Report on the Design of a Network: Academic Year 2019-20
VerifiedAdded on 2022/09/09
|12
|1621
|19
Report
AI Summary
This report provides a comprehensive overview of network design, focusing on the architecture for a company with specific floor-level requirements, including wired and wireless connections, servers, and firewalls. The design incorporates structured cabling, VLANs, and IP addressing (172.20.0.0/16). The report details the use of various network protocols, including default, static, and dynamic routing, as well as DNS, SMTP, and FTP. It also addresses security considerations through defense in depth and system hardening techniques. The conclusion emphasizes the importance of a layered security approach in the face of evolving cyber threats. References to relevant research papers are included.

Running head: REPORT ON DESIGN OF A NETWORK
By
Academic Year: 2019-20
Module: Design of a Network
By
Academic Year: 2019-20
Module: Design of a Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Design of a network
Introduction
An organization's IT network is the foundation of its business as it associates every one of its
PCs and related gadgets together, enabling staff to work all the more effectively over the
association. With something so strategic it's pivotal it is structured and set up appropriately.
In case you're considering how to plan a system, this blog means to assist you with
understanding the nuts and bolts of good system framework structure. Systems have changed
throughout the years from divergent, designed networks to incorporated multi-layered
networks with a blend of designed and remote passageways, and an amalgamation of gadgets
all returning to a similar spot(Aries, & Lapukhov, 2018).
Scenario of the Network
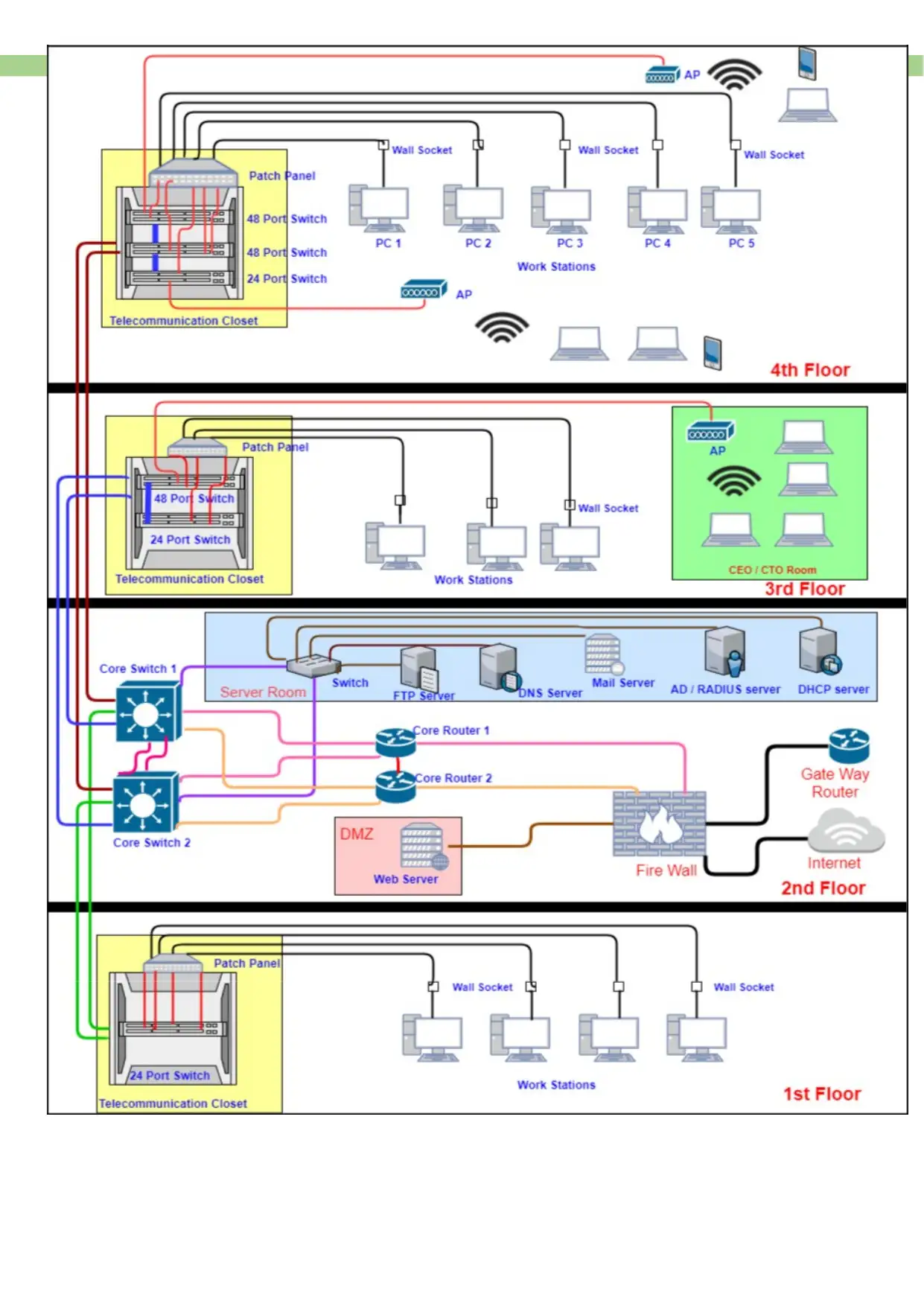
The company’s building has four floors each with specific requirements
The forth floor will support 50 machines. Apart from that it should have wireless
connection that supports 25 devices.
The third will have wireless connection that supports 30 devices.
The third floor will have an office for the managing director
We will have server and firewall in the second floor
The first flow will be for customers
Floors layout
Introduction
An organization's IT network is the foundation of its business as it associates every one of its
PCs and related gadgets together, enabling staff to work all the more effectively over the
association. With something so strategic it's pivotal it is structured and set up appropriately.
In case you're considering how to plan a system, this blog means to assist you with
understanding the nuts and bolts of good system framework structure. Systems have changed
throughout the years from divergent, designed networks to incorporated multi-layered
networks with a blend of designed and remote passageways, and an amalgamation of gadgets
all returning to a similar spot(Aries, & Lapukhov, 2018).
Scenario of the Network
The company’s building has four floors each with specific requirements
The forth floor will support 50 machines. Apart from that it should have wireless
connection that supports 25 devices.
The third will have wireless connection that supports 30 devices.
The third floor will have an office for the managing director
We will have server and firewall in the second floor
The first flow will be for customers
Floors layout
Design of a network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Design of a network
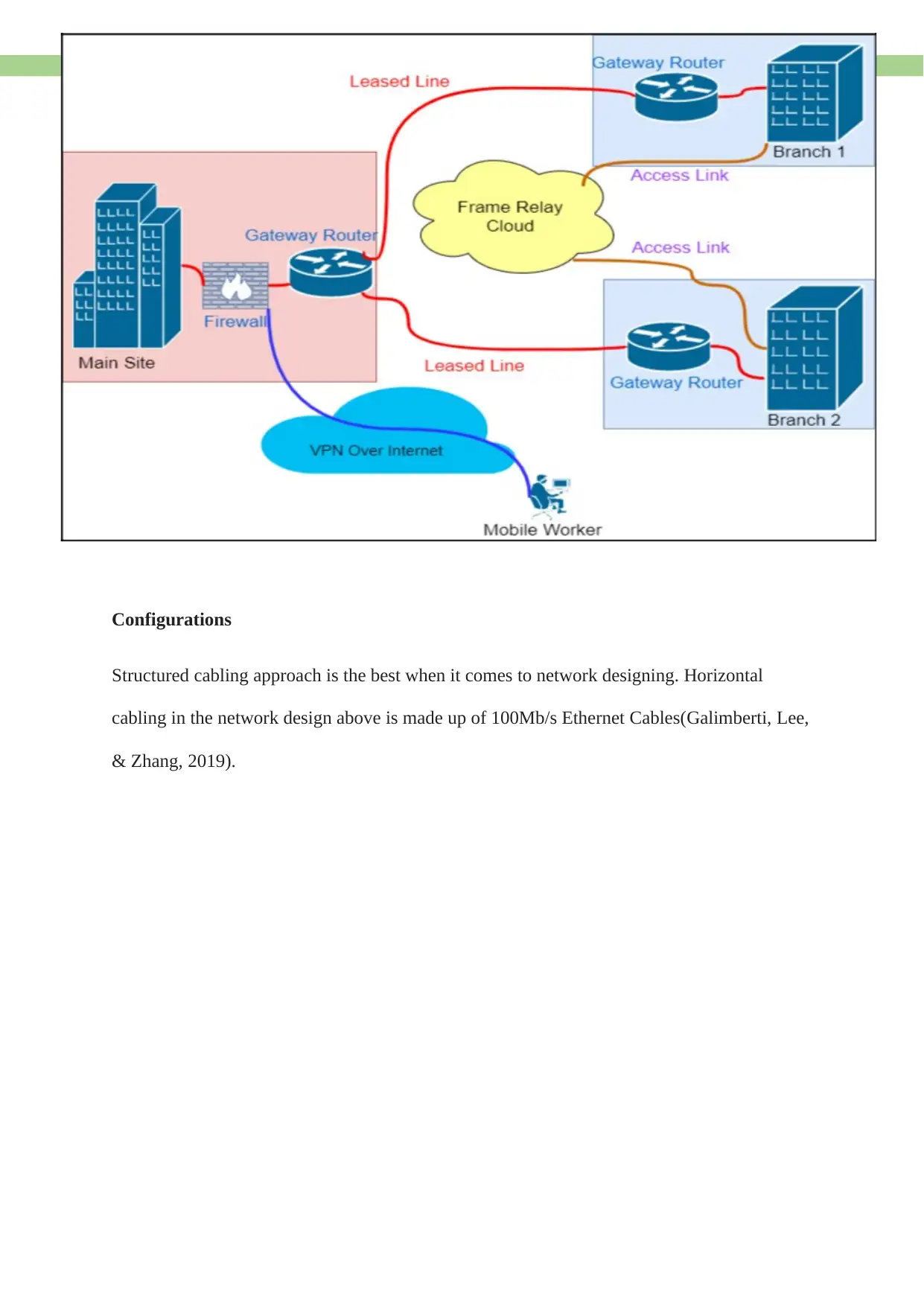
Configurations
Structured cabling approach is the best when it comes to network designing. Horizontal
cabling in the network design above is made up of 100Mb/s Ethernet Cables(Galimberti, Lee,
& Zhang, 2019).
Configurations
Structured cabling approach is the best when it comes to network designing. Horizontal
cabling in the network design above is made up of 100Mb/s Ethernet Cables(Galimberti, Lee,
& Zhang, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Design of a network
VLAN Description in the Network Design
VLAN Description in the Network Design
Design of a network
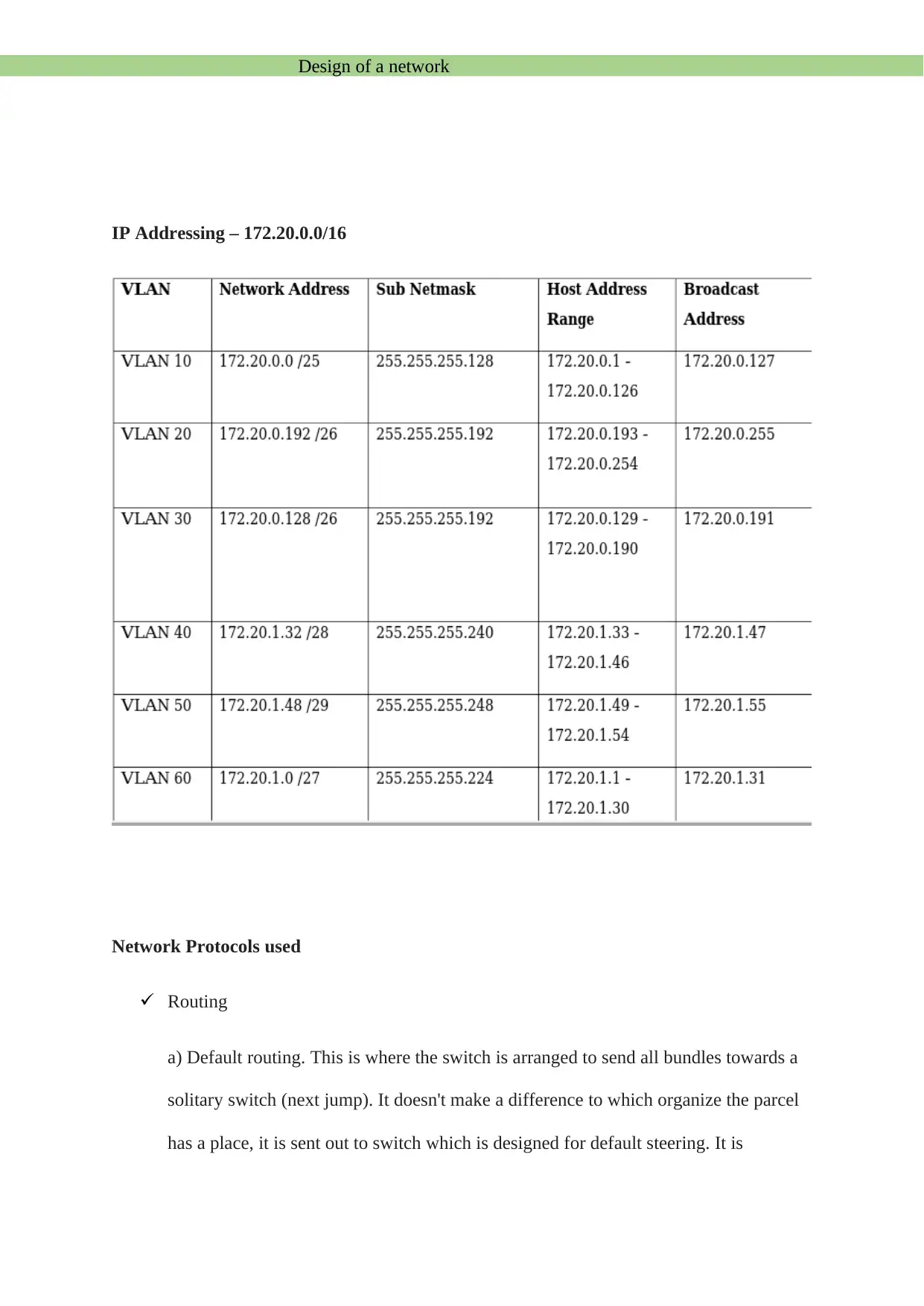
IP Addressing – 172.20.0.0/16
Network Protocols used
Routing
a) Default routing. This is where the switch is arranged to send all bundles towards a
solitary switch (next jump). It doesn't make a difference to which organize the parcel
has a place, it is sent out to switch which is designed for default steering. It is
IP Addressing – 172.20.0.0/16
Network Protocols used
Routing
a) Default routing. This is where the switch is arranged to send all bundles towards a
solitary switch (next jump). It doesn't make a difference to which organize the parcel
has a place, it is sent out to switch which is designed for default steering. It is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Design of a network
commonly utilized with stub switches. A stub switch is a switch which has just one
course to arrive at all different systems(Barth, Torvi, Minei, & Crabbe ,2016).
b) Static routing. Static steering is a procedure where we need to physically include
courses in directing table.
Advantages
No steering overhead for switch CPU which implies a less expensive switch can be
utilized to do directing.
It includes security on the grounds that no one but overseer can permit directing to
specific systems as it were(Hossain, 2018).
No transmission capacity utilization between switches.
Weaknesses
For an enormous system, it is a tumultuous assignment for chairman to physically
include each course for the system in the steering table on every switch.
The director ought to have great information on the topology. On the off chance that
another manager comes, at that point he needs to physically include each course so he
ought to have generally excellent information on the courses of the topology(Jain,
Sharma, Rao, & Levenson, 2015).
c) Dynamic routing. Dynamic routing makes programmed change of the courses as
per the present condition of the course in the directing table. Dynamic directing uses
conventions to find arrange goals and the courses to arrive at it. Tear and OSPF are
the best instances of dynamic directing convention. Programmed modification will be
commonly utilized with stub switches. A stub switch is a switch which has just one
course to arrive at all different systems(Barth, Torvi, Minei, & Crabbe ,2016).
b) Static routing. Static steering is a procedure where we need to physically include
courses in directing table.
Advantages
No steering overhead for switch CPU which implies a less expensive switch can be
utilized to do directing.
It includes security on the grounds that no one but overseer can permit directing to
specific systems as it were(Hossain, 2018).
No transmission capacity utilization between switches.
Weaknesses
For an enormous system, it is a tumultuous assignment for chairman to physically
include each course for the system in the steering table on every switch.
The director ought to have great information on the topology. On the off chance that
another manager comes, at that point he needs to physically include each course so he
ought to have generally excellent information on the courses of the topology(Jain,
Sharma, Rao, & Levenson, 2015).
c) Dynamic routing. Dynamic routing makes programmed change of the courses as
per the present condition of the course in the directing table. Dynamic directing uses
conventions to find arrange goals and the courses to arrive at it. Tear and OSPF are
the best instances of dynamic directing convention. Programmed modification will be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Design of a network
made to arrive at the system goal in the event that one course goes down(Neumann,
2015).
Domain Name Server
DNS is a host name to IP address interpretation administration. DNS is an
appropriated database actualized in a chain of command of name servers. It is an
application layer convention for message trade among customers and servers(Shakya,
Prasad, Alsadoon, Zajko, & Elchouemi, 2016, November).
SMTP
A straightforward mail move protocol(SMTP) is utilized to move the sends. The real
mail move is done through MTA for example Message Transfer Agents. To move
mail starting with one framework then onto the next, the framework must have the
customer message move operators and server message move specialists. The customer
message move operator is utilized to send the mail and server message move
specialists are utilized to get the mail. Straightforward Mail Transfer Protocol (SMTP)
Simple Mail Transfer Protocol is the main convention that characterizes Message
Transfer Agents (MTA) customer and server. Basic mail move convention is utilized
to characterize how the two directions and reactions must be sent to and fro. It is
utilized multiple times, between the sender and the sender's letters server and between
the two mail servers.
FTP
FTP is the first File Transfer Protocol and appreciates wide help from an assortment
of customers and gadgets. Tragically, FTP is naturally an uncertain convention,
made to arrive at the system goal in the event that one course goes down(Neumann,
2015).
Domain Name Server
DNS is a host name to IP address interpretation administration. DNS is an
appropriated database actualized in a chain of command of name servers. It is an
application layer convention for message trade among customers and servers(Shakya,
Prasad, Alsadoon, Zajko, & Elchouemi, 2016, November).
SMTP
A straightforward mail move protocol(SMTP) is utilized to move the sends. The real
mail move is done through MTA for example Message Transfer Agents. To move
mail starting with one framework then onto the next, the framework must have the
customer message move operators and server message move specialists. The customer
message move operator is utilized to send the mail and server message move
specialists are utilized to get the mail. Straightforward Mail Transfer Protocol (SMTP)
Simple Mail Transfer Protocol is the main convention that characterizes Message
Transfer Agents (MTA) customer and server. Basic mail move convention is utilized
to characterize how the two directions and reactions must be sent to and fro. It is
utilized multiple times, between the sender and the sender's letters server and between
the two mail servers.
FTP
FTP is the first File Transfer Protocol and appreciates wide help from an assortment
of customers and gadgets. Tragically, FTP is naturally an uncertain convention,

Design of a network
moving directions and information over a decoded association. It likewise gives no
real way to a server to demonstrate to a customer that the server is who it professes to
be. This can permit listening stealthily on passwords and information, just as
association capturing by malevolent servers. FTPS was acquainted with take care of
these issues by including secure TLS encryption and validation to the FTP
convention.
While FTPS is a noteworthy security improvement over FTP, the two conventions
have constraints. Both FTP and FTPS require different ports (one port to give
directions and a different port for every single index posting or document move) to
perform record move activity. This requires an enormous number of open ports for a
record move framework. The necessity to set up sending for these ports is a security
worry in numerous situations and can make investigating issues troublesome.
Defense in depth
Defense in depth is a system utilizing numerous safety efforts to ensure the honesty of data.
Along these lines of reasoning is utilized to cover all points of business security -
purposefully being excess when fundamental. On the off chance that one line of safeguard is
undermined, extra layers of guard are set up to guarantee that dangers don't get lost in an
outright flood. This technique tends to the security vulnerabilities that unavoidably exist in
innovation, faculty, and tasks inside a system(Snyder, Teachworth, Calderon, & Biswas,
2016)).
System hardening
moving directions and information over a decoded association. It likewise gives no
real way to a server to demonstrate to a customer that the server is who it professes to
be. This can permit listening stealthily on passwords and information, just as
association capturing by malevolent servers. FTPS was acquainted with take care of
these issues by including secure TLS encryption and validation to the FTP
convention.
While FTPS is a noteworthy security improvement over FTP, the two conventions
have constraints. Both FTP and FTPS require different ports (one port to give
directions and a different port for every single index posting or document move) to
perform record move activity. This requires an enormous number of open ports for a
record move framework. The necessity to set up sending for these ports is a security
worry in numerous situations and can make investigating issues troublesome.
Defense in depth
Defense in depth is a system utilizing numerous safety efforts to ensure the honesty of data.
Along these lines of reasoning is utilized to cover all points of business security -
purposefully being excess when fundamental. On the off chance that one line of safeguard is
undermined, extra layers of guard are set up to guarantee that dangers don't get lost in an
outright flood. This technique tends to the security vulnerabilities that unavoidably exist in
innovation, faculty, and tasks inside a system(Snyder, Teachworth, Calderon, & Biswas,
2016)).
System hardening
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Design of a network
System hardening implies verifying and designing a framework so that it lessens its surface
of powerlessness as it were. This is done to a great extent by expelling pointless
programming, hardening default certifications, handicapping superfluous administrations, and
adjusting other design parameters from default esteems with the goal that the framework
works safely for an engaged arrangement of administrations.
hardening is typically done by adhering to industry standard setup rules, for example, from
CIS (Center for Internet Security) or potentially merchant hardening rules. These should be
deliberately adjusted to guarantee that the usefulness of the framework isn't affected.
Conclusion
The present cyberthreats are developing and developing quickly. Barrier inside and out is a
strong, complete way to deal with using a mix of cutting edge security instruments to ensure
basic information and square dangers before they arrive at endpoints. Endpoint assurance,
including antivirus and firewalls, are as yet instrumental components of complete security; be
that as it may, a safeguard top to bottom methodology is considering critical to be as these
techniques for organize security alone are never again enough
System hardening implies verifying and designing a framework so that it lessens its surface
of powerlessness as it were. This is done to a great extent by expelling pointless
programming, hardening default certifications, handicapping superfluous administrations, and
adjusting other design parameters from default esteems with the goal that the framework
works safely for an engaged arrangement of administrations.
hardening is typically done by adhering to industry standard setup rules, for example, from
CIS (Center for Internet Security) or potentially merchant hardening rules. These should be
deliberately adjusted to guarantee that the usefulness of the framework isn't affected.
Conclusion
The present cyberthreats are developing and developing quickly. Barrier inside and out is a
strong, complete way to deal with using a mix of cutting edge security instruments to ensure
basic information and square dangers before they arrive at endpoints. Endpoint assurance,
including antivirus and firewalls, are as yet instrumental components of complete security; be
that as it may, a safeguard top to bottom methodology is considering critical to be as these
techniques for organize security alone are never again enough
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

0 Design of a network
References
Aries, E., & Lapukhov, P. (2018). Network Working Group C. Filsfils, Ed. Internet-Draft S.
Previdi Intended status: Informational Cisco Systems, Inc. Expires: June 2, 2019 G.
Dawra LinkedIn.
Barth, C., Torvi, R., Minei, I., & Crabbe, E. (2016). PCE Working Group H.
Ananthakrishnan
Internet-Draft Packet Design Intended status: Standards Track S. Sivabalan Expires:
September 11, 2016 Cisco.
Galimberti, G., Lee, Y., & Zhang, F. (2019). CCAMP G. Martinelli, Ed. Internet-Draft Cisco
Intended status: Informational H. Zheng, Ed. Expires: September 5, 2019 Huawei
Technologies.
Hossain, M. (2018). Cisco Certified Network Associate (CCNA).
Jain, V., Sharma, G. P., Rao, D., & Levenson, H. (2015). U.S. Patent No. 9,083,613.
Washington, DC: U.S. Patent and Trademark Office.
Neumann, J. C. (2015). The book of GNS3: build virtual network labs using Cisco, Juniper,
and more. No Starch Press.
Shakya, A., Prasad, P. W. C., Alsadoon, A., Zajko, G., & Elchouemi, A. (2016, November).
References
Aries, E., & Lapukhov, P. (2018). Network Working Group C. Filsfils, Ed. Internet-Draft S.
Previdi Intended status: Informational Cisco Systems, Inc. Expires: June 2, 2019 G.
Dawra LinkedIn.
Barth, C., Torvi, R., Minei, I., & Crabbe, E. (2016). PCE Working Group H.
Ananthakrishnan
Internet-Draft Packet Design Intended status: Standards Track S. Sivabalan Expires:
September 11, 2016 Cisco.
Galimberti, G., Lee, Y., & Zhang, F. (2019). CCAMP G. Martinelli, Ed. Internet-Draft Cisco
Intended status: Informational H. Zheng, Ed. Expires: September 5, 2019 Huawei
Technologies.
Hossain, M. (2018). Cisco Certified Network Associate (CCNA).
Jain, V., Sharma, G. P., Rao, D., & Levenson, H. (2015). U.S. Patent No. 9,083,613.
Washington, DC: U.S. Patent and Trademark Office.
Neumann, J. C. (2015). The book of GNS3: build virtual network labs using Cisco, Juniper,
and more. No Starch Press.
Shakya, A., Prasad, P. W. C., Alsadoon, A., Zajko, G., & Elchouemi, A. (2016, November).

1 Design of a network
Development of the Wireless Cisco Networking Laboratory pod. In 2016
International Conference on Advances in Electrical, Electronic and Systems
Engineering (ICAEES) (pp. 208-213). IEEE.
Snyder, I. M., Teachworth, M. D., Calderon, B. A., & Biswas, S. Z. (2016). U.S. Patent
Application No. 29/542,001.
Development of the Wireless Cisco Networking Laboratory pod. In 2016
International Conference on Advances in Electrical, Electronic and Systems
Engineering (ICAEES) (pp. 208-213). IEEE.
Snyder, I. M., Teachworth, M. D., Calderon, B. A., & Biswas, S. Z. (2016). U.S. Patent
Application No. 29/542,001.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




