Mobile Cloud Computing Security: Implementation & Technologies
VerifiedAdded on 2023/06/10
|16
|2709
|322
Project
AI Summary
This project focuses on the implementation of cloud security measures within a mobile cloud computing environment, particularly for educational purposes. It highlights the importance of mobile cloud computing in areas lacking internet service providers and emphasizes the necessity of security measures to ensure data availability, integrity, and confidentiality. The project includes a review of existing literature, detailing prior work in mobile cloud web server creation and ad hoc network configurations. It outlines the tools and procedures involved in replicating a mobile computing environment, configuring security measures, and deploying a prototype educational tool. Furthermore, it provides a risk analysis, identifying potential threats from both cloud customer and provider perspectives, along with mitigation techniques. The project also includes a work breakdown structure, timeline, and Gantt chart to illustrate the project's progression and key milestones.

Running Head: EMERGING TECHNOLOGIES AND INNOVATIONS
Implementation of Cloud Security
[Name of the student]
[Name of the University]
[Author note]
Implementation of Cloud Security
[Name of the student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1EMERGING TECHNOLOGIES AND INNOVATIONS
Table of Contents
Introduction:....................................................................................................................................2
Importance of the project:................................................................................................................2
Data collection:................................................................................................................................3
Tools used:...................................................................................................................................4
Procedure:....................................................................................................................................4
Risk analysis:...................................................................................................................................5
Risk Matrix:.................................................................................................................................8
Work Breakdown Structure...........................................................................................................10
Timeline.........................................................................................................................................10
Gantt chart.....................................................................................................................................12
Conclusion:....................................................................................................................................12
References:....................................................................................................................................14
Table of Contents
Introduction:....................................................................................................................................2
Importance of the project:................................................................................................................2
Data collection:................................................................................................................................3
Tools used:...................................................................................................................................4
Procedure:....................................................................................................................................4
Risk analysis:...................................................................................................................................5
Risk Matrix:.................................................................................................................................8
Work Breakdown Structure...........................................................................................................10
Timeline.........................................................................................................................................10
Gantt chart.....................................................................................................................................12
Conclusion:....................................................................................................................................12
References:....................................................................................................................................14

2EMERGING TECHNOLOGIES AND INNOVATIONS
Introduction:
Cloud computing is associated with allowing the users to share the information without
investment of too much money in the resources which are under use. It is possible for one to
access the data in a remote way which are present in the servers. Mobile Cloud computing is
considered to be a filed which involves the usage of the mobile devices (Rittinghouse &
Ransome, 2016). There exists move to make use of mobile devices which are having the
capability of delivering a cloud computing services in an ad hoc configuration which would not
be associated with the usage of data centers of large size. This turns out to be very helpful in the
certain situations which might include the locations without an internet provider. The main aim
of this project is to demonstrate the application of an educational use scenario where certain
security measures are to be identified which are necessary for the purpose of delivering contents
related to education in a mobile cloud computing environment.
Importance of the project:
Mobile computing acts as a very useful cloud computing environment where there exists
no internet service providers. In order to make the cloud much more practical it is very necessary
to include the security measures. K12 along with the higher education requires so essential
security measures so as to have a guaranteed delivery, availability of the information and
confidentiality of each and every participants taking part in the virtual educational environment
(Zhang et al., 2017). Due to this reason it is very necessary to identify the hardware along with
the software technology which are necessary in order to assure the fact that authentic educational
contents along with the privacy of the users personal data are maintained.
Introduction:
Cloud computing is associated with allowing the users to share the information without
investment of too much money in the resources which are under use. It is possible for one to
access the data in a remote way which are present in the servers. Mobile Cloud computing is
considered to be a filed which involves the usage of the mobile devices (Rittinghouse &
Ransome, 2016). There exists move to make use of mobile devices which are having the
capability of delivering a cloud computing services in an ad hoc configuration which would not
be associated with the usage of data centers of large size. This turns out to be very helpful in the
certain situations which might include the locations without an internet provider. The main aim
of this project is to demonstrate the application of an educational use scenario where certain
security measures are to be identified which are necessary for the purpose of delivering contents
related to education in a mobile cloud computing environment.
Importance of the project:
Mobile computing acts as a very useful cloud computing environment where there exists
no internet service providers. In order to make the cloud much more practical it is very necessary
to include the security measures. K12 along with the higher education requires so essential
security measures so as to have a guaranteed delivery, availability of the information and
confidentiality of each and every participants taking part in the virtual educational environment
(Zhang et al., 2017). Due to this reason it is very necessary to identify the hardware along with
the software technology which are necessary in order to assure the fact that authentic educational
contents along with the privacy of the users personal data are maintained.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3EMERGING TECHNOLOGIES AND INNOVATIONS
Data collection:
The collection of the data has been done by from the various literary work that has been
done in the past. After reviewing of the literary work on this particular topic certain crucial facts
had been noted which helped a lot in understanding the significance of this proposed research
work. Below are the literary works which have been reviewed in order to complete the process of
collecting the data:
Fuller, (2012) at Norflok State University in his master’s thesis stated that two devices
belonging to android platform were used for the purpose of creating a mobile cloud web server
and storage environment. This was doen for the purpose of demonstrating the feasibility of the
mobile cloud computing environment. This initially proved the fact that it is possible to use the
mobile devices for the purpose of setting up a mobile cloud server (Meng, 2017).
Huerta-Canepa and Lee, (2010) was associated with developing a mobile cloud network
configuration which consisted of a user that is placed in a fixed location. In case when there is a
requirement of computing task but there existed insufficient amount of resources then the system
would be listened for an ad hoc node present in the current vicinity. However it was seen that the
research project did not required the user to be present in a fixed location and it also
demonstrated the fact that there exists various advantages of being located in various places
while using the mobile computing environment (Jiang, Ma & Wei, 2016).
There exists some great benefits of education in the mobile computing environment. For
the purpose of measuring the scalability it is necessary to deploy the mobile cloud computing
and scaling is to be done so as to make sure that the demands of the users are meet which are
totally unpredictable because of the flexible nature of the resource provisioning (Hashem et al.,
Data collection:
The collection of the data has been done by from the various literary work that has been
done in the past. After reviewing of the literary work on this particular topic certain crucial facts
had been noted which helped a lot in understanding the significance of this proposed research
work. Below are the literary works which have been reviewed in order to complete the process of
collecting the data:
Fuller, (2012) at Norflok State University in his master’s thesis stated that two devices
belonging to android platform were used for the purpose of creating a mobile cloud web server
and storage environment. This was doen for the purpose of demonstrating the feasibility of the
mobile cloud computing environment. This initially proved the fact that it is possible to use the
mobile devices for the purpose of setting up a mobile cloud server (Meng, 2017).
Huerta-Canepa and Lee, (2010) was associated with developing a mobile cloud network
configuration which consisted of a user that is placed in a fixed location. In case when there is a
requirement of computing task but there existed insufficient amount of resources then the system
would be listened for an ad hoc node present in the current vicinity. However it was seen that the
research project did not required the user to be present in a fixed location and it also
demonstrated the fact that there exists various advantages of being located in various places
while using the mobile computing environment (Jiang, Ma & Wei, 2016).
There exists some great benefits of education in the mobile computing environment. For
the purpose of measuring the scalability it is necessary to deploy the mobile cloud computing
and scaling is to be done so as to make sure that the demands of the users are meet which are
totally unpredictable because of the flexible nature of the resource provisioning (Hashem et al.,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4EMERGING TECHNOLOGIES AND INNOVATIONS
2015). It is possible for the service providers to expand and add an application or a service not
having or having a little amount of constraint on the message collected from the resource. One of
the example of is the involvement of the mobile cloud computing in the learning process which
is known as “Cornucopia” which has been put into action for the researchers of the
undergraduate students belonging to the field of genetics and another example is the “Plantations
Pathfinder” Which is specially designed for the purpose of supplying information and also for
the purpose of providing a collaborative space for the persons visiting the gardens.
Development of another mobile cloud computing education model was also done in which
the tutors are capable of putting tutorials for the students in the clouds so as to help out the
students. This similar concept can also be utilized in projects of this kind where testing of the
security is going to be done in the cloud deployed for the people who are associated with the
usage of cloud from outside.
Methods and timeline:
Tools used:
The project would be requiring certain tools which includes an Android Smartphone and
an Android tablet. The software that is to be used along with this is the Serverman and the
WebDAV. The main reason for choosing this two software is because of the fact that this
software are easily available in the android market along with being available for the other
mobile devices as well.
Procedure:
Replication of the mobile computing environment would be done by installation of the
Serversman on the phone that is to be used by the user and the WebDEV is to be installed on the
2015). It is possible for the service providers to expand and add an application or a service not
having or having a little amount of constraint on the message collected from the resource. One of
the example of is the involvement of the mobile cloud computing in the learning process which
is known as “Cornucopia” which has been put into action for the researchers of the
undergraduate students belonging to the field of genetics and another example is the “Plantations
Pathfinder” Which is specially designed for the purpose of supplying information and also for
the purpose of providing a collaborative space for the persons visiting the gardens.
Development of another mobile cloud computing education model was also done in which
the tutors are capable of putting tutorials for the students in the clouds so as to help out the
students. This similar concept can also be utilized in projects of this kind where testing of the
security is going to be done in the cloud deployed for the people who are associated with the
usage of cloud from outside.
Methods and timeline:
Tools used:
The project would be requiring certain tools which includes an Android Smartphone and
an Android tablet. The software that is to be used along with this is the Serverman and the
WebDAV. The main reason for choosing this two software is because of the fact that this
software are easily available in the android market along with being available for the other
mobile devices as well.
Procedure:
Replication of the mobile computing environment would be done by installation of the
Serversman on the phone that is to be used by the user and the WebDEV is to be installed on the
5EMERGING TECHNOLOGIES AND INNOVATIONS
tablet of the user which is to be followed by linking of the latter program with the former one.
Once the initial setup is completed the security measures are to be configured in the mobile
computing environment. Followed by this deploying of a prototype educational tool is to be done
in the mobile cloud computing environment. Lastly the various actions are to be tested on the
two mobile cloud computing devices which would be documented.
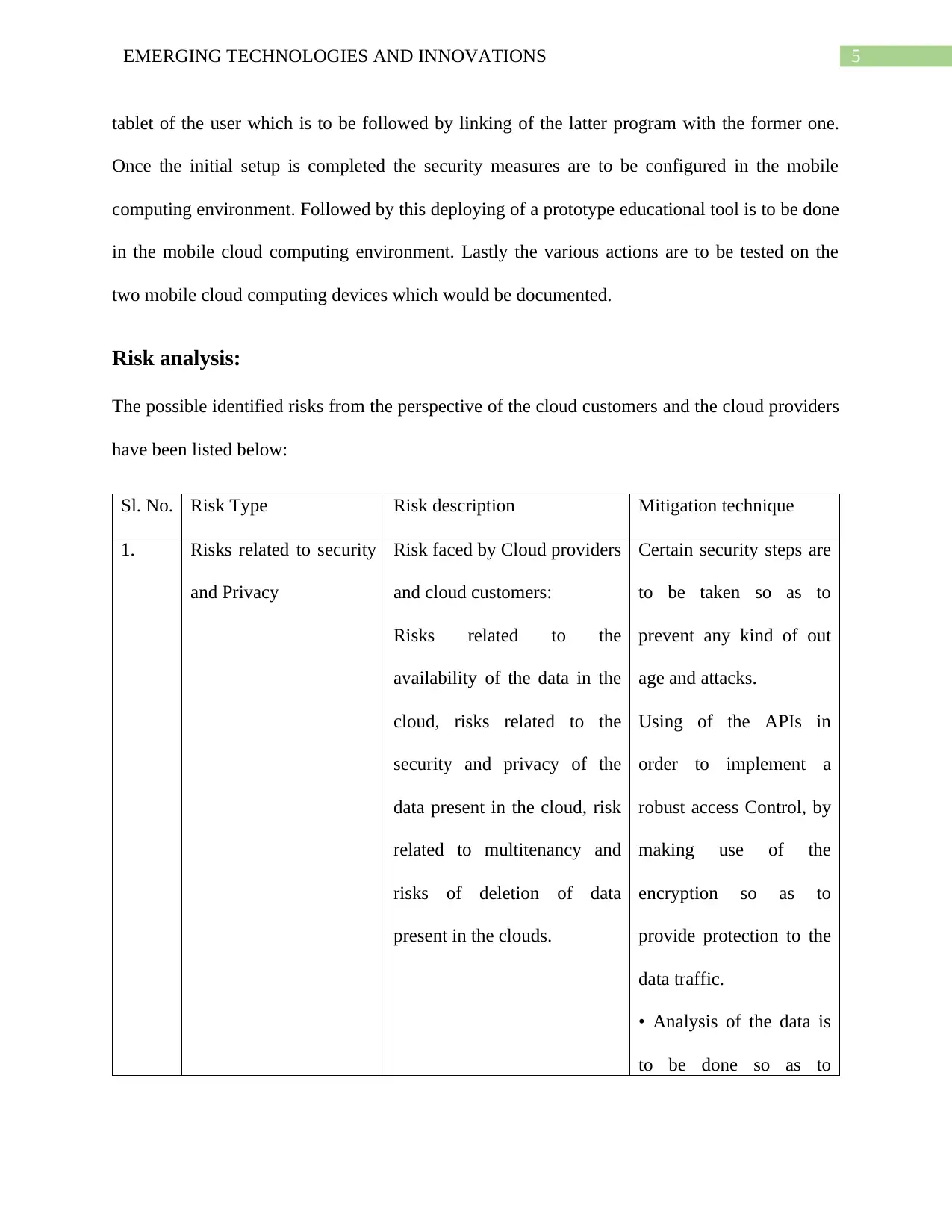
Risk analysis:
The possible identified risks from the perspective of the cloud customers and the cloud providers
have been listed below:
Sl. No. Risk Type Risk description Mitigation technique
1. Risks related to security
and Privacy
Risk faced by Cloud providers
and cloud customers:
Risks related to the
availability of the data in the
cloud, risks related to the
security and privacy of the
data present in the cloud, risk
related to multitenancy and
risks of deletion of data
present in the clouds.
Certain security steps are
to be taken so as to
prevent any kind of out
age and attacks.
Using of the APIs in
order to implement a
robust access Control, by
making use of the
encryption so as to
provide protection to the
data traffic.
• Analysis of the data is
to be done so as to
tablet of the user which is to be followed by linking of the latter program with the former one.
Once the initial setup is completed the security measures are to be configured in the mobile
computing environment. Followed by this deploying of a prototype educational tool is to be done
in the mobile cloud computing environment. Lastly the various actions are to be tested on the
two mobile cloud computing devices which would be documented.
Risk analysis:
The possible identified risks from the perspective of the cloud customers and the cloud providers
have been listed below:
Sl. No. Risk Type Risk description Mitigation technique
1. Risks related to security
and Privacy
Risk faced by Cloud providers
and cloud customers:
Risks related to the
availability of the data in the
cloud, risks related to the
security and privacy of the
data present in the cloud, risk
related to multitenancy and
risks of deletion of data
present in the clouds.
Certain security steps are
to be taken so as to
prevent any kind of out
age and attacks.
Using of the APIs in
order to implement a
robust access Control, by
making use of the
encryption so as to
provide protection to the
data traffic.
• Analysis of the data is
to be done so as to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6EMERGING TECHNOLOGIES AND INNOVATIONS
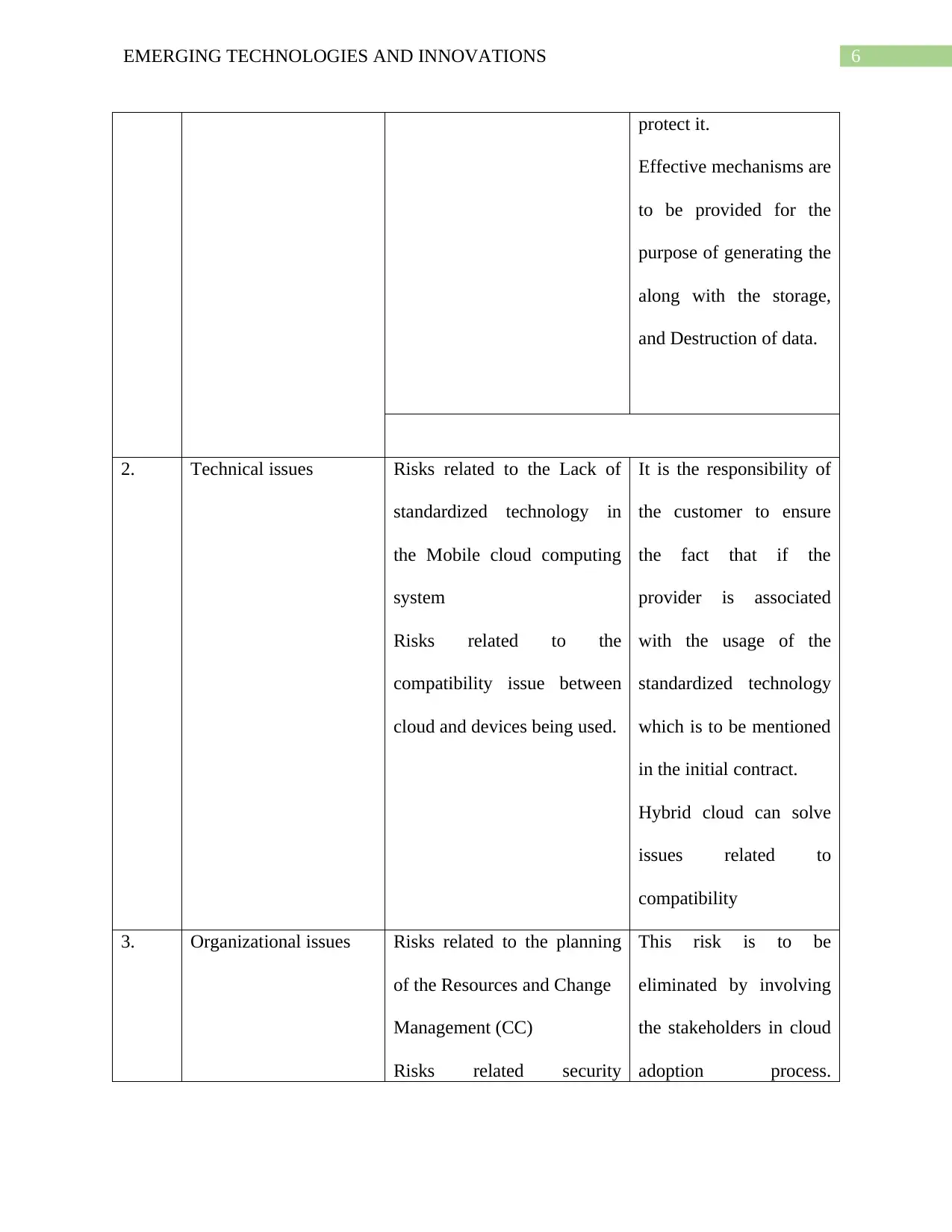
protect it.
Effective mechanisms are
to be provided for the
purpose of generating the
along with the storage,
and Destruction of data.
2. Technical issues Risks related to the Lack of
standardized technology in
the Mobile cloud computing
system
Risks related to the
compatibility issue between
cloud and devices being used.
It is the responsibility of
the customer to ensure
the fact that if the
provider is associated
with the usage of the
standardized technology
which is to be mentioned
in the initial contract.
Hybrid cloud can solve
issues related to
compatibility
3. Organizational issues Risks related to the planning
of the Resources and Change
Management (CC)
Risks related security
This risk is to be
eliminated by involving
the stakeholders in cloud
adoption process.
protect it.
Effective mechanisms are
to be provided for the
purpose of generating the
along with the storage,
and Destruction of data.
2. Technical issues Risks related to the Lack of
standardized technology in
the Mobile cloud computing
system
Risks related to the
compatibility issue between
cloud and devices being used.
It is the responsibility of
the customer to ensure
the fact that if the
provider is associated
with the usage of the
standardized technology
which is to be mentioned
in the initial contract.
Hybrid cloud can solve
issues related to
compatibility
3. Organizational issues Risks related to the planning
of the Resources and Change
Management (CC)
Risks related security
This risk is to be
eliminated by involving
the stakeholders in cloud
adoption process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7EMERGING TECHNOLOGIES AND INNOVATIONS
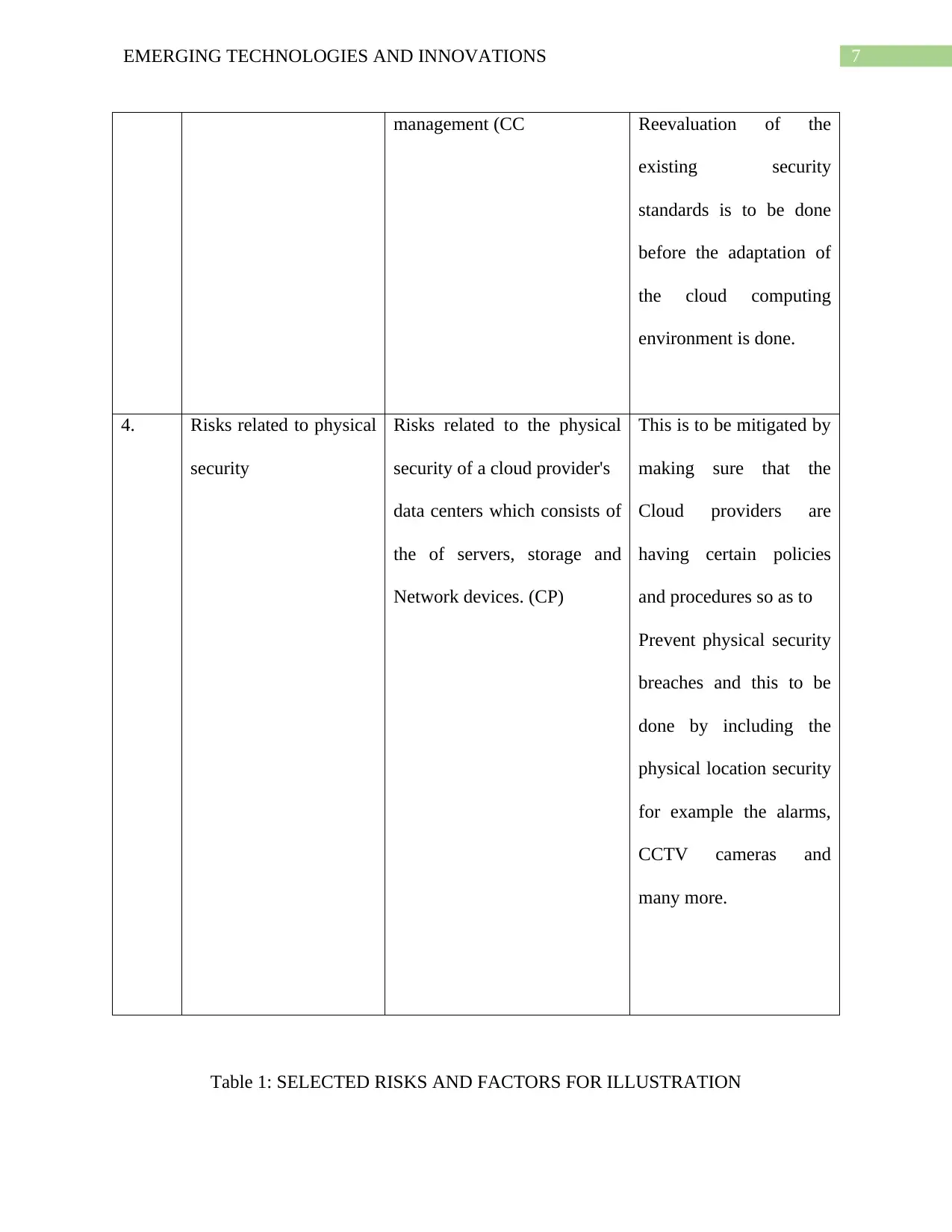
management (CC Reevaluation of the
existing security
standards is to be done
before the adaptation of
the cloud computing
environment is done.
4. Risks related to physical
security
Risks related to the physical
security of a cloud provider's
data centers which consists of
the of servers, storage and
Network devices. (CP)
This is to be mitigated by
making sure that the
Cloud providers are
having certain policies
and procedures so as to
Prevent physical security
breaches and this to be
done by including the
physical location security
for example the alarms,
CCTV cameras and
many more.
Table 1: SELECTED RISKS AND FACTORS FOR ILLUSTRATION
management (CC Reevaluation of the
existing security
standards is to be done
before the adaptation of
the cloud computing
environment is done.
4. Risks related to physical
security
Risks related to the physical
security of a cloud provider's
data centers which consists of
the of servers, storage and
Network devices. (CP)
This is to be mitigated by
making sure that the
Cloud providers are
having certain policies
and procedures so as to
Prevent physical security
breaches and this to be
done by including the
physical location security
for example the alarms,
CCTV cameras and
many more.
Table 1: SELECTED RISKS AND FACTORS FOR ILLUSTRATION
8EMERGING TECHNOLOGIES AND INNOVATIONS
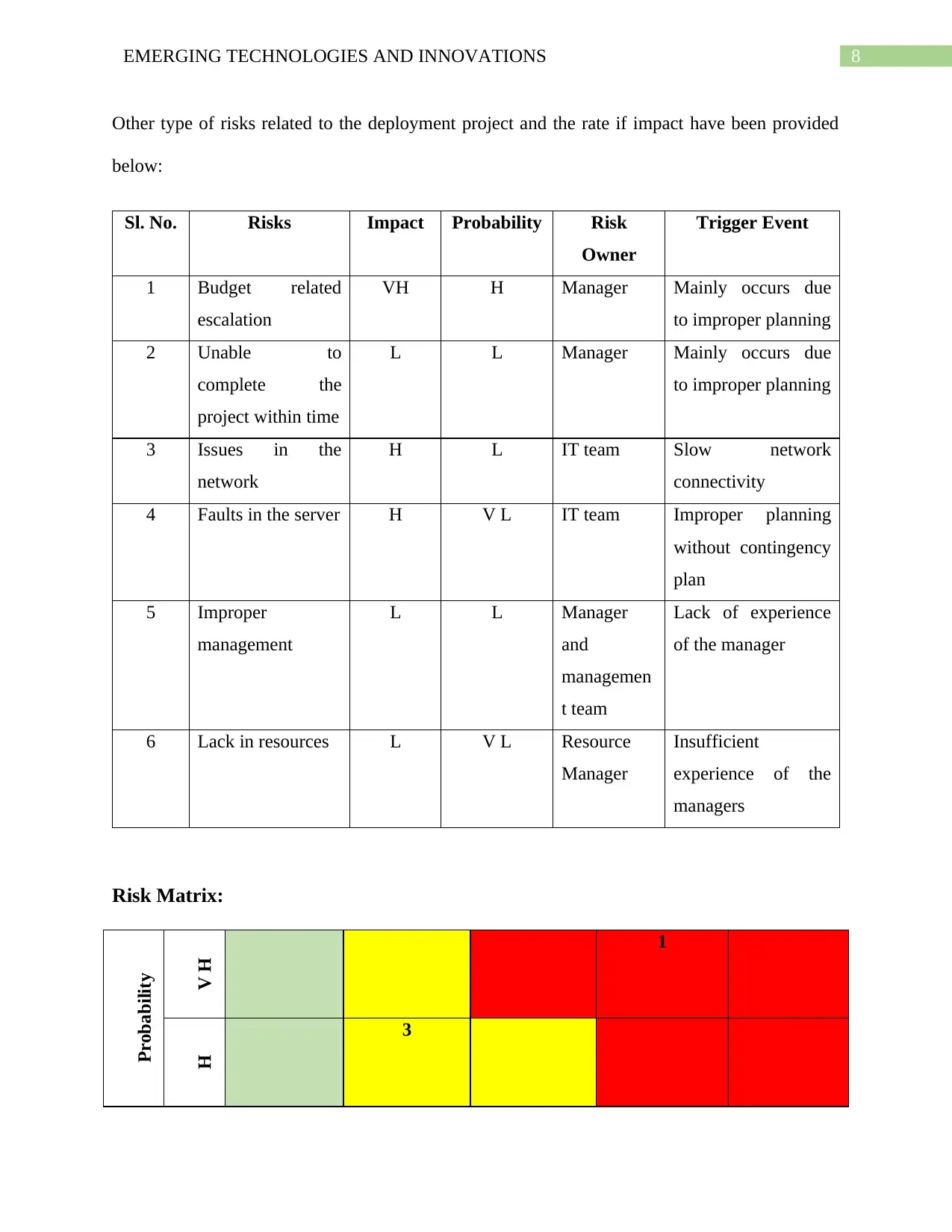
Other type of risks related to the deployment project and the rate if impact have been provided
below:
Sl. No. Risks Impact Probability Risk
Owner
Trigger Event
1 Budget related
escalation
VH H Manager Mainly occurs due
to improper planning
2 Unable to
complete the
project within time
L L Manager Mainly occurs due
to improper planning
3 Issues in the
network
H L IT team Slow network
connectivity
4 Faults in the server H V L IT team Improper planning
without contingency
plan
5 Improper
management
L L Manager
and
managemen
t team
Lack of experience
of the manager
6 Lack in resources L V L Resource
Manager
Insufficient
experience of the
managers
Risk Matrix:
Probability
V H 1
H
3
Other type of risks related to the deployment project and the rate if impact have been provided
below:
Sl. No. Risks Impact Probability Risk
Owner
Trigger Event
1 Budget related
escalation
VH H Manager Mainly occurs due
to improper planning
2 Unable to
complete the
project within time
L L Manager Mainly occurs due
to improper planning
3 Issues in the
network
H L IT team Slow network
connectivity
4 Faults in the server H V L IT team Improper planning
without contingency
plan
5 Improper
management
L L Manager
and
managemen
t team
Lack of experience
of the manager
6 Lack in resources L V L Resource
Manager
Insufficient
experience of the
managers
Risk Matrix:
Probability
V H 1
H
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
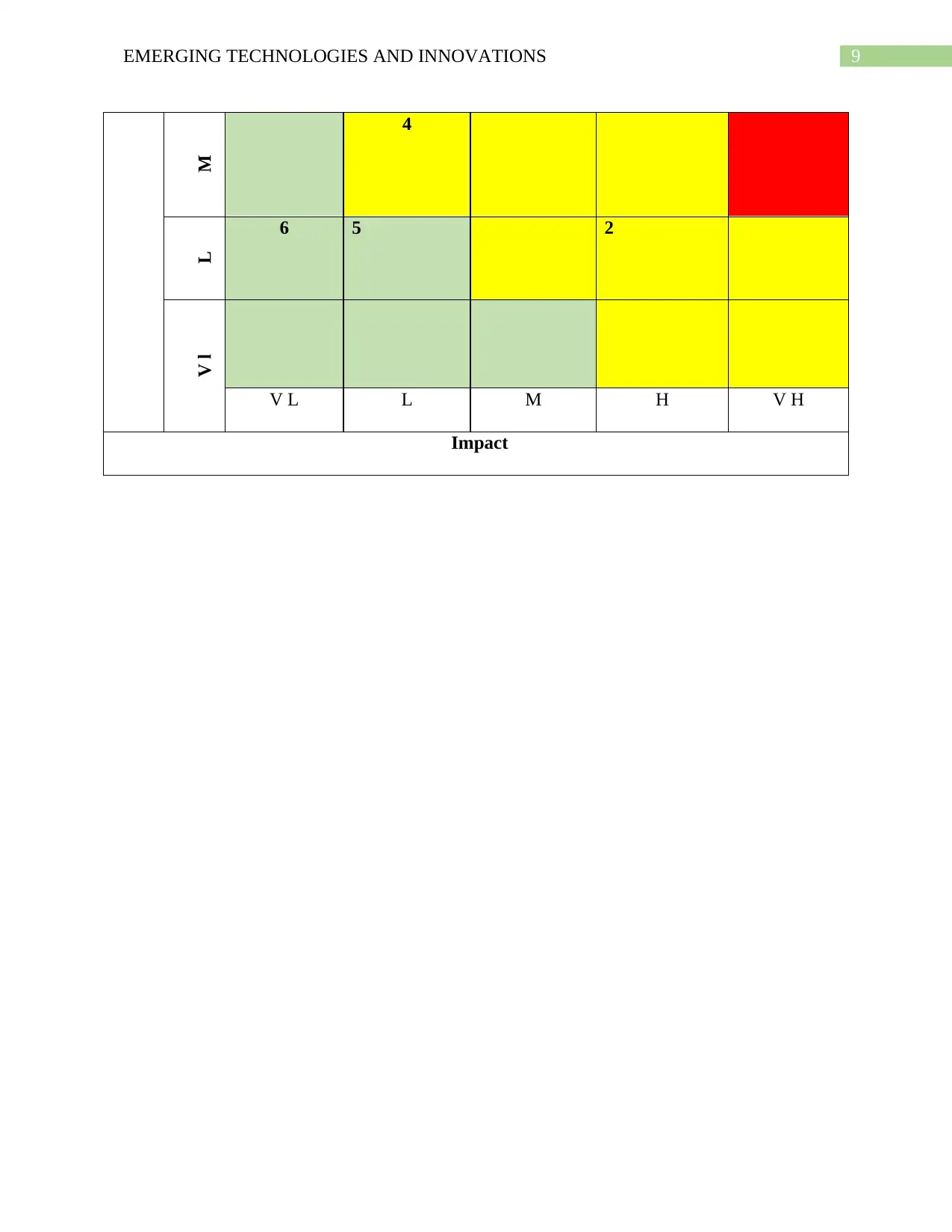
9EMERGING TECHNOLOGIES AND INNOVATIONS
M
4
L 6 5 2
V l
V L L M H V H
Impact
M
4
L 6 5 2
V l
V L L M H V H
Impact
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10EMERGING TECHNOLOGIES AND INNOVATIONS
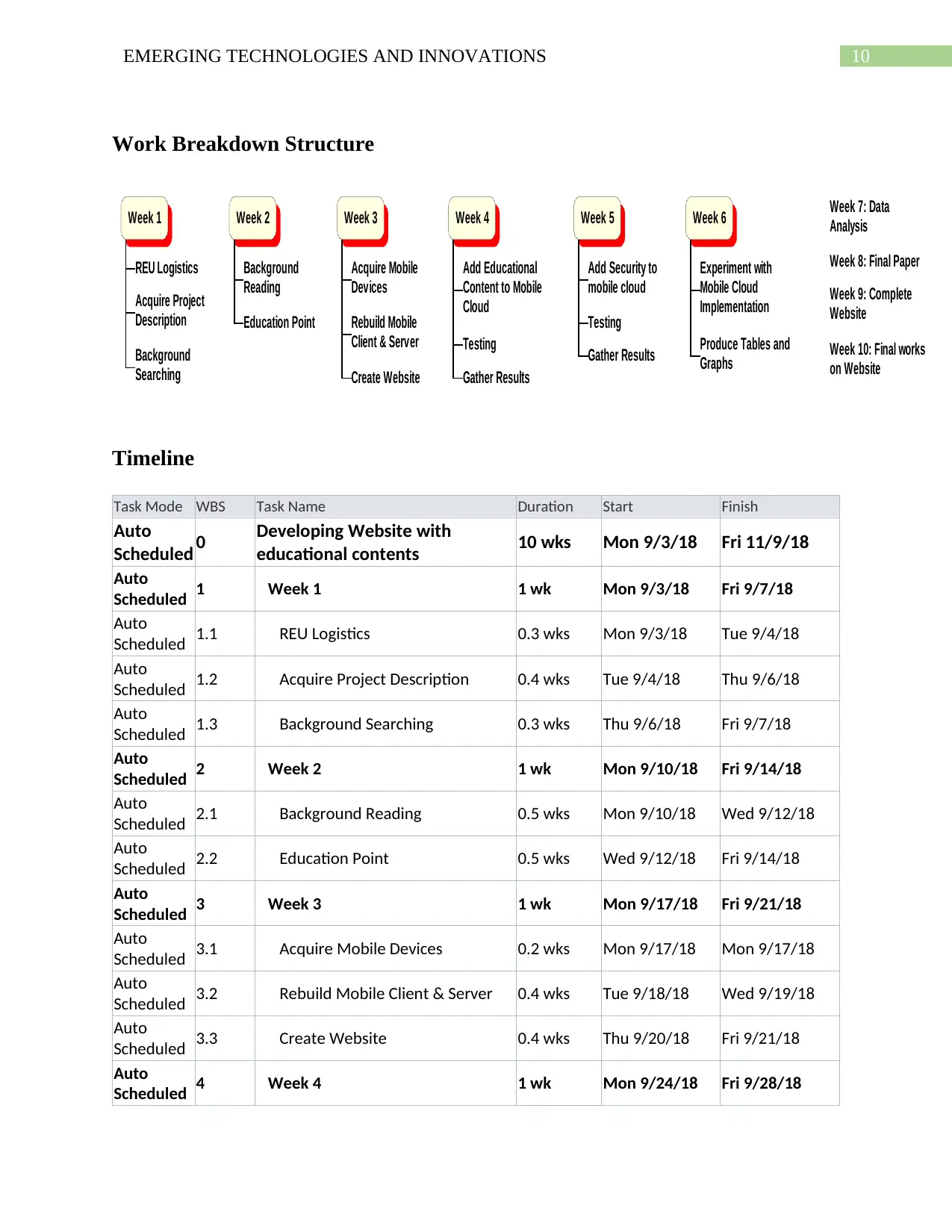
Work Breakdown Structure
Week 1
REU Logistics
Acquire Project
Description
Background
Searching
Week 2
Background
Reading
Education Point
Week 3
Acquire Mobile
Devices
Rebuild Mobile
Client & Server
Create Website
Week 4
Add Educational
Content to Mobile
Cloud
Testing
Gather Results
Week 5
Add Security to
mobile cloud
Testing
Gather Results
Week 6
Experiment with
Mobile Cloud
Implementation
Produce Tables and
Graphs
Week 7: Data
Analysis
Week 8: Final Paper
Week 9: Complete
Website
Week 10: Final works
on Website
Timeline
Task Mode WBS Task Name Duration Start Finish
Auto
Scheduled 0 Developing Website with
educational contents 10 wks Mon 9/3/18 Fri 11/9/18
Auto
Scheduled 1 Week 1 1 wk Mon 9/3/18 Fri 9/7/18
Auto
Scheduled 1.1 REU Logistics 0.3 wks Mon 9/3/18 Tue 9/4/18
Auto
Scheduled 1.2 Acquire Project Description 0.4 wks Tue 9/4/18 Thu 9/6/18
Auto
Scheduled 1.3 Background Searching 0.3 wks Thu 9/6/18 Fri 9/7/18
Auto
Scheduled 2 Week 2 1 wk Mon 9/10/18 Fri 9/14/18
Auto
Scheduled 2.1 Background Reading 0.5 wks Mon 9/10/18 Wed 9/12/18
Auto
Scheduled 2.2 Education Point 0.5 wks Wed 9/12/18 Fri 9/14/18
Auto
Scheduled 3 Week 3 1 wk Mon 9/17/18 Fri 9/21/18
Auto
Scheduled 3.1 Acquire Mobile Devices 0.2 wks Mon 9/17/18 Mon 9/17/18
Auto
Scheduled 3.2 Rebuild Mobile Client & Server 0.4 wks Tue 9/18/18 Wed 9/19/18
Auto
Scheduled 3.3 Create Website 0.4 wks Thu 9/20/18 Fri 9/21/18
Auto
Scheduled 4 Week 4 1 wk Mon 9/24/18 Fri 9/28/18
Work Breakdown Structure
Week 1
REU Logistics
Acquire Project
Description
Background
Searching
Week 2
Background
Reading
Education Point
Week 3
Acquire Mobile
Devices
Rebuild Mobile
Client & Server
Create Website
Week 4
Add Educational
Content to Mobile
Cloud
Testing
Gather Results
Week 5
Add Security to
mobile cloud
Testing
Gather Results
Week 6
Experiment with
Mobile Cloud
Implementation
Produce Tables and
Graphs
Week 7: Data
Analysis
Week 8: Final Paper
Week 9: Complete
Website
Week 10: Final works
on Website
Timeline
Task Mode WBS Task Name Duration Start Finish
Auto
Scheduled 0 Developing Website with
educational contents 10 wks Mon 9/3/18 Fri 11/9/18
Auto
Scheduled 1 Week 1 1 wk Mon 9/3/18 Fri 9/7/18
Auto
Scheduled 1.1 REU Logistics 0.3 wks Mon 9/3/18 Tue 9/4/18
Auto
Scheduled 1.2 Acquire Project Description 0.4 wks Tue 9/4/18 Thu 9/6/18
Auto
Scheduled 1.3 Background Searching 0.3 wks Thu 9/6/18 Fri 9/7/18
Auto
Scheduled 2 Week 2 1 wk Mon 9/10/18 Fri 9/14/18
Auto
Scheduled 2.1 Background Reading 0.5 wks Mon 9/10/18 Wed 9/12/18
Auto
Scheduled 2.2 Education Point 0.5 wks Wed 9/12/18 Fri 9/14/18
Auto
Scheduled 3 Week 3 1 wk Mon 9/17/18 Fri 9/21/18
Auto
Scheduled 3.1 Acquire Mobile Devices 0.2 wks Mon 9/17/18 Mon 9/17/18
Auto
Scheduled 3.2 Rebuild Mobile Client & Server 0.4 wks Tue 9/18/18 Wed 9/19/18
Auto
Scheduled 3.3 Create Website 0.4 wks Thu 9/20/18 Fri 9/21/18
Auto
Scheduled 4 Week 4 1 wk Mon 9/24/18 Fri 9/28/18
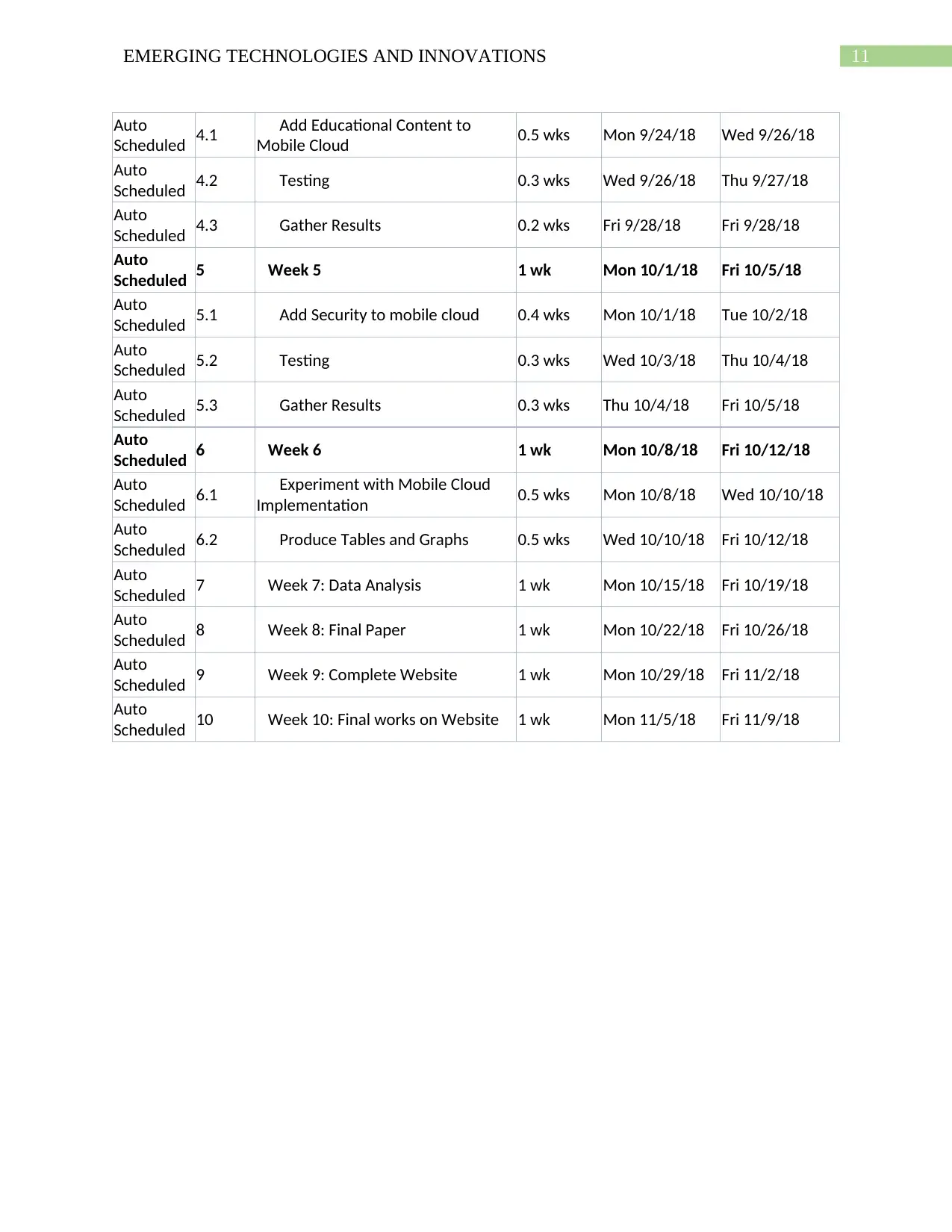
11EMERGING TECHNOLOGIES AND INNOVATIONS
Auto
Scheduled 4.1 Add Educational Content to
Mobile Cloud 0.5 wks Mon 9/24/18 Wed 9/26/18
Auto
Scheduled 4.2 Testing 0.3 wks Wed 9/26/18 Thu 9/27/18
Auto
Scheduled 4.3 Gather Results 0.2 wks Fri 9/28/18 Fri 9/28/18
Auto
Scheduled 5 Week 5 1 wk Mon 10/1/18 Fri 10/5/18
Auto
Scheduled 5.1 Add Security to mobile cloud 0.4 wks Mon 10/1/18 Tue 10/2/18
Auto
Scheduled 5.2 Testing 0.3 wks Wed 10/3/18 Thu 10/4/18
Auto
Scheduled 5.3 Gather Results 0.3 wks Thu 10/4/18 Fri 10/5/18
Auto
Scheduled 6 Week 6 1 wk Mon 10/8/18 Fri 10/12/18
Auto
Scheduled 6.1 Experiment with Mobile Cloud
Implementation 0.5 wks Mon 10/8/18 Wed 10/10/18
Auto
Scheduled 6.2 Produce Tables and Graphs 0.5 wks Wed 10/10/18 Fri 10/12/18
Auto
Scheduled 7 Week 7: Data Analysis 1 wk Mon 10/15/18 Fri 10/19/18
Auto
Scheduled 8 Week 8: Final Paper 1 wk Mon 10/22/18 Fri 10/26/18
Auto
Scheduled 9 Week 9: Complete Website 1 wk Mon 10/29/18 Fri 11/2/18
Auto
Scheduled 10 Week 10: Final works on Website 1 wk Mon 11/5/18 Fri 11/9/18
Auto
Scheduled 4.1 Add Educational Content to
Mobile Cloud 0.5 wks Mon 9/24/18 Wed 9/26/18
Auto
Scheduled 4.2 Testing 0.3 wks Wed 9/26/18 Thu 9/27/18
Auto
Scheduled 4.3 Gather Results 0.2 wks Fri 9/28/18 Fri 9/28/18
Auto
Scheduled 5 Week 5 1 wk Mon 10/1/18 Fri 10/5/18
Auto
Scheduled 5.1 Add Security to mobile cloud 0.4 wks Mon 10/1/18 Tue 10/2/18
Auto
Scheduled 5.2 Testing 0.3 wks Wed 10/3/18 Thu 10/4/18
Auto
Scheduled 5.3 Gather Results 0.3 wks Thu 10/4/18 Fri 10/5/18
Auto
Scheduled 6 Week 6 1 wk Mon 10/8/18 Fri 10/12/18
Auto
Scheduled 6.1 Experiment with Mobile Cloud
Implementation 0.5 wks Mon 10/8/18 Wed 10/10/18
Auto
Scheduled 6.2 Produce Tables and Graphs 0.5 wks Wed 10/10/18 Fri 10/12/18
Auto
Scheduled 7 Week 7: Data Analysis 1 wk Mon 10/15/18 Fri 10/19/18
Auto
Scheduled 8 Week 8: Final Paper 1 wk Mon 10/22/18 Fri 10/26/18
Auto
Scheduled 9 Week 9: Complete Website 1 wk Mon 10/29/18 Fri 11/2/18
Auto
Scheduled 10 Week 10: Final works on Website 1 wk Mon 11/5/18 Fri 11/9/18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




