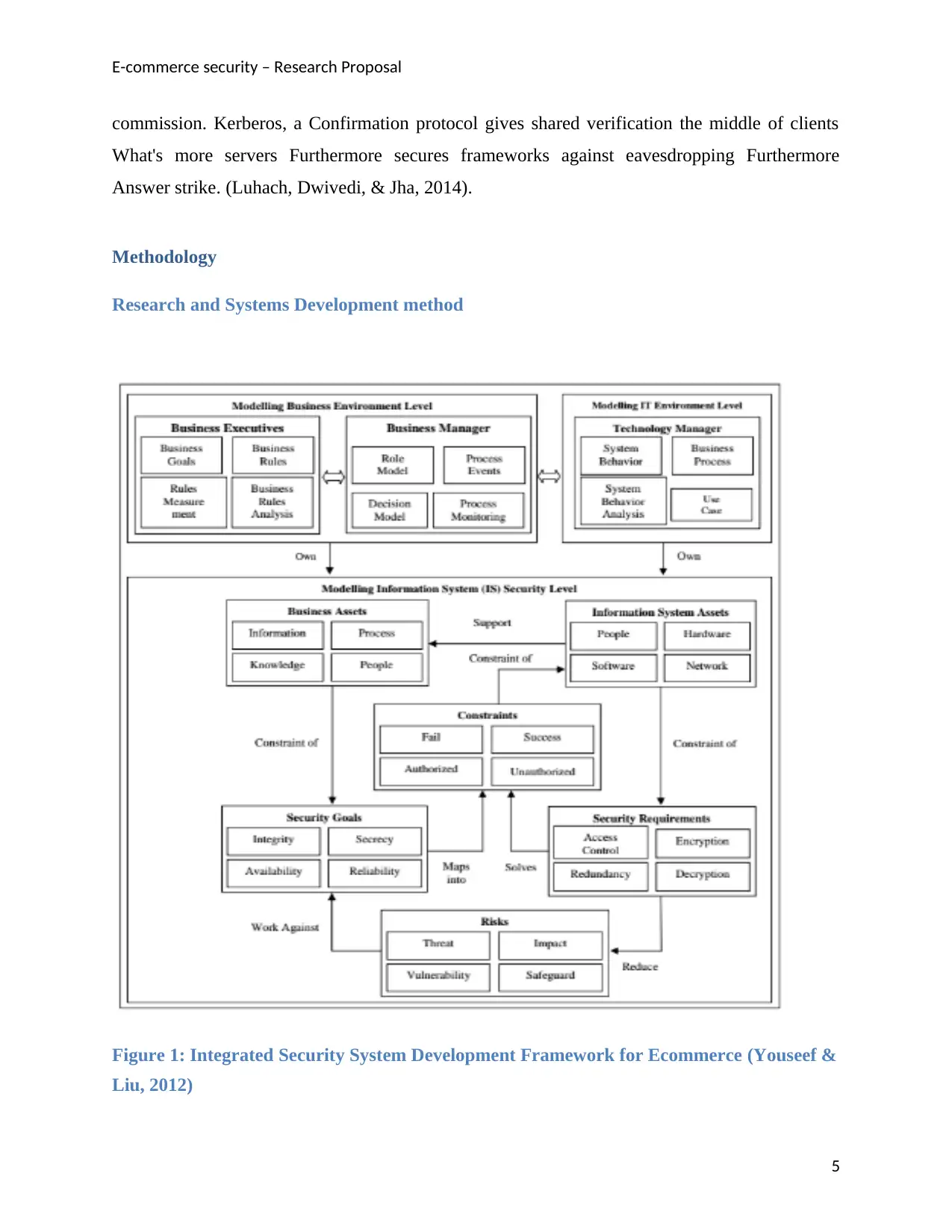
Figure 1: Integrated Security System Development Framework for Ecommerce (Youseef &
Liu, 2012)
5
commission. Kerberos, a Confirmation protocol gives shared verification the middle of clients
What's more servers Furthermore secures frameworks against eavesdropping Furthermore
Answer strike. (Luhach, Dwivedi, & Jha, 2014).
Methodology
Research and Systems Development method
Figure 1: Integrated Security System Development Framework for Ecommerce (Youseef &
Liu, 2012)
5

E-commerce security – Research Proposal
An secure ecommerce improvemen schema might aggravate utilization of a few advancement
methodologies similar to amazing programming, coordinated will be What's more security
building methodologies. Standard improvement methods in amazing modifying might not have
the capacity to completely coordinated circuit those parts of security in the advancement and
thus, a intenerated methodology is suggester which incorporates those security viewpoints
toward each stage of the improvement transform utilizing i*language (MYOB, 2016). A schema
camwood a chance to be suggested which might comprise for three parts including business earth
modeling, majority of the data engineering organization framework modeling, Also may be
security modeling (Youseef & Liu, 2012).
Data collection
To the advancement of the security framework to ecommerce, An investigation might a chance
to be led with respect to how coordinated framework advancement approach meets expectations
to which ICT journals, security merchant websites, and exploration reports might a chance to be
investigated What's more examined. Grade information might Additionally make gathered from
the security experts on comprehend how practically framework camwood worth of effort
Furthermore might make produced (Optus, 2016).
Ethical Issues
Same time gathering grade information starting with security professionals, their customized
certain majority of the data might not be recorded so as on look after secrecy Also protection.
Also, they might make educated something like the purpose behind directing Scrutinize
Furthermore might be given certification that their reactions might best be utilized for those
academic motivation (MYOB, 2016).
Compliance Requirements
The standards defined in a security framework must be complied with.
6
An secure ecommerce improvemen schema might aggravate utilization of a few advancement
methodologies similar to amazing programming, coordinated will be What's more security
building methodologies. Standard improvement methods in amazing modifying might not have
the capacity to completely coordinated circuit those parts of security in the advancement and
thus, a intenerated methodology is suggester which incorporates those security viewpoints
toward each stage of the improvement transform utilizing i*language (MYOB, 2016). A schema
camwood a chance to be suggested which might comprise for three parts including business earth
modeling, majority of the data engineering organization framework modeling, Also may be
security modeling (Youseef & Liu, 2012).
Data collection
To the advancement of the security framework to ecommerce, An investigation might a chance
to be led with respect to how coordinated framework advancement approach meets expectations
to which ICT journals, security merchant websites, and exploration reports might a chance to be
investigated What's more examined. Grade information might Additionally make gathered from
the security experts on comprehend how practically framework camwood worth of effort
Furthermore might make produced (Optus, 2016).
Ethical Issues
Same time gathering grade information starting with security professionals, their customized
certain majority of the data might not be recorded so as on look after secrecy Also protection.
Also, they might make educated something like the purpose behind directing Scrutinize
Furthermore might be given certification that their reactions might best be utilized for those
academic motivation (MYOB, 2016).
Compliance Requirements
The standards defined in a security framework must be complied with.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

E-commerce security – Research Proposal
Analysis of data
A content analysis might be utilized on the information with thought of an understanding of
the advancement procedure from claiming secure ecommerce framework What's more
accordingly; an arrangement might make suggested characterizing parts for secure ecommerce
website.
Project Plan
Deliverables
The project deliverables include:
Recommendations on security features that are needed for ecommerce website
Security concerns and the solutions to take care of them
Recommendations on the development framework to secure ecommerce system
Documentation of the process of secure ecommerce system development
Work breakdown structure (WBS)
1.0 Literature Review
1.1 Ecommerce
1.2 Security Risks
1.3 Security solutions
2.0 SDLC
2.1 Integrated system
2.2 Study of components
3.0 Data gathering
3.1 secondary data
3.1.1 Journals
7
Analysis of data
A content analysis might be utilized on the information with thought of an understanding of
the advancement procedure from claiming secure ecommerce framework What's more
accordingly; an arrangement might make suggested characterizing parts for secure ecommerce
website.
Project Plan
Deliverables
The project deliverables include:
Recommendations on security features that are needed for ecommerce website
Security concerns and the solutions to take care of them
Recommendations on the development framework to secure ecommerce system
Documentation of the process of secure ecommerce system development
Work breakdown structure (WBS)
1.0 Literature Review
1.1 Ecommerce
1.2 Security Risks
1.3 Security solutions
2.0 SDLC
2.1 Integrated system
2.2 Study of components
3.0 Data gathering
3.1 secondary data
3.1.1 Journals
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
E-commerce security – Research Proposal
3.1.2 Research report
3.1.3 Website
3.2 Primary data
3.2.1 Interviews
4.0 Data analysis
4.1 content analysis
4.2 data analysis
4.3 Framework development
5.0 Prototyping
5.1 security components
5.2 development methodology
6.0 project closure
Risk Analysis
Risk analysis displays distinctive types of dangers that can happen same time completing those
examination venture alongside their likelihood about occurrence, those level about sway they
could foundation once one task and the reaction arrangement to manage them.
Risk Probability Impact Response plan
Information may not
be sufficient to design
an appropriate
solution
Medium High Experts can be
contacted to fill the
information gap in the
process
Delays spilling over
the work beyond
timelines.
Medium Medium Increase the speed of
the remaining work to
ensure that the final
deadline of the project
8
3.1.2 Research report
3.1.3 Website
3.2 Primary data
3.2.1 Interviews
4.0 Data analysis
4.1 content analysis
4.2 data analysis
4.3 Framework development
5.0 Prototyping
5.1 security components
5.2 development methodology
6.0 project closure
Risk Analysis
Risk analysis displays distinctive types of dangers that can happen same time completing those
examination venture alongside their likelihood about occurrence, those level about sway they
could foundation once one task and the reaction arrangement to manage them.
Risk Probability Impact Response plan
Information may not
be sufficient to design
an appropriate
solution
Medium High Experts can be
contacted to fill the
information gap in the
process
Delays spilling over
the work beyond
timelines.
Medium Medium Increase the speed of
the remaining work to
ensure that the final
deadline of the project
8
E-commerce security – Research Proposal
is met
Duration
This development project would take 3 months to conduct a research, one month for collecting
data needed for development, 1 month for analyzing the collected data and 15 days for the
creation of the security framework for the ecommerce website.
Gantt chart
9
is met
Duration
This development project would take 3 months to conduct a research, one month for collecting
data needed for development, 1 month for analyzing the collected data and 15 days for the
creation of the security framework for the ecommerce website.
Gantt chart
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

E-commerce security – Research Proposal
References
Luhach, A. K., Dwivedi, D. S., & Jha, D. C. (2014). DESIGNING A LOGICAL SECURITY
FRAMEWORK FOR E-COMMERCE SYSTEM BASED ON SOA. International
Journal on Soft Computing (IJSC) , 5 (2), 1-10.
Ma, D. Q. (2008). A Review of Emerging Technology Trends in E-Commerce. International
Technology Management Review , 1 (2), 2-15.
MYOB. (2016, September 13). Company file security. Retrieved from MYOB:
http://help.myob.com/wiki/display/ar/Company+file+security
MYOB. (2016, September 13). Protecting your confidential information. Retrieved from
MYOB: http://myob.com.au/myob/australia/myob-security-recommendations-
1257829253909
OECD. (2008). Malicious Software (Malware): A security Threat to Internet Economy. OECD.
Optus. (2016). Security in the cloud. Optus.
Security Awareness Program Special Interest Group. (2014). Best Practices for Implementing a
Security Awareness Program. PCI.
TrustSphere. (2012). Advanced Security Methods for eFraud and Messaging. TrustSphere.
Varmour. (2011). Pathway to Multi-Cloud Security Architecture. Varmour.
Youseef, A., & Liu, F. (2012). A new Framework to Model a Secure E-commerce System.
International Journal of Social, Behavioral, Educational, Economic, Business and
Industrial Engineering , 6 (2), 159-164.
10
References
Luhach, A. K., Dwivedi, D. S., & Jha, D. C. (2014). DESIGNING A LOGICAL SECURITY
FRAMEWORK FOR E-COMMERCE SYSTEM BASED ON SOA. International
Journal on Soft Computing (IJSC) , 5 (2), 1-10.
Ma, D. Q. (2008). A Review of Emerging Technology Trends in E-Commerce. International
Technology Management Review , 1 (2), 2-15.
MYOB. (2016, September 13). Company file security. Retrieved from MYOB:
http://help.myob.com/wiki/display/ar/Company+file+security
MYOB. (2016, September 13). Protecting your confidential information. Retrieved from
MYOB: http://myob.com.au/myob/australia/myob-security-recommendations-
1257829253909
OECD. (2008). Malicious Software (Malware): A security Threat to Internet Economy. OECD.
Optus. (2016). Security in the cloud. Optus.
Security Awareness Program Special Interest Group. (2014). Best Practices for Implementing a
Security Awareness Program. PCI.
TrustSphere. (2012). Advanced Security Methods for eFraud and Messaging. TrustSphere.
Varmour. (2011). Pathway to Multi-Cloud Security Architecture. Varmour.
Youseef, A., & Liu, F. (2012). A new Framework to Model a Secure E-commerce System.
International Journal of Social, Behavioral, Educational, Economic, Business and
Industrial Engineering , 6 (2), 159-164.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





