E-Commerce Applications: Analyzing Vulnerabilities, Attacks & Security
VerifiedAdded on 2022/09/17
|10
|1904
|20
Report
AI Summary
This report provides an overview of vulnerabilities, attacks, and countermeasures in e-commerce applications. It categorizes attacks into man-made and automated types, highlighting the impact of security breaches on customer trust and online transactions. The report discusses administrative, physical, and technical security vulnerabilities, including database server threats, firewall weaknesses, TCP/IP vulnerabilities, lack of XML validation, and client-side validation issues. It recommends countermeasures such as using firewalls, secure socket layers, strong passwords, and regular security audits. The importance of employee awareness and the impact of security vulnerabilities on e-commerce businesses are also emphasized. The report concludes that a combination of technological advancements, security protocols, and end-user awareness is crucial for safeguarding against e-commerce attacks. Desklib offers similar solved assignments and past papers for students.

1
E-Commerce Applications: Vulnerabilities, Attacks and Countermeasures
Student’s Name:
Institution Affiliation:
E-Commerce Applications: Vulnerabilities, Attacks and Countermeasures
Student’s Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
The broad utilization of web based business makes new ways for both picture and brands to be
attacked. Attackers utilizing different tricks and strategies to discover different escape clauses in
the framework. While there has been great approaches to recognize dangers, teaching clients and
distinguishing countermeasures. Attacks on client delicate data has the unfavorable impact of
diminishing the purchaser confidence on online exchanges, which occurs in Internet business.
Anticipation is superior to fix, great learning and comprehension of the online dangers can be
utilized as a device to stay away from online attacks.
Keywords: Attack on E-commerce, Online frauds, E-Commerce, Security breach,
Vulnerabilities, Fraud.
Introduction
Broad utilization of web has given the ascent to new advancements in the innovation. Web has
turned into the mechanism for doing the few exchanges on the web. Its convenience and
accessibility showed up as the best advertising and business apparatus of the Internet. In late
2010, the Avalanche phishing activity was in charge of an amazing 68% of all phishing
attacks[1]. This paper abridges the information of different kinds of assaults. We attempted to
isolate the assault in two general classifications for example man made attacks and robotized
attacks. In a decade ago web based business industry endured a great deal by way lacking trust
and client base, different installment entryways and bank approval procedures are helpless
against the man-in-center sort of attacks. A denial of service assault results in to association's
Internet entry difficult to reach and interferes with the on-line business exercises. The more
Abstract
The broad utilization of web based business makes new ways for both picture and brands to be
attacked. Attackers utilizing different tricks and strategies to discover different escape clauses in
the framework. While there has been great approaches to recognize dangers, teaching clients and
distinguishing countermeasures. Attacks on client delicate data has the unfavorable impact of
diminishing the purchaser confidence on online exchanges, which occurs in Internet business.
Anticipation is superior to fix, great learning and comprehension of the online dangers can be
utilized as a device to stay away from online attacks.
Keywords: Attack on E-commerce, Online frauds, E-Commerce, Security breach,
Vulnerabilities, Fraud.
Introduction
Broad utilization of web has given the ascent to new advancements in the innovation. Web has
turned into the mechanism for doing the few exchanges on the web. Its convenience and
accessibility showed up as the best advertising and business apparatus of the Internet. In late
2010, the Avalanche phishing activity was in charge of an amazing 68% of all phishing
attacks[1]. This paper abridges the information of different kinds of assaults. We attempted to
isolate the assault in two general classifications for example man made attacks and robotized
attacks. In a decade ago web based business industry endured a great deal by way lacking trust
and client base, different installment entryways and bank approval procedures are helpless
against the man-in-center sort of attacks. A denial of service assault results in to association's
Internet entry difficult to reach and interferes with the on-line business exercises. The more

3
genuine classification of assaults is those that include the robbery or annihilation of secure data.
This sort of security break puts enduring impacts on the focused on E-business site.
Vulnerabilities
Vulnerabilities is a occurrence which enables an assailant to lessen a authentication. To misuse a
defenselessness, an assailant must have at any rate one appropriate device or procedure that can
interface with a framework shortcoming[1]
Administrative security vulnerabilities in E-commerce
a) Database server threats and vulnerabilities: According to Verison data breach investigation
report, there are different procedures to attack a database. Outside attacks can misarrange the
data in the database[2]. In addition to misarrangemet, feeble and unreliable Web and mobile
application can be utilized to attack the database. Web and mobile apps such as e-commerce is
targeted by attackers all the time[3].
b) Firewall vulnerabilities: According to Magic quadrant document, a firewall weakness is
characterized as a blunder executed during firewall structure, execution, or design, that can be
misused to assault the confided in system that the firewall should ensure [8].
Physical security vulnerabilities in E-commerce
a) Transfer control protocol vulnerabilities : Transfer control protocol is extremely prominent
and known to each one, internet protocol that handles steering bundles of information from one
PC to another one. TCP , is to ensure that the information is transmitted from one computer to
another one safely [3] ,[9].
genuine classification of assaults is those that include the robbery or annihilation of secure data.
This sort of security break puts enduring impacts on the focused on E-business site.
Vulnerabilities
Vulnerabilities is a occurrence which enables an assailant to lessen a authentication. To misuse a
defenselessness, an assailant must have at any rate one appropriate device or procedure that can
interface with a framework shortcoming[1]
Administrative security vulnerabilities in E-commerce
a) Database server threats and vulnerabilities: According to Verison data breach investigation
report, there are different procedures to attack a database. Outside attacks can misarrange the
data in the database[2]. In addition to misarrangemet, feeble and unreliable Web and mobile
application can be utilized to attack the database. Web and mobile apps such as e-commerce is
targeted by attackers all the time[3].
b) Firewall vulnerabilities: According to Magic quadrant document, a firewall weakness is
characterized as a blunder executed during firewall structure, execution, or design, that can be
misused to assault the confided in system that the firewall should ensure [8].
Physical security vulnerabilities in E-commerce
a) Transfer control protocol vulnerabilities : Transfer control protocol is extremely prominent
and known to each one, internet protocol that handles steering bundles of information from one
PC to another one. TCP , is to ensure that the information is transmitted from one computer to
another one safely [3] ,[9].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
b) IPS vulnerabilities: The fundamental elements of interruption avoidance frameworks is to
recognize vindictive movement, log data about pernicious action, endeavor to square/stop action,
and report action[4],[5],[6].
Technical security vulnerabilities in E-commerce
a) Lack of XML validation check: Inability to actualize approval when parsing data through
XML gives assailant the best approach to supply malignant information to the application. By
tolerating a XML report before checking for vulnerability, the software engineer gives a chance
to assailants to duplicate unforeseen, nonsensical, or noxious info.
b) Clients side validation: Carrying out validation in the client side using Javascript gives an
assurance in the servre side validation. You should ensure that both the client and the server side
validations are working since attacker can manipulate the client’s side validation code and logs
in to the customers or admin account[7], [9]. Customer side approval is generally utilized, yet
isn't security important.
Recommendations and counter measures
A significant number of these attacks can be halted and identified early. To keep application free
of an attack needs organised methodology. Three methodologies has been examined in this
research. Here are the suggestions for security upgrades, a far reaching security plan is appeared
so as to oversee security hazard[10], [11].
Platform threats and vulnerabilities
Network port exploits.
b) IPS vulnerabilities: The fundamental elements of interruption avoidance frameworks is to
recognize vindictive movement, log data about pernicious action, endeavor to square/stop action,
and report action[4],[5],[6].
Technical security vulnerabilities in E-commerce
a) Lack of XML validation check: Inability to actualize approval when parsing data through
XML gives assailant the best approach to supply malignant information to the application. By
tolerating a XML report before checking for vulnerability, the software engineer gives a chance
to assailants to duplicate unforeseen, nonsensical, or noxious info.
b) Clients side validation: Carrying out validation in the client side using Javascript gives an
assurance in the servre side validation. You should ensure that both the client and the server side
validations are working since attacker can manipulate the client’s side validation code and logs
in to the customers or admin account[7], [9]. Customer side approval is generally utilized, yet
isn't security important.
Recommendations and counter measures
A significant number of these attacks can be halted and identified early. To keep application free
of an attack needs organised methodology. Three methodologies has been examined in this
research. Here are the suggestions for security upgrades, a far reaching security plan is appeared
so as to oversee security hazard[10], [11].
Platform threats and vulnerabilities
Network port exploits.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
a) E-commerce applications should use firewalls in the server.
b) They should use secure socket layer as well. Not haviing correct settings in the application.
The administrators should be keen when setting up configurations on the system. Their accounts
should have strong passwords as well[12], [13].
Authentification vulnerabilities
The system should allow strong and complex passwords so that it can be dificult for
hackers to crack the passswords.
The system admins should audit users accounts regularly to ensure that they have proper
access to data in the database.
Programming vulnerabilities
Passwords and any other sensitive information should not be stored
Developers should use use website vulnerability scanners which crawl the entire website
and checks for cross site forgery requests.
Data access vulnerabilities
Developers should use latest frameworks which correctly encrpts database access.
Server certificates such as secure socket shell should be correctly implemented in the
domain.
Using Strong and complex passwords
a) E-commerce applications should use firewalls in the server.
b) They should use secure socket layer as well. Not haviing correct settings in the application.
The administrators should be keen when setting up configurations on the system. Their accounts
should have strong passwords as well[12], [13].
Authentification vulnerabilities
The system should allow strong and complex passwords so that it can be dificult for
hackers to crack the passswords.
The system admins should audit users accounts regularly to ensure that they have proper
access to data in the database.
Programming vulnerabilities
Passwords and any other sensitive information should not be stored
Developers should use use website vulnerability scanners which crawl the entire website
and checks for cross site forgery requests.
Data access vulnerabilities
Developers should use latest frameworks which correctly encrpts database access.
Server certificates such as secure socket shell should be correctly implemented in the
domain.
Using Strong and complex passwords

6
According to the Open web application security, One of the main vulnerability that attackers
looks for in an application is usse of simple passwords. Simple passwords allow attackers to use
available tools and log in to the system. They look for default usernames and passwords such as
admin for root for username and password respectively[14].
Firewall
Firewall is essential feature in a server where you hosting your application. It protects your
application from malware. It should be configured such that all the data coming to the
application comes through firewall before being stored in the database[1], [2].
Employees awareness
Representatives and their work places are the fundamental focuses for attackers. It is important
to keep employees upto data on security measures regarding the most recent assault procedures
being utilized by assailant[11]. Workers ought to be told to report any suspicious movement,
messages to security dept.
Impact of security vulnerability in e-commerce
E-commerce exploit of vulnerabilities have huge impact on the business. The more the attack is
carried out the more the impact becomes on the business. In most cases attackers targets stored
information such as credit cards information[12]. Gaining access to the credit card information
means that they can exploit the clients from vendors systems.
According to the Open web application security, One of the main vulnerability that attackers
looks for in an application is usse of simple passwords. Simple passwords allow attackers to use
available tools and log in to the system. They look for default usernames and passwords such as
admin for root for username and password respectively[14].
Firewall
Firewall is essential feature in a server where you hosting your application. It protects your
application from malware. It should be configured such that all the data coming to the
application comes through firewall before being stored in the database[1], [2].
Employees awareness
Representatives and their work places are the fundamental focuses for attackers. It is important
to keep employees upto data on security measures regarding the most recent assault procedures
being utilized by assailant[11]. Workers ought to be told to report any suspicious movement,
messages to security dept.
Impact of security vulnerability in e-commerce
E-commerce exploit of vulnerabilities have huge impact on the business. The more the attack is
carried out the more the impact becomes on the business. In most cases attackers targets stored
information such as credit cards information[12]. Gaining access to the credit card information
means that they can exploit the clients from vendors systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
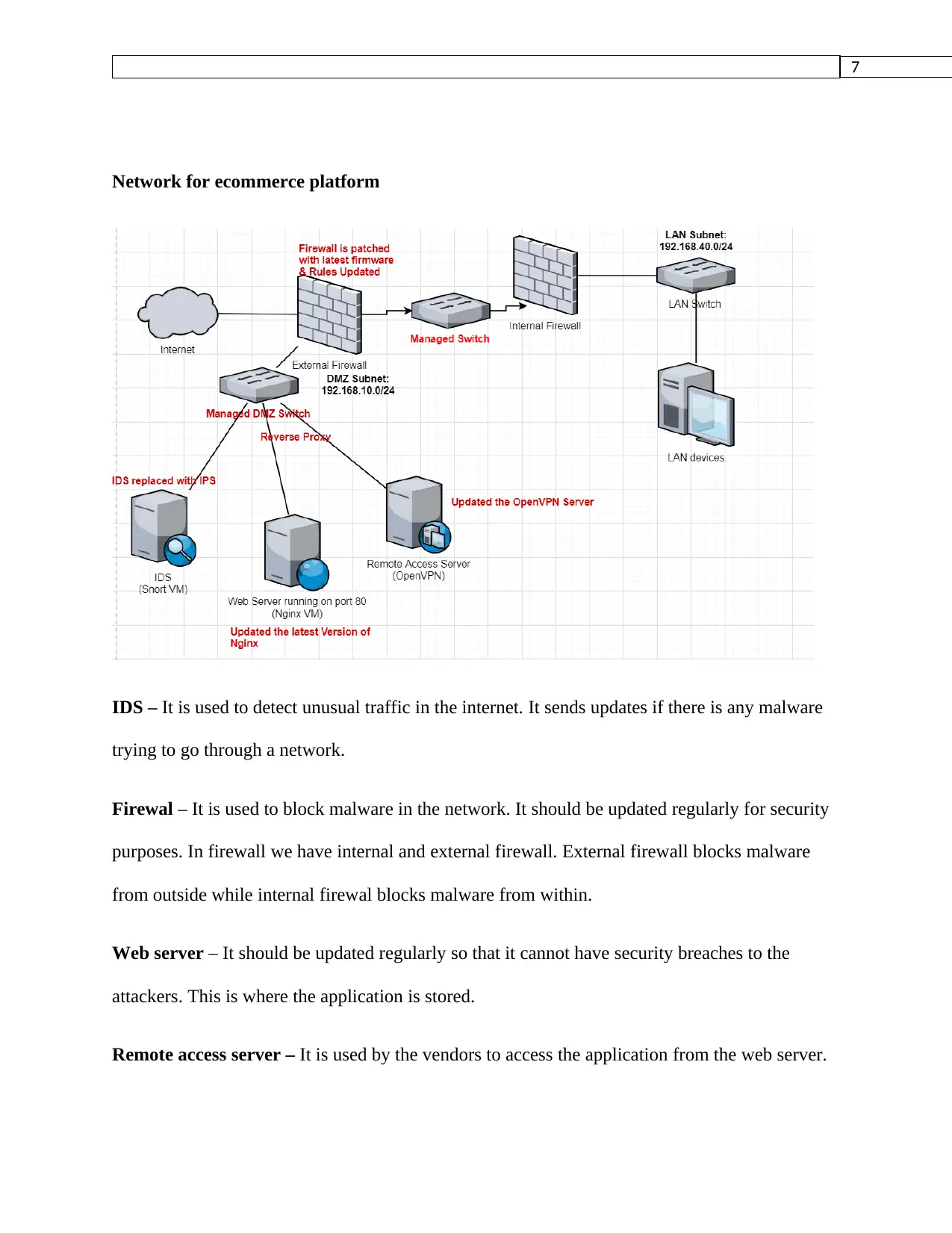
7
Network for ecommerce platform
IDS – It is used to detect unusual traffic in the internet. It sends updates if there is any malware
trying to go through a network.
Firewal – It is used to block malware in the network. It should be updated regularly for security
purposes. In firewall we have internal and external firewall. External firewall blocks malware
from outside while internal firewal blocks malware from within.
Web server – It should be updated regularly so that it cannot have security breaches to the
attackers. This is where the application is stored.
Remote access server – It is used by the vendors to access the application from the web server.
Network for ecommerce platform
IDS – It is used to detect unusual traffic in the internet. It sends updates if there is any malware
trying to go through a network.
Firewal – It is used to block malware in the network. It should be updated regularly for security
purposes. In firewall we have internal and external firewall. External firewall blocks malware
from outside while internal firewal blocks malware from within.
Web server – It should be updated regularly so that it cannot have security breaches to the
attackers. This is where the application is stored.
Remote access server – It is used by the vendors to access the application from the web server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Conclusion
We believe that there should be a certified security for the customer side application and a blend
of use of the two advances and end client mindfulness are the main powerful methods for
safeguard against internet business attacks. Innovations, such as IDS(Intrusion detection system),
and programming languages framework will upgrade the vulnerability of the application since it
has been tasted by many and receives updated regularly. Having just a layer 3 gadget ensuring
basic parts of the system is never again adequate. Application engineers should examine their
code to ensure that there is no security patch in the application before deploying it to the
production environment.
Conclusion
We believe that there should be a certified security for the customer side application and a blend
of use of the two advances and end client mindfulness are the main powerful methods for
safeguard against internet business attacks. Innovations, such as IDS(Intrusion detection system),
and programming languages framework will upgrade the vulnerability of the application since it
has been tasted by many and receives updated regularly. Having just a layer 3 gadget ensuring
basic parts of the system is never again adequate. Application engineers should examine their
code to ensure that there is no security patch in the application before deploying it to the
production environment.

9
References
[1] Rod Rasmussen,Greg Aaron, “Global Phishing Survey: Trends and Domain Name Use”,
“Internet Policy Committee, 1H2010 October 2016
[2] P.S. Keila and D.B. Skillicorn, "Detecting Unusual and Deceptive Communication in
Email",External Technical Report,School of Computing Queen’s University,Kingston, Ontario,
Canada K7L 3N6,ISSN-0836-0227-2005-498,June 8, 2017
[3] Darshanand Khusial ,Ross McKegney , "e-Commerce security: Attacks and preventive
strategies", IBM Software Group at the IBM Toronto lab.,13 Apr 2019
[4]Brian Cashell, William D. Jackson, Mark Jickling, and Baird Webel, "The Economic Impact
of Cyber-Attacks",CRS Report for Congress, The Library of Congress, Government and
Finance Division, April 1, 2016
[5] Malware statics 2011 : http://en.wikipedia.org/wiki/File:Malware_statics_2015-03-16-
en.svg
[6] P S Lokhande, B B Meshram, “ Evaluation of High Performance, Secure Enterprise
Content Management System, International Conference on Electronics, Information and
Communication Systems Engineering., ICEICE-2017, Jodhpur , Rajsthan, India.,March 28th-
30th -2018.
[7] P.S. Lokhande, P.H. Rathod, " Buffer Overflow Attack Detection By Using Different
Techniques", 2nd International Conference On “Recent Trends in Business, Management &
IT”In association with Department of Commerce & Research Centre University of Pune,24th
April 2018
References
[1] Rod Rasmussen,Greg Aaron, “Global Phishing Survey: Trends and Domain Name Use”,
“Internet Policy Committee, 1H2010 October 2016
[2] P.S. Keila and D.B. Skillicorn, "Detecting Unusual and Deceptive Communication in
Email",External Technical Report,School of Computing Queen’s University,Kingston, Ontario,
Canada K7L 3N6,ISSN-0836-0227-2005-498,June 8, 2017
[3] Darshanand Khusial ,Ross McKegney , "e-Commerce security: Attacks and preventive
strategies", IBM Software Group at the IBM Toronto lab.,13 Apr 2019
[4]Brian Cashell, William D. Jackson, Mark Jickling, and Baird Webel, "The Economic Impact
of Cyber-Attacks",CRS Report for Congress, The Library of Congress, Government and
Finance Division, April 1, 2016
[5] Malware statics 2011 : http://en.wikipedia.org/wiki/File:Malware_statics_2015-03-16-
en.svg
[6] P S Lokhande, B B Meshram, “ Evaluation of High Performance, Secure Enterprise
Content Management System, International Conference on Electronics, Information and
Communication Systems Engineering., ICEICE-2017, Jodhpur , Rajsthan, India.,March 28th-
30th -2018.
[7] P.S. Lokhande, P.H. Rathod, " Buffer Overflow Attack Detection By Using Different
Techniques", 2nd International Conference On “Recent Trends in Business, Management &
IT”In association with Department of Commerce & Research Centre University of Pune,24th
April 2018
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
[8] Seny Kamara, Sonia Fahmy, Eugene Schultz, Florian Kerschbaum, and Michael
Frantzen,“Analysis of Vulnerabilities in Internet Firewalls”,Center for Education and Research
in Information Assurance and Security (CERIAS),Purdue University656 Oval Dr., West
Lafayette, IN 47907–2039, USA
[9] Dave Wichers, COO, Aspect Security OWASP Board Member,“OWASP Top 10 – 2015
The Top 10 Most Critical Web Application Security Risks, OWASP Foundation-2018”
[10] Engin Kirdaa,, Nenad Jovanovicb, Christopher Kruegelc, Giovanni Vigna, “Client-side
cross-site scripting protection”, Computers and Security, Elsevier, 2017.
[11] Narn-Yih Lee, Yu-Chung Chiu, “Improved remote authentication scheme with smart
card”, Elsevier, Computer Standards & Interfaces 27 (2016) 177–180
[12] Web Link: http://www.thc.org/blob/manhydra/thc_hydra_article_r3.pdf
[13] Web Link : http://pr.openwall.net/dl/pwdump/pwdump4.zip
[14] Web Link : http://www.antsight.com/zsl/rainbowcrack
[8] Seny Kamara, Sonia Fahmy, Eugene Schultz, Florian Kerschbaum, and Michael
Frantzen,“Analysis of Vulnerabilities in Internet Firewalls”,Center for Education and Research
in Information Assurance and Security (CERIAS),Purdue University656 Oval Dr., West
Lafayette, IN 47907–2039, USA
[9] Dave Wichers, COO, Aspect Security OWASP Board Member,“OWASP Top 10 – 2015
The Top 10 Most Critical Web Application Security Risks, OWASP Foundation-2018”
[10] Engin Kirdaa,, Nenad Jovanovicb, Christopher Kruegelc, Giovanni Vigna, “Client-side
cross-site scripting protection”, Computers and Security, Elsevier, 2017.
[11] Narn-Yih Lee, Yu-Chung Chiu, “Improved remote authentication scheme with smart
card”, Elsevier, Computer Standards & Interfaces 27 (2016) 177–180
[12] Web Link: http://www.thc.org/blob/manhydra/thc_hydra_article_r3.pdf
[13] Web Link : http://pr.openwall.net/dl/pwdump/pwdump4.zip
[14] Web Link : http://www.antsight.com/zsl/rainbowcrack
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





