Digital Forensics Report: EMTS Data Recovery Using Various Tools
VerifiedAdded on 2023/06/12
|21
|2379
|235
Report
AI Summary
This digital forensics report investigates data loss for the EMTS organization, focusing on the recovery of suspicious data from a hard drive and USB. The report details the analysis conducted by Bob Aspen, a contract employee, using tools such as Winhex, Pro Discover, and image steganography. Winhex is used to recover deleted images from the USB, Pro Discover recovers deleted files, and image steganography recovers hidden text within images. The report outlines the steps taken with each tool, providing screenshots and explanations of the recovery processes. The conclusion summarizes the successful creation of the digital forensic report and the recovery of lost data, emphasizing the effectiveness of the chosen digital forensics tools in addressing EMTS's data loss incident.
DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The organization EMTS investigates the digital forensic tool for preparing digital
forensic report. The aim of this project includes preparing digital forensic report, due to loss of
suspicious data from the organization’s hard drive and USB. So, it required to recover by
analyzing the digital forensics tool. The EMTS organization chief decided to makes the digital
forensic report and it is taken care by Bob Aspen, who works as Exotic Mountain Tour Services’
contract employee. So, the Bob aspen investigates and creates organization’s digital forensic
report. The digital forensic tool will be investigated.
2
The organization EMTS investigates the digital forensic tool for preparing digital
forensic report. The aim of this project includes preparing digital forensic report, due to loss of
suspicious data from the organization’s hard drive and USB. So, it required to recover by
analyzing the digital forensics tool. The EMTS organization chief decided to makes the digital
forensic report and it is taken care by Bob Aspen, who works as Exotic Mountain Tour Services’
contract employee. So, the Bob aspen investigates and creates organization’s digital forensic
report. The digital forensic tool will be investigated.
2

Table of Contents
1. Introduction.........................................................................................................................................4
1.1 Background..................................................................................................................................4
1.2 Scope of the project.....................................................................................................................4
1.3 Used Tools...................................................................................................................................4
2. Analysis of the tools............................................................................................................................5
3. Evidence and Findings.........................................................................................................................7
3.1 Use Winhex tool Recover the deleted image in the usb...............................................................7
3.2 Use Pro Discover tool to recover the files..................................................................................13
3.3 Use Image Stenography tool to recover the hidden text in Image..............................................16
4. Conclusion.........................................................................................................................................20
References.................................................................................................................................................21
3
1. Introduction.........................................................................................................................................4
1.1 Background..................................................................................................................................4
1.2 Scope of the project.....................................................................................................................4
1.3 Used Tools...................................................................................................................................4
2. Analysis of the tools............................................................................................................................5
3. Evidence and Findings.........................................................................................................................7
3.1 Use Winhex tool Recover the deleted image in the usb...............................................................7
3.2 Use Pro Discover tool to recover the files..................................................................................13
3.3 Use Image Stenography tool to recover the hidden text in Image..............................................16
4. Conclusion.........................................................................................................................................20
References.................................................................................................................................................21
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
1.1 Background
The Exotic Maintain Tour Services organization is to investigate the digital forensics and
this investigation is used for preparing organizational digital forensic report. It also investigates
intellectual property that was by Bob Aspen, who actually works as EMTS organization’s
contract employee. Generally, this organization has the very expansive and completed analysis of
marketing process on the customer services. It also creates plan for product deal of effective and
efficient advertisement, with a superior bicycle which has its tour service. It ensures to promote
the material under the disclosure of superior bicycles. But it suspicious data was lost and it
requires data recovery. So, it investigates the digital forensic tool (Cohen, 2012). Thus, EMTS’s
chief decided to recover the data and it was handled by the web server executive named, Bob
Aspen. Because, this organization contains web based main activity in the organizational system
and it differentiates the suspicious connections. Hence, there was deletion of suspicious data and
the organization requires recovery.
1.2 Project Scope
The project scope includes creating digital forensic report for the organization named
EMTS, as it lost some suspicious data from its hard drive and USB. So, there is a serious need
for investigating the digital forensic tool. So, it needs to recover by analysis the digital forensics
tool. The EMTS organization chief decided to makes the digital forensic report and it was
handled by Bob Aspen, who worked as EMTS’s contract employee. This report will ensure to
complete the recovery of the deleted/ lost files (Filler & Fridrich, 2010). In the given case
scenarios, pro discover tool will be utilized for recovering the deleted files, present in the USB,
then the image steganography tool is utilized for recovering the hidden text, from the image, and
Winhex tool is utilized for recovering the deleted image, which was present in the USB. Before
finding the evidence for EMTS, the forensics tools must be analyzed.
1.3 Used Tools
EMTS utilizes the following the digital forensic tool for recovering the suspicious data:
Pro Discover Tool
Winhex Tool
4
1.1 Background
The Exotic Maintain Tour Services organization is to investigate the digital forensics and
this investigation is used for preparing organizational digital forensic report. It also investigates
intellectual property that was by Bob Aspen, who actually works as EMTS organization’s
contract employee. Generally, this organization has the very expansive and completed analysis of
marketing process on the customer services. It also creates plan for product deal of effective and
efficient advertisement, with a superior bicycle which has its tour service. It ensures to promote
the material under the disclosure of superior bicycles. But it suspicious data was lost and it
requires data recovery. So, it investigates the digital forensic tool (Cohen, 2012). Thus, EMTS’s
chief decided to recover the data and it was handled by the web server executive named, Bob
Aspen. Because, this organization contains web based main activity in the organizational system
and it differentiates the suspicious connections. Hence, there was deletion of suspicious data and
the organization requires recovery.
1.2 Project Scope
The project scope includes creating digital forensic report for the organization named
EMTS, as it lost some suspicious data from its hard drive and USB. So, there is a serious need
for investigating the digital forensic tool. So, it needs to recover by analysis the digital forensics
tool. The EMTS organization chief decided to makes the digital forensic report and it was
handled by Bob Aspen, who worked as EMTS’s contract employee. This report will ensure to
complete the recovery of the deleted/ lost files (Filler & Fridrich, 2010). In the given case
scenarios, pro discover tool will be utilized for recovering the deleted files, present in the USB,
then the image steganography tool is utilized for recovering the hidden text, from the image, and
Winhex tool is utilized for recovering the deleted image, which was present in the USB. Before
finding the evidence for EMTS, the forensics tools must be analyzed.
1.3 Used Tools
EMTS utilizes the following the digital forensic tool for recovering the suspicious data:
Pro Discover Tool
Winhex Tool
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Image Steganography Tool
2. Analysis of the tools
Pro Discover Tool
This tool is utilized for providing next generation solution for cyber-crime and it backed by
industry leader (Gregorieff & Clevers, 2010). It has the cutting edge features to provide the
standards of industry to have proactive computer forensics. Because, it is most powerful
computer security tool and that used to enables the computer professionals to locate the all the
data on the computer. It is used to protect the evidence and creates the quality evidentially
reports to utilize in the legal proceedings. It utilizes lease destructive methodology and industry
best practices to provide the valuable Meta data. It can easily recover the deleted file, access the
windows alternate data streams, and examine the slack space. Generally, this tool handles and
manages the security concerns of the organization and it is designed for NIST disk imaging tool.
It insures high-quality and supports VM ware for running the images that were captured. Then, it
bit streams the copy of hard drive for maintaining the original evidence safe for an organization.
The pro discover tool has the various features such as,
Automated report generation
Ensure high quality
Event log file
Examine the Linux file systems
Examine the sun Solaris UFS file
Extracts the EXIF information
Integrated and GUI interface function is used to assure the ease of use and quick start.
Integrated thumbnail graphics
Integrated viewer to examine the files
Searching entire disk
Internet history
Proving data integrity
Perl scripts usage
Usage of user provide along with national Drug intelligence
Winhex Tool
5
2. Analysis of the tools
Pro Discover Tool
This tool is utilized for providing next generation solution for cyber-crime and it backed by
industry leader (Gregorieff & Clevers, 2010). It has the cutting edge features to provide the
standards of industry to have proactive computer forensics. Because, it is most powerful
computer security tool and that used to enables the computer professionals to locate the all the
data on the computer. It is used to protect the evidence and creates the quality evidentially
reports to utilize in the legal proceedings. It utilizes lease destructive methodology and industry
best practices to provide the valuable Meta data. It can easily recover the deleted file, access the
windows alternate data streams, and examine the slack space. Generally, this tool handles and
manages the security concerns of the organization and it is designed for NIST disk imaging tool.
It insures high-quality and supports VM ware for running the images that were captured. Then, it
bit streams the copy of hard drive for maintaining the original evidence safe for an organization.
The pro discover tool has the various features such as,
Automated report generation
Ensure high quality
Event log file
Examine the Linux file systems
Examine the sun Solaris UFS file
Extracts the EXIF information
Integrated and GUI interface function is used to assure the ease of use and quick start.
Integrated thumbnail graphics
Integrated viewer to examine the files
Searching entire disk
Internet history
Proving data integrity
Perl scripts usage
Usage of user provide along with national Drug intelligence
Winhex Tool
5

Winhex forensic tool is utilized for providing effective data recovery. Moreover, it is a
powerful application that can use as advanced hex editor. It is used for data analysis, data wiping
tool, editing, recover and forensic tool to protect the evidence and gathering the evidence. It will
possibly help with the mechanized capacity which makes great utilization for the record headers’
presence (Hussein Khalafalla, 2017). Winhex tool has various features such as,
Conversion between the Intel hex, ASCII, binary etc.
Compare and analyze the files.
Disk cloning
Editing data structures using templates
Encode records
Divide and unify the Even and odd words into bytes.
Examine and look at records.
Extensive program help.
Gather the free and slack space on Hard Drive.
Import all the clip board formats
It has scripting and programming interfaces
It contains the disk editor for the CD-ROM, floppy disks, smart media, hard disks,
floppy disks etc.
It splitting and concatenating and files
It use the various data recovery techniques
Join and split records.
Make hashes and checksums.
Recapture information.
Support file of any size.
Search for text based on keywords.
Wipe drives.
Image Steganography Tool
It is a tool which is utilized for recovering the hidden text, in the Image from the USB,
hard drive etc. (K & M, 2015). It is also hides the secret information in the form of an audio file
with the help of a tool called steganography. It is used for modifying the pixels images to hidden
the texts and add the noise to audio sample to hidden the information. The steganography tool is
6
powerful application that can use as advanced hex editor. It is used for data analysis, data wiping
tool, editing, recover and forensic tool to protect the evidence and gathering the evidence. It will
possibly help with the mechanized capacity which makes great utilization for the record headers’
presence (Hussein Khalafalla, 2017). Winhex tool has various features such as,
Conversion between the Intel hex, ASCII, binary etc.
Compare and analyze the files.
Disk cloning
Editing data structures using templates
Encode records
Divide and unify the Even and odd words into bytes.
Examine and look at records.
Extensive program help.
Gather the free and slack space on Hard Drive.
Import all the clip board formats
It has scripting and programming interfaces
It contains the disk editor for the CD-ROM, floppy disks, smart media, hard disks,
floppy disks etc.
It splitting and concatenating and files
It use the various data recovery techniques
Join and split records.
Make hashes and checksums.
Recapture information.
Support file of any size.
Search for text based on keywords.
Wipe drives.
Image Steganography Tool
It is a tool which is utilized for recovering the hidden text, in the Image from the USB,
hard drive etc. (K & M, 2015). It is also hides the secret information in the form of an audio file
with the help of a tool called steganography. It is used for modifying the pixels images to hidden
the texts and add the noise to audio sample to hidden the information. The steganography tool is
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
have various software’s. Here, image steganography tool will be used because it is utilized for
the hidden text, which is present in the images. It is used to provide the best way to protect the
EMTS organization privacy and it market is hard to determine the private communicate to takes
the place. It recovers the hidden text by using the steghide program and it performs the
steganography. It is used to reduce the chance of data leakage. It generally has the various ways
to achieving the steganography in digital communication (Pforte, 2016).
3. Evidence and Findings
3.1 Use Winhex tool Recover the deleted image in the usb
For recovering the deleted image of the USB, the Winhex forensic tool is used. Digital
forensic tool has various forensic tools for recovering all the deleted images. However, Winhex
tool is most effective and efficient to provide the deleted image within seconds. It is very popular
tool to recover the corrupted images. EMTS deleted its most significant information from the
USB. Thus, it requires to be recovered with the digital forensics tool. Here, the corrupted images
will be recovered (Advances in Digital Forensics 9, 2016). The below screens is corrupted and it
shown below.
Here, the screenshot is shows the corrupted images.
7
the hidden text, which is present in the images. It is used to provide the best way to protect the
EMTS organization privacy and it market is hard to determine the private communicate to takes
the place. It recovers the hidden text by using the steghide program and it performs the
steganography. It is used to reduce the chance of data leakage. It generally has the various ways
to achieving the steganography in digital communication (Pforte, 2016).
3. Evidence and Findings
3.1 Use Winhex tool Recover the deleted image in the usb
For recovering the deleted image of the USB, the Winhex forensic tool is used. Digital
forensic tool has various forensic tools for recovering all the deleted images. However, Winhex
tool is most effective and efficient to provide the deleted image within seconds. It is very popular
tool to recover the corrupted images. EMTS deleted its most significant information from the
USB. Thus, it requires to be recovered with the digital forensics tool. Here, the corrupted images
will be recovered (Advances in Digital Forensics 9, 2016). The below screens is corrupted and it
shown below.
Here, the screenshot is shows the corrupted images.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
To recover the corrupted image by open the Winhex recovery tool. It is shown below.
After, open the USB. It is shown below (Gogolin, 2013).
8
After, open the USB. It is shown below (Gogolin, 2013).
8
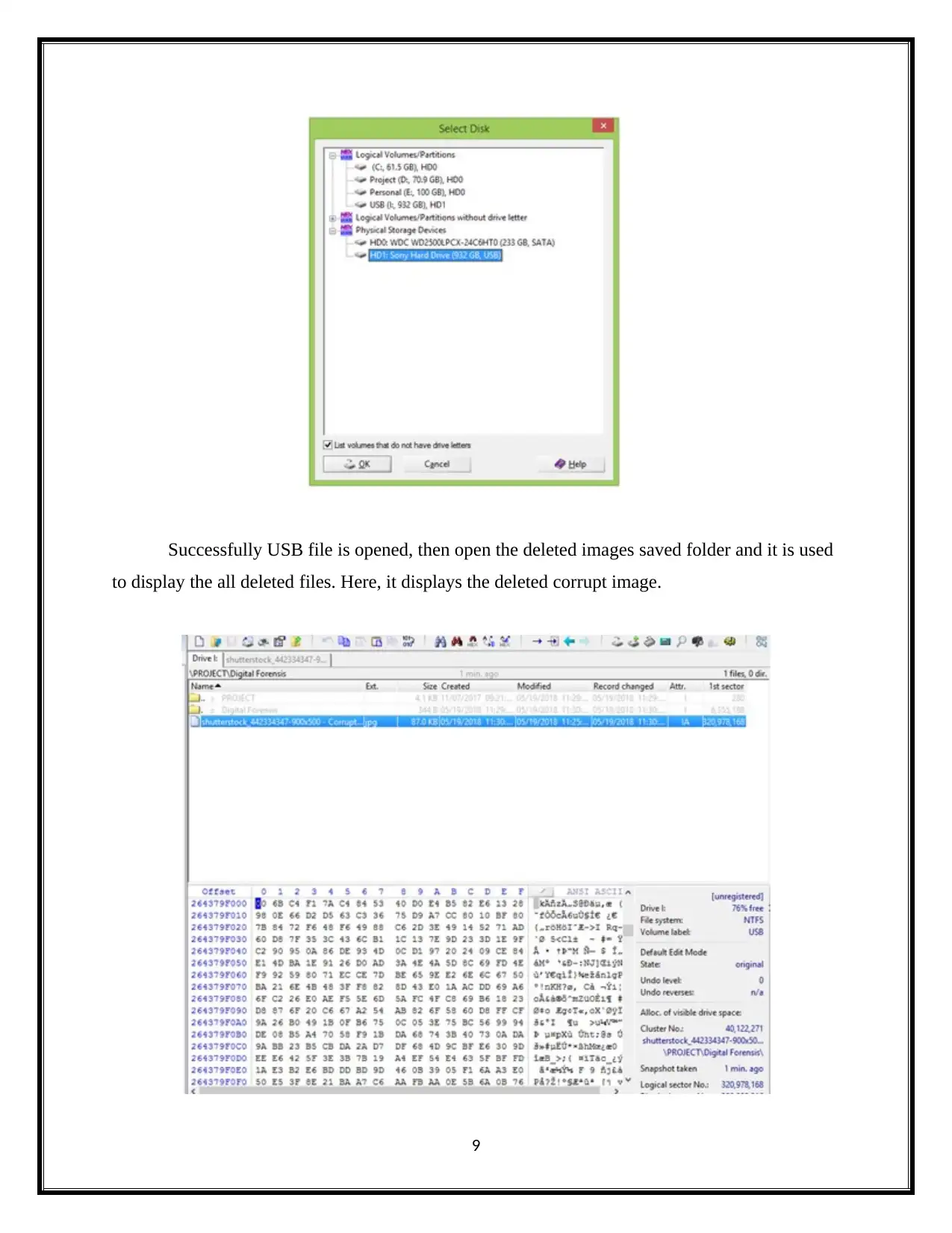
Successfully USB file is opened, then open the deleted images saved folder and it is used
to display the all deleted files. Here, it displays the deleted corrupt image.
9
to display the all deleted files. Here, it displays the deleted corrupt image.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
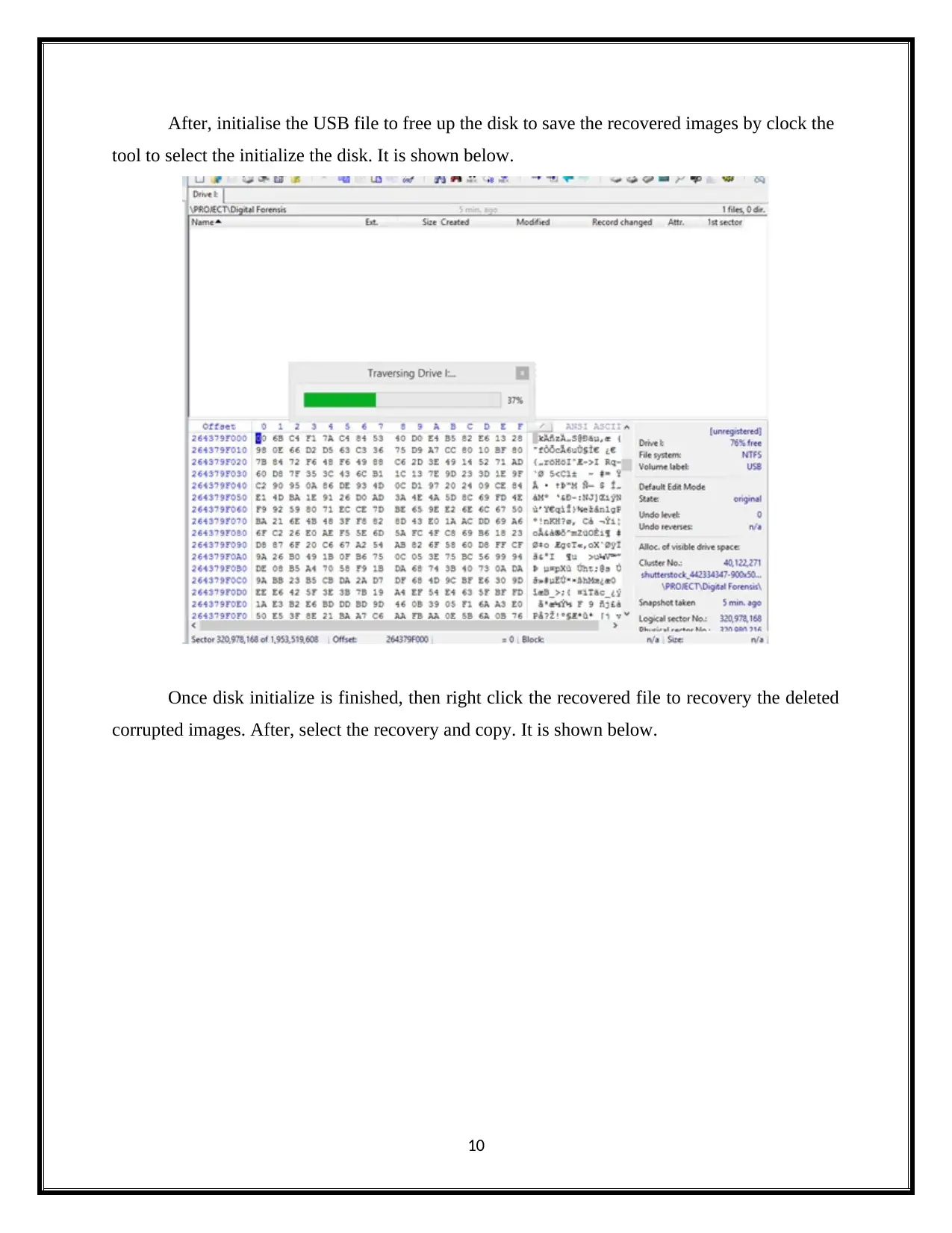
After, initialise the USB file to free up the disk to save the recovered images by clock the
tool to select the initialize the disk. It is shown below.
Once disk initialize is finished, then right click the recovered file to recovery the deleted
corrupted images. After, select the recovery and copy. It is shown below.
10
tool to select the initialize the disk. It is shown below.
Once disk initialize is finished, then right click the recovered file to recovery the deleted
corrupted images. After, select the recovery and copy. It is shown below.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
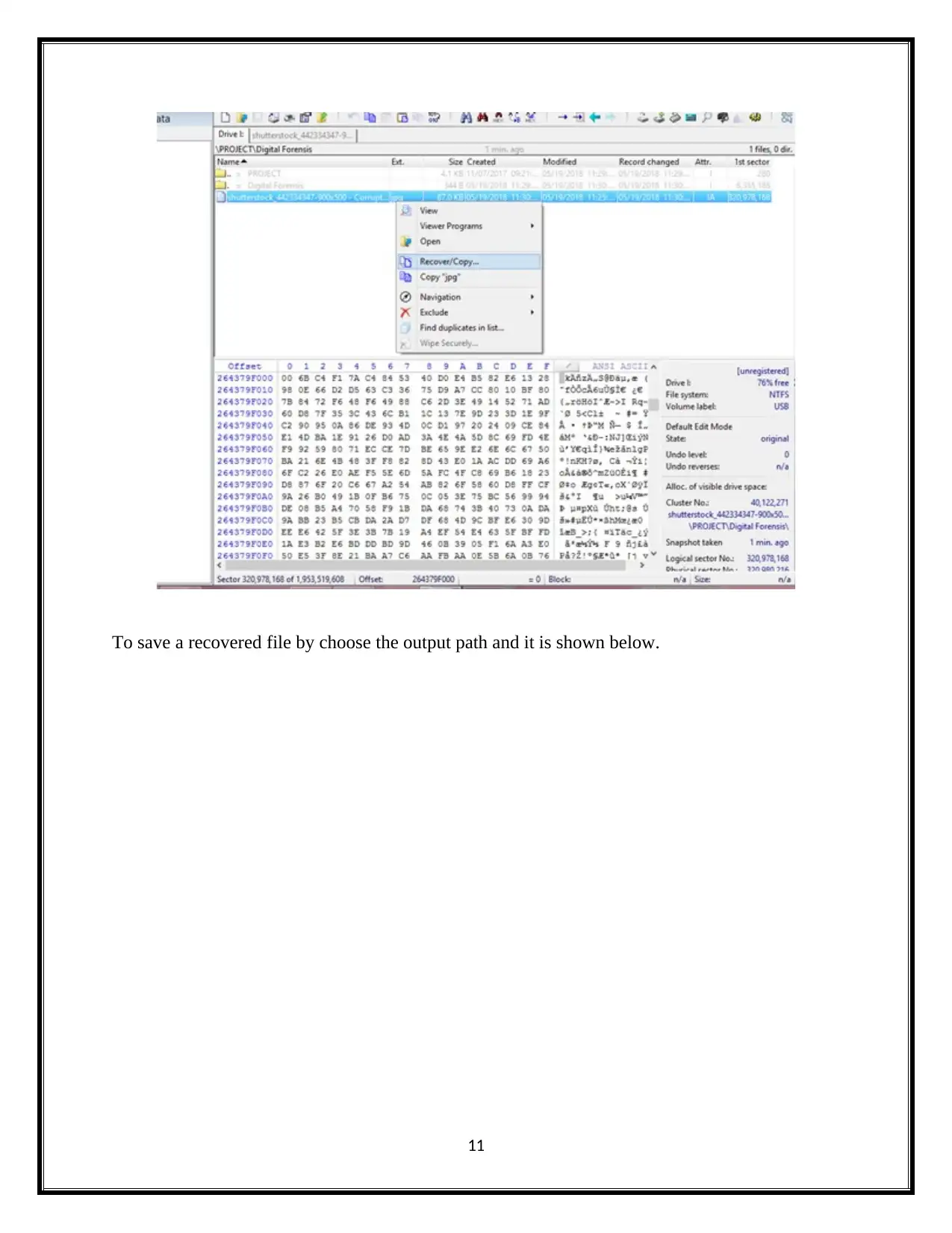
To save a recovered file by choose the output path and it is shown below.
11
11
Finally, it shows the corrupted file.
12
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


