The Impact of Social Media on Global Internet Censorship Practices
VerifiedAdded on 2020/04/07
|14
|3246
|63
Report
AI Summary
This report investigates the effects of social media on internet censorship, examining how social platforms influence information control and user access. The research problem focuses on the impact of internet censorship and its challenges, including the violation of users' rights, security and privacy concerns, and data breaching. The study employs a qualitative methodology, analyzing existing literature and methodologies to understand the tactics used for internet censorship, the role of social media in communication, and the rise of illegal websites. The report reviews existing methodologies, proposes a research methodology, and discusses the benefits and limitations of using surveys. The findings highlight the impact of social media on internet censorship, including the spread of false information, cyber-attacks, and the importance of data mining for security purposes. The report concludes by emphasizing the need to understand the effects of social media on internet censorship, and the need to address the challenges associated with it.

NIT 6130 Introduction to Research 1
EFFECTS OF SOCIAL MEDIA ON INTERNET CENSORSHIP
By Student’s Name
Code+ course name
Professor’s name
University name
City, State
Date
EFFECTS OF SOCIAL MEDIA ON INTERNET CENSORSHIP
By Student’s Name
Code+ course name
Professor’s name
University name
City, State
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIT 6130 Introduction to Research 2
Table of Contents
RESEARCH PROBLEM AND LITERATURE COLLECTED..................................................................3
TYPES OF METHODOLOGY...................................................................................................................5
Qualitative verses Quantitative................................................................................................................5
Chosen Methodology...............................................................................................................................6
Similarity between Qualitative and Quantitative.....................................................................................6
REVIEW OF EXISTING METHODOLOGIES..........................................................................................6
PROPOSED METHOLOGY.....................................................................................................................10
Identification and Justification...............................................................................................................10
Benefits of Survey.................................................................................................................................10
Limitations of Survey............................................................................................................................10
Framework and Explanation..................................................................................................................10
References List..........................................................................................................................................13
Table of Contents
RESEARCH PROBLEM AND LITERATURE COLLECTED..................................................................3
TYPES OF METHODOLOGY...................................................................................................................5
Qualitative verses Quantitative................................................................................................................5
Chosen Methodology...............................................................................................................................6
Similarity between Qualitative and Quantitative.....................................................................................6
REVIEW OF EXISTING METHODOLOGIES..........................................................................................6
PROPOSED METHOLOGY.....................................................................................................................10
Identification and Justification...............................................................................................................10
Benefits of Survey.................................................................................................................................10
Limitations of Survey............................................................................................................................10
Framework and Explanation..................................................................................................................10
References List..........................................................................................................................................13
NIT 6130 Introduction to Research 3
METHODOLOGY
Introduction
Research methodology is the process, procedure and principles used to identify a problem and
find a problem that will assist in finding a solution to the problem identified.
RESEARCH PROBLEM AND LITERATURE COLLECTED
RESEARCH PROBLEM SUB-PROBLEM COLLECTED LITERATURE
Problem 1
Internet censorship is one of
the major control parts in the
internet world. Different
stakeholders use internet
censorship to help them
secure their information and
data when they use the
internet. The internet provides
necessary information as well
as educating users. Despite
internet bearing many benefits
to its users, it also has
different challenges
associated to it that renders it
reliable. This study aims at
determining the different
issues related to internet
censorship in the world
(Romano, 2009).
Internet censorship as part of
the control mechanism in the
cyber world is affected by
different challenges.
Sub-problem 1
Censorship leads to users’
rights being violated. Many
networks have been banned
thus decreasing the number
of internet users. This
decreases educational
resources for students.
Sub-problem 2
Censorship leads to problem
of internet security and
privacy of information and
data. Cyber bullying is an
issue related to internet
censorship. This can harass
the user either physically or
mentally (Sina, 2014).
Sub-problem 3
Censorship has led to
information and data
resistance in the process of
transfer. In the process of
transaction, data breaching
may occur (State, 2013).
Literature tries to review what
other people did or said before.
Literature 1
MacKinnon (2010, p. 125),
gives tactics used to control
internet. This strategies include
cyber-attacks, network and
device control, control of
domain name and localized
restriction and disconnection.
This has reduced ability by users
to complain about political
issues and social problems.
Literature 2
Feng & Guo (2013, p. 234), in
their study examining control
strategies of internet censorship
in China; they identified an
online blocking system used
(Toepfl, 2011). The Chinese
government used this included
URL blocking, hijack domain
names, block main passwords
and BGP hijacking. The
government of China use
internet censorship in a
hierarchical system and internet
carried out by operators in
METHODOLOGY
Introduction
Research methodology is the process, procedure and principles used to identify a problem and
find a problem that will assist in finding a solution to the problem identified.
RESEARCH PROBLEM AND LITERATURE COLLECTED
RESEARCH PROBLEM SUB-PROBLEM COLLECTED LITERATURE
Problem 1
Internet censorship is one of
the major control parts in the
internet world. Different
stakeholders use internet
censorship to help them
secure their information and
data when they use the
internet. The internet provides
necessary information as well
as educating users. Despite
internet bearing many benefits
to its users, it also has
different challenges
associated to it that renders it
reliable. This study aims at
determining the different
issues related to internet
censorship in the world
(Romano, 2009).
Internet censorship as part of
the control mechanism in the
cyber world is affected by
different challenges.
Sub-problem 1
Censorship leads to users’
rights being violated. Many
networks have been banned
thus decreasing the number
of internet users. This
decreases educational
resources for students.
Sub-problem 2
Censorship leads to problem
of internet security and
privacy of information and
data. Cyber bullying is an
issue related to internet
censorship. This can harass
the user either physically or
mentally (Sina, 2014).
Sub-problem 3
Censorship has led to
information and data
resistance in the process of
transfer. In the process of
transaction, data breaching
may occur (State, 2013).
Literature tries to review what
other people did or said before.
Literature 1
MacKinnon (2010, p. 125),
gives tactics used to control
internet. This strategies include
cyber-attacks, network and
device control, control of
domain name and localized
restriction and disconnection.
This has reduced ability by users
to complain about political
issues and social problems.
Literature 2
Feng & Guo (2013, p. 234), in
their study examining control
strategies of internet censorship
in China; they identified an
online blocking system used
(Toepfl, 2011). The Chinese
government used this included
URL blocking, hijack domain
names, block main passwords
and BGP hijacking. The
government of China use
internet censorship in a
hierarchical system and internet
carried out by operators in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NIT 6130 Introduction to Research 4
This causes theft of property
and copy right violation
different region
Literature 3
Hearns-Branaman, (2009, p.
134), some websites give false
information to divert the views
and thoughts of common people.
The increased number of users
has increased internet
censorship. Many internet
transaction leads to data
breaching. The hacking causes
huge financial loses theft and
violation of networks and
copyright. Therefore, various
countries of various companies
have employed data mining for
security purposes.
Problem 2
The number of internet users
is growing rapidly in the day-
to-day operations. The life of
each individual has improved
due to use of internet to
provide a large amount of
information and knowledge in
different fields and social
interaction. Despite all these
benefits, different issues arise
questioning the reliability and
credibility of the use of
internet. Therefore, the
research aims at examining
internet security and effects of
social media in internet
censorship.
Sub-problem 4
Social media has enhanced
communication and
connection among millions
of persons together.
Different challenges arise
Sub-problem 5
Social media has led to
many illegal websites that
brings social harm. This
gives rise to pornographic
images and videos. Some
other websites provide
procedures of bomb making
and drug making. This
causes major harm to the
society. There is the problem
of cyber-attacks
Literature 4
In the literature of Deibert &
Rohozinski,( 2010), the
educational resources for
students has reduced the
websites used by students
provide reduced information for
information and data.
Government and other parties
are therefore responsible for
internet censorship.
Literature 5
Many studies examine the risks
of interaction between cyber-
censorship and online activism.
In the study by Leibold, (2011,
p. 126) showed a struggle
between cyber-censorship and
online activism as the evil
versus good.
This causes theft of property
and copy right violation
different region
Literature 3
Hearns-Branaman, (2009, p.
134), some websites give false
information to divert the views
and thoughts of common people.
The increased number of users
has increased internet
censorship. Many internet
transaction leads to data
breaching. The hacking causes
huge financial loses theft and
violation of networks and
copyright. Therefore, various
countries of various companies
have employed data mining for
security purposes.
Problem 2
The number of internet users
is growing rapidly in the day-
to-day operations. The life of
each individual has improved
due to use of internet to
provide a large amount of
information and knowledge in
different fields and social
interaction. Despite all these
benefits, different issues arise
questioning the reliability and
credibility of the use of
internet. Therefore, the
research aims at examining
internet security and effects of
social media in internet
censorship.
Sub-problem 4
Social media has enhanced
communication and
connection among millions
of persons together.
Different challenges arise
Sub-problem 5
Social media has led to
many illegal websites that
brings social harm. This
gives rise to pornographic
images and videos. Some
other websites provide
procedures of bomb making
and drug making. This
causes major harm to the
society. There is the problem
of cyber-attacks
Literature 4
In the literature of Deibert &
Rohozinski,( 2010), the
educational resources for
students has reduced the
websites used by students
provide reduced information for
information and data.
Government and other parties
are therefore responsible for
internet censorship.
Literature 5
Many studies examine the risks
of interaction between cyber-
censorship and online activism.
In the study by Leibold, (2011,
p. 126) showed a struggle
between cyber-censorship and
online activism as the evil
versus good.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIT 6130 Introduction to Research 5
The study by MacKinnon ,
(2010, p. 126) analyzed the
public discourse on online
activism and censorship in
China. He noted that single,
open and free internet brings
democracy and freedom.
China’s network
authoritarianism is the main
control feature.
TYPES OF METHODOLOGY
Research involves different types depending on methodology of research used, knowledge, user
group and the type of problem investigated. This gives rise to the different types of methodology
identified as qualitative, quantitative, basic, applied and problem-oriented and Problem solving.
Qualitative and quantitative forms our major concern (Brennen, 2013, p. 26).
Qualitative verses Quantitative
Quantitative method
Quantitative methodology puts emphasis on numbers or numeric figures. This method aim to
measure the amount or quantity compares past records and project the future. It also refers to
systematic investigation of the phenomena and quantitative properties as well as their
relationships. Its goal is to employ and develop mathematical theories, hypothesis and models of
the phenomena.it gives an important connection between mathematical expression and empirical
observation to quantitative relationships. Here, statistical methods are used and in the field of
commerce and economics (Merriam, 1998, p. 67).
The study by MacKinnon ,
(2010, p. 126) analyzed the
public discourse on online
activism and censorship in
China. He noted that single,
open and free internet brings
democracy and freedom.
China’s network
authoritarianism is the main
control feature.
TYPES OF METHODOLOGY
Research involves different types depending on methodology of research used, knowledge, user
group and the type of problem investigated. This gives rise to the different types of methodology
identified as qualitative, quantitative, basic, applied and problem-oriented and Problem solving.
Qualitative and quantitative forms our major concern (Brennen, 2013, p. 26).
Qualitative verses Quantitative
Quantitative method
Quantitative methodology puts emphasis on numbers or numeric figures. This method aim to
measure the amount or quantity compares past records and project the future. It also refers to
systematic investigation of the phenomena and quantitative properties as well as their
relationships. Its goal is to employ and develop mathematical theories, hypothesis and models of
the phenomena.it gives an important connection between mathematical expression and empirical
observation to quantitative relationships. Here, statistical methods are used and in the field of
commerce and economics (Merriam, 1998, p. 67).

NIT 6130 Introduction to Research 6
Qualitative method
This method provides a non-quantitative analysis. This method collects, analyses, and interprets
data through observation of what people say and do. It also involves meanings, characteristics,
definitions, symbols, description and metaphors of things. It is subjective and use various ways
of collecting data and information e.g. focus groups and in-depth interviews. This type of
methodology is open-ended and exploratory.
Chosen Methodology
In this study I, will use qualitative method because it will help me collect, analyze and interpret
data through observation of what people say and do. In addition, it is open and exploratory to
provide me an opportunity to use various methods to collect data and information e.g. Focus
groups and in-depth interviews to get and understand more information.
Similarity between Qualitative and Quantitative
Both quantitative and qualitative methods are that the use observations in order to collect
data of what participant do.
Both qualitative and quantitative methods compares past records and predicts for future
happenings.
Qualitative method
This method provides a non-quantitative analysis. This method collects, analyses, and interprets
data through observation of what people say and do. It also involves meanings, characteristics,
definitions, symbols, description and metaphors of things. It is subjective and use various ways
of collecting data and information e.g. focus groups and in-depth interviews. This type of
methodology is open-ended and exploratory.
Chosen Methodology
In this study I, will use qualitative method because it will help me collect, analyze and interpret
data through observation of what people say and do. In addition, it is open and exploratory to
provide me an opportunity to use various methods to collect data and information e.g. Focus
groups and in-depth interviews to get and understand more information.
Similarity between Qualitative and Quantitative
Both quantitative and qualitative methods are that the use observations in order to collect
data of what participant do.
Both qualitative and quantitative methods compares past records and predicts for future
happenings.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NIT 6130 Introduction to Research 7
REVIEW OF EXISTING METHODOLOGIES
Literature tries to review what other people did or said before
LITERATURE RESEARCH
PROBLEM
METHODOLOGY YOUR SUB-
PROBLEM
RELEVANCE
Literature 1
MacKinnon ,
(2010, p. 125),
gives tactics
used to control
internet. This
strategies include
cyber-attacks,
network and
device control,
control of
domain name
and localized
restriction and
disconnection.
This has reduced
ability by users
to complain
about political
issues and social
problems.
Literature 2
According to
Feng & Guo,
(2013, p. 234), in
their study
examining
control strategies
of internet
censorship in
China, they
identified an
online blocking
system used. The
Problem1
Internet in China
has appositive
impact on politics
and individual
growth. Despite
media growth and
commercialization,
internet remains
under government
control.
Problem 2
Continuous use of
internet leads to
lack of internet
security and
privacy of
information and
data. In addition,
cyber bullying is
another challenge.
Method 1
The methodology
used was qualitative
to enable researcher
collect, analyze and
interpret data and
information
collected (Alexa,
2014).
Method 2
Empirical study was
used to determine
the control strategy
used by China.
Sub problem
Social media
has led to
many illegal
websites that
brings social
harm. This
gives rise to
pornographic
images and
videos. Some
other
websites
provide
procedures of
bomb making
and drug
making. This
causes major
harm to the
society.
There is the
problem of
cyber-attacks
Relevance 1
The study has
helped me
determine the
tactics that a
country may
employ in order
to reduce the
number of
internet users
who violate the
rights and
copyrights of
others.
Relevance 2
Since the
internet use has
many
challenges, the
review on the
study of control
mechanism will
assist me in
determining the
strategies used
to control
insecurities in
REVIEW OF EXISTING METHODOLOGIES
Literature tries to review what other people did or said before
LITERATURE RESEARCH
PROBLEM
METHODOLOGY YOUR SUB-
PROBLEM
RELEVANCE
Literature 1
MacKinnon ,
(2010, p. 125),
gives tactics
used to control
internet. This
strategies include
cyber-attacks,
network and
device control,
control of
domain name
and localized
restriction and
disconnection.
This has reduced
ability by users
to complain
about political
issues and social
problems.
Literature 2
According to
Feng & Guo,
(2013, p. 234), in
their study
examining
control strategies
of internet
censorship in
China, they
identified an
online blocking
system used. The
Problem1
Internet in China
has appositive
impact on politics
and individual
growth. Despite
media growth and
commercialization,
internet remains
under government
control.
Problem 2
Continuous use of
internet leads to
lack of internet
security and
privacy of
information and
data. In addition,
cyber bullying is
another challenge.
Method 1
The methodology
used was qualitative
to enable researcher
collect, analyze and
interpret data and
information
collected (Alexa,
2014).
Method 2
Empirical study was
used to determine
the control strategy
used by China.
Sub problem
Social media
has led to
many illegal
websites that
brings social
harm. This
gives rise to
pornographic
images and
videos. Some
other
websites
provide
procedures of
bomb making
and drug
making. This
causes major
harm to the
society.
There is the
problem of
cyber-attacks
Relevance 1
The study has
helped me
determine the
tactics that a
country may
employ in order
to reduce the
number of
internet users
who violate the
rights and
copyrights of
others.
Relevance 2
Since the
internet use has
many
challenges, the
review on the
study of control
mechanism will
assist me in
determining the
strategies used
to control
insecurities in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NIT 6130 Introduction to Research 8
Chinese
government used
this included
URL blocking,
hijack domain
names, block
main passwords
and BGP
hijacking (BBC,
2010). The
government of
China use
internet
censorship in a
hierarchical
system and
internet carried
out by operators
in different
region.
Literature 3
From Hearns-
Branaman,
(2009, p. 134),
some websites
give false
information to
divert the views
and thoughts of
common people.
The increased
number of users
has increased
internet
censorship.
Many internet
transaction leads
to data
breaching. The
Problem3
Data breaching
and illegal
websites.
Method3
The exploratory and
quantitative study
was used to
determine the
number of financial
transactions and
financial loses that
accrue from use of
the internet and
ways to
improve
privacy.
Relevance 3
Having the idea
of false
information and
data breaching
over the
internet, this
will enable the
users of the
internet to be
careful on the
type of
information to
share as well as
knowing the
importance of
data mining in
securing data.
Chinese
government used
this included
URL blocking,
hijack domain
names, block
main passwords
and BGP
hijacking (BBC,
2010). The
government of
China use
internet
censorship in a
hierarchical
system and
internet carried
out by operators
in different
region.
Literature 3
From Hearns-
Branaman,
(2009, p. 134),
some websites
give false
information to
divert the views
and thoughts of
common people.
The increased
number of users
has increased
internet
censorship.
Many internet
transaction leads
to data
breaching. The
Problem3
Data breaching
and illegal
websites.
Method3
The exploratory and
quantitative study
was used to
determine the
number of financial
transactions and
financial loses that
accrue from use of
the internet and
ways to
improve
privacy.
Relevance 3
Having the idea
of false
information and
data breaching
over the
internet, this
will enable the
users of the
internet to be
careful on the
type of
information to
share as well as
knowing the
importance of
data mining in
securing data.
NIT 6130 Introduction to Research 9
hacking causes
huge financial
loses theft and
violation of
networks and
copyright.
Therefore,
various countries
of various
companies have
employed data
mining for
security
purposes.
internet.
Literature 4
In the study
Deibert &
Rohozinski,
(2010), content
rating system,
the educational
resources for
students has
reduced the
websites used by
students provide
reduced
information for
information and
data.
Government and
other parties are
therefore
Problem 4
Education and
internet
Method 4
Quantitative study to
examine the
percentage of
information that has
reduced from the
internet as well as
the number of
students affected
Relevance 4
Reviewing the
literature will
help me to
suggest more
educational
resources for
students. In
addition, it will
assist the
students to
concentrate in
their studies.
hacking causes
huge financial
loses theft and
violation of
networks and
copyright.
Therefore,
various countries
of various
companies have
employed data
mining for
security
purposes.
internet.
Literature 4
In the study
Deibert &
Rohozinski,
(2010), content
rating system,
the educational
resources for
students has
reduced the
websites used by
students provide
reduced
information for
information and
data.
Government and
other parties are
therefore
Problem 4
Education and
internet
Method 4
Quantitative study to
examine the
percentage of
information that has
reduced from the
internet as well as
the number of
students affected
Relevance 4
Reviewing the
literature will
help me to
suggest more
educational
resources for
students. In
addition, it will
assist the
students to
concentrate in
their studies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NIT 6130 Introduction to Research 10
responsible for
internet
censorship.
PROPOSED METHOLOGY
Identification and Justification
Based on the existing research methodologies I will propose Survey as a method of data
collection. This is because developing it is easy by use of survey software. Survey can be in
form of online, mobile, paper survey or any of the combination. It allows a wide coverage.
Benefits of Survey
It is easily administered.
Compared to various methods, survey is developed within short period.
Cost effective depending on the mode of survey
Survey can be used in the remote areas through mobile, online, email and telephone.
Survey is used to collect information for a large group.
Advanced statistical tool, survey software are used to analyze data in order to determine
reliability and validity of variables
Limitations of Survey
Respondents may give inaccurate and false information.
Participants may feel uncomfortable to give information in an unfavorable manner.
A closed-ended survey is less valid compared to other questions.
responsible for
internet
censorship.
PROPOSED METHOLOGY
Identification and Justification
Based on the existing research methodologies I will propose Survey as a method of data
collection. This is because developing it is easy by use of survey software. Survey can be in
form of online, mobile, paper survey or any of the combination. It allows a wide coverage.
Benefits of Survey
It is easily administered.
Compared to various methods, survey is developed within short period.
Cost effective depending on the mode of survey
Survey can be used in the remote areas through mobile, online, email and telephone.
Survey is used to collect information for a large group.
Advanced statistical tool, survey software are used to analyze data in order to determine
reliability and validity of variables
Limitations of Survey
Respondents may give inaccurate and false information.
Participants may feel uncomfortable to give information in an unfavorable manner.
A closed-ended survey is less valid compared to other questions.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NIT 6130 Introduction to Research 11
Presence of data errors due to lack of reference (Brennen, 2013, p. 70).
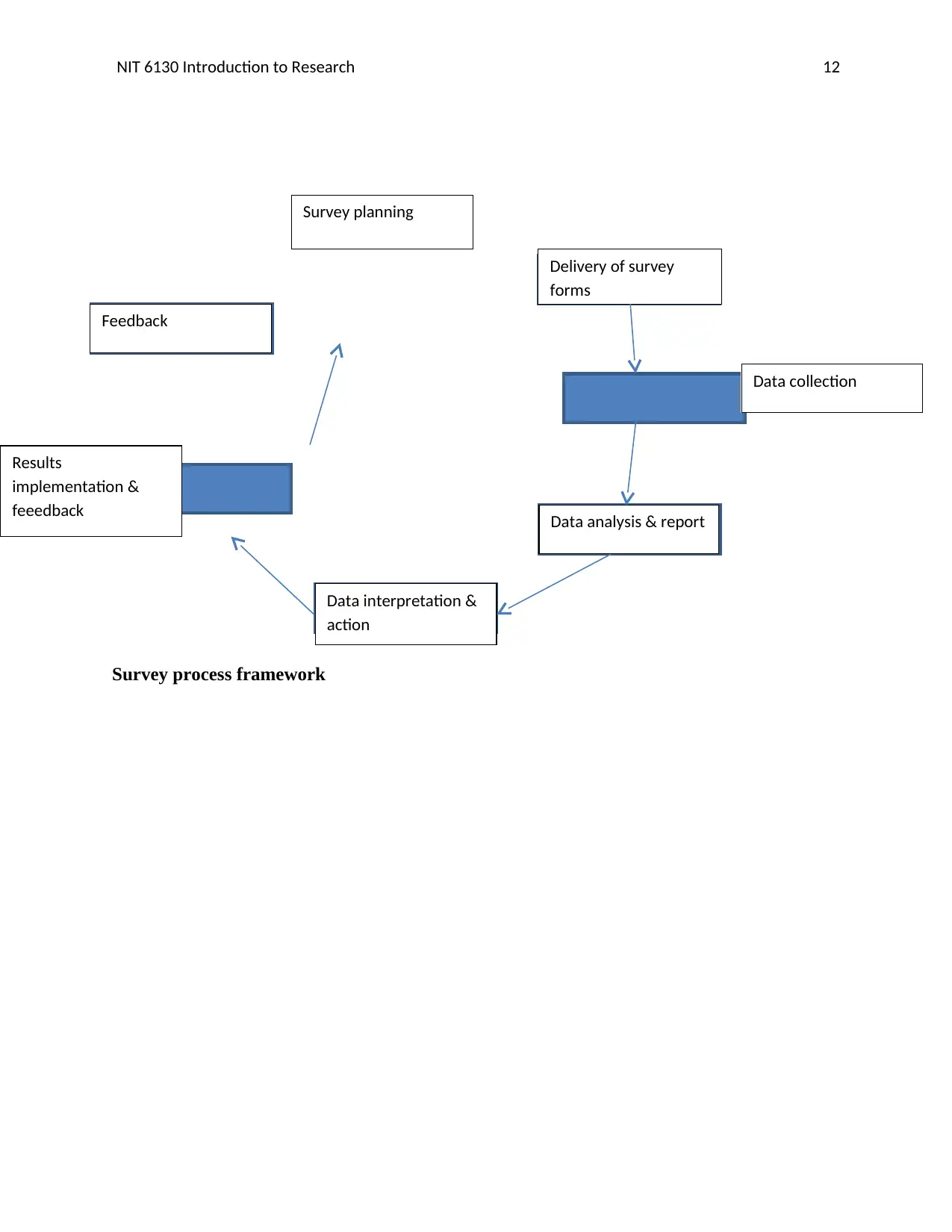
Framework and Explanation
Planning of the survey
This is the initial stage of survey and begins with plans on who to participate, which
mode to use, where to go and how results will be analyzed.
Delivery of Survey Form
The surveyor delivers the survey form to the participants for the response about the research
topic.
Data Collection and promotion of survey
The researcher collects data and information to be used for analysis.
Data Analysis & Results Report
Data is analyzed and a full report generated for further implementation.
Interpretation and Action.
The results and findings are interpreted so that future actions are planned.
Implementation & Monitoring
The actions are implemented a monitoring takes place to identify the successes and challenges
for feedback.
Feedback & Promotion of Feedback.
The feedback is sent back on challenges and achievements for further recommendations and
solutions.
Presence of data errors due to lack of reference (Brennen, 2013, p. 70).
Framework and Explanation
Planning of the survey
This is the initial stage of survey and begins with plans on who to participate, which
mode to use, where to go and how results will be analyzed.
Delivery of Survey Form
The surveyor delivers the survey form to the participants for the response about the research
topic.
Data Collection and promotion of survey
The researcher collects data and information to be used for analysis.
Data Analysis & Results Report
Data is analyzed and a full report generated for further implementation.
Interpretation and Action.
The results and findings are interpreted so that future actions are planned.
Implementation & Monitoring
The actions are implemented a monitoring takes place to identify the successes and challenges
for feedback.
Feedback & Promotion of Feedback.
The feedback is sent back on challenges and achievements for further recommendations and
solutions.
NIT 6130 Introduction to Research 12
Survey process framework
Survey planning
Delivery of survey
forms
Feedback
Data collection
Results
implementation &
feeedback Data analysis & report
Data interpretation &
action
Survey process framework
Survey planning
Delivery of survey
forms
Feedback
Data collection
Results
implementation &
feeedback Data analysis & report
Data interpretation &
action
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





