Analysis of Emerging Trends in Networking Isolation in Cloud Computing
VerifiedAdded on 2020/03/13
|2
|1538
|91
Report
AI Summary
This report provides an analysis of emerging trends in networking isolation techniques within cloud computing, focusing on data and application isolation for multi-tenant environments. It explores the significance of data isolation in ensuring the security of each tenant's data and applications, examining various levels of database isolation including independent databases, shared databases with isolated data structures, and shared databases with shared data structures. The report also discusses multi-tenant application isolation strategies, such as sharing middleware and virtualization. The study emphasizes the importance of mandatory access control and virtualization techniques in enhancing cloud security. The paper concludes by highlighting the need for robust isolation measures to ensure secure cloud computing environments.

> [Please Fill your Session Number] <
Study of Emerging Trends in Networking
Isolation techniques in Cloud Computing
(August 2017)
[Please fill your name]
[Please fill your occupation]
Data of multi-tenant is put away together in cloud computing, with a specific end goal to guarantee the information security of
tenants that should be done to disengage the application and information of each tenant. The security of every one of the tenants might
be influenced and even reason the entire framework to be separated if the plan of information confine is disappointment, accordingly it
is qualified to research and investigation the arrangement of information seclusion of multitenant in cloud computing condition. In this
paper, the research and analysis is carried out as an answer for application and information isolation of multi-tenant in cloud
computing.
Index Terms — Cloud computing, multi-tenant, data isolation, virtualization.
I. INTRODUCTION
HIS paper aims to provide a critical understanding of what
already exists and what needs to be done with respect to
isolation security in cloud computing. Each tenant does not
know about the presence of different tenants in nature of cloud
computing, which implies that each tenant thought they have
possessed all administration asset and information in
framework [5], notwithstanding, multi-tenant information is
put away together keeping in mind the end goal to make
certain the security of use information, so the application and
information of tenants must to be disconnected totally, it is
important that each tenant cannot be permitted to get to the
information of others, the security answer for every one of the
tenants of the information is probably going to be influenced
truly if confinement is fall flat or not finished [1], it is
extremely basic to examine on multi-tenant information
detachment to guarantee the security of each tenants.
T
II. NEW SOLUTION FOR ISOLATION OF MULTI-TENANT
A. Data isolation
Multi-tenant information disconnection is a basic
innovation in multi-tenant plot, the inability to detach the
information will be the safe concealed inconvenience in multi-
tenant condition to each tenant [8]. In Multi-tenant condition,
the information does not permit to be shared, so the related
defensive measures ought to be taken to help multi-tenant
information cannot be gotten to by different tenants. Multi-
tenant information detachment is generally isolated into three
levels, including an independent database, a shared database,
isolated data structure and shared database, shared data
architecture.
Independent Database: This scheme is that each tenant has a
different database, so tenant information confinement is the
most abnormal amount and security is ideal, however the cost
is too high.
Advantages: For each tenant there is autonomous database,
which rearranges the development of the information model
and meets the one of a kind needs of various tenants [5]; if
something would fall flat, it is moderately easy to reestablish
the information.
Drawbacks: With the expanding number of establishment
database, the support expenses and buy costs are higher. This
plan resembles the conventional one that a client, an
arrangement of information, an arrangement of organization,
the main contrast is that the product are brought together
orchestrated by administrators [3]. This plan is appropriate for
the bank and doctor's facility that information require an
abnormal state of the information isolation. This plan can be
enhanced the rental evaluating [1]. On the off chance that the
cost is low, the item takes the low street. At that point this plan
is not fit.
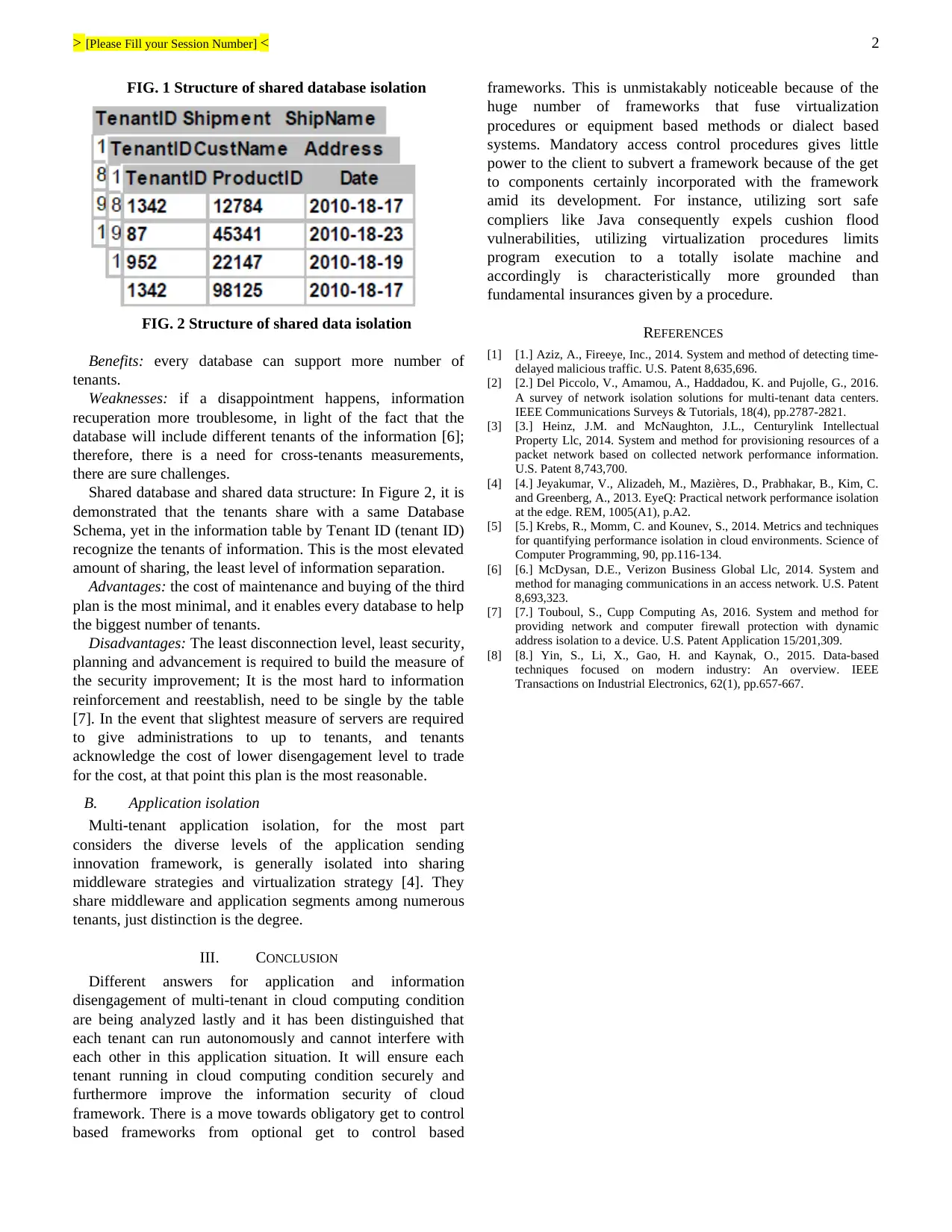
Shared database and data structure isolation: In Figure 1 it
is demonstrated that increasingly or every one of the tenants
share the database, however an tenant relates to a different
(Schema is the arrangement of database objects, keeping in
mind the end goal to recognize the different sets expecting to
give each set a name, for example, a table compares to a
mapping's item, the pattern name is by and large equivalent to
the tenant's record name) [2]. The plan supply intelligent
information seclusion for the higher security of tenants'
necessity is not totally confined.
1
Study of Emerging Trends in Networking
Isolation techniques in Cloud Computing
(August 2017)
[Please fill your name]
[Please fill your occupation]
Data of multi-tenant is put away together in cloud computing, with a specific end goal to guarantee the information security of
tenants that should be done to disengage the application and information of each tenant. The security of every one of the tenants might
be influenced and even reason the entire framework to be separated if the plan of information confine is disappointment, accordingly it
is qualified to research and investigation the arrangement of information seclusion of multitenant in cloud computing condition. In this
paper, the research and analysis is carried out as an answer for application and information isolation of multi-tenant in cloud
computing.
Index Terms — Cloud computing, multi-tenant, data isolation, virtualization.
I. INTRODUCTION
HIS paper aims to provide a critical understanding of what
already exists and what needs to be done with respect to
isolation security in cloud computing. Each tenant does not
know about the presence of different tenants in nature of cloud
computing, which implies that each tenant thought they have
possessed all administration asset and information in
framework [5], notwithstanding, multi-tenant information is
put away together keeping in mind the end goal to make
certain the security of use information, so the application and
information of tenants must to be disconnected totally, it is
important that each tenant cannot be permitted to get to the
information of others, the security answer for every one of the
tenants of the information is probably going to be influenced
truly if confinement is fall flat or not finished [1], it is
extremely basic to examine on multi-tenant information
detachment to guarantee the security of each tenants.
T
II. NEW SOLUTION FOR ISOLATION OF MULTI-TENANT
A. Data isolation
Multi-tenant information disconnection is a basic
innovation in multi-tenant plot, the inability to detach the
information will be the safe concealed inconvenience in multi-
tenant condition to each tenant [8]. In Multi-tenant condition,
the information does not permit to be shared, so the related
defensive measures ought to be taken to help multi-tenant
information cannot be gotten to by different tenants. Multi-
tenant information detachment is generally isolated into three
levels, including an independent database, a shared database,
isolated data structure and shared database, shared data
architecture.
Independent Database: This scheme is that each tenant has a
different database, so tenant information confinement is the
most abnormal amount and security is ideal, however the cost
is too high.
Advantages: For each tenant there is autonomous database,
which rearranges the development of the information model
and meets the one of a kind needs of various tenants [5]; if
something would fall flat, it is moderately easy to reestablish
the information.
Drawbacks: With the expanding number of establishment
database, the support expenses and buy costs are higher. This
plan resembles the conventional one that a client, an
arrangement of information, an arrangement of organization,
the main contrast is that the product are brought together
orchestrated by administrators [3]. This plan is appropriate for
the bank and doctor's facility that information require an
abnormal state of the information isolation. This plan can be
enhanced the rental evaluating [1]. On the off chance that the
cost is low, the item takes the low street. At that point this plan
is not fit.
Shared database and data structure isolation: In Figure 1 it
is demonstrated that increasingly or every one of the tenants
share the database, however an tenant relates to a different
(Schema is the arrangement of database objects, keeping in
mind the end goal to recognize the different sets expecting to
give each set a name, for example, a table compares to a
mapping's item, the pattern name is by and large equivalent to
the tenant's record name) [2]. The plan supply intelligent
information seclusion for the higher security of tenants'
necessity is not totally confined.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
> [Please Fill your Session Number] <
FIG. 1 Structure of shared database isolation
FIG. 2 Structure of shared data isolation
Benefits: every database can support more number of
tenants.
Weaknesses: if a disappointment happens, information
recuperation more troublesome, in light of the fact that the
database will include different tenants of the information [6];
therefore, there is a need for cross-tenants measurements,
there are sure challenges.
Shared database and shared data structure: In Figure 2, it is
demonstrated that the tenants share with a same Database
Schema, yet in the information table by Tenant ID (tenant ID)
recognize the tenants of information. This is the most elevated
amount of sharing, the least level of information separation.
Advantages: the cost of maintenance and buying of the third
plan is the most minimal, and it enables every database to help
the biggest number of tenants.
Disadvantages: The least disconnection level, least security,
planning and advancement is required to build the measure of
the security improvement; It is the most hard to information
reinforcement and reestablish, need to be single by the table
[7]. In the event that slightest measure of servers are required
to give administrations to up to tenants, and tenants
acknowledge the cost of lower disengagement level to trade
for the cost, at that point this plan is the most reasonable.
B. Application isolation
Multi-tenant application isolation, for the most part
considers the diverse levels of the application sending
innovation framework, is generally isolated into sharing
middleware strategies and virtualization strategy [4]. They
share middleware and application segments among numerous
tenants, just distinction is the degree.
III. CONCLUSION
Different answers for application and information
disengagement of multi-tenant in cloud computing condition
are being analyzed lastly and it has been distinguished that
each tenant can run autonomously and cannot interfere with
each other in this application situation. It will ensure each
tenant running in cloud computing condition securely and
furthermore improve the information security of cloud
framework. There is a move towards obligatory get to control
based frameworks from optional get to control based
frameworks. This is unmistakably noticeable because of the
huge number of frameworks that fuse virtualization
procedures or equipment based methods or dialect based
systems. Mandatory access control procedures gives little
power to the client to subvert a framework because of the get
to components certainly incorporated with the framework
amid its development. For instance, utilizing sort safe
compliers like Java consequently expels cushion flood
vulnerabilities, utilizing virtualization procedures limits
program execution to a totally isolate machine and
accordingly is characteristically more grounded than
fundamental insurances given by a procedure.
REFERENCES
[1] [1.] Aziz, A., Fireeye, Inc., 2014. System and method of detecting time-
delayed malicious traffic. U.S. Patent 8,635,696.
[2] [2.] Del Piccolo, V., Amamou, A., Haddadou, K. and Pujolle, G., 2016.
A survey of network isolation solutions for multi-tenant data centers.
IEEE Communications Surveys & Tutorials, 18(4), pp.2787-2821.
[3] [3.] Heinz, J.M. and McNaughton, J.L., Centurylink Intellectual
Property Llc, 2014. System and method for provisioning resources of a
packet network based on collected network performance information.
U.S. Patent 8,743,700.
[4] [4.] Jeyakumar, V., Alizadeh, M., Mazières, D., Prabhakar, B., Kim, C.
and Greenberg, A., 2013. EyeQ: Practical network performance isolation
at the edge. REM, 1005(A1), p.A2.
[5] [5.] Krebs, R., Momm, C. and Kounev, S., 2014. Metrics and techniques
for quantifying performance isolation in cloud environments. Science of
Computer Programming, 90, pp.116-134.
[6] [6.] McDysan, D.E., Verizon Business Global Llc, 2014. System and
method for managing communications in an access network. U.S. Patent
8,693,323.
[7] [7.] Touboul, S., Cupp Computing As, 2016. System and method for
providing network and computer firewall protection with dynamic
address isolation to a device. U.S. Patent Application 15/201,309.
[8] [8.] Yin, S., Li, X., Gao, H. and Kaynak, O., 2015. Data-based
techniques focused on modern industry: An overview. IEEE
Transactions on Industrial Electronics, 62(1), pp.657-667.
2
FIG. 1 Structure of shared database isolation
FIG. 2 Structure of shared data isolation
Benefits: every database can support more number of
tenants.
Weaknesses: if a disappointment happens, information
recuperation more troublesome, in light of the fact that the
database will include different tenants of the information [6];
therefore, there is a need for cross-tenants measurements,
there are sure challenges.
Shared database and shared data structure: In Figure 2, it is
demonstrated that the tenants share with a same Database
Schema, yet in the information table by Tenant ID (tenant ID)
recognize the tenants of information. This is the most elevated
amount of sharing, the least level of information separation.
Advantages: the cost of maintenance and buying of the third
plan is the most minimal, and it enables every database to help
the biggest number of tenants.
Disadvantages: The least disconnection level, least security,
planning and advancement is required to build the measure of
the security improvement; It is the most hard to information
reinforcement and reestablish, need to be single by the table
[7]. In the event that slightest measure of servers are required
to give administrations to up to tenants, and tenants
acknowledge the cost of lower disengagement level to trade
for the cost, at that point this plan is the most reasonable.
B. Application isolation
Multi-tenant application isolation, for the most part
considers the diverse levels of the application sending
innovation framework, is generally isolated into sharing
middleware strategies and virtualization strategy [4]. They
share middleware and application segments among numerous
tenants, just distinction is the degree.
III. CONCLUSION
Different answers for application and information
disengagement of multi-tenant in cloud computing condition
are being analyzed lastly and it has been distinguished that
each tenant can run autonomously and cannot interfere with
each other in this application situation. It will ensure each
tenant running in cloud computing condition securely and
furthermore improve the information security of cloud
framework. There is a move towards obligatory get to control
based frameworks from optional get to control based
frameworks. This is unmistakably noticeable because of the
huge number of frameworks that fuse virtualization
procedures or equipment based methods or dialect based
systems. Mandatory access control procedures gives little
power to the client to subvert a framework because of the get
to components certainly incorporated with the framework
amid its development. For instance, utilizing sort safe
compliers like Java consequently expels cushion flood
vulnerabilities, utilizing virtualization procedures limits
program execution to a totally isolate machine and
accordingly is characteristically more grounded than
fundamental insurances given by a procedure.
REFERENCES
[1] [1.] Aziz, A., Fireeye, Inc., 2014. System and method of detecting time-
delayed malicious traffic. U.S. Patent 8,635,696.
[2] [2.] Del Piccolo, V., Amamou, A., Haddadou, K. and Pujolle, G., 2016.
A survey of network isolation solutions for multi-tenant data centers.
IEEE Communications Surveys & Tutorials, 18(4), pp.2787-2821.
[3] [3.] Heinz, J.M. and McNaughton, J.L., Centurylink Intellectual
Property Llc, 2014. System and method for provisioning resources of a
packet network based on collected network performance information.
U.S. Patent 8,743,700.
[4] [4.] Jeyakumar, V., Alizadeh, M., Mazières, D., Prabhakar, B., Kim, C.
and Greenberg, A., 2013. EyeQ: Practical network performance isolation
at the edge. REM, 1005(A1), p.A2.
[5] [5.] Krebs, R., Momm, C. and Kounev, S., 2014. Metrics and techniques
for quantifying performance isolation in cloud environments. Science of
Computer Programming, 90, pp.116-134.
[6] [6.] McDysan, D.E., Verizon Business Global Llc, 2014. System and
method for managing communications in an access network. U.S. Patent
8,693,323.
[7] [7.] Touboul, S., Cupp Computing As, 2016. System and method for
providing network and computer firewall protection with dynamic
address isolation to a device. U.S. Patent Application 15/201,309.
[8] [8.] Yin, S., Li, X., Gao, H. and Kaynak, O., 2015. Data-based
techniques focused on modern industry: An overview. IEEE
Transactions on Industrial Electronics, 62(1), pp.657-667.
2
1 out of 2
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.