Employee Database Report - ACCT6001 Module - Semester 1
VerifiedAdded on 2021/06/17
|5
|590
|431
Report
AI Summary
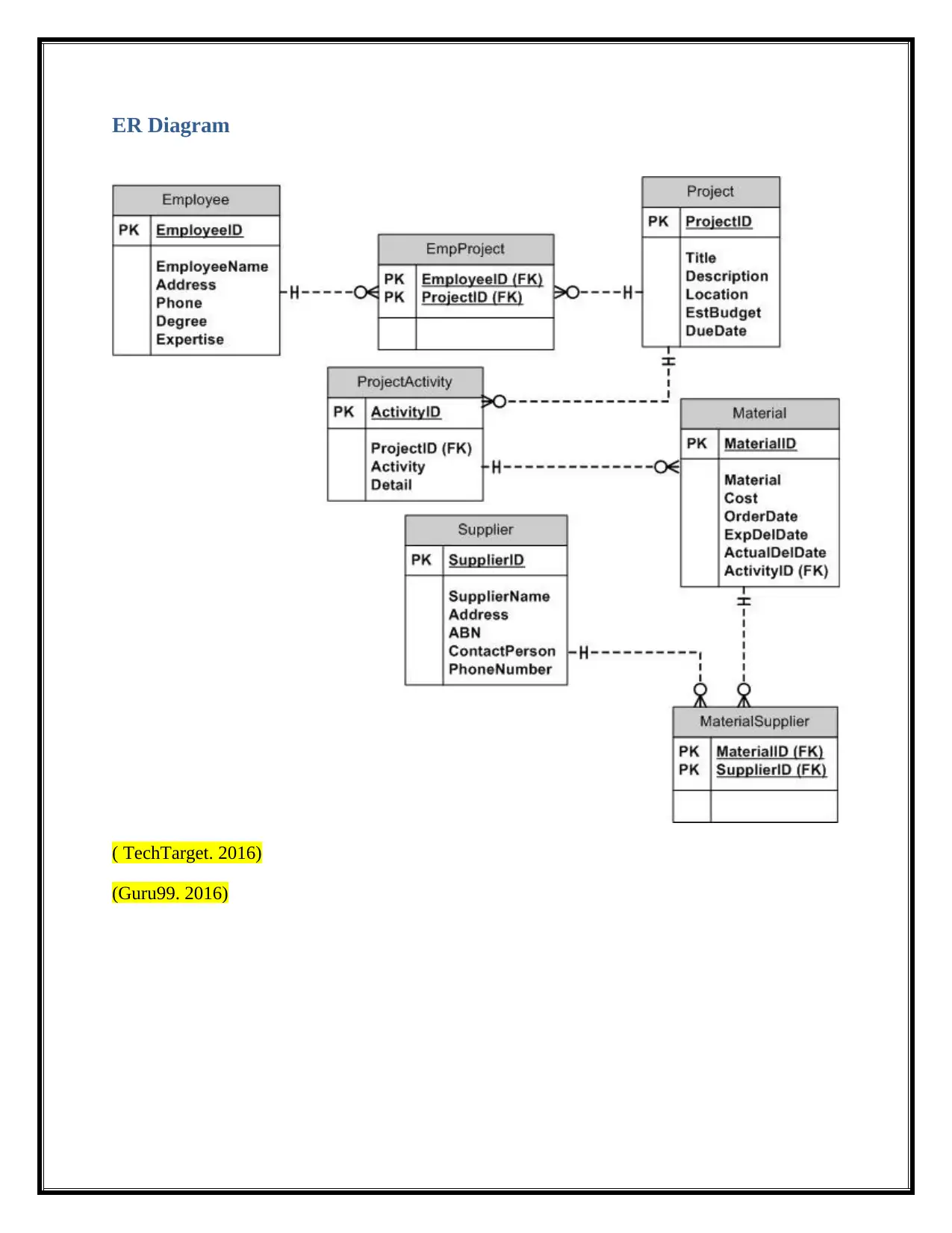
The report focuses on the design and implementation of an Employee Database, starting with an overview of its importance and the limitations of file systems compared to relational database management systems (RDBMS). It highlights the use of an Entity-Relationship (ER) diagram and its conversion to a relational database, specifically using Microsoft Access. The report covers essential IT controls, including backup/recovery, performance optimization, integrity, security, and user access control, emphasizing their importance for data protection. Furthermore, it addresses ethical, privacy, and security issues, such as administrator rights, data protection measures, and customer data confidentiality. References to relevant resources are provided, offering a comprehensive view of database design, implementation, and security considerations.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)