ACCT6001: Report on Employee Database, IT Controls, and Ethical Issues
VerifiedAdded on 2021/06/17
|5
|600
|96
Report
AI Summary
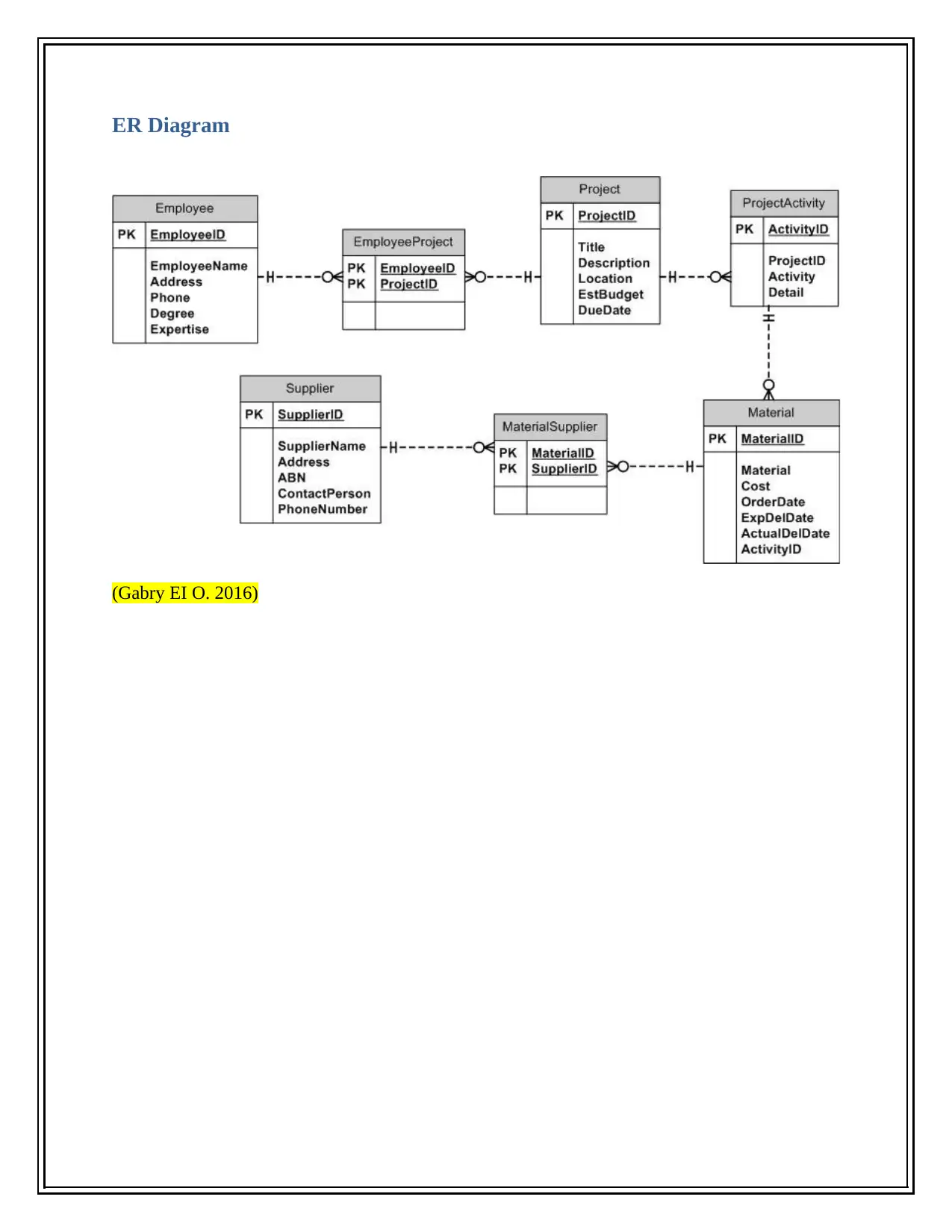
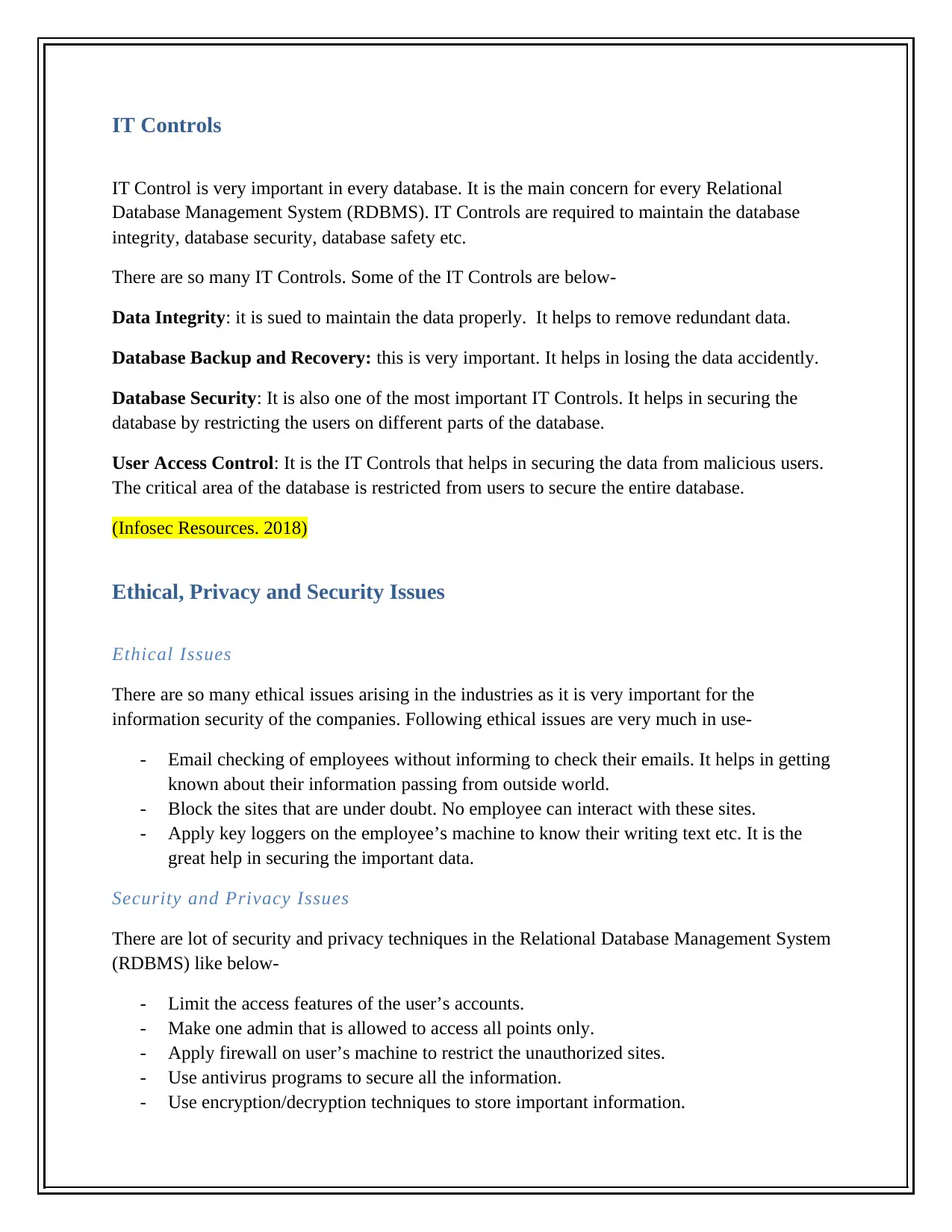
This report focuses on the implementation of an employee database using a Relational Database Management System (RDBMS), specifically within MS Access. It explores the advantages of using a database system over a file system, emphasizing features like data security, query building, and backup/recovery. The report highlights the importance of IT controls, including data integrity, database security, and user access control, to maintain database integrity and security. Furthermore, it addresses ethical, privacy, and security issues, such as employee email monitoring, website blocking, and the use of key loggers. The report also mentions security and privacy techniques within RDBMS, like access limitations, firewalls, antivirus programs, and encryption methods. The report is supported by references to relevant sources, including a discussion on Entity Relationship Diagrams (ERD) and IT audit planning.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)