Effectiveness of Data Security in Mobile Computing: A Research Report
VerifiedAdded on 2023/01/06
|23
|4078
|47
Report
AI Summary
This report investigates the effectiveness of data security in mobile computing. It employs a positivism philosophy, deductive approach, and survey strategy with a cross-sectional time horizon to collect and analyze data. The research utilizes questionnaires to gather quantitative data, focusing on respondents' knowledge, security types, reasons for securing data, and perceived benefits and issues related to mobile computing security. The data analysis involves frequency distribution, presenting findings on various aspects of mobile computing security. The report concludes with recommendations based on the research findings, aiming to achieve the research objectives. The study highlights the importance of data security and its impact on businesses and users. The report is a comprehensive analysis of the current state of mobile computing security and offers insights into future directions.

userr
Research Methods AE_2
(Data security in mobile computing)
Research Methods AE_2
(Data security in mobile computing)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT
Main purpose of this report is to define effectiveness of data security in mobile
computing. This is a main purpose and for attaining this, questionnaire used by researcher that
results in collecting valid and reliable outcomes within less period of time. Different types of
research methodologies used by researcher such as positivism philosophy, deductive approach,
survey strategy, cross-sectional time horizon etc. These are considered more essential
methodology within an investigation. These helped researcher in attainment of research aim and
objectives systematically and successfully. Findings also helped in identification of the opinion
of respondents about the data security in mobile computing. At last, conclusion and
recommendations, these chapter helped in accomplishment of all research objectives in
successful manner.
Main purpose of this report is to define effectiveness of data security in mobile
computing. This is a main purpose and for attaining this, questionnaire used by researcher that
results in collecting valid and reliable outcomes within less period of time. Different types of
research methodologies used by researcher such as positivism philosophy, deductive approach,
survey strategy, cross-sectional time horizon etc. These are considered more essential
methodology within an investigation. These helped researcher in attainment of research aim and
objectives systematically and successfully. Findings also helped in identification of the opinion
of respondents about the data security in mobile computing. At last, conclusion and
recommendations, these chapter helped in accomplishment of all research objectives in
successful manner.

Table of Contents
ABSTRACT.....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
RESEARCH METHODOLOGY ....................................................................................................5
DATA ANALYSIS .........................................................................................................................7
CONCLUSION AND RECOMMENDATIONS .........................................................................18
REFERENCES .............................................................................................................................20
APPENDIX ...................................................................................................................................21
ABSTRACT.....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
RESEARCH METHODOLOGY ....................................................................................................5
DATA ANALYSIS .........................................................................................................................7
CONCLUSION AND RECOMMENDATIONS .........................................................................18
REFERENCES .............................................................................................................................20
APPENDIX ...................................................................................................................................21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Mobile computing refers as an interaction of human-computer in which a computer is
anticipated to be transported in normal usage that permits for the transmission of voice, video
and data. Mobile computing consist of mobile hardware, mobile communication and mobile
software (Bouazzouni, Conchon and Peyrard, 2018). In addition, mobile computing introduces as
the set of IT technologies, services, products and also operational strategies as well as procedures
that make sure last consumers to gain access to information, computation and related capabilities
and resources while mobile. There are different benefits and importance of mobile computing
such as location flexibility, saves time, enhanced productivity etc. This will be essential in
securing of data in mobile computing.
Mobile computing refers as an interaction of human-computer in which a computer is
anticipated to be transported in normal usage that permits for the transmission of voice, video
and data. Mobile computing consist of mobile hardware, mobile communication and mobile
software (Bouazzouni, Conchon and Peyrard, 2018). In addition, mobile computing introduces as
the set of IT technologies, services, products and also operational strategies as well as procedures
that make sure last consumers to gain access to information, computation and related capabilities
and resources while mobile. There are different benefits and importance of mobile computing
such as location flexibility, saves time, enhanced productivity etc. This will be essential in
securing of data in mobile computing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH METHODOLOGY
Research methodology introduces to the important and significant process of collecting
as well as analysing valuable data regarding the topic. Primary intent of research methodology is
to facilitate researcher by giving reliable and useful information. This part of the research report
consists of various kind of methodology which are valuable for investigator in accomplishment
aim and objectives of the study within less period of time (Guan and et. al., 2018). Some
important types of research methodologies will be explained as below:
Research philosophy: This section of the methodology has two essential types of
philosophies are called positivism and interpretivisim. Theses philosophies are essential but
according to the existing study, positivism kind of research philosophy is more useful because it
facilitates in collecting, analysing and using of quantitative data that outputs in completion of full
research systematically. Interpretivisim research philosophy is not valuable within a current
study because it requires qualitative data that takes maximum time (Huang and et. al., 2018).
Justification: In conducting the present investigation, there will be the positivism
research philosophy used. The main reason to use this philosophy is that it provides the in- depth
analysis or explanation regarding the mobile computing in detailed manner. This research
philology is based on the quantitative method and its main focus is on providing the positive
outcomes.
Research approach: Inductive and deductive are considered two types of research
approaches. For doing this investigation, deductive approach is more suitable because it
facilitates in analysing of quantitative information in less period of time. Inductive approach is
not essential for carrying out present investigation because it requires qualitative data that takes
maximum and cost also (Ibtihal and Hassan, 2020).
Justification: Deductive research approach is more effective because it mainly consists
beginning with theory, developing the hypothesis from that theory and then gathering data for
test hypothesis. The main benefit of using the deductive research approach is that it provides the
reliable and valid information.
Research strategy: There are various types of research strategies including case study,
experimental, survey, action research etc. These are considered main types but for executing this
investigation, survey will be applied. This will assist in gathering of primary and quantitative
Research methodology introduces to the important and significant process of collecting
as well as analysing valuable data regarding the topic. Primary intent of research methodology is
to facilitate researcher by giving reliable and useful information. This part of the research report
consists of various kind of methodology which are valuable for investigator in accomplishment
aim and objectives of the study within less period of time (Guan and et. al., 2018). Some
important types of research methodologies will be explained as below:
Research philosophy: This section of the methodology has two essential types of
philosophies are called positivism and interpretivisim. Theses philosophies are essential but
according to the existing study, positivism kind of research philosophy is more useful because it
facilitates in collecting, analysing and using of quantitative data that outputs in completion of full
research systematically. Interpretivisim research philosophy is not valuable within a current
study because it requires qualitative data that takes maximum time (Huang and et. al., 2018).
Justification: In conducting the present investigation, there will be the positivism
research philosophy used. The main reason to use this philosophy is that it provides the in- depth
analysis or explanation regarding the mobile computing in detailed manner. This research
philology is based on the quantitative method and its main focus is on providing the positive
outcomes.
Research approach: Inductive and deductive are considered two types of research
approaches. For doing this investigation, deductive approach is more suitable because it
facilitates in analysing of quantitative information in less period of time. Inductive approach is
not essential for carrying out present investigation because it requires qualitative data that takes
maximum and cost also (Ibtihal and Hassan, 2020).
Justification: Deductive research approach is more effective because it mainly consists
beginning with theory, developing the hypothesis from that theory and then gathering data for
test hypothesis. The main benefit of using the deductive research approach is that it provides the
reliable and valid information.
Research strategy: There are various types of research strategies including case study,
experimental, survey, action research etc. These are considered main types but for executing this
investigation, survey will be applied. This will assist in gathering of primary and quantitative

data effectively and timely (Kumar, Raj and Jelciana, 2018). The benefit of using this method is
that it is time saving and collect the large number of information from this.
Research choice: This is an essential part of methodology that is divided into three types
including mixed method, multi-mixed method and mono method. These are important but
according to the present study, mono method is suitable and effective choice. This choice assist
investigator in assembling of only single type of information, either qualitative or quantitative.
Along with the, quantitative data will be selected under mono choice. Biggest reason behind
applying quantitative data is it facilitate in completion of full project effectively and
systematically (Li and et. al., 2018).
Justification: There will be quantitative research used as this is helpful in providing the
reliable information on the basis of facts and figures. Some variables are consisting as data
related to the relevant information. in this method it is easier to collect information that gives the
positive outcomes.
Time horizon: Time is important for investigator because it facilitate researcher in
starting and completion of full project effectively. There are 2 important types of time horizon
which are cross-sectional and longitudinal. These types are essential but within the present study,
cross-sectional time horizon is essential. This approach is based on current situation and also
facilitate investigator in completion of full project effectively and timely (Liao and et. al., 2020).
Longitudinal approach is not valuable in this study because it takes maximum time in research
completion.
Justification: In this, cross- sectional time horizon will be used because it provides the
accurate time to an investigator on the basis of set activities. It will be beneficial because it
provides the accurate time for completion of the research.
Data collection: Data will be collected from two sources such as primary and secondary.
For gathering primary data, questionnaire is a best source that will be used by investigator. In
case of secondary research, there are different number of effective sources including books,
articles, magazines, publication research and many other related to the research topic. All these
sources were only used for literature review in gathering of secondary information (Mishra and
et. al., 2018).
Justification: In conducting the present investigation, there will be the primary and
secondary both method used. In the primary method, there will be questionnaire developed by
that it is time saving and collect the large number of information from this.
Research choice: This is an essential part of methodology that is divided into three types
including mixed method, multi-mixed method and mono method. These are important but
according to the present study, mono method is suitable and effective choice. This choice assist
investigator in assembling of only single type of information, either qualitative or quantitative.
Along with the, quantitative data will be selected under mono choice. Biggest reason behind
applying quantitative data is it facilitate in completion of full project effectively and
systematically (Li and et. al., 2018).
Justification: There will be quantitative research used as this is helpful in providing the
reliable information on the basis of facts and figures. Some variables are consisting as data
related to the relevant information. in this method it is easier to collect information that gives the
positive outcomes.
Time horizon: Time is important for investigator because it facilitate researcher in
starting and completion of full project effectively. There are 2 important types of time horizon
which are cross-sectional and longitudinal. These types are essential but within the present study,
cross-sectional time horizon is essential. This approach is based on current situation and also
facilitate investigator in completion of full project effectively and timely (Liao and et. al., 2020).
Longitudinal approach is not valuable in this study because it takes maximum time in research
completion.
Justification: In this, cross- sectional time horizon will be used because it provides the
accurate time to an investigator on the basis of set activities. It will be beneficial because it
provides the accurate time for completion of the research.
Data collection: Data will be collected from two sources such as primary and secondary.
For gathering primary data, questionnaire is a best source that will be used by investigator. In
case of secondary research, there are different number of effective sources including books,
articles, magazines, publication research and many other related to the research topic. All these
sources were only used for literature review in gathering of secondary information (Mishra and
et. al., 2018).
Justification: In conducting the present investigation, there will be the primary and
secondary both method used. In the primary method, there will be questionnaire developed by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

consisting different questions. Other than this, there will be secondary method used by consisting
different sources for attaining the research objectives in literature review part.
Research instruments: There are various number of research instruments such as focus
group, modelling, interview, questionnaire and observation. All these are essential but according
to the present study, questionnaire is more valuable and suitable instrument for investigator. This
technique helps researcher in collecting of valid and reliable information regarding the topic in
less period of time (Sajjad and et. al., 2018).
Research ethics: Ethics are necessary in an investigation because it facilitates
investigator in wind-up of full project ethically. There are some valuable research principles of
ethics such as non-meleficence, autonomy, beneficence, veracity, justice and confidentiality. All
these are important and useful for investigator in carrying out full research project ethically and
systematically (Zhang and et. al., 2018).
different sources for attaining the research objectives in literature review part.
Research instruments: There are various number of research instruments such as focus
group, modelling, interview, questionnaire and observation. All these are essential but according
to the present study, questionnaire is more valuable and suitable instrument for investigator. This
technique helps researcher in collecting of valid and reliable information regarding the topic in
less period of time (Sajjad and et. al., 2018).
Research ethics: Ethics are necessary in an investigation because it facilitates
investigator in wind-up of full project ethically. There are some valuable research principles of
ethics such as non-meleficence, autonomy, beneficence, veracity, justice and confidentiality. All
these are important and useful for investigator in carrying out full research project ethically and
systematically (Zhang and et. al., 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
DATA ANALYSIS
Data analysis is the systematic and valuable process of evaluating qualitative or
quantitative data regarding the specify field of study. Current investigation is based on
quantitative data and for evaluating that kind of data, frequency distribution analysis will be used
as an analytical technique (Zheng and et. al., 2018). By using this technique, investigator will
make frequency distribution table and then distribute full table in individual table. Frequency
distribution table of current investigation will be shown as below:
Frequency distribution analysis
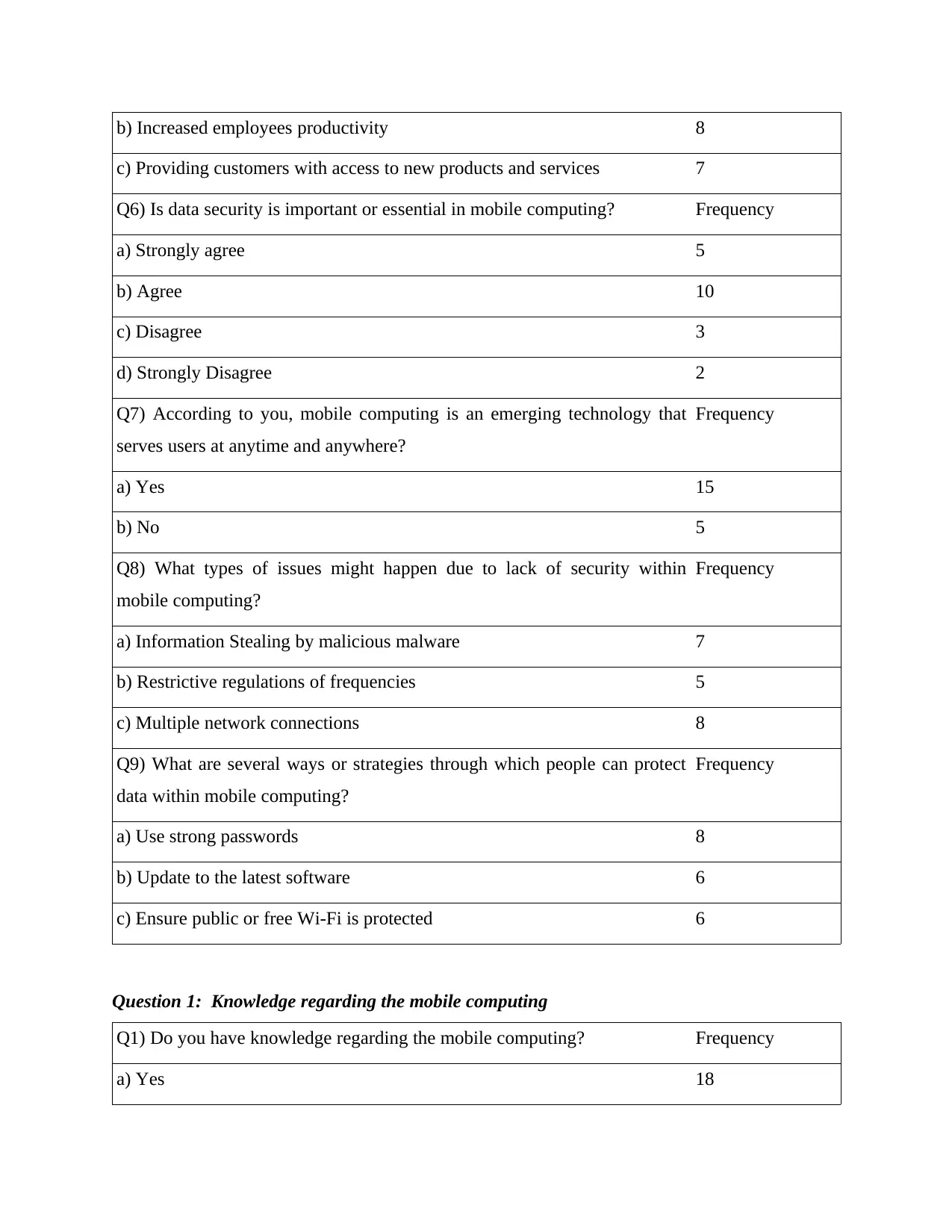
Q1) Do you have knowledge regarding the mobile computing? Frequency
a) Yes 18
b) No 2
Q2) According to you, what types of mobile computing important for
securing data?
Frequency
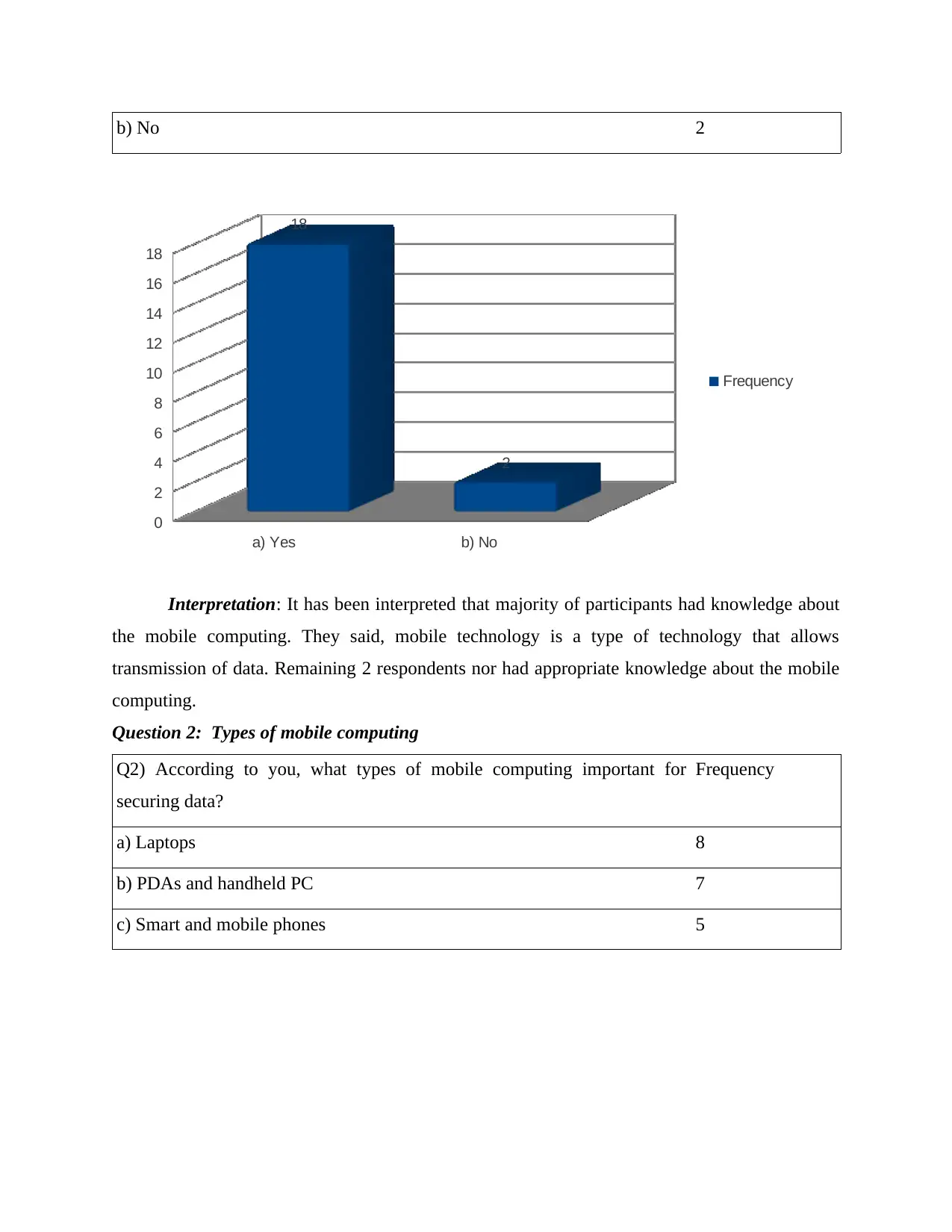
a) Laptops 8
b) PDAs and handheld PC 7
c) Smart and mobile phones 5
Q3) What are some reasons of securing data in mobile computing? Frequency
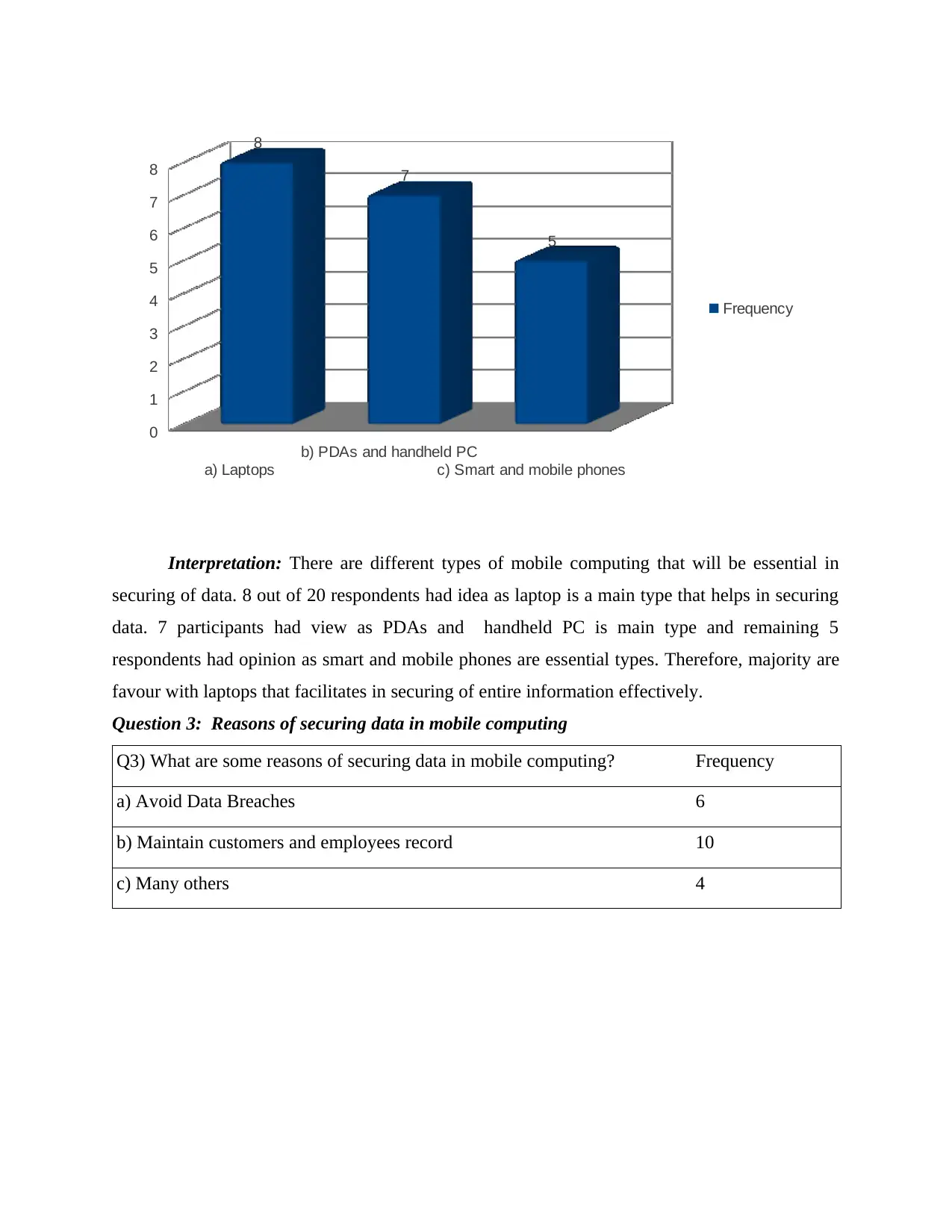
a) Avoid Data Breaches 6
b) Maintain customers and employees record 10
c) Many others 4
Q4) According to you, what is the security in mobile computing? Frequency
a) Protection of smartphones 8
b) Protection of portable computing devices 7
c) Protect computers for hackers 5
Q5) What are the benefits of data security in mobile computing? Frequency
a) Increased responsiveness to customer's needs 5
Data analysis is the systematic and valuable process of evaluating qualitative or
quantitative data regarding the specify field of study. Current investigation is based on
quantitative data and for evaluating that kind of data, frequency distribution analysis will be used
as an analytical technique (Zheng and et. al., 2018). By using this technique, investigator will
make frequency distribution table and then distribute full table in individual table. Frequency
distribution table of current investigation will be shown as below:
Frequency distribution analysis
Q1) Do you have knowledge regarding the mobile computing? Frequency
a) Yes 18
b) No 2
Q2) According to you, what types of mobile computing important for
securing data?
Frequency
a) Laptops 8
b) PDAs and handheld PC 7
c) Smart and mobile phones 5
Q3) What are some reasons of securing data in mobile computing? Frequency
a) Avoid Data Breaches 6
b) Maintain customers and employees record 10
c) Many others 4
Q4) According to you, what is the security in mobile computing? Frequency
a) Protection of smartphones 8
b) Protection of portable computing devices 7
c) Protect computers for hackers 5
Q5) What are the benefits of data security in mobile computing? Frequency
a) Increased responsiveness to customer's needs 5
b) Increased employees productivity 8
c) Providing customers with access to new products and services 7
Q6) Is data security is important or essential in mobile computing? Frequency
a) Strongly agree 5
b) Agree 10
c) Disagree 3
d) Strongly Disagree 2
Q7) According to you, mobile computing is an emerging technology that
serves users at anytime and anywhere?
Frequency
a) Yes 15
b) No 5
Q8) What types of issues might happen due to lack of security within
mobile computing?
Frequency
a) Information Stealing by malicious malware 7
b) Restrictive regulations of frequencies 5
c) Multiple network connections 8
Q9) What are several ways or strategies through which people can protect
data within mobile computing?
Frequency
a) Use strong passwords 8
b) Update to the latest software 6
c) Ensure public or free Wi-Fi is protected 6
Question 1: Knowledge regarding the mobile computing
Q1) Do you have knowledge regarding the mobile computing? Frequency
a) Yes 18
c) Providing customers with access to new products and services 7
Q6) Is data security is important or essential in mobile computing? Frequency
a) Strongly agree 5
b) Agree 10
c) Disagree 3
d) Strongly Disagree 2
Q7) According to you, mobile computing is an emerging technology that
serves users at anytime and anywhere?
Frequency
a) Yes 15
b) No 5
Q8) What types of issues might happen due to lack of security within
mobile computing?
Frequency
a) Information Stealing by malicious malware 7
b) Restrictive regulations of frequencies 5
c) Multiple network connections 8
Q9) What are several ways or strategies through which people can protect
data within mobile computing?
Frequency
a) Use strong passwords 8
b) Update to the latest software 6
c) Ensure public or free Wi-Fi is protected 6
Question 1: Knowledge regarding the mobile computing
Q1) Do you have knowledge regarding the mobile computing? Frequency
a) Yes 18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
b) No 2
a) Yes b) No
0
2
4
6
8
10
12
14
16
18
18
2
Frequency
Interpretation: It has been interpreted that majority of participants had knowledge about
the mobile computing. They said, mobile technology is a type of technology that allows
transmission of data. Remaining 2 respondents nor had appropriate knowledge about the mobile
computing.
Question 2: Types of mobile computing
Q2) According to you, what types of mobile computing important for
securing data?
Frequency
a) Laptops 8
b) PDAs and handheld PC 7
c) Smart and mobile phones 5
a) Yes b) No
0
2
4
6
8
10
12
14
16
18
18
2
Frequency
Interpretation: It has been interpreted that majority of participants had knowledge about
the mobile computing. They said, mobile technology is a type of technology that allows
transmission of data. Remaining 2 respondents nor had appropriate knowledge about the mobile
computing.
Question 2: Types of mobile computing
Q2) According to you, what types of mobile computing important for
securing data?
Frequency
a) Laptops 8
b) PDAs and handheld PC 7
c) Smart and mobile phones 5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
a) Laptops
b) PDAs and handheld PC
c) Smart and mobile phones
0
1
2
3
4
5
6
7
8
8
7
5
Frequency
Interpretation: There are different types of mobile computing that will be essential in
securing of data. 8 out of 20 respondents had idea as laptop is a main type that helps in securing
data. 7 participants had view as PDAs and handheld PC is main type and remaining 5
respondents had opinion as smart and mobile phones are essential types. Therefore, majority are
favour with laptops that facilitates in securing of entire information effectively.
Question 3: Reasons of securing data in mobile computing
Q3) What are some reasons of securing data in mobile computing? Frequency
a) Avoid Data Breaches 6
b) Maintain customers and employees record 10
c) Many others 4
b) PDAs and handheld PC
c) Smart and mobile phones
0
1
2
3
4
5
6
7
8
8
7
5
Frequency
Interpretation: There are different types of mobile computing that will be essential in
securing of data. 8 out of 20 respondents had idea as laptop is a main type that helps in securing
data. 7 participants had view as PDAs and handheld PC is main type and remaining 5
respondents had opinion as smart and mobile phones are essential types. Therefore, majority are
favour with laptops that facilitates in securing of entire information effectively.
Question 3: Reasons of securing data in mobile computing
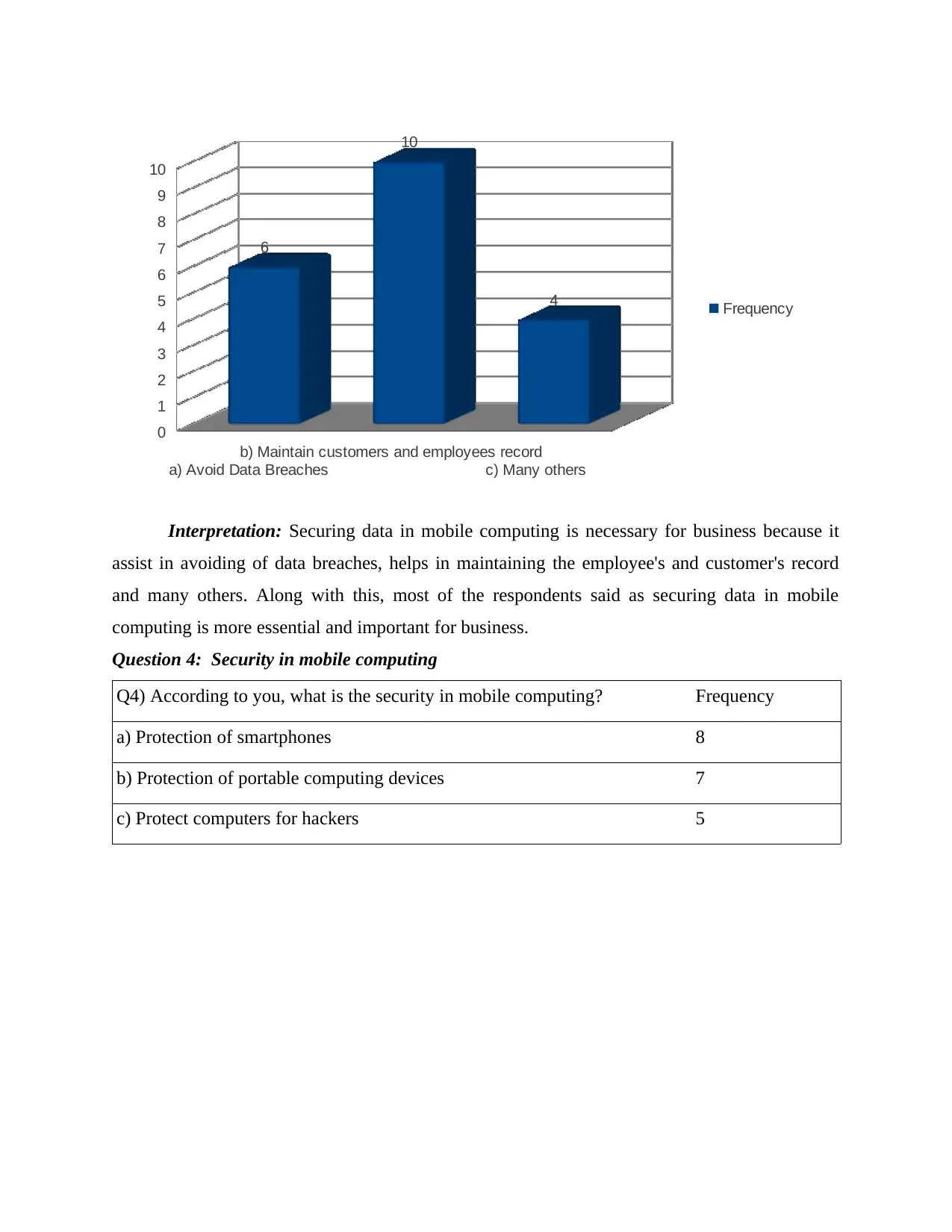
Q3) What are some reasons of securing data in mobile computing? Frequency
a) Avoid Data Breaches 6
b) Maintain customers and employees record 10
c) Many others 4
a) Avoid Data Breaches
b) Maintain customers and employees record
c) Many others
0
1
2
3
4
5
6
7
8
9
10
6
10
4 Frequency
Interpretation: Securing data in mobile computing is necessary for business because it
assist in avoiding of data breaches, helps in maintaining the employee's and customer's record
and many others. Along with this, most of the respondents said as securing data in mobile
computing is more essential and important for business.
Question 4: Security in mobile computing
Q4) According to you, what is the security in mobile computing? Frequency
a) Protection of smartphones 8
b) Protection of portable computing devices 7
c) Protect computers for hackers 5
b) Maintain customers and employees record
c) Many others
0
1
2
3
4
5
6
7
8
9
10
6
10
4 Frequency
Interpretation: Securing data in mobile computing is necessary for business because it
assist in avoiding of data breaches, helps in maintaining the employee's and customer's record
and many others. Along with this, most of the respondents said as securing data in mobile
computing is more essential and important for business.
Question 4: Security in mobile computing
Q4) According to you, what is the security in mobile computing? Frequency
a) Protection of smartphones 8
b) Protection of portable computing devices 7
c) Protect computers for hackers 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





