Analyzing Consumer Trust, Data Privacy on E-Commerce Businesses
VerifiedAdded on 2023/06/11
|15
|4634
|216
Report
AI Summary
This report investigates the crucial role of consumer trust and data privacy in the performance of e-commerce businesses in Australia. It addresses the increasing importance of online trust in the digital marketplace, highlighting consumer concerns about data privacy and the potential negative impacts of privacy breaches on business performance. The study aims to identify factors that establish consumer trust, explore influences on consumers' willingness to share personal information online, and analyze the effects of data privacy concerns on e-commerce businesses. It references prior research to emphasize the collection and use of consumer data, the personalization-privacy paradox, and the significance of trust-building elements, such as merchant legitimacy, technology, order fulfillment, customer control, tone, and consumer collaboration. The research also points to the importance of reliable security measures, brand reputation, and hassle-free transactions in fostering consumer trust. Ultimately, the study seeks to provide insights that can help online vendors understand and address consumer concerns, thereby improving business performance in the Australian e-commerce landscape. Desklib provides a variety of solved assignments and study resources for students.

Analyzing the Impact of Consumer
Trust and Data Privacy on the
Performance of E-Commerce
Businesses in Australia
Trust and Data Privacy on the
Performance of E-Commerce
Businesses in Australia
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Research Title........................................................................................................................................2
Introduction...........................................................................................................................................2
Detail Statement of the Problem............................................................................................................3
Research Aim and Objectives................................................................................................................4
Research Questions...............................................................................................................................4
Justification and Potential Output of the Research project....................................................................4
Why is the chosen project important both theoretically and practically?...........................................4
What are potential outputs and outcomes of the research?....................................................................5
Conceptual Framework..........................................................................................................................6
Methodology and Presenting Secondary Data.......................................................................................8
Secondary Data..................................................................................................................................8
Primary Data......................................................................................................................................9
Sampling Technique and Sample Size...............................................................................................9
Organization of the Study, project Budget and Schedule...................................................................9
Budget for Conducting the Study....................................................................................................10
Gantt Chart......................................................................................................................................11
References...........................................................................................................................................12
1 | P a g e
Research Title........................................................................................................................................2
Introduction...........................................................................................................................................2
Detail Statement of the Problem............................................................................................................3
Research Aim and Objectives................................................................................................................4
Research Questions...............................................................................................................................4
Justification and Potential Output of the Research project....................................................................4
Why is the chosen project important both theoretically and practically?...........................................4
What are potential outputs and outcomes of the research?....................................................................5
Conceptual Framework..........................................................................................................................6
Methodology and Presenting Secondary Data.......................................................................................8
Secondary Data..................................................................................................................................8
Primary Data......................................................................................................................................9
Sampling Technique and Sample Size...............................................................................................9
Organization of the Study, project Budget and Schedule...................................................................9
Budget for Conducting the Study....................................................................................................10
Gantt Chart......................................................................................................................................11
References...........................................................................................................................................12
1 | P a g e

Research Title
There are several factors that tend to make a significant impact on the consumers’ trust
towards the businesses. Thus on the basis of the above aspects, the research title has been
designed as follows:
Analyzing the Impact of Consumer Trust and Data Privacy on the performance of E-
Commerce Businesses in Australia
Introduction
With rapid advancements and innovations in technology like internet, the contemporary
business environment has undergone significant changes. Internet has led to the development
of a global marketplace with huge business opportunities. In this context, Doig, (2016)
advocated that internet has not only proved to be beneficial for the businesses, rather internet
has also enabled consumers with more power to control several aspects of their lives that
include knowledge, time, decision, communications, satisfaction and their expenditure.
However, in the present era of internet and e-commerce, trust and privacy has emerged as an
important aspect. It has been opined by Tsai et al., (2011) that one of the most important
reason that consumers at present refrain themselves often from making their purchases from
internet vendors is the lack of trust and concern about their data privacy. So, it can be said
that there exist a need for promoting trust and confidence among the consumers to encourage
them to make their purchases online. The consumers prefer their personal information and
identity to be confidential because of the fear of getting exposed to online fraud. Moreover,
the potential risk in context to e-commerce is high because of the lack of physical interaction,
anonymity and distance. Trust has been advocated by Li et al., (2011) as an important tool for
a successful transaction in both the online and offline environment and a single incident of
breach of data privacy on the part of the internet vendors can affect the level of trust of the
consumers towards the vendor and can have a significant negative impact on their business.
Thus, drawing inferences from the above aspects and the challenges that internet vendors face
in enhancing the level of trust on the part of the consumers, the researcher in the present
study would emphasize on analyzing the impact of consumer trust and data privacy on the
performance of e-commerce businesses in Australia.
2 | P a g e
There are several factors that tend to make a significant impact on the consumers’ trust
towards the businesses. Thus on the basis of the above aspects, the research title has been
designed as follows:
Analyzing the Impact of Consumer Trust and Data Privacy on the performance of E-
Commerce Businesses in Australia
Introduction
With rapid advancements and innovations in technology like internet, the contemporary
business environment has undergone significant changes. Internet has led to the development
of a global marketplace with huge business opportunities. In this context, Doig, (2016)
advocated that internet has not only proved to be beneficial for the businesses, rather internet
has also enabled consumers with more power to control several aspects of their lives that
include knowledge, time, decision, communications, satisfaction and their expenditure.
However, in the present era of internet and e-commerce, trust and privacy has emerged as an
important aspect. It has been opined by Tsai et al., (2011) that one of the most important
reason that consumers at present refrain themselves often from making their purchases from
internet vendors is the lack of trust and concern about their data privacy. So, it can be said
that there exist a need for promoting trust and confidence among the consumers to encourage
them to make their purchases online. The consumers prefer their personal information and
identity to be confidential because of the fear of getting exposed to online fraud. Moreover,
the potential risk in context to e-commerce is high because of the lack of physical interaction,
anonymity and distance. Trust has been advocated by Li et al., (2011) as an important tool for
a successful transaction in both the online and offline environment and a single incident of
breach of data privacy on the part of the internet vendors can affect the level of trust of the
consumers towards the vendor and can have a significant negative impact on their business.
Thus, drawing inferences from the above aspects and the challenges that internet vendors face
in enhancing the level of trust on the part of the consumers, the researcher in the present
study would emphasize on analyzing the impact of consumer trust and data privacy on the
performance of e-commerce businesses in Australia.
2 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Detail Statement of the Problem
While comparing the traditional business environment with the online business environment,
it is observed that that physical cues like the appearance of the store and direct contact of the
consumers with the sales person in case of traditional shopping environment is absent in the
online shopping environment (Youn, 2009). However, with rapid globalization and
advancements in technology, more and more business organizations are swinging towards
internet to interact directly with the customers and provide them better services. So, this
result in getting more customers conducted in a network generating huge volume of customer
data. These data prove to be useful from the business organizations for extracting useful
knowledge about the customers and predicting the buying behavior of the consumers. These
data are used not only to serve the above mentioned purpose of analyzing the consumer
purchase behavior; rather they are also sold to third parties (Lee et al., 2011). So, this raises
the concern of data privacy and misuse of the customers’ private data and personal
information. Online vendors are also involved in creating consumers’ profiles of their online
activities like the websites that are most frequently visited by the customers, their browsing
habits to efficiently leverage their past behavior for predicting and influencing their future
behavior. This type of personalization tends to depend on two factors as has been proposed
by Taylor et al., (2009). The factors include the ability of the marketer to acquire and process
the information of the consumers and the willingness on the part of the consumers to share
their information and make use of the personalization services. Thus, it can be said that the
personalization and privacy can be in conflict that can be referred to as personalization-
privacy paradox. So, it has been proposed by Urban et al., (2009) that the above aspect leads
to major challenge for the e-commerce businesses since breach of data privacy and misuse of
the personal information and details of the consumers can lead to adverse impact on the
business and also on their performance.
So, it becomes important to analyze the factors that can lead to enhanced relationship of trust
between the consumers and e-commerce businesses. Thus, the researcher in the present study
would aim at analyzing the factors that can enhance the trust of the consumers towards online
vendors and how concerns related to data privacy can affect the performance of the e-
commerce businesses in Australia.
3 | P a g e
While comparing the traditional business environment with the online business environment,
it is observed that that physical cues like the appearance of the store and direct contact of the
consumers with the sales person in case of traditional shopping environment is absent in the
online shopping environment (Youn, 2009). However, with rapid globalization and
advancements in technology, more and more business organizations are swinging towards
internet to interact directly with the customers and provide them better services. So, this
result in getting more customers conducted in a network generating huge volume of customer
data. These data prove to be useful from the business organizations for extracting useful
knowledge about the customers and predicting the buying behavior of the consumers. These
data are used not only to serve the above mentioned purpose of analyzing the consumer
purchase behavior; rather they are also sold to third parties (Lee et al., 2011). So, this raises
the concern of data privacy and misuse of the customers’ private data and personal
information. Online vendors are also involved in creating consumers’ profiles of their online
activities like the websites that are most frequently visited by the customers, their browsing
habits to efficiently leverage their past behavior for predicting and influencing their future
behavior. This type of personalization tends to depend on two factors as has been proposed
by Taylor et al., (2009). The factors include the ability of the marketer to acquire and process
the information of the consumers and the willingness on the part of the consumers to share
their information and make use of the personalization services. Thus, it can be said that the
personalization and privacy can be in conflict that can be referred to as personalization-
privacy paradox. So, it has been proposed by Urban et al., (2009) that the above aspect leads
to major challenge for the e-commerce businesses since breach of data privacy and misuse of
the personal information and details of the consumers can lead to adverse impact on the
business and also on their performance.
So, it becomes important to analyze the factors that can lead to enhanced relationship of trust
between the consumers and e-commerce businesses. Thus, the researcher in the present study
would aim at analyzing the factors that can enhance the trust of the consumers towards online
vendors and how concerns related to data privacy can affect the performance of the e-
commerce businesses in Australia.
3 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research Aim and Objectives
The researcher would aim at gaining an enhanced understanding of the consumers’ trust in e-
commerce businesses in Australia together and analyzing the impact of consumers’ concerns
towards data privacy on the performance of e-commerce businesses in Australia. Thus, the
research study would strive to achieve the following objectives:
To identify the factors that helps in establishing consumers’ trust in e-commerce
businesses in Australia.
To investigate the factors that influences the willingness of the consumers to share
their personal information online.
To analyze the impact of data privacy concerns of customers on the performance of e-
commerce businesses in Australia.
Research Questions
What are the factors that help in establishing consumers’ trust in e-commerce
businesses in Australia?
What are the factors that influence the willingness of the consumers to share their
personal information online?
What is the impact of data privacy concerns of customers on the performance of e-
commerce businesses in Australia?
Justification and Potential Output of the Research project
Why is the chosen project important both theoretically and practically?
According to the study conducted by Kim et al., (2009), it is observed that the increasing use
of internet has facilitated the business organizations with more ways of collecting the
customers’ data and the potential customers. The concern in collecting consumers’ data is the
fact that most of the consumers’ data are collected without the consumer even realizing the
fact by making use of the unobtrusive data collection methods. According to Wu et al.,
(2012), an individual when visits the website of a company unwittingly provides the company
with information like his or her IP address, the page that has referred the individual to
website of the company and the page individual is viewing. On the other hand the company
websites also make of cookies and other tracking devices to collect more relevant customers’
data. These practices in the contemporary business environment have gained popularity since
4 | P a g e
The researcher would aim at gaining an enhanced understanding of the consumers’ trust in e-
commerce businesses in Australia together and analyzing the impact of consumers’ concerns
towards data privacy on the performance of e-commerce businesses in Australia. Thus, the
research study would strive to achieve the following objectives:
To identify the factors that helps in establishing consumers’ trust in e-commerce
businesses in Australia.
To investigate the factors that influences the willingness of the consumers to share
their personal information online.
To analyze the impact of data privacy concerns of customers on the performance of e-
commerce businesses in Australia.
Research Questions
What are the factors that help in establishing consumers’ trust in e-commerce
businesses in Australia?
What are the factors that influence the willingness of the consumers to share their
personal information online?
What is the impact of data privacy concerns of customers on the performance of e-
commerce businesses in Australia?
Justification and Potential Output of the Research project
Why is the chosen project important both theoretically and practically?
According to the study conducted by Kim et al., (2009), it is observed that the increasing use
of internet has facilitated the business organizations with more ways of collecting the
customers’ data and the potential customers. The concern in collecting consumers’ data is the
fact that most of the consumers’ data are collected without the consumer even realizing the
fact by making use of the unobtrusive data collection methods. According to Wu et al.,
(2012), an individual when visits the website of a company unwittingly provides the company
with information like his or her IP address, the page that has referred the individual to
website of the company and the page individual is viewing. On the other hand the company
websites also make of cookies and other tracking devices to collect more relevant customers’
data. These practices in the contemporary business environment have gained popularity since
4 | P a g e

it proves to be beneficial in enhancing the marketing efforts of the business. The customers’
data are used by the marketers to facilitate the customers with a more personalized browsing
experience (Belanger & Crossler, 2011). However, with increase in such activities, the
concern is about the privacy issues and what customers are giving up for reaping the benefits
of personalization. So, it becomes important for the online vendors to understand the fact that
issues of data privacy can affect their business performance.
In Addition to the above theoretical aspects, the researcher has also observed the survey
conducted by the Centre for Internet Safety at the University of Canberra in partnership with
eBay.com.au to analyze the attitude of the eBay users towards the privacy and how it
influences and affects their online actions (Canberra, 2012). The survey has revealed the fact
that privacy is an important determinant for the consumers to perform online activities
especially in context to their decision of buying and selling goods and services online. The
survey also led to the findings that the consumers are concerned most about the privacy of
their financial data and identity theft. According to the survey, 85% of the Australians are of
the opinion that data breach notification should be made mandatory for the businesses
(Canberra, 2012). Moreover, across the globe, it has been observed that there were 2.6
million data records those have been stolen or lost or exposed i.e. there have been a surge of
88% in 2018 in comparison to 2017 (Cso, 2018). So, these aspects clearly evidence the
emerging issue of data privacy for the consumers making their transactions online. So, on the
basis of the above aspects, it can be said that it important to conduct study on the emerging
issue to bring the facts into the notice of individual consumers and companies so that
necessary steps can be taken. Moreover, the study would also be beneficial in making the
online vendors aware of the factors that influence consumers’ trust and how the data privacy
concerns and issues related to consumer personal identity theft can affect their business
performance.
What are potential outputs and outcomes of the research?
The potential outcome of the research would lead to the fact that consumers’ trust plays a
major role in encouraging the consumers to get involved in buying and selling products from
the particular online vendors. On the other hand, it is expected that the study would lead to
the findings that the concerns on the part of the customers regarding data privacy and
personal identity theft can have a negative impact on the performance of the business.
5 | P a g e
data are used by the marketers to facilitate the customers with a more personalized browsing
experience (Belanger & Crossler, 2011). However, with increase in such activities, the
concern is about the privacy issues and what customers are giving up for reaping the benefits
of personalization. So, it becomes important for the online vendors to understand the fact that
issues of data privacy can affect their business performance.
In Addition to the above theoretical aspects, the researcher has also observed the survey
conducted by the Centre for Internet Safety at the University of Canberra in partnership with
eBay.com.au to analyze the attitude of the eBay users towards the privacy and how it
influences and affects their online actions (Canberra, 2012). The survey has revealed the fact
that privacy is an important determinant for the consumers to perform online activities
especially in context to their decision of buying and selling goods and services online. The
survey also led to the findings that the consumers are concerned most about the privacy of
their financial data and identity theft. According to the survey, 85% of the Australians are of
the opinion that data breach notification should be made mandatory for the businesses
(Canberra, 2012). Moreover, across the globe, it has been observed that there were 2.6
million data records those have been stolen or lost or exposed i.e. there have been a surge of
88% in 2018 in comparison to 2017 (Cso, 2018). So, these aspects clearly evidence the
emerging issue of data privacy for the consumers making their transactions online. So, on the
basis of the above aspects, it can be said that it important to conduct study on the emerging
issue to bring the facts into the notice of individual consumers and companies so that
necessary steps can be taken. Moreover, the study would also be beneficial in making the
online vendors aware of the factors that influence consumers’ trust and how the data privacy
concerns and issues related to consumer personal identity theft can affect their business
performance.
What are potential outputs and outcomes of the research?
The potential outcome of the research would lead to the fact that consumers’ trust plays a
major role in encouraging the consumers to get involved in buying and selling products from
the particular online vendors. On the other hand, it is expected that the study would lead to
the findings that the concerns on the part of the customers regarding data privacy and
personal identity theft can have a negative impact on the performance of the business.
5 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Conceptual Framework
According to the study conducted Cases et al., (2010), developing the trust that leads to
enhanced level of satisfaction on the part of the customers is an important and complex task.
Palvia, (2009) in his study has identified six elements those when combined can lead to the
development of a trust pyramid. The trust pyramid can be illustrated with the help of the
following figure:
[Source: Palvia, 2009]
From the above figure, it is observed that the core elements that are important for the
business organizations to maintain their position in the market and secure their position
include the merchant legitimacy, the technology and the robust order fulfilment. These
elements form the base of the pyramid. Above the base elements, there also exist some subtle
elements that can be referred to as trust builders that can be used by the businesses for
differentiating itself from the competitors (Palvia, 2009). These elements include the
customers’ control, the tone, and consumer collaboration. Thus, the six elements collectively
develop the confidence and the comfort that are needed for enhancing the satisfaction on the
part of the customers and enhancing the base of loyal customers.
On the basis of the above figure, it is important for the business organizations to adopt the
most reliable security measures on their website and it should be efficiently communicated to
the consumers in a language they understand. Moreover, it has been proposed by Kshetri,
6 | P a g e
According to the study conducted Cases et al., (2010), developing the trust that leads to
enhanced level of satisfaction on the part of the customers is an important and complex task.
Palvia, (2009) in his study has identified six elements those when combined can lead to the
development of a trust pyramid. The trust pyramid can be illustrated with the help of the
following figure:
[Source: Palvia, 2009]
From the above figure, it is observed that the core elements that are important for the
business organizations to maintain their position in the market and secure their position
include the merchant legitimacy, the technology and the robust order fulfilment. These
elements form the base of the pyramid. Above the base elements, there also exist some subtle
elements that can be referred to as trust builders that can be used by the businesses for
differentiating itself from the competitors (Palvia, 2009). These elements include the
customers’ control, the tone, and consumer collaboration. Thus, the six elements collectively
develop the confidence and the comfort that are needed for enhancing the satisfaction on the
part of the customers and enhancing the base of loyal customers.
On the basis of the above figure, it is important for the business organizations to adopt the
most reliable security measures on their website and it should be efficiently communicated to
the consumers in a language they understand. Moreover, it has been proposed by Kshetri,
6 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(2014) that for online vendors, brand name plays an important role in enhancing the trust of
the consumers. This is because, brand name assist the consumers in making their choice when
they possess little information about the functionality and quality of the products. So, it can
be said that familiar names coupled with reputable performance records proves to be
beneficial in enhancing the consumers’ trust.
In context to trust development, Limbu et al., (2011) has opined that consumers prefer
placing orders and receiving the products without much hassle. Thus, if the costs are not
clearly defined and right information is not made available, it can have negative impact on
the consumers’ preference towards the brand. In addition to the above factors, it has been
advocated by Gerlach et al., (2015) that developing consumers’ trust is something more than
the technical features of a website. Consumers prefer to be assured of the fact that their
personal information and data and their personal identity is handled with much sensitivity.
So, is these privacy concerns are breached, the consumers do not prefer making purchases
from the brand that has negative impact on the performance of the business. So, it is
important that the businesses should post an easy to read privacy statement on their website
to inform the consumers about the ways in which their personal information are collected and
handled.
Mothersbaugh et al., (2012) argued that when consumers are aware of the fact that they have
a control on how business organizations can access their personal data and information, it
helps in building a sense of trust on the part of the consumers towards the brand. So, in this
context, the businesses can smartly seek permission from the customers to collect their
personal information and data to ensure and make the customers feel that they have full
control on their buying process as well on how their information and data is being collected.
This leads to a positive influence on the perception of the consumers towards the brand. This
motivates them to prefer making their purchases from that particular vendor which ultimately
enhances the performance of the business.
Collaboration has also been emphasized on by Leon et al., (2013) as an important element in
nurturing the trust among the consumers towards the brand. So, if consumers are allowed to
collect advice and suggestions from the former customers both in terms of the product quality
and in terms of their privacy concerns, it plays an important role in developing a sense of
trust among the consumers towards the brand. Thus, with enhanced trust consumers prefer
7 | P a g e
the consumers. This is because, brand name assist the consumers in making their choice when
they possess little information about the functionality and quality of the products. So, it can
be said that familiar names coupled with reputable performance records proves to be
beneficial in enhancing the consumers’ trust.
In context to trust development, Limbu et al., (2011) has opined that consumers prefer
placing orders and receiving the products without much hassle. Thus, if the costs are not
clearly defined and right information is not made available, it can have negative impact on
the consumers’ preference towards the brand. In addition to the above factors, it has been
advocated by Gerlach et al., (2015) that developing consumers’ trust is something more than
the technical features of a website. Consumers prefer to be assured of the fact that their
personal information and data and their personal identity is handled with much sensitivity.
So, is these privacy concerns are breached, the consumers do not prefer making purchases
from the brand that has negative impact on the performance of the business. So, it is
important that the businesses should post an easy to read privacy statement on their website
to inform the consumers about the ways in which their personal information are collected and
handled.
Mothersbaugh et al., (2012) argued that when consumers are aware of the fact that they have
a control on how business organizations can access their personal data and information, it
helps in building a sense of trust on the part of the consumers towards the brand. So, in this
context, the businesses can smartly seek permission from the customers to collect their
personal information and data to ensure and make the customers feel that they have full
control on their buying process as well on how their information and data is being collected.
This leads to a positive influence on the perception of the consumers towards the brand. This
motivates them to prefer making their purchases from that particular vendor which ultimately
enhances the performance of the business.
Collaboration has also been emphasized on by Leon et al., (2013) as an important element in
nurturing the trust among the consumers towards the brand. So, if consumers are allowed to
collect advice and suggestions from the former customers both in terms of the product quality
and in terms of their privacy concerns, it plays an important role in developing a sense of
trust among the consumers towards the brand. Thus, with enhanced trust consumers prefer
7 | P a g e

making their purchases from a particular brand and thus it enhances the performance of the
business.
Thus, from the above discussions, it can be inferred that the six elements that include the state
of the art security, merchant legitimacy, fulfilment, tone, customer control and consumer
collaboration leads to the development of a deep and trusting relationship between the brand
and the customers. The consumers and the brand can also follow a step by step process for
exchanging value which would ultimately lead to enhanced trust. So, every time a consumer
willingly shares some of their personal information with the brand, the brand should reward
the efforts of the consumers with richer experiences and some personalized services. So, this
mutually beneficial relationship can lead to enhanced trust and enhanced trust can lead to
enhanced performance of the business through repeat purchases and word of mouth
marketing.
Thus, the conceptual framework on the basis of the above aspects can be developed as
follows:
State of the art
security
Enhanced level of
trust of consumers
towards the brand,
More repeat
purchases and word
of mouth marketing
Enhanced business
performance
Merchant legitimacy
Fulfilment
Tone
Customer control
Consumer
collaboration
Methodology and Presenting Secondary Data
Secondary Data
The researcher would collect secondary data from various sources that would include the
articles, books and internet. The researcher would also search literature on the basis of the
research title and ensure that the articles and journals selected for collecting secondary data
are peer reviewed articles and journals and have been published in English Language and
have been published between the years 2009 to 2017. The researcher would also collect
8 | P a g e
business.
Thus, from the above discussions, it can be inferred that the six elements that include the state
of the art security, merchant legitimacy, fulfilment, tone, customer control and consumer
collaboration leads to the development of a deep and trusting relationship between the brand
and the customers. The consumers and the brand can also follow a step by step process for
exchanging value which would ultimately lead to enhanced trust. So, every time a consumer
willingly shares some of their personal information with the brand, the brand should reward
the efforts of the consumers with richer experiences and some personalized services. So, this
mutually beneficial relationship can lead to enhanced trust and enhanced trust can lead to
enhanced performance of the business through repeat purchases and word of mouth
marketing.
Thus, the conceptual framework on the basis of the above aspects can be developed as
follows:
State of the art
security
Enhanced level of
trust of consumers
towards the brand,
More repeat
purchases and word
of mouth marketing
Enhanced business
performance
Merchant legitimacy
Fulfilment
Tone
Customer control
Consumer
collaboration
Methodology and Presenting Secondary Data
Secondary Data
The researcher would collect secondary data from various sources that would include the
articles, books and internet. The researcher would also search literature on the basis of the
research title and ensure that the articles and journals selected for collecting secondary data
are peer reviewed articles and journals and have been published in English Language and
have been published between the years 2009 to 2017. The researcher would also collect
8 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

secondary data from reliable websites and also from the research papers available in the
library and from the lectures and notes and study materials provided by the mentors (Hair and
Money, 2011). The search for available literature would be conducted through Google
Scholar and Google search engine by making an effective use of the key words like consumer
trust, e-commerce, internet, transparency, data security, data privacy, theft of personal
identity, personalization, brand reputations, business performance, customer satisfaction and
customer loyalty.
Primary Data
The researcher in order to satisfy the demands of the study would collect primary data by
conducting a questionnaire survey (Bernard, 2011). The purpose of the questionnaire survey
would be to collect information in context to the consumers’ perception towards the
importance of the different trust factors and how they would behave or conduct their online
activities if they realize that their personal data and identity is at stake or is misused. The
questions in the questionnaire would be developed on the basis of the factors identified in the
literature review (Morgan, 2007). The questionnaire survey would be targeted towards the
group of individuals who are 18 years and above and would include both men and women.
The questionnaire survey would continue until the researcher would have collected 80
properly filled in questionnaires. The collected response of the customers would be statically
analyzed by making an effective use of the SPSS software. The data would be presented
through charts, tables and graphs.
Sampling Technique and Sample Size
The sample selection for the questionnaire survey would be done through probabilistic
sampling technique to ensure that the respondents are offered equal opportunity to participate
in the survey (Lodico and Spaulding, 2010). The number of respondents that would be
targeted by the researcher would include 80 respondents.
Organization of the Study, project Budget and Schedule
Chapter 1: Introduction
The introduction chapter would provide the background of the study, the research
rationale, the problem statement, the research aim and objectives and the research
questions.
Chapter 2: Literature Review
9 | P a g e
library and from the lectures and notes and study materials provided by the mentors (Hair and
Money, 2011). The search for available literature would be conducted through Google
Scholar and Google search engine by making an effective use of the key words like consumer
trust, e-commerce, internet, transparency, data security, data privacy, theft of personal
identity, personalization, brand reputations, business performance, customer satisfaction and
customer loyalty.
Primary Data
The researcher in order to satisfy the demands of the study would collect primary data by
conducting a questionnaire survey (Bernard, 2011). The purpose of the questionnaire survey
would be to collect information in context to the consumers’ perception towards the
importance of the different trust factors and how they would behave or conduct their online
activities if they realize that their personal data and identity is at stake or is misused. The
questions in the questionnaire would be developed on the basis of the factors identified in the
literature review (Morgan, 2007). The questionnaire survey would be targeted towards the
group of individuals who are 18 years and above and would include both men and women.
The questionnaire survey would continue until the researcher would have collected 80
properly filled in questionnaires. The collected response of the customers would be statically
analyzed by making an effective use of the SPSS software. The data would be presented
through charts, tables and graphs.
Sampling Technique and Sample Size
The sample selection for the questionnaire survey would be done through probabilistic
sampling technique to ensure that the respondents are offered equal opportunity to participate
in the survey (Lodico and Spaulding, 2010). The number of respondents that would be
targeted by the researcher would include 80 respondents.
Organization of the Study, project Budget and Schedule
Chapter 1: Introduction
The introduction chapter would provide the background of the study, the research
rationale, the problem statement, the research aim and objectives and the research
questions.
Chapter 2: Literature Review
9 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The chapter would provide some theoretical aspects in context internet and e-
commerce together with consumers’ trust in e-commerce and the factors that affect
the consumers’ trust. It would also include the arguments of the early researchers and
scholars about the relationship between the data privacy concerns and business
performance and would provide a conceptual framework.
Chapter 3: Research Methodology
The research methodology would present the empirical methods that would contribute
towards conducting the study successfully. It would also provide the research
strategy, research approach, research design, data collection methods, data analysis
methods, sampling size and sampling technique, research ethics and research
limitation with a proper gantt chart to highlight the activities with adequate time
frame.
Chapter 4: Data Analysis, Findings and Discussion
The present chapter would include the analysis of the responses collected from the
survey. The chapter would present the results of the questionnaire and then it would
end with the discussions of the results.
Chapter 5: Conclusion and Recommendations
The final chapter would summarize the study and emphasize on analyzing the
successful achievement of the research objectives on the basis of the alignment
between the researcher’s theoretical knowledge gained form literature review and
from the practical observations collected from questionnaire survey. The chapter
would end with recommendations and future scope of the research.
Budget for Conducting the Study
The study would demand wide range of resources that would include the financial resources,
the physical resources in the form of pencil, pen, paper, smartphone, printer, internet services
and computer and scanner. The study would also involve travelling expenses. Thus, the
expense breakdown can be presented as follows:
10 | P a g e
commerce together with consumers’ trust in e-commerce and the factors that affect
the consumers’ trust. It would also include the arguments of the early researchers and
scholars about the relationship between the data privacy concerns and business
performance and would provide a conceptual framework.
Chapter 3: Research Methodology
The research methodology would present the empirical methods that would contribute
towards conducting the study successfully. It would also provide the research
strategy, research approach, research design, data collection methods, data analysis
methods, sampling size and sampling technique, research ethics and research
limitation with a proper gantt chart to highlight the activities with adequate time
frame.
Chapter 4: Data Analysis, Findings and Discussion
The present chapter would include the analysis of the responses collected from the
survey. The chapter would present the results of the questionnaire and then it would
end with the discussions of the results.
Chapter 5: Conclusion and Recommendations
The final chapter would summarize the study and emphasize on analyzing the
successful achievement of the research objectives on the basis of the alignment
between the researcher’s theoretical knowledge gained form literature review and
from the practical observations collected from questionnaire survey. The chapter
would end with recommendations and future scope of the research.
Budget for Conducting the Study
The study would demand wide range of resources that would include the financial resources,
the physical resources in the form of pencil, pen, paper, smartphone, printer, internet services
and computer and scanner. The study would also involve travelling expenses. Thus, the
expense breakdown can be presented as follows:
10 | P a g e
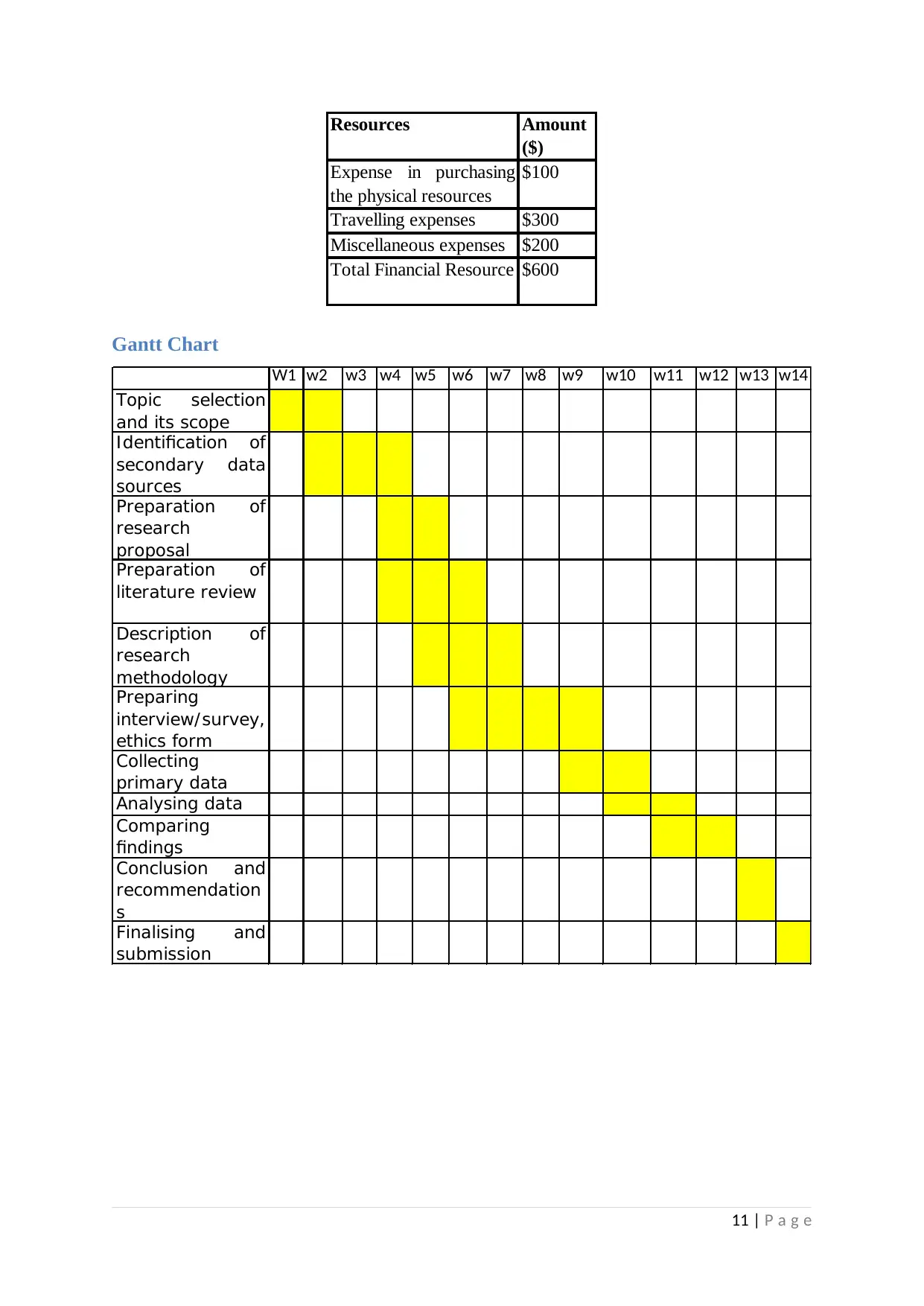
Resources Amount
($)
Expense in purchasing
the physical resources
$100
Travelling expenses $300
Miscellaneous expenses $200
Total Financial Resource $600
Gantt Chart
W1 w2 w3 w4 w5 w6 w7 w8 w9 w10 w11 w12 w13 w14
Topic selection
and its scope
Identification of
secondary data
sources
Preparation of
research
proposal
Preparation of
literature review
Description of
research
methodology
Preparing
interview/ survey,
ethics form
Collecting
primary data
Analysing data
Comparing
findings
Conclusion and
recommendation
s
Finalising and
submission
11 | P a g e
($)
Expense in purchasing
the physical resources
$100
Travelling expenses $300
Miscellaneous expenses $200
Total Financial Resource $600
Gantt Chart
W1 w2 w3 w4 w5 w6 w7 w8 w9 w10 w11 w12 w13 w14
Topic selection
and its scope
Identification of
secondary data
sources
Preparation of
research
proposal
Preparation of
literature review
Description of
research
methodology
Preparing
interview/ survey,
ethics form
Collecting
primary data
Analysing data
Comparing
findings
Conclusion and
recommendation
s
Finalising and
submission
11 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





