Wireless Network Assignment: Modulation, CRC, Modes, and OSI/TCP
VerifiedAdded on 2022/10/19
|11
|1163
|13
Homework Assignment
AI Summary
This assignment solution addresses various aspects of wireless networks, including modulation techniques such as ASK, FSK, PSK, and QAM, alongside the computation of frequency assignments for different bit combinations. It also delves into the Cyclic Redundancy Check (CRC) error detection process and its implementation. Furthermore, the solution explores Direct Sequence Spread Spectrum, compares Infrastructure and Ad Hoc modes in WLAN, and contrasts the OSI and TCP/IP models. The assignment encompasses detailed calculations, waveform drawings, and explanations of key concepts in wireless communication, providing a comprehensive understanding of the subject matter. The solution includes all the required diagrams and calculations for each question in the assignment brief.

WIRELESS NETWORK
STUDENT NAME
COLLEGE
STUDENT NAME
COLLEGE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
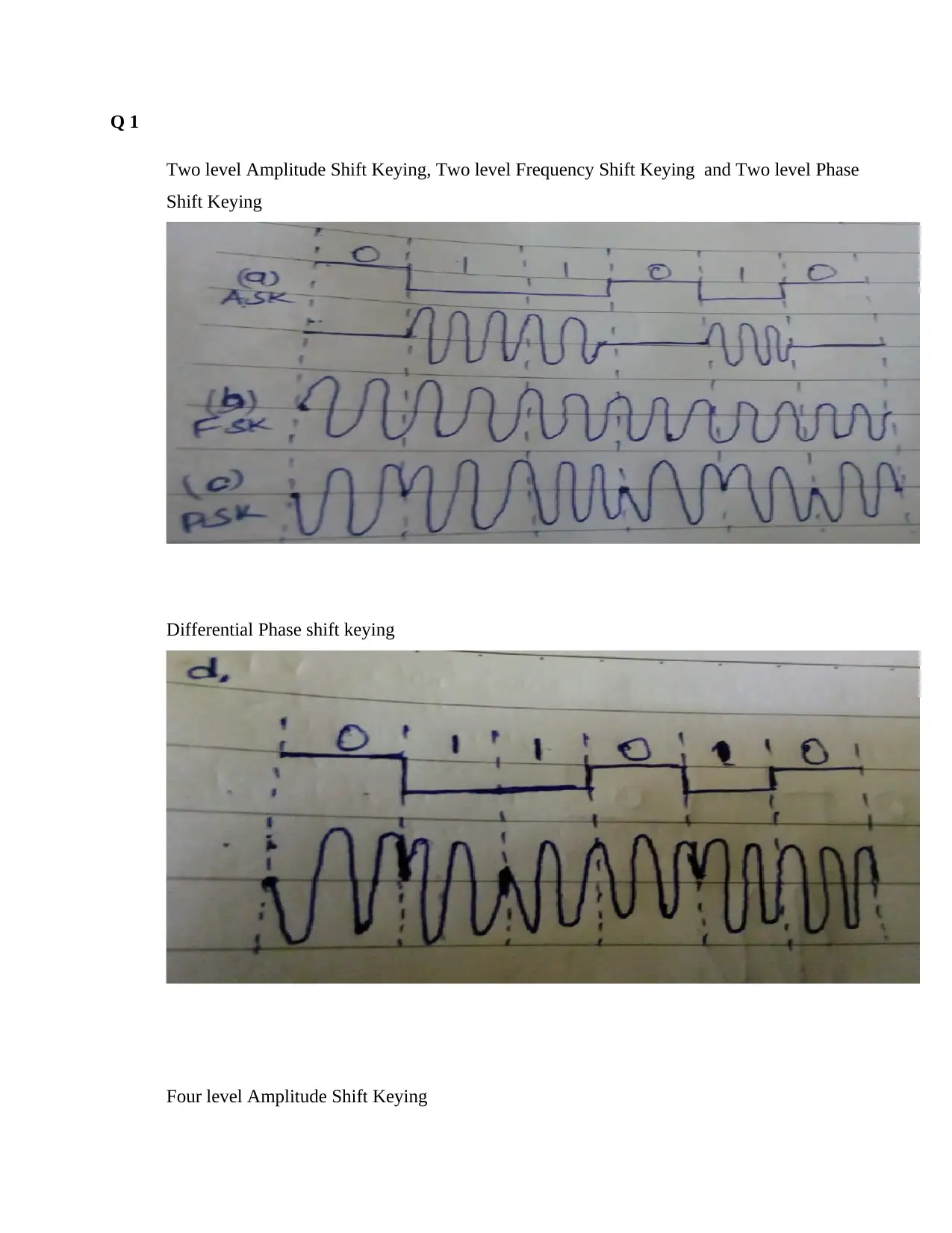
Q 1
Two level Amplitude Shift Keying, Two level Frequency Shift Keying and Two level Phase
Shift Keying
Differential Phase shift keying
Four level Amplitude Shift Keying
Two level Amplitude Shift Keying, Two level Frequency Shift Keying and Two level Phase
Shift Keying
Differential Phase shift keying
Four level Amplitude Shift Keying

Four level Phase Shift Keying and Eight level Amplitude Shift Keying
Q 2
Fi= fc+ (2i -1-M)fd
F1= 125 kHz 0000
F2= 175 kHz 0001
F3= 225 kHz 0011
F4=275 kHz 0111
F5=325 kHz 1000
F6=375 kHz 1100
F7=425 kHz 0100
F8=475 kHz 0110
Q 2
Fi= fc+ (2i -1-M)fd
F1= 125 kHz 0000
F2= 175 kHz 0001
F3= 225 kHz 0011
F4=275 kHz 0111
F5=325 kHz 1000
F6=375 kHz 1100
F7=425 kHz 0100
F8=475 kHz 0110
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
F9=525 kHz 0101
F10=575 kHz 1010
F11=625 kHz 0010
F12=675 kHz 1001
F13=725 kHz 1011
F14=775 kHz 1101
F15=825 kHz 1110
F16=875 kHz 1111
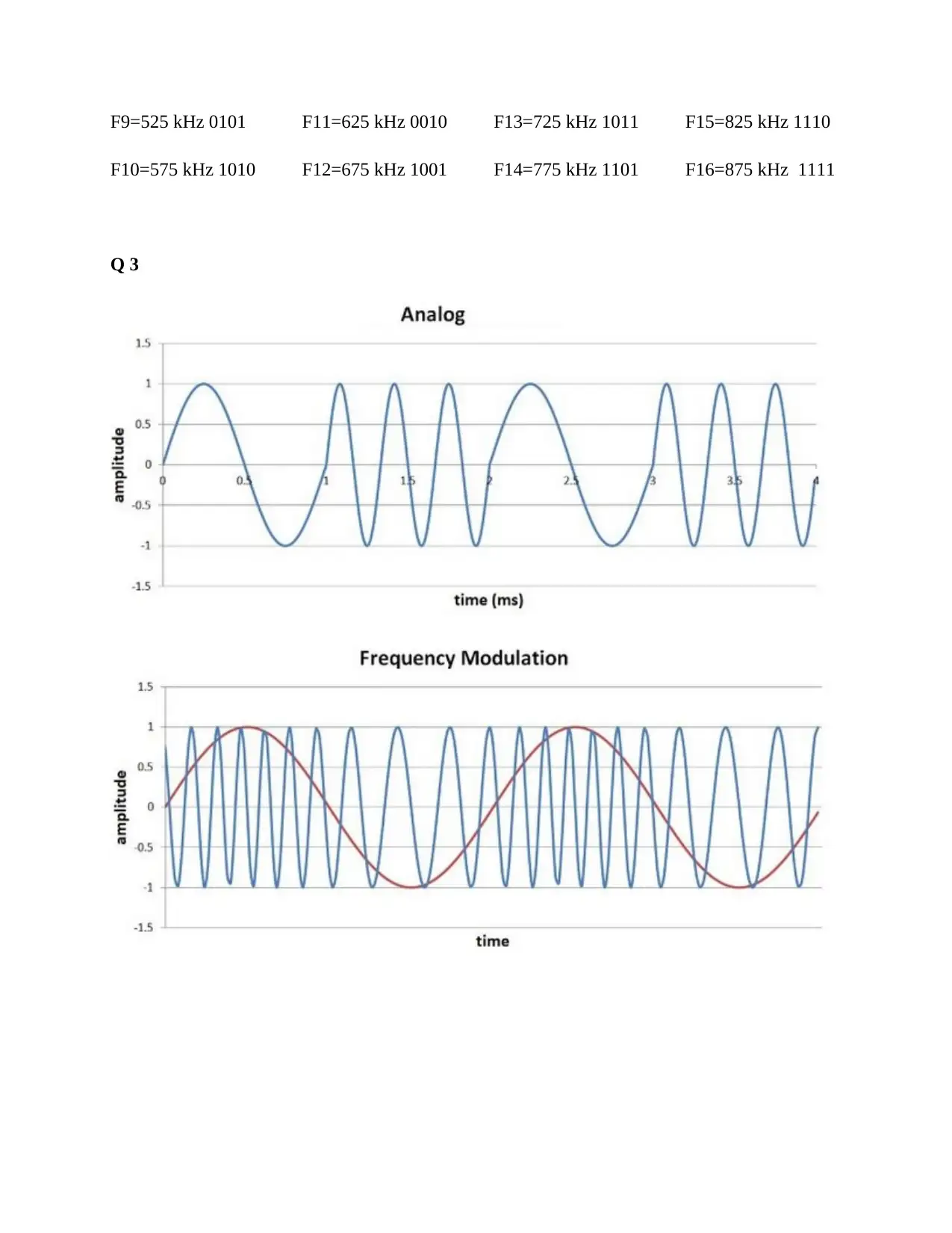
Q 3
F10=575 kHz 1010
F11=625 kHz 0010
F12=675 kHz 1001
F13=725 kHz 1011
F14=775 kHz 1101
F15=825 kHz 1110
F16=875 kHz 1111
Q 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
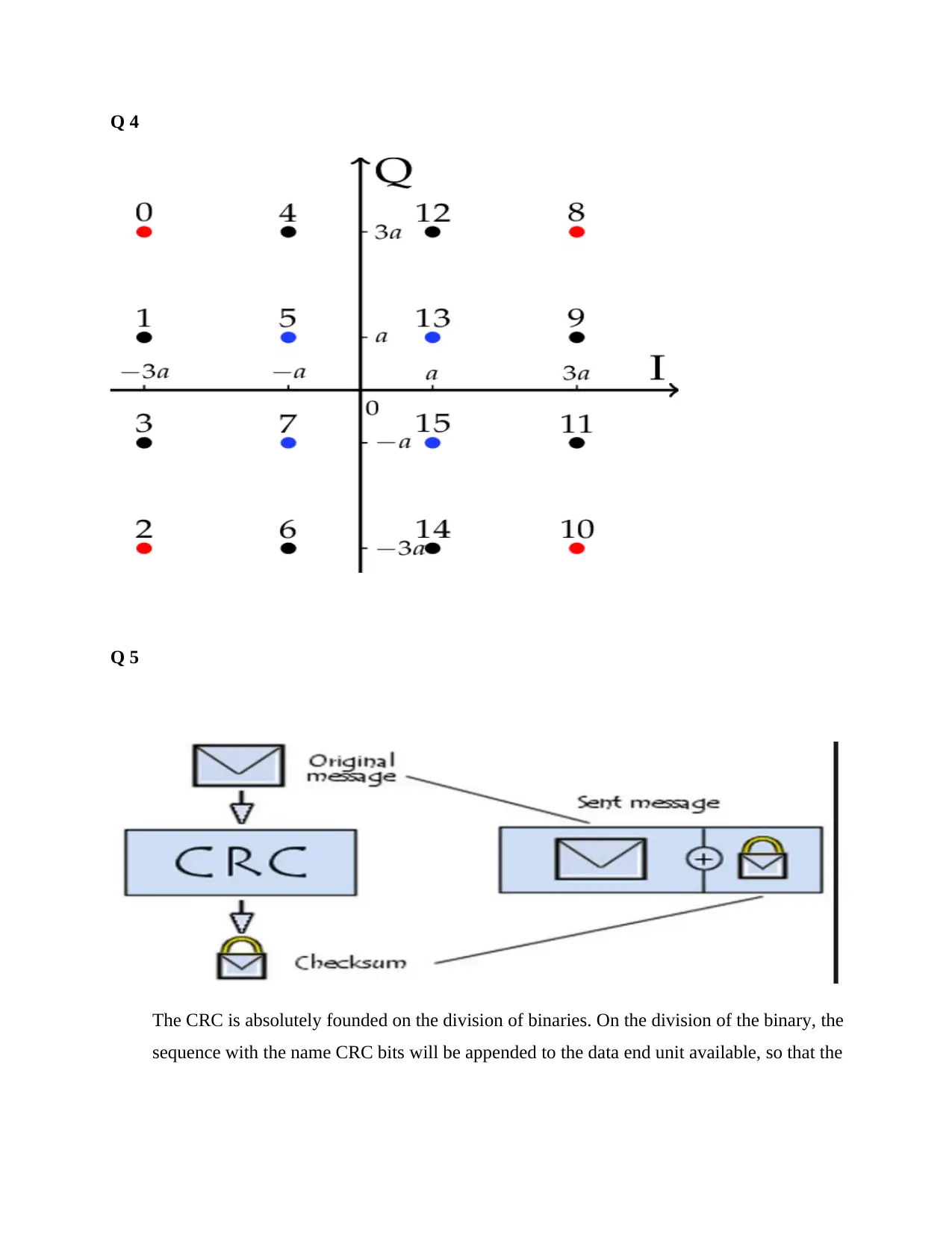
Q 4
Q 5
The CRC is absolutely founded on the division of binaries. On the division of the binary, the
sequence with the name CRC bits will be appended to the data end unit available, so that the
Q 5
The CRC is absolutely founded on the division of binaries. On the division of the binary, the
sequence with the name CRC bits will be appended to the data end unit available, so that the

outcome of the data unit can be as more accurate as possible on its divisibility by a second
which in this case is a binary number which is pre-determined.
The unit data which is coming will then by divided with a second at the very destination. In
this case, if the remainder does not appear or remain, then the data unit will be regarded as
correct data then it will be accepted. The existence of a remainder indicates that the data which
was being transmitted is damaged and therefore it will be rejected as damaged data.
Q 6
d(t) 1 1 0 1 1
x(t): +1 + 1 - 1 + 1 +1
c(t): 1 0 1 1 1 1 0 0
g(t): +1 -1 +1 +1 +1 +1 -1 -1 +1
Spread sequence, p(t) = x(t)g(t):
x(t): +1 +1 +1 +1 +1 +1 -1 -1 -1 +1 +1 +1
g(t): +1 + 1 -1 +1 -1 -1 +1 +1 +1 -1 -1 +1
p(t): +1 - 1 -1 +1 +1 -1 -1 -1 -1 -1 -1 +1
The sequence is 100110000001
Q 7
d(t) 1 0 1 1
x(t): +1 - 1 + 1 +1
c(t): 1 0 1 0 1 1 0 1 1 0 1 0
g(t): +1 -1 +1 -1 +1 +1 -1 +1 +1 -1 + 1 -1
which in this case is a binary number which is pre-determined.
The unit data which is coming will then by divided with a second at the very destination. In
this case, if the remainder does not appear or remain, then the data unit will be regarded as
correct data then it will be accepted. The existence of a remainder indicates that the data which
was being transmitted is damaged and therefore it will be rejected as damaged data.
Q 6
d(t) 1 1 0 1 1
x(t): +1 + 1 - 1 + 1 +1
c(t): 1 0 1 1 1 1 0 0
g(t): +1 -1 +1 +1 +1 +1 -1 -1 +1
Spread sequence, p(t) = x(t)g(t):
x(t): +1 +1 +1 +1 +1 +1 -1 -1 -1 +1 +1 +1
g(t): +1 + 1 -1 +1 -1 -1 +1 +1 +1 -1 -1 +1
p(t): +1 - 1 -1 +1 +1 -1 -1 -1 -1 -1 -1 +1
The sequence is 100110000001
Q 7
d(t) 1 0 1 1
x(t): +1 - 1 + 1 +1
c(t): 1 0 1 0 1 1 0 1 1 0 1 0
g(t): +1 -1 +1 -1 +1 +1 -1 +1 +1 -1 + 1 -1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
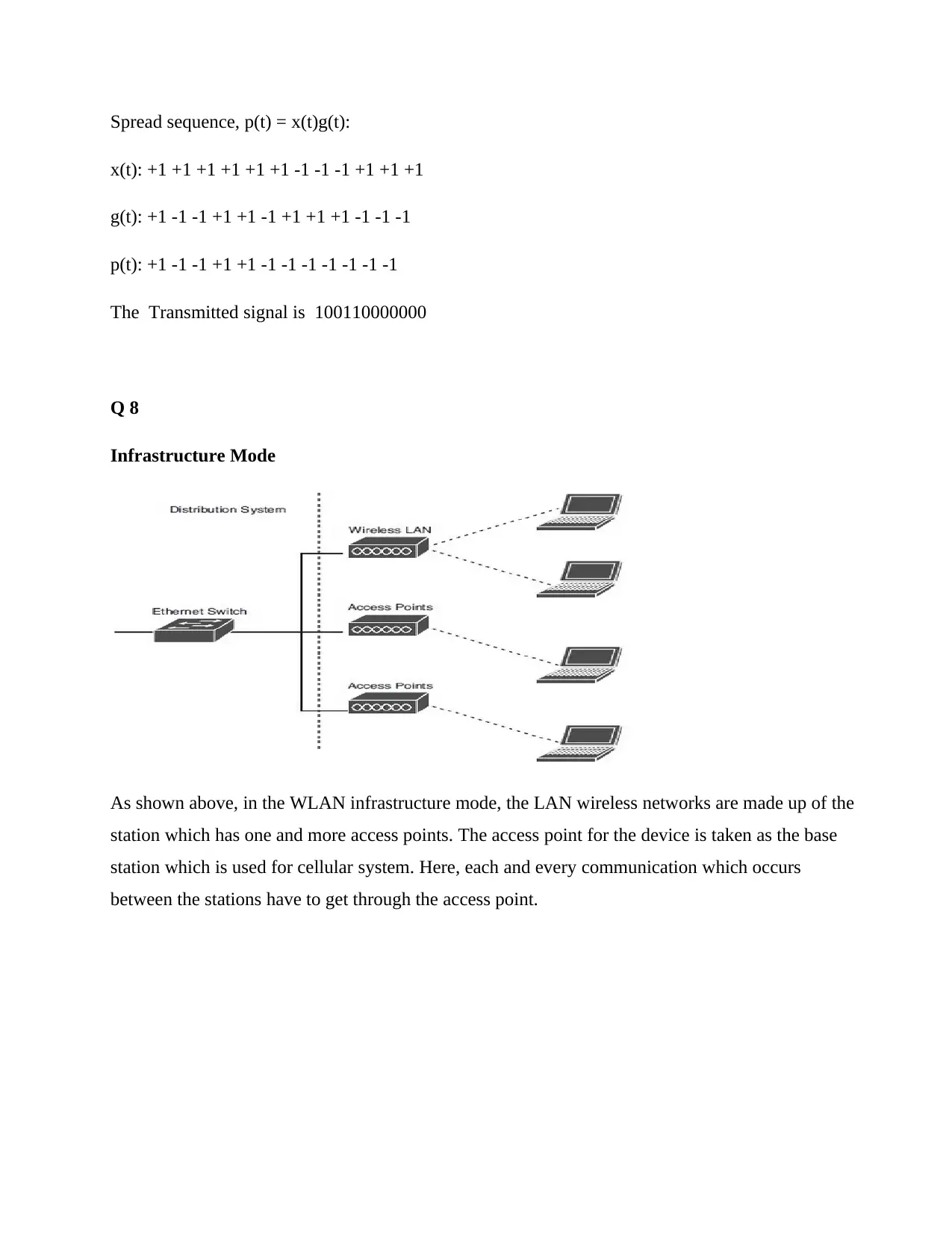
Spread sequence, p(t) = x(t)g(t):
x(t): +1 +1 +1 +1 +1 +1 -1 -1 -1 +1 +1 +1
g(t): +1 -1 -1 +1 +1 -1 +1 +1 +1 -1 -1 -1
p(t): +1 -1 -1 +1 +1 -1 -1 -1 -1 -1 -1 -1
The Transmitted signal is 100110000000
Q 8
Infrastructure Mode
As shown above, in the WLAN infrastructure mode, the LAN wireless networks are made up of the
station which has one and more access points. The access point for the device is taken as the base
station which is used for cellular system. Here, each and every communication which occurs
between the stations have to get through the access point.
x(t): +1 +1 +1 +1 +1 +1 -1 -1 -1 +1 +1 +1
g(t): +1 -1 -1 +1 +1 -1 +1 +1 +1 -1 -1 -1
p(t): +1 -1 -1 +1 +1 -1 -1 -1 -1 -1 -1 -1
The Transmitted signal is 100110000000
Q 8
Infrastructure Mode
As shown above, in the WLAN infrastructure mode, the LAN wireless networks are made up of the
station which has one and more access points. The access point for the device is taken as the base
station which is used for cellular system. Here, each and every communication which occurs
between the stations have to get through the access point.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
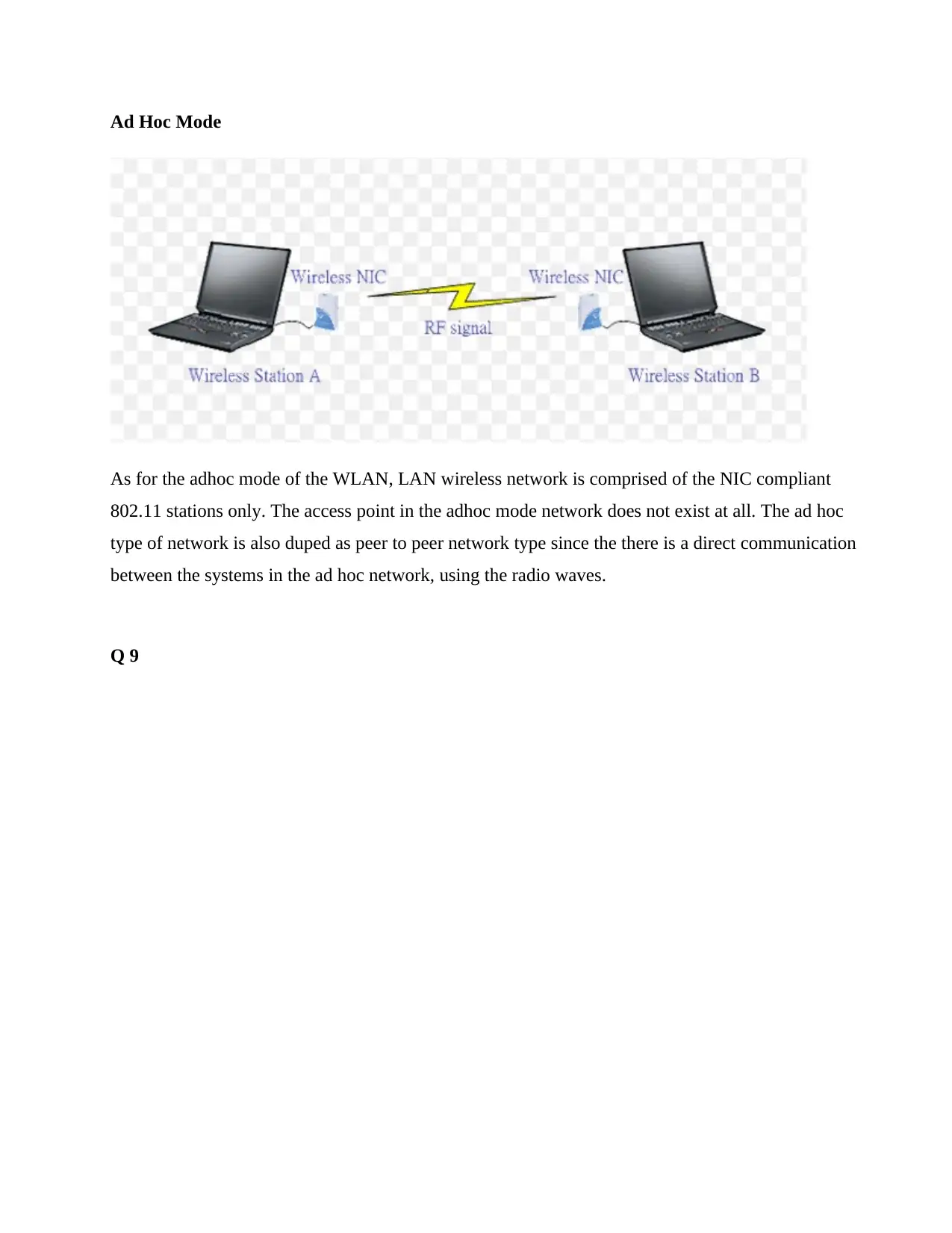
Ad Hoc Mode
As for the adhoc mode of the WLAN, LAN wireless network is comprised of the NIC compliant
802.11 stations only. The access point in the adhoc mode network does not exist at all. The ad hoc
type of network is also duped as peer to peer network type since the there is a direct communication
between the systems in the ad hoc network, using the radio waves.
Q 9
As for the adhoc mode of the WLAN, LAN wireless network is comprised of the NIC compliant
802.11 stations only. The access point in the adhoc mode network does not exist at all. The ad hoc
type of network is also duped as peer to peer network type since the there is a direct communication
between the systems in the ad hoc network, using the radio waves.
Q 9
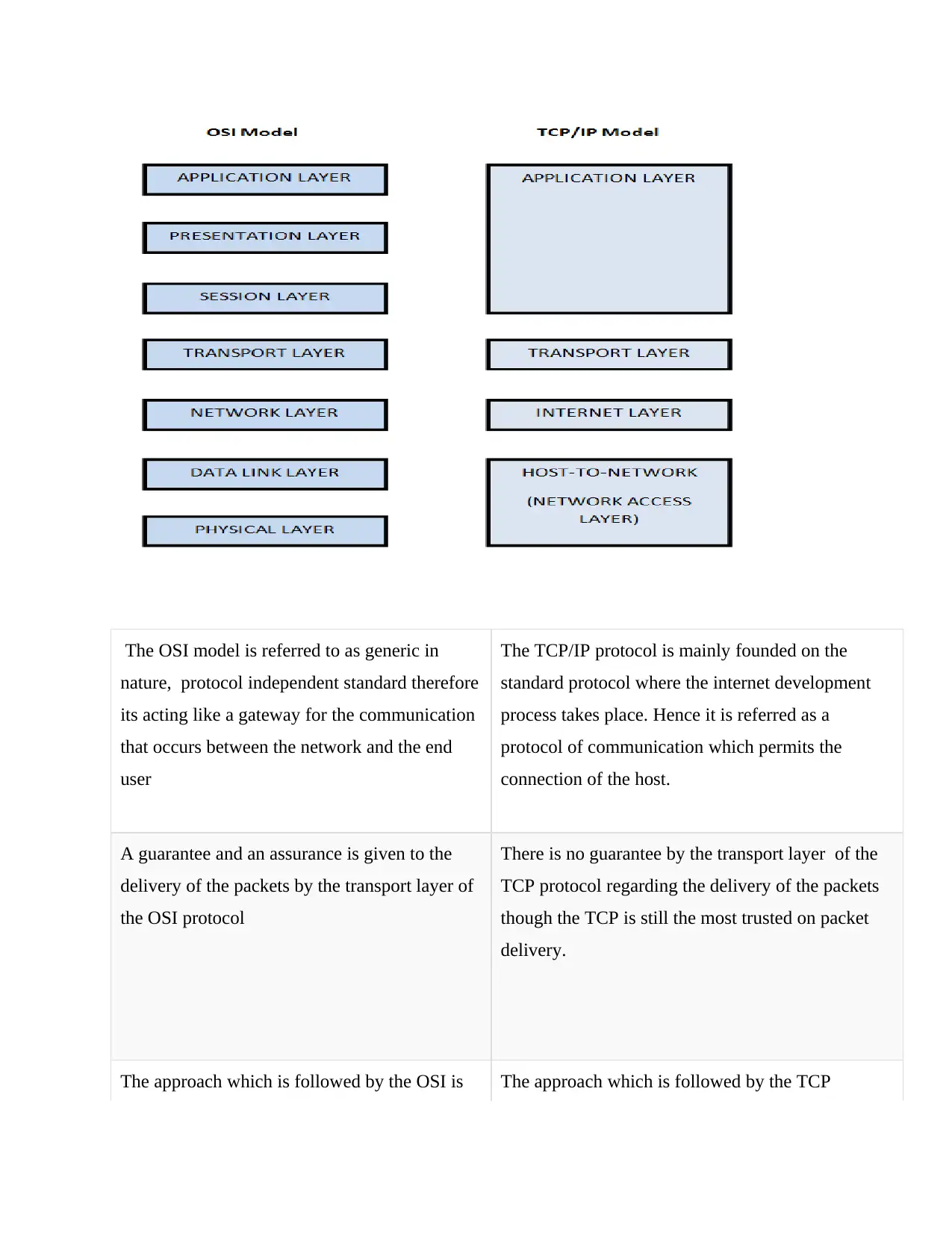
The OSI model is referred to as generic in
nature, protocol independent standard therefore
its acting like a gateway for the communication
that occurs between the network and the end
user
The TCP/IP protocol is mainly founded on the
standard protocol where the internet development
process takes place. Hence it is referred as a
protocol of communication which permits the
connection of the host.
A guarantee and an assurance is given to the
delivery of the packets by the transport layer of
the OSI protocol
There is no guarantee by the transport layer of the
TCP protocol regarding the delivery of the packets
though the TCP is still the most trusted on packet
delivery.
The approach which is followed by the OSI is The approach which is followed by the TCP
nature, protocol independent standard therefore
its acting like a gateway for the communication
that occurs between the network and the end
user
The TCP/IP protocol is mainly founded on the
standard protocol where the internet development
process takes place. Hence it is referred as a
protocol of communication which permits the
connection of the host.
A guarantee and an assurance is given to the
delivery of the packets by the transport layer of
the OSI protocol
There is no guarantee by the transport layer of the
TCP protocol regarding the delivery of the packets
though the TCP is still the most trusted on packet
delivery.
The approach which is followed by the OSI is The approach which is followed by the TCP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the vertical approach protocol is the horizontal approach.
The OSI protocol is made up of the separated
presentation and the session layer as shown in
the diagram above.
The TCP protocol only has presentation layer joined
with the session layer as shown above.
The OSI model protocol has its Transport
Layer being Connection Oriented
The Transport Layer of the TCP protocol is both
Connection less and also Connection oriented.
Q 10
The preference of the cells with hexagonal shapes is much more as compared to the preference of
the circular cell shapes and the square cell shapes because of the following important and crucial
reason
The surface area of the cells with the hexagonal shapes are much larger as compared to the
cells with their shapes in circle and squares. Therefore, for the hexagonal cells, the number
of the cells which are needed to cover a particular larger geographical area is smaller as
compared when using the circle shape cell and the square shape cells.
The cells with hexagonal shapes also, approximates closely the radiation circular pattern
which is currently used by the omni- directional antennas which are found on the base station
like the transmitters. The square and the circular shape cells are not used since they leave
gaps in between them if they are implemented.
Bibliography
Anon, (n.d.). Industrial Wireless Networks | Emerson US. [online] Available at:
https://www.emerson.com/en-us/automation/measurement-instrumentation/wireless-infrastructure/
wireless-networks [Accessed 24 May 2019].
Anon, (n.d.). Performance of Wireless Networks: Introduction to Wireless .... [online] Available at:
https://hpbn.co/introduction-to-wireless-networks/ [Accessed 24 May 2019].
The OSI protocol is made up of the separated
presentation and the session layer as shown in
the diagram above.
The TCP protocol only has presentation layer joined
with the session layer as shown above.
The OSI model protocol has its Transport
Layer being Connection Oriented
The Transport Layer of the TCP protocol is both
Connection less and also Connection oriented.
Q 10
The preference of the cells with hexagonal shapes is much more as compared to the preference of
the circular cell shapes and the square cell shapes because of the following important and crucial
reason
The surface area of the cells with the hexagonal shapes are much larger as compared to the
cells with their shapes in circle and squares. Therefore, for the hexagonal cells, the number
of the cells which are needed to cover a particular larger geographical area is smaller as
compared when using the circle shape cell and the square shape cells.
The cells with hexagonal shapes also, approximates closely the radiation circular pattern
which is currently used by the omni- directional antennas which are found on the base station
like the transmitters. The square and the circular shape cells are not used since they leave
gaps in between them if they are implemented.
Bibliography
Anon, (n.d.). Industrial Wireless Networks | Emerson US. [online] Available at:
https://www.emerson.com/en-us/automation/measurement-instrumentation/wireless-infrastructure/
wireless-networks [Accessed 24 May 2019].
Anon, (n.d.). Performance of Wireless Networks: Introduction to Wireless .... [online] Available at:
https://hpbn.co/introduction-to-wireless-networks/ [Accessed 24 May 2019].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Anon, (n.d.). Types of Wireless Network Explained with Standards. [online] Available at:
https://www.computernetworkingnotes.com/ccna-study-guide/types-of-wireless-network-explained-
with-standards.html [Accessed 24 May 2019].
Anon, (n.d.). Wi-Fi & Networking - Best Buy. [online] Available at:
https://www.bestbuy.com/site/computers-pcs/networking/abcat0503000.c?id=abcat0503000
[Accessed 24 May 2019].
Anon, (n.d.). Wireless Networks - ece.rutgers.edu. [online] Available at:
https://www.ece.rutgers.edu/~marsic/books/WN/book-WN_marsic.pdf [Accessed 24 May 2019].
https://www.computernetworkingnotes.com/ccna-study-guide/types-of-wireless-network-explained-
with-standards.html [Accessed 24 May 2019].
Anon, (n.d.). Wi-Fi & Networking - Best Buy. [online] Available at:
https://www.bestbuy.com/site/computers-pcs/networking/abcat0503000.c?id=abcat0503000
[Accessed 24 May 2019].
Anon, (n.d.). Wireless Networks - ece.rutgers.edu. [online] Available at:
https://www.ece.rutgers.edu/~marsic/books/WN/book-WN_marsic.pdf [Accessed 24 May 2019].
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





