ITC571 - Emerging Technology and Innovations: Big Data Security Report
VerifiedAdded on 2020/03/16
|7
|2837
|67
Report
AI Summary
This report, prepared for the ITC571 course at Charles Sturt University, examines security and privacy threats within the realm of big data. It critically analyzes the role of emerging technologies and innovations in mitigating these threats, with a focus on disaster management systems. The research employs a quantitative methodology, collecting data through questionnaires administered to engineers and experts in the field. The findings reveal insights into the effectiveness of current technologies, the challenges of implementation, and the most utilized technologies for managing security issues. The report includes a literature review, research methodology, results, and discussion, culminating in conclusions that highlight the importance of innovation in addressing big data security challenges. The study emphasizes the significance of data accessibility, confidentiality, and integrity, providing a comprehensive overview of the current landscape and future directions in big data security.

Full Name
Student ID
Subject ITC571 – Emerging Technology and Innovations
Assignment No Final Report
Due Date
Lecturer’s Name Malka N. Halgamuge
Security and privacy threats in big data
Email:
School of Computing and Mathematics, Charles Sturt University, Melbourne, Victoria
Abstract –
Despite the fact that numerous strategies can be presented with the end goal of examination, practices and
its immediate impact, subjective techniques are especially specific and can be named as vital for the
distinctive courses keeping in mind the end goal to think about the marvels of the cyber security
perspective. The examination planned keeping in mind the end goal to know the distinctive viewpoint
identified with the case can incorporate human PC communication, esteem and outline, computerized and
data education, engineering morals and decent variety and consideration. The study analyzes the role of
emerging technologies and innovation in order to manage natural hazards. Introduction has been provided
that includes aim and background of the study. In addition, research methodology is discussed along with
results and discussion of the data accumulated for the research.
GRAPHIC ABSTRACT
Key Words— Big data, data security
1. INTRODUCTION
Section 1: Significance of the research
In this day and age the systems administration idea is consolidated from the idea of government foundation
to web keeping money. Hence, it can be expressed that the system assurance is not any more an additional
alternative. Cyber security can be shown as a worldwide worry, as breaks which are prominent have mostly
Student ID
Subject ITC571 – Emerging Technology and Innovations
Assignment No Final Report
Due Date
Lecturer’s Name Malka N. Halgamuge
Security and privacy threats in big data
Email:
School of Computing and Mathematics, Charles Sturt University, Melbourne, Victoria
Abstract –
Despite the fact that numerous strategies can be presented with the end goal of examination, practices and
its immediate impact, subjective techniques are especially specific and can be named as vital for the
distinctive courses keeping in mind the end goal to think about the marvels of the cyber security
perspective. The examination planned keeping in mind the end goal to know the distinctive viewpoint
identified with the case can incorporate human PC communication, esteem and outline, computerized and
data education, engineering morals and decent variety and consideration. The study analyzes the role of
emerging technologies and innovation in order to manage natural hazards. Introduction has been provided
that includes aim and background of the study. In addition, research methodology is discussed along with
results and discussion of the data accumulated for the research.
GRAPHIC ABSTRACT
Key Words— Big data, data security
1. INTRODUCTION
Section 1: Significance of the research
In this day and age the systems administration idea is consolidated from the idea of government foundation
to web keeping money. Hence, it can be expressed that the system assurance is not any more an additional
alternative. Cyber security can be shown as a worldwide worry, as breaks which are prominent have mostly
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

surrendered many variables of worry that basically gives a worry that hacks and different assaults which
are identified with the security which could jeopardize the economy of the worldwide. A cyber assault can
be alluded to as a ponder abuse identified with the PC framework, mechanical ward systems and project.
The cyber aggressors primarily utilize the vindictive code action and other programming's to adjust the PC
code, information and the rationale which results in the outcome which can be named as problematic which
principally trade off the information and specifically prompt cyber wrongdoings, for example, distinguish
the framework penetration and the theft.
Section 2: How original is the approach?
The research paper is based on original research, which generates new knowledge instead of summarizing
the content that is already known in a new form [2]. There are several ways of generating new knowledge
such as observations, experiments and new approaches for solving the existing issues [3]. The report has
been achieved by the researcher and explain hypothesis of the study along with research questions. In
addition, the researcher has provided detailed report of research methods. Moreover, results as well as
possible implications are interpreted in the present research that proves originality of the research.
Section 3-4: Literature review in the area what you are working
By the methods for qualitative approach with accentuation on the information examination, it has been seen
that the episode of the cyber are expanding on an everyday premise which mostly prompt a lost in the
information concerning a considerable lot of the associations [11]. The occurrence rate was dissected for
various sorts of assault vectors which are considered which helps in giving the detail depiction identified
with the cyber assaults for a specific association.
The aim of the researcher is establishing out the primary issue which is identified with the cyber attacks
and with it executing fundamental practical imminent to decrease the general impact of the assaults on the
off chance that they are joined in the entrance territory of the universe of the web. It is especially helpful
because of the factor that early recognition of the issue can be straightforwardly minimizing the general
influence which it can have on the forthcoming of the information [10]. It can be expressed that the
inspirations, influence and the acts of individuals can be specifically compelling in the worry of the most
cyber security activities [4]. The general population are particularly falling behind the primary intention of
picking up the entrance concerning the data and the basic innovation which are disappointed, this
fundamentally esteems the idea of independence, protection, versatility and the entrance of the data,
procedures and arrangement that are for the most part work with individuals.
The fundamental outcome which is accomplished from the procedure are:
• Confidentiality: Any critical data which must be kept secured must be constantly kept classified.
This data ought to be gotten to by individuals or the framework that have the simple authorization to allow
access to those.
• Integrity: Maintaining the idea of integrity which is identified with the data resources so as to keep
each and everything in place, entire and uncorrupted configuration.
• Availability: Maintaining the idea of accessibility of the services, framework and the data when
required by the customer and the business is accomplished.
Section 5: Research gap
Even though the research has several benefits for the applicants to use emerging technologies in order to
manage natural disasters and hazards, there are some gaps in the research. Research aims and objectives
can be formulated broadly that would be helpful to research on large aspects [9]. In addition, integration of
additional methods of data collection could increase the opportunity as well as depth of analysis along with
the statement.
are identified with the security which could jeopardize the economy of the worldwide. A cyber assault can
be alluded to as a ponder abuse identified with the PC framework, mechanical ward systems and project.
The cyber aggressors primarily utilize the vindictive code action and other programming's to adjust the PC
code, information and the rationale which results in the outcome which can be named as problematic which
principally trade off the information and specifically prompt cyber wrongdoings, for example, distinguish
the framework penetration and the theft.
Section 2: How original is the approach?
The research paper is based on original research, which generates new knowledge instead of summarizing
the content that is already known in a new form [2]. There are several ways of generating new knowledge
such as observations, experiments and new approaches for solving the existing issues [3]. The report has
been achieved by the researcher and explain hypothesis of the study along with research questions. In
addition, the researcher has provided detailed report of research methods. Moreover, results as well as
possible implications are interpreted in the present research that proves originality of the research.
Section 3-4: Literature review in the area what you are working
By the methods for qualitative approach with accentuation on the information examination, it has been seen
that the episode of the cyber are expanding on an everyday premise which mostly prompt a lost in the
information concerning a considerable lot of the associations [11]. The occurrence rate was dissected for
various sorts of assault vectors which are considered which helps in giving the detail depiction identified
with the cyber assaults for a specific association.
The aim of the researcher is establishing out the primary issue which is identified with the cyber attacks
and with it executing fundamental practical imminent to decrease the general impact of the assaults on the
off chance that they are joined in the entrance territory of the universe of the web. It is especially helpful
because of the factor that early recognition of the issue can be straightforwardly minimizing the general
influence which it can have on the forthcoming of the information [10]. It can be expressed that the
inspirations, influence and the acts of individuals can be specifically compelling in the worry of the most
cyber security activities [4]. The general population are particularly falling behind the primary intention of
picking up the entrance concerning the data and the basic innovation which are disappointed, this
fundamentally esteems the idea of independence, protection, versatility and the entrance of the data,
procedures and arrangement that are for the most part work with individuals.
The fundamental outcome which is accomplished from the procedure are:
• Confidentiality: Any critical data which must be kept secured must be constantly kept classified.
This data ought to be gotten to by individuals or the framework that have the simple authorization to allow
access to those.
• Integrity: Maintaining the idea of integrity which is identified with the data resources so as to keep
each and everything in place, entire and uncorrupted configuration.
• Availability: Maintaining the idea of accessibility of the services, framework and the data when
required by the customer and the business is accomplished.
Section 5: Research gap
Even though the research has several benefits for the applicants to use emerging technologies in order to
manage natural disasters and hazards, there are some gaps in the research. Research aims and objectives
can be formulated broadly that would be helpful to research on large aspects [9]. In addition, integration of
additional methods of data collection could increase the opportunity as well as depth of analysis along with
the statement.

In addition, the signature related to database as well as database along with habits that keeps pace with bad
components, which are mainly keeps pace with the volume of malware having new strains created daily.
On the other hand, lack of stability helps managing of the identities and applications and data with the
products with serious scalability narrowing down the security analysis into sub set event.
Section 6: Aim of your research
The aim of the research is to critically analyze the role of emerging technologies and innovation in order to
manage security issues and threats in big data. In addition, the research covers the challenges and issues
involved with the use of emerging technologies and innovation in research.
2. MATERIAL & METHODS
Research methodology is the procedure of doing systematic approach for solving research issues. It is the
way of explaining, exploring as well as making prediction of research phenomena. In the present research,
several methodological tools such as research philosophy, approach and design strategies as well as data
collection methods and selects the appropriate ones.
A. Data Collection
There are generally two types of data collection process such as primary and secondary data collection
method. Secondary data are collected from journals, book and several websites. On the other hand, primary
data are collected through quantitative as well as qualitative method [12]. In this perspective, the researcher
has selected quantitative method as preferred research for the research. In order to collect raw data
regarding the role of emerging technologies in managing security issues and threats in big data, the
researcher has made close-ended questionnaire, where engineers and experts involved with the
development and application of emerging technologies are asked to answer the question regarding the
impact of emerging technologies on managing security issues and threats in big data.
B. Data Inclusion Criteria
An inclusion criterion is one of the characteristics that prospective subjects need to be included in the
study. Inclusion criteria and exclusion criteria ensure appropriateness of the study. In the present study,
data from different secondary sources like books, journals and websites are gathered that are discussed in
literature review chapter of the research. Data are filtered through inclusion criteria such as language and
the year of publication. The articles that are in English language written and published after 2013 are
selected in the research.
Table 1: Selected Attribute Description
Attribute Name Data
Type
Description
A. R. Mavlyutov and P.
Cudre-Mauroux,
"Managing Big
Interval Data with
CINTIA: the
Checkpoint
INTerval
Array", IEEE
Transactions on
Secondary
data
Article has published in 2017,
Written n English
components, which are mainly keeps pace with the volume of malware having new strains created daily.
On the other hand, lack of stability helps managing of the identities and applications and data with the
products with serious scalability narrowing down the security analysis into sub set event.
Section 6: Aim of your research
The aim of the research is to critically analyze the role of emerging technologies and innovation in order to
manage security issues and threats in big data. In addition, the research covers the challenges and issues
involved with the use of emerging technologies and innovation in research.
2. MATERIAL & METHODS
Research methodology is the procedure of doing systematic approach for solving research issues. It is the
way of explaining, exploring as well as making prediction of research phenomena. In the present research,
several methodological tools such as research philosophy, approach and design strategies as well as data
collection methods and selects the appropriate ones.
A. Data Collection
There are generally two types of data collection process such as primary and secondary data collection
method. Secondary data are collected from journals, book and several websites. On the other hand, primary
data are collected through quantitative as well as qualitative method [12]. In this perspective, the researcher
has selected quantitative method as preferred research for the research. In order to collect raw data
regarding the role of emerging technologies in managing security issues and threats in big data, the
researcher has made close-ended questionnaire, where engineers and experts involved with the
development and application of emerging technologies are asked to answer the question regarding the
impact of emerging technologies on managing security issues and threats in big data.
B. Data Inclusion Criteria
An inclusion criterion is one of the characteristics that prospective subjects need to be included in the
study. Inclusion criteria and exclusion criteria ensure appropriateness of the study. In the present study,
data from different secondary sources like books, journals and websites are gathered that are discussed in
literature review chapter of the research. Data are filtered through inclusion criteria such as language and
the year of publication. The articles that are in English language written and published after 2013 are
selected in the research.
Table 1: Selected Attribute Description
Attribute Name Data
Type
Description
A. R. Mavlyutov and P.
Cudre-Mauroux,
"Managing Big
Interval Data with
CINTIA: the
Checkpoint
INTerval
Array", IEEE
Transactions on
Secondary
data
Article has published in 2017,
Written n English
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Big Data, pp. 1-1,
2017.
[4] J. Moreno, M.
Serrano and E.
Fernández-Medina,
"Main Issues in Big
Data Security", Future
Internet, vol. 8, no. 3, p.
44, 2016.
Secondary
data
Article has published in 2016,
Written n English
C. Data Analysis
The accumulated quantitative data about the role of emerging technologies for managing natural disaster
has analyzed with the help of quantitative data analysis. The data are presented in table and graph format
whereas statistical data analysis has been conducted with the help of excel sheet. Thus, excel sheet has been
considered as preferred tool for testing of the research aim.
III RESULTS
In this section of study, WH questions are forwarded to 75 engineers and experts related to the emerging
technologies and innovation for managing security issues and threats in big data. Hence, in order to
perform such analysis a survey has been conducted. The accumulated data are analyzed with the help of
statistical analysis.
Statistical analysis
Q1. How far you agree that current emerging technologies and innovation are able to manage security
issues and threats in big data?
Options Frequency % Total frequency Total respondents
Strongly agreed 33.33% 25 75
Agreed 26.66% 20 75
Neutral 6.67% 5 75
Disagreed 20%10 15 75
Strongly disagreed 13.33% 10 75
Table 2: Emerging technologies in managing security issues and threats in big data
Q2. What are the technologies used mostly for managing security issues and threats in big data?
Options Frequency % Total frequency Total respondents
GPS 20%10 15 75
Remote sensing 20%10 15 75
Internet 26.66% 20 75
Warning system 16% 12 75
Forecasting system 17.33% 13 75
2017.
[4] J. Moreno, M.
Serrano and E.
Fernández-Medina,
"Main Issues in Big
Data Security", Future
Internet, vol. 8, no. 3, p.
44, 2016.
Secondary
data
Article has published in 2016,
Written n English
C. Data Analysis
The accumulated quantitative data about the role of emerging technologies for managing natural disaster
has analyzed with the help of quantitative data analysis. The data are presented in table and graph format
whereas statistical data analysis has been conducted with the help of excel sheet. Thus, excel sheet has been
considered as preferred tool for testing of the research aim.
III RESULTS
In this section of study, WH questions are forwarded to 75 engineers and experts related to the emerging
technologies and innovation for managing security issues and threats in big data. Hence, in order to
perform such analysis a survey has been conducted. The accumulated data are analyzed with the help of
statistical analysis.
Statistical analysis
Q1. How far you agree that current emerging technologies and innovation are able to manage security
issues and threats in big data?
Options Frequency % Total frequency Total respondents
Strongly agreed 33.33% 25 75
Agreed 26.66% 20 75
Neutral 6.67% 5 75
Disagreed 20%10 15 75
Strongly disagreed 13.33% 10 75
Table 2: Emerging technologies in managing security issues and threats in big data
Q2. What are the technologies used mostly for managing security issues and threats in big data?
Options Frequency % Total frequency Total respondents
GPS 20%10 15 75
Remote sensing 20%10 15 75
Internet 26.66% 20 75
Warning system 16% 12 75
Forecasting system 17.33% 13 75
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
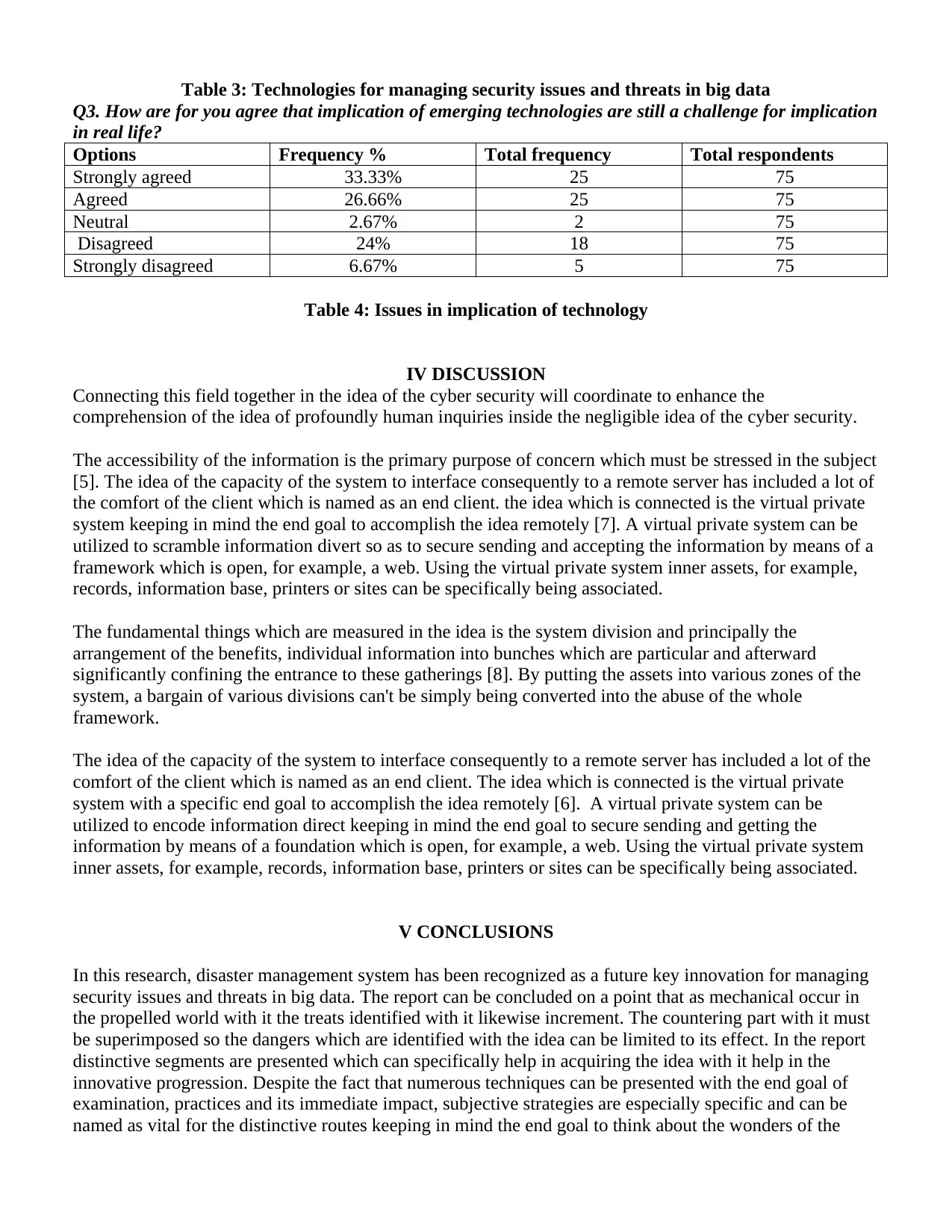
Table 3: Technologies for managing security issues and threats in big data
Q3. How are for you agree that implication of emerging technologies are still a challenge for implication
in real life?
Options Frequency % Total frequency Total respondents
Strongly agreed 33.33% 25 75
Agreed 26.66% 25 75
Neutral 2.67% 2 75
Disagreed 24% 18 75
Strongly disagreed 6.67% 5 75
Table 4: Issues in implication of technology
IV DISCUSSION
Connecting this field together in the idea of the cyber security will coordinate to enhance the
comprehension of the idea of profoundly human inquiries inside the negligible idea of the cyber security.
The accessibility of the information is the primary purpose of concern which must be stressed in the subject
[5]. The idea of the capacity of the system to interface consequently to a remote server has included a lot of
the comfort of the client which is named as an end client. the idea which is connected is the virtual private
system keeping in mind the end goal to accomplish the idea remotely [7]. A virtual private system can be
utilized to scramble information divert so as to secure sending and accepting the information by means of a
framework which is open, for example, a web. Using the virtual private system inner assets, for example,
records, information base, printers or sites can be specifically being associated.
The fundamental things which are measured in the idea is the system division and principally the
arrangement of the benefits, individual information into bunches which are particular and afterward
significantly confining the entrance to these gatherings [8]. By putting the assets into various zones of the
system, a bargain of various divisions can't be simply being converted into the abuse of the whole
framework.
The idea of the capacity of the system to interface consequently to a remote server has included a lot of the
comfort of the client which is named as an end client. The idea which is connected is the virtual private
system with a specific end goal to accomplish the idea remotely [6]. A virtual private system can be
utilized to encode information direct keeping in mind the end goal to secure sending and getting the
information by means of a foundation which is open, for example, a web. Using the virtual private system
inner assets, for example, records, information base, printers or sites can be specifically being associated.
V CONCLUSIONS
In this research, disaster management system has been recognized as a future key innovation for managing
security issues and threats in big data. The report can be concluded on a point that as mechanical occur in
the propelled world with it the treats identified with it likewise increment. The countering part with it must
be superimposed so the dangers which are identified with the idea can be limited to its effect. In the report
distinctive segments are presented which can specifically help in acquiring the idea with it help in the
innovative progression. Despite the fact that numerous techniques can be presented with the end goal of
examination, practices and its immediate impact, subjective strategies are especially specific and can be
named as vital for the distinctive routes keeping in mind the end goal to think about the wonders of the
Q3. How are for you agree that implication of emerging technologies are still a challenge for implication
in real life?
Options Frequency % Total frequency Total respondents
Strongly agreed 33.33% 25 75
Agreed 26.66% 25 75
Neutral 2.67% 2 75
Disagreed 24% 18 75
Strongly disagreed 6.67% 5 75
Table 4: Issues in implication of technology
IV DISCUSSION
Connecting this field together in the idea of the cyber security will coordinate to enhance the
comprehension of the idea of profoundly human inquiries inside the negligible idea of the cyber security.
The accessibility of the information is the primary purpose of concern which must be stressed in the subject
[5]. The idea of the capacity of the system to interface consequently to a remote server has included a lot of
the comfort of the client which is named as an end client. the idea which is connected is the virtual private
system keeping in mind the end goal to accomplish the idea remotely [7]. A virtual private system can be
utilized to scramble information divert so as to secure sending and accepting the information by means of a
framework which is open, for example, a web. Using the virtual private system inner assets, for example,
records, information base, printers or sites can be specifically being associated.
The fundamental things which are measured in the idea is the system division and principally the
arrangement of the benefits, individual information into bunches which are particular and afterward
significantly confining the entrance to these gatherings [8]. By putting the assets into various zones of the
system, a bargain of various divisions can't be simply being converted into the abuse of the whole
framework.
The idea of the capacity of the system to interface consequently to a remote server has included a lot of the
comfort of the client which is named as an end client. The idea which is connected is the virtual private
system with a specific end goal to accomplish the idea remotely [6]. A virtual private system can be
utilized to encode information direct keeping in mind the end goal to secure sending and getting the
information by means of a foundation which is open, for example, a web. Using the virtual private system
inner assets, for example, records, information base, printers or sites can be specifically being associated.
V CONCLUSIONS
In this research, disaster management system has been recognized as a future key innovation for managing
security issues and threats in big data. The report can be concluded on a point that as mechanical occur in
the propelled world with it the treats identified with it likewise increment. The countering part with it must
be superimposed so the dangers which are identified with the idea can be limited to its effect. In the report
distinctive segments are presented which can specifically help in acquiring the idea with it help in the
innovative progression. Despite the fact that numerous techniques can be presented with the end goal of
examination, practices and its immediate impact, subjective strategies are especially specific and can be
named as vital for the distinctive routes keeping in mind the end goal to think about the wonders of the
digital security perspective. The exploration forthcoming with a specific end goal to know the distinctive
perspective identified with the case can incorporate human PC connection (HCI), esteem and outline,
advanced and data proficiency, designing morals and decent variety and consideration. Connecting these
entire field together in the idea of the cyber security will coordinate enhance the comprehension of the idea
of profoundly human inquiries inside the minor idea of the digital security.
REFERENCES
[1]P. Kaur and A. Monga, "Managing Big Data: A Step towards Huge Data Security", International
Journal of Wireless and Microwave Technologies, vol. 6, no. 2, pp. 10-20, 2016.
[2]R. Kemp, "Legal aspects of managing Big Data", Computer Law & Security Review, vol. 30, no. 5, pp.
482-491, 2014.
[3]X. Ma and D. Wu, "Research on Information Security Issues Facing the Era of Big Data", Applied
Mechanics and Materials, vol. 651-653, pp. 1913-1916, 2014.
[4]J. Moreno, M. Serrano and E. Fernández-Medina, "Main Issues in Big Data Security", Future Internet,
vol. 8, no. 3, p. 44, 2016.
[5]R. Mavlyutov and P. Cudre-Mauroux, "Managing Big Interval Data with CINTIA: the Checkpoint
INTerval Array", IEEE Transactions on Big Data, pp. 1-1, 2017.
[6]A. Gholami and E. Laure, "Big Data Security and Privacy Issues in the CLOUD", International Journal
of Network Security & Its Applications, vol. 8, no. 1, pp. 59-79, 2016.
[7]Big Data. Swindon: BCS Learning & Development Limited, 2014.
[8]S. Soares, IBM InfoSphere. Ketchum: M C Press, 2013.
[9]C. Bennett and R. Grant, Visions of Privacy. Toronto: University of Toronto Press, 2016.
[10]S. Yu, X. Lin, J. Mišić and X. Shen, Networking for big data. .
[11]F. García M árquez and B. Lev, Big data management. .
[12]A. Fletcher, "Applying critical realism in qualitative research: methodology meets
method", International Journal of Social Research Methodology, vol. 20, no. 2, pp. 181-194, 2016.
Appendix (if needed)
Main activities/ stages 1st
week
2nd
week
3rd
week
4th
week
5th
week
6th week
Topic Selection
Data collection from secondary
sources
Framing layout of the research
Literature review
Formation of the research Plan
perspective identified with the case can incorporate human PC connection (HCI), esteem and outline,
advanced and data proficiency, designing morals and decent variety and consideration. Connecting these
entire field together in the idea of the cyber security will coordinate enhance the comprehension of the idea
of profoundly human inquiries inside the minor idea of the digital security.
REFERENCES
[1]P. Kaur and A. Monga, "Managing Big Data: A Step towards Huge Data Security", International
Journal of Wireless and Microwave Technologies, vol. 6, no. 2, pp. 10-20, 2016.
[2]R. Kemp, "Legal aspects of managing Big Data", Computer Law & Security Review, vol. 30, no. 5, pp.
482-491, 2014.
[3]X. Ma and D. Wu, "Research on Information Security Issues Facing the Era of Big Data", Applied
Mechanics and Materials, vol. 651-653, pp. 1913-1916, 2014.
[4]J. Moreno, M. Serrano and E. Fernández-Medina, "Main Issues in Big Data Security", Future Internet,
vol. 8, no. 3, p. 44, 2016.
[5]R. Mavlyutov and P. Cudre-Mauroux, "Managing Big Interval Data with CINTIA: the Checkpoint
INTerval Array", IEEE Transactions on Big Data, pp. 1-1, 2017.
[6]A. Gholami and E. Laure, "Big Data Security and Privacy Issues in the CLOUD", International Journal
of Network Security & Its Applications, vol. 8, no. 1, pp. 59-79, 2016.
[7]Big Data. Swindon: BCS Learning & Development Limited, 2014.
[8]S. Soares, IBM InfoSphere. Ketchum: M C Press, 2013.
[9]C. Bennett and R. Grant, Visions of Privacy. Toronto: University of Toronto Press, 2016.
[10]S. Yu, X. Lin, J. Mišić and X. Shen, Networking for big data. .
[11]F. García M árquez and B. Lev, Big data management. .
[12]A. Fletcher, "Applying critical realism in qualitative research: methodology meets
method", International Journal of Social Research Methodology, vol. 20, no. 2, pp. 181-194, 2016.
Appendix (if needed)
Main activities/ stages 1st
week
2nd
week
3rd
week
4th
week
5th
week
6th week
Topic Selection
Data collection from secondary
sources
Framing layout of the research
Literature review
Formation of the research Plan
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Selection of the Appropriate
Research Techniques
Primary data collection
Analysis & Interpretation of
Data Collection
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
Research Techniques
Primary data collection
Analysis & Interpretation of
Data Collection
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
![Cyber Security Research Paper Abstract - [University] - [Course Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fbd%2F04151bc652ee49f480e5594ea23a69c7.jpg&w=256&q=75)




