Wireless Network and Communication Assignment, Semester 2
VerifiedAdded on 2023/03/30
|19
|1141
|234
Homework Assignment
AI Summary
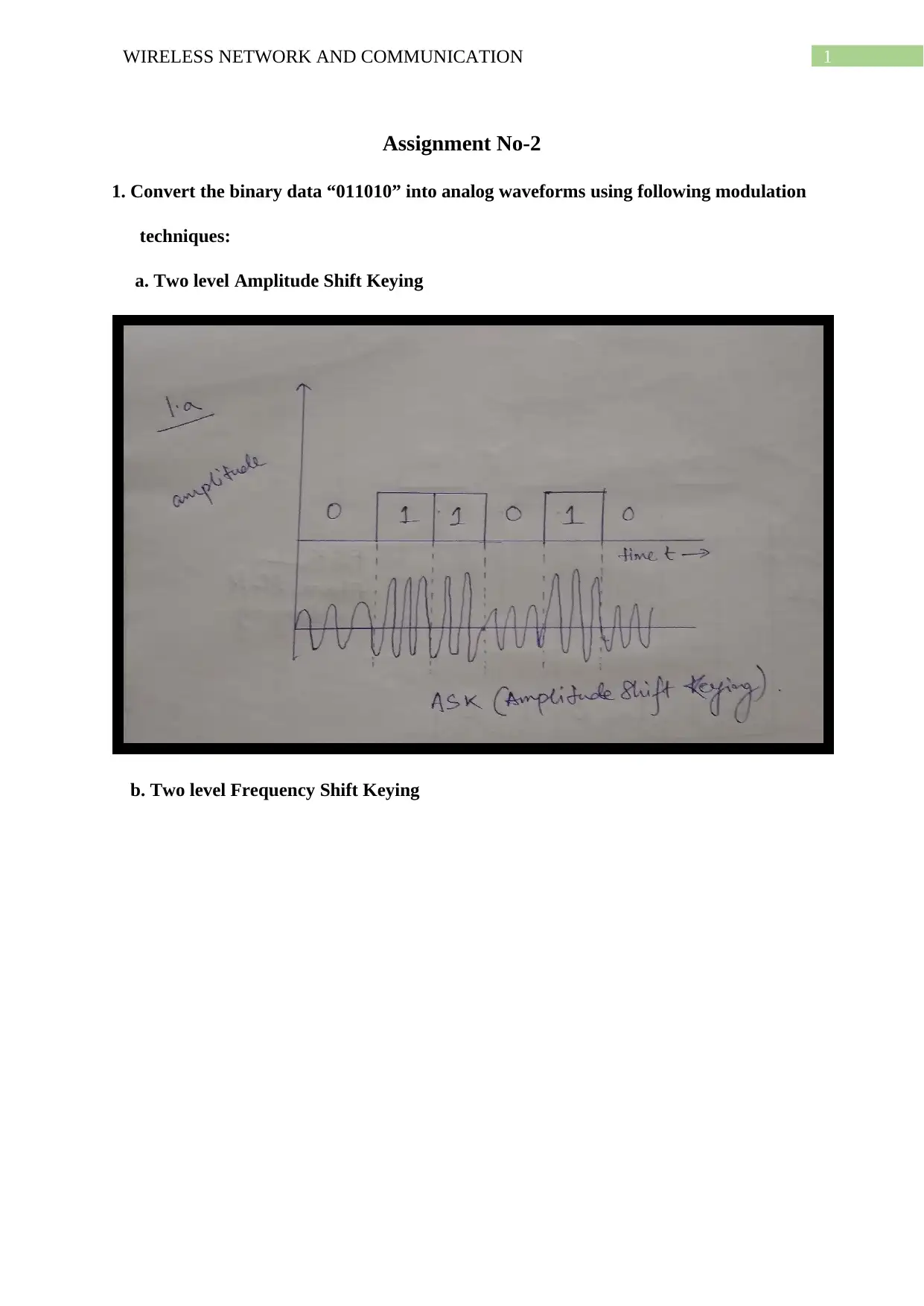
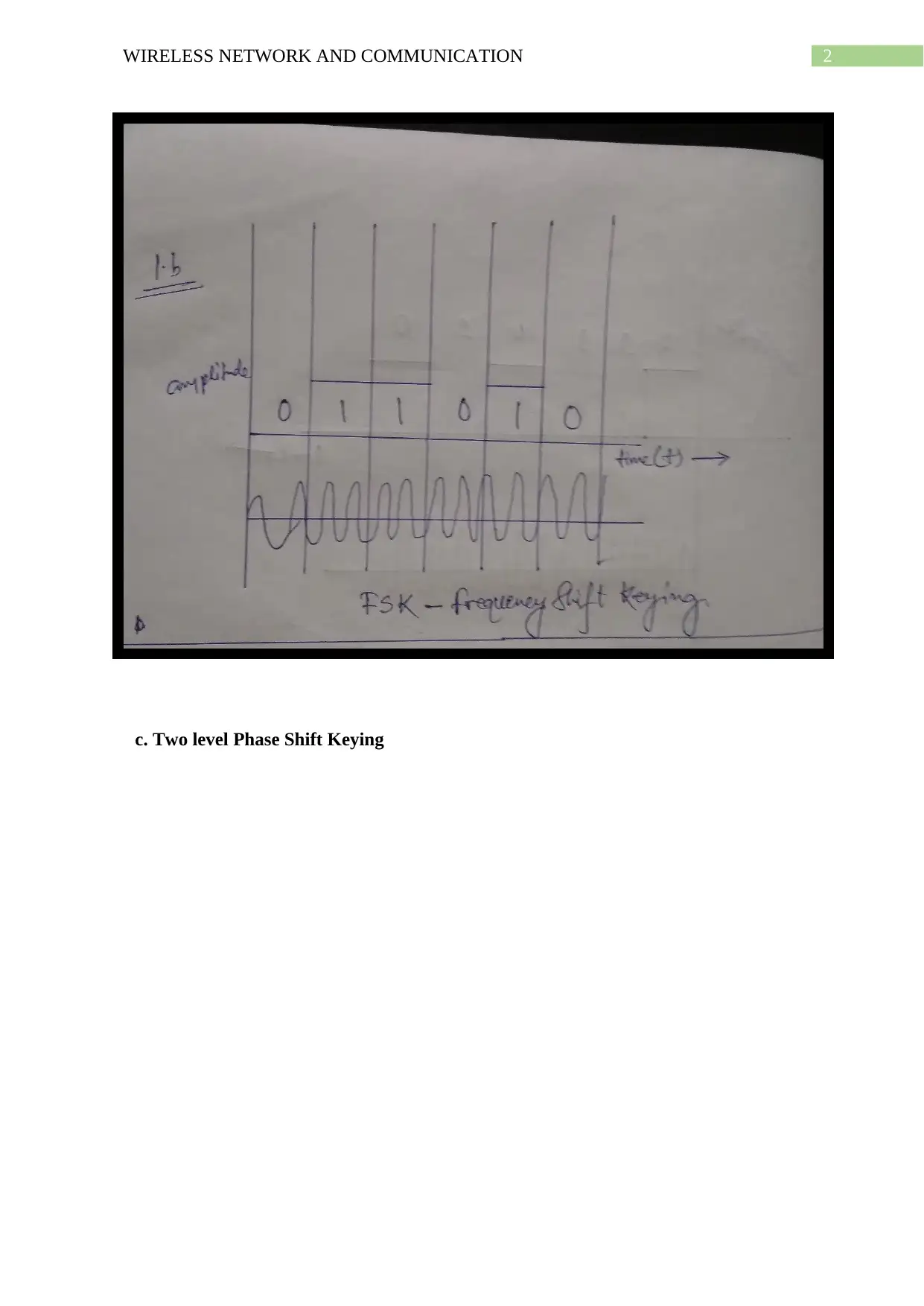
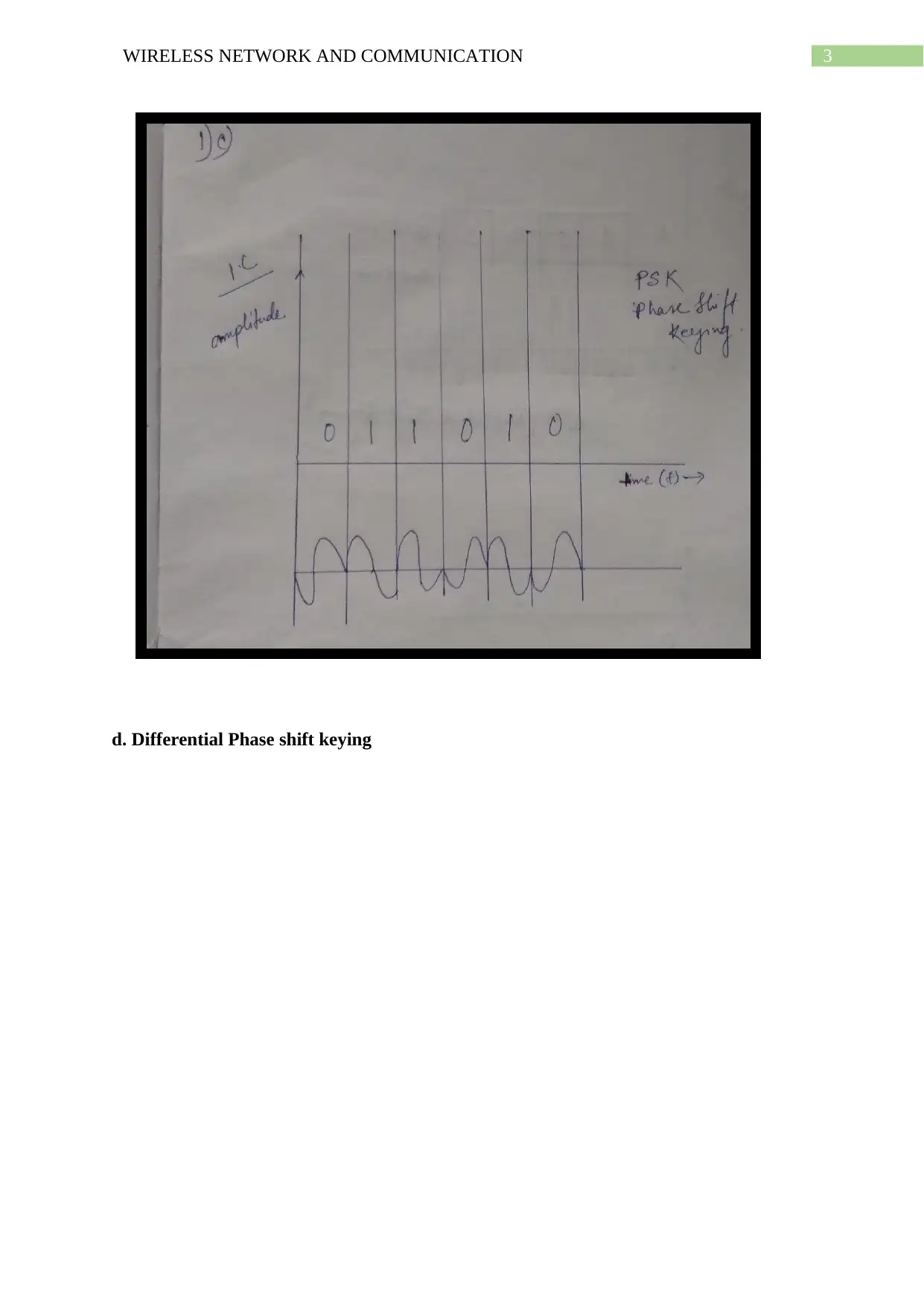
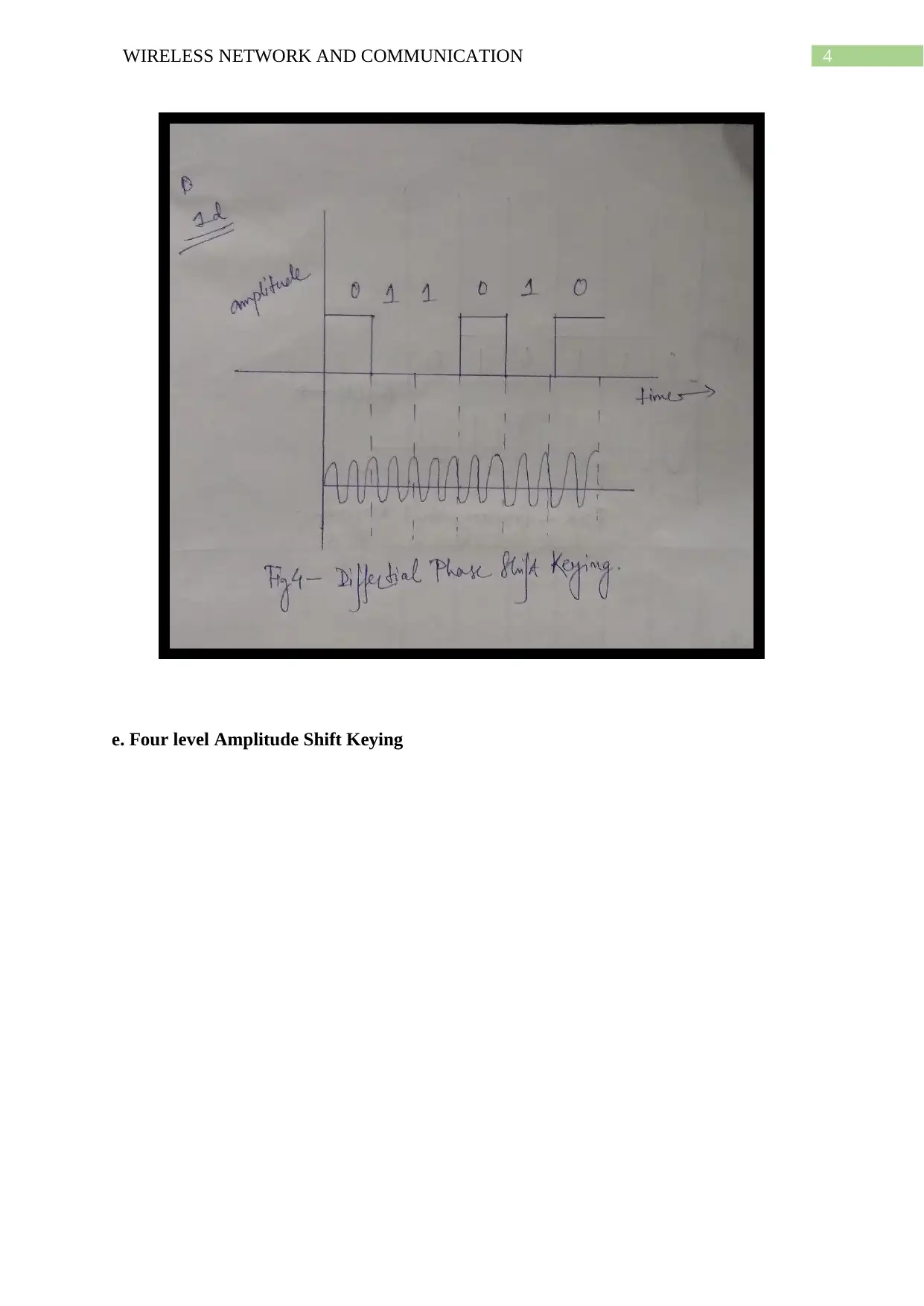
This document presents a comprehensive solution to a wireless network and communication assignment. It covers various modulation techniques such as Amplitude Shift Keying, Frequency Shift Keying, and Phase Shift Keying, including their application to binary data conversion. The assignment also includes computations for frequency assignments based on given parameters, the drawing of analog and frequency modulation waveforms, and the creation of a 16 QAM constellation diagram. Furthermore, it explains the error detection process using Cyclic Redundancy Check (CRC) and computes the frame check sequence and transmitted signal using Direct Sequence Spread Spectrum. The solution further differentiates between Infrastructure and ad hoc modes in WLAN, compares TCP and OSI protocols, and explains the advantages of hexagonal cell shapes in cellular communications. References are also provided.
1 out of 19












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)