SEC 430 - Risk Management of IT Infrastructure at Emirates Future Bank
VerifiedAdded on 2023/04/22
|3
|803
|366
Homework Assignment
AI Summary
This assignment focuses on the risk management of the IT infrastructure for Emirates Future Investment Bank (EFIB). It identifies risks, threats, and vulnerabilities across seven domains: Users, Workstations, LAN, LAN to WAN, Application, WAN, and Remote. The assignment further explores threat-vulnerability pairs, potential losses associated with each, and proposes recommendations to the CIO for mitigating these risks. It also includes a Plan of Action and Milestones (POAM) for implementing the recommended solutions, assigning responsibilities for data classification, vulnerability management, and traffic filtering. This document is available on Desklib, a platform that provides students with access to past papers and solved assignments.
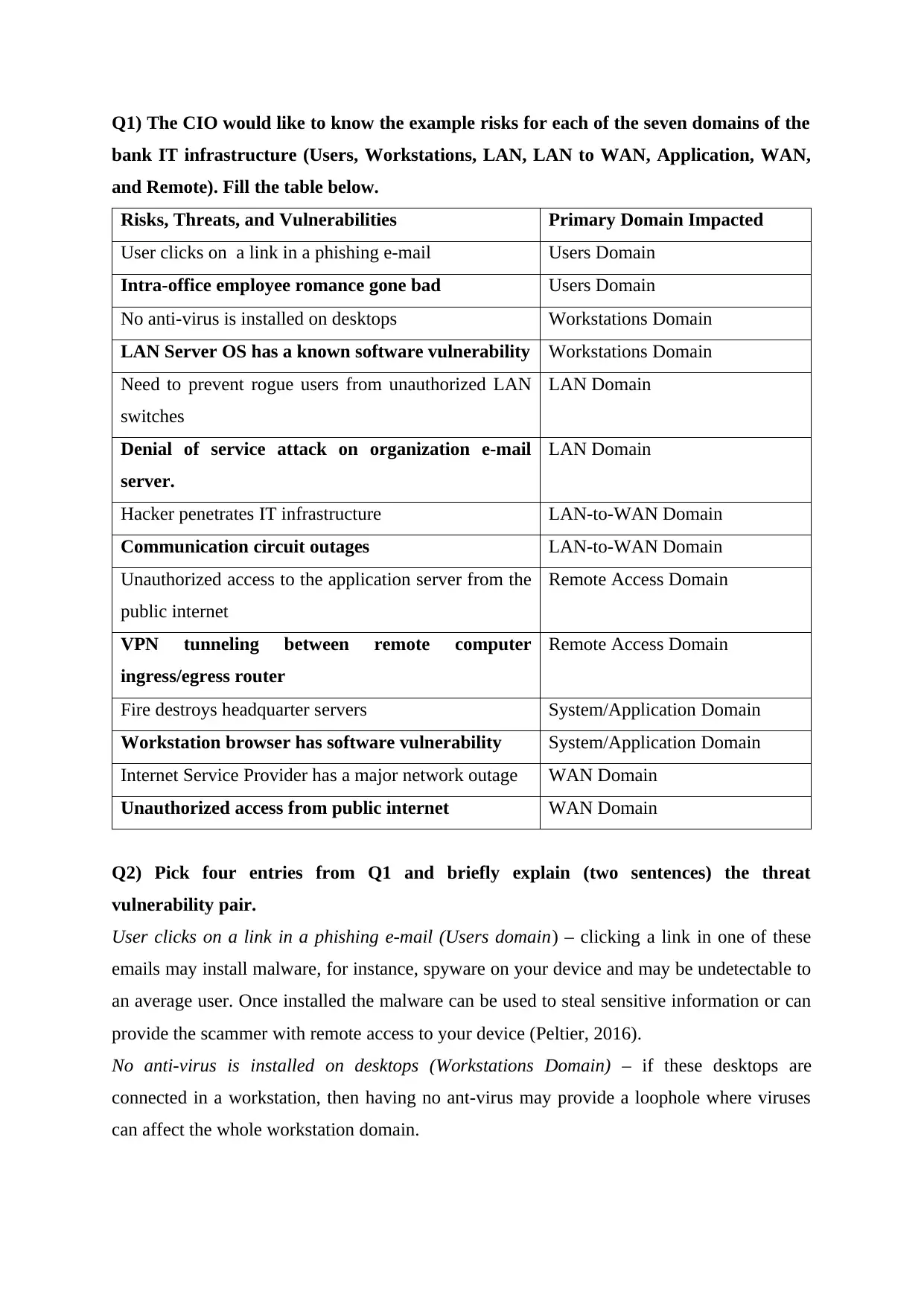
Q1) The CIO would like to know the example risks for each of the seven domains of the
bank IT infrastructure (Users, Workstations, LAN, LAN to WAN, Application, WAN,
and Remote). Fill the table below.
Risks, Threats, and Vulnerabilities Primary Domain Impacted
User clicks on a link in a phishing e-mail Users Domain
Intra-office employee romance gone bad Users Domain
No anti-virus is installed on desktops Workstations Domain
LAN Server OS has a known software vulnerability Workstations Domain
Need to prevent rogue users from unauthorized LAN
switches
LAN Domain
Denial of service attack on organization e-mail
server.
LAN Domain
Hacker penetrates IT infrastructure LAN-to-WAN Domain
Communication circuit outages LAN-to-WAN Domain
Unauthorized access to the application server from the
public internet
Remote Access Domain
VPN tunneling between remote computer
ingress/egress router
Remote Access Domain
Fire destroys headquarter servers System/Application Domain
Workstation browser has software vulnerability System/Application Domain
Internet Service Provider has a major network outage WAN Domain
Unauthorized access from public internet WAN Domain
Q2) Pick four entries from Q1 and briefly explain (two sentences) the threat
vulnerability pair.
User clicks on a link in a phishing e-mail (Users domain) – clicking a link in one of these
emails may install malware, for instance, spyware on your device and may be undetectable to
an average user. Once installed the malware can be used to steal sensitive information or can
provide the scammer with remote access to your device (Peltier, 2016).
No anti-virus is installed on desktops (Workstations Domain) – if these desktops are
connected in a workstation, then having no ant-virus may provide a loophole where viruses
can affect the whole workstation domain.
bank IT infrastructure (Users, Workstations, LAN, LAN to WAN, Application, WAN,
and Remote). Fill the table below.
Risks, Threats, and Vulnerabilities Primary Domain Impacted
User clicks on a link in a phishing e-mail Users Domain
Intra-office employee romance gone bad Users Domain
No anti-virus is installed on desktops Workstations Domain
LAN Server OS has a known software vulnerability Workstations Domain
Need to prevent rogue users from unauthorized LAN
switches
LAN Domain
Denial of service attack on organization e-mail
server.
LAN Domain
Hacker penetrates IT infrastructure LAN-to-WAN Domain
Communication circuit outages LAN-to-WAN Domain
Unauthorized access to the application server from the
public internet
Remote Access Domain
VPN tunneling between remote computer
ingress/egress router
Remote Access Domain
Fire destroys headquarter servers System/Application Domain
Workstation browser has software vulnerability System/Application Domain
Internet Service Provider has a major network outage WAN Domain
Unauthorized access from public internet WAN Domain
Q2) Pick four entries from Q1 and briefly explain (two sentences) the threat
vulnerability pair.
User clicks on a link in a phishing e-mail (Users domain) – clicking a link in one of these
emails may install malware, for instance, spyware on your device and may be undetectable to
an average user. Once installed the malware can be used to steal sensitive information or can
provide the scammer with remote access to your device (Peltier, 2016).
No anti-virus is installed on desktops (Workstations Domain) – if these desktops are
connected in a workstation, then having no ant-virus may provide a loophole where viruses
can affect the whole workstation domain.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Need to prevent rogue users from unauthorized LAN switches (LAN Domain) – One can use
MAC address whitelisting so that only specified devices can connect to given sensitive
networks.
Hacker penetrates IT infrastructure (LAN-to-WAN Domain) - A firewall with unnecessary
ports open can allow access from the Internet.
Q3) For each threat-vulnerability pair from Q2, briefly describe the potential loss.
User clicks on a link in a phishing e-mail (Users domain) - User can destroy data in the
application (intentionally or not) and delete all files.
No anti-virus is installed on desktops (Workstations Domain) - A workstation’s hard drive
can fail to cause lost data (Whitman, Mattord, Mackey, & Green, 2012).
Need to prevent rogue users from unauthorized LAN switches (LAN Domain) - A worm can
spread through the LAN and infect all computers in it.
Hacker penetrates IT infrastructure (LAN-to-WAN Domain) - Weak ingress/egress traffic
filtering can degrade network performance.
Q4) For each loss described in Q3, propose a recommendation to the CIO.
The user can destroy data in the application (intentionally or not) and delete all files. To solve
this problem, The data classification standard and encryption policy definition are needed to
minimize data loss.
A workstation’s hard drive can fail to cause lost data. To solve this problem, ensure that all
software vulnerabilities are addressed.
A worm can spread through the LAN and infect all computers in it. To solve this problem is
to ensure no unauthorized persons using the LAN
Weak ingress/egress traffic filtering can degrade network performance. To solve this problem
is to make sure the firewall does not have unnecessary ports.
Q5) Assuming the CIO is interested in all of the recommendations in Q4, assign
responsibilities and propose a POAM.
The user can destroy data in the application (intentionally or not) and delete all files. The best
POAM is Data Classification Standard and Encryption Policy Definition.
A workstation’s hard drive can fail to cause lost data. The best POAM is Production Data
Back-up Policy Definition
A worm can spread through the LAN and infect all computers in it. The best POAM is
Vulnerability Management and Vulnerability Window Policy Definition.
Weak ingress/egress traffic filtering can degrade network performance. The best POAM is
Internet Ingress/Egress Traffic Policy Definition
MAC address whitelisting so that only specified devices can connect to given sensitive
networks.
Hacker penetrates IT infrastructure (LAN-to-WAN Domain) - A firewall with unnecessary
ports open can allow access from the Internet.
Q3) For each threat-vulnerability pair from Q2, briefly describe the potential loss.
User clicks on a link in a phishing e-mail (Users domain) - User can destroy data in the
application (intentionally or not) and delete all files.
No anti-virus is installed on desktops (Workstations Domain) - A workstation’s hard drive
can fail to cause lost data (Whitman, Mattord, Mackey, & Green, 2012).
Need to prevent rogue users from unauthorized LAN switches (LAN Domain) - A worm can
spread through the LAN and infect all computers in it.
Hacker penetrates IT infrastructure (LAN-to-WAN Domain) - Weak ingress/egress traffic
filtering can degrade network performance.
Q4) For each loss described in Q3, propose a recommendation to the CIO.
The user can destroy data in the application (intentionally or not) and delete all files. To solve
this problem, The data classification standard and encryption policy definition are needed to
minimize data loss.
A workstation’s hard drive can fail to cause lost data. To solve this problem, ensure that all
software vulnerabilities are addressed.
A worm can spread through the LAN and infect all computers in it. To solve this problem is
to ensure no unauthorized persons using the LAN
Weak ingress/egress traffic filtering can degrade network performance. To solve this problem
is to make sure the firewall does not have unnecessary ports.
Q5) Assuming the CIO is interested in all of the recommendations in Q4, assign
responsibilities and propose a POAM.
The user can destroy data in the application (intentionally or not) and delete all files. The best
POAM is Data Classification Standard and Encryption Policy Definition.
A workstation’s hard drive can fail to cause lost data. The best POAM is Production Data
Back-up Policy Definition
A worm can spread through the LAN and infect all computers in it. The best POAM is
Vulnerability Management and Vulnerability Window Policy Definition.
Weak ingress/egress traffic filtering can degrade network performance. The best POAM is
Internet Ingress/Egress Traffic Policy Definition

References
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: Guidelines
for Effective Information Security Management. Boca Raton, FL: CRC Press.
Whitman, M. E., Mattord, H. J., Mackey, D., & Green, A. (2012). Guide to Network
Security. Boston, MA: Cengage Learning.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: Guidelines
for Effective Information Security Management. Boca Raton, FL: CRC Press.
Whitman, M. E., Mattord, H. J., Mackey, D., & Green, A. (2012). Guide to Network
Security. Boston, MA: Cengage Learning.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 3
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


