University Cloud Security Report: Employee Data, SaaS, and Privacy
VerifiedAdded on 2020/02/24
|34
|6311
|63
Report
AI Summary
This report provides a comprehensive analysis of cloud security concerns, specifically focusing on employee data within the Department of Administrative Service (DAS). It examines various security threats and risks, including the lack of a security architecture, phishing attacks, malware, and vulnerabilities associated with SaaS implementation. The report assesses the likelihood, impact, and priority of these threats, proposing preventive actions and contingency plans. It also delves into privacy threats like computer and telephone monitoring, video surveillance, and email monitoring, evaluating their impact and suggesting mitigation strategies. The report discusses the implications of digital identity and data sensitivity, providing insights into how to secure employee data and maintain privacy in a cloud environment. It also includes detailed tables outlining security and privacy threats, their descriptions, and proposed solutions. The report also examines the effect of security breaches on employees and the organization.

Cloud Security
Name of the student
Name of the University
Author Note
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Introduction:
The DAS or the Department of the Administrative Service provides numerous
services to other departments at Australia. The services have been delivered from the data
centre of the department.
The Software as a Service has been the licensing model and the software delivery
hosted centrally. These services have been provided from the data centers of DAS.
The report has covered the security and privacy about the employee data. Next it
has discussed the problems regarding the digital identity. Lastly it has undergone through
the problems about data sensitivity and the provider solution.
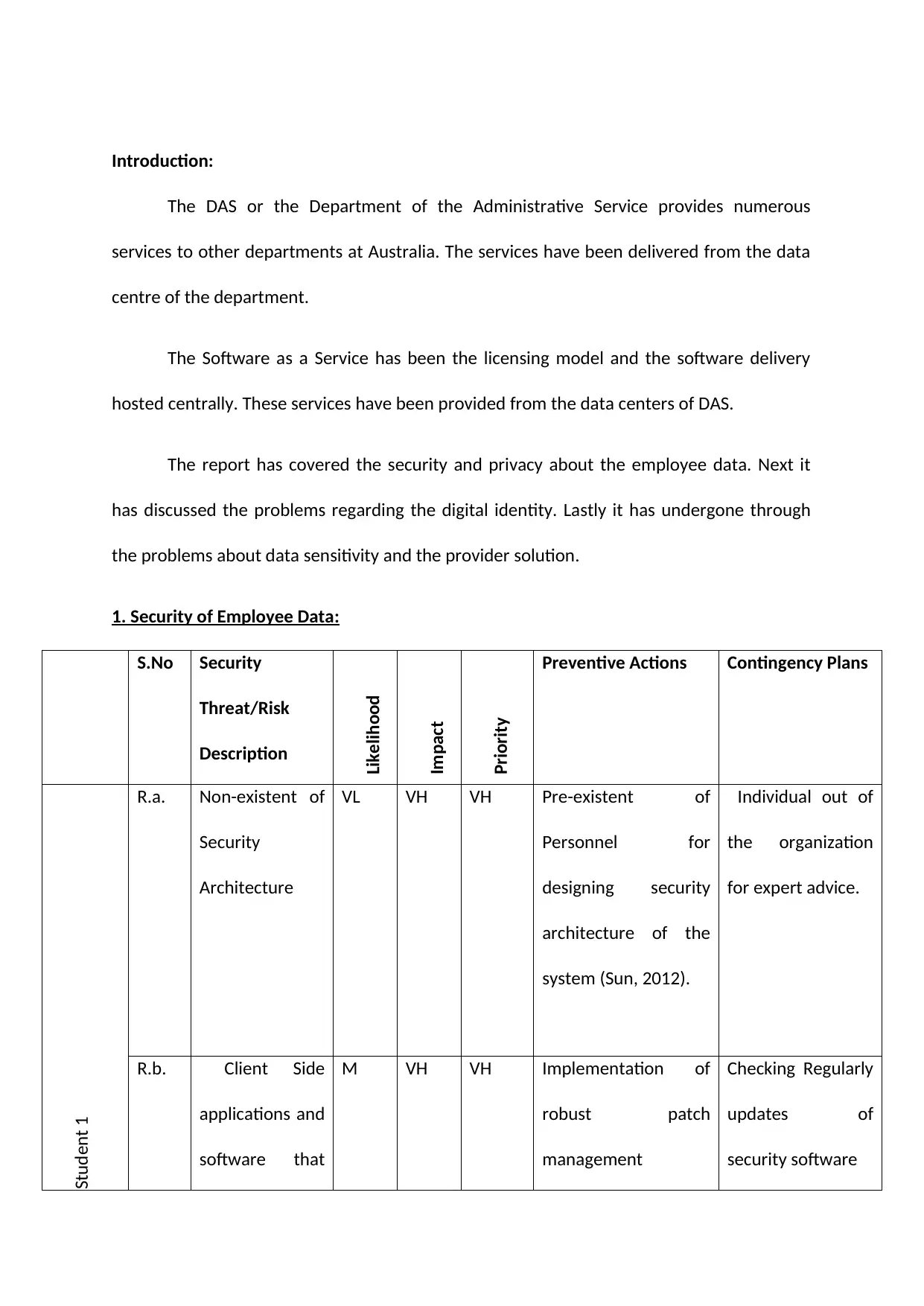
1. Security of Employee Data:
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R.a. Non-existent of
Security
Architecture
VL VH VH Pre-existent of
Personnel for
designing security
architecture of the
system (Sun, 2012).
Individual out of
the organization
for expert advice.
R.b. Client Side
applications and
software that
M VH VH Implementation of
robust patch
management
Checking Regularly
updates of
security software
The DAS or the Department of the Administrative Service provides numerous
services to other departments at Australia. The services have been delivered from the data
centre of the department.
The Software as a Service has been the licensing model and the software delivery
hosted centrally. These services have been provided from the data centers of DAS.
The report has covered the security and privacy about the employee data. Next it
has discussed the problems regarding the digital identity. Lastly it has undergone through
the problems about data sensitivity and the provider solution.
1. Security of Employee Data:
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R.a. Non-existent of
Security
Architecture
VL VH VH Pre-existent of
Personnel for
designing security
architecture of the
system (Sun, 2012).
Individual out of
the organization
for expert advice.
R.b. Client Side
applications and
software that
M VH VH Implementation of
robust patch
management
Checking Regularly
updates of
security software
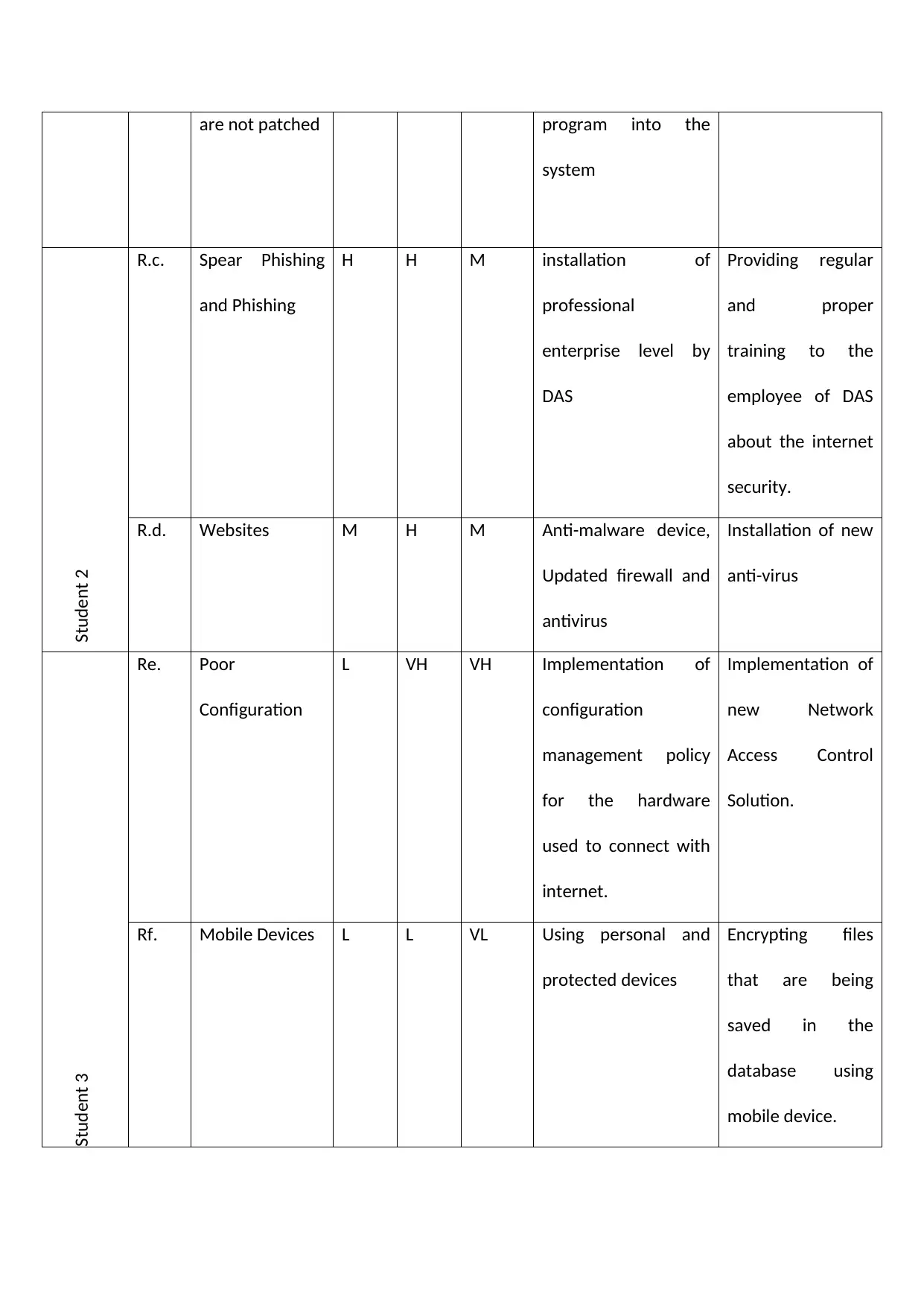
are not patched program into the
system
Student 2
R.c. Spear Phishing
and Phishing
H H M installation of
professional
enterprise level by
DAS
Providing regular
and proper
training to the
employee of DAS
about the internet
security.
R.d. Websites M H M Anti-malware device,
Updated firewall and
antivirus
Installation of new
anti-virus
Re. Poor
Configuration
L VH VH Implementation of
configuration
management policy
for the hardware
used to connect with
internet.
Implementation of
new Network
Access Control
Solution.
Student 3
Rf. Mobile Devices L L VL Using personal and
protected devices
Encrypting files
that are being
saved in the
database using
mobile device.
system
Student 2
R.c. Spear Phishing
and Phishing
H H M installation of
professional
enterprise level by
DAS
Providing regular
and proper
training to the
employee of DAS
about the internet
security.
R.d. Websites M H M Anti-malware device,
Updated firewall and
antivirus
Installation of new
anti-virus
Re. Poor
Configuration
L VH VH Implementation of
configuration
management policy
for the hardware
used to connect with
internet.
Implementation of
new Network
Access Control
Solution.
Student 3
Rf. Mobile Devices L L VL Using personal and
protected devices
Encrypting files
that are being
saved in the
database using
mobile device.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
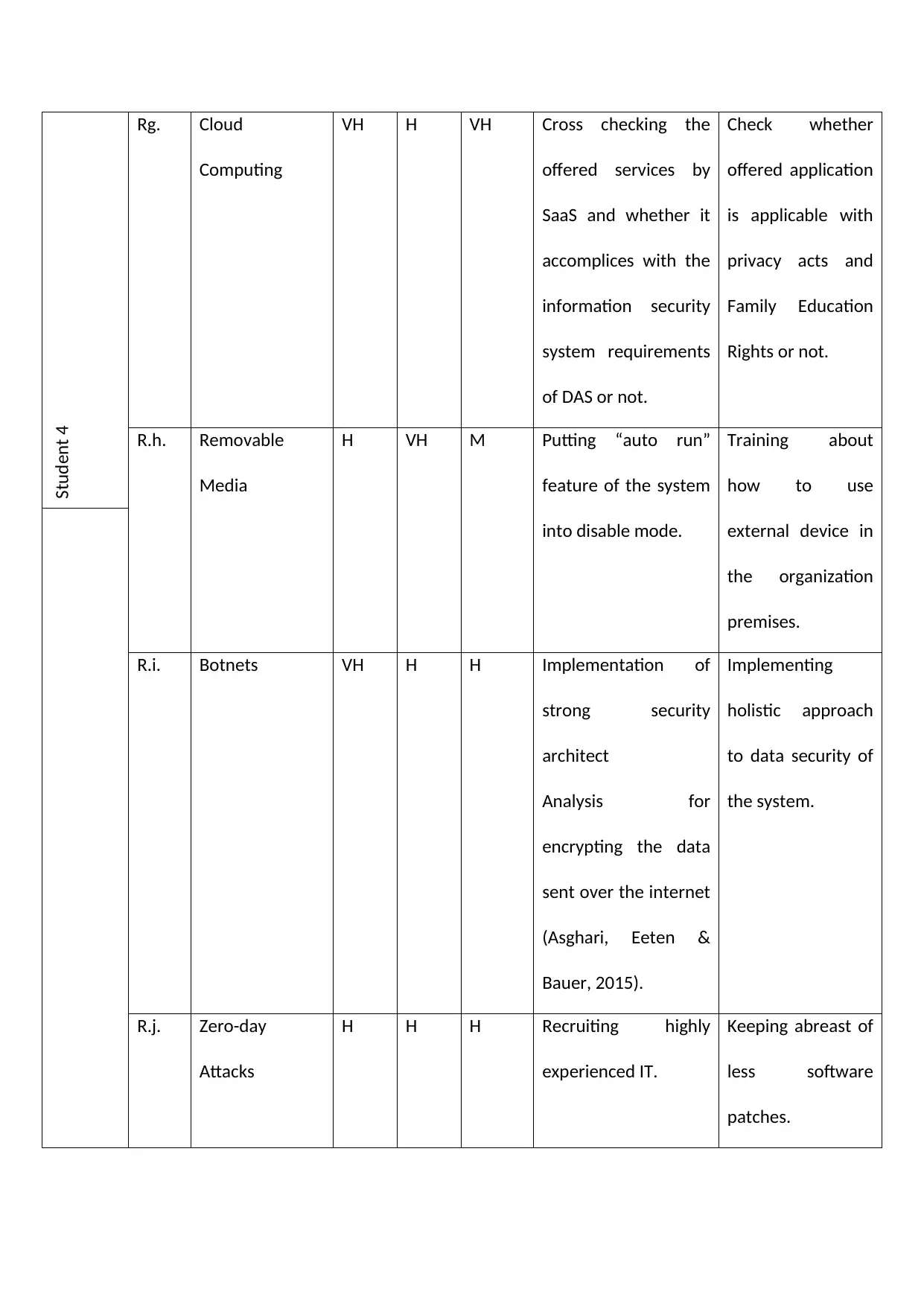
Student 4
Rg. Cloud
Computing
VH H VH Cross checking the
offered services by
SaaS and whether it
accomplices with the
information security
system requirements
of DAS or not.
Check whether
offered application
is applicable with
privacy acts and
Family Education
Rights or not.
R.h. Removable
Media
H VH M Putting “auto run”
feature of the system
into disable mode.
Training about
how to use
external device in
the organization
premises.
R.i. Botnets VH H H Implementation of
strong security
architect
Analysis for
encrypting the data
sent over the internet
(Asghari, Eeten &
Bauer, 2015).
Implementing
holistic approach
to data security of
the system.
R.j. Zero-day
Attacks
H H H Recruiting highly
experienced IT.
Keeping abreast of
less software
patches.
Rg. Cloud
Computing
VH H VH Cross checking the
offered services by
SaaS and whether it
accomplices with the
information security
system requirements
of DAS or not.
Check whether
offered application
is applicable with
privacy acts and
Family Education
Rights or not.
R.h. Removable
Media
H VH M Putting “auto run”
feature of the system
into disable mode.
Training about
how to use
external device in
the organization
premises.
R.i. Botnets VH H H Implementation of
strong security
architect
Analysis for
encrypting the data
sent over the internet
(Asghari, Eeten &
Bauer, 2015).
Implementing
holistic approach
to data security of
the system.
R.j. Zero-day
Attacks
H H H Recruiting highly
experienced IT.
Keeping abreast of
less software
patches.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Existing security threats to Employee data
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH

Explain issues
1. The threats identified in the previous decades are same almost. This continued to
plaguing the business at present. The popular threat in the in-house HR database has
been the additional privileges as the employees are been granted. The DAS could fail
in updating the access privileges for the altering roles of the employees at their
organization. The users could also abuse the legitimate database privileges for
unauthorized reasons (Lafuente, 2015). There could also be the attacks regarding the
database injections. One of the primary types of these attacks has been the NoSQL
and the SQL injections.
2. The SQL injections are targeted to the traditional data base systems. The other one
has been targeting on the platforms of the big-data. In both the scenarios the attack
of the input injection done successfully could deliver the attacker with the restricted
access into the entire database. Then there has been the malware. This is a long
lasting danger. This has been used to retrieve the sensitive data through the original
legitimate customers using the damaged devices. The following one is the exposure
of the storage media.
3. The media backup storage has been unprotected regularly from the assaults. In the
same way the numerous security beaches has been incorporated with the theft of
the tapes and discs supporting the database. There has been exploitation of the less
powerful databases also. This has been taking about a month to fix the issues. The
attackers have been presently knowledgeable regarding in which way to rob the
unpatched databases or databases having default records and configuration
parameters.
1. The threats identified in the previous decades are same almost. This continued to
plaguing the business at present. The popular threat in the in-house HR database has
been the additional privileges as the employees are been granted. The DAS could fail
in updating the access privileges for the altering roles of the employees at their
organization. The users could also abuse the legitimate database privileges for
unauthorized reasons (Lafuente, 2015). There could also be the attacks regarding the
database injections. One of the primary types of these attacks has been the NoSQL
and the SQL injections.
2. The SQL injections are targeted to the traditional data base systems. The other one
has been targeting on the platforms of the big-data. In both the scenarios the attack
of the input injection done successfully could deliver the attacker with the restricted
access into the entire database. Then there has been the malware. This is a long
lasting danger. This has been used to retrieve the sensitive data through the original
legitimate customers using the damaged devices. The following one is the exposure
of the storage media.
3. The media backup storage has been unprotected regularly from the assaults. In the
same way the numerous security beaches has been incorporated with the theft of
the tapes and discs supporting the database. There has been exploitation of the less
powerful databases also. This has been taking about a month to fix the issues. The
attackers have been presently knowledgeable regarding in which way to rob the
unpatched databases or databases having default records and configuration
parameters.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
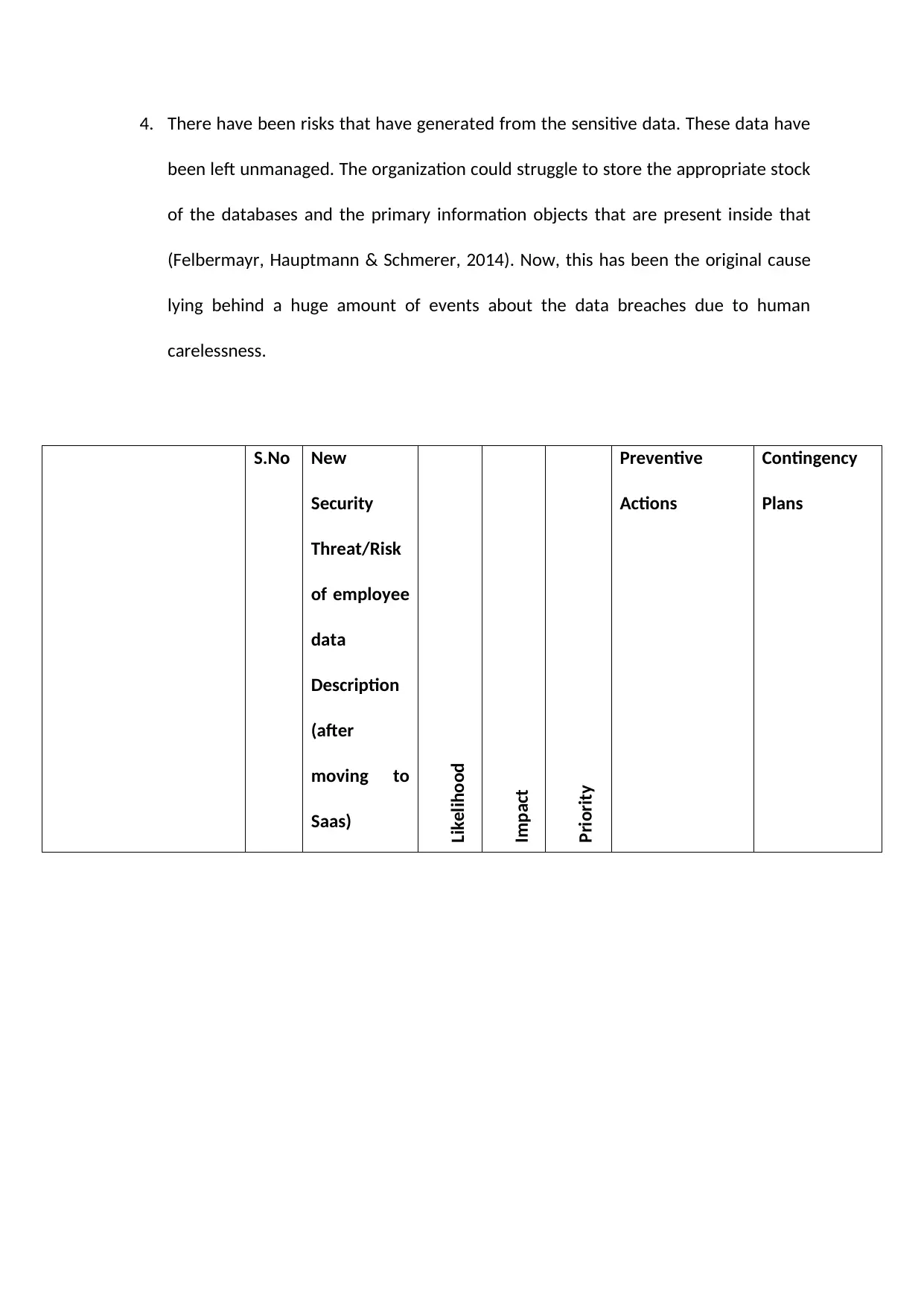
4. There have been risks that have generated from the sensitive data. These data have
been left unmanaged. The organization could struggle to store the appropriate stock
of the databases and the primary information objects that are present inside that
(Felbermayr, Hauptmann & Schmerer, 2014). Now, this has been the original cause
lying behind a huge amount of events about the data breaches due to human
carelessness.
S.No New
Security
Threat/Risk
of employee
data
Description
(after
moving to
Saas)
Likelihood
Impact
Priority
Preventive
Actions
Contingency
Plans
been left unmanaged. The organization could struggle to store the appropriate stock
of the databases and the primary information objects that are present inside that
(Felbermayr, Hauptmann & Schmerer, 2014). Now, this has been the original cause
lying behind a huge amount of events about the data breaches due to human
carelessness.
S.No New
Security
Threat/Risk
of employee
data
Description
(after
moving to
Saas)
Likelihood
Impact
Priority
Preventive
Actions
Contingency
Plans
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
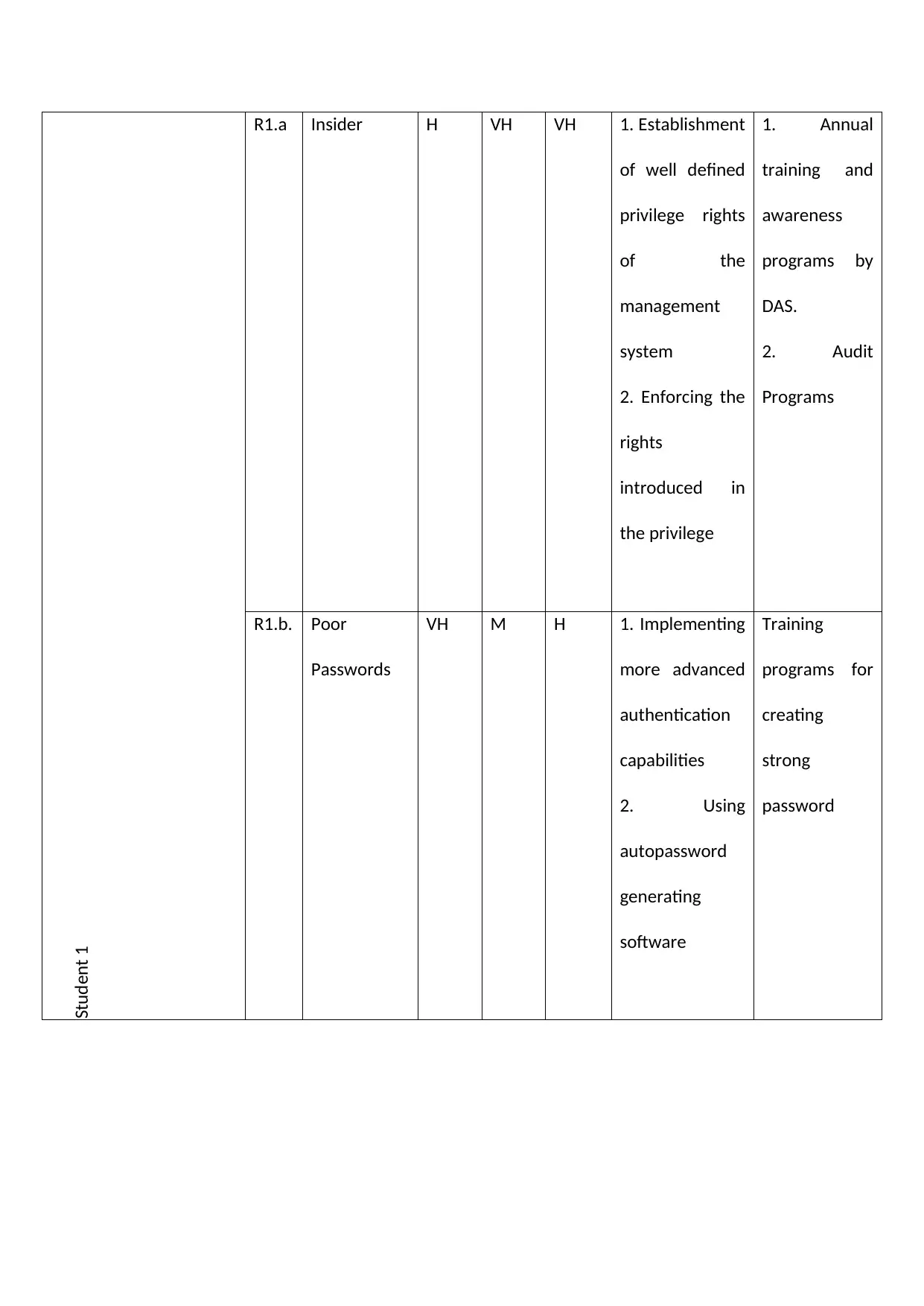
Student 1
R1.a Insider H VH VH 1. Establishment
of well defined
privilege rights
of the
management
system
2. Enforcing the
rights
introduced in
the privilege
1. Annual
training and
awareness
programs by
DAS.
2. Audit
Programs
R1.b. Poor
Passwords
VH M H 1. Implementing
more advanced
authentication
capabilities
2. Using
autopassword
generating
software
Training
programs for
creating
strong
password
R1.a Insider H VH VH 1. Establishment
of well defined
privilege rights
of the
management
system
2. Enforcing the
rights
introduced in
the privilege
1. Annual
training and
awareness
programs by
DAS.
2. Audit
Programs
R1.b. Poor
Passwords
VH M H 1. Implementing
more advanced
authentication
capabilities
2. Using
autopassword
generating
software
Training
programs for
creating
strong
password
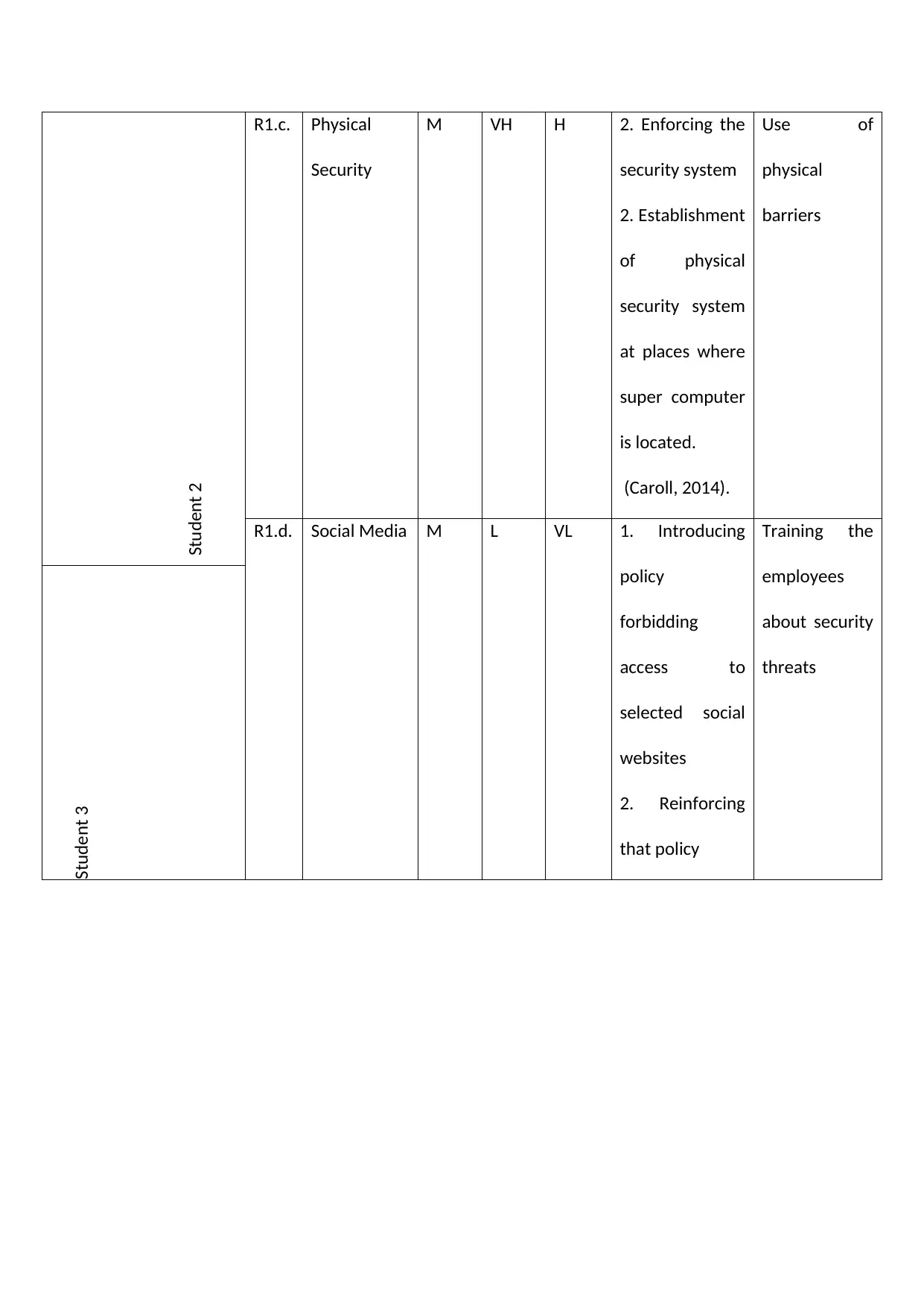
Student 2
R1.c. Physical
Security
M VH H 2. Enforcing the
security system
2. Establishment
of physical
security system
at places where
super computer
is located.
(Caroll, 2014).
Use of
physical
barriers
R1.d. Social Media M L VL 1. Introducing
policy
forbidding
access to
selected social
websites
2. Reinforcing
that policy
Training the
employees
about security
threats
Student 3
R1.c. Physical
Security
M VH H 2. Enforcing the
security system
2. Establishment
of physical
security system
at places where
super computer
is located.
(Caroll, 2014).
Use of
physical
barriers
R1.d. Social Media M L VL 1. Introducing
policy
forbidding
access to
selected social
websites
2. Reinforcing
that policy
Training the
employees
about security
threats
Student 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Student 4
R1.e. Social
Engineering
M L VL How to avoid
from being
manipulated by
an unwanted
individual, and
be safe (Mann,
2012).
Training
employees
about self
responsibility
on securing
password.
New Security Threat to Employee data (after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
Explain issues
1. The initial risk originating after incorporating the SAAS has been the usage risk. This
has been indicating the risk incurred by DAS. The basis has been the manner in which
they use the specific application of SaaS. At first it has been found whether the
organization is using the application about the functions of critical business. Then it
is to be identified whether the app could have stored the sensitive data. Since the
reply has been negative in both the situations, the application must go to the lower
risk rank very quickly (Pfeifer, 2016).
2. The following one is the risks regarding the information security. It has been seen
that how DAS could use the SaaS application. Next they could move towards the
risks of information security. The using of the risk concentrated on how the DAS has
been using the application. Hence the security risk of data has been focusing on the
manner in which the service providers have been taking care of the data.
R1.e. Social
Engineering
M L VL How to avoid
from being
manipulated by
an unwanted
individual, and
be safe (Mann,
2012).
Training
employees
about self
responsibility
on securing
password.
New Security Threat to Employee data (after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
Explain issues
1. The initial risk originating after incorporating the SAAS has been the usage risk. This
has been indicating the risk incurred by DAS. The basis has been the manner in which
they use the specific application of SaaS. At first it has been found whether the
organization is using the application about the functions of critical business. Then it
is to be identified whether the app could have stored the sensitive data. Since the
reply has been negative in both the situations, the application must go to the lower
risk rank very quickly (Pfeifer, 2016).
2. The following one is the risks regarding the information security. It has been seen
that how DAS could use the SaaS application. Next they could move towards the
risks of information security. The using of the risk concentrated on how the DAS has
been using the application. Hence the security risk of data has been focusing on the
manner in which the service providers have been taking care of the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3. The subsequent one is the operational risk confirmation from the provider of SaaS.
This has been tending the manner in which the supplier has been dealing with the
daily operations. Despite this, DAS must consider the data security risk as the subset
of this problematic range. However they come out of that due to its significance
(Kristal, 2017). Lastly there have been the application risks originating from the SaaS
providers. This has been the intrinsic problems created by the manner in which the
application was developed.
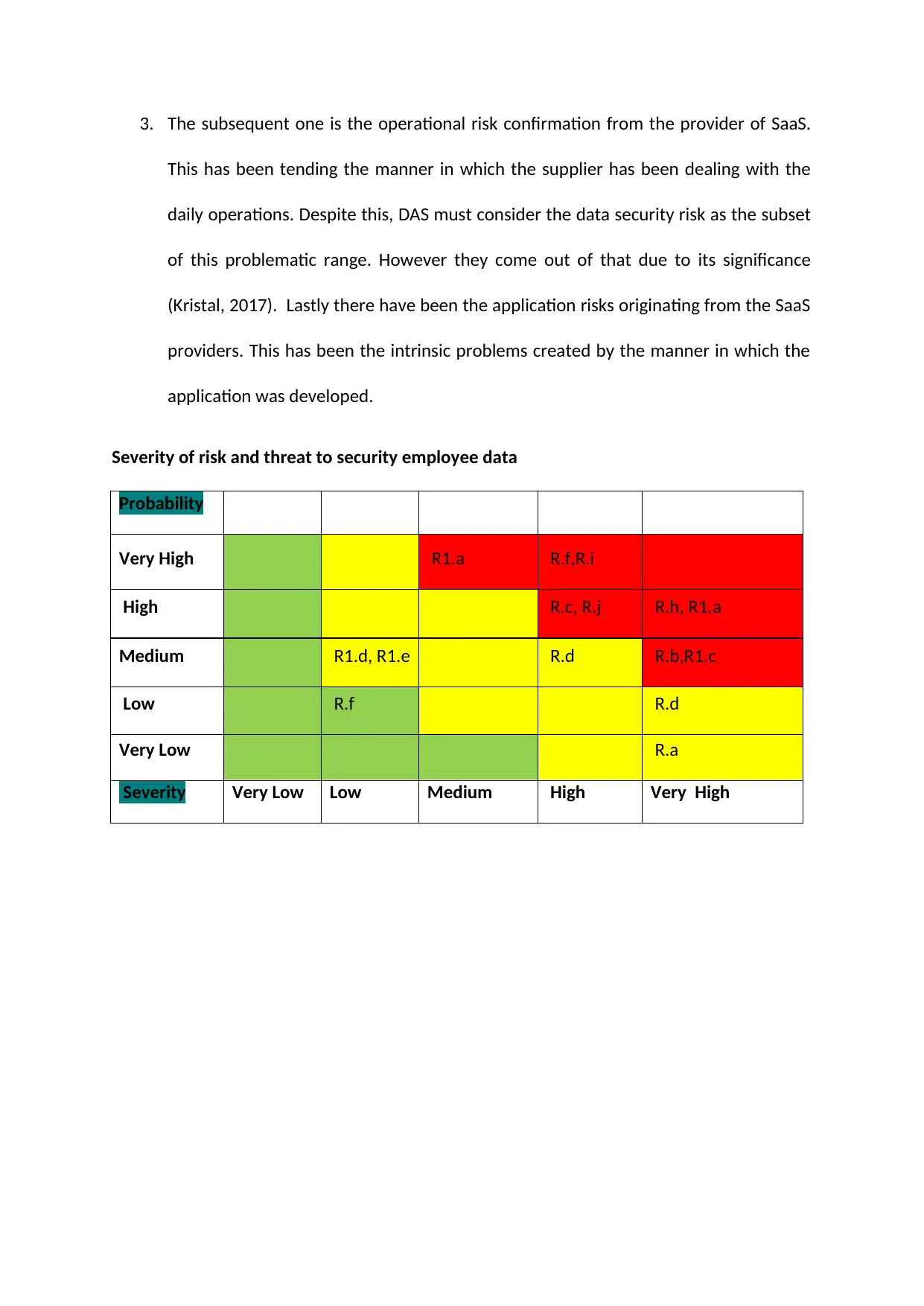
Severity of risk and threat to security employee data
Probability
Very High R1.a R.f,R.i
High R.c, R.j R.h, R1.a
Medium R1.d, R1.e R.d R.b,R1.c
Low R.f R.d
Very Low R.a
Severity Very Low Low Medium High Very High
This has been tending the manner in which the supplier has been dealing with the
daily operations. Despite this, DAS must consider the data security risk as the subset
of this problematic range. However they come out of that due to its significance
(Kristal, 2017). Lastly there have been the application risks originating from the SaaS
providers. This has been the intrinsic problems created by the manner in which the
application was developed.
Severity of risk and threat to security employee data
Probability
Very High R1.a R.f,R.i
High R.c, R.j R.h, R1.a
Medium R1.d, R1.e R.d R.b,R1.c
Low R.f R.d
Very Low R.a
Severity Very Low Low Medium High Very High

For the employees, the information loss due to the workers has been in terms of
passionate replies. This has been more when contrasted with the retailer and the
association they have been working with. The reason behind this has been that the victim
could essentially disjoin the connections and the business at any other place. As viewed
from the perspective of psychology, the ability to pick any item has been the monstrous
differentiator for the victim of the breach. There has been no necessity to purchase the
items from them. The condition also includes working with particular organization giving
them the authority for opting the condition and the manner in which the relation develops
(Müller & Neumann, 2015).
The capability of picking is eradicated while accepting the notice of the breach of the
Personally Identifiable Data or PII from the DAS. The way in which they must act and reply
and where they have been venting their dread, outrage and disappointment has been
pointing to the additional hazard for the DAS. It has been precisely what has offended the
bar of the party that is preying on.
During the research on the event and to approve what has actually occurred, the IT
employees of the organization and most of the C-suite probably stopped the general
operations keeping the business at hold. As any event gets changed to be open and notices
are provided to the workers, the next phase of the internal disturbance commences (Smith
& Ross, 2014). The workers have been investing extra measure of time during the day time.
This is done by exploring the administrations that are made available. It is done by calling
the restoration group of the call centre for effectively views how they must protect their
own selves during the advancement.
passionate replies. This has been more when contrasted with the retailer and the
association they have been working with. The reason behind this has been that the victim
could essentially disjoin the connections and the business at any other place. As viewed
from the perspective of psychology, the ability to pick any item has been the monstrous
differentiator for the victim of the breach. There has been no necessity to purchase the
items from them. The condition also includes working with particular organization giving
them the authority for opting the condition and the manner in which the relation develops
(Müller & Neumann, 2015).
The capability of picking is eradicated while accepting the notice of the breach of the
Personally Identifiable Data or PII from the DAS. The way in which they must act and reply
and where they have been venting their dread, outrage and disappointment has been
pointing to the additional hazard for the DAS. It has been precisely what has offended the
bar of the party that is preying on.
During the research on the event and to approve what has actually occurred, the IT
employees of the organization and most of the C-suite probably stopped the general
operations keeping the business at hold. As any event gets changed to be open and notices
are provided to the workers, the next phase of the internal disturbance commences (Smith
& Ross, 2014). The workers have been investing extra measure of time during the day time.
This is done by exploring the administrations that are made available. It is done by calling
the restoration group of the call centre for effectively views how they must protect their
own selves during the advancement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 34
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





